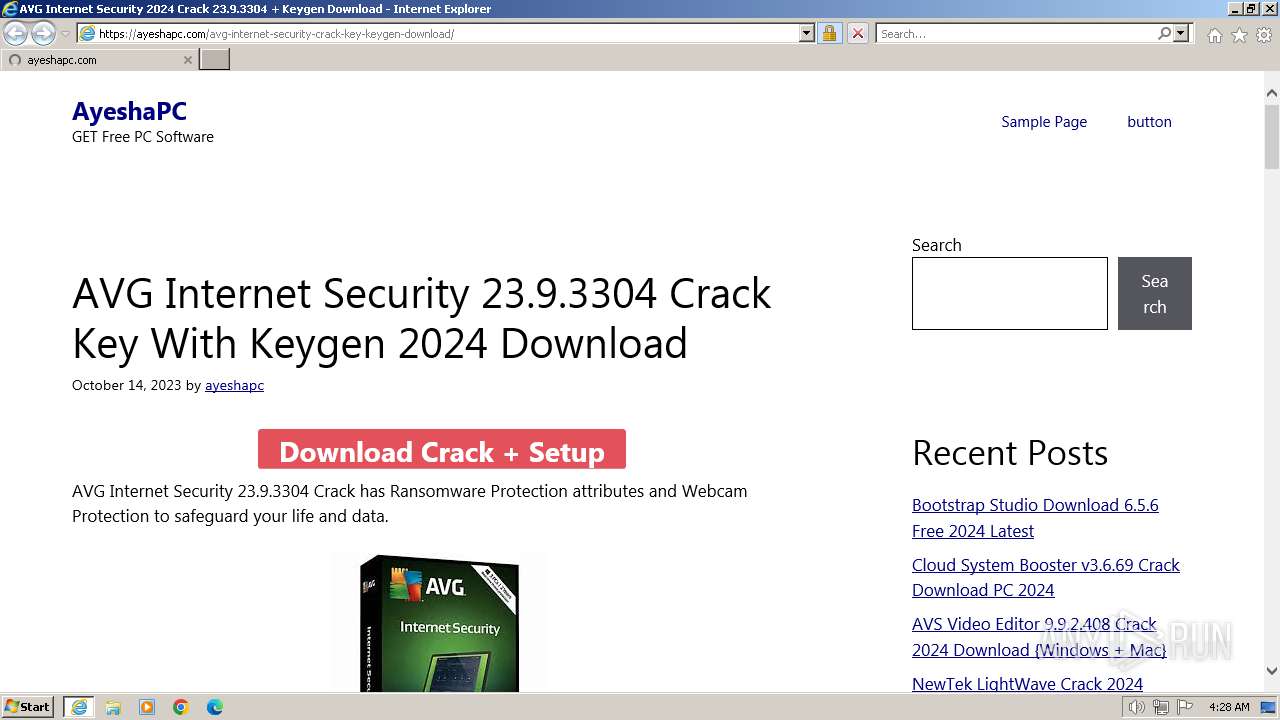
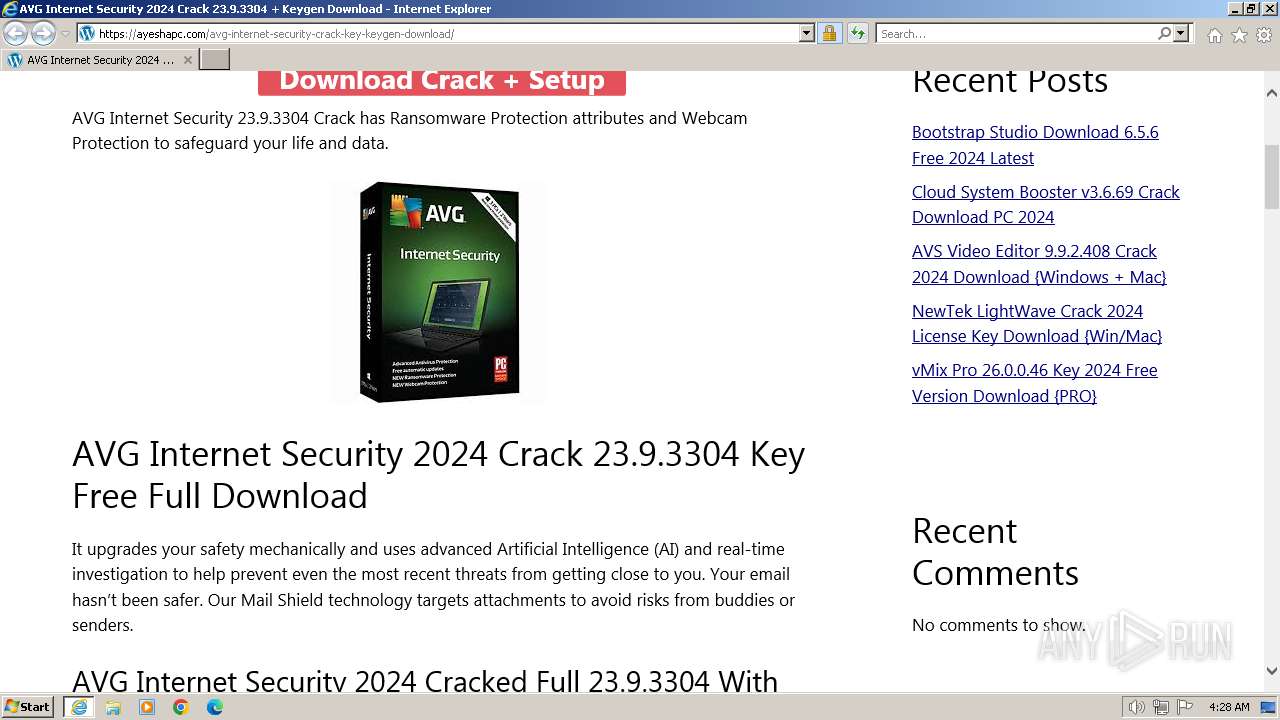
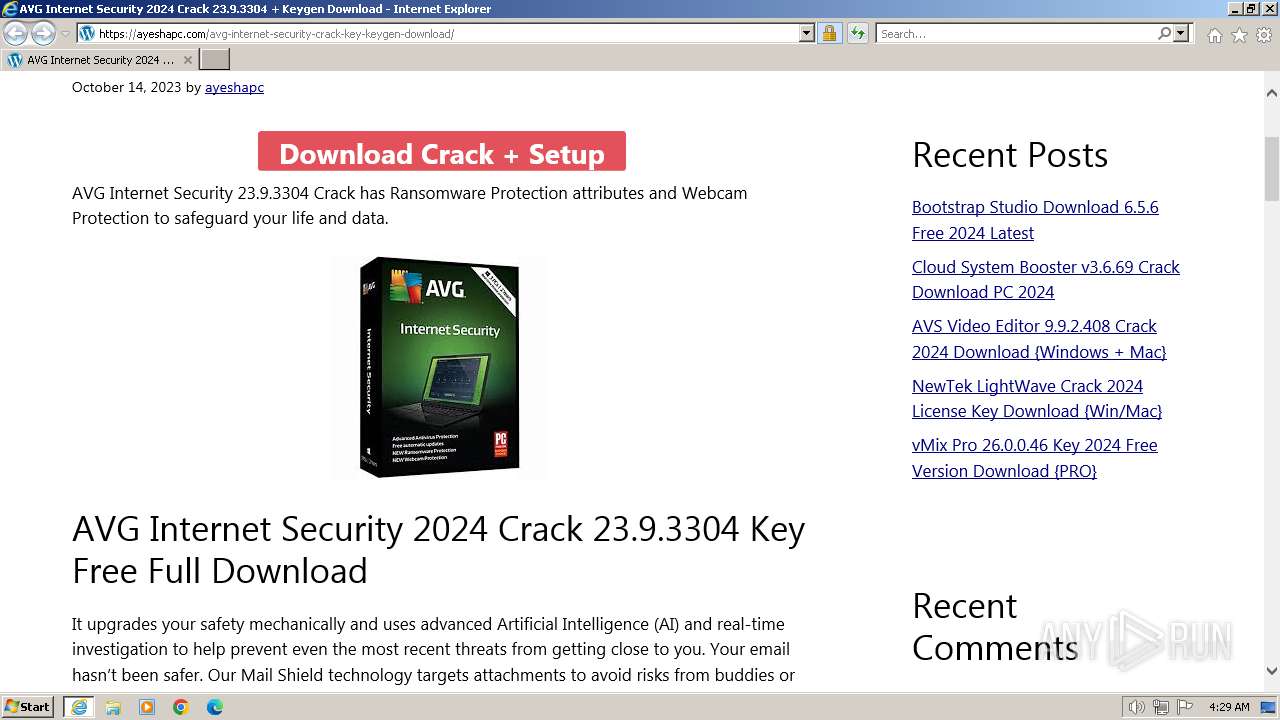
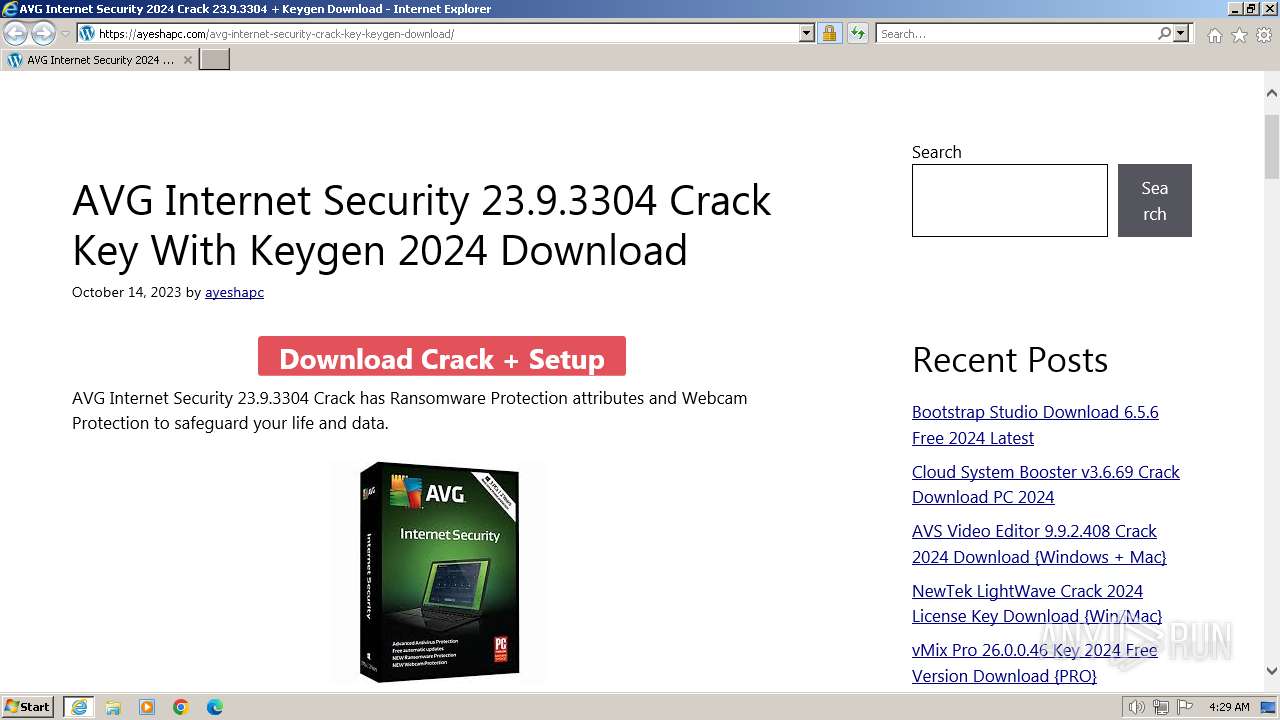
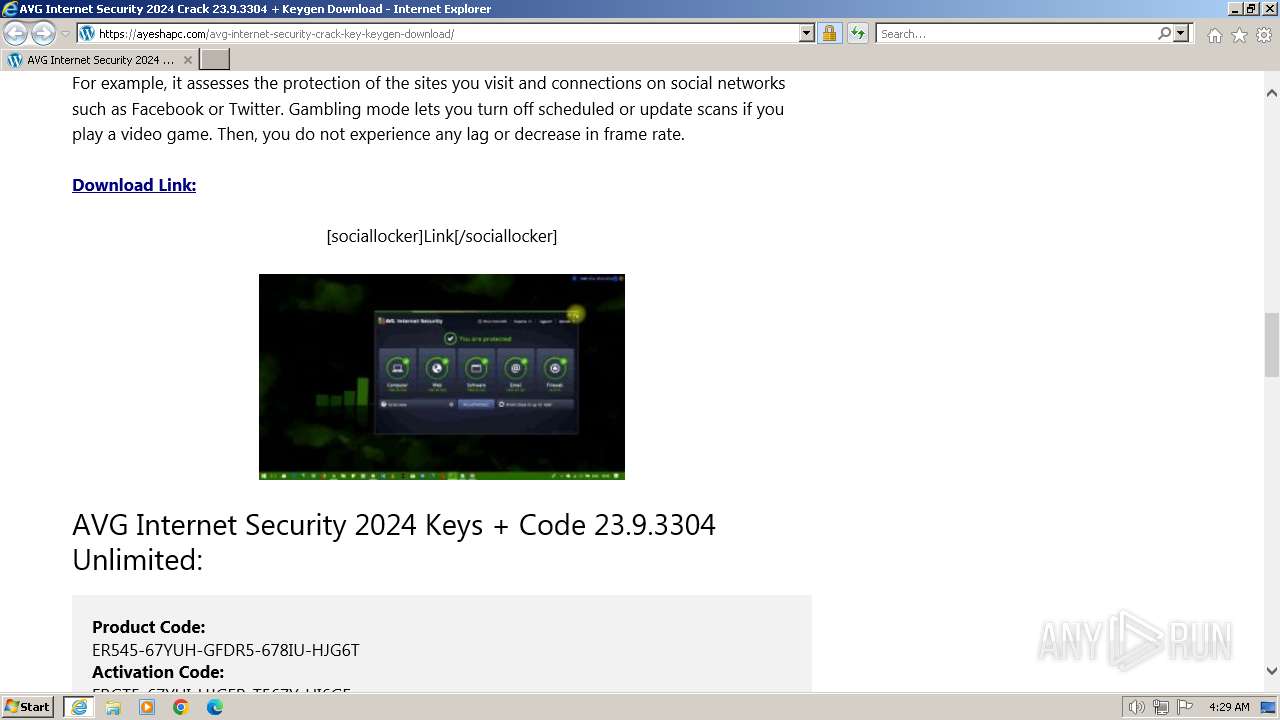
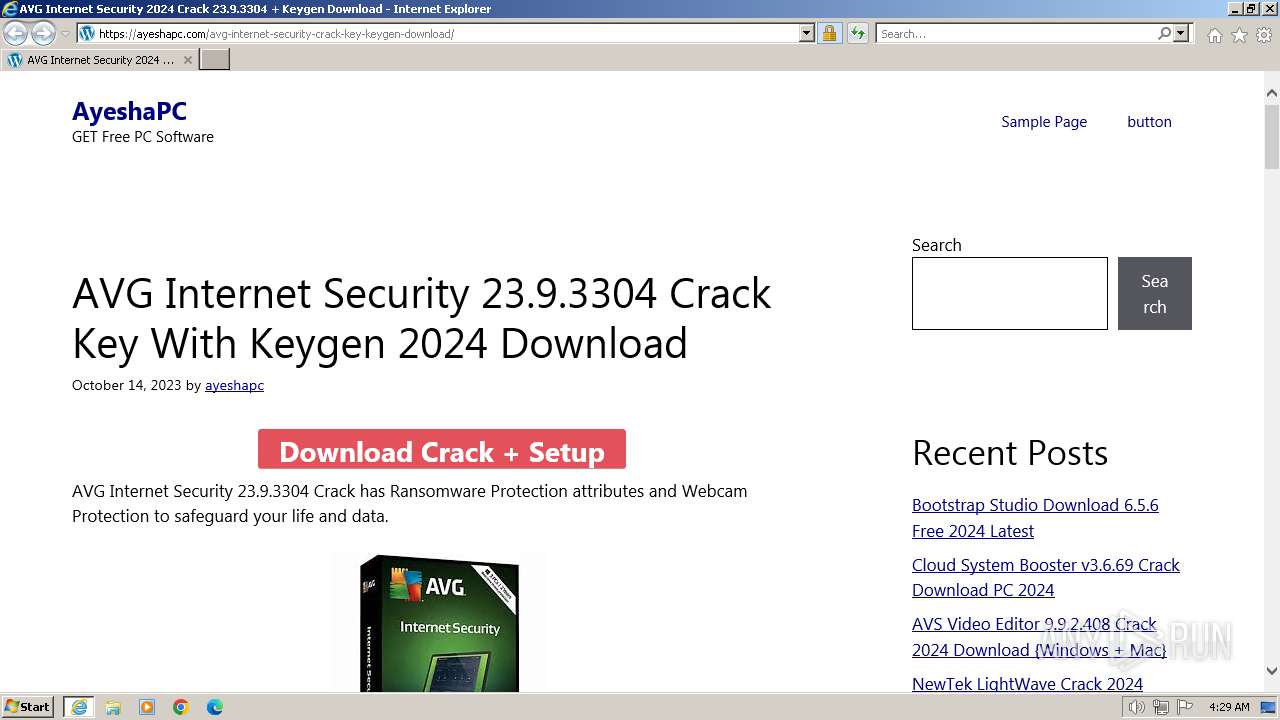
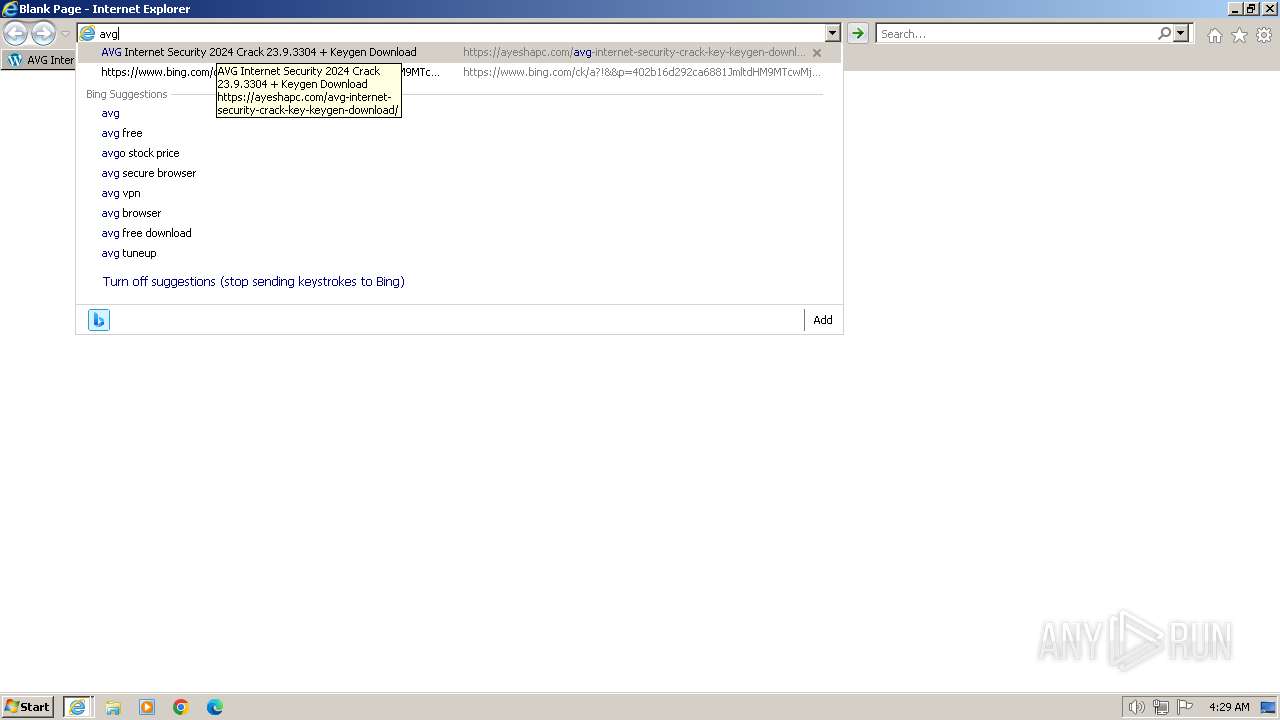
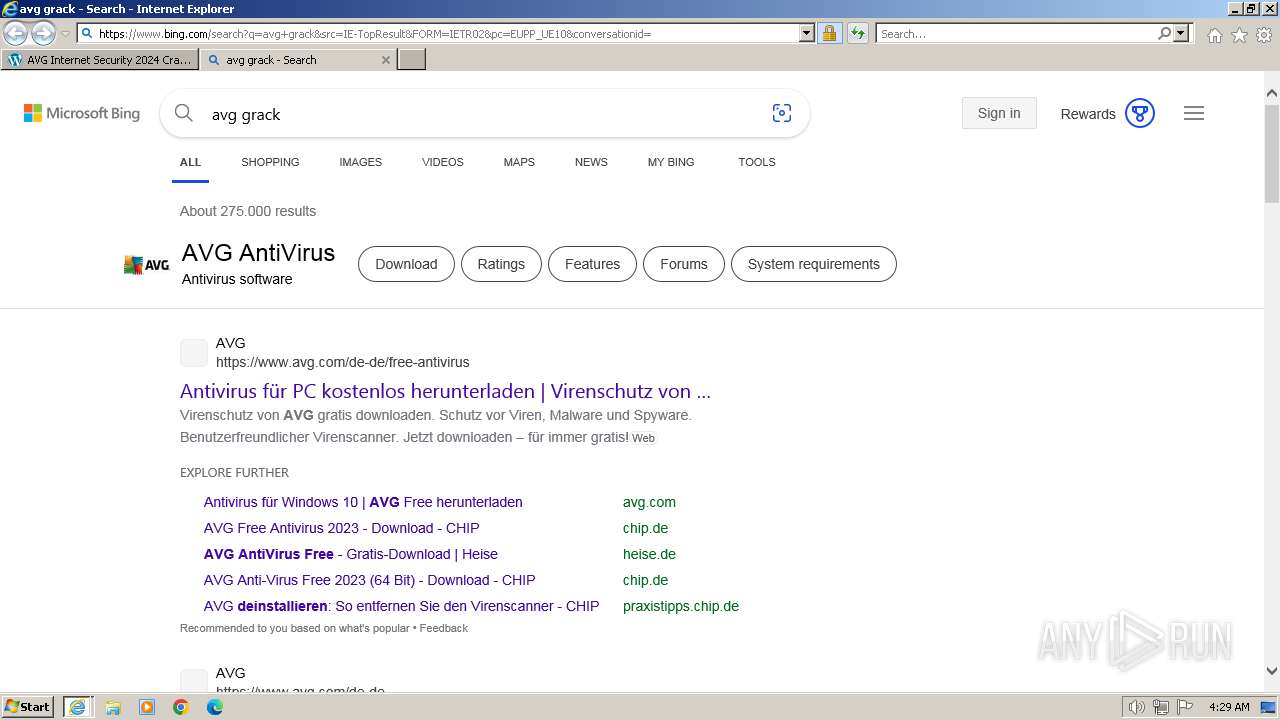
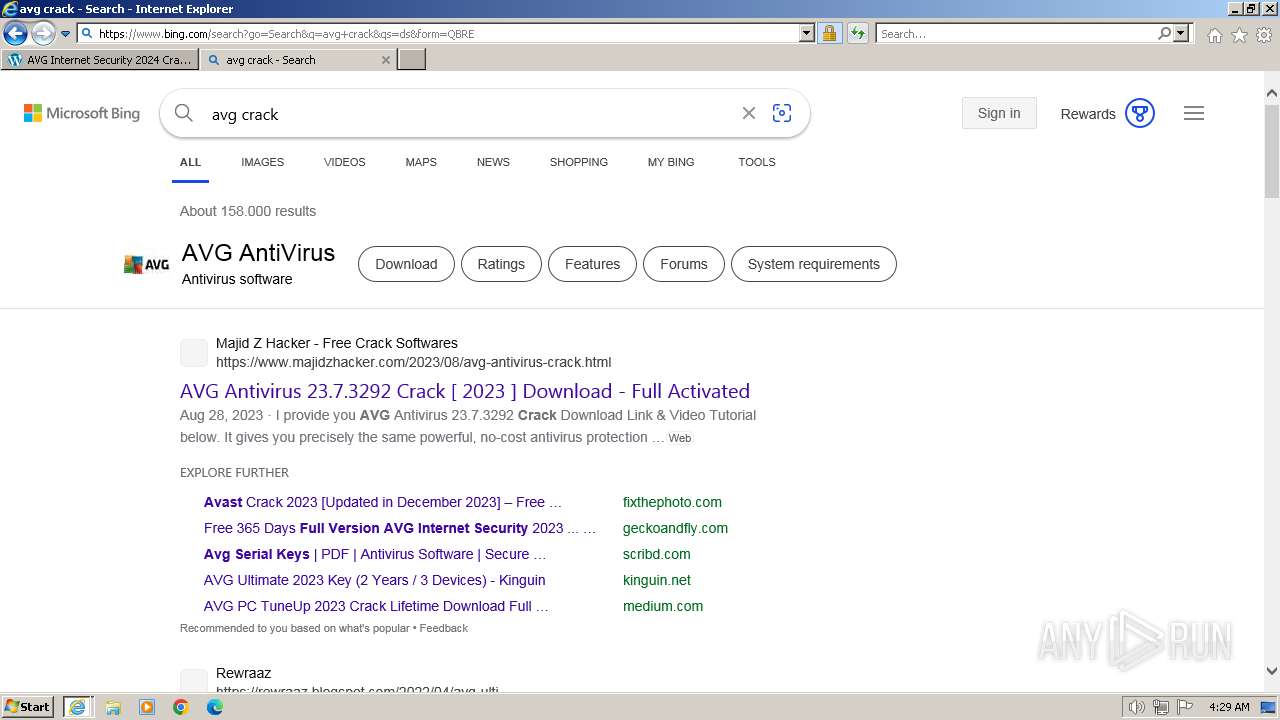
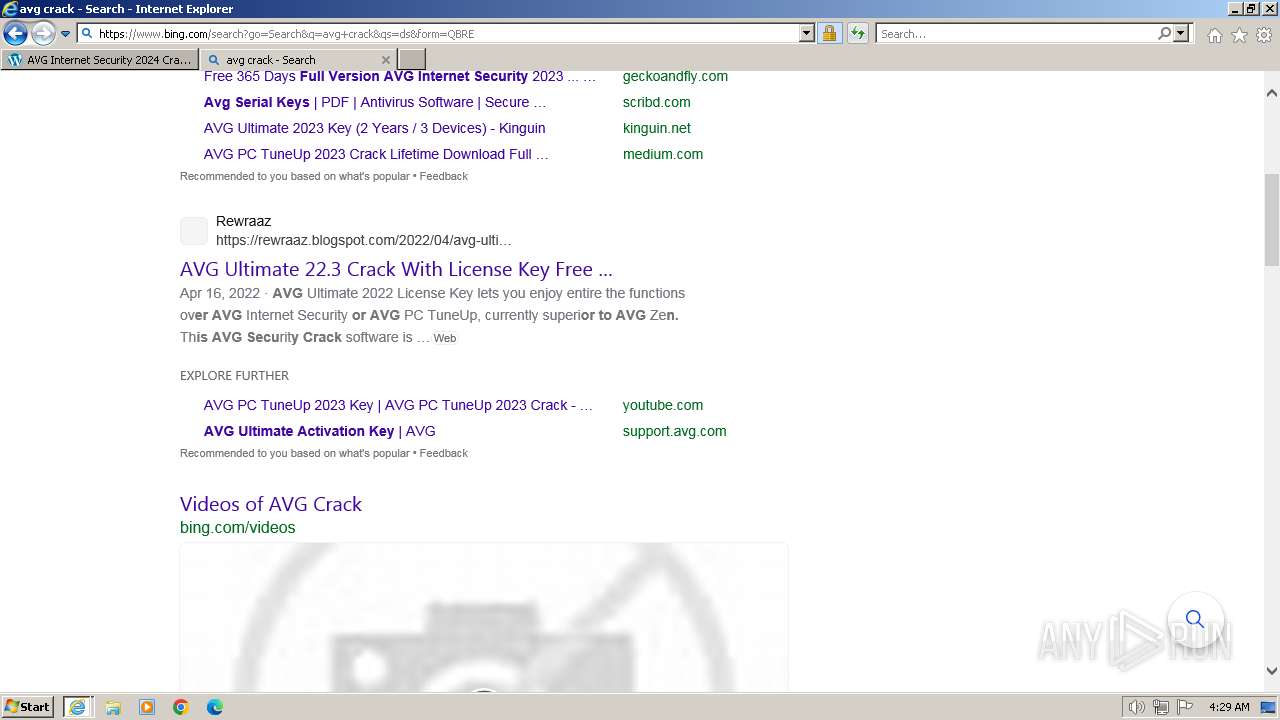
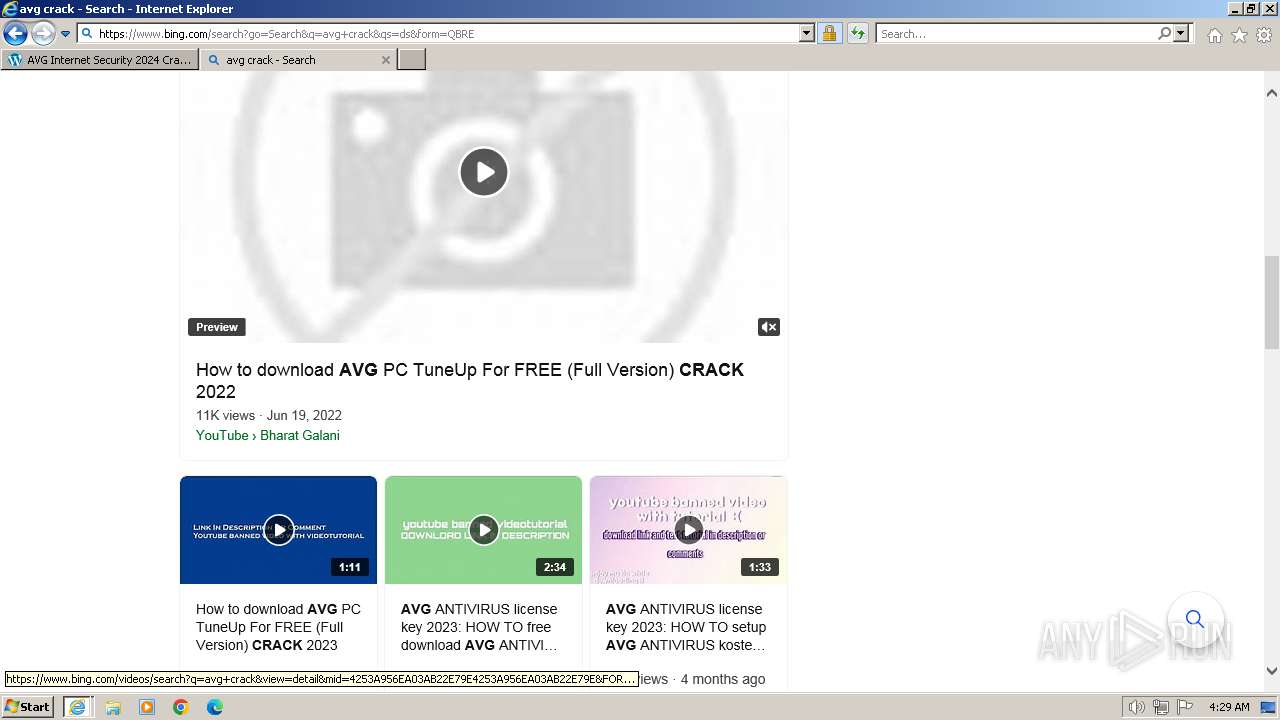
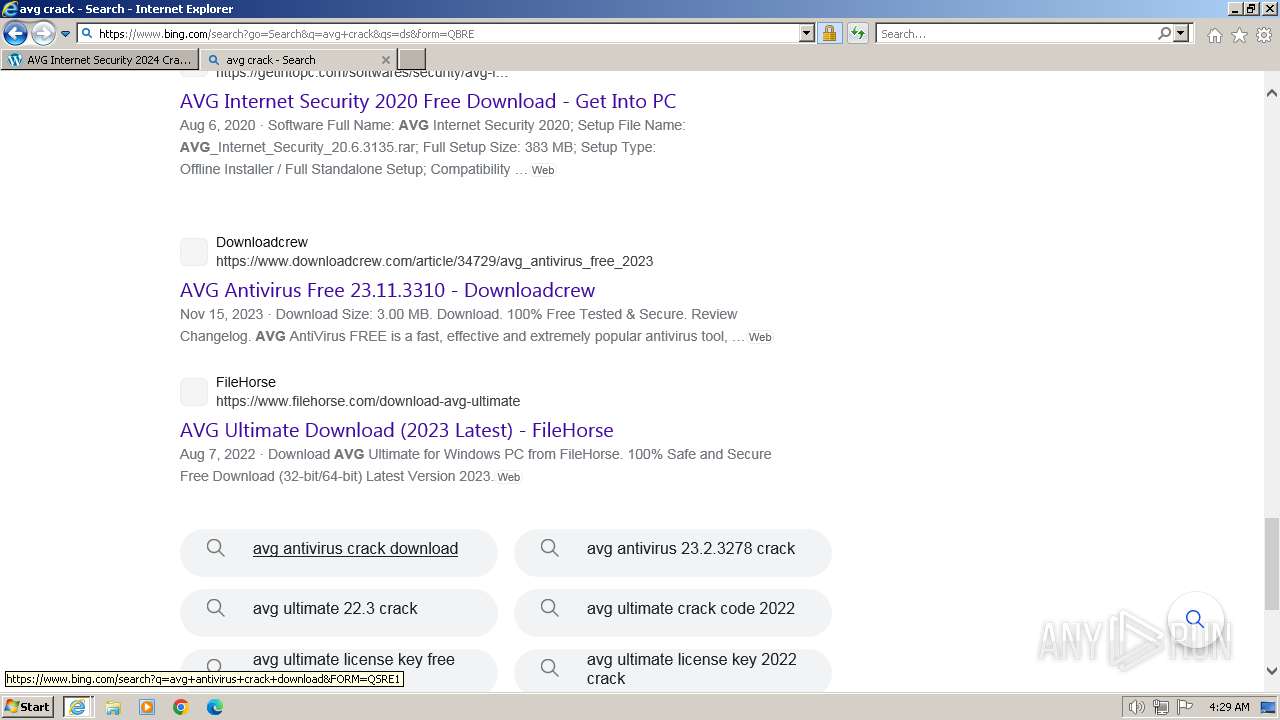
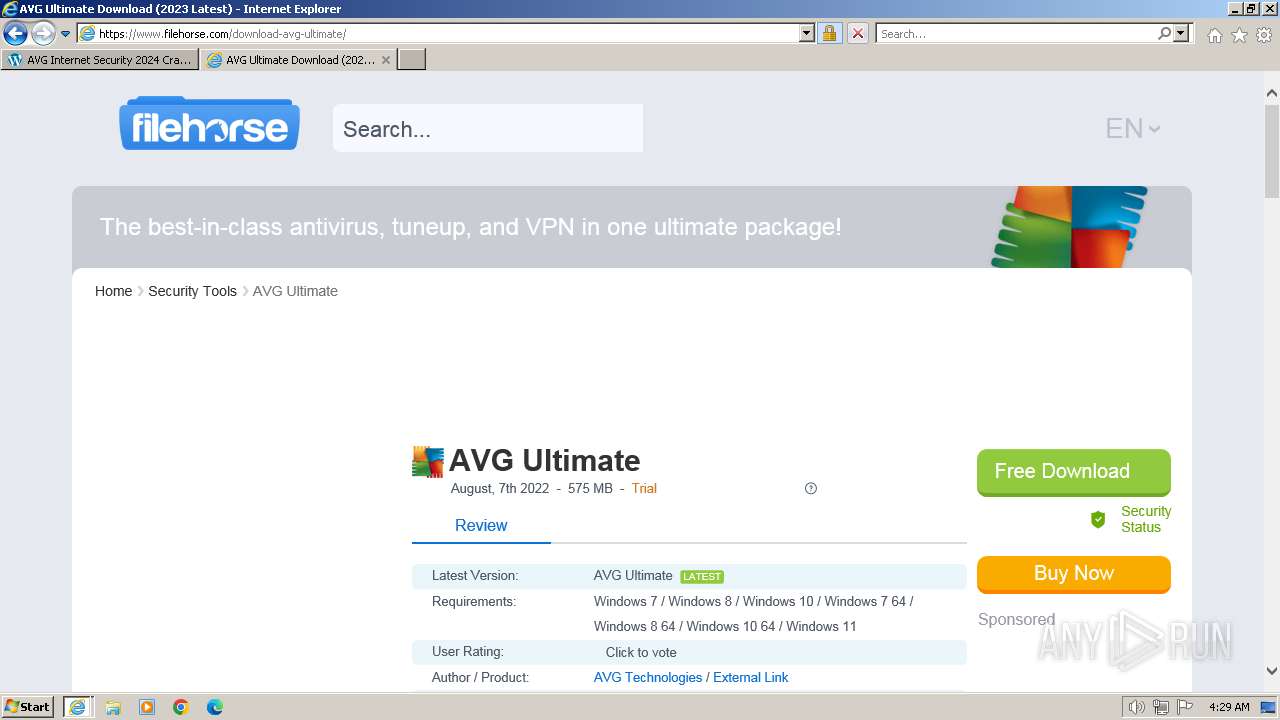
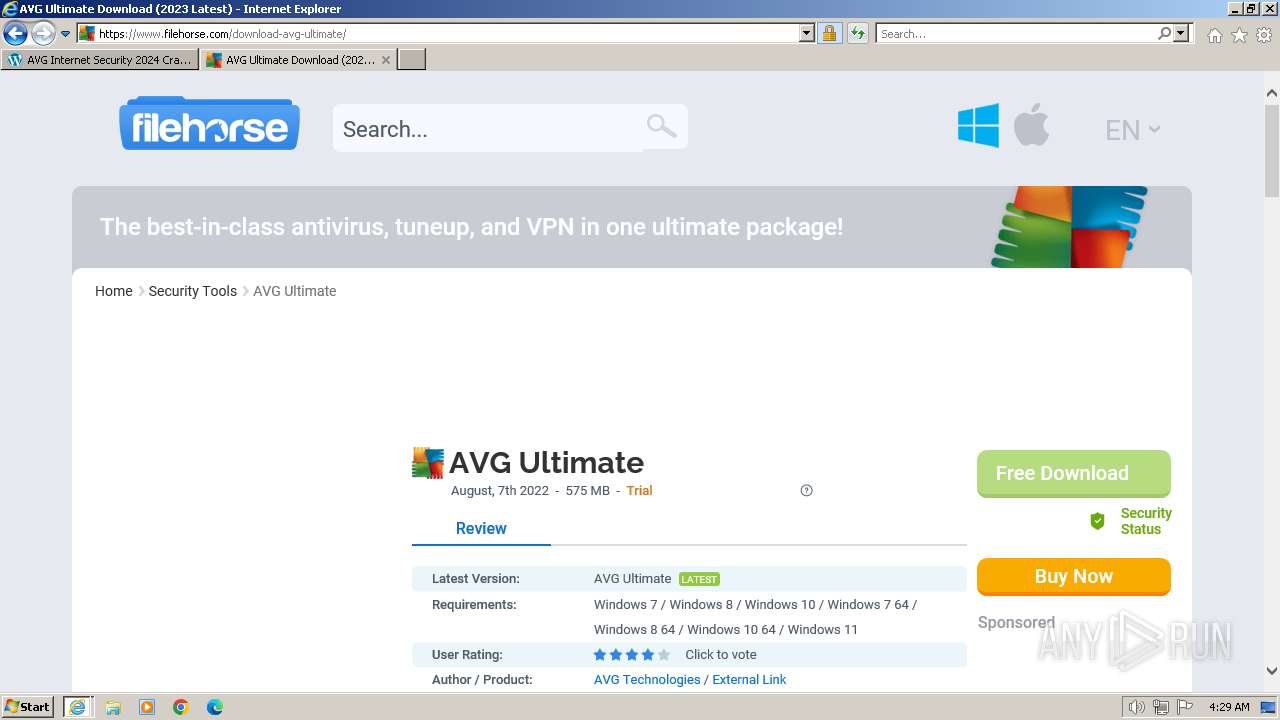
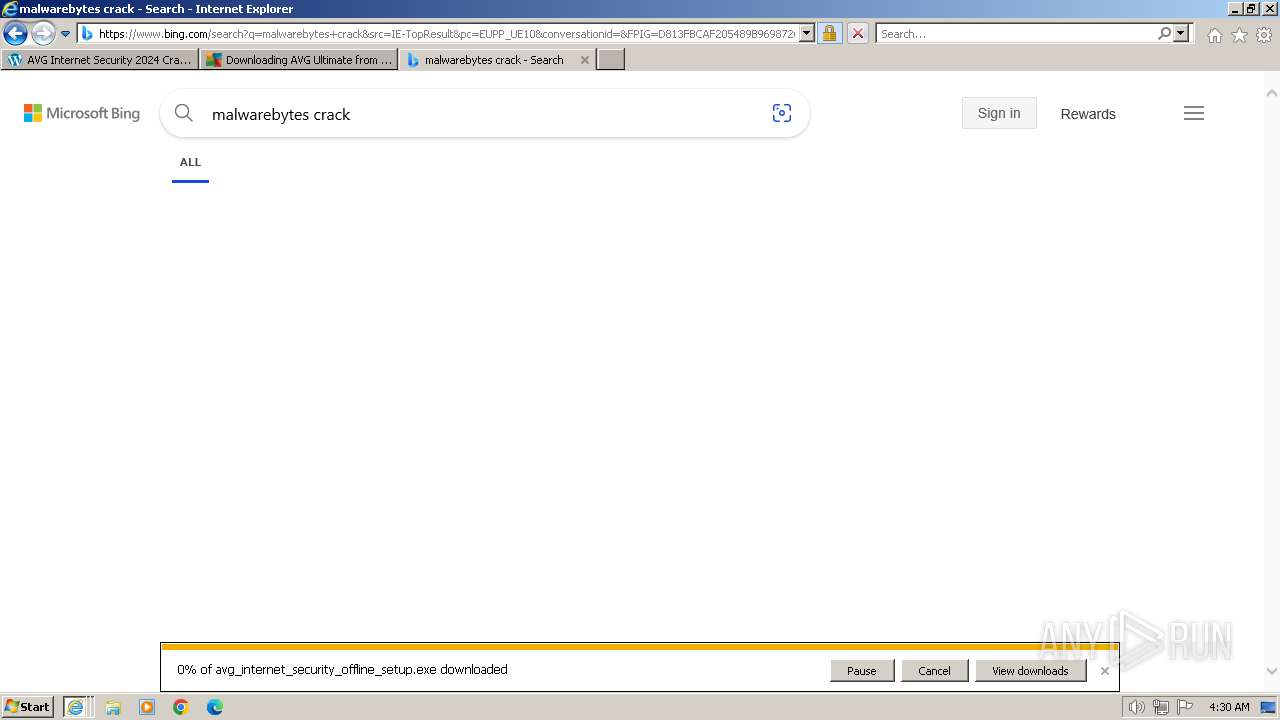
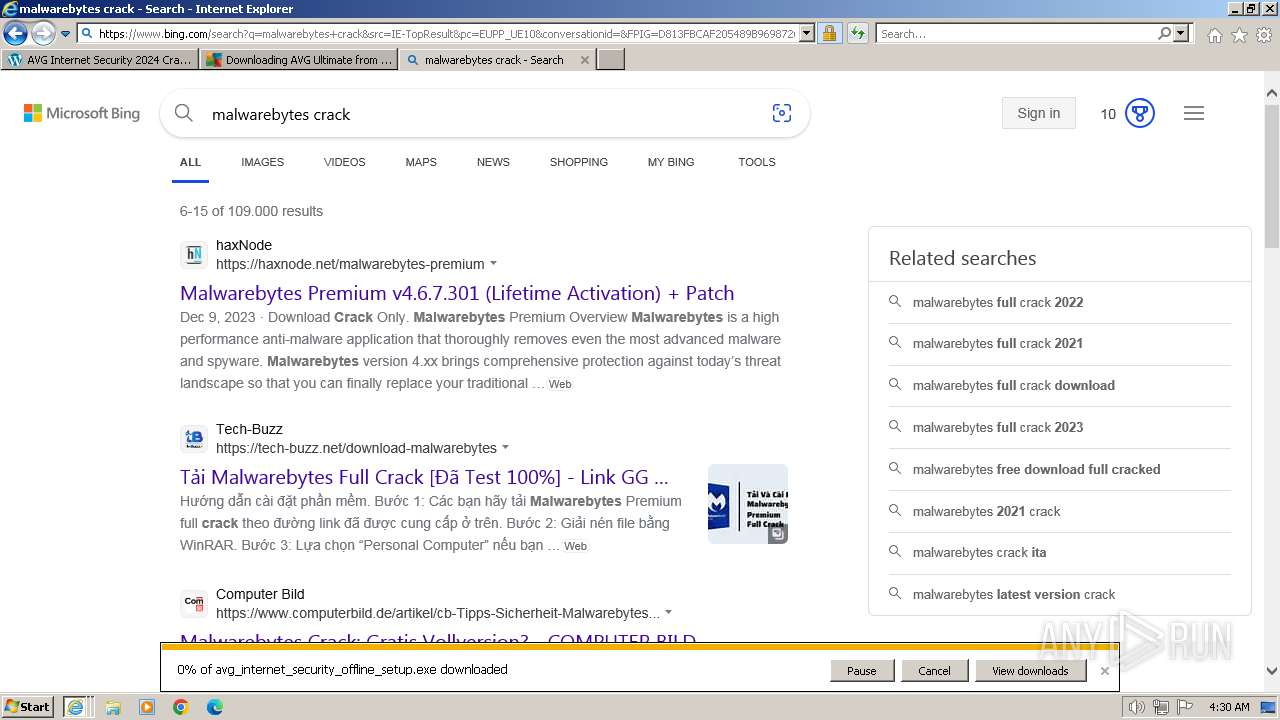
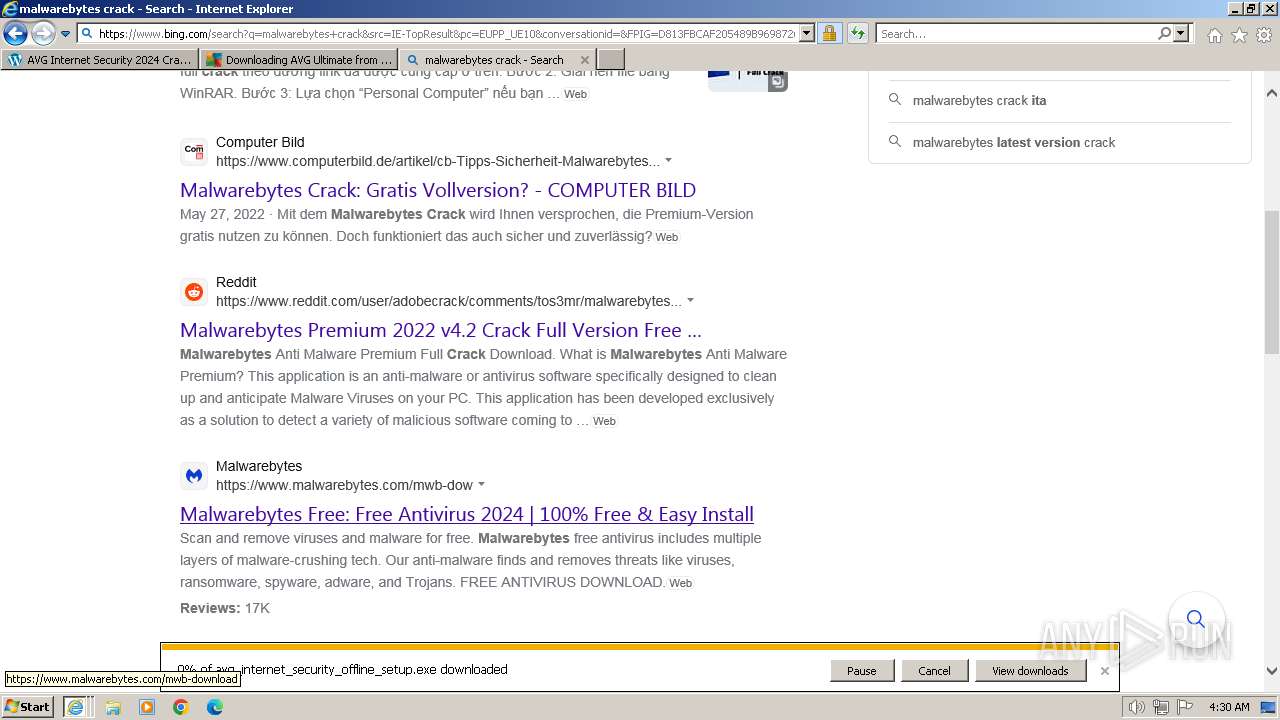
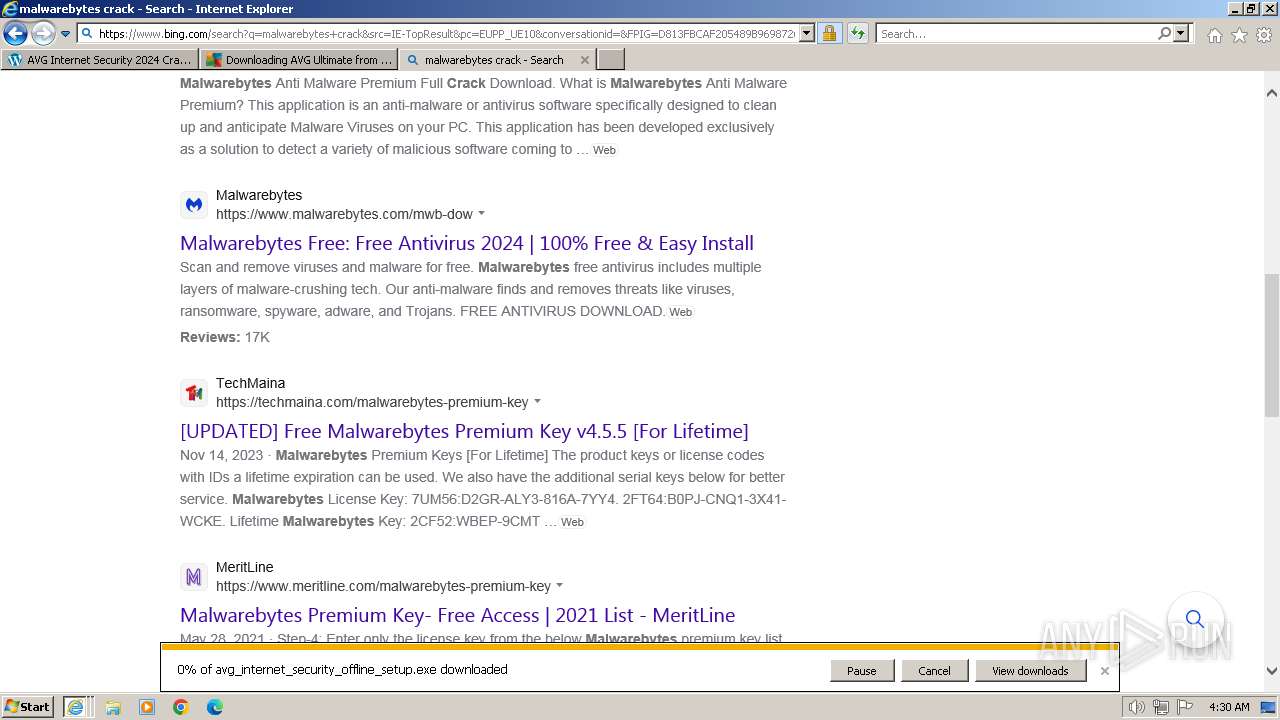
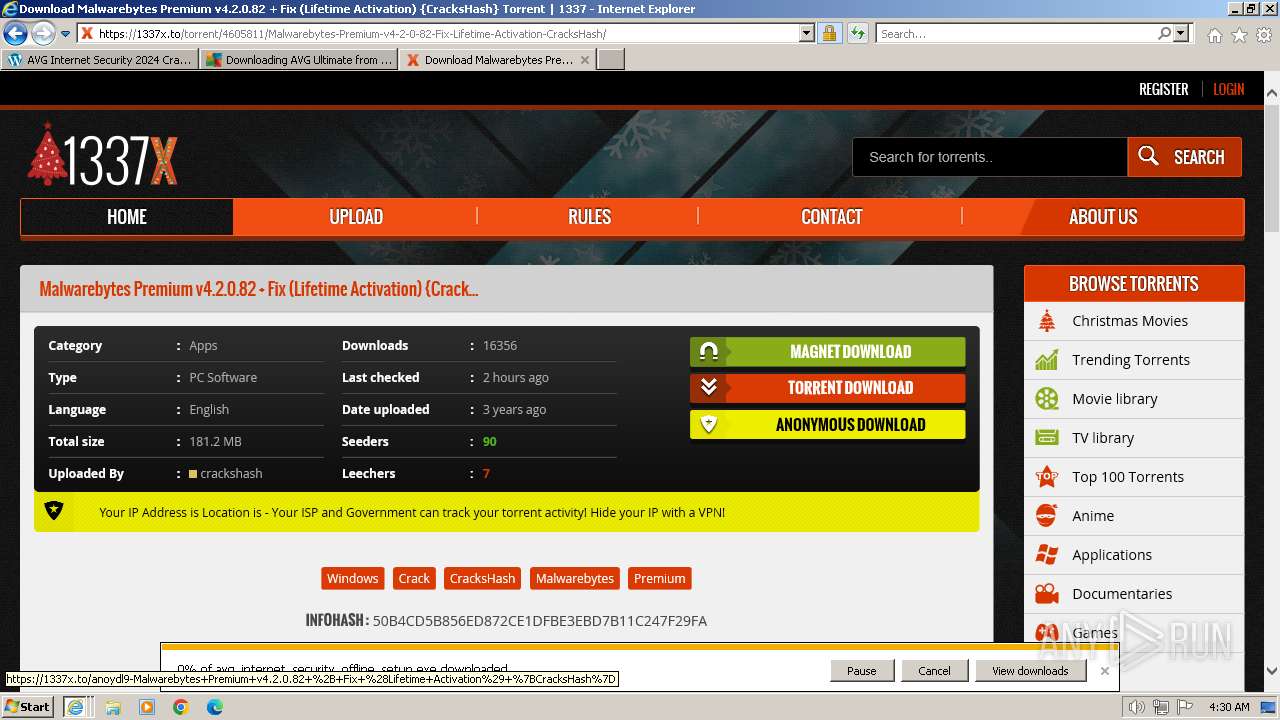
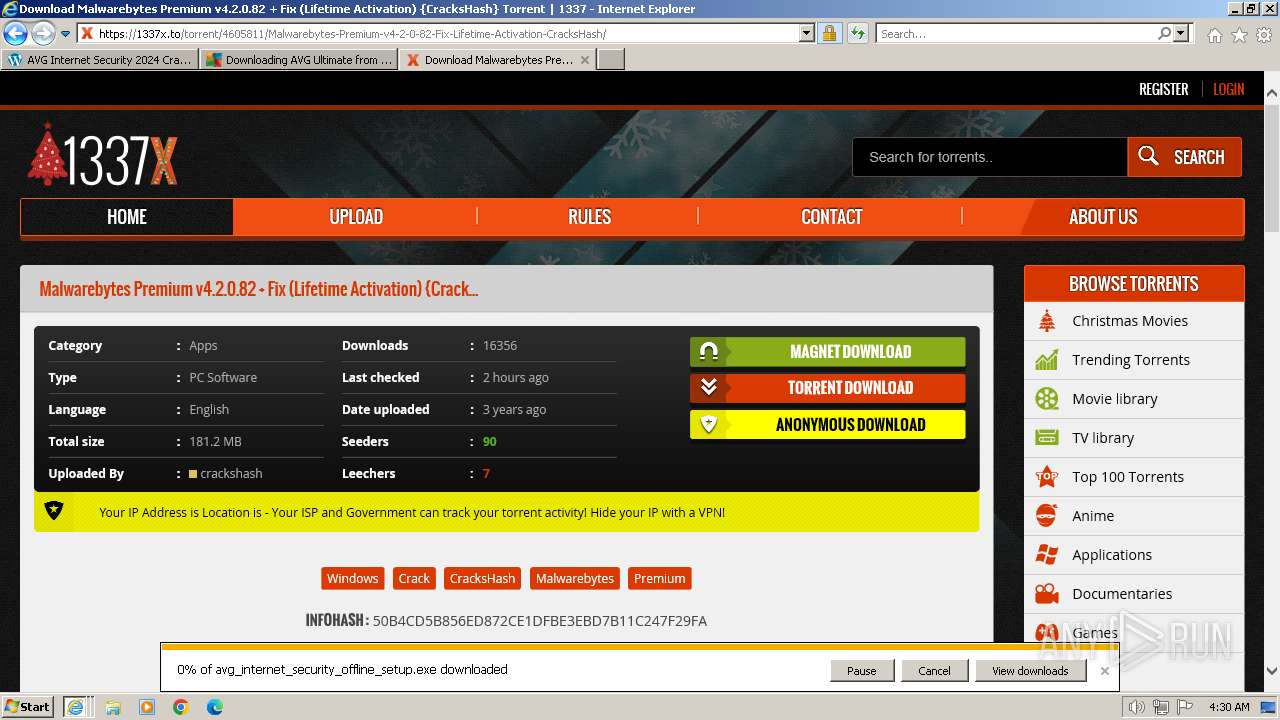
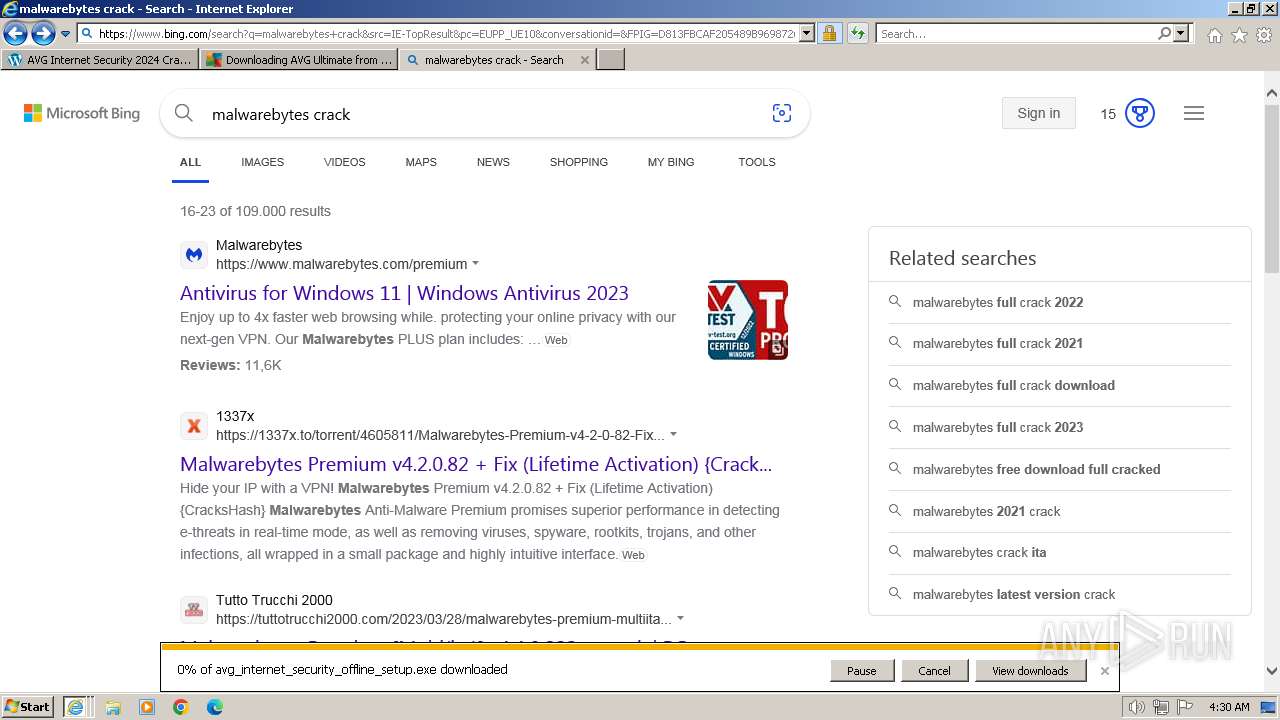
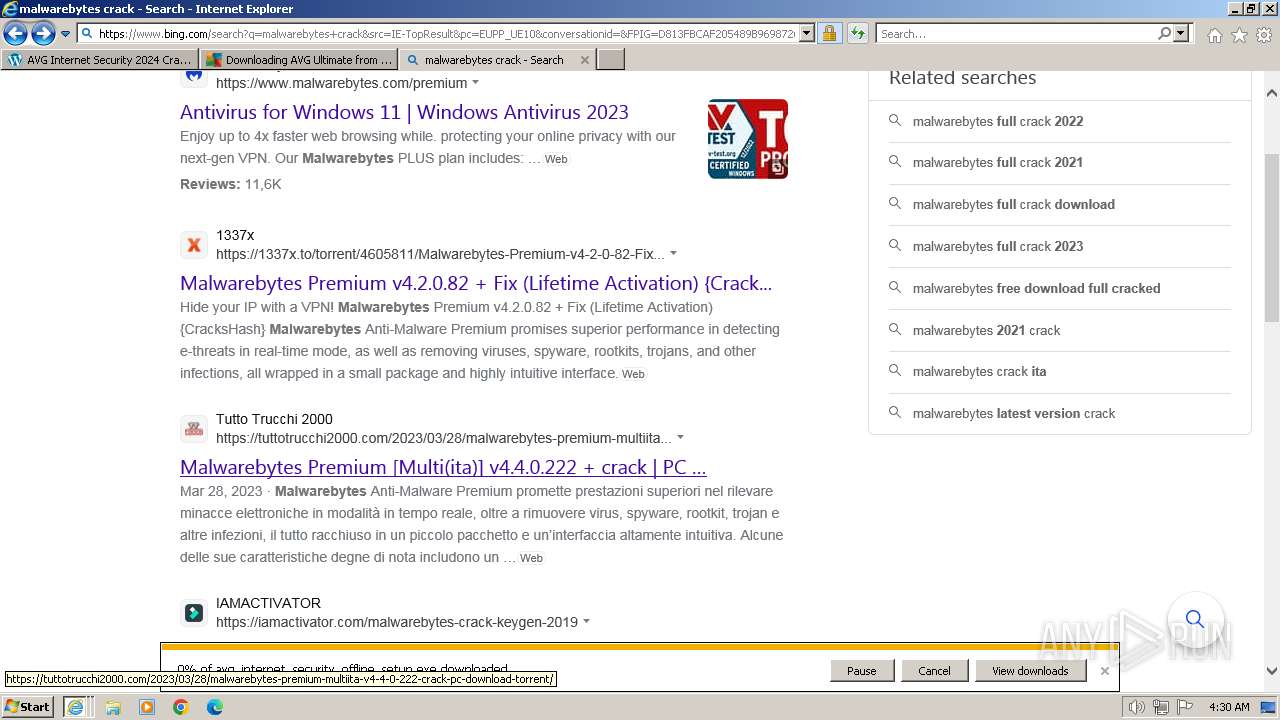
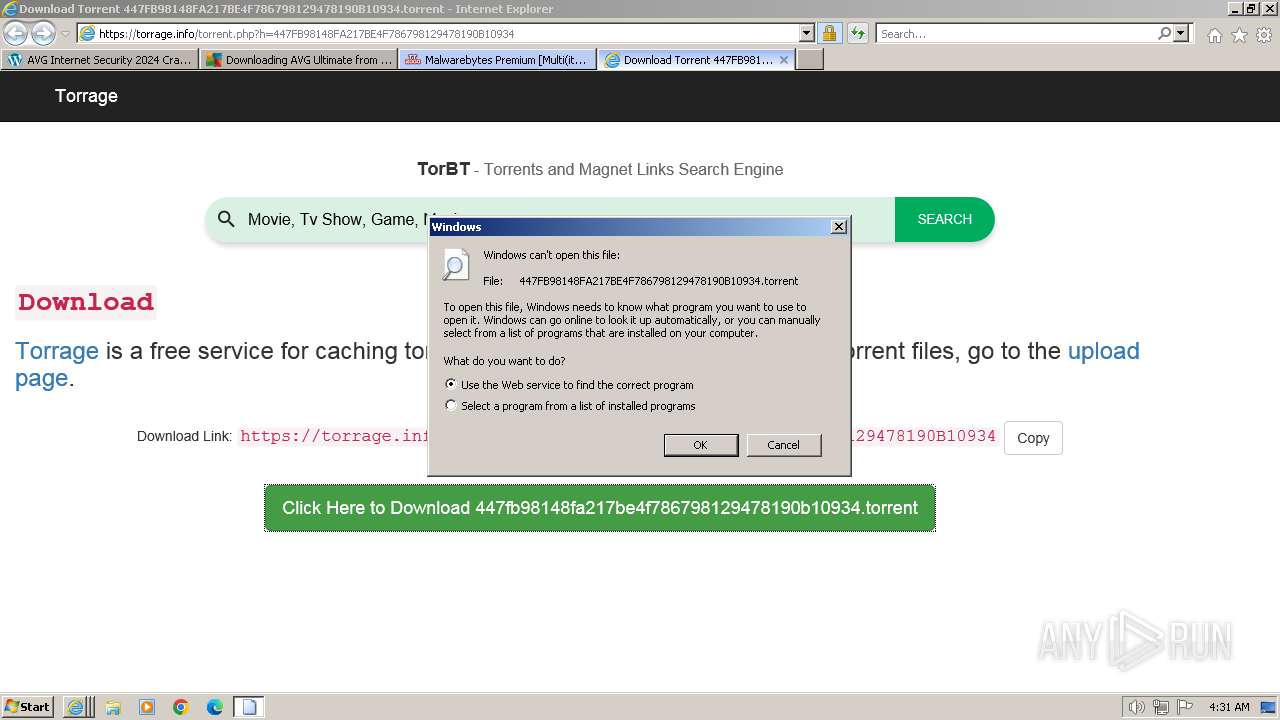
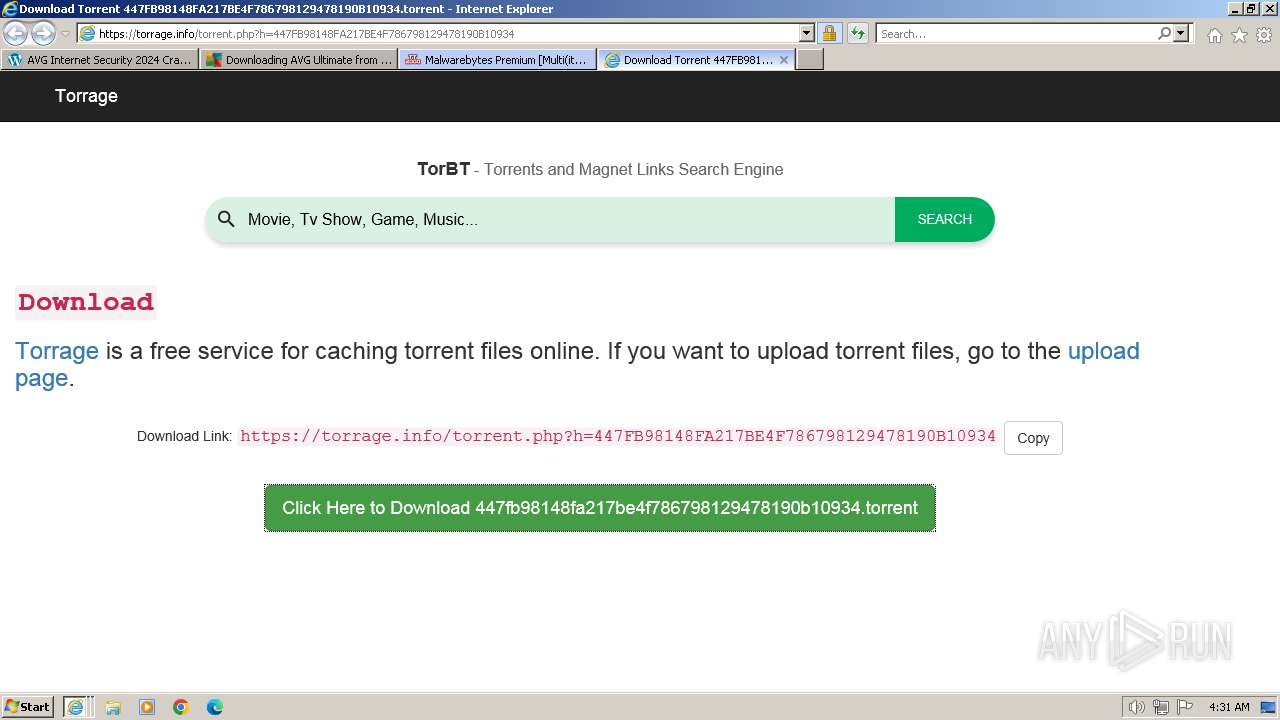
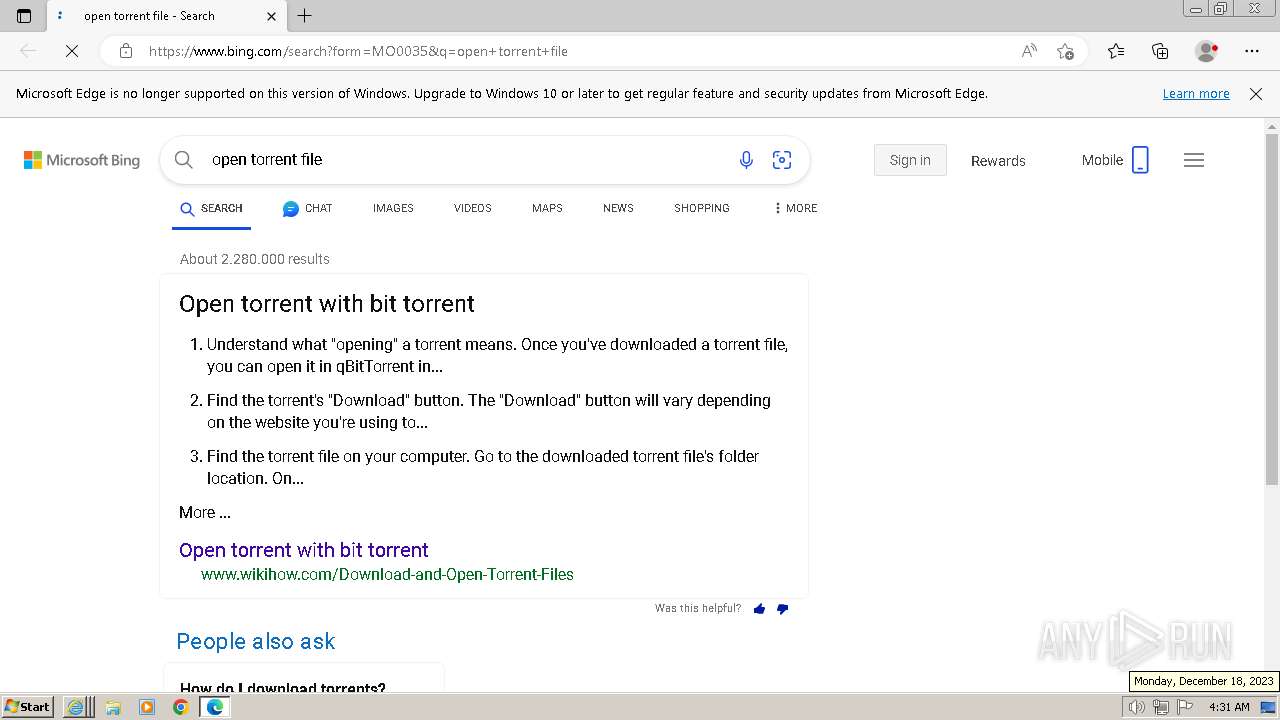
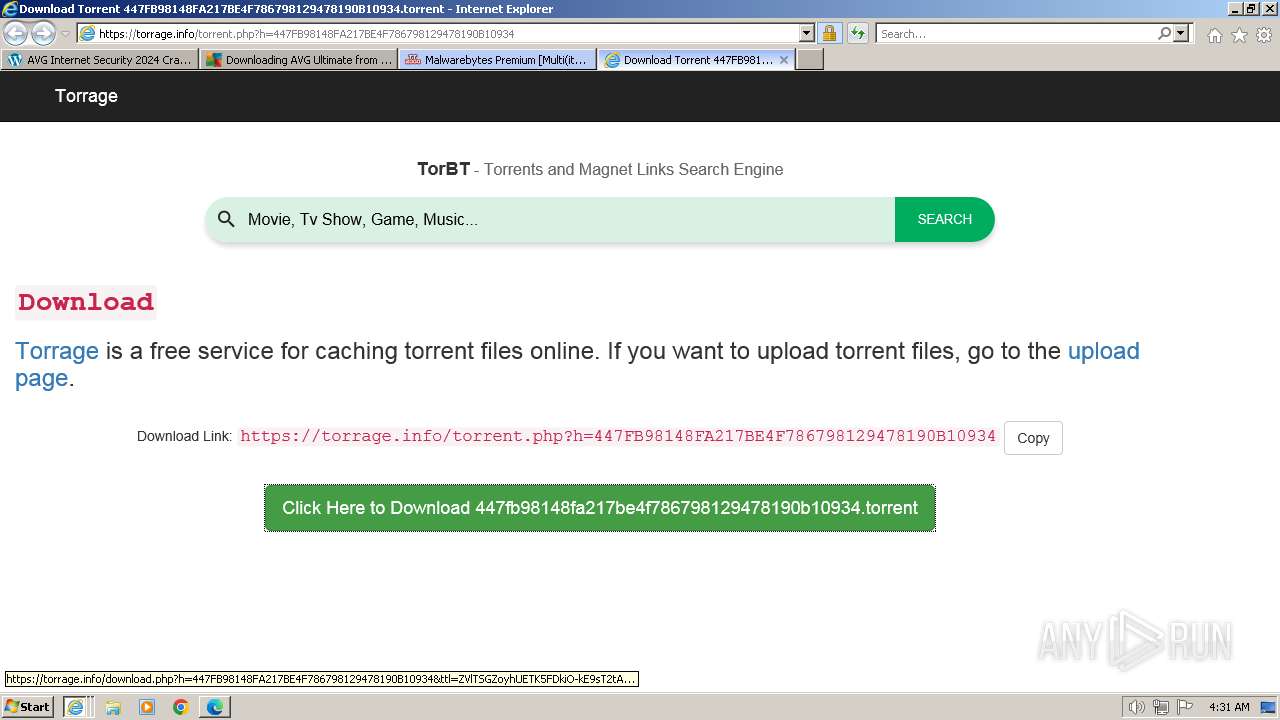
