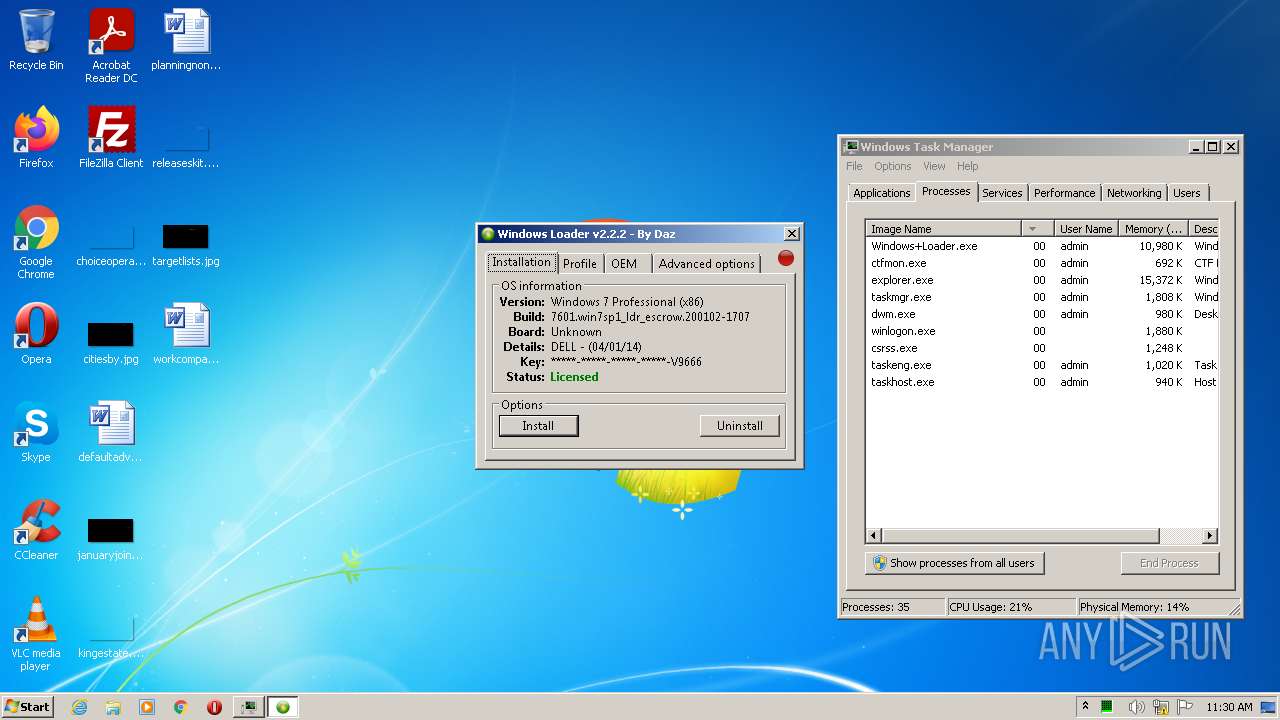
| File name: | Windows+Loader.exe |
| Full analysis: | https://app.any.run/tasks/9208a907-0f7a-42e2-b124-32aad9946cda |
| Verdict: | Malicious activity |
| Analysis date: | July 26, 2022, 10:29:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 323C0FD51071400B51EEDB1BE90A8188 |
| SHA1: | 0EFC35935957C25193BBE9A83AB6CAA25A487ADA |
| SHA256: | 2F2ABA1E074F5F4BAA08B524875461889F8F04D4FFC43972AC212E286022AB94 |
| SSDEEP: | 49152:cEYCFEvlmOmTgtFM3uK5m3imrHuiff+puWV355FXw/+zuWV355FXw/+DuWV355FP:cEYzEFTgtFM3ukm3imPnt |
MALICIOUS
Drops executable file immediately after starts
- Windows+Loader.exe (PID: 1876)
Application was dropped or rewritten from another process
- bootsect.exe (PID: 3576)
SUSPICIOUS
Checks supported languages
- Windows+Loader.exe (PID: 1876)
- cmd.exe (PID: 2092)
- cmd.exe (PID: 4028)
- cmd.exe (PID: 3664)
- cmd.exe (PID: 328)
- cscript.exe (PID: 2532)
- cmd.exe (PID: 3660)
- cscript.exe (PID: 2952)
- cmd.exe (PID: 3160)
- bootsect.exe (PID: 3576)
- cmd.exe (PID: 3016)
- cmd.exe (PID: 1692)
- cmd.exe (PID: 3016)
- cmd.exe (PID: 948)
- cmd.exe (PID: 3248)
Reads the computer name
- Windows+Loader.exe (PID: 1876)
- cscript.exe (PID: 2952)
- cscript.exe (PID: 2532)
Reads Environment values
- Windows+Loader.exe (PID: 1876)
Reads Windows Product ID
- Windows+Loader.exe (PID: 1876)
Application launched itself
- cmd.exe (PID: 3664)
- cmd.exe (PID: 3016)
Executable content was dropped or overwritten
- Windows+Loader.exe (PID: 1876)
Drops a file with a compile date too recent
- Windows+Loader.exe (PID: 1876)
INFO
Checks supported languages
- taskmgr.exe (PID: 968)
- icacls.exe (PID: 3744)
- icacls.exe (PID: 2296)
- takeown.exe (PID: 3716)
- compact.exe (PID: 3088)
- shutdown.exe (PID: 752)
- takeown.exe (PID: 3324)
Reads the computer name
- taskmgr.exe (PID: 968)
- icacls.exe (PID: 3744)
- takeown.exe (PID: 3716)
- icacls.exe (PID: 2296)
- shutdown.exe (PID: 752)
- takeown.exe (PID: 3324)
Manual execution by user
- taskmgr.exe (PID: 968)
Checks Windows Trust Settings
- cscript.exe (PID: 2532)
- cscript.exe (PID: 2952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (30.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (20) |
| .exe | | | UPX compressed Win32 Executable (19.6) |
| .exe | | | Win32 EXE Yoda's Crypter (19.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.7) |
EXIF
EXE
| InternalName: | - |
|---|---|
| OriginalFileName: | Windows Loader.exe |
| ProductName: | - |
| ProductVersion: | - |
| LegalCopyright: | - |
| FileDescription: | - |
| Release: | Final |
| Country: | - |
| FileVersion: | 2.2.2.0 |
| CompanyName: | - |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | Pre-release, Private build |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 2.2.2.0 |
| FileVersionNumber: | 2.2.2.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x21a9a0 |
| UninitializedDataSize: | 1613824 |
| InitializedDataSize: | 28672 |
| CodeSize: | 593920 |
| LinkerVersion: | 8 |
| PEType: | PE32 |
| TimeStamp: | 2007:10:31 17:53:19+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Total processes
71
Monitored processes
23
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | cmd.exe /A /C "C:\Windows\System32\cscript.exe //nologo C:\Windows\System32\slmgr.vbs -ilc "C:\Dell.XRM-MS"" | C:\Windows\system32\cmd.exe | — | Windows+Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 752 | shutdown -r -t 0 | C:\Windows\system32\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 948 | cmd.exe /A /C "icacls C:\ldrscan\bootwin /grant *S-1-1-0:(F)" | C:\Windows\system32\cmd.exe | — | Windows+Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 968 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1692 | cmd.exe /A /C "shutdown -r -t 0" | C:\Windows\system32\cmd.exe | — | Windows+Loader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1876 | "C:\Users\admin\AppData\Local\Temp\Windows+Loader.exe" | C:\Users\admin\AppData\Local\Temp\Windows+Loader.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2092 | cmd.exe /c takeown /f C:\ldrscan\bootwin | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2296 | icacls C:\ldrscan\bootwin /grant *S-1-1-0:(F) | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2532 | C:\Windows\System32\cscript.exe //nologo C:\Windows\System32\slmgr.vbs -ilc "C:\Dell.XRM-MS" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2952 | C:\Windows\System32\cscript.exe //nologo C:\Windows\System32\slmgr.vbs -ipk 32KD2-K9CTF-M3DJT-4J3WC-733WD | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
795
Read events
795
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3576 | bootsect.exe | \Device\HarddiskVolume1 | — | |
MD5:— | SHA256:— | |||
| 1876 | Windows+Loader.exe | C:\bootsect.dat | executable | |
MD5:— | SHA256:— | |||
| 1876 | Windows+Loader.exe | C:\Dell.XRM-MS | xml | |
MD5:18B1E45BF56F40C3C4BBE65831178216 | SHA256:D072A059D3ED3E75C98B85B41E4319E8D5CFAE0E0C239B62436A3AD34003AB4A | |||
| 1876 | Windows+Loader.exe | \\?\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963}\MCZUG | binary | |
MD5:— | SHA256:— | |||
| 1876 | Windows+Loader.exe | C:\bootsect.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report