| File name: | 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe |
| Full analysis: | https://app.any.run/tasks/fc65a3d9-bfdc-47d8-a9c0-31f5d5ee422e |
| Verdict: | Malicious activity |
| Analysis date: | July 20, 2025, 00:03:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, UPX compressed, 5 sections |
| MD5: | B797FF929B50AF21A3ABC198618ED6FB |
| SHA1: | 85830278B59D4DB6ADD01DF4D3601E86BDF364E0 |
| SHA256: | 2F4129205E4F9C50533D76180EBF5394F9903831223D6DD400B22567B7CB9BE6 |
| SSDEEP: | 98304:L4kEm2O0uh68QqoBXSCXPGms1lw3F0YmKDSd0ujR58Vq84wE8hnHkiSZLc5v1IV5:Uc |
MALICIOUS
Create files in the Startup directory
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
SUSPICIOUS
Executable content was dropped or overwritten
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
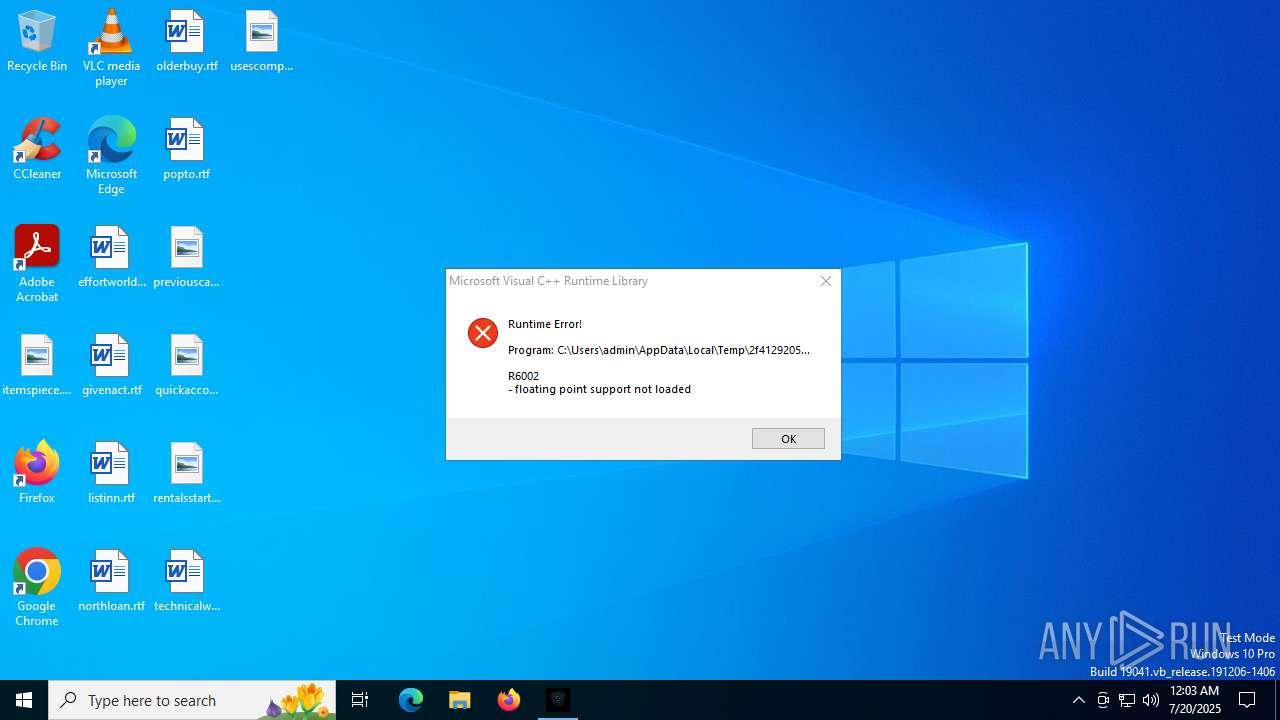
Executes application which crashes
- h21vnc.exe (PID: 6004)
INFO
Create files in a temporary directory
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
The sample compiled with english language support
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
Reads mouse settings
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
Checks supported languages
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
- h21vnc.exe (PID: 6004)
Creates files or folders in the user directory
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
- WerFault.exe (PID: 1392)
Launching a file from the Startup directory
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
Reads the machine GUID from the registry
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
Reads the computer name
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
UPX packer has been detected
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
The process uses AutoIt
- 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe (PID: 4888)
Checks proxy server information
- WerFault.exe (PID: 1392)
Reads the software policy settings
- WerFault.exe (PID: 1392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (12.9) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (12.7) |
| .exe | | | Win32 EXE Yoda's Crypter (12.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:05:08 21:27:44+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 352256 |
| InitializedDataSize: | 1097728 |
| UninitializedDataSize: | 1617920 |
| EntryPoint: | 0x2800a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | wuauclt |
| OriginalFileName: | TieringEngineService |
| CompanyName: | MpSigStub |
| FileVersion: | 931.231.288.131 |
| LegalCopyright: | rwinsta |
| ProductName: | NetCfgNotifyObjectHost |
| ProductVersion: | 288.219.12.534 |
Total processes
140
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1392 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6004 -s 592 | C:\Windows\SysWOW64\WerFault.exe | h21vnc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2032 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | C:\WINDOWS\system32\svchost.exe -k | C:\Windows\System32\svchost.exe | — | h21vnc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 4888 | "C:\Users\admin\AppData\Local\Temp\2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe" | C:\Users\admin\AppData\Local\Temp\2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe | explorer.exe | ||||||||||||