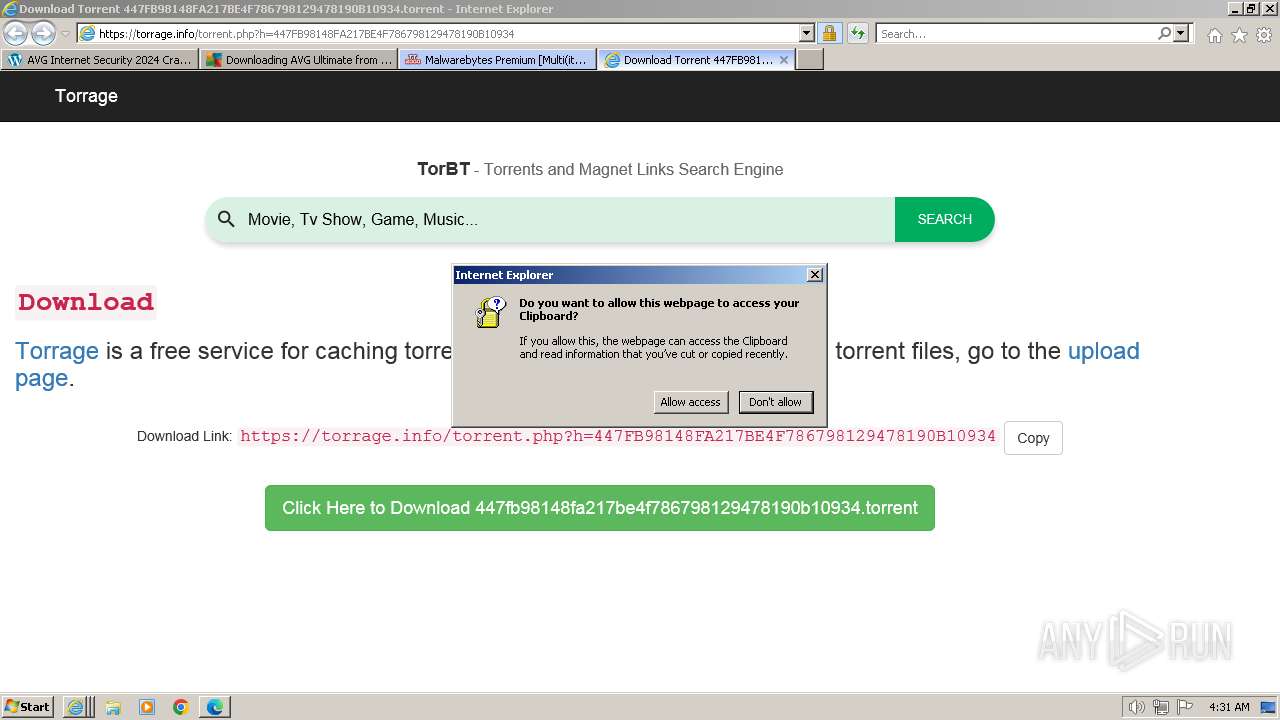
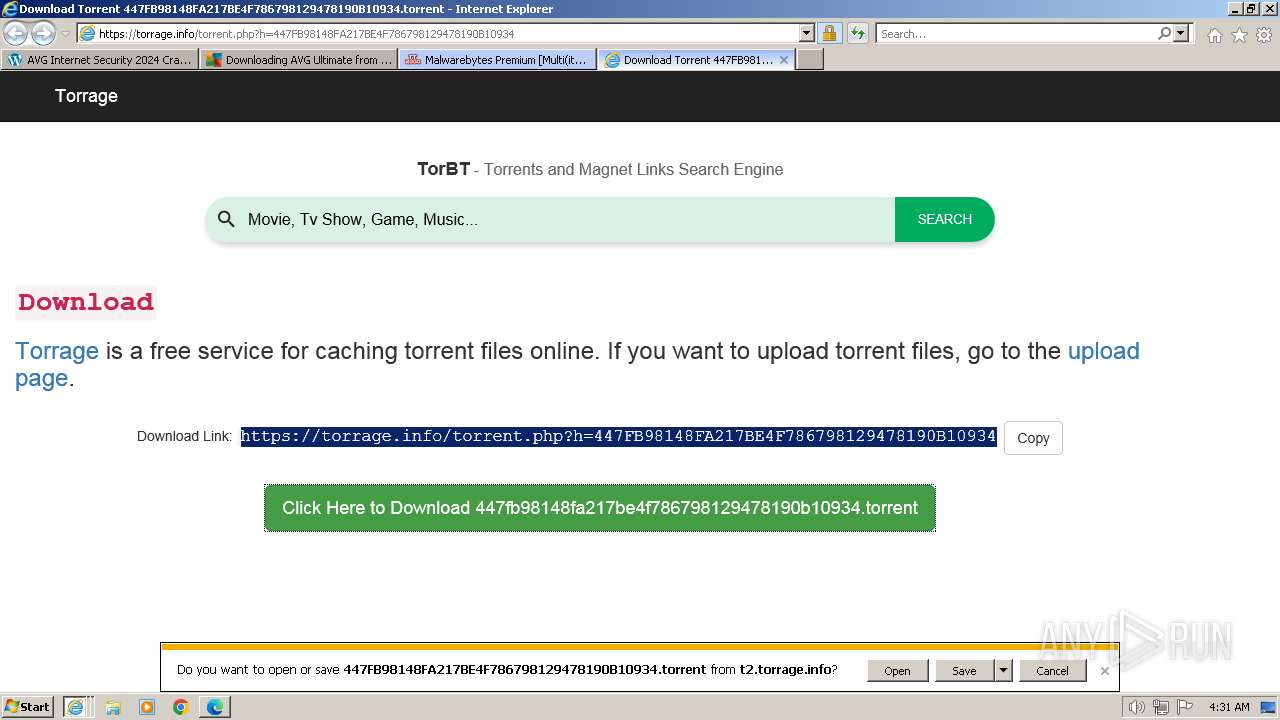
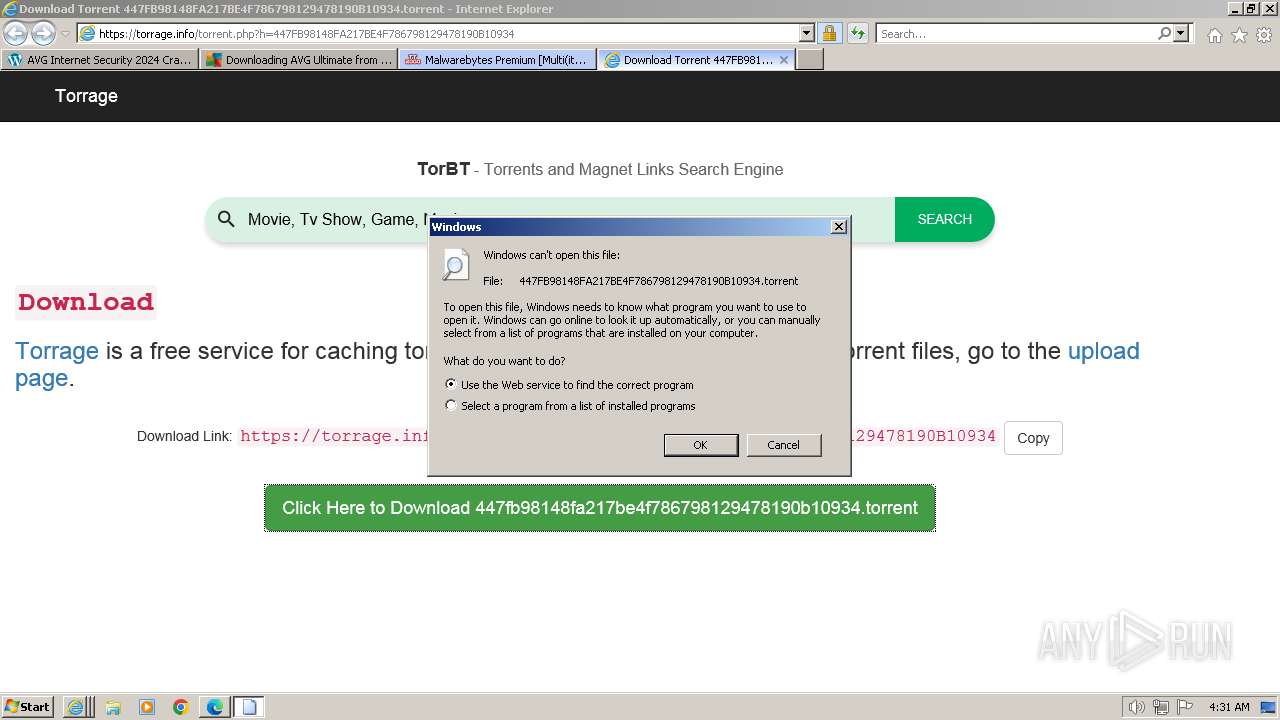
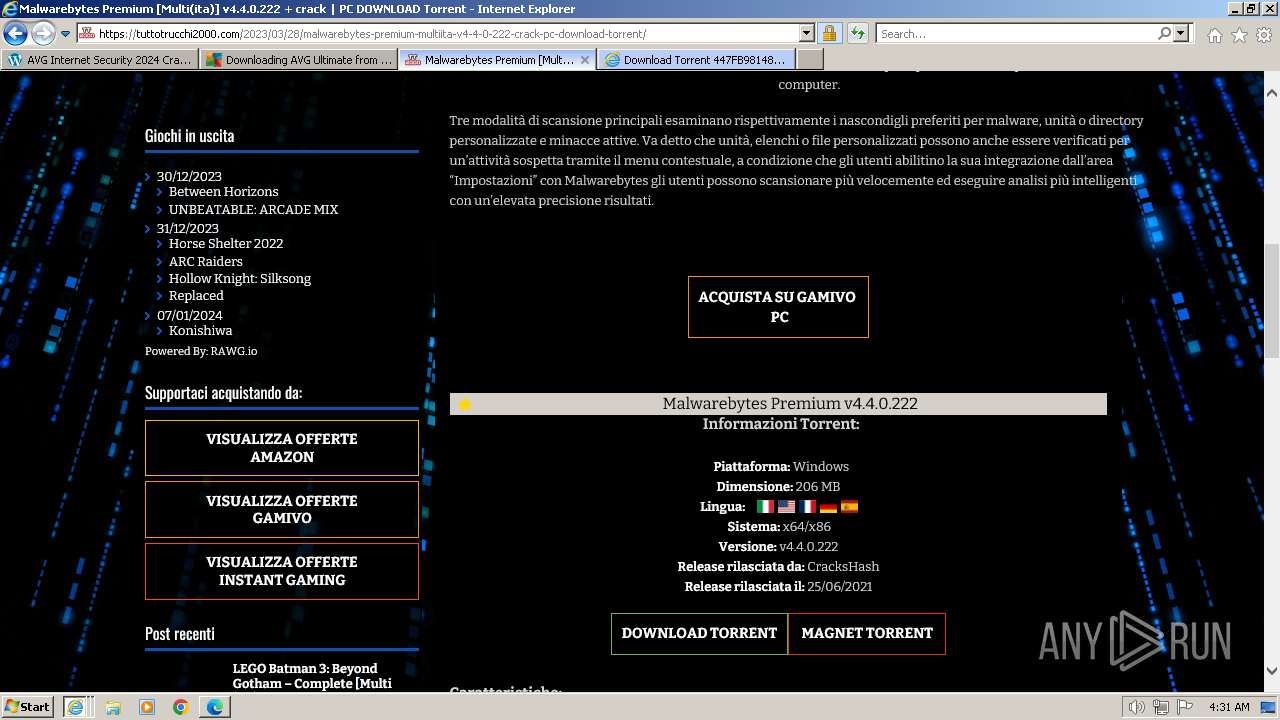
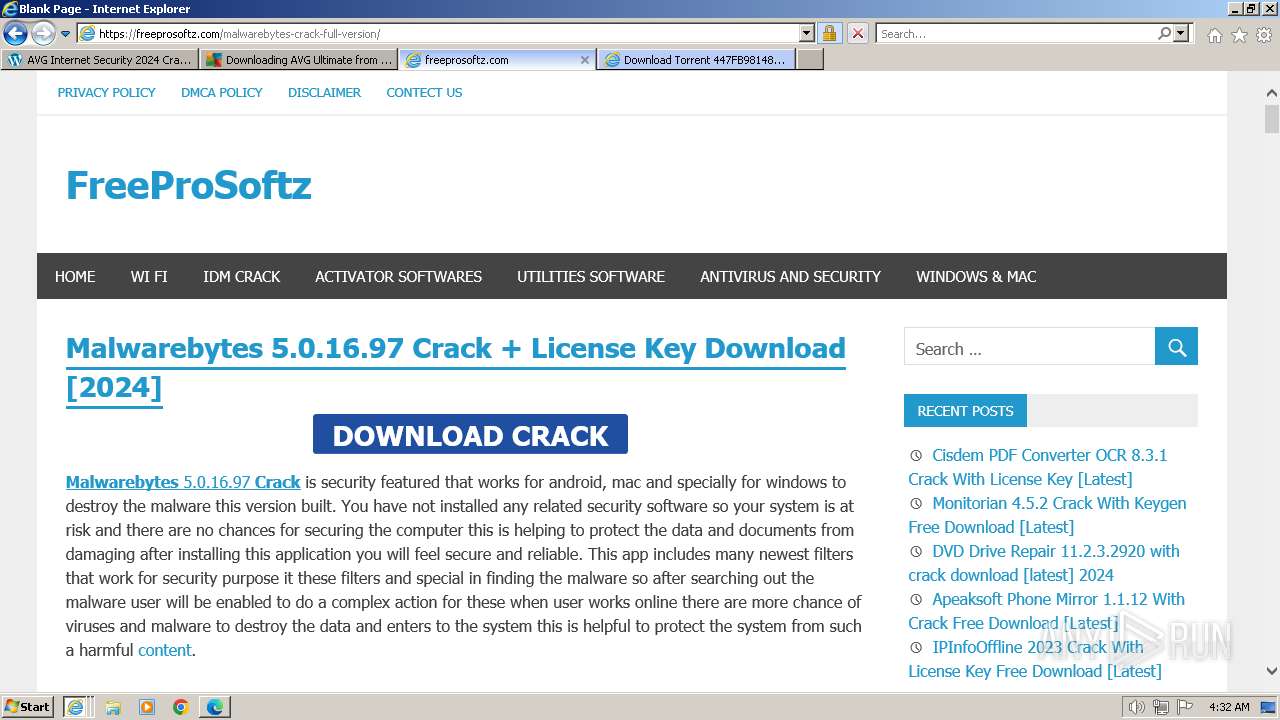
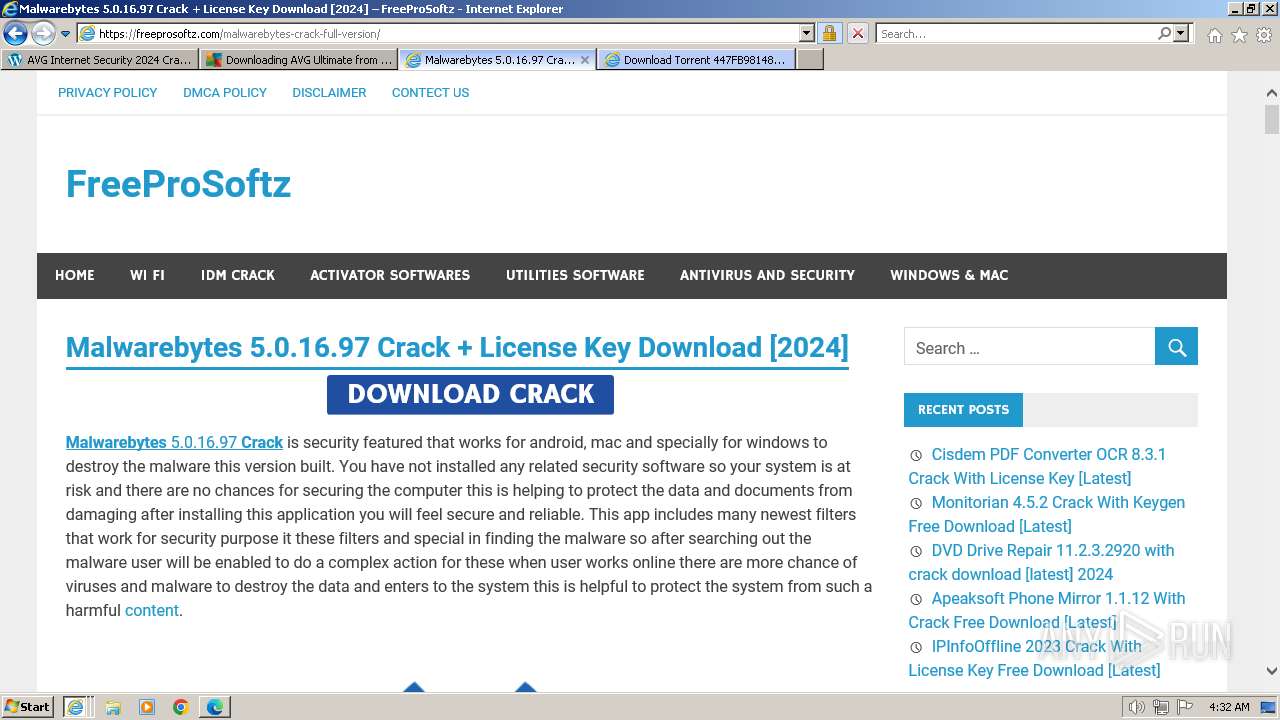
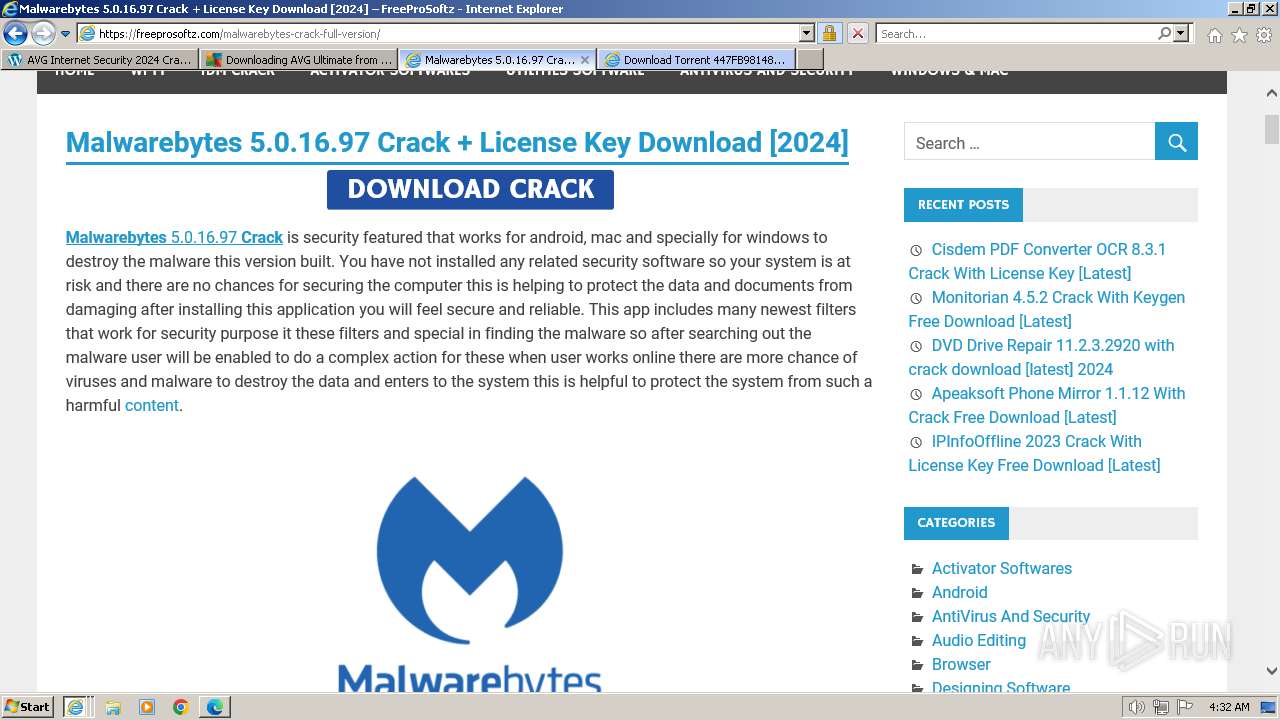
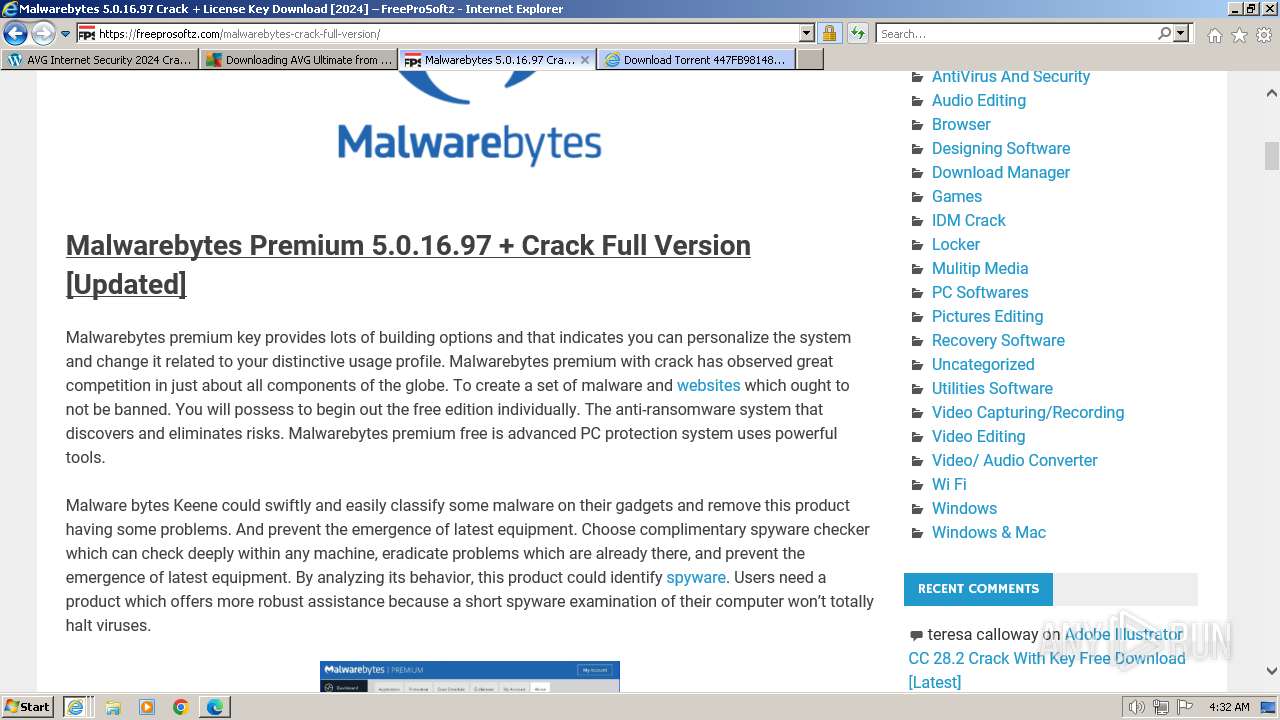
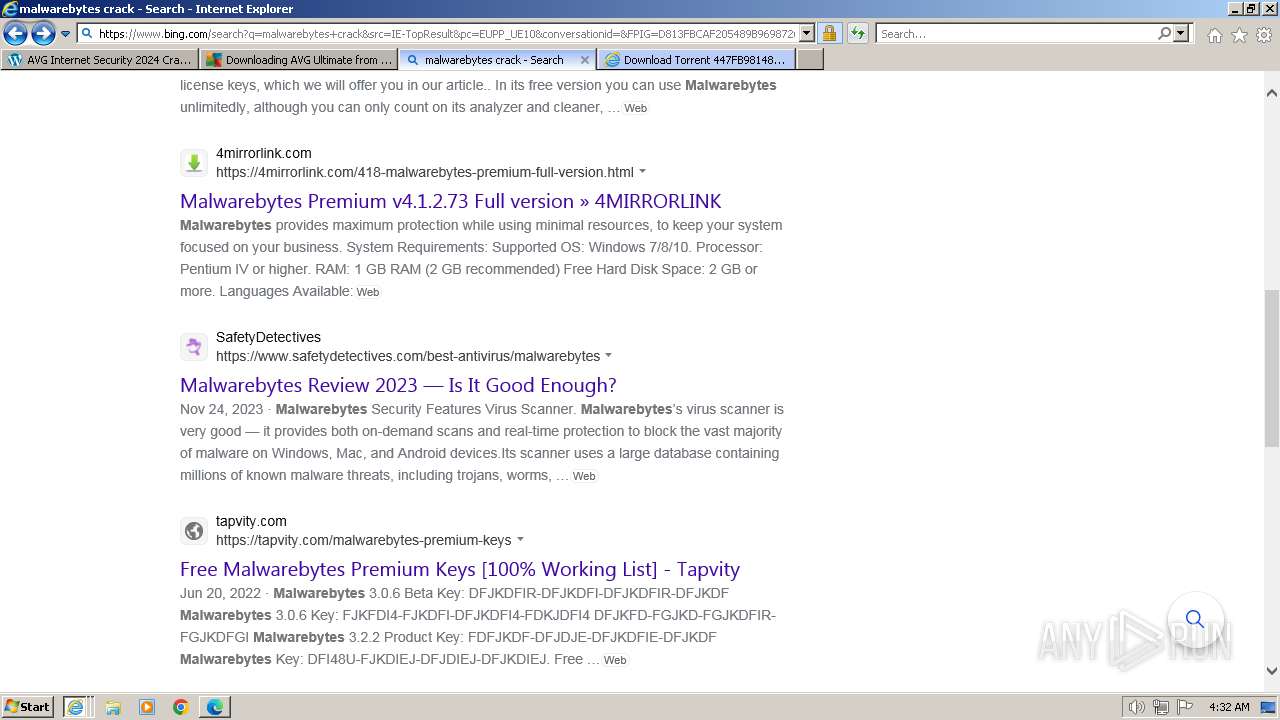
| URL: | https://www.bing.com/ck/a?!&&p=402b16d292ca6881JmltdHM9MTcwMjc3MTIwMCZpZ3VpZD0zMzAyYWMyNC0xMTFiLTZlNWYtMDVkMy1iZmMwMTAzMjZmNzgmaW5zaWQ9NTM2Mg&ptn=3&ver=2&hsh=3&fclid=3302ac24-111b-6e5f-05d3-bfc010326f78&psq=avg+crack+keygen&u=a1aHR0cHM6Ly9heWVzaGFwYy5jb20vYXZnLWludGVybmV0LXNlY3VyaXR5LWNyYWNrLWtleS1rZXlnZW4tZG93bmxvYWQv&ntb=1 |
| Full analysis: | https://app.any.run/tasks/87f81384-8ed4-4e51-99b2-3a79b3691a5a |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2023, 04:28:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 14AD4B7E221DA16D8A1A67B0EEED4519 |
| SHA1: | F62B5C622634587468C63D056C3081223BFF9605 |
| SHA256: | 2F2EDDFC2005BBE2A0F84BA3543C36FBCD2D8619ECF969684A9DAD6D9B029014 |
| SSDEEP: | 6:2OLsRz8cW0Pex4QUOfOiM/DAroDfEv7ztWDU6isykpQm70gD+Xo//cvUX:2r9di0AroDg7ztWIC570Jecvm |
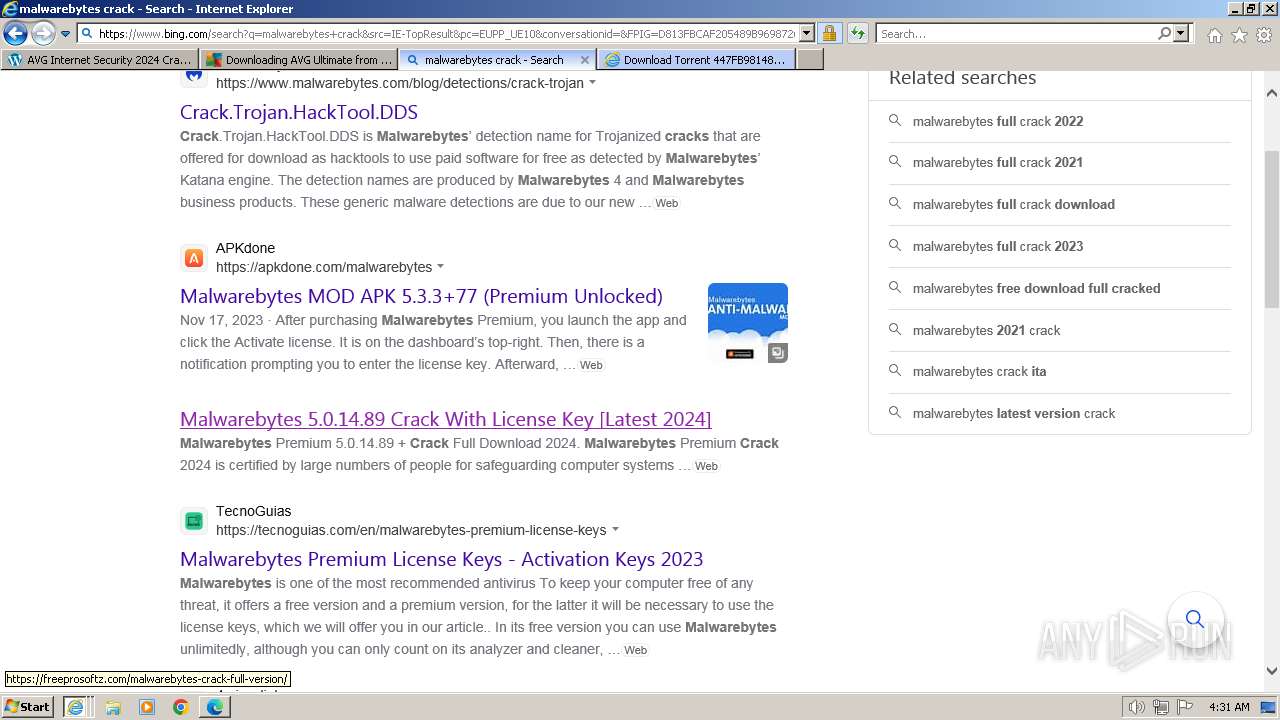
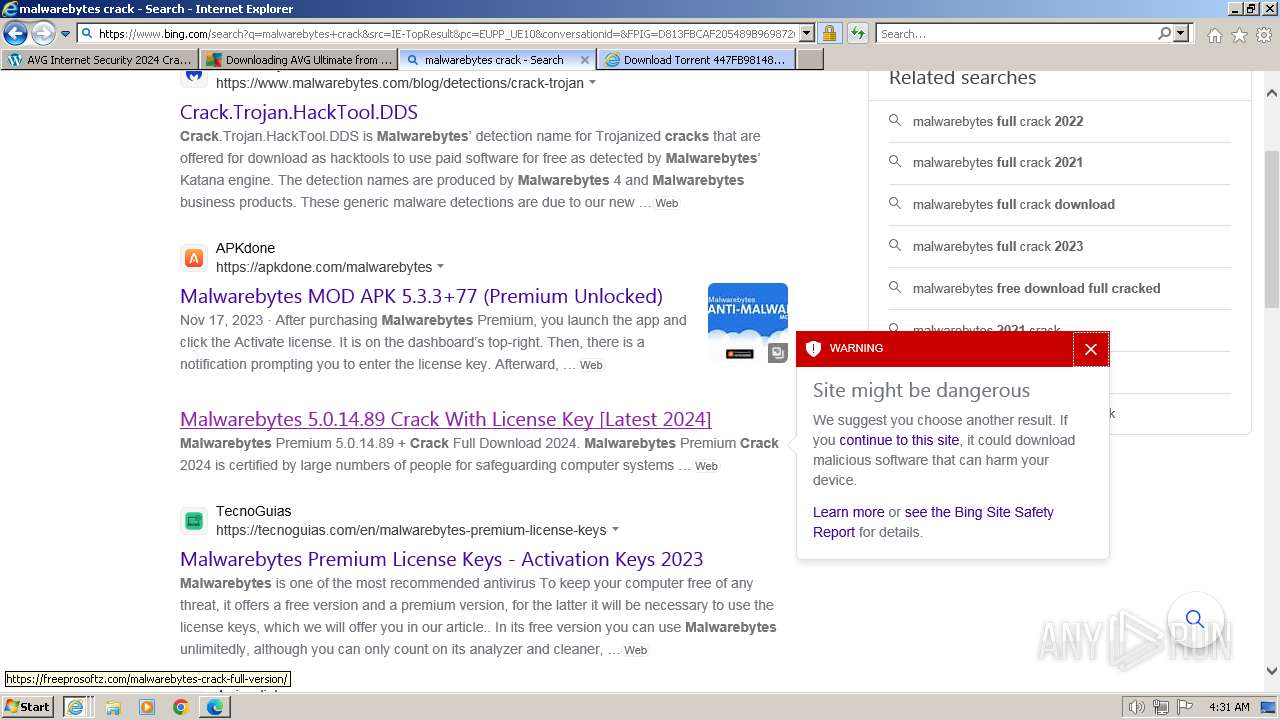
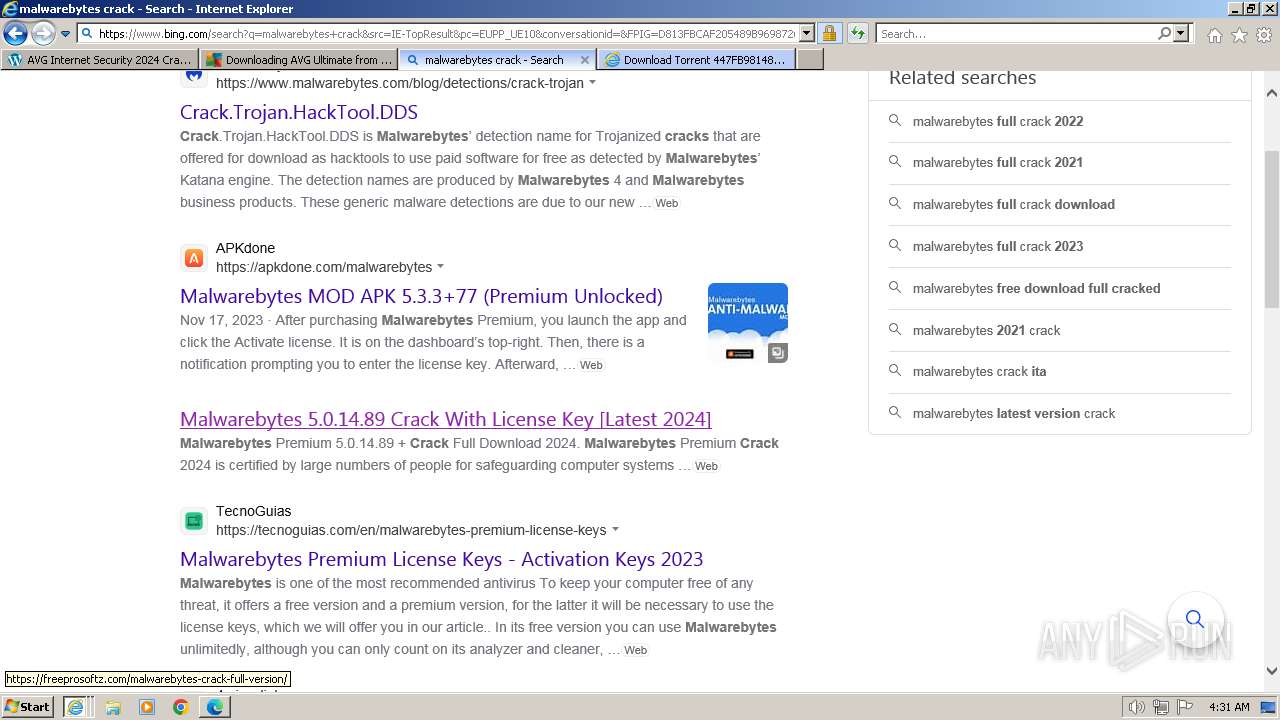
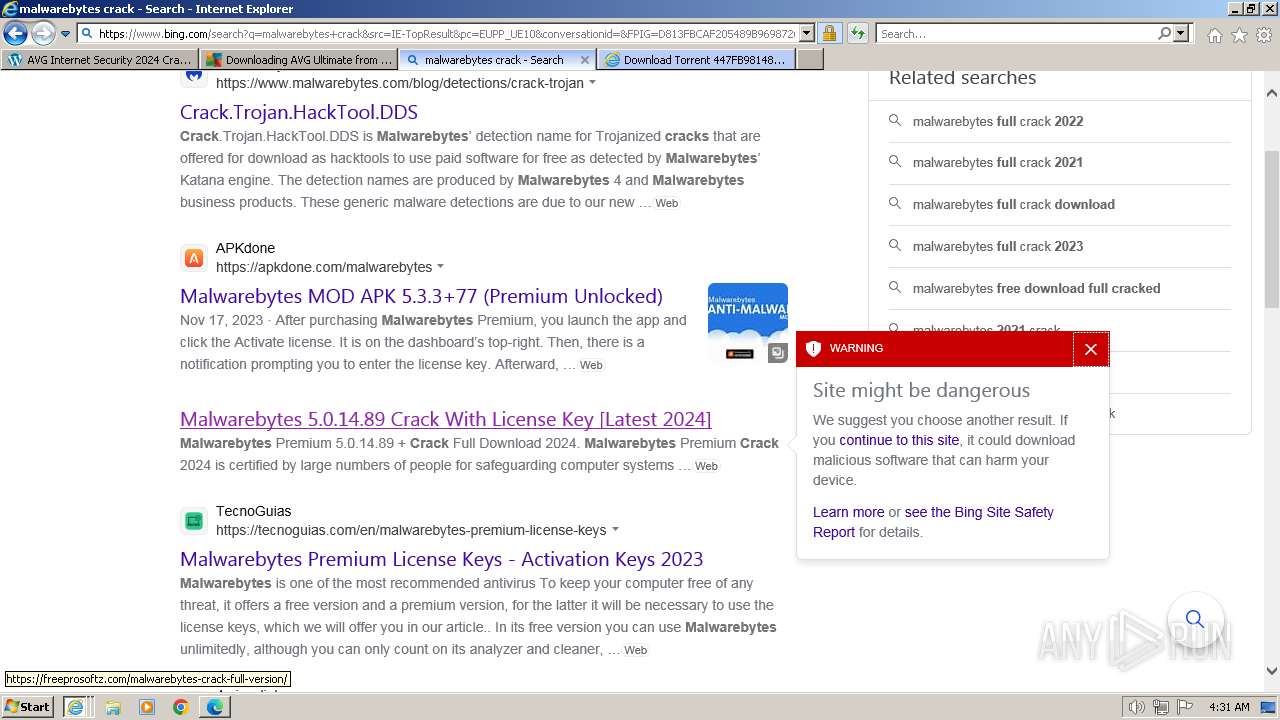
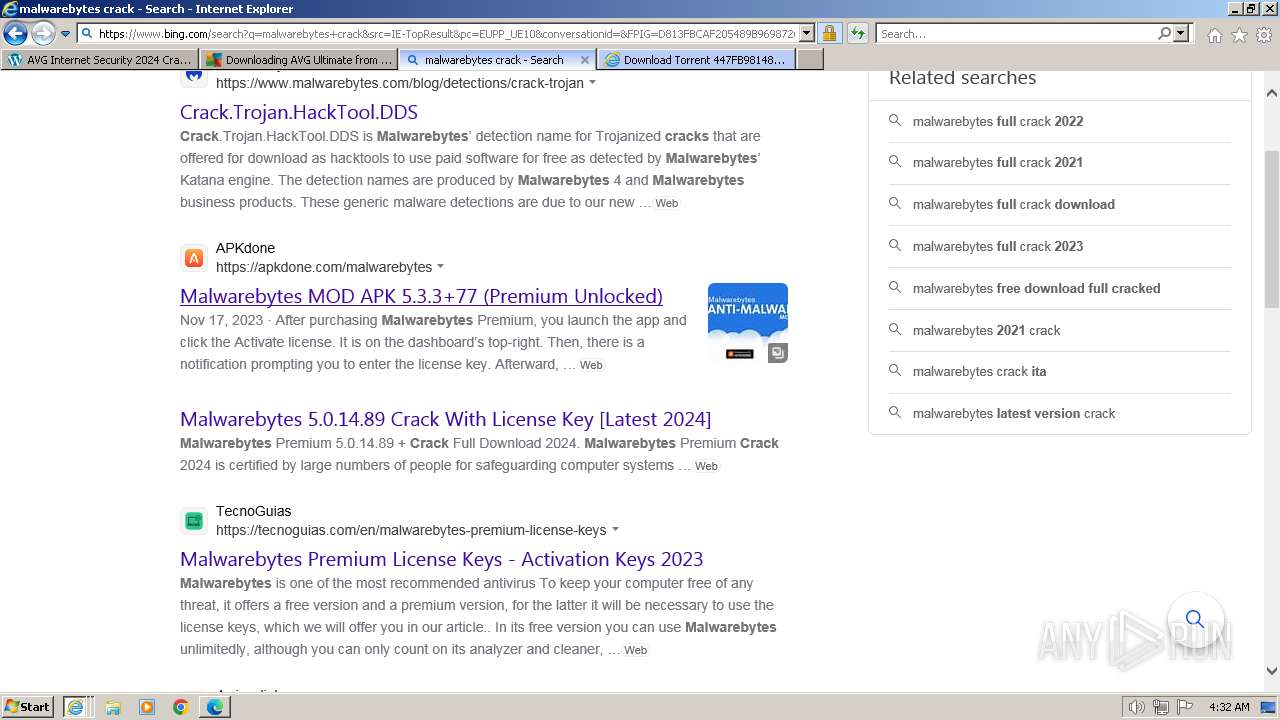
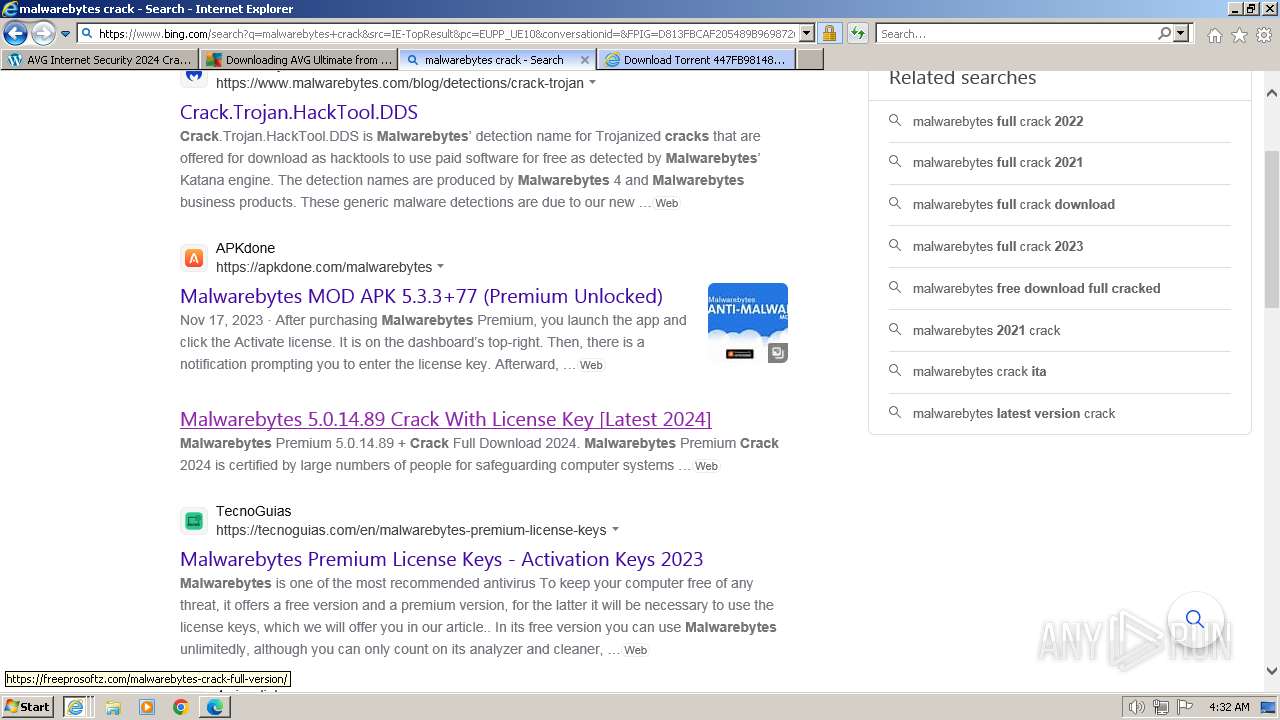
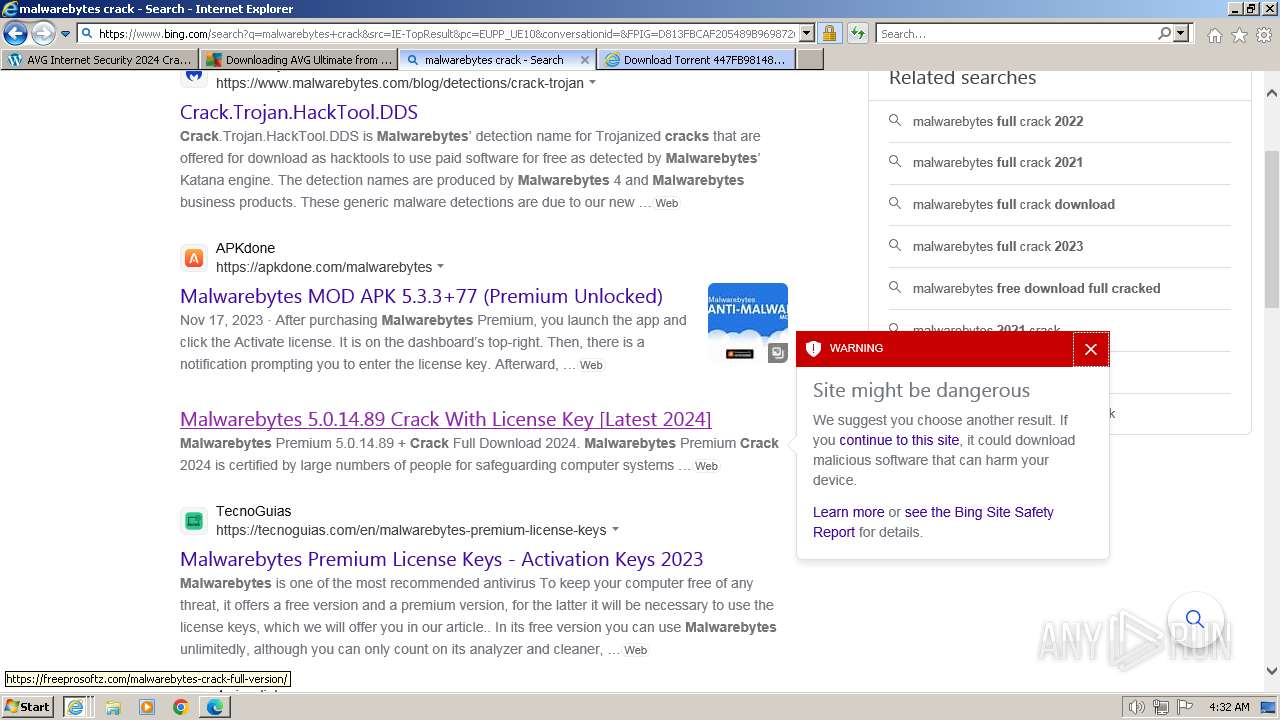
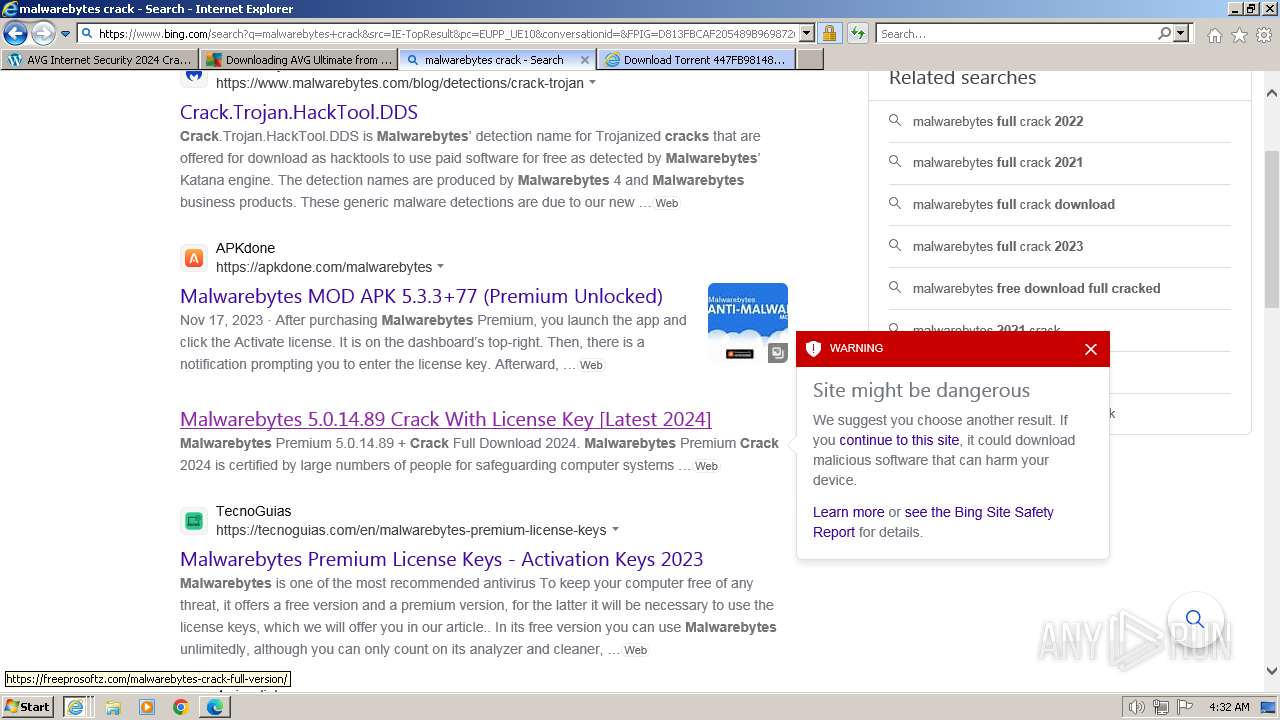
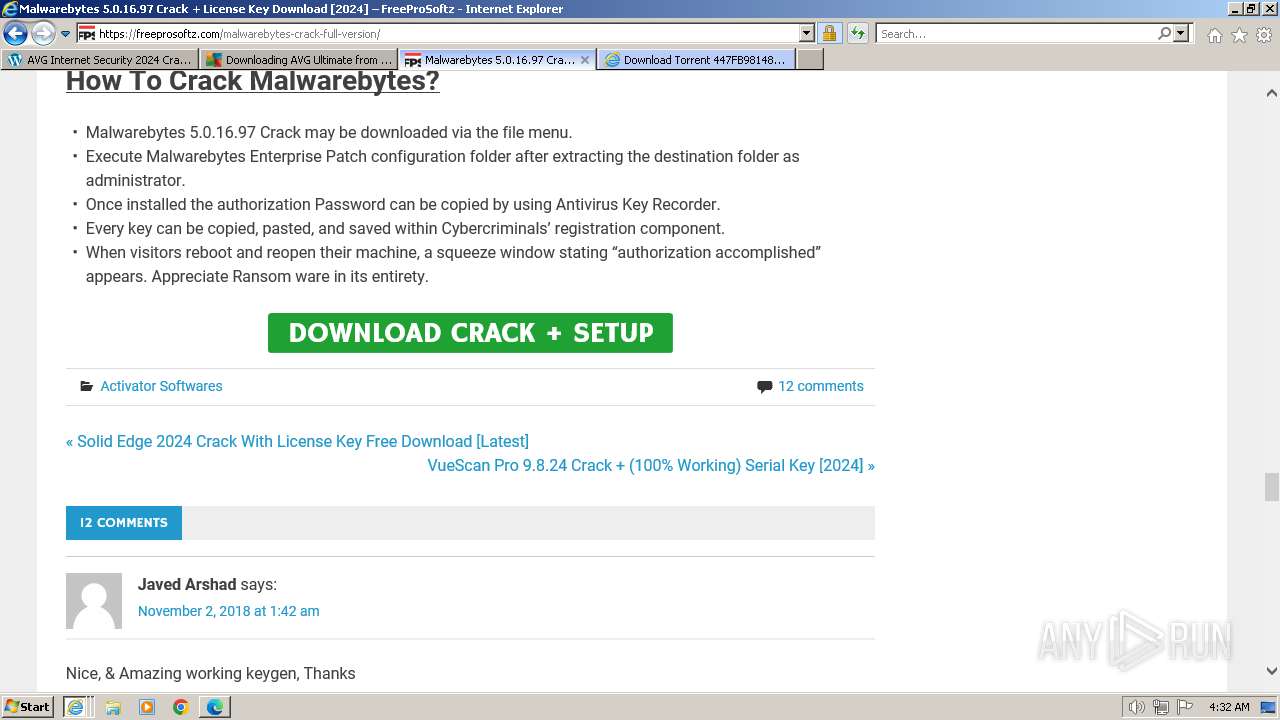
MALICIOUS
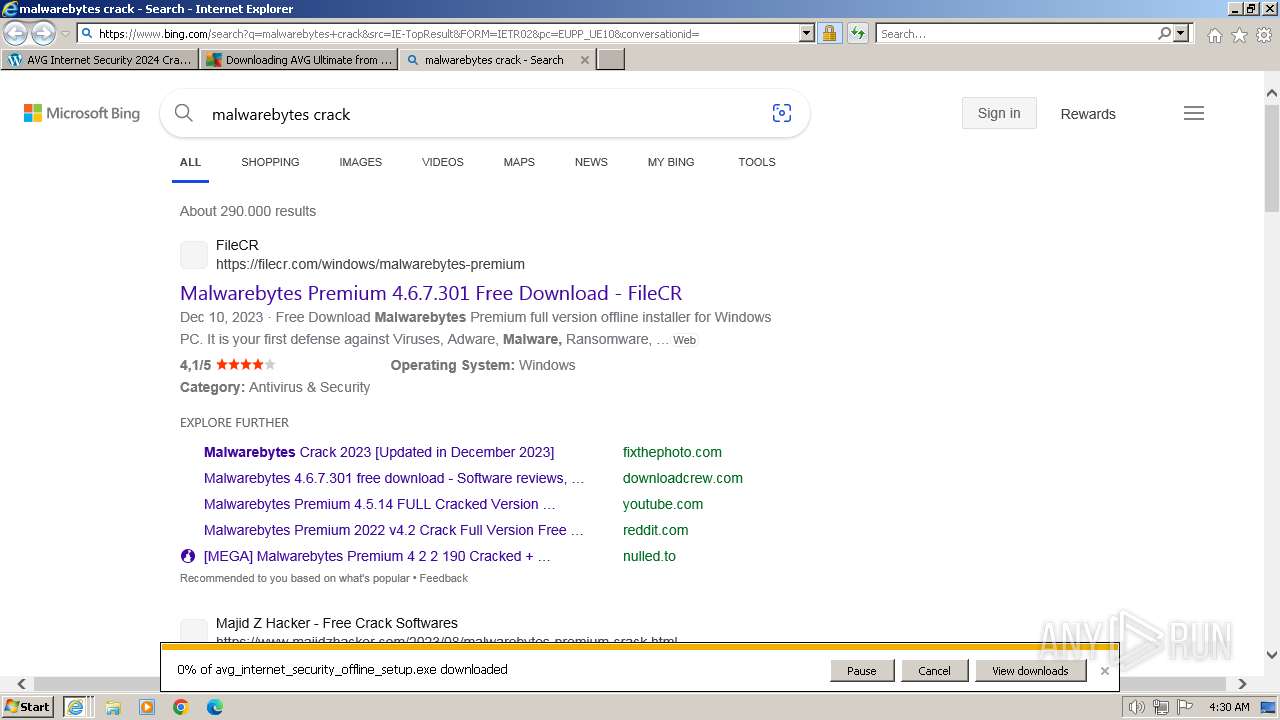
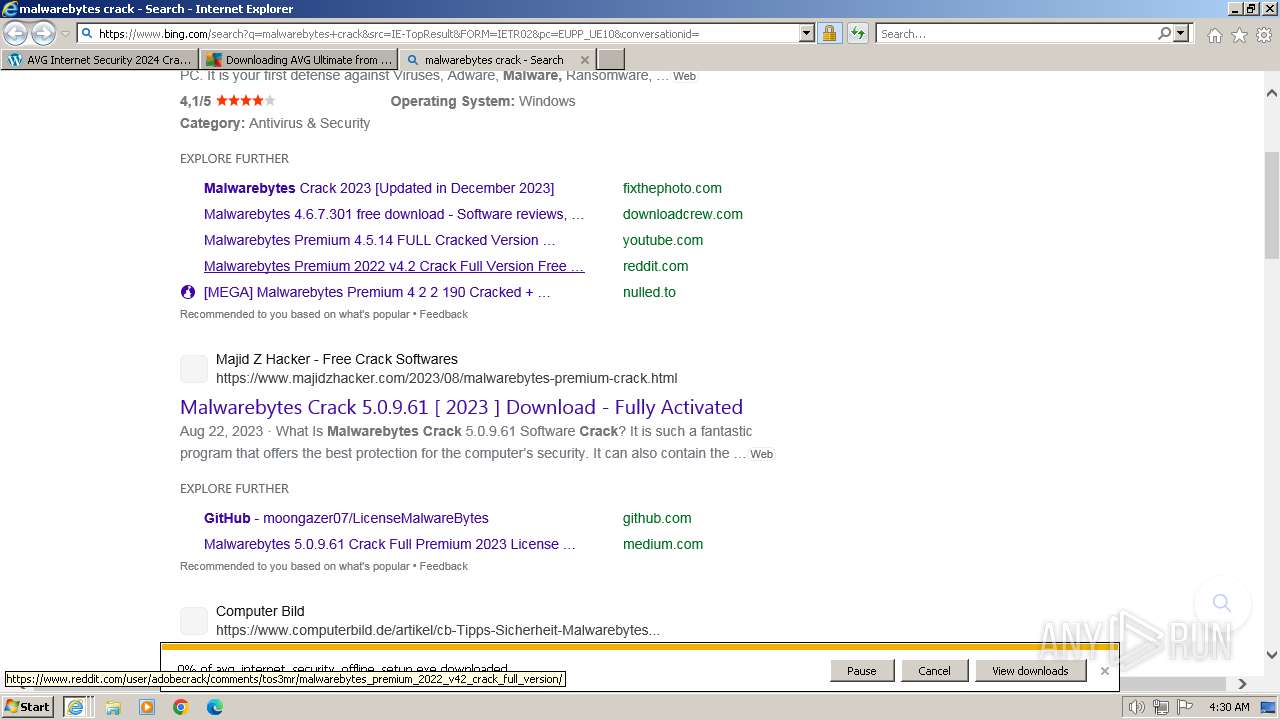
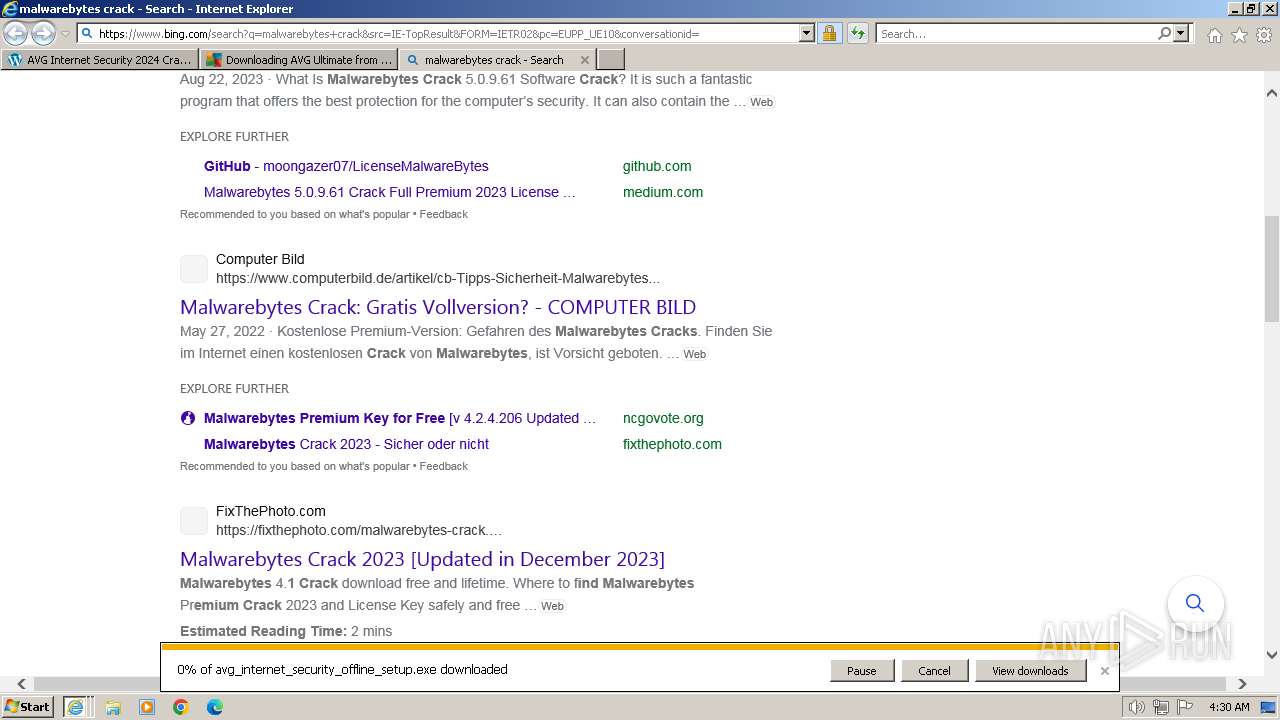
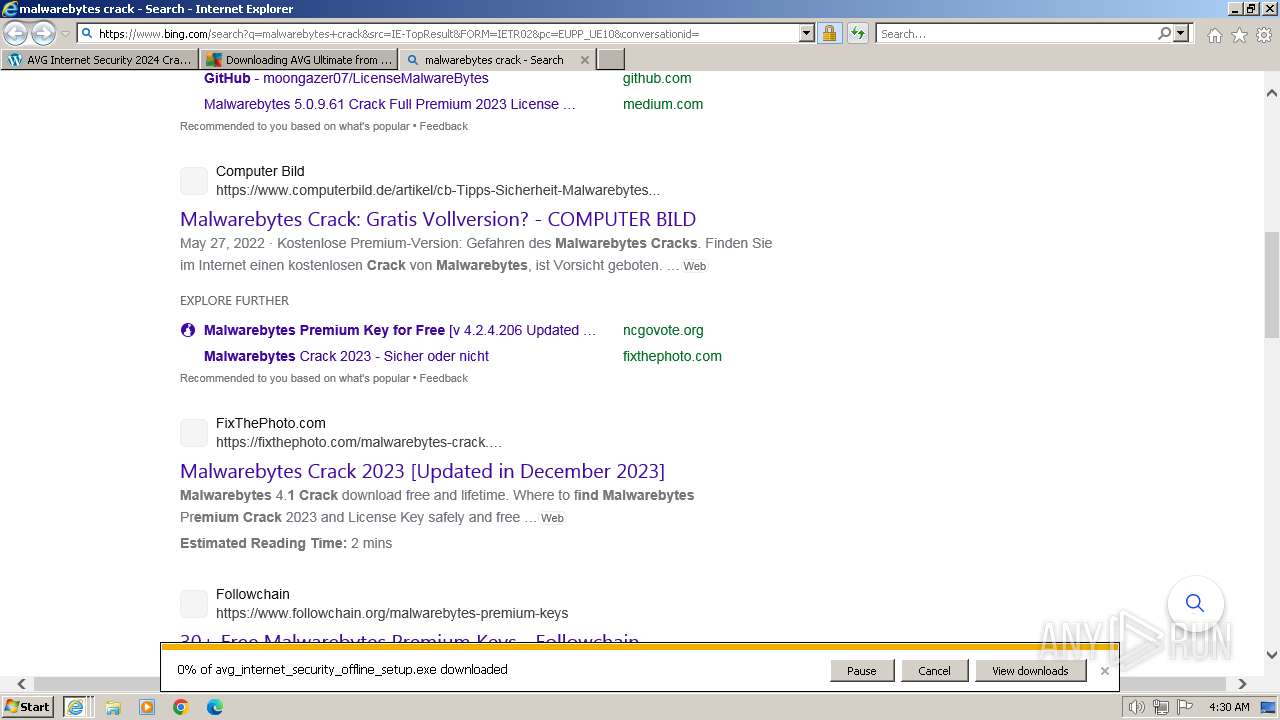
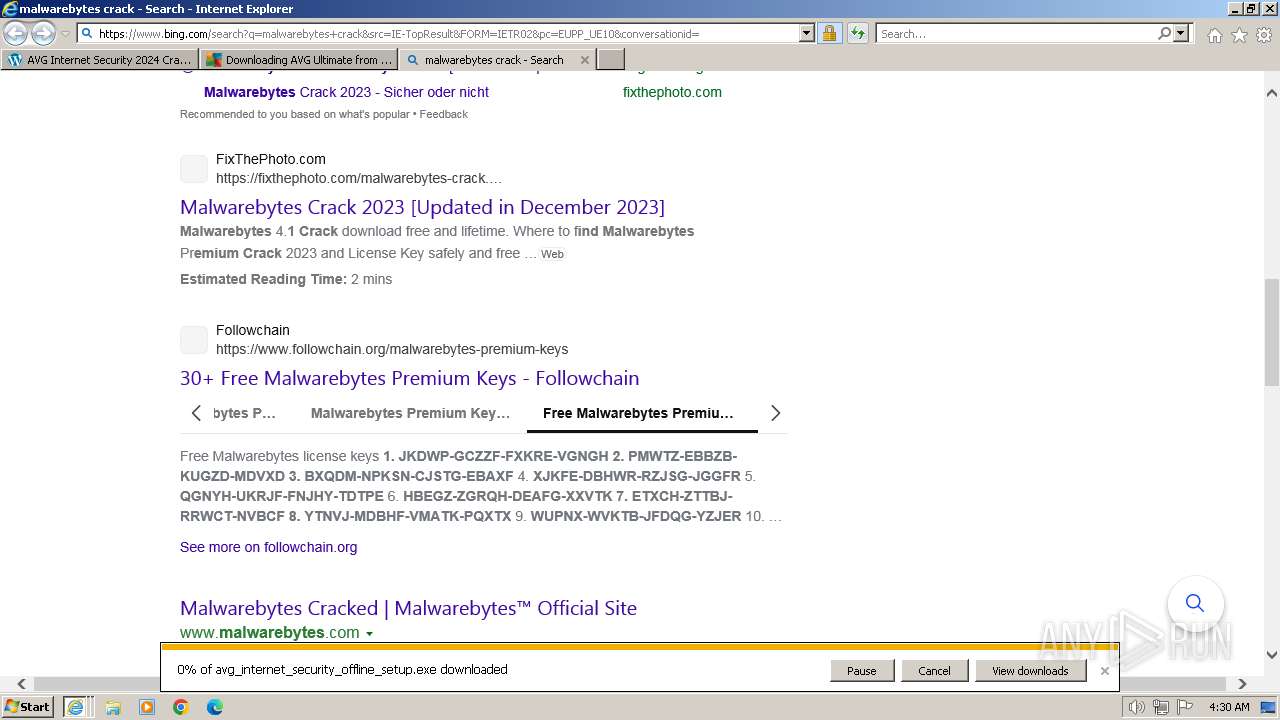
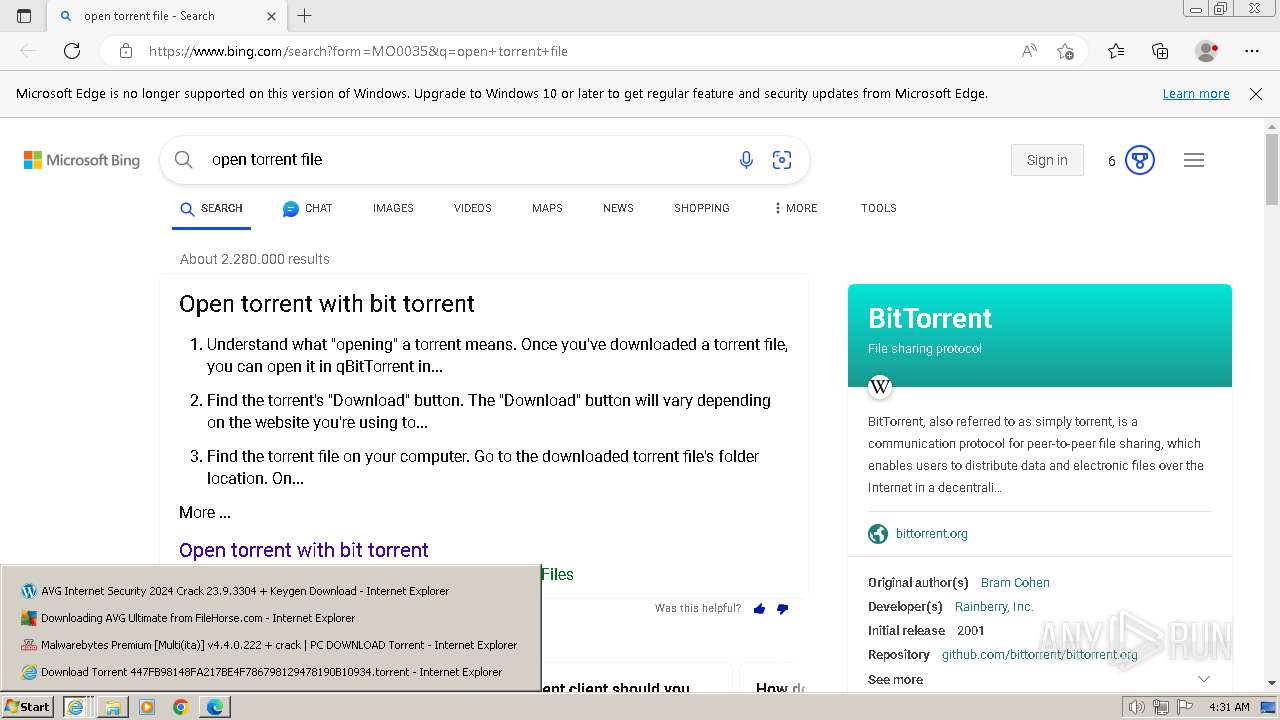
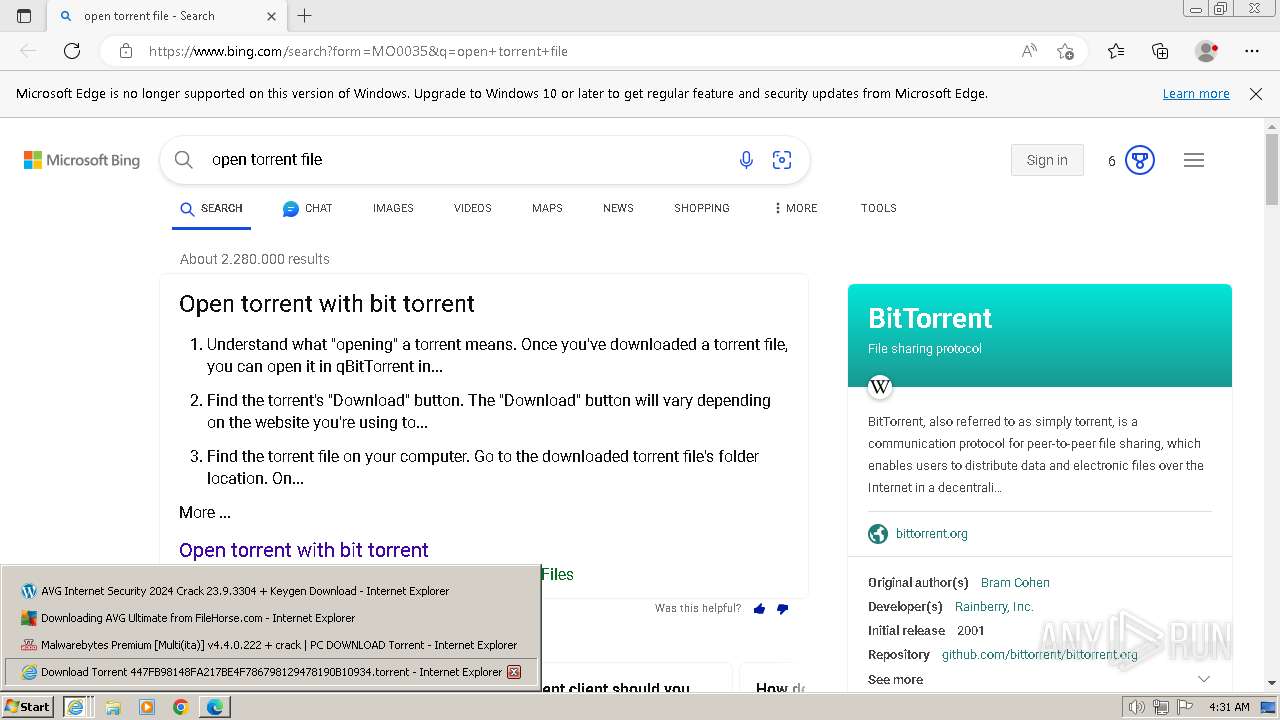
Bing abused for phishing
- iexplore.exe (PID: 2040)
SUSPICIOUS
Reads the Internet Settings
- rundll32.exe (PID: 3452)
Uses RUNDLL32.EXE to load library
- iexplore.exe (PID: 2040)
INFO
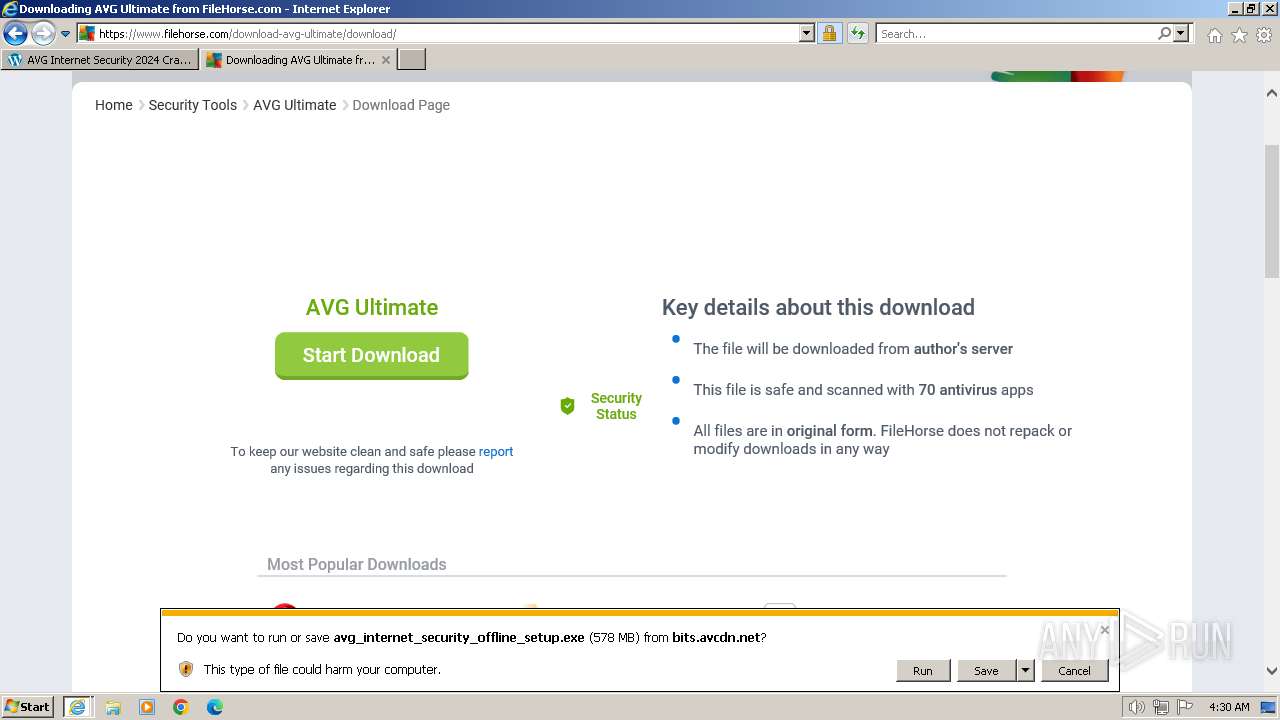
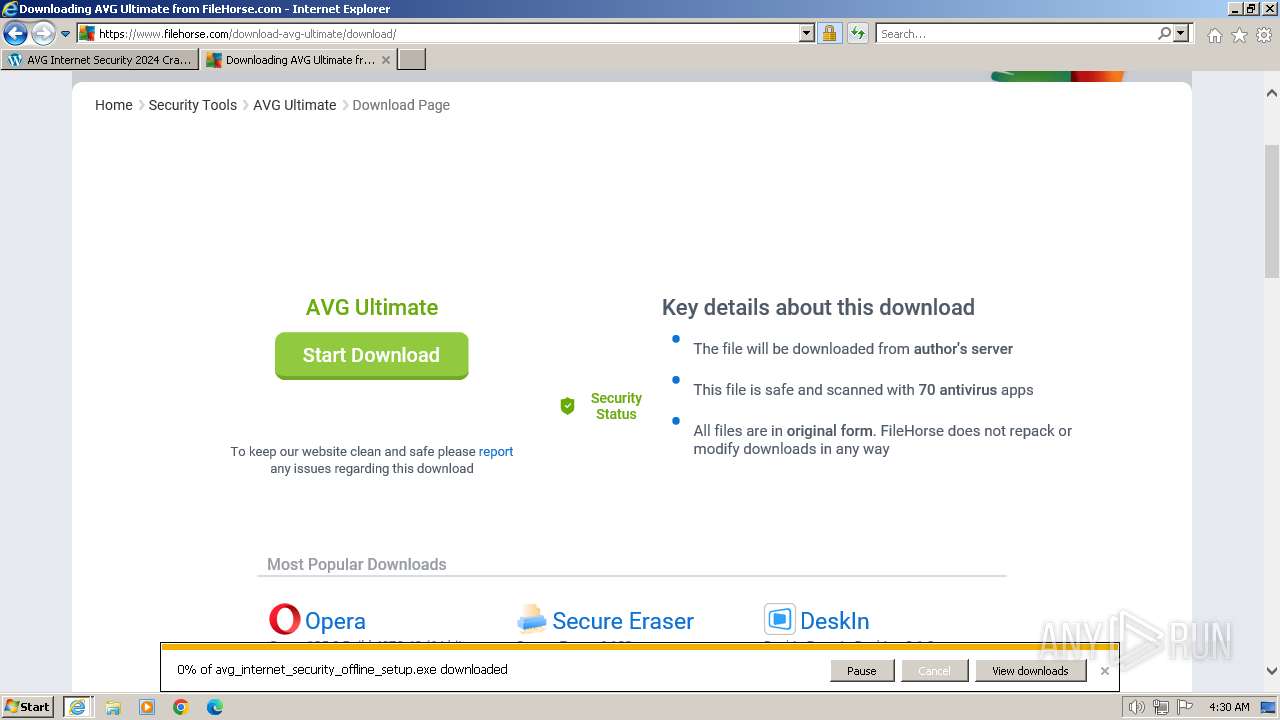
Drops the executable file immediately after the start
- iexplore.exe (PID: 2340)
Application launched itself
- iexplore.exe (PID: 2040)
- msedge.exe (PID: 3540)
The process uses the downloaded file
- iexplore.exe (PID: 2040)
Checks supported languages
- wmpnscfg.exe (PID: 4036)
Reads the computer name
- wmpnscfg.exe (PID: 4036)
Manual execution by a user
- wmpnscfg.exe (PID: 4036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
65
Monitored processes
29
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2040 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 332 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1284 --field-trial-handle=1276,i,10390951570399879058,2531183728663966993,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 560 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=3572 --field-trial-handle=1276,i,10390951570399879058,2531183728663966993,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1728 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3828 --field-trial-handle=1276,i,10390951570399879058,2531183728663966993,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1852 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2552 --field-trial-handle=1276,i,10390951570399879058,2531183728663966993,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.bing.com/ck/a?!&&p=402b16d292ca6881JmltdHM9MTcwMjc3MTIwMCZpZ3VpZD0zMzAyYWMyNC0xMTFiLTZlNWYtMDVkMy1iZmMwMTAzMjZmNzgmaW5zaWQ9NTM2Mg&ptn=3&ver=2&hsh=3&fclid=3302ac24-111b-6e5f-05d3-bfc010326f78&psq=avg+crack+keygen&u=a1aHR0cHM6Ly9heWVzaGFwYy5jb20vYXZnLWludGVybmV0LXNlY3VyaXR5LWNyYWNrLWtleS1rZXlnZW4tZG93bmxvYWQv&ntb=1" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1504 --field-trial-handle=1276,i,10390951570399879058,2531183728663966993,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3592 --field-trial-handle=1276,i,10390951570399879058,2531183728663966993,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2340 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2040 CREDAT:1119500 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2524 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3804 --field-trial-handle=1276,i,10390951570399879058,2531183728663966993,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
60 543
Read events
60 407
Write events
131
Delete events
5
Modification events
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
10
Suspicious files
313
Text files
596
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\AVG-Internet-Security-2019-Crack-Key-With-Keygen-Download1[1].jpg | image | |
MD5:A55C16ACC5156B7FAA3F13B597CDEF5E | SHA256:3356B708FF3EEB2C91411A854F57DA10CC438D94FAA04B4C672DD528FEAB4EDC | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:8794C4BF742CD29CCE8D57360615643F | SHA256:0B1703C4BE5A10D09ABEDFBD109ED986D52C091FD7567F27C13573CF6C5DC7EB | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:91F5EB94663F5BD73A29FB771DE337A4 | SHA256:7D6BD6B21BFD3E45E52A1EA4A046E5F0D5C9747D54462BEDD127E14D739523D5 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\a[1].htm | html | |
MD5:680E64694847F6B499C3B0C5A8EEE562 | SHA256:659357710E2E7088277BC840B5AC356067DDA43419CB03A51D192BB4A0403EB4 | |||
| 2040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:95671A98B1868C9D3041F2AE2F627D6C | SHA256:D329DE8AA3EB7A4D9A21F3491A7A7E174AC4CE1BAAF3F9DA01FEE6F5BC17ABE6 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:518860CA5350B8B52C03CA54D037340C | SHA256:8A6109FC4A4E3B8B25192901C56AFD9F074118C8D04FD2AD26384969975F1715 | |||
| 2040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:308DB8CFCC0A741A057178725F4ABEE7 | SHA256:33413A313B94DC3EBC54DE4D62F9F2966D2F9DDFEFB8EDC518CED8E2BBD5AA4E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
264
DNS requests
129
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
296 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
296 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6b21170b0e7a1648 | unknown | compressed | 4.66 Kb | unknown |
296 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
296 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2040 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?08d91df001b427ad | unknown | — | — | unknown |
296 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
2040 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a85e8d0c2f0a71a5 | unknown | — | — | unknown |
296 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d6d69799ff621c73 | unknown | compressed | 65.2 Kb | unknown |
296 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e4fe275728f4107f | unknown | compressed | 65.2 Kb | unknown |
296 | iexplore.exe | GET | 200 | 23.60.200.134:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
296 | iexplore.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | unknown |
296 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
296 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
296 | iexplore.exe | 104.21.68.225:443 | ayeshapc.com | CLOUDFLARENET | — | unknown |
2040 | iexplore.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | unknown |
296 | iexplore.exe | 216.58.206.35:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2040 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ayeshapc.com |
| unknown |
ocsp.pki.goog |
| whitelisted |
x78qegokj.cfd |
| unknown |
static.addtoany.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
api.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |