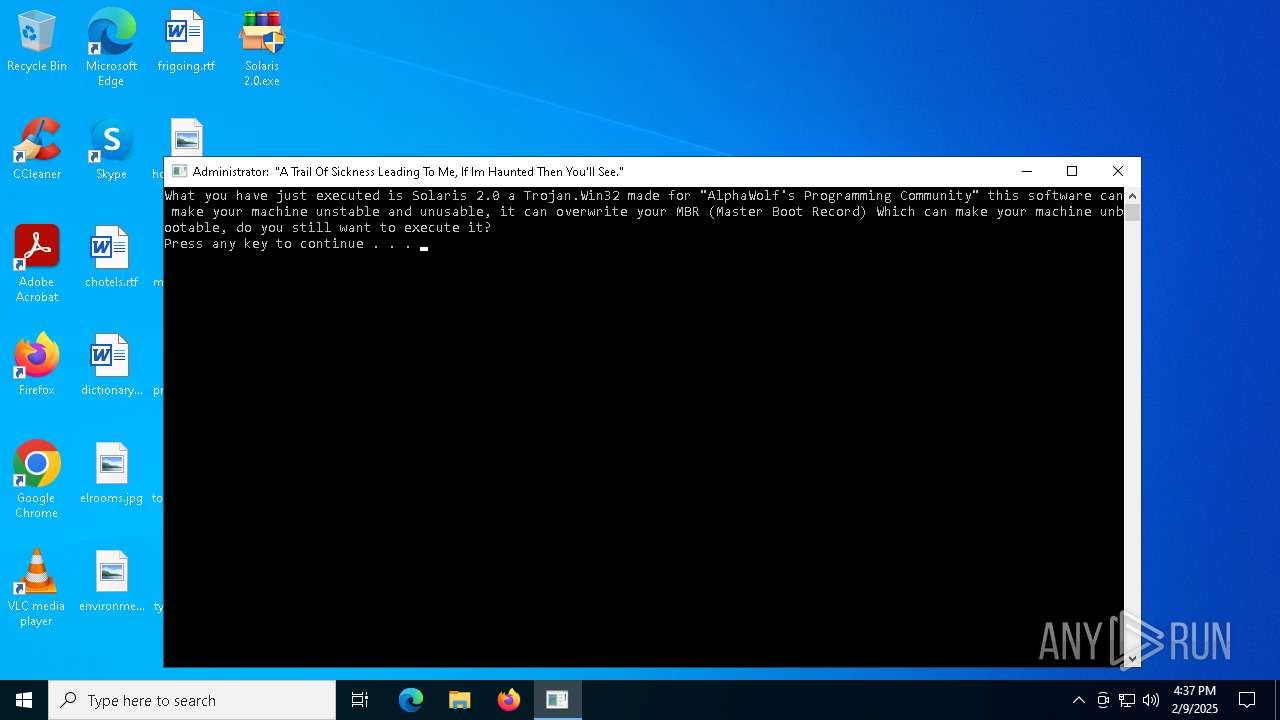
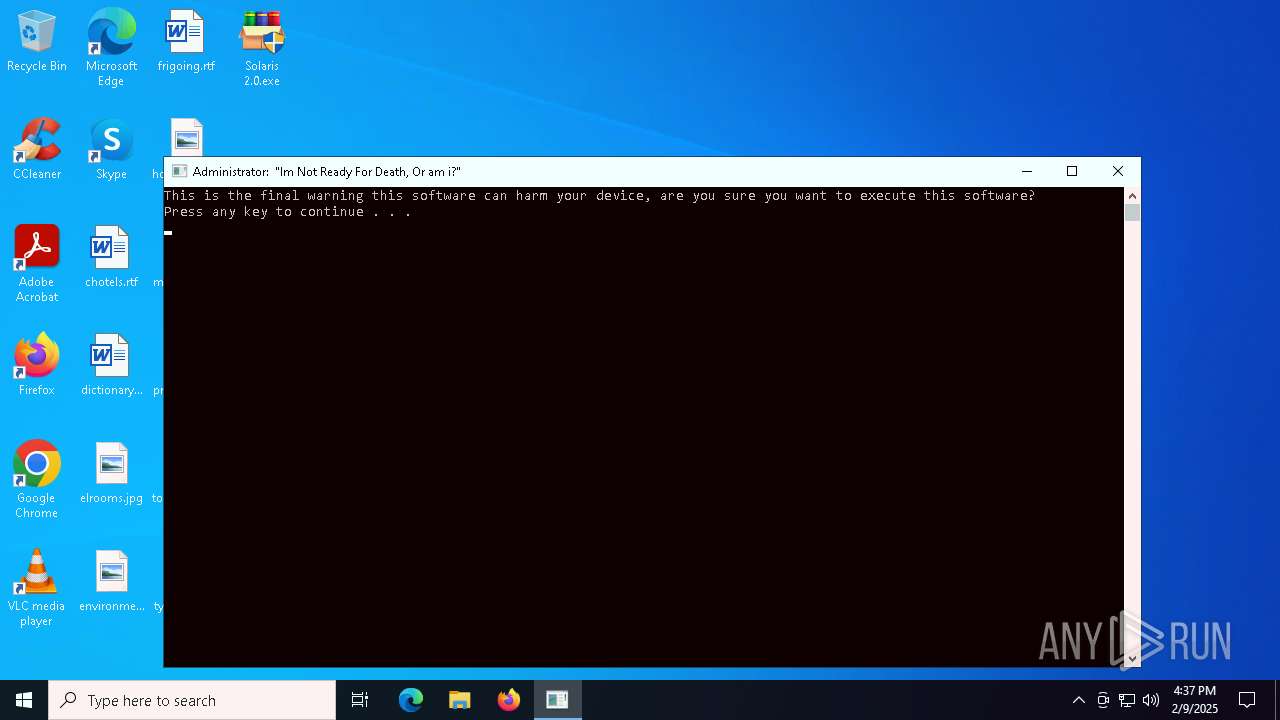
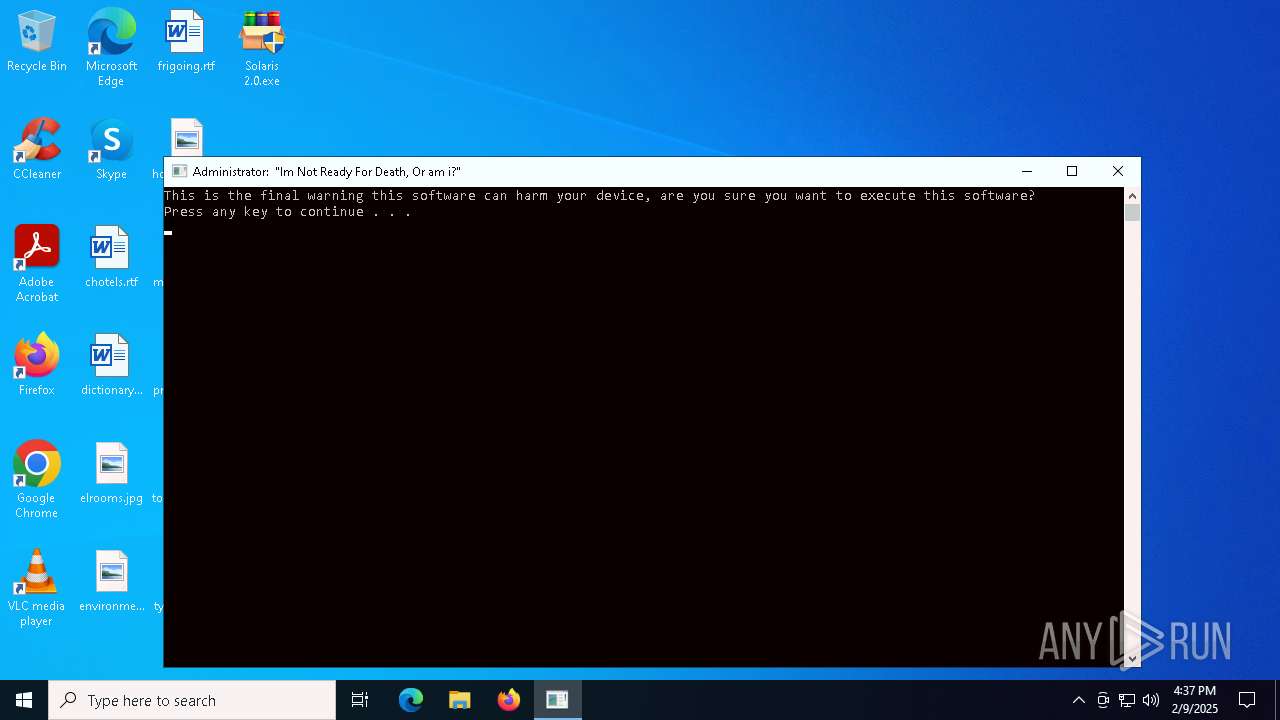
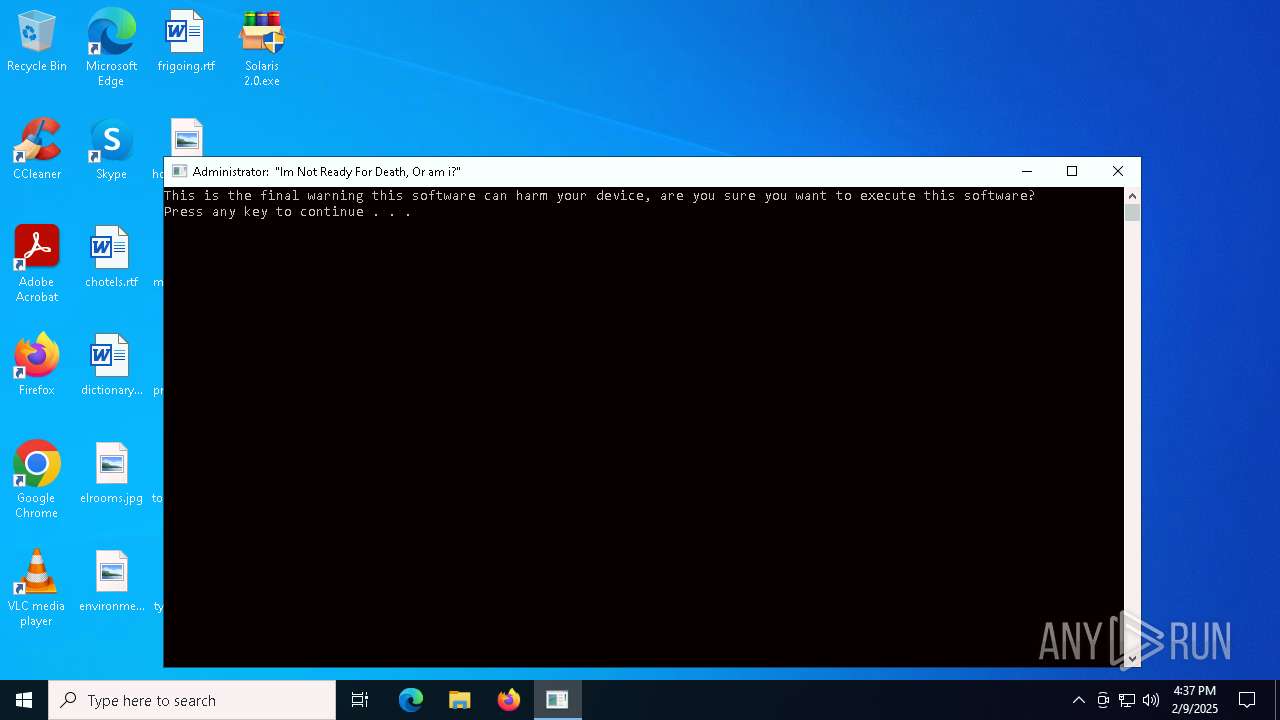
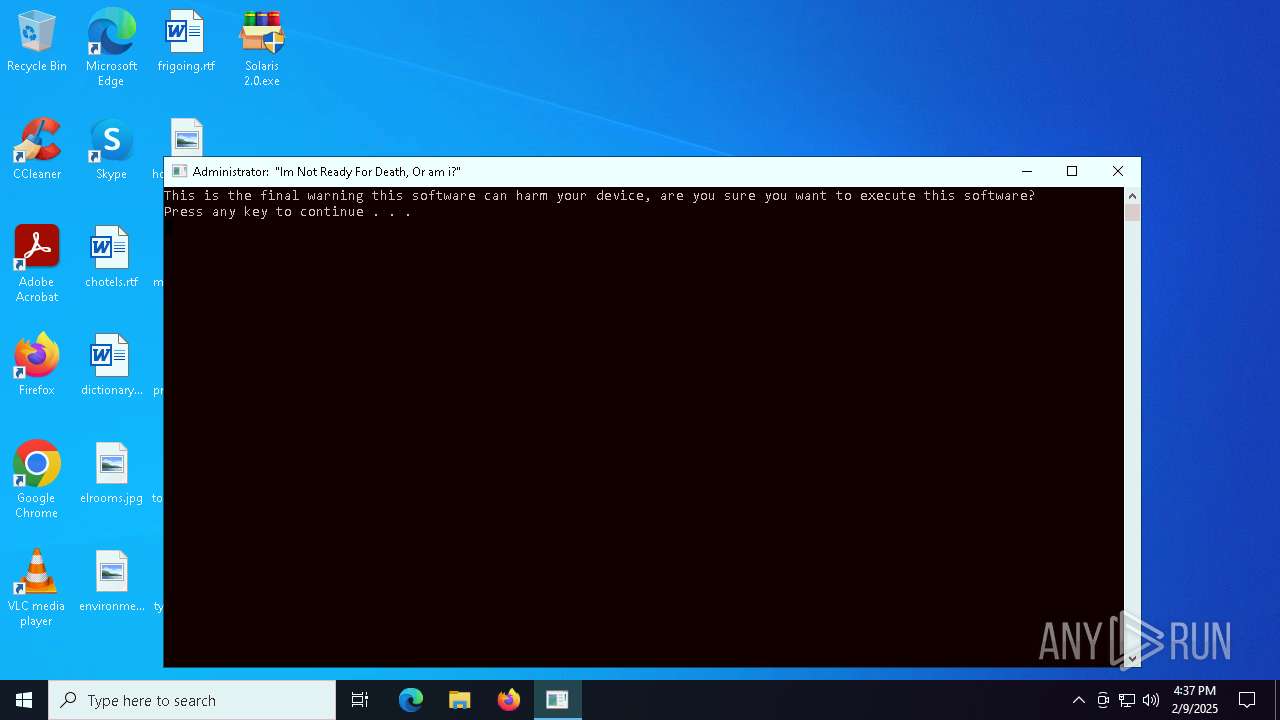
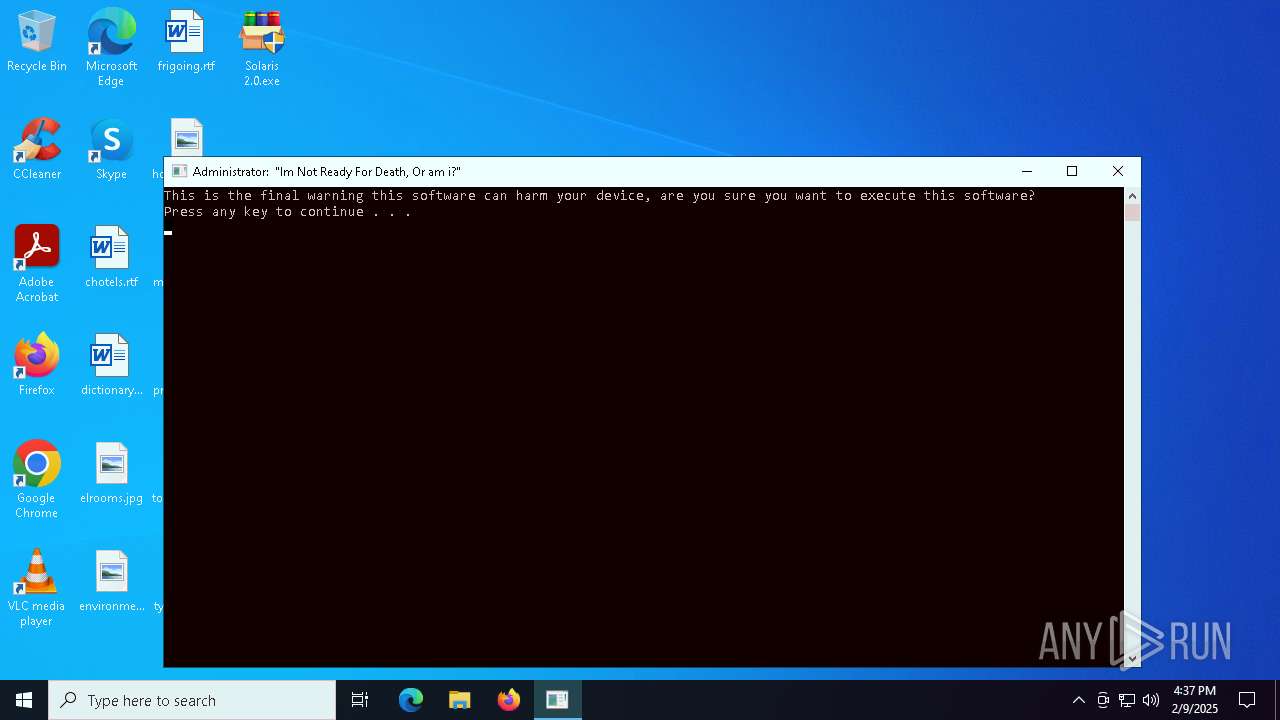
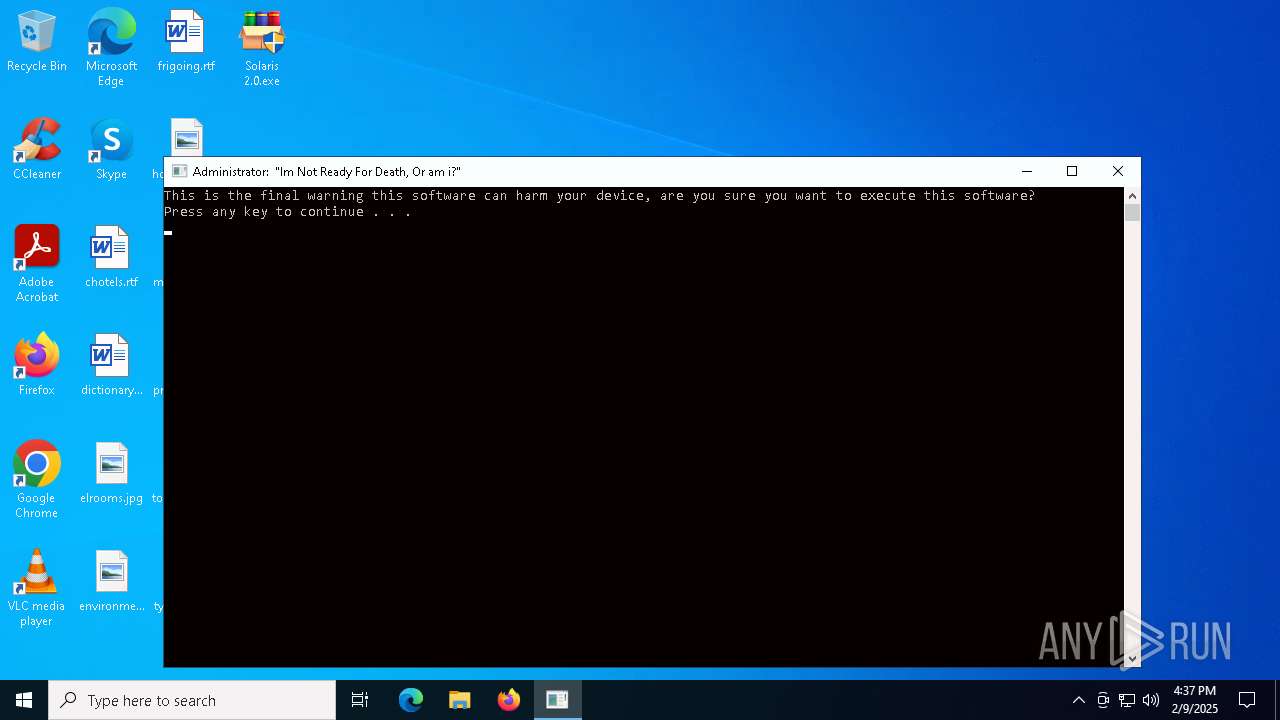
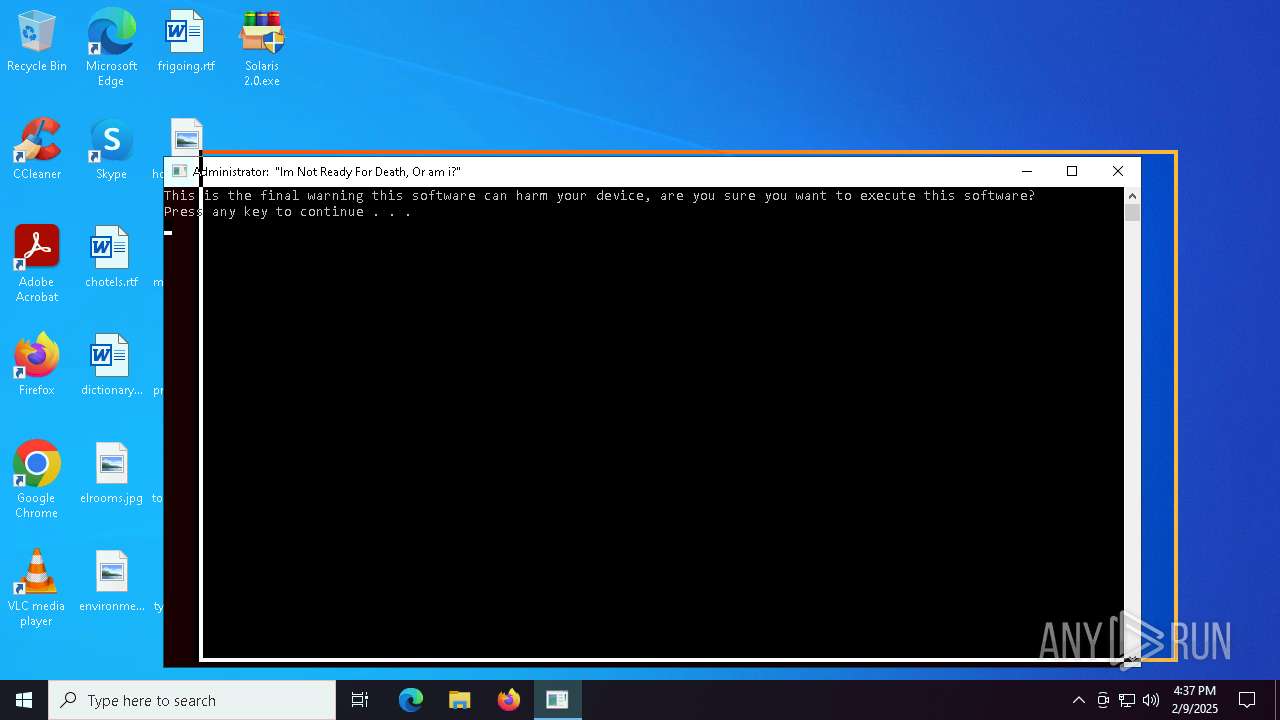
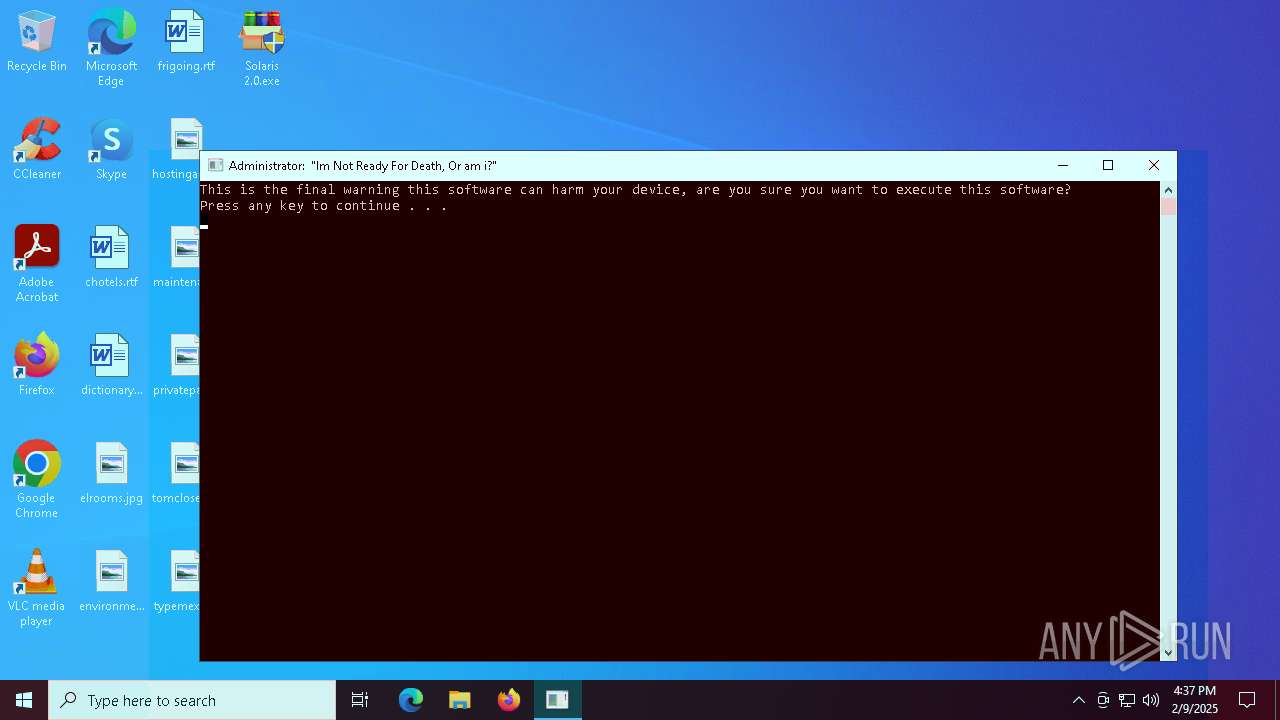
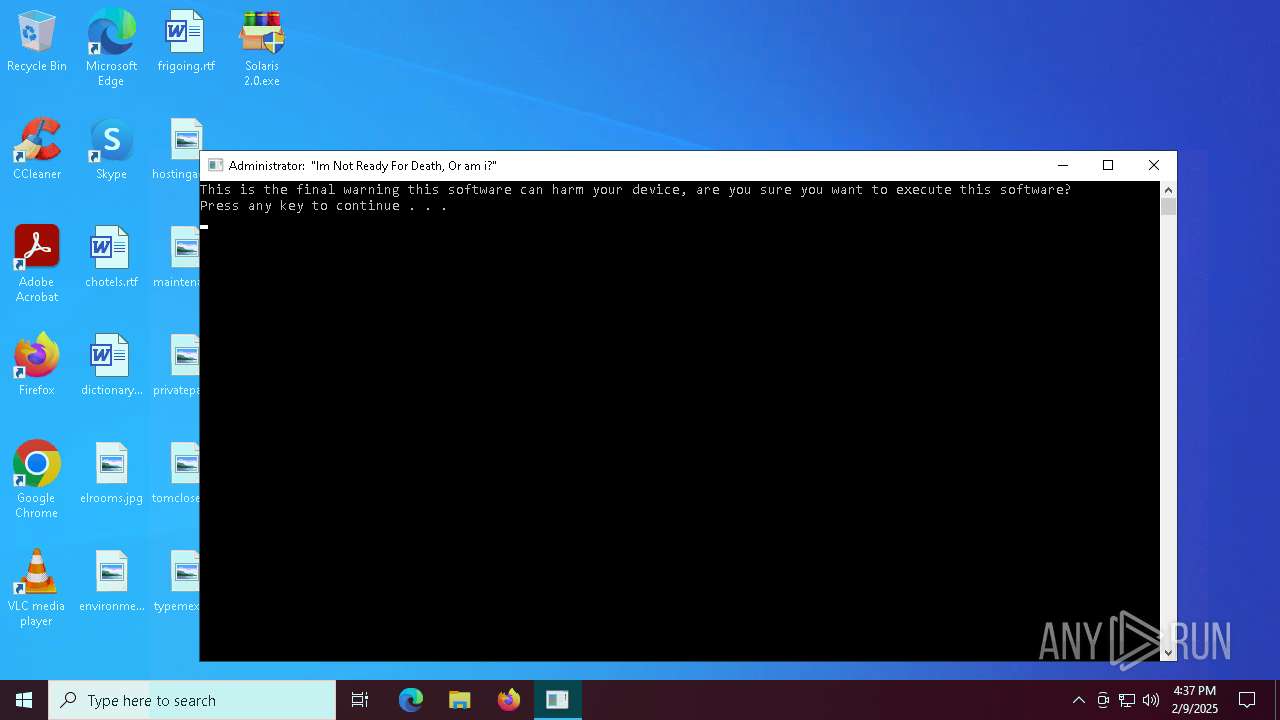
| File name: | Solaris 2.0.zip |
| Full analysis: | https://app.any.run/tasks/eb2a2497-ee74-4015-95b6-0fda7d0ca7be |
| Verdict: | Malicious activity |
| Analysis date: | February 09, 2025, 16:36:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | data |
| MD5: | 70689946DB6AED0958F37BA2F17D8271 |
| SHA1: | 620748231B1DA670182D7A45660438390A2A7EF3 |
| SHA256: | 2F42FC40A52387C55807F6B8317AE35B3CF8C1120F97554A6CF4B1201DF0845E |
| SSDEEP: | 98304:DFT+frTOGwn0OZpk8lw5pDJjta3q6iNCmGMzTOwUTjqyS++pZhuNhgQdIJDhXjeP:fTIqWAMWtdglhP0Fso09+o6Si |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates file in the systems drive root
- Solaris 2.0.exe (PID: 6952)
- conhost.exe (PID: 7048)
- Solaris.exe (PID: 7040)
- cmd.exe (PID: 7108)
- HITBMAP.exe (PID: 7144)
- AFirst.exe (PID: 4128)
- conhost.exe (PID: 5460)
- conhost.exe (PID: 3224)
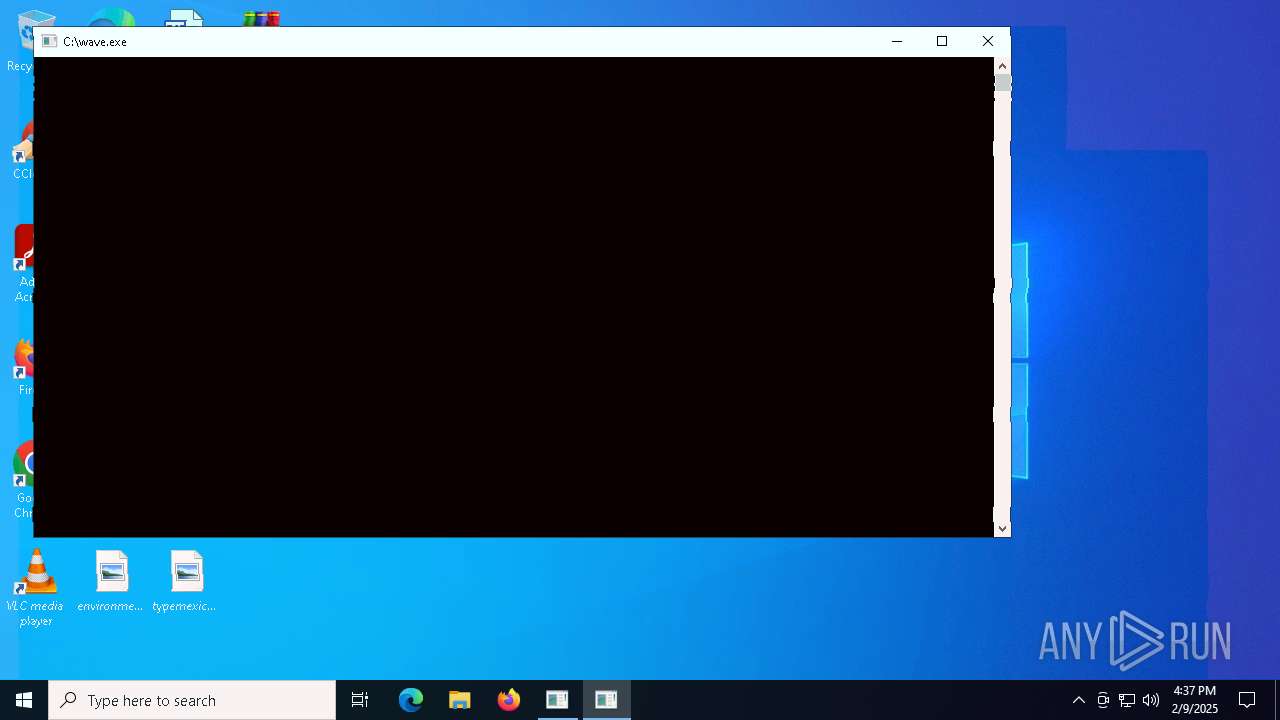
- wave.exe (PID: 5872)
- FIRST3.exe (PID: 2600)
- FIRST.exe (PID: 2728)
- FIRST3.exe (PID: 6576)
- conhost.exe (PID: 7032)
- FIRST3.exe (PID: 6844)
- FIRST3.exe (PID: 7060)
- FIRST.exe (PID: 7052)
- ATohou.exe (PID: 936)
- conhost.exe (PID: 6380)
- conhost.exe (PID: 6564)
- conhost.exe (PID: 6056)
- FIRST.exe (PID: 6760)
- conhost.exe (PID: 6732)
- RGB2.exe (PID: 6536)
- Circle2.exe (PID: 3144)
- AWave.exe (PID: 3920)
- conhost.exe (PID: 3612)
- conhost.exe (PID: 3664)
- CircleR.exe (PID: 6508)
- wave.exe (PID: 1172)
- conhost.exe (PID: 6332)
- conhost.exe (PID: 6452)
- ARGB.exe (PID: 5572)
- Shake.exe (PID: 1400)
- wave.exe (PID: 6404)
- APurple.exe (PID: 4300)
- conhost.exe (PID: 3000)
- Purple.exe (PID: 5208)
- Circle.exe (PID: 3832)
- Whoa.exe (PID: 6652)
- Circle.exe (PID: 1224)
- conhost.exe (PID: 5964)
- conhost.exe (PID: 4360)
- AWhoa.exe (PID: 640)
- AWhoa2.exe (PID: 1576)
- conhost.exe (PID: 6632)
- FIRST3.exe (PID: 6384)
- LAST.exe (PID: 6464)
- conhost.exe (PID: 6700)