User: admin Company: MpSigStub Integrity Level: MEDIUM Description: wuauclt Version: 931.231.288.131 Modules
| |||||||||||||||
| 6004 | C:\Users\admin\AppData\Local\Temp\h21vnc.exe | C:\Users\admin\AppData\Local\Temp\h21vnc.exe | 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
Total events
3 339
Read events
3 339
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
6
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1392 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_h21vnc.exe_621f36305e8aaf2bb2e86cdc8d4b1b2b7a85e0ea_c5da2225_8d8a411c-60f5-4120-9c8c-ddc3d26f67f7\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4888 | 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe | C:\Users\admin\AppData\Local\Temp\h21vnc.exe | executable | |
MD5:153A674EC4BF72F7EE879BDA3EFB7071 | SHA256:36D31B2C7C3352C0DF1541D8F88B6149EB75E34D307AB36FECE69EF4A0C0A82E | |||
| 4888 | 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\PkgMgr.url | binary | |
MD5:FF8C19D02CFA405DA7D6793139B46F4C | SHA256:9B43C301AE44B0870A912CD018C05C2789D96A6B2B43E889B51C85F69D4C649F | |||
| 1392 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD57B.tmp.dmp | binary | |
MD5:F4DF5AA5C3EB5298E03ABA5CE2F5A228 | SHA256:F39A75308658B52FCD39AF5C5DDB20775F54BE5E25EC2C550A605CCA0DB13C3E | |||
| 4888 | 2f4129205e4f9c50533d76180ebf5394f9903831223d6dd400b22567b7cb9be6.exe | C:\Users\admin\AppData\Roaming\mighost\dstokenclean.exe | executable | |
MD5:D05DDA166E3B1020B99C767FD6FC9A05 | SHA256:8573A1D567B77C875548C40E2691D3886BE0C3022997BC1CA08A2CEFFF23E37F | |||
| 1392 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD5CA.tmp.WERInternalMetadata.xml | xml | |
MD5:4E528C4D5B264DB5E05BC2F6AEAA2714 | SHA256:FF5FD50EF6E73F0CDA5D55FC23F2152AE751CC1968E56DEDC82D13074CA06A61 | |||
| 1392 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:59F4837287068CCE20DB5DF92011167E | SHA256:4D441044A817C4A7A1CF00D628470BC9285638B68DB581C1F17748EC1FCF13E3 | |||
| 1392 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:0F7B8F6A846AA9CA52FA562DDDCDB5ED | SHA256:AFF90E65A81289B80D1FCC5E71B3D88E5D1AAFE22CE358EB6E28A56D1845263D | |||
| 1392 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD5EB.tmp.xml | xml | |
MD5:9D50C214287E2A20C39E507C8923EEB2 | SHA256:AA6207B5C0A4C58FD84C3B4EAFD7AEFAE179E1699ED68A5CDC34401E89F48C86 | |||
| 1392 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:D310523737A0D4D05066857AC157F458 | SHA256:0A0520D498306689AFA3CAC09ACE82E09229108FC9FABA5A906291D077004484 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
24
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1392 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1392 | WerFault.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4032 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
828 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4032 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1392 | WerFault.exe | 52.168.117.173:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1392 | WerFault.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1392 | WerFault.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |