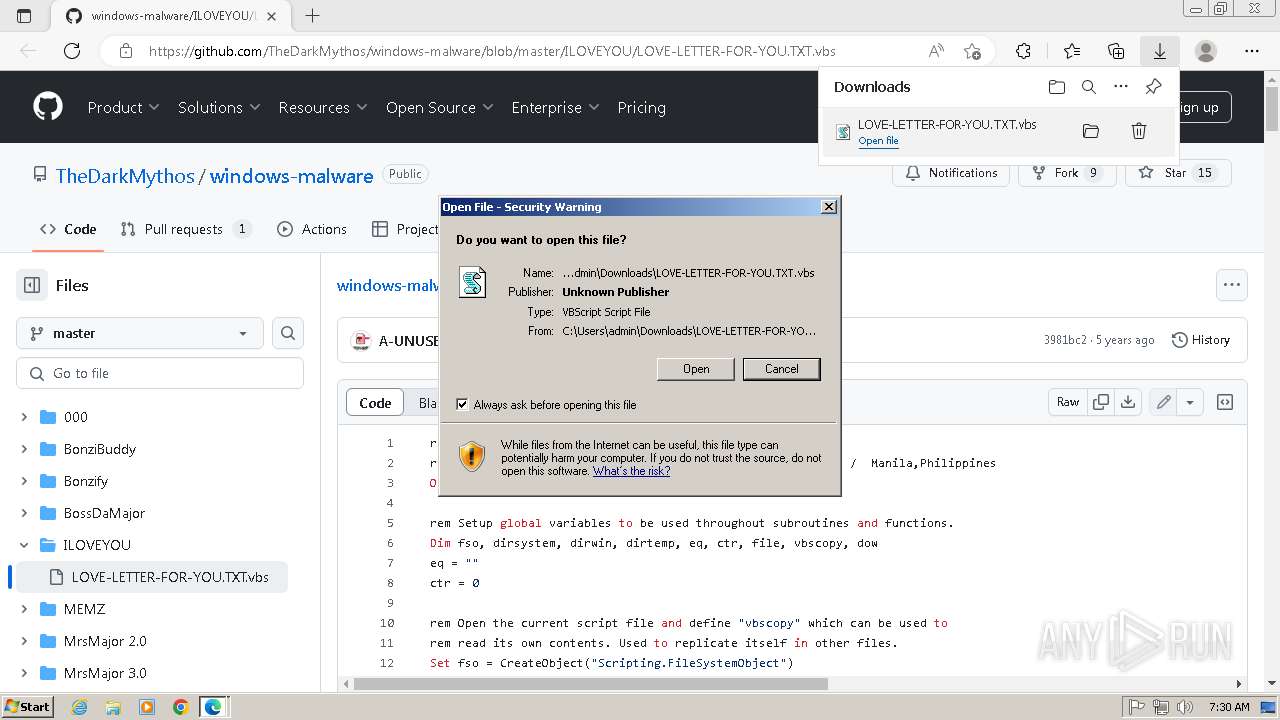
