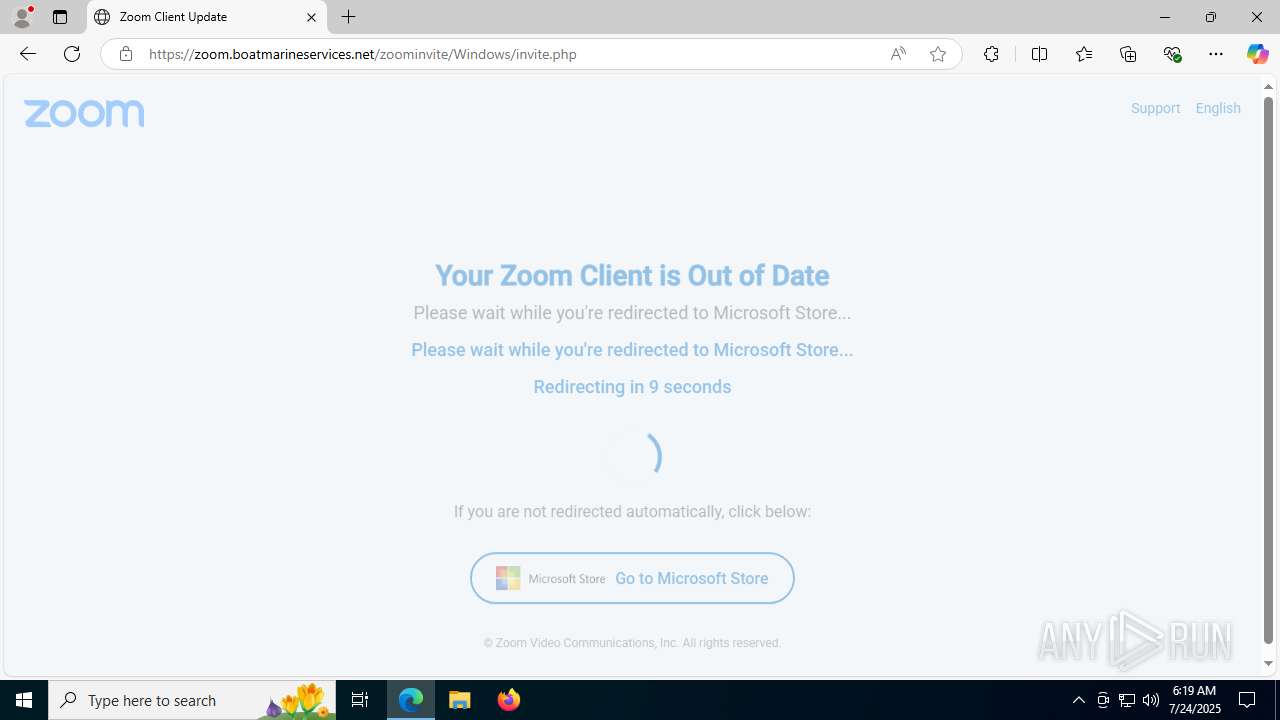
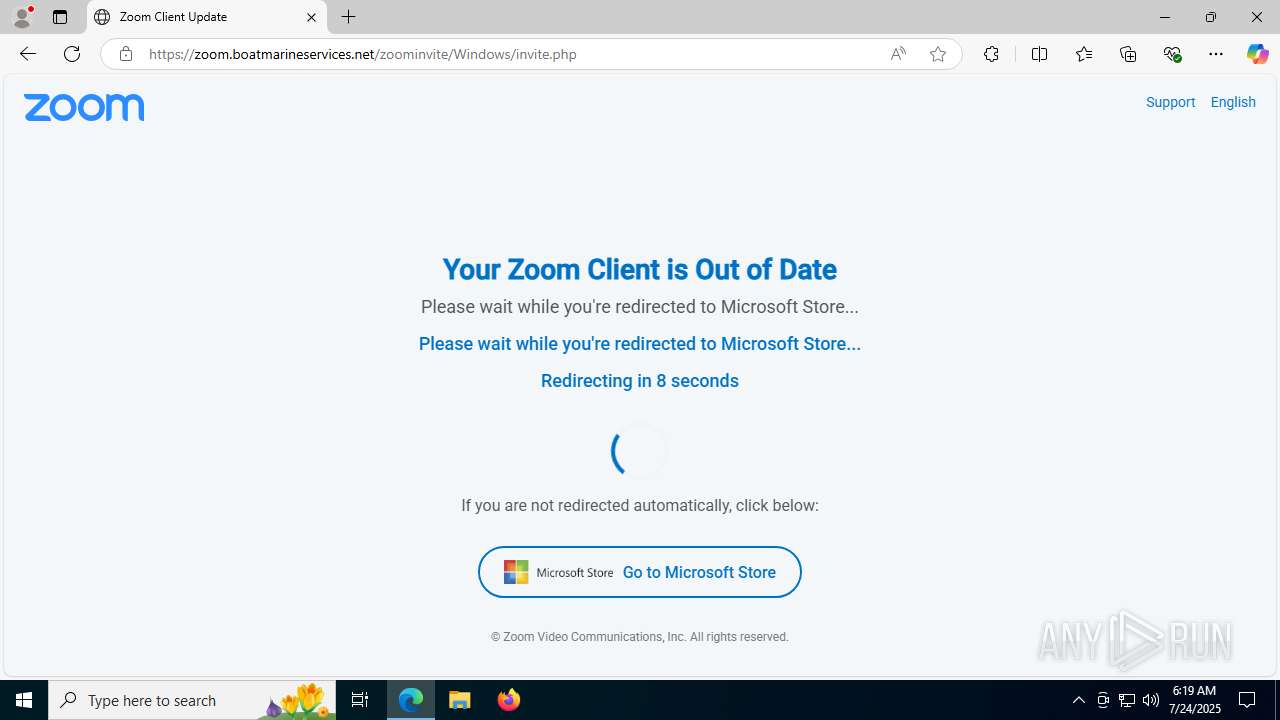
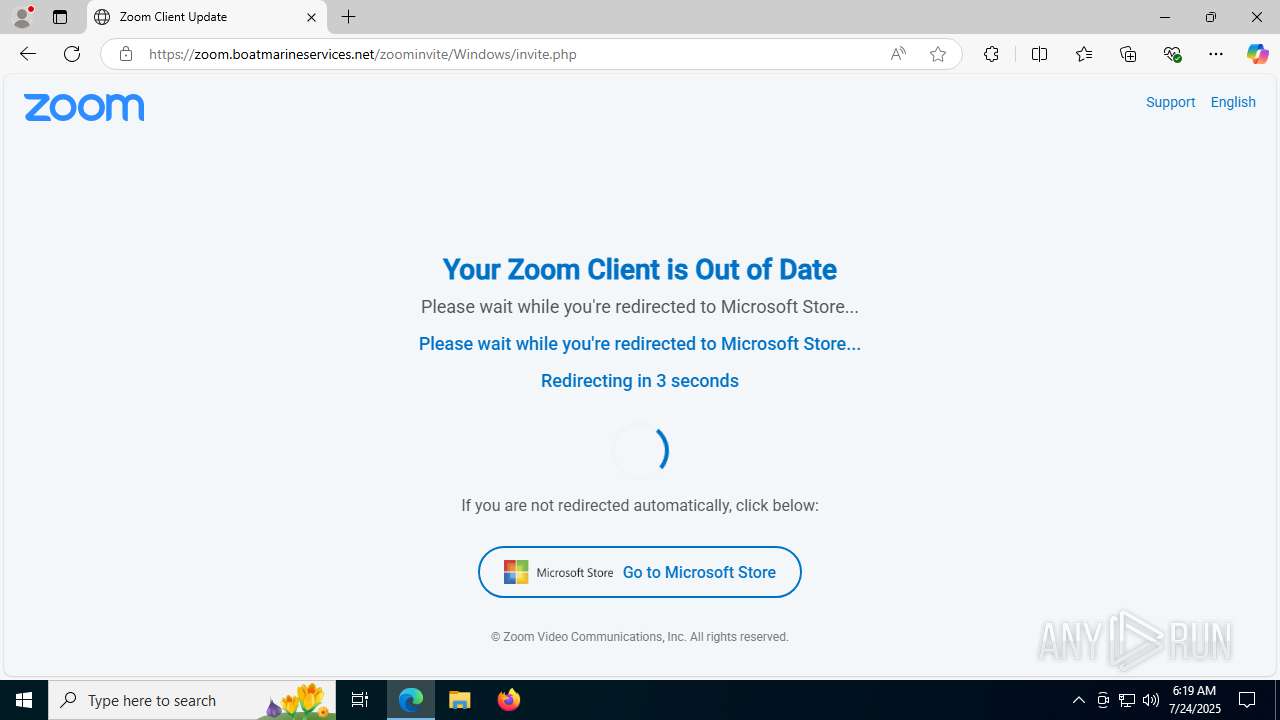
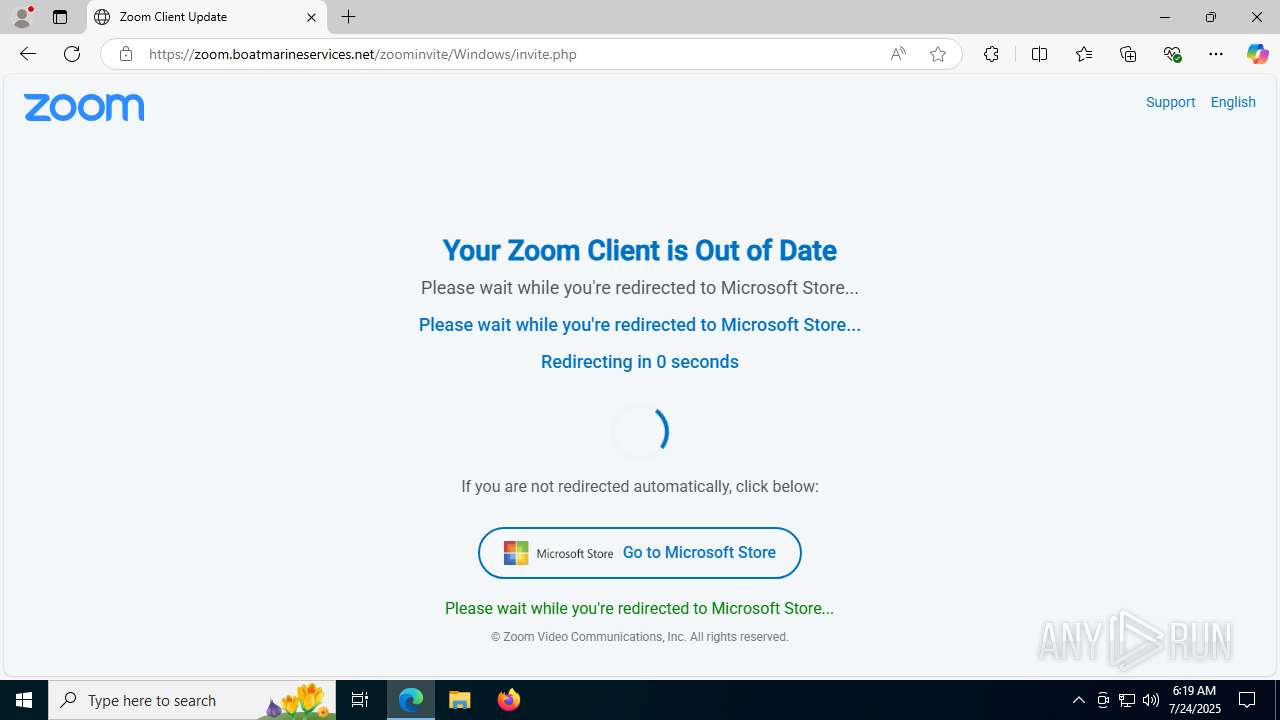
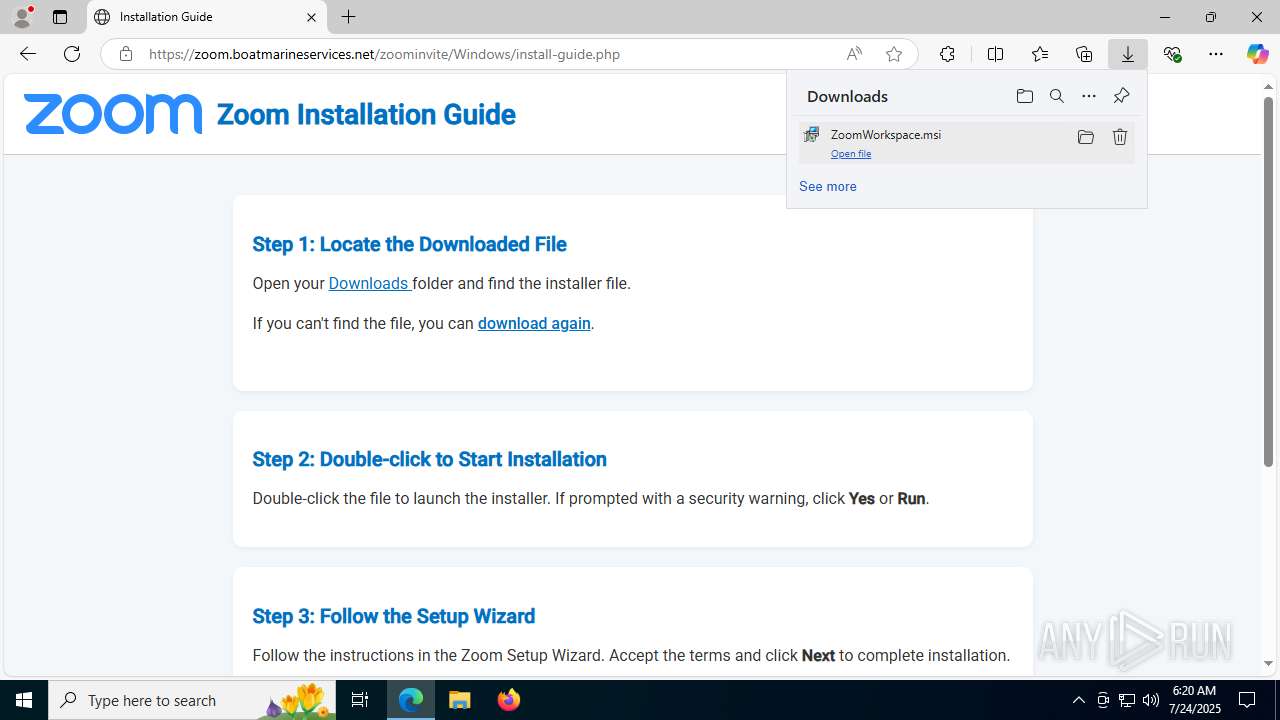
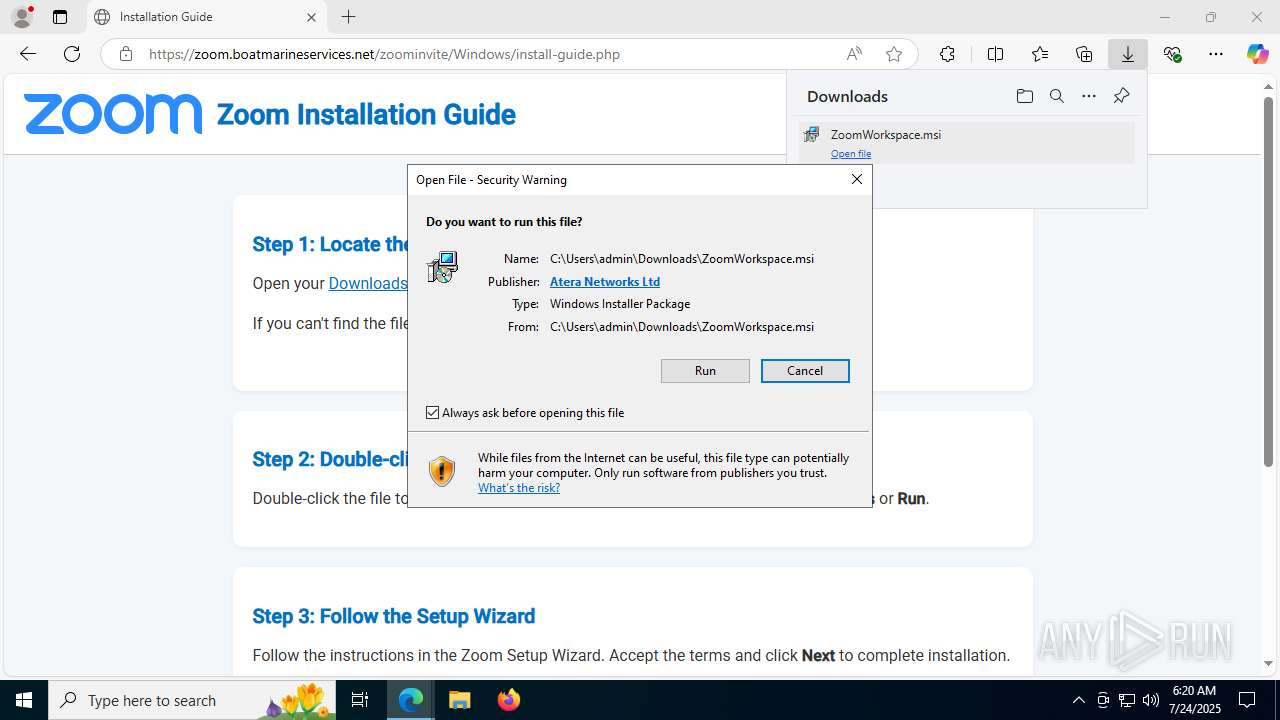
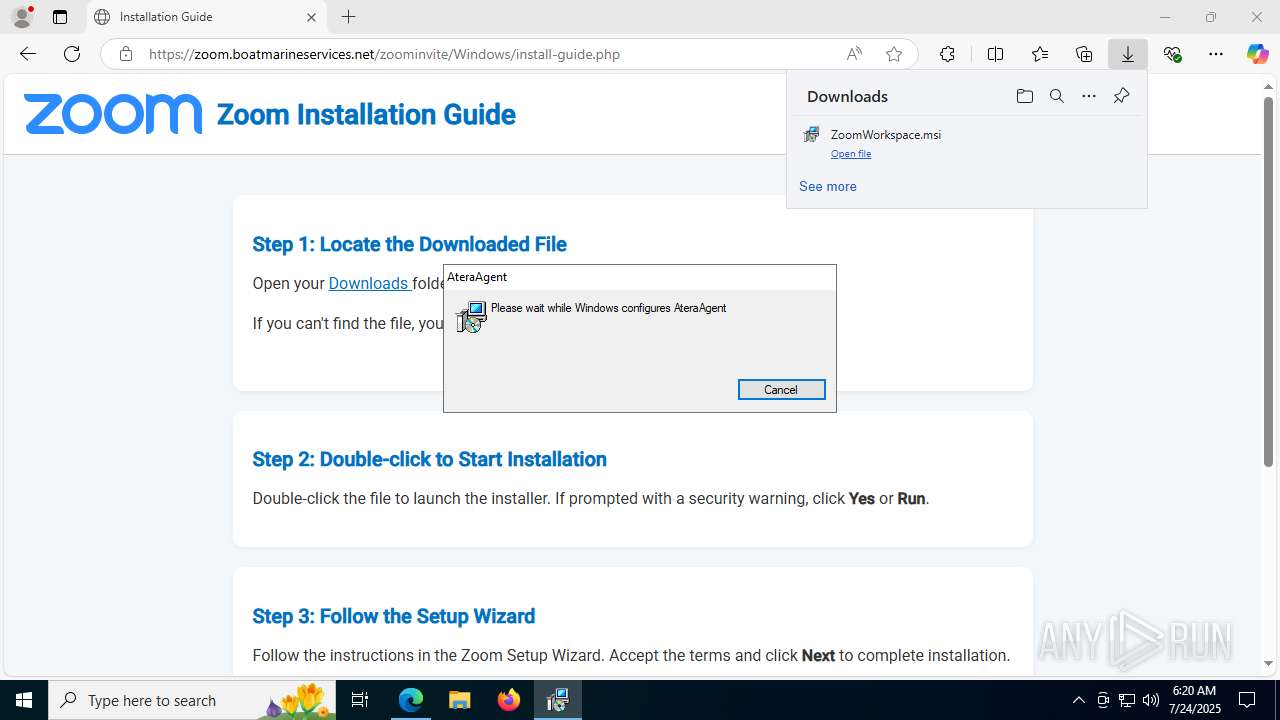
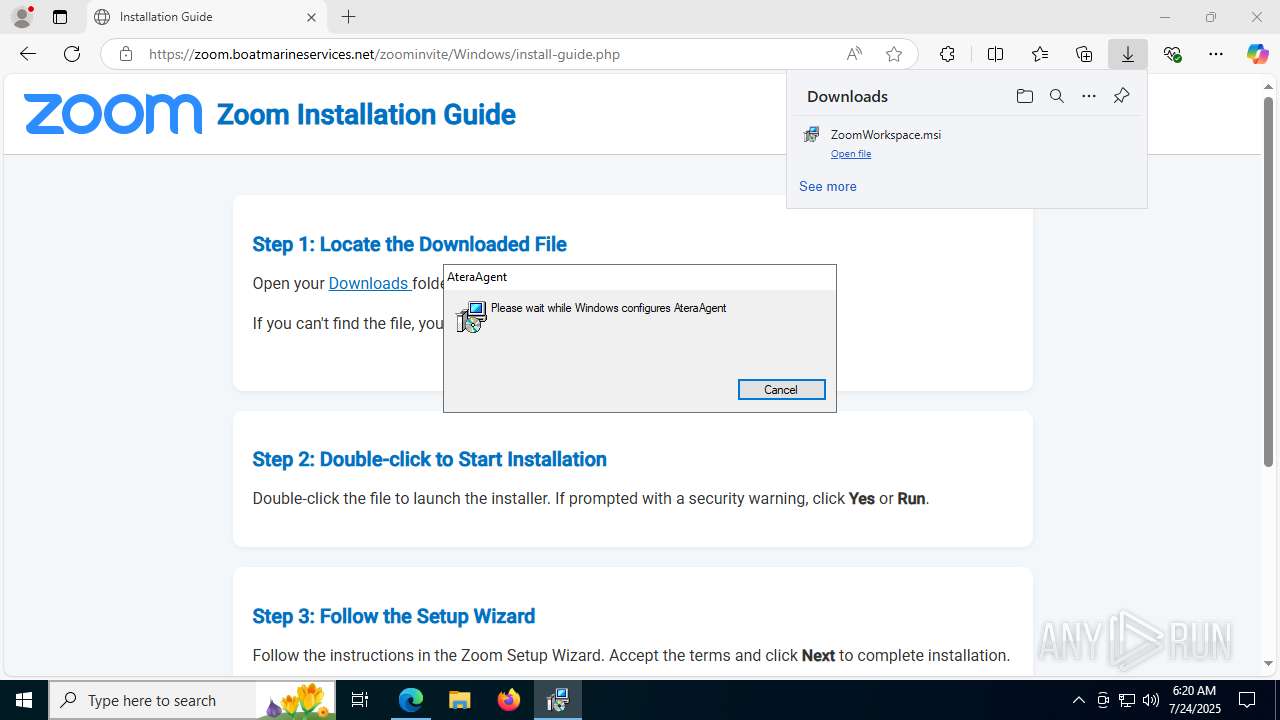
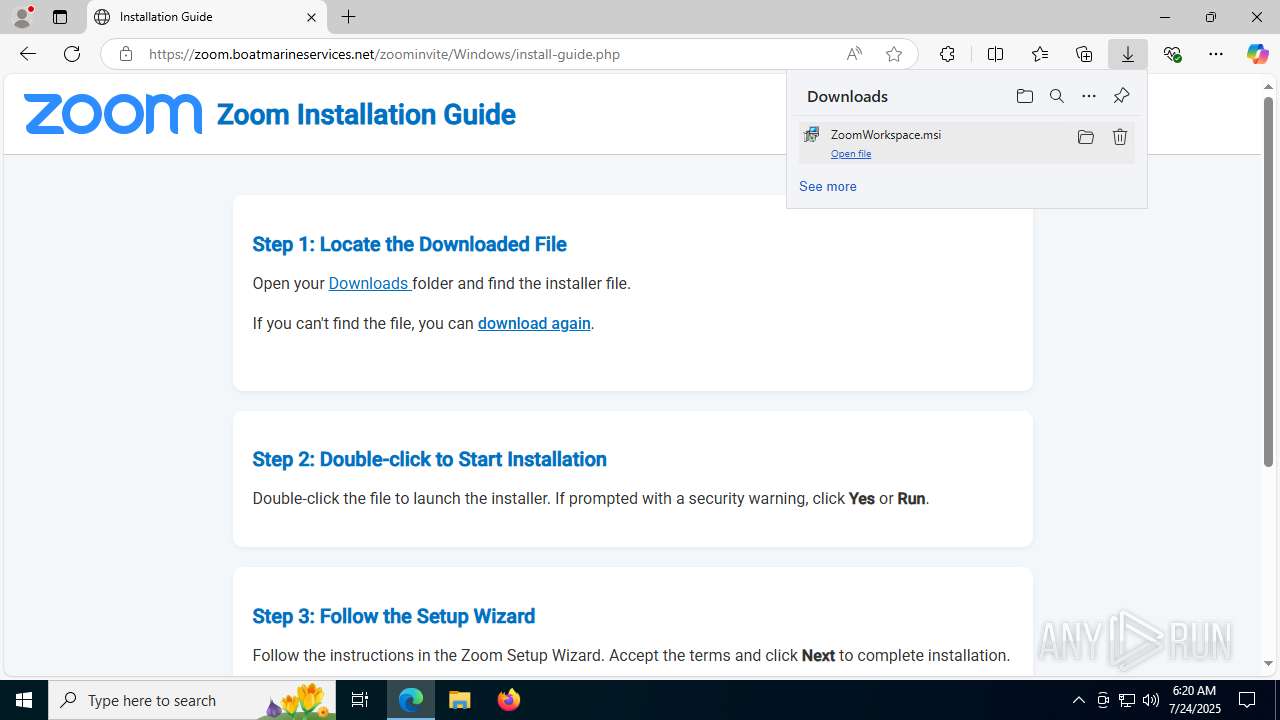
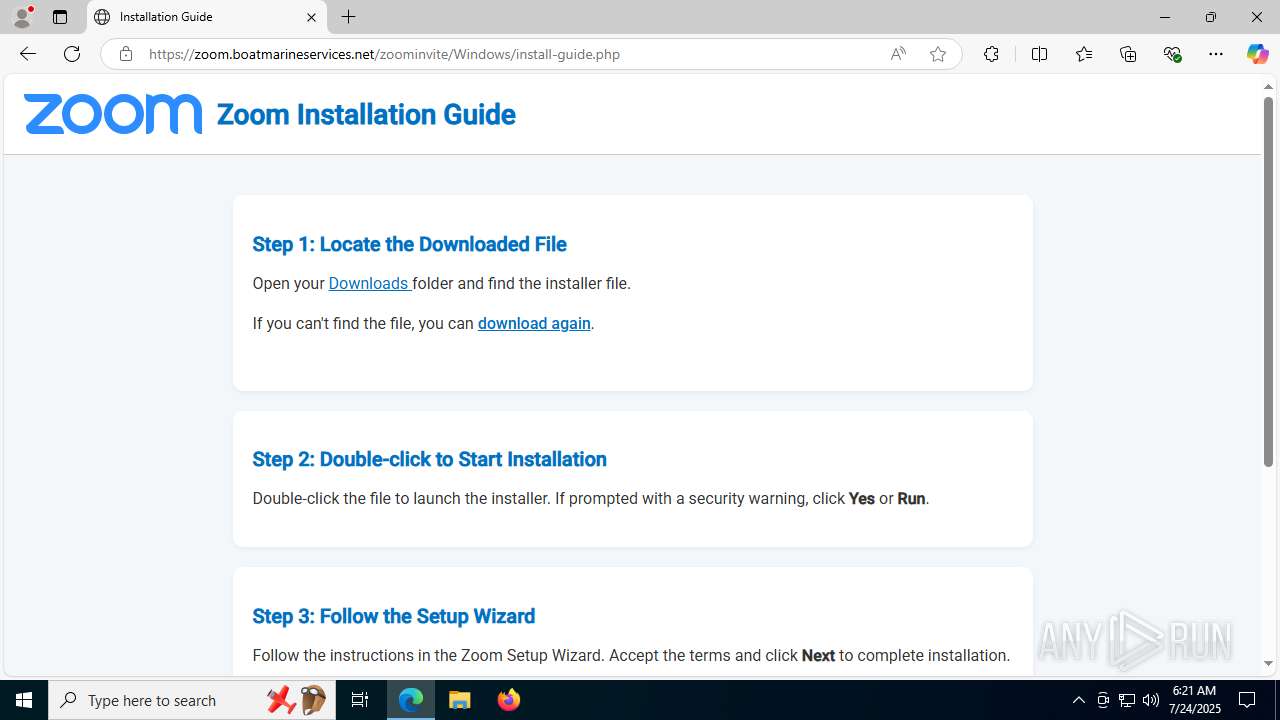
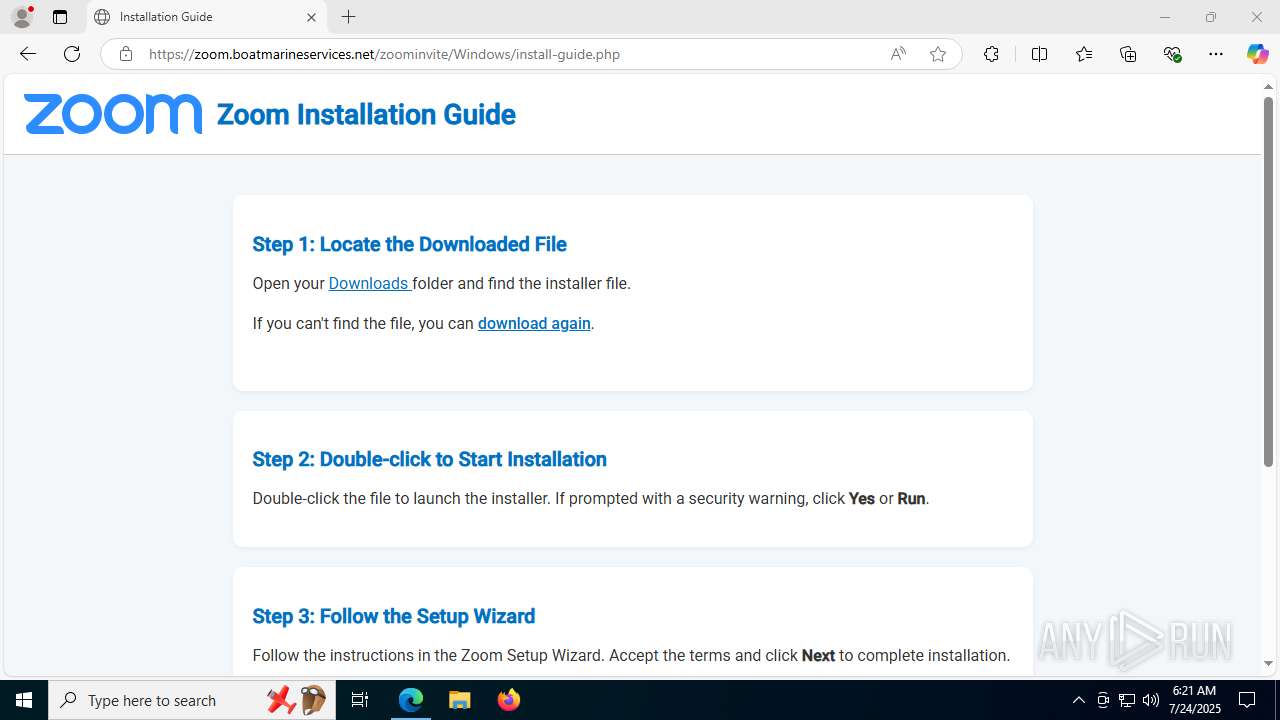
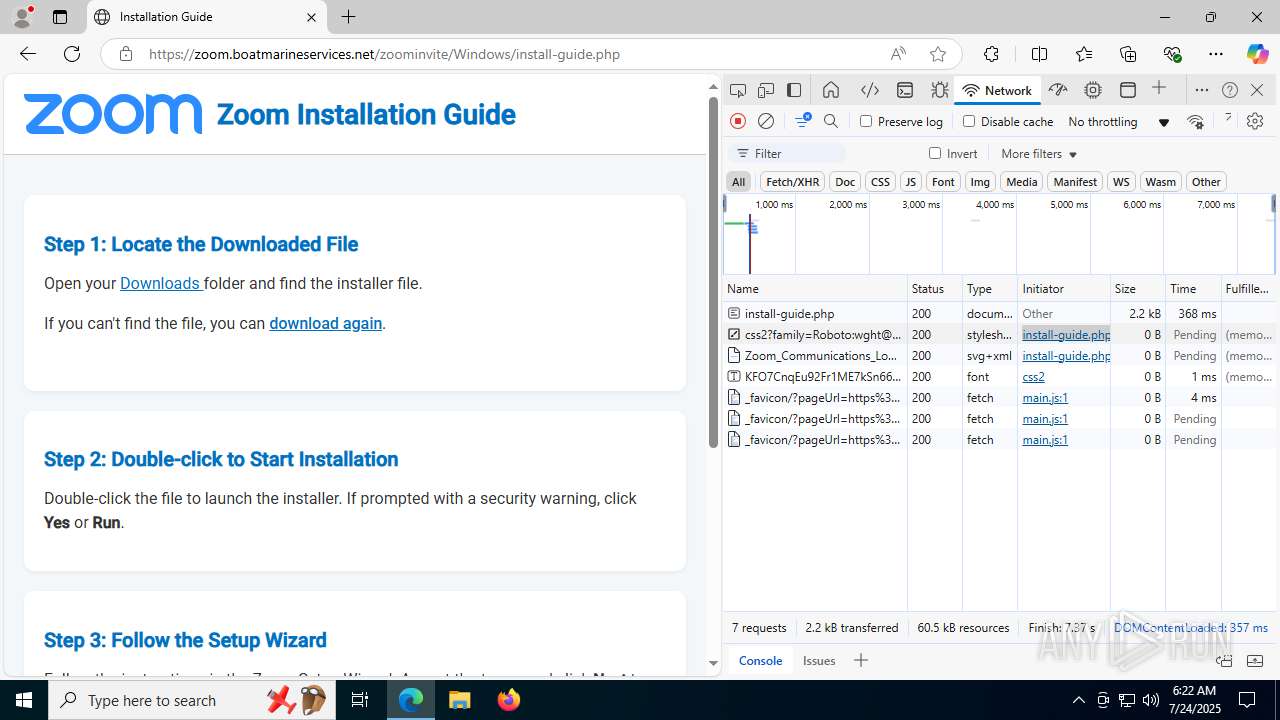
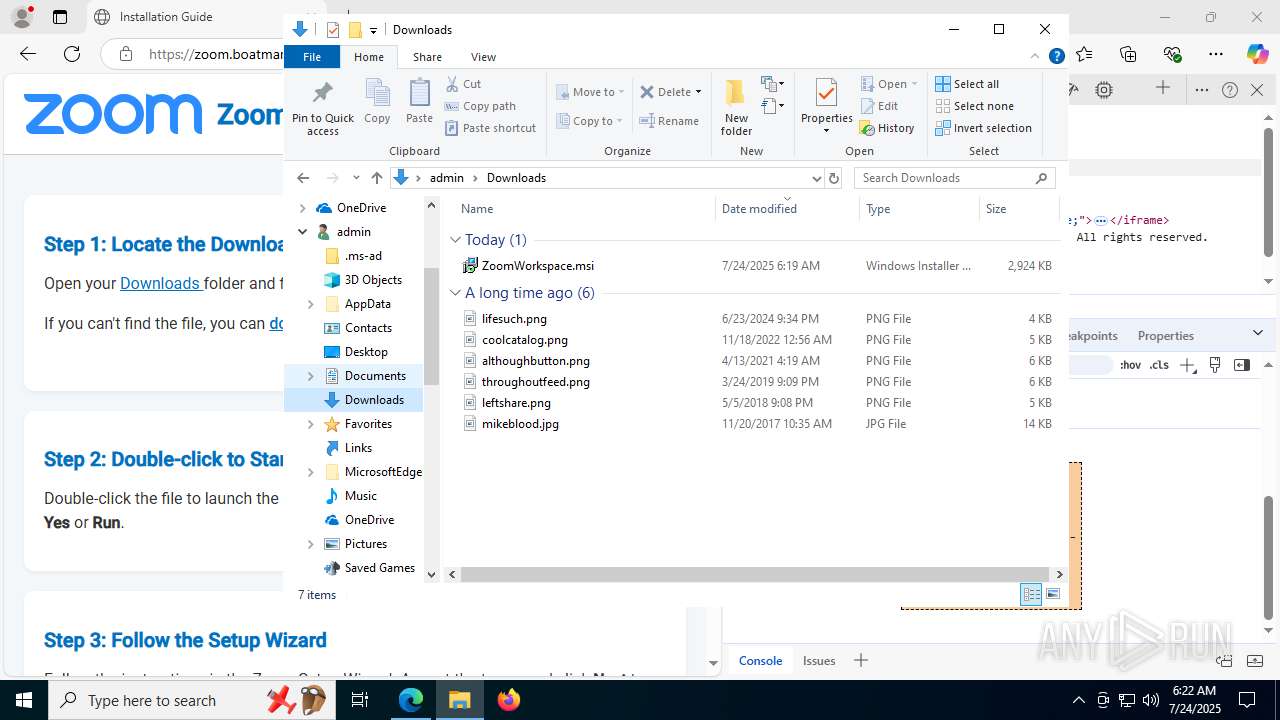
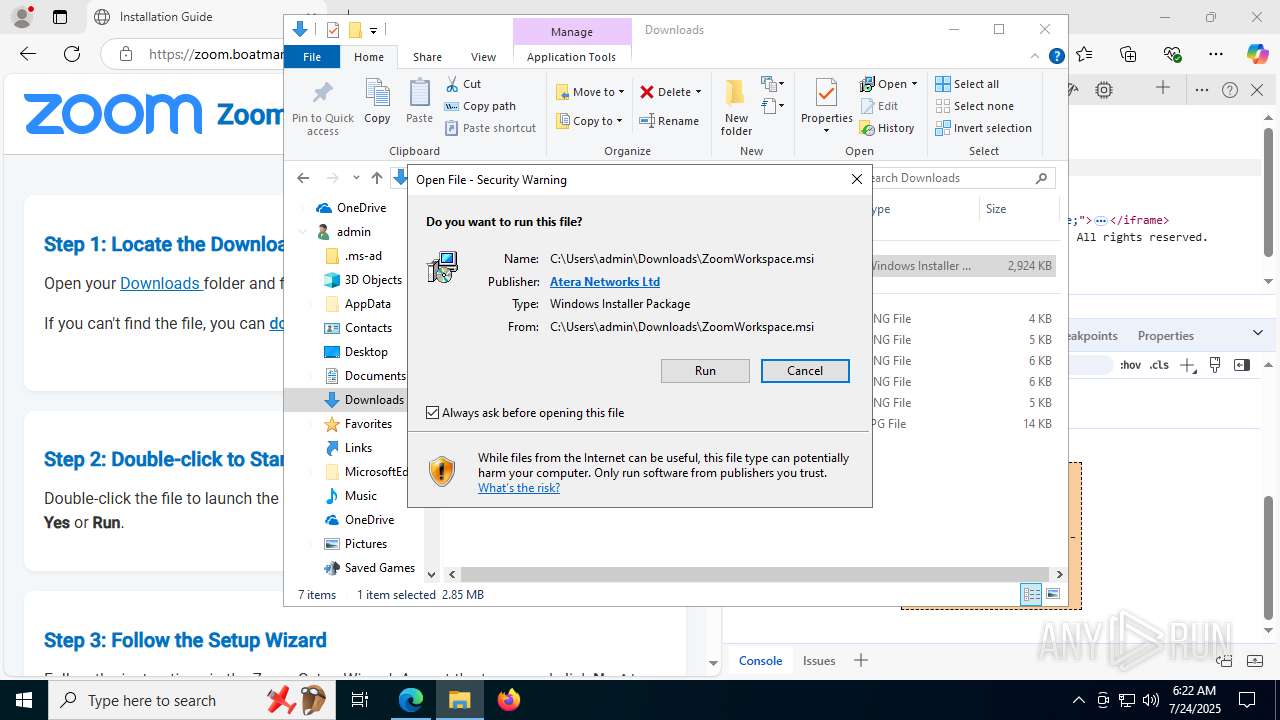
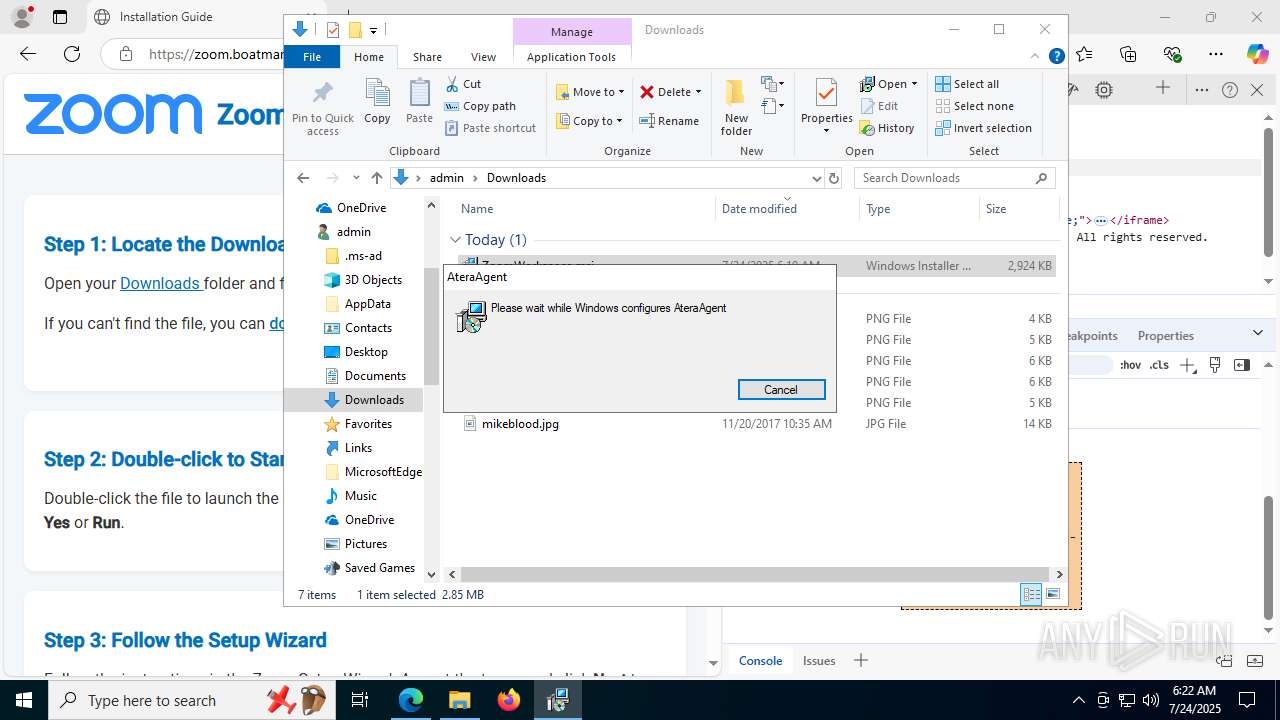
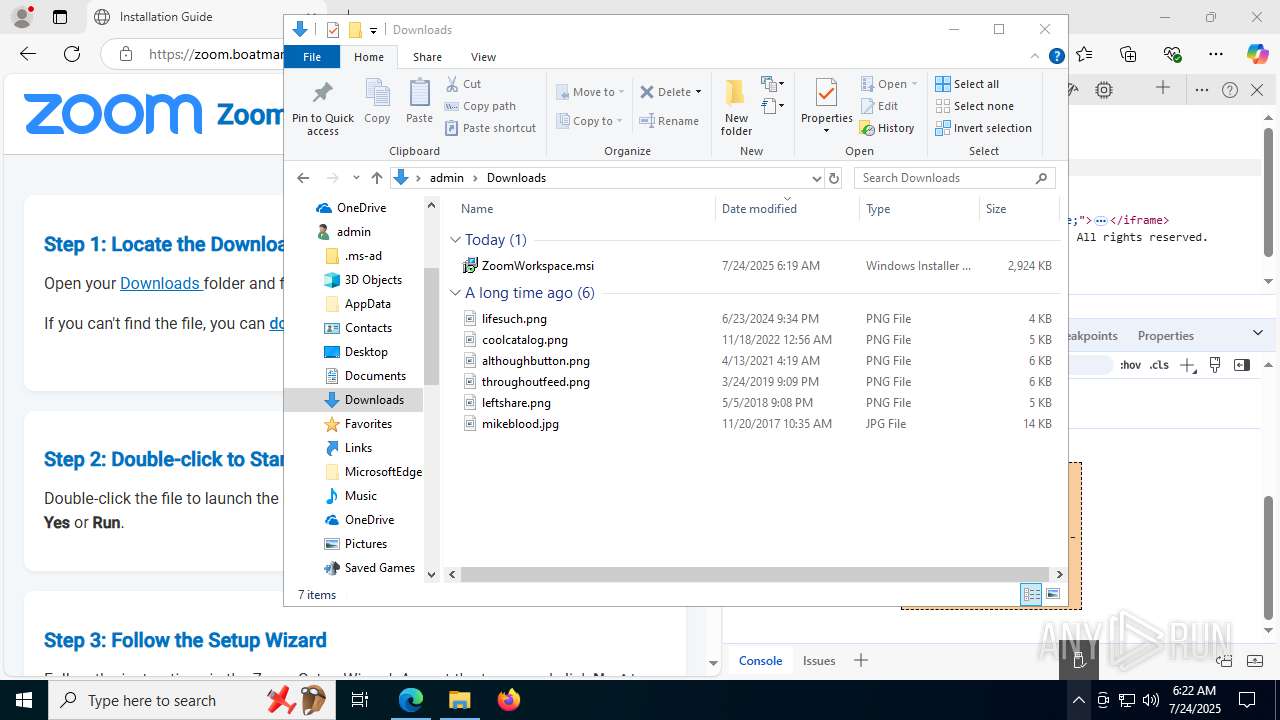
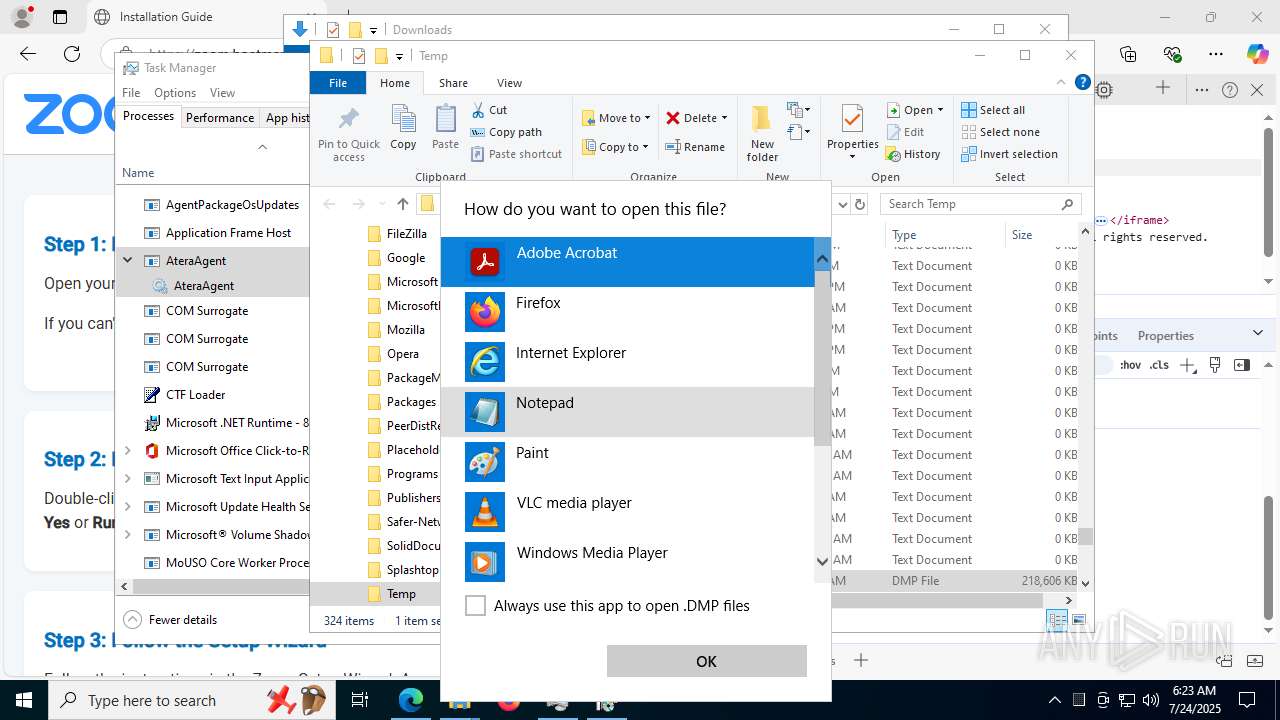
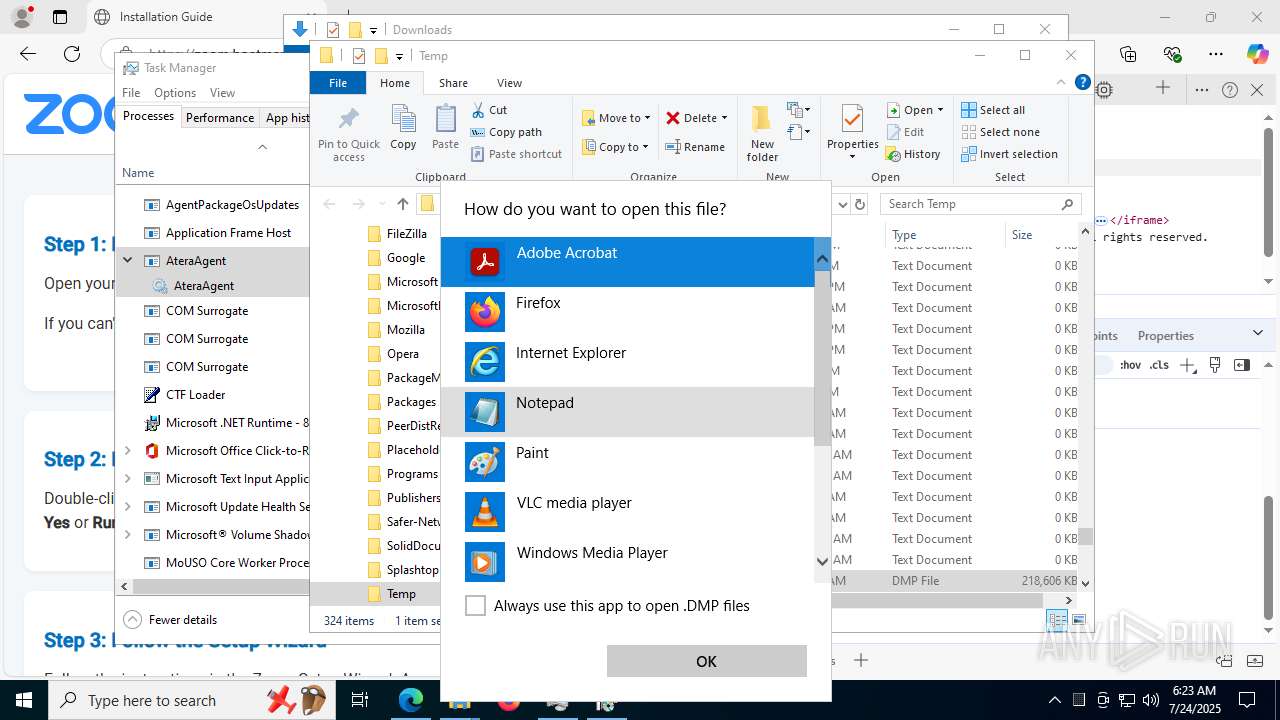
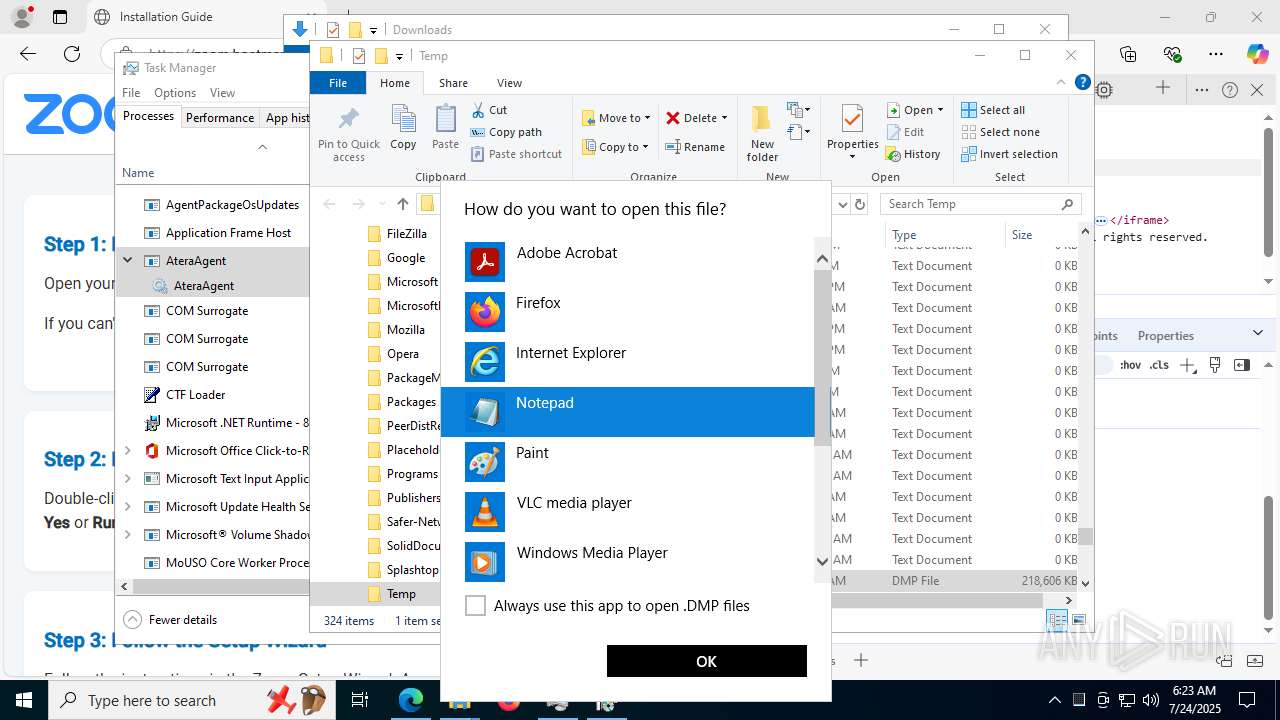
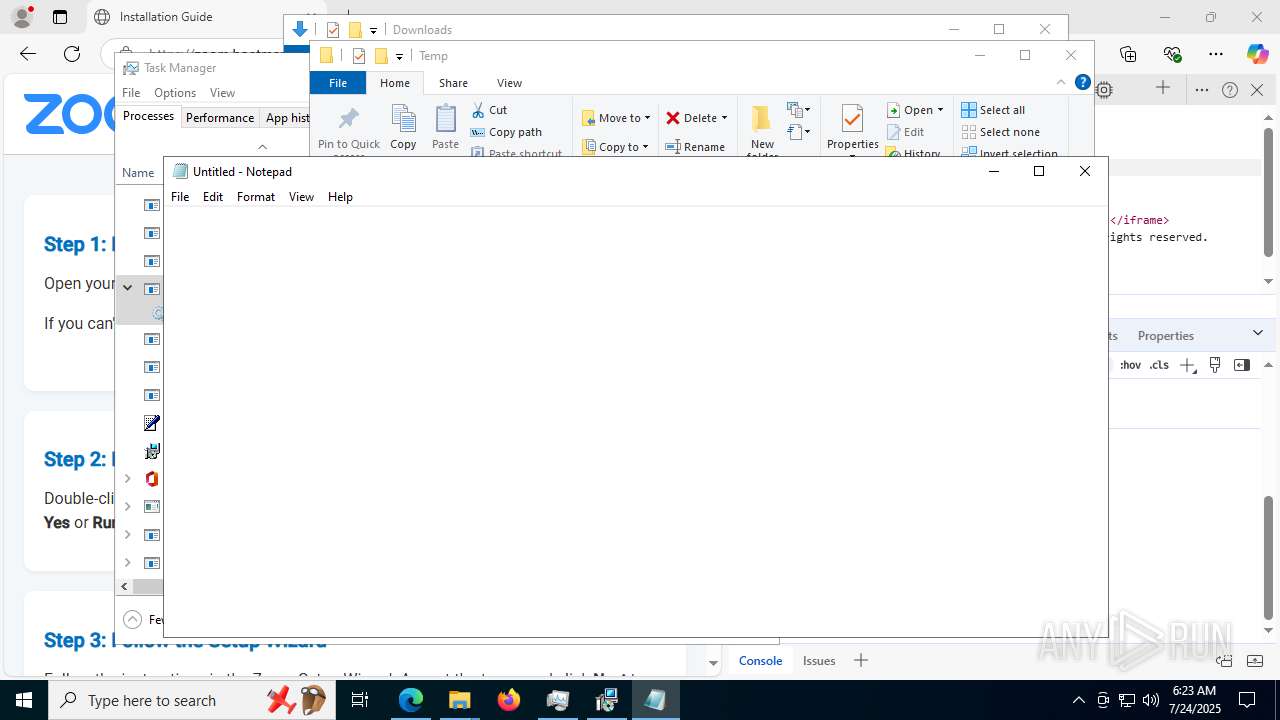
| URL: | https://zoom.boatmarineservices.net/zoominvite |
| Full analysis: | https://app.any.run/tasks/007863e1-4be5-43b1-811a-3df8b74719eb |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2025, 06:19:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D06C132B1FCB7EF3BF217EFBD005D171 |
| SHA1: | C08CB8E76A5F79679051AE858F7F7857B3114B63 |
| SHA256: | 2F16A59201089E8DE87149C4DF9E7E925DAAAFDD18FF5ADE588624AAA57E0E96 |
| SSDEEP: | 3:N88LrM0jMrRKmQ:28LY4MrW |
MALICIOUS
Starts NET.EXE for service management
- msiexec.exe (PID: 4308)
- net.exe (PID: 5900)
- msiexec.exe (PID: 8684)
- net.exe (PID: 1728)
- net.exe (PID: 8840)
Bypass execution policy to execute commands
- powershell.exe (PID: 7932)
- powershell.exe (PID: 1704)
- powershell.exe (PID: 3620)
Changes powershell execution policy (Bypass)
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageAgentInformation.exe (PID: 9132)
- AgentPackageAgentInformation.exe (PID: 2876)
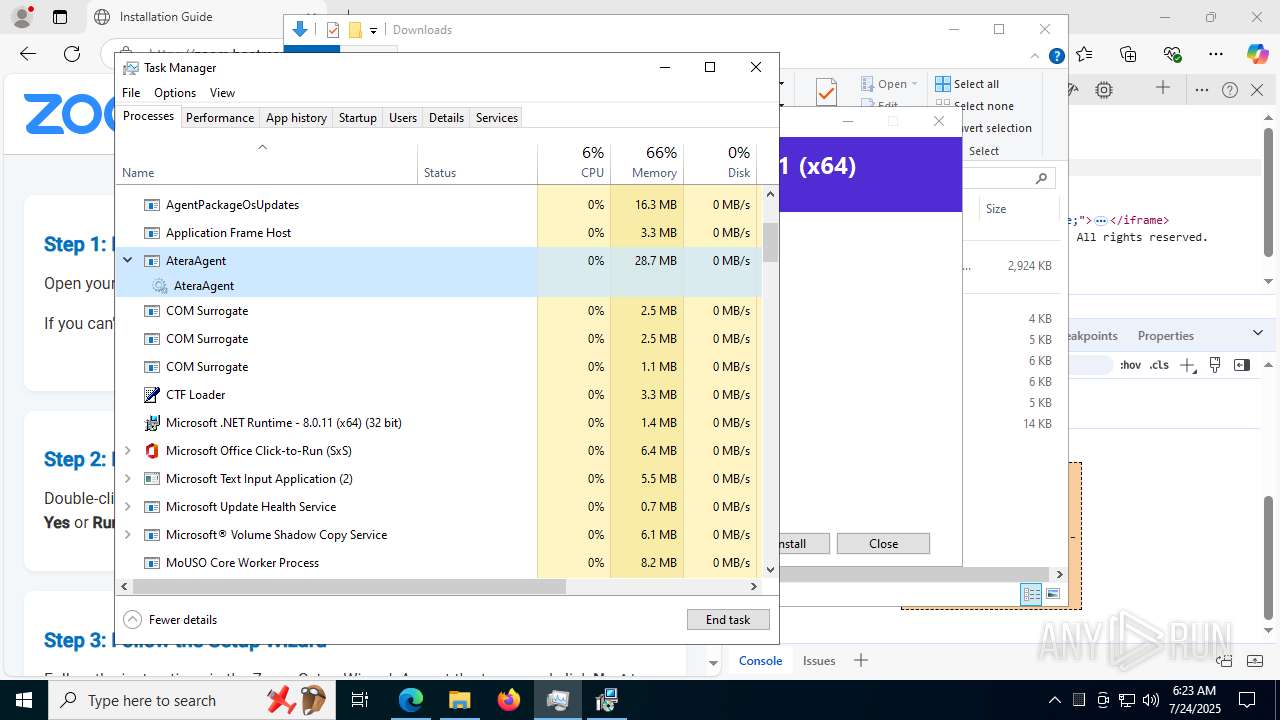
ATERA mutex has been found
- AgentPackageInternalPoller.exe (PID: 8820)
- AgentPackageMonitoring.exe (PID: 8788)
- AgentPackageInternalPoller.exe (PID: 7624)
- AgentPackageMonitoring.exe (PID: 3640)
Changes the autorun value in the registry
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
SUSPICIOUS
Process drops legitimate windows executable
- msedge.exe (PID: 6492)
- msiexec.exe (PID: 7380)
- AteraAgent.exe (PID: 5340)
- AteraAgent.exe (PID: 1040)
- AgentPackageUpgradeAgent.exe (PID: 8704)
- 8-0-11.exe (PID: 1712)
- 8-0-11.exe (PID: 7208)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
- AteraAgent.exe (PID: 3652)
- Agent.Package.Availability.exe (PID: 7648)
- AgentPackageUpgradeAgent.exe (PID: 6644)
- AgentPackageUpgradeAgent.exe (PID: 6656)
Executes as Windows Service
- VSSVC.exe (PID: 7812)
- AteraAgent.exe (PID: 5340)
- AteraAgent.exe (PID: 1040)
- SRService.exe (PID: 9084)
- AteraAgent.exe (PID: 3652)
Executable content was dropped or overwritten
- rundll32.exe (PID: 8004)
- rundll32.exe (PID: 6208)
- rundll32.exe (PID: 7172)
- rundll32.exe (PID: 3704)
- AteraAgent.exe (PID: 5340)
- SplashtopStreamer.exe (PID: 8524)
- PreVerCheck.exe (PID: 8588)
- csc.exe (PID: 8180)
- SetupUtil.exe (PID: 8860)
- AteraAgent.exe (PID: 1040)
- AgentPackageUpgradeAgent.exe (PID: 8704)
- rundll32.exe (PID: 2708)
- rundll32.exe (PID: 7756)
- AgentPackageTicketing.exe (PID: 7868)
- rundll32.exe (PID: 8528)
- csc.exe (PID: 7396)
- AgentPackageRuntimeInstaller.exe (PID: 9116)
- 8-0-11.exe (PID: 1712)
- 8-0-11.exe (PID: 7208)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
- rundll32.exe (PID: 8968)
- AteraAgent.exe (PID: 3652)
- AgentPackageTicketing.exe (PID: 4048)
- Agent.Package.Availability.exe (PID: 7648)
- csc.exe (PID: 7744)
- Agent.Package.Availability.exe (PID: 7836)
- AgentPackageUpgradeAgent.exe (PID: 6656)
- AgentPackageUpgradeAgent.exe (PID: 6644)
- rundll32.exe (PID: 2428)
- rundll32.exe (PID: 8508)
- rundll32.exe (PID: 8868)
- rundll32.exe (PID: 8632)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 8924)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7380)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 4308)
- cmd.exe (PID: 9172)
- cmd.exe (PID: 8436)
- cmd.exe (PID: 8380)
- cmd.exe (PID: 8748)
- cmd.exe (PID: 7188)
- cmd.exe (PID: 7468)
- cmd.exe (PID: 2588)
- cmd.exe (PID: 8868)
- cmd.exe (PID: 9028)
- cmd.exe (PID: 9112)
- msiexec.exe (PID: 8684)
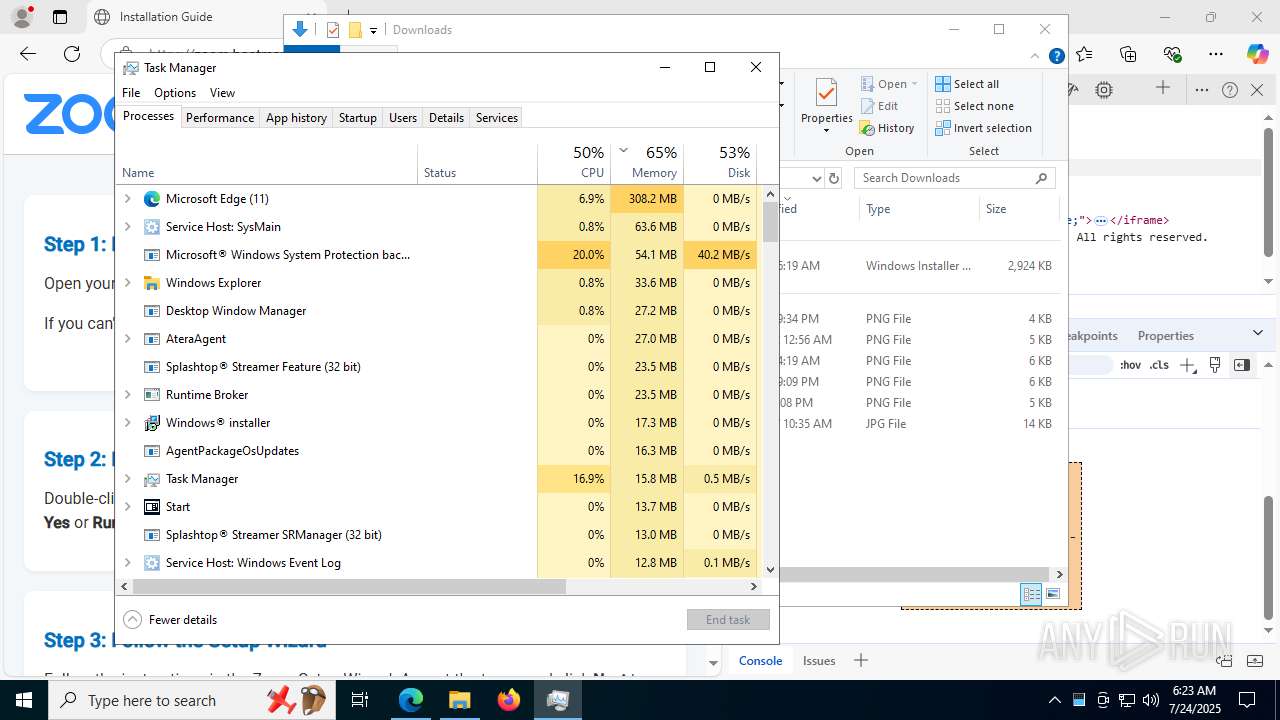
ATERAAGENT has been detected
- AteraAgent.exe (PID: 2976)
- AteraAgent.exe (PID: 5340)
- AteraAgent.exe (PID: 1040)
- AteraAgent.exe (PID: 8128)
- AteraAgent.exe (PID: 2876)
- AteraAgent.exe (PID: 3652)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 8004)
- rundll32.exe (PID: 3704)
- AteraAgent.exe (PID: 5340)
- AteraAgent.exe (PID: 1040)
- AgentPackageMonitoring.exe (PID: 6240)
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageMarketplace.exe (PID: 8008)
- rundll32.exe (PID: 2708)
- AgentPackageTicketing.exe (PID: 7868)
- AgentPackageAgentInformation.exe (PID: 9132)
- rundll32.exe (PID: 8968)
- AteraAgent.exe (PID: 3652)
- AgentPackageInternalPoller.exe (PID: 7624)
- AgentPackageSTRemote.exe (PID: 4788)
- Agent.Package.Availability.exe (PID: 7648)
- AgentPackageMonitoring.exe (PID: 3640)
- AgentPackageAgentInformation.exe (PID: 2876)
- AgentPackageUpgradeAgent.exe (PID: 8704)
- rundll32.exe (PID: 2428)
- rundll32.exe (PID: 8868)
Reads security settings of Internet Explorer
- AteraAgent.exe (PID: 2976)
- AteraAgent.exe (PID: 5340)
- AteraAgent.exe (PID: 1040)
- SplashtopStreamer.exe (PID: 8524)
- AgentPackageAgentInformation.exe (PID: 7696)
- SetupUtil.exe (PID: 8860)
- AgentPackageAgentInformation.exe (PID: 9132)
- 8-0-11.exe (PID: 7208)
- AteraAgent.exe (PID: 2876)
- AteraAgent.exe (PID: 3652)
- AgentPackageAgentInformation.exe (PID: 2876)
Reads the date of Windows installation
- AteraAgent.exe (PID: 5340)
- AteraAgent.exe (PID: 1040)
- AteraAgent.exe (PID: 3652)
Restarts service on failure
- sc.exe (PID: 7644)
- sc.exe (PID: 6460)
- sc.exe (PID: 3888)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 5340)
- AteraAgent.exe (PID: 1040)
- AteraAgent.exe (PID: 3652)
The process hides Powershell's copyright startup banner
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageAgentInformation.exe (PID: 9132)
- AgentPackageAgentInformation.exe (PID: 2876)
Starts POWERSHELL.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageAgentInformation.exe (PID: 9132)
- AgentPackageAgentInformation.exe (PID: 2876)
The process bypasses the loading of PowerShell profile settings
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageAgentInformation.exe (PID: 9132)
- AgentPackageAgentInformation.exe (PID: 2876)
The process executes Powershell scripts
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageAgentInformation.exe (PID: 9132)
- AgentPackageAgentInformation.exe (PID: 2876)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 8672)
- AgentPackageAgentInformation.exe (PID: 7696)
- SetupUtil.exe (PID: 8860)
- AgentPackageRuntimeInstaller.exe (PID: 9116)
- AgentPackageAgentInformation.exe (PID: 9132)
- AgentPackageRuntimeInstaller.exe (PID: 7316)
- AgentPackageAgentInformation.exe (PID: 2876)
CSC.EXE is used to compile C# code
- csc.exe (PID: 8180)
- csc.exe (PID: 7396)
- csc.exe (PID: 7744)
The process executes VB scripts
- cmd.exe (PID: 9136)
- cmd.exe (PID: 5032)
- cmd.exe (PID: 7460)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 9180)
- cscript.exe (PID: 2460)
- cscript.exe (PID: 8888)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 9180)
- cscript.exe (PID: 2460)
- cscript.exe (PID: 8888)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- cscript.exe (PID: 9180)
- cscript.exe (PID: 2460)
- cscript.exe (PID: 8888)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 9180)
- cscript.exe (PID: 2460)
- cscript.exe (PID: 8888)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 9180)
- cscript.exe (PID: 2460)
- cscript.exe (PID: 8888)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 9180)
- cscript.exe (PID: 2460)
- cscript.exe (PID: 8888)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 9180)
- cscript.exe (PID: 2460)
- cscript.exe (PID: 8888)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 9180)
- cscript.exe (PID: 2460)
- cscript.exe (PID: 8888)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 9180)
- cscript.exe (PID: 2460)
- cscript.exe (PID: 8888)
Searches for installed software
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageAgentInformation.exe (PID: 9132)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
- 8-0-11.exe (PID: 7208)
- Agent.Package.Software.exe (PID: 8932)
- AgentPackageAgentInformation.exe (PID: 2876)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 6940)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 8924)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 7380)
The process creates files with name similar to system file names
- msiexec.exe (PID: 7380)
- AteraAgent.exe (PID: 1040)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 8672)
- SRService.exe (PID: 8560)
Starts a Microsoft application from unusual location
- 8-0-11.exe (PID: 7208)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
Starts itself from another location
- 8-0-11.exe (PID: 7208)
- Agent.Package.Availability.exe (PID: 7648)
- AgentPackageUpgradeAgent.exe (PID: 6656)
Creates a software uninstall entry
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
Connects to unusual port
- Agent.Package.Availability.exe (PID: 7648)
- Agent.Package.Availability.exe (PID: 7836)
Application launched itself
- dotnet-runtime-8.0.11-win-x64.exe (PID: 6940)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 6656)
INFO
Checks supported languages
- identity_helper.exe (PID: 7852)
- msiexec.exe (PID: 7380)
- msiexec.exe (PID: 3644)
- AteraAgent.exe (PID: 2976)
- msiexec.exe (PID: 4308)
- AteraAgent.exe (PID: 5340)
- AgentPackageAgentInformation.exe (PID: 7904)
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageAgentInformation.exe (PID: 6868)
- AgentPackageSTRemote.exe (PID: 2280)
- AteraAgent.exe (PID: 1040)
- AgentPackageAgentInformation.exe (PID: 4884)
- AgentPackageMonitoring.exe (PID: 6240)
- SplashtopStreamer.exe (PID: 8524)
- PreVerCheck.exe (PID: 8588)
- msiexec.exe (PID: 8672)
- _is43E0.exe (PID: 8760)
- _is43E0.exe (PID: 8800)
- _is43E0.exe (PID: 8840)
- _is43E0.exe (PID: 8880)
- _is43E0.exe (PID: 8920)
- _is43E0.exe (PID: 8968)
- _is43E0.exe (PID: 9004)
- _is43E0.exe (PID: 9044)
- _is43E0.exe (PID: 9124)
- cvtres.exe (PID: 1244)
- csc.exe (PID: 8180)
- _is43E0.exe (PID: 9084)
- _is4DB5.exe (PID: 8388)
- _is4DB5.exe (PID: 2460)
- _is4DB5.exe (PID: 7472)
- _is4DB5.exe (PID: 8828)
- _is4DB5.exe (PID: 7452)
- _is4DB5.exe (PID: 8632)
- _is4DB5.exe (PID: 2464)
- _is4DB5.exe (PID: 8824)
- _is4DB5.exe (PID: 8560)
- _is712C.exe (PID: 9016)
- _is712C.exe (PID: 8288)
- _is4DB5.exe (PID: 8876)
- _is712C.exe (PID: 8428)
- _is712C.exe (PID: 8980)
- _is712C.exe (PID: 4884)
- _is712C.exe (PID: 8564)
- _is712C.exe (PID: 7496)
- SetupUtil.exe (PID: 7452)
- _is712C.exe (PID: 5348)
- _is712C.exe (PID: 6544)
- _is712C.exe (PID: 6012)
- SetupUtil.exe (PID: 8860)
- SetupUtil.exe (PID: 8800)
- _is8429.exe (PID: 5764)
- _is8429.exe (PID: 9072)
- _is8429.exe (PID: 868)
- _is8429.exe (PID: 8196)
- _is8429.exe (PID: 9140)
- _is8429.exe (PID: 7368)
- SRSelfSignCertUtil.exe (PID: 7196)
- _is8429.exe (PID: 8732)
- _is8429.exe (PID: 6544)
- _is8429.exe (PID: 7448)
- _is87A5.exe (PID: 7456)
- SRService.exe (PID: 8560)
- _is87A5.exe (PID: 8948)
- _is8429.exe (PID: 8440)
- _is87A5.exe (PID: 2992)
- _is87A5.exe (PID: 8936)
- _is87A5.exe (PID: 7548)
- _is87A5.exe (PID: 8820)
- _is87A5.exe (PID: 8456)
- _is87A5.exe (PID: 8968)
- _is87A5.exe (PID: 9180)
- _is87A5.exe (PID: 2328)
- SRService.exe (PID: 7020)
- SRManager.exe (PID: 8364)
- SRServer.exe (PID: 8440)
- SRService.exe (PID: 9084)
- SRAppPB.exe (PID: 7244)
- SRFeature.exe (PID: 4024)
- SRAgent.exe (PID: 436)
- SRUtility.exe (PID: 8008)
- BdEpSDK.exe (PID: 1028)
- AgentPackageMonitoring.exe (PID: 8788)
- AgentPackageInternalPoller.exe (PID: 8820)
- AgentPackageRuntimeInstaller.exe (PID: 9116)
- AgentPackageHeartbeat.exe (PID: 7080)
- AgentPackageADRemote.exe (PID: 8644)
- AgentPackageMarketplace.exe (PID: 8008)
- AgentPackageSystemTools.exe (PID: 2460)
- AgentPackageUpgradeAgent.exe (PID: 8704)
- AgentPackageTicketing.exe (PID: 7868)
- Agent.Package.Watchdog.exe (PID: 8496)
- Agent.Package.Software.exe (PID: 9076)
- Agent.Package.Availability.exe (PID: 6140)
- AgentPackageOsUpdates.exe (PID: 8676)
- msiexec.exe (PID: 8684)
- cvtres.exe (PID: 4032)
- csc.exe (PID: 7396)
- AteraAgent.exe (PID: 8128)
- 8-0-11.exe (PID: 1712)
- 8-0-11.exe (PID: 7208)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
- AteraAgent.exe (PID: 2876)
- AgentPackageAgentInformation.exe (PID: 9132)
- msiexec.exe (PID: 4448)
- AteraAgent.exe (PID: 3652)
- lockscreen.ext.exe (PID: 8916)
- wifiNetwork.ext.exe (PID: 1288)
- msiexec.exe (PID: 1352)
- msiexec.exe (PID: 8644)
- dotnet.exe (PID: 2120)
- osqueryi.exe (PID: 8340)
- AgentPackageInternalPoller.exe (PID: 7624)
- dotnet.exe (PID: 7084)
- AgentPackageHeartbeat.exe (PID: 4948)
- Agent.Package.Availability.exe (PID: 7648)
- AgentPackageAgentInformation.exe (PID: 2876)
- AgentPackageSTRemote.exe (PID: 4788)
- AgentPackageSystemTools.exe (PID: 1268)
- AgentPackageRuntimeInstaller.exe (PID: 7316)
- AgentPackageMarketplace.exe (PID: 1096)
- Agent.Package.Watchdog.exe (PID: 888)
- AgentPackageMonitoring.exe (PID: 3640)
- AgentPackageADRemote.exe (PID: 1508)
- Agent.Package.Software.exe (PID: 8932)
- AgentPackageTicketing.exe (PID: 4048)
- SRUtility.exe (PID: 5032)
- dotnet.exe (PID: 6332)
- Agent.Package.Availability.exe (PID: 7836)
- csc.exe (PID: 7744)
- cvtres.exe (PID: 8096)
- SRVirtualDisplay.exe (PID: 6736)
- AgentPackageUpgradeAgent.exe (PID: 6656)
- AgentPackageHeartbeat.exe (PID: 4032)
- msiexec.exe (PID: 7392)
- AgentPackageUpgradeAgent.exe (PID: 6644)
- AgentPackageTicketing.exe (PID: 8032)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 6940)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 6656)
- AgentPackageHeartbeat.exe (PID: 9096)
- AgentPackageMonitoring.exe (PID: 7980)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 8924)
- AgentPackageTicketing.exe (PID: 8528)
- AgentPackageInternalPoller.exe (PID: 9096)
- AgentPackageHeartbeat.exe (PID: 4984)
- Agent.Package.Watchdog.exe (PID: 7256)
Reads Environment values
- identity_helper.exe (PID: 7852)
- AteraAgent.exe (PID: 2976)
- AteraAgent.exe (PID: 5340)
- AgentPackageAgentInformation.exe (PID: 7904)
- AgentPackageAgentInformation.exe (PID: 6868)
- AgentPackageAgentInformation.exe (PID: 4884)
- AgentPackageSTRemote.exe (PID: 2280)
- AteraAgent.exe (PID: 1040)
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageMonitoring.exe (PID: 6240)
- AgentPackageMonitoring.exe (PID: 8788)
- AgentPackageAgentInformation.exe (PID: 9132)
- AgentPackageInternalPoller.exe (PID: 8820)
- AgentPackageHeartbeat.exe (PID: 7080)
- AgentPackageUpgradeAgent.exe (PID: 8704)
- AgentPackageRuntimeInstaller.exe (PID: 9116)
- AgentPackageADRemote.exe (PID: 8644)
- AgentPackageSystemTools.exe (PID: 2460)
- AgentPackageMarketplace.exe (PID: 8008)
- AgentPackageTicketing.exe (PID: 7868)
- AgentPackageOsUpdates.exe (PID: 8676)
- AteraAgent.exe (PID: 8128)
- AteraAgent.exe (PID: 2876)
- AteraAgent.exe (PID: 3652)
- AgentPackageHeartbeat.exe (PID: 4948)
- AgentPackageInternalPoller.exe (PID: 7624)
- AgentPackageAgentInformation.exe (PID: 2876)
- AgentPackageSTRemote.exe (PID: 4788)
- AgentPackageADRemote.exe (PID: 1508)
- AgentPackageMonitoring.exe (PID: 3640)
- AgentPackageRuntimeInstaller.exe (PID: 7316)
- AgentPackageSystemTools.exe (PID: 1268)
- AgentPackageTicketing.exe (PID: 4048)
- AgentPackageMarketplace.exe (PID: 1096)
- SRManager.exe (PID: 8364)
- AgentPackageHeartbeat.exe (PID: 4032)
- AgentPackageUpgradeAgent.exe (PID: 6656)
- AgentPackageUpgradeAgent.exe (PID: 6644)
- AgentPackageTicketing.exe (PID: 8032)
- AgentPackageHeartbeat.exe (PID: 9096)
- AgentPackageMonitoring.exe (PID: 7980)
- AgentPackageHeartbeat.exe (PID: 4984)
- AgentPackageTicketing.exe (PID: 8528)
- AgentPackageInternalPoller.exe (PID: 9096)
Reads the computer name
- identity_helper.exe (PID: 7852)
- msiexec.exe (PID: 7380)
- msiexec.exe (PID: 3644)
- AteraAgent.exe (PID: 2976)
- msiexec.exe (PID: 4308)
- AteraAgent.exe (PID: 5340)
- AgentPackageAgentInformation.exe (PID: 6868)
- AgentPackageAgentInformation.exe (PID: 7904)
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageAgentInformation.exe (PID: 4884)
- AgentPackageSTRemote.exe (PID: 2280)
- AteraAgent.exe (PID: 1040)
- AgentPackageMonitoring.exe (PID: 6240)
- SplashtopStreamer.exe (PID: 8524)
- msiexec.exe (PID: 8672)
- _is43E0.exe (PID: 8760)
- _is43E0.exe (PID: 8800)
- _is43E0.exe (PID: 8840)
- _is43E0.exe (PID: 8968)
- _is43E0.exe (PID: 9004)
- _is43E0.exe (PID: 9044)
- _is43E0.exe (PID: 8920)
- _is43E0.exe (PID: 9084)
- _is43E0.exe (PID: 9124)
- _is4DB5.exe (PID: 8560)
- _is4DB5.exe (PID: 8632)
- _is4DB5.exe (PID: 2460)
- _is4DB5.exe (PID: 7472)
- _is4DB5.exe (PID: 8828)
- _is4DB5.exe (PID: 2464)
- _is4DB5.exe (PID: 8824)
- _is4DB5.exe (PID: 8388)
- _is4DB5.exe (PID: 7452)
- _is712C.exe (PID: 9016)
- _is4DB5.exe (PID: 8876)
- _is712C.exe (PID: 8428)
- _is712C.exe (PID: 6544)
- _is712C.exe (PID: 4884)
- _is712C.exe (PID: 6012)
- _is712C.exe (PID: 8564)
- _is712C.exe (PID: 7496)
- _is712C.exe (PID: 8288)
- _is712C.exe (PID: 5348)
- _is712C.exe (PID: 8980)
- SetupUtil.exe (PID: 8860)
- _is43E0.exe (PID: 8880)
- _is8429.exe (PID: 5764)
- _is8429.exe (PID: 9072)
- _is8429.exe (PID: 868)
- _is8429.exe (PID: 8196)
- _is8429.exe (PID: 9140)
- SRSelfSignCertUtil.exe (PID: 7196)
- _is8429.exe (PID: 6544)
- _is8429.exe (PID: 7448)
- _is8429.exe (PID: 8732)
- SRService.exe (PID: 8560)
- _is87A5.exe (PID: 7456)
- _is87A5.exe (PID: 8948)
- _is8429.exe (PID: 7368)
- _is8429.exe (PID: 8440)
- _is87A5.exe (PID: 8936)
- _is87A5.exe (PID: 8456)
- _is87A5.exe (PID: 8820)
- _is87A5.exe (PID: 2992)
- _is87A5.exe (PID: 2328)
- _is87A5.exe (PID: 8968)
- _is87A5.exe (PID: 9180)
- _is87A5.exe (PID: 7548)
- SRServer.exe (PID: 8440)
- SRService.exe (PID: 7020)
- SRService.exe (PID: 9084)
- SRAppPB.exe (PID: 7244)
- SRFeature.exe (PID: 4024)
- SRAgent.exe (PID: 436)
- SRManager.exe (PID: 8364)
- AgentPackageMonitoring.exe (PID: 8788)
- AgentPackageInternalPoller.exe (PID: 8820)
- AgentPackageUpgradeAgent.exe (PID: 8704)
- AgentPackageRuntimeInstaller.exe (PID: 9116)
- AgentPackageHeartbeat.exe (PID: 7080)
- AgentPackageADRemote.exe (PID: 8644)
- AgentPackageSystemTools.exe (PID: 2460)
- AgentPackageMarketplace.exe (PID: 8008)
- AgentPackageTicketing.exe (PID: 7868)
- Agent.Package.Watchdog.exe (PID: 8496)
- Agent.Package.Software.exe (PID: 9076)
- Agent.Package.Availability.exe (PID: 6140)
- AgentPackageOsUpdates.exe (PID: 8676)
- msiexec.exe (PID: 8684)
- AteraAgent.exe (PID: 8128)
- 8-0-11.exe (PID: 1712)
- 8-0-11.exe (PID: 7208)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
- AgentPackageAgentInformation.exe (PID: 9132)
- AteraAgent.exe (PID: 2876)
- AteraAgent.exe (PID: 3652)
- osqueryi.exe (PID: 8340)
- lockscreen.ext.exe (PID: 8916)
- wifiNetwork.ext.exe (PID: 1288)
- msiexec.exe (PID: 1352)
- msiexec.exe (PID: 4448)
- msiexec.exe (PID: 8644)
- AgentPackageInternalPoller.exe (PID: 7624)
- AgentPackageHeartbeat.exe (PID: 4948)
- AgentPackageSTRemote.exe (PID: 4788)
- AgentPackageAgentInformation.exe (PID: 2876)
- AgentPackageSystemTools.exe (PID: 1268)
- AgentPackageADRemote.exe (PID: 1508)
- AgentPackageMonitoring.exe (PID: 3640)
- Agent.Package.Availability.exe (PID: 7648)
- AgentPackageRuntimeInstaller.exe (PID: 7316)
- AgentPackageMarketplace.exe (PID: 1096)
- AgentPackageTicketing.exe (PID: 4048)
- Agent.Package.Watchdog.exe (PID: 888)
- Agent.Package.Software.exe (PID: 8932)
- Agent.Package.Availability.exe (PID: 7836)
- AgentPackageUpgradeAgent.exe (PID: 6656)
- SRVirtualDisplay.exe (PID: 6736)
- AgentPackageHeartbeat.exe (PID: 4032)
- msiexec.exe (PID: 7392)
- AgentPackageUpgradeAgent.exe (PID: 6644)
- AgentPackageTicketing.exe (PID: 8032)
- AgentPackageHeartbeat.exe (PID: 9096)
- AgentPackageMonitoring.exe (PID: 7980)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 8924)
- AgentPackageTicketing.exe (PID: 8528)
- AgentPackageHeartbeat.exe (PID: 4984)
- AgentPackageInternalPoller.exe (PID: 9096)
- Agent.Package.Watchdog.exe (PID: 7256)
Application launched itself
- msedge.exe (PID: 6492)
Executable content was dropped or overwritten
- msedge.exe (PID: 6492)
- msiexec.exe (PID: 7380)
- msiexec.exe (PID: 8672)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 4884)
- Taskmgr.exe (PID: 3608)
- msiexec.exe (PID: 7316)
- Taskmgr.exe (PID: 7884)
- OpenWith.exe (PID: 7208)
- notepad.exe (PID: 8788)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6492)
- OpenWith.exe (PID: 7208)
Reads the software policy settings
- msiexec.exe (PID: 4884)
- rundll32.exe (PID: 8004)
- msiexec.exe (PID: 7380)
- AteraAgent.exe (PID: 5340)
- AteraAgent.exe (PID: 2976)
- rundll32.exe (PID: 3704)
- AgentPackageAgentInformation.exe (PID: 6868)
- AgentPackageAgentInformation.exe (PID: 7904)
- AgentPackageSTRemote.exe (PID: 2280)
- AteraAgent.exe (PID: 1040)
- AgentPackageMonitoring.exe (PID: 6240)
- msiexec.exe (PID: 8672)
- cscript.exe (PID: 9180)
- AgentPackageAgentInformation.exe (PID: 7696)
- slui.exe (PID: 6980)
- SRManager.exe (PID: 8364)
- AgentPackageHeartbeat.exe (PID: 7080)
- AgentPackageMarketplace.exe (PID: 8008)
- AgentPackageADRemote.exe (PID: 8644)
- AgentPackageRuntimeInstaller.exe (PID: 9116)
- AgentPackageInternalPoller.exe (PID: 8820)
- AgentPackageUpgradeAgent.exe (PID: 8704)
- rundll32.exe (PID: 2708)
- AgentPackageTicketing.exe (PID: 7868)
- cscript.exe (PID: 2460)
- AgentPackageAgentInformation.exe (PID: 9132)
- AgentPackageMonitoring.exe (PID: 8788)
- AteraAgent.exe (PID: 2876)
- rundll32.exe (PID: 8968)
- AgentPackageInternalPoller.exe (PID: 7624)
- AteraAgent.exe (PID: 3652)
- AgentPackageHeartbeat.exe (PID: 4948)
- AgentPackageSTRemote.exe (PID: 4788)
- AgentPackageMarketplace.exe (PID: 1096)
- AgentPackageRuntimeInstaller.exe (PID: 7316)
- Agent.Package.Availability.exe (PID: 7648)
- Agent.Package.Software.exe (PID: 8932)
- AgentPackageTicketing.exe (PID: 4048)
- Agent.Package.Availability.exe (PID: 7836)
- cscript.exe (PID: 8888)
- AgentPackageMonitoring.exe (PID: 3640)
- AgentPackageAgentInformation.exe (PID: 2876)
- AgentPackageHeartbeat.exe (PID: 4032)
- msiexec.exe (PID: 7316)
- rundll32.exe (PID: 2428)
- rundll32.exe (PID: 8868)
- AgentPackageHeartbeat.exe (PID: 9096)
- AgentPackageHeartbeat.exe (PID: 4984)
Create files in a temporary directory
- rundll32.exe (PID: 6208)
- rundll32.exe (PID: 8004)
- rundll32.exe (PID: 7172)
- rundll32.exe (PID: 3704)
- rundll32.exe (PID: 8508)
- rundll32.exe (PID: 8868)
- rundll32.exe (PID: 8632)
- rundll32.exe (PID: 2428)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 8924)
- Taskmgr.exe (PID: 7884)
The sample compiled with english language support
- rundll32.exe (PID: 8004)
- rundll32.exe (PID: 6208)
- rundll32.exe (PID: 7172)
- rundll32.exe (PID: 3704)
- AteraAgent.exe (PID: 5340)
- SplashtopStreamer.exe (PID: 8524)
- PreVerCheck.exe (PID: 8588)
- msiexec.exe (PID: 7380)
- msiexec.exe (PID: 8672)
- SetupUtil.exe (PID: 8860)
- AteraAgent.exe (PID: 1040)
- rundll32.exe (PID: 7756)
- rundll32.exe (PID: 2708)
- rundll32.exe (PID: 8528)
- 8-0-11.exe (PID: 1712)
- 8-0-11.exe (PID: 7208)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
- rundll32.exe (PID: 8968)
- AteraAgent.exe (PID: 3652)
- AgentPackageUpgradeAgent.exe (PID: 6656)
- rundll32.exe (PID: 2428)
- rundll32.exe (PID: 8508)
- rundll32.exe (PID: 8868)
- rundll32.exe (PID: 8632)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 8924)
Checks proxy server information
- rundll32.exe (PID: 8004)
- rundll32.exe (PID: 3704)
- slui.exe (PID: 6980)
- rundll32.exe (PID: 2428)
- rundll32.exe (PID: 8868)
Disables trace logs
- rundll32.exe (PID: 8004)
- AteraAgent.exe (PID: 5340)
- rundll32.exe (PID: 3704)
- AgentPackageAgentInformation.exe (PID: 6868)
- AgentPackageAgentInformation.exe (PID: 7904)
- AgentPackageSTRemote.exe (PID: 2280)
- AteraAgent.exe (PID: 1040)
- AgentPackageMonitoring.exe (PID: 6240)
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageHeartbeat.exe (PID: 7080)
- AgentPackageInternalPoller.exe (PID: 8820)
- AgentPackageADRemote.exe (PID: 8644)
- AgentPackageRuntimeInstaller.exe (PID: 9116)
- AgentPackageMarketplace.exe (PID: 8008)
- AgentPackageUpgradeAgent.exe (PID: 8704)
- rundll32.exe (PID: 2708)
- AgentPackageTicketing.exe (PID: 7868)
- AgentPackageAgentInformation.exe (PID: 9132)
- AgentPackageMonitoring.exe (PID: 8788)
- rundll32.exe (PID: 8968)
- AteraAgent.exe (PID: 3652)
- AgentPackageHeartbeat.exe (PID: 4948)
- AgentPackageInternalPoller.exe (PID: 7624)
- AgentPackageSTRemote.exe (PID: 4788)
- AgentPackageRuntimeInstaller.exe (PID: 7316)
- AgentPackageTicketing.exe (PID: 4048)
- AgentPackageMonitoring.exe (PID: 3640)
- AgentPackageAgentInformation.exe (PID: 2876)
- AgentPackageHeartbeat.exe (PID: 4032)
- rundll32.exe (PID: 2428)
- rundll32.exe (PID: 8868)
- AgentPackageHeartbeat.exe (PID: 9096)
- AgentPackageHeartbeat.exe (PID: 4984)
- AgentPackageMarketplace.exe (PID: 1096)
Manages system restore points
- SrTasks.exe (PID: 7000)
- SrTasks.exe (PID: 8512)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7380)
- AteraAgent.exe (PID: 2976)
- AteraAgent.exe (PID: 5340)
- AgentPackageAgentInformation.exe (PID: 7904)
- AgentPackageAgentInformation.exe (PID: 6868)
- AgentPackageAgentInformation.exe (PID: 7696)
- AgentPackageAgentInformation.exe (PID: 4884)
- AgentPackageSTRemote.exe (PID: 2280)
- AteraAgent.exe (PID: 1040)
- AgentPackageMonitoring.exe (PID: 6240)
- msiexec.exe (PID: 8672)
- csc.exe (PID: 8180)
- SRSelfSignCertUtil.exe (PID: 7196)
- SRManager.exe (PID: 8364)
- AgentPackageAgentInformation.exe (PID: 9132)
- AgentPackageMonitoring.exe (PID: 8788)
- AgentPackageHeartbeat.exe (PID: 7080)
- AgentPackageRuntimeInstaller.exe (PID: 9116)
- AgentPackageADRemote.exe (PID: 8644)
- AgentPackageSystemTools.exe (PID: 2460)
- AgentPackageInternalPoller.exe (PID: 8820)
- AgentPackageUpgradeAgent.exe (PID: 8704)
- AgentPackageMarketplace.exe (PID: 8008)
- AgentPackageTicketing.exe (PID: 7868)
- AgentPackageOsUpdates.exe (PID: 8676)
- csc.exe (PID: 7396)
- AteraAgent.exe (PID: 8128)
- AteraAgent.exe (PID: 2876)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
- AteraAgent.exe (PID: 3652)
- AgentPackageHeartbeat.exe (PID: 4948)
- AgentPackageInternalPoller.exe (PID: 7624)
- AgentPackageSTRemote.exe (PID: 4788)
- AgentPackageSystemTools.exe (PID: 1268)
- AgentPackageAgentInformation.exe (PID: 2876)
- AgentPackageRuntimeInstaller.exe (PID: 7316)
- AgentPackageADRemote.exe (PID: 1508)
- AgentPackageMarketplace.exe (PID: 1096)
- AgentPackageMonitoring.exe (PID: 3640)
- Agent.Package.Availability.exe (PID: 7648)
- AgentPackageTicketing.exe (PID: 4048)
- Agent.Package.Availability.exe (PID: 7836)
- csc.exe (PID: 7744)
- AgentPackageHeartbeat.exe (PID: 4032)
- AgentPackageUpgradeAgent.exe (PID: 6656)
- AgentPackageUpgradeAgent.exe (PID: 6644)
- AgentPackageTicketing.exe (PID: 8032)
- AgentPackageMonitoring.exe (PID: 7980)
- AgentPackageHeartbeat.exe (PID: 9096)
- AgentPackageHeartbeat.exe (PID: 4984)
- AgentPackageTicketing.exe (PID: 8528)
- AgentPackageInternalPoller.exe (PID: 9096)
Creates a software uninstall entry
- msiexec.exe (PID: 7380)
Creates files in the program directory
- AteraAgent.exe (PID: 2976)
- AteraAgent.exe (PID: 5340)
- AgentPackageSTRemote.exe (PID: 2280)
- AgentPackageMonitoring.exe (PID: 6240)
- AgentPackageAgentInformation.exe (PID: 7696)
- SetupUtil.exe (PID: 8860)
- SRSelfSignCertUtil.exe (PID: 7196)
- SRService.exe (PID: 8560)
- SRManager.exe (PID: 8364)
- SRAgent.exe (PID: 436)
- AteraAgent.exe (PID: 1040)
- AgentPackageInternalPoller.exe (PID: 8820)
- AgentPackageRuntimeInstaller.exe (PID: 9116)
- AgentPackageSystemTools.exe (PID: 2460)
- AgentPackageUpgradeAgent.exe (PID: 8704)
- AgentPackageMonitoring.exe (PID: 8788)
- AgentPackageTicketing.exe (PID: 7868)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
- AteraAgent.exe (PID: 2876)
- AgentPackageInternalPoller.exe (PID: 7624)
- AteraAgent.exe (PID: 3652)
- Agent.Package.Availability.exe (PID: 7648)
- Agent.Package.Watchdog.exe (PID: 888)
- Agent.Package.Software.exe (PID: 8932)
- AgentPackageMonitoring.exe (PID: 3640)
- AgentPackageRuntimeInstaller.exe (PID: 7316)
- AgentPackageTicketing.exe (PID: 4048)
- AgentPackageAgentInformation.exe (PID: 2876)
- SRVirtualDisplay.exe (PID: 6736)
- AgentPackageMonitoring.exe (PID: 7980)
SPLASHTOP has been detected
- AgentPackageSTRemote.exe (PID: 2280)
- msiexec.exe (PID: 7380)
- SetupUtil.exe (PID: 7452)
- msiexec.exe (PID: 8672)
- msiexec.exe (PID: 8672)
- SetupUtil.exe (PID: 7452)
- SetupUtil.exe (PID: 8800)
- SetupUtil.exe (PID: 8800)
- SetupUtil.exe (PID: 8860)
- cmd.exe (PID: 8912)
- conhost.exe (PID: 8760)
- cmd.exe (PID: 7464)
- conhost.exe (PID: 7420)
- SRSelfSignCertUtil.exe (PID: 7196)
- conhost.exe (PID: 8564)
- SRService.exe (PID: 8560)
- conhost.exe (PID: 1652)
- SRService.exe (PID: 9084)
- SRManager.exe (PID: 8364)
- SRManager.exe (PID: 8364)
- SRService.exe (PID: 9084)
- SRServer.exe (PID: 8440)
- PreVerCheck.exe (PID: 8588)
- SRService.exe (PID: 7020)
- SRAppPB.exe (PID: 7244)
- SRUtility.exe (PID: 8008)
- SRAgent.exe (PID: 436)
- SRFeature.exe (PID: 4024)
- SRFeature.exe (PID: 4024)
- conhost.exe (PID: 6532)
- SRAgent.exe (PID: 436)
- SRAppPB.exe (PID: 7244)
- BdEpSDK.exe (PID: 1028)
- SRUtility.exe (PID: 8008)
- SRServer.exe (PID: 8440)
- conhost.exe (PID: 8832)
- AgentPackageSTRemote.exe (PID: 2280)
- AgentPackageAgentInformation.exe (PID: 9132)
- Taskmgr.exe (PID: 3608)
- conhost.exe (PID: 5652)
- lockscreen.ext.exe (PID: 8916)
- wifiNetwork.ext.exe (PID: 1288)
- osqueryi.exe (PID: 8340)
- AgentPackageSTRemote.exe (PID: 4788)
- conhost.exe (PID: 7996)
- SRUtility.exe (PID: 5032)
- AgentPackageSTRemote.exe (PID: 4788)
- SRUtility.exe (PID: 5032)
- AgentPackageAgentInformation.exe (PID: 2876)
- SRVirtualDisplay.exe (PID: 6736)
- SRVirtualDisplay.exe (PID: 6736)
- Taskmgr.exe (PID: 7884)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7932)
- powershell.exe (PID: 1704)
- powershell.exe (PID: 3620)
The sample compiled with chinese language support
- msiexec.exe (PID: 7380)
Manual execution by a user
- Taskmgr.exe (PID: 7184)
- Taskmgr.exe (PID: 3608)
- msiexec.exe (PID: 7316)
- Taskmgr.exe (PID: 7884)
- Taskmgr.exe (PID: 5340)
- dotnet-runtime-8.0.11-win-x64.exe (PID: 6940)
Launching a file from a Registry key
- dotnet-runtime-8.0.11-win-x64.exe (PID: 2328)
Process checks computer location settings
- Agent.Package.Software.exe (PID: 8932)
- Agent.Package.Watchdog.exe (PID: 888)
- Agent.Package.Watchdog.exe (PID: 7256)
Reads product name
- SRManager.exe (PID: 8364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
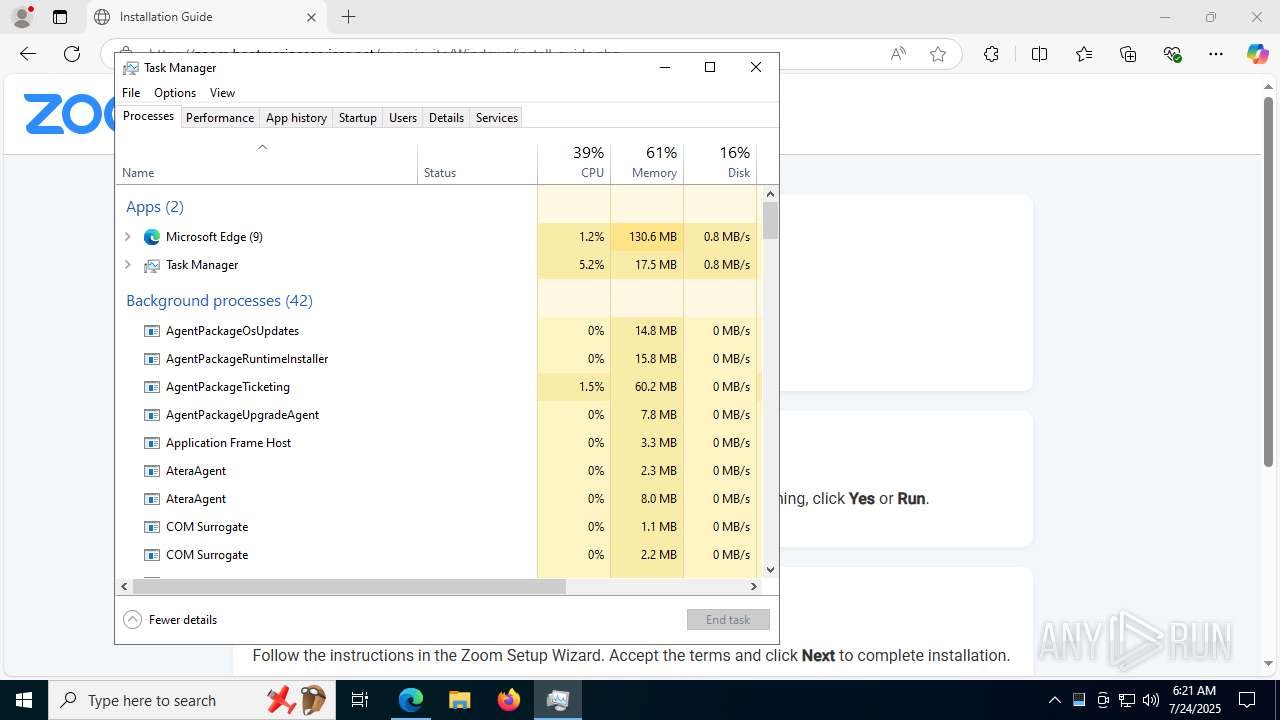
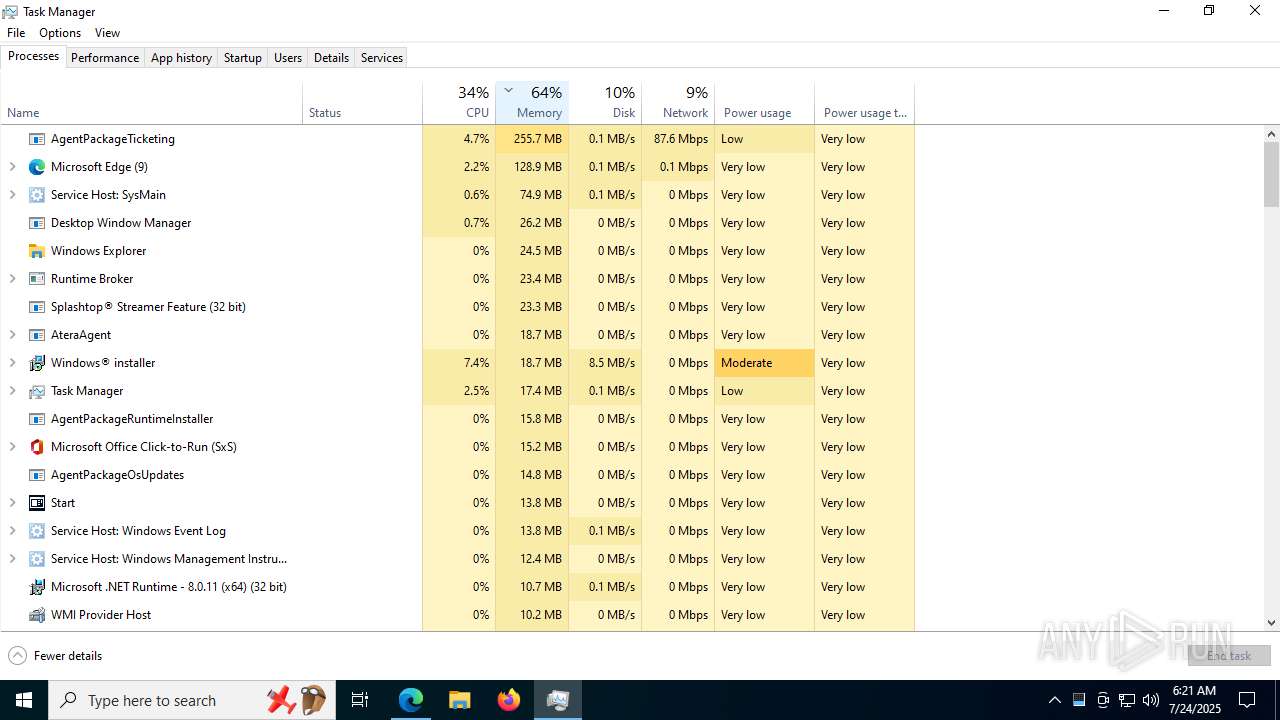
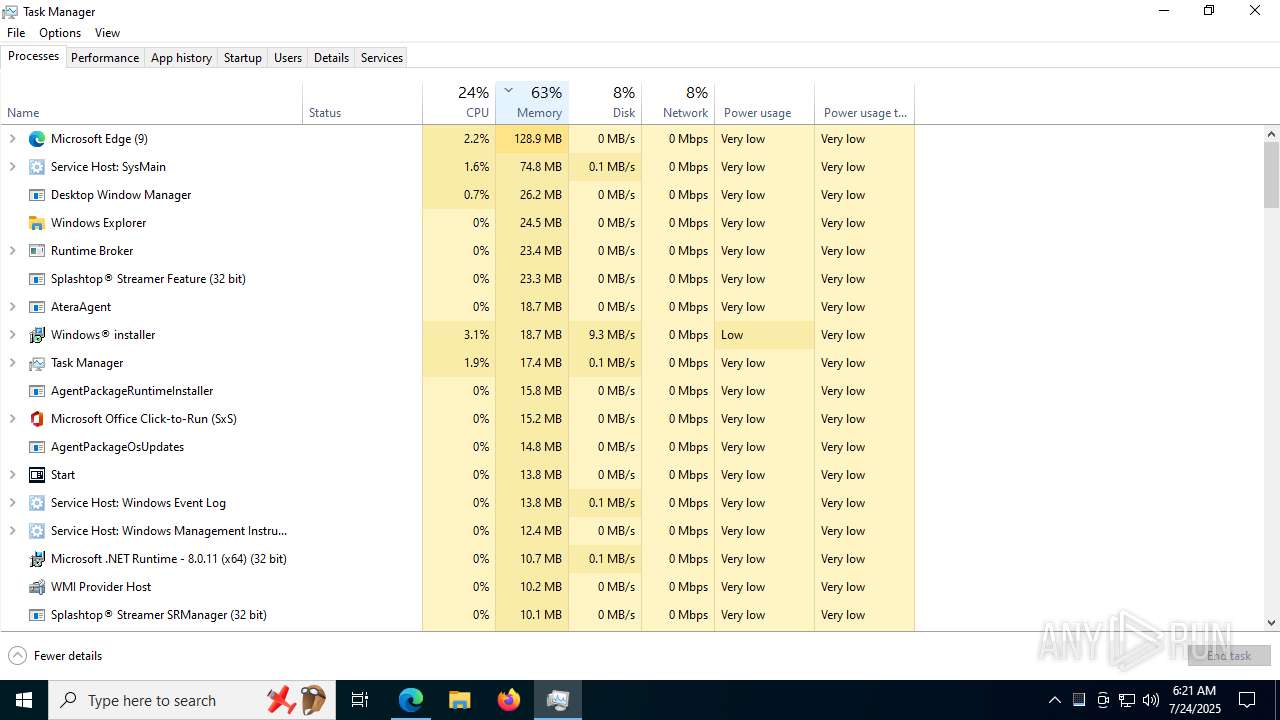
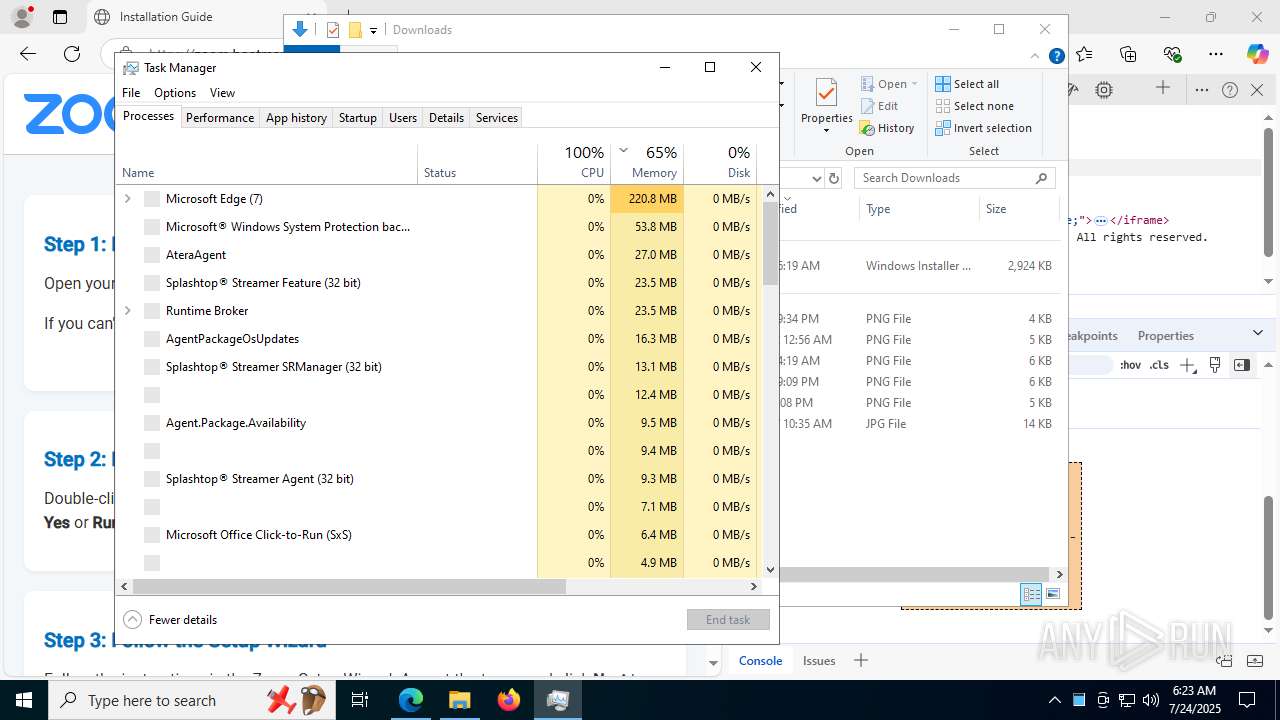
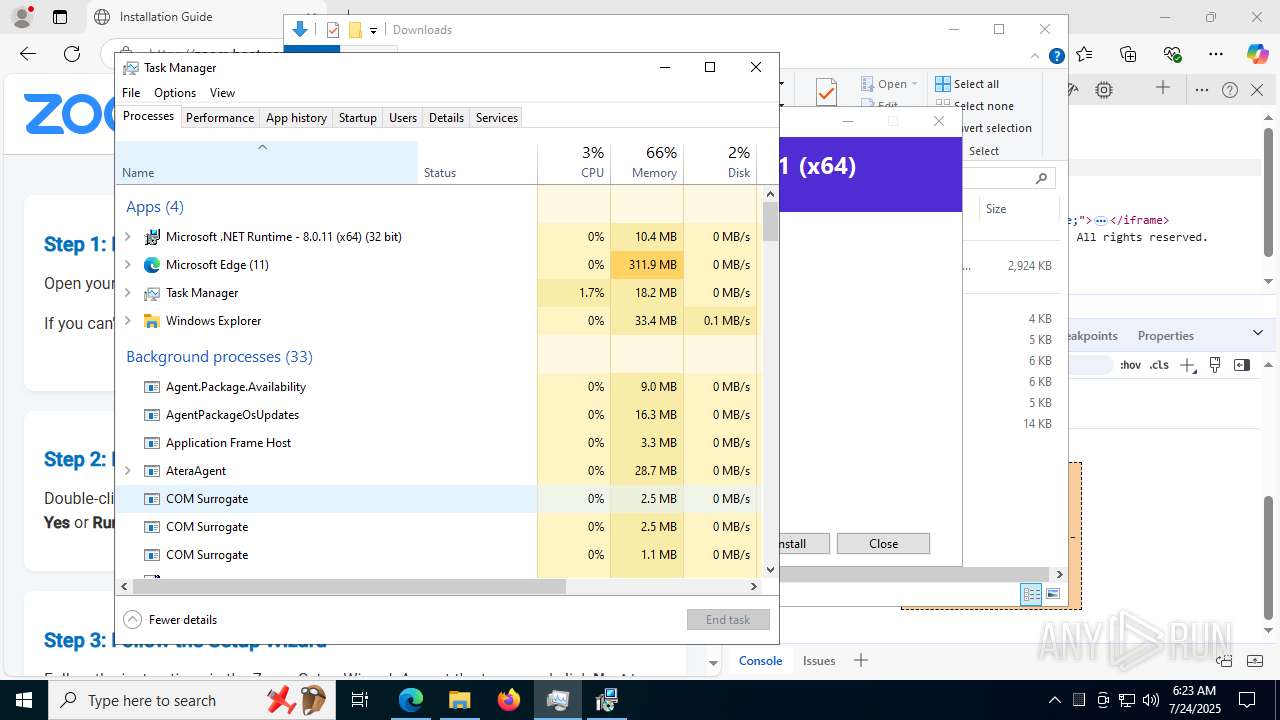
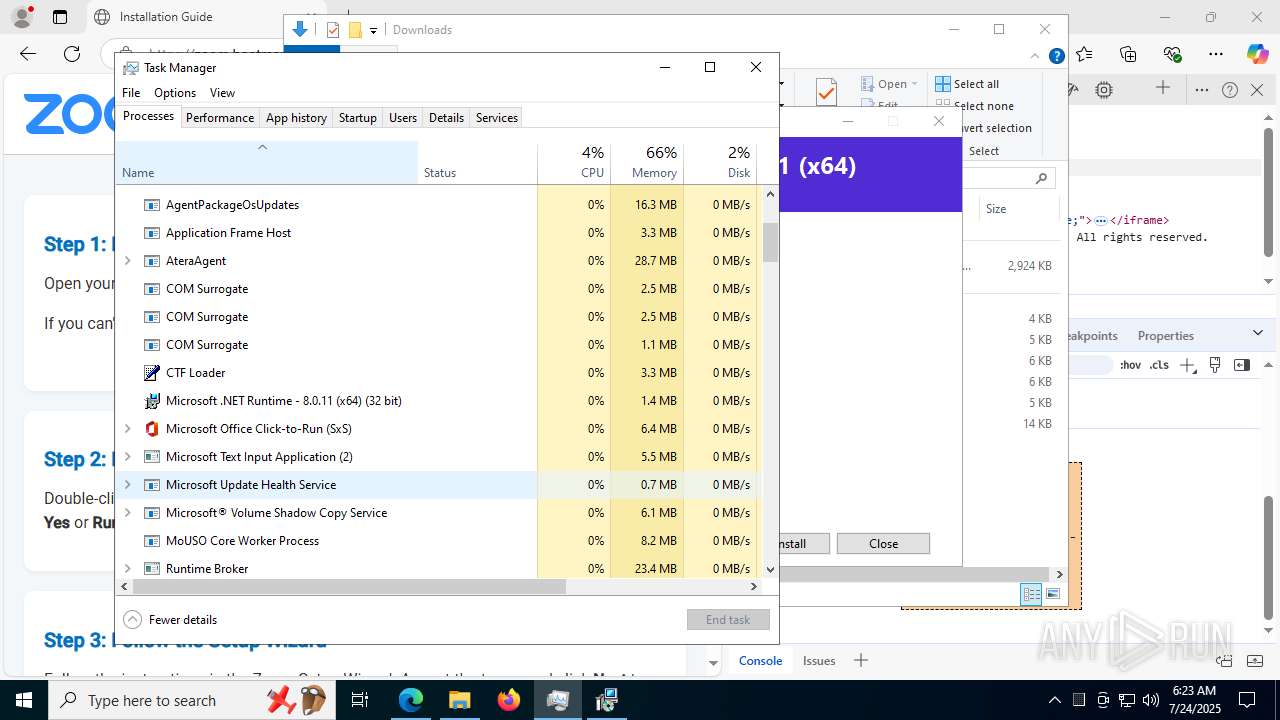
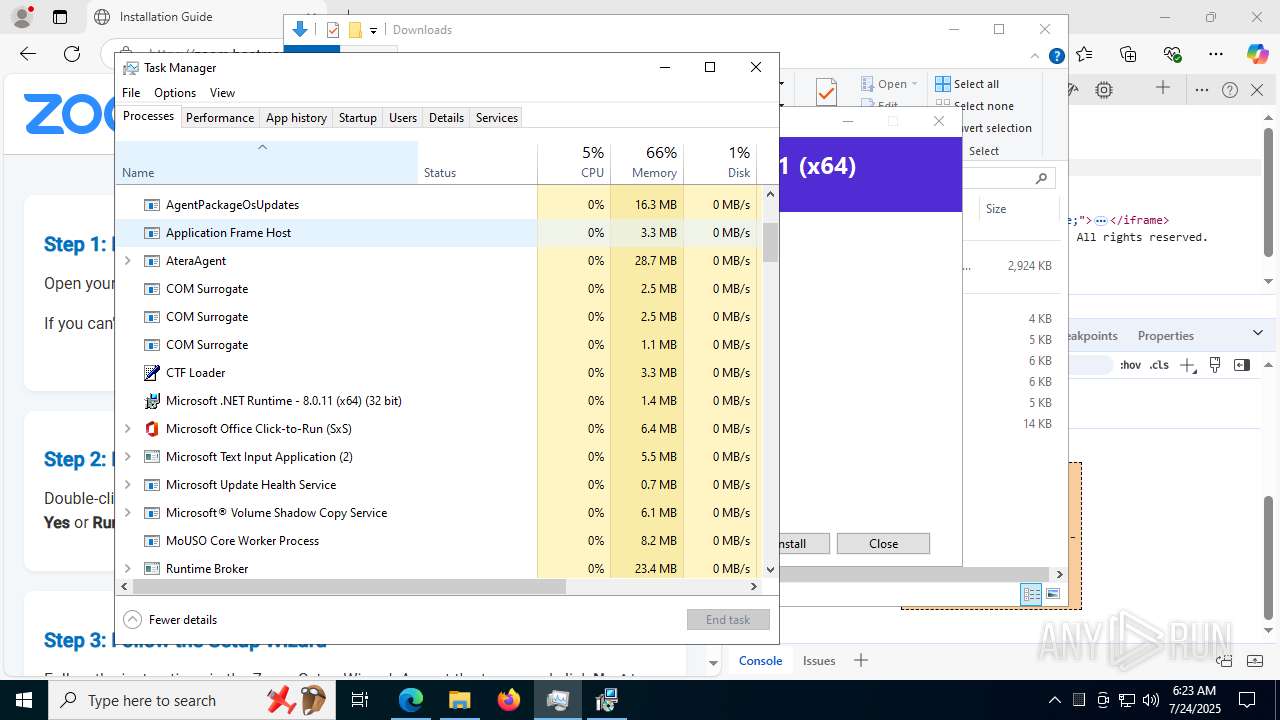
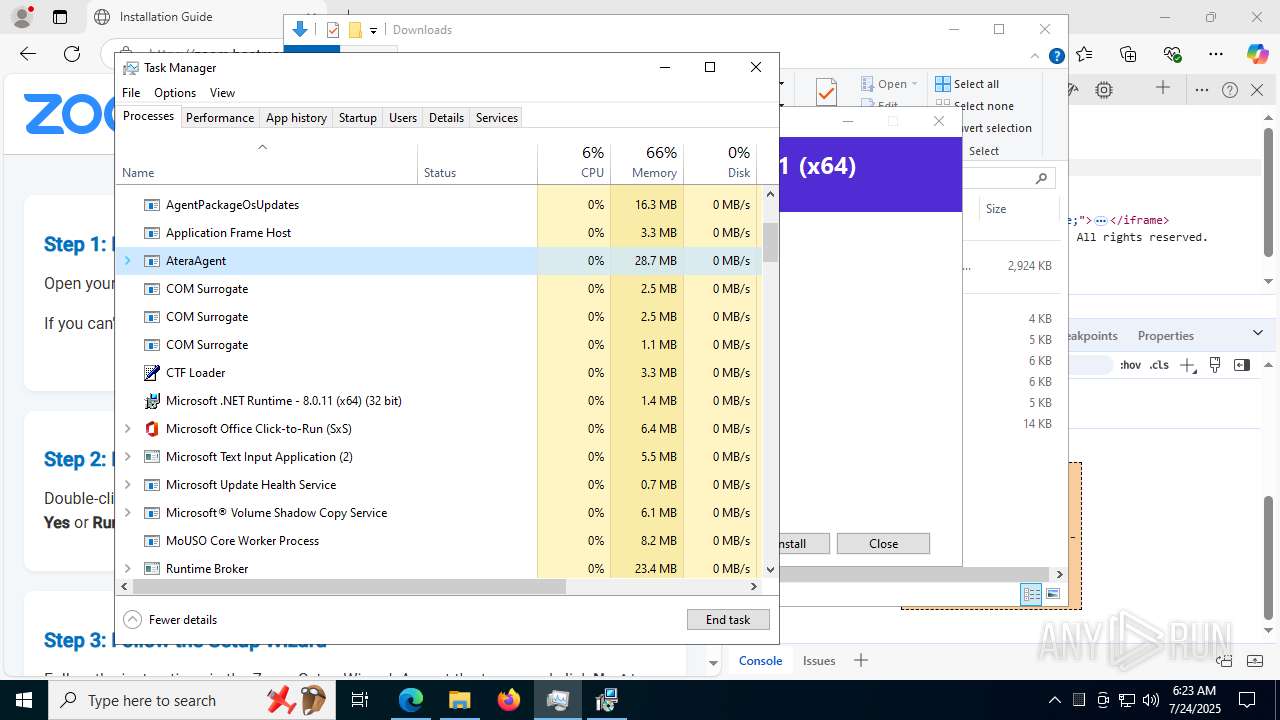
Total processes
513
Monitored processes
352
Malicious processes
24
Suspicious processes
15
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | "C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\SRAgent.exe" | C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\SRAgent.exe | — | SRManager.exe | |||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop® Streamer Agent Version: 3.74.4.29 Modules
| |||||||||||||||
| 684 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc43b5f208,0x7ffc43b5f214,0x7ffc43b5f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 868 | C:\WINDOWS\TEMP\{07C33F2C-01C4-42D6-9456-E41864325B9A}\_is8429.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{E7B66B83-79B8-40E0-8FFB-F13B8A5B3A59} | C:\Windows\Temp\{07C33F2C-01C4-42D6-9456-E41864325B9A}\_is8429.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Flexera Integrity Level: SYSTEM Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 27.0.122 Modules
| |||||||||||||||
| 888 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\Agent.Package.Watchdog\Agent.Package.Watchdog.exe" c6b34154-a625-4889-aea7-76d1eaf3c236 "ba8cdf20-19ea-47c1-8339-a56c0482c442" agent-api.atera.com/Production 443 or8ixLi90Mf "eyJBcmd1bWVudHMiOiJ7XHUwMDIyQ29tbWFuZE5hbWVcdTAwMjI6XHUwMDIybWFpbnRlbmFuY2VcdTAwMjIsXHUwMDIyRW5hYmxlZFx1MDAyMjpmYWxzZSxcdTAwMjJSZXBlYXRJbnRlcnZhbE1pbnV0ZXNcdTAwMjI6MTAsXHUwMDIyRGF5c0ludGVydmFsXHUwMDIyOjEsXHUwMDIyUmVwZWF0RHVyYXRpb25EYXlzXHUwMDIyOjF9In0=" 001Q300000V259sIAB | C:\Program Files\ATERA Networks\AteraAgent\Packages\Agent.Package.Watchdog\Agent.Package.Watchdog.exe | — | AteraAgent.exe | |||||||||||
User: SYSTEM Company: Agent.Package.Watchdog Integrity Level: SYSTEM Description: Agent.Package.Watchdog Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 1028 | "C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\BdEpSDK.exe" -v | C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\BdEpSDK.exe | — | SRAgent.exe | |||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: SplashtopR Streamer BdEpSDK Exit code: 4294967294 Version: 1.0.0.8 Modules
| |||||||||||||||
| 1040 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe" | C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe | services.exe | ||||||||||||
User: SYSTEM Company: ATERA Networks Ltd. Integrity Level: SYSTEM Description: AteraAgent Exit code: 1 Version: 1.8.7.2 Modules
| |||||||||||||||
| 1044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | dotnet.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMarketplace\AgentPackageMarketplace.exe" c6b34154-a625-4889-aea7-76d1eaf3c236 "95c3e853-21fc-47c7-890b-b02f7ea5a931" agent-api.atera.com/Production 443 or8ixLi90Mf "agentprovision" 001Q300000V259sIAB | C:\Program Files\ATERA Networks\AteraAgent\Packages\AgentPackageMarketplace\AgentPackageMarketplace.exe | AteraAgent.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: AgentPackageMarketplace Exit code: 0 Version: 1.6.0.0 Modules
| |||||||||||||||
| 1136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\WINDOWS\TEMP\RES4893.tmp" "c:\Windows\Temp\uf5eh0n2\CSC9CA93E685514C5BB03A5A5C2B11A698.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
Total events
153 872
Read events
151 502
Write events
2 129
Delete events
241
Modification events
| (PID) Process: | (6492) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6492) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6492) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6492) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6492) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6492) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\721762 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {EDDE5DD3-57CA-4ABA-BADB-D38769F699FB} | |||
| (PID) Process: | (6492) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6492) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 2EF808163D992F00 | |||
| (PID) Process: | (6492) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\721762 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {EAE4380B-C7B9-4140-A3DA-08487C89F8D9} | |||
| (PID) Process: | (6492) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\721762 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C77F9E4A-1CA3-4D3E-9F21-2A2FD8B2291F} | |||
Executable files
1 293
Suspicious files
623
Text files
386
Unknown types
57
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF18d50e.TMP | — | |
MD5:— | SHA256:— | |||
| 6492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF18d50e.TMP | — | |
MD5:— | SHA256:— | |||
| 6492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF18d54c.TMP | — | |
MD5:— | SHA256:— | |||
| 6492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF18d54c.TMP | — | |
MD5:— | SHA256:— | |||
| 6492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF18d54c.TMP | — | |
MD5:— | SHA256:— | |||
| 6492 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
207
DNS requests
150
Threats
71
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1964 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:LKoWQsTTzGNpH85baFZs7OUM-A2YQqfQETFJqsjKQEM&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2064 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3628 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6492 | msedge.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
3628 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6492 | msedge.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAnTy%2FhDMohv9omwS69%2Fdow%3D | unknown | — | — | whitelisted |
6492 | msedge.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
7896 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1753752856&P2=404&P3=2&P4=OBjeobf0QhD4PEDuVwZeRa9a9OkumcPY0hK7K%2fKn00xpwNM%2bk%2bIEaWEUOX6AGGOvDU5I6q%2fhMvp%2b%2fKC2wDsKCQ%3d%3d | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2464 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1964 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1964 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1964 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1964 | msedge.exe | 2.16.241.220:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
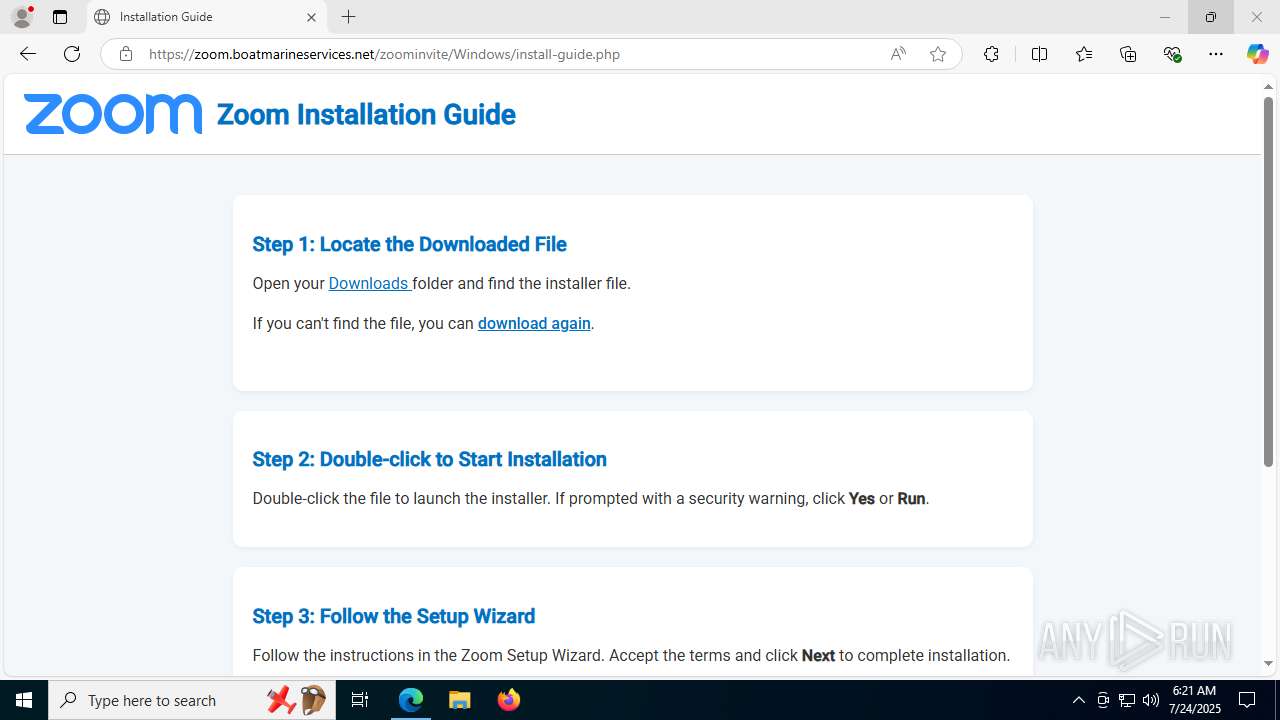
1964 | msedge.exe | 104.21.32.1:443 | zoom.boatmarineservices.net | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
zoom.boatmarineservices.net |
| unknown |
copilot.microsoft.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
www.bing.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1964 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
1964 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
1964 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
1964 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
1964 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
1964 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
8004 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
3704 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
3704 | rundll32.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
5340 | AteraAgent.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible Atera Remote Access Software Domain observed in TLS SNI (agent-api .atera .com) |
Process | Message |
|---|---|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|
SplashtopStreamer.exe | [8524]2025-07-24 06:20:37 [CUtility::OSInfo] OS 10.0(19045) x64:1 (Last=0) |
SplashtopStreamer.exe | [8524]2025-07-24 06:20:37 [CUnPack::FindHeader] Name:C:\WINDOWS\TEMP\SplashtopStreamer.exe (Last=0) |
SplashtopStreamer.exe | [8524]2025-07-24 06:20:37 [CUnPack::FindHeader] Sign Size:10376 (Last=0) |
SplashtopStreamer.exe | [8524]2025-07-24 06:20:37 [CUnPack::FindHeader] Header offset:434176 (Last=183) |
SplashtopStreamer.exe | [8524]2025-07-24 06:20:37 [CUnPack::UnPackFiles] FreeSpace:233029554176 FileSize:63187968 (Last=0) |
SplashtopStreamer.exe | [8524]2025-07-24 06:20:37 [CUnPack::UnPackFiles] (1/5)UnPack file name:C:\WINDOWS\TEMP\unpack\setup.msi (63187968) (Last=0) |
SplashtopStreamer.exe | [8524]2025-07-24 06:20:38 [CUnPack::UnPackFiles] UnPack count:1 len:63187968 File:(null) (Last=0) |
SplashtopStreamer.exe | [8524]2025-07-24 06:20:38 [CUnPack::UnPackFiles] FreeSpace:232966348800 FileSize:15 (Last=183) |
SplashtopStreamer.exe | [8524]2025-07-24 06:20:38 [CUnPack::UnPackFiles] (2/5)UnPack file name:C:\WINDOWS\TEMP\unpack\run.bat (15) (Last=122) |