- conhost.exe (PID: 6484)
- conhost.exe (PID: 6668)
- Squares2.exe (PID: 6432)
- Squares.exe (PID: 6696)
- Squares3.exe (PID: 6528)
- rotate.exe (PID: 6724)
Executable content was dropped or overwritten
- Solaris 2.0.exe (PID: 6952)
- Whoa.exe (PID: 6652)
Reads security settings of Internet Explorer
- Solaris 2.0.exe (PID: 6952)
Starts CMD.EXE for commands execution
- Solaris.exe (PID: 7040)
- Whoa.exe (PID: 6652)
Executing commands from a ".bat" file
- Solaris.exe (PID: 7040)
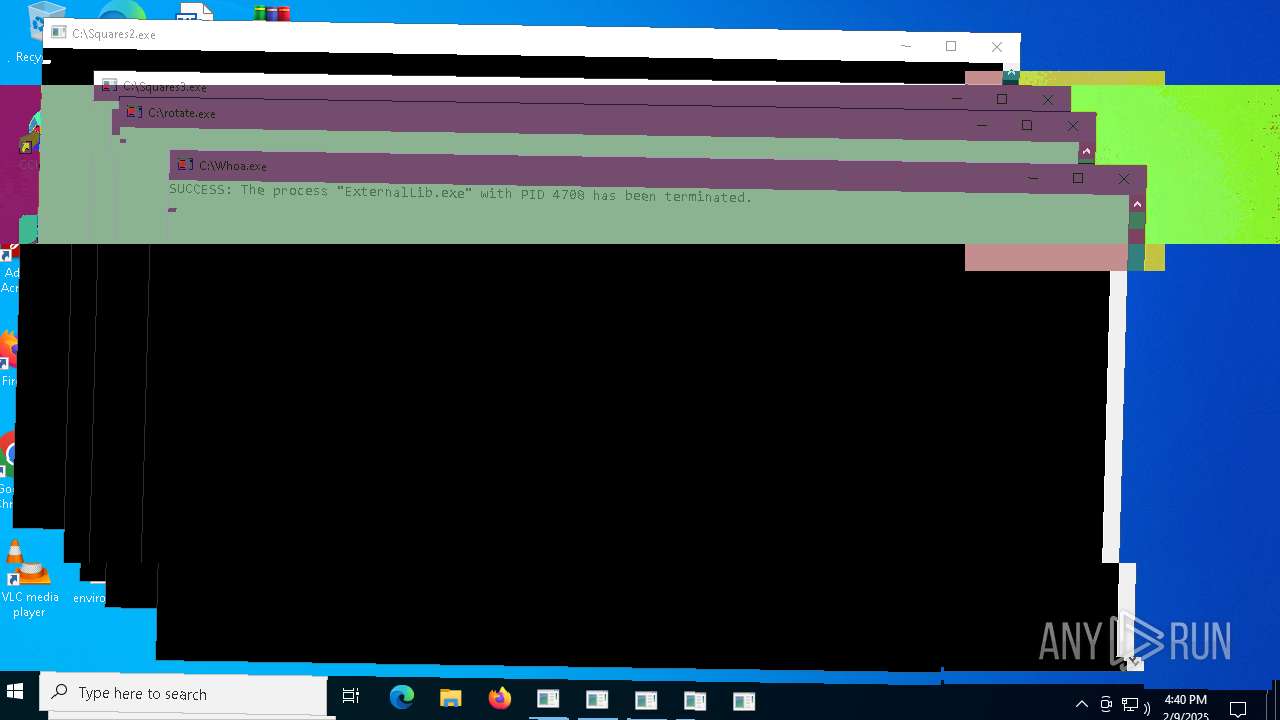
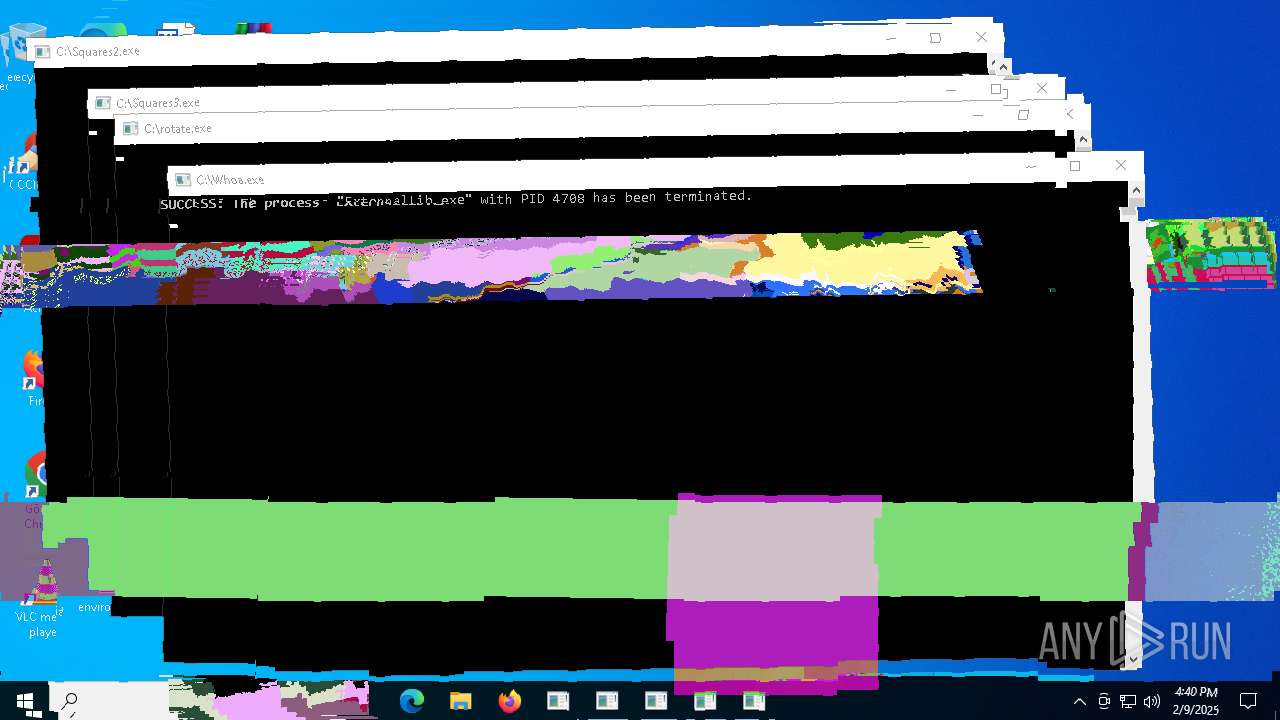
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7108)
- cmd.exe (PID: 6032)
There is functionality for taking screenshot (YARA)
- HITBMAP.exe (PID: 7144)
- wave.exe (PID: 5872)
- RGB2.exe (PID: 6536)
- Circle2.exe (PID: 3144)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7108)
INFO
Manual execution by a user
- Solaris 2.0.exe (PID: 6896)
- Solaris 2.0.exe (PID: 6952)
Checks supported languages
- SearchApp.exe (PID: 5064)
- Solaris 2.0.exe (PID: 6952)
- Solaris.exe (PID: 7040)
- wave.exe (PID: 5872)
- FIRST3.exe (PID: 2600)
- FIRST.exe (PID: 2728)
- FIRST3.exe (PID: 6576)
- FIRST3.exe (PID: 6844)
- FIRST3.exe (PID: 7060)
- FIRST.exe (PID: 7052)
- ATohou.exe (PID: 936)
- FIRST.exe (PID: 6760)
- Circle2.exe (PID: 3144)
- AWave.exe (PID: 3920)
- CircleR.exe (PID: 6508)
- RGB2.exe (PID: 6536)
- Circle.exe (PID: 3832)
- Shake.exe (PID: 1400)
- ARGB.exe (PID: 5572)
- wave.exe (PID: 6404)
- APurple.exe (PID: 4300)
- wave.exe (PID: 1172)
- Purple.exe (PID: 5208)
- Circle.exe (PID: 1224)
- Whoa.exe (PID: 6652)
- AWhoa2.exe (PID: 1576)
- HITBMAP.exe (PID: 7144)
- AWhoa.exe (PID: 640)
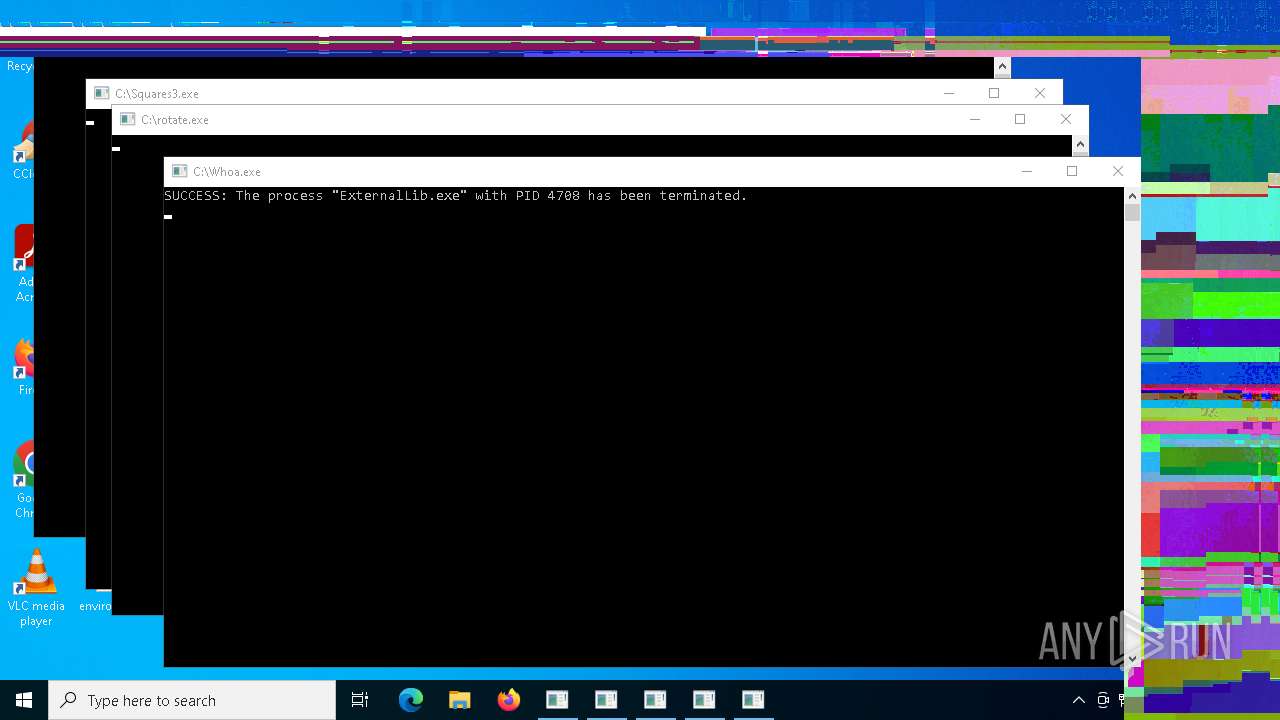
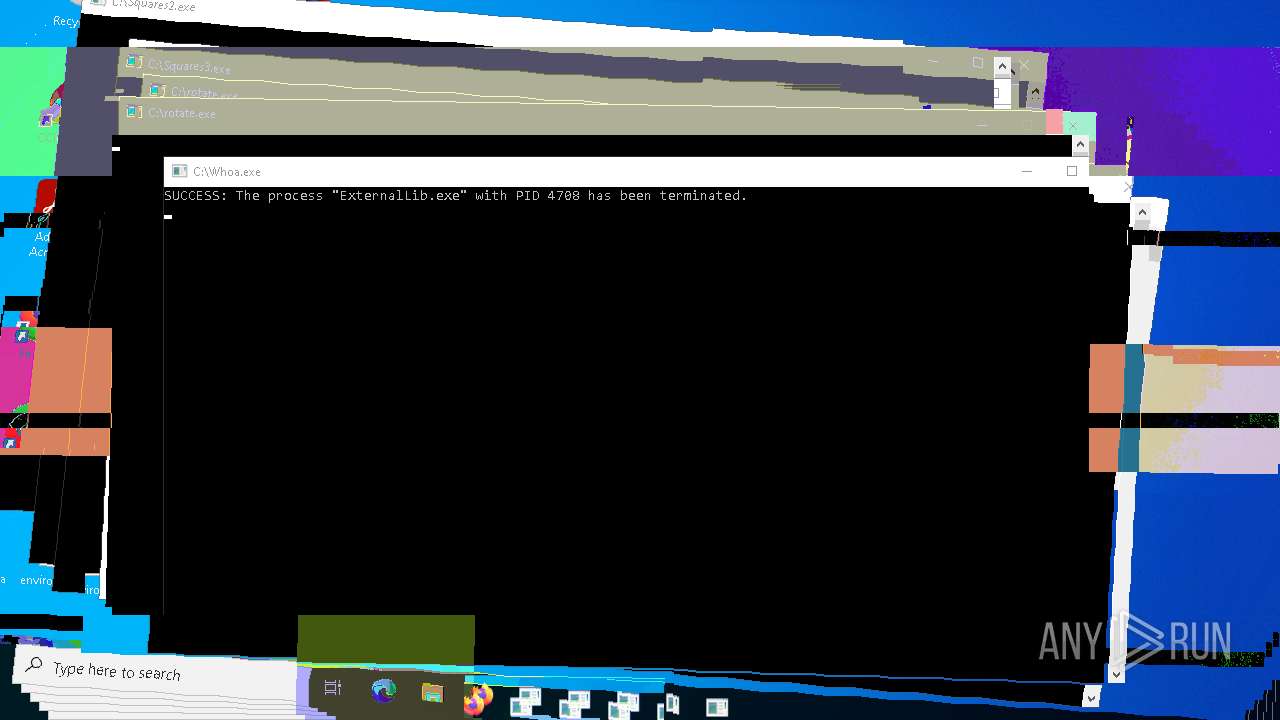
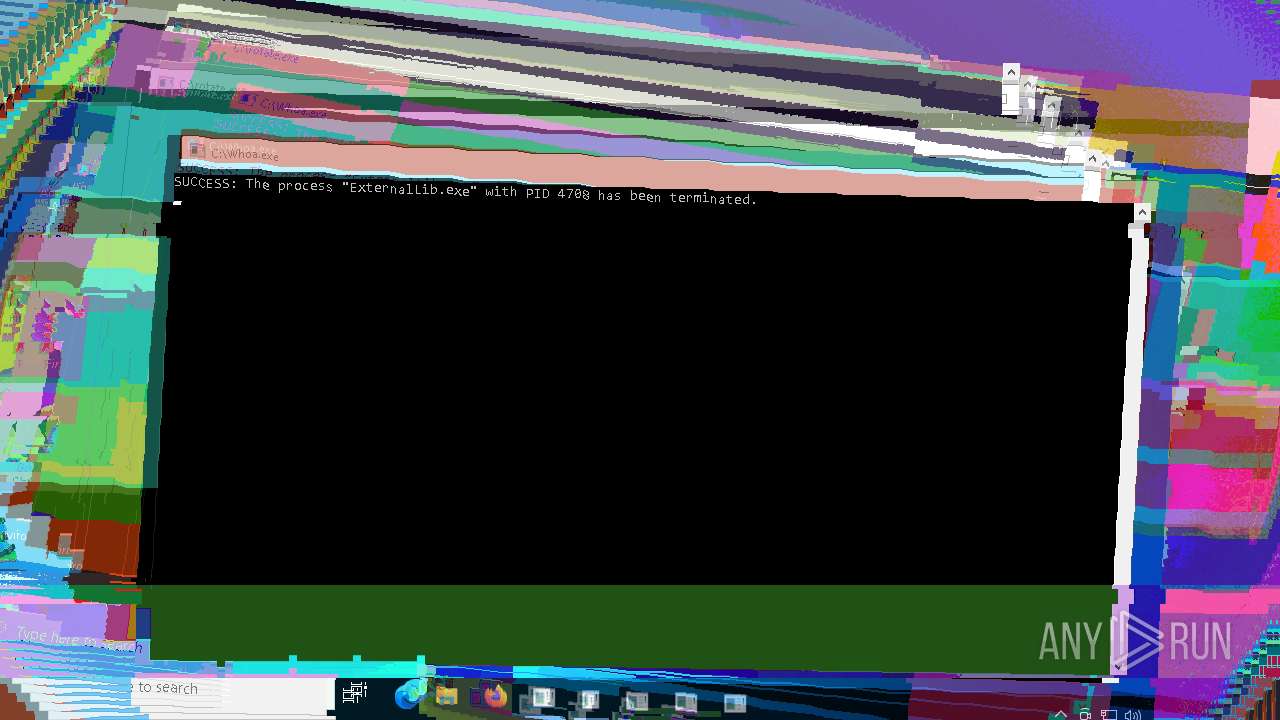
- ExternalLib.exe (PID: 4708)
- AFirst.exe (PID: 4128)
- Squares2.exe (PID: 6432)
- FIRST3.exe (PID: 6384)
- LAST.exe (PID: 6464)
- Squares.exe (PID: 6696)
- Squares3.exe (PID: 6528)
- rotate.exe (PID: 6724)
Reads the computer name
- Solaris 2.0.exe (PID: 6952)
- AFirst.exe (PID: 4128)
- ATohou.exe (PID: 936)
- AWave.exe (PID: 3920)
- ARGB.exe (PID: 5572)
- APurple.exe (PID: 4300)
- AWhoa2.exe (PID: 1576)
- AWhoa.exe (PID: 640)
Process checks computer location settings
- Solaris 2.0.exe (PID: 6952)
- SearchApp.exe (PID: 5064)
Create files in a temporary directory
- Solaris.exe (PID: 7040)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5064)
Reads the software policy settings
- SearchApp.exe (PID: 5064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
233
Monitored processes
106
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | PING localhost -n 3 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | taskkill /f /im ExternalLib.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | C:\AWhoa.exe | C:\AWhoa.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 836 | PING localhost -n 2 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | PING localhost -n 2 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | PING localhost -n 2 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | C:\ATohou.exe | C:\ATohou.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1016 | PING localhost -n 20 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1172 | C:\wave.exe | C:\wave.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1216 | taskkill /f /im FIRST3.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 258
Read events
14 192
Write events
50
Delete events
16
Modification events
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Solaris 2.0.zip | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5432) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\ConstraintIndex |
| Operation: | write | Name: | CurrentConstraintIndexCabPath |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0049006E007000750074005F007B00380033003200620036003800640032002D0037006600650032002D0034006500370031002D0061003300610064002D003200360031003600360062003600350036006500630036007D00000030A812C2107BDB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\AppsConstraintIndex |
| Operation: | write | Name: | LatestConstraintIndexFolder |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C005000610063006B0061006700650073005C004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E005300650061007200630068005F006300770035006E003100680032007400780079006500770079005C004C006F00630061006C00530074006100740065005C0043006F006E00730074007200610069006E00740049006E006400650078005C0041007000700073005F007B00330030006300360036003800330066002D0039006500650033002D0034003700660037002D0062003700340033002D003700610033006300620061003800310065003700340030007D00000030A812C2107BDB01 | |||
Executable files
34
Suspicious files
7
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5432 | WinRAR.exe | C:\Users\admin\Desktop\Solaris 2.0.exe | — | |
MD5:— | SHA256:— | |||
| 6952 | Solaris 2.0.exe | C:\ACube.exe | executable | |
MD5:1350AD92D4EB35B3B5D9D6A540B44B26 | SHA256:36635E74187D053799FE06A457FB80E88B8F9353ECC0E9DE99544CDA71E26330 | |||
| 6952 | Solaris 2.0.exe | C:\ADun.exe | executable | |
MD5:811F99752EEA779FE1B9E8B037B374A0 | SHA256:7B909447057C4A860B50A95DC35B6956DEF5B74C154133D59716DF4F9AEA6FD5 | |||
| 6952 | Solaris 2.0.exe | C:\AFirst.exe | executable | |
MD5:E21EB450137C6E787270F58A1074E9BB | SHA256:2E04CCC256D2F7590AFEAADC7C052AC4B2BE3C7FEBA16F3226979D5A1FB19D48 | |||
| 6952 | Solaris 2.0.exe | C:\tasks.txt | text | |
MD5:4173787AC51B8AED10BB422AC44D1202 | SHA256:0AFE41FCA69BF58CB6374C8BFF84218B7692F452915EACF9C3ABA83966376CEB | |||
| 6952 | Solaris 2.0.exe | C:\APurple.exe | executable | |
MD5:E2100774735D298BA44FE500FD39685E | SHA256:BCEDAFAF4BFC87F26DE5B9B5BEC2CC41155E7C3BA5C0836090EBE9D4E44BB8B7 | |||
| 6952 | Solaris 2.0.exe | C:\FIRST.exe | executable | |
MD5:160E43B5F824292DB1D18C378D12C2FD | SHA256:CFDE7B7F764F3E26E6126DA6091FD6FB6944333D1B10C85C96151ECFEE56B70A | |||
| 6952 | Solaris 2.0.exe | C:\CircleR.exe | executable | |
MD5:3320736FA889FB1D20392E58F15884A1 | SHA256:91F70A29E8C90D89BF2CDCC389A7A06EEF0D4710FF255D204119857ACE898036 | |||
| 6952 | Solaris 2.0.exe | C:\Circle2.exe | executable | |
MD5:89C39815003090838EB6B7BD87F5525D | SHA256:9EBDA86D4ED28999D69C1E0F50FCAB9B191BF15ACC1D9CC0A597263EE36B6610 | |||
| 6952 | Solaris 2.0.exe | C:\FIRST3.exe | executable | |
MD5:EAD502D394DE29812FD9036AEE094F76 | SHA256:5B6359FC7B67CF6883D7BEE2F3FAD9A130572124EACFC849710104B30B5359D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
35
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3220 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6752 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6752 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3220 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.21.65.153:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
1176 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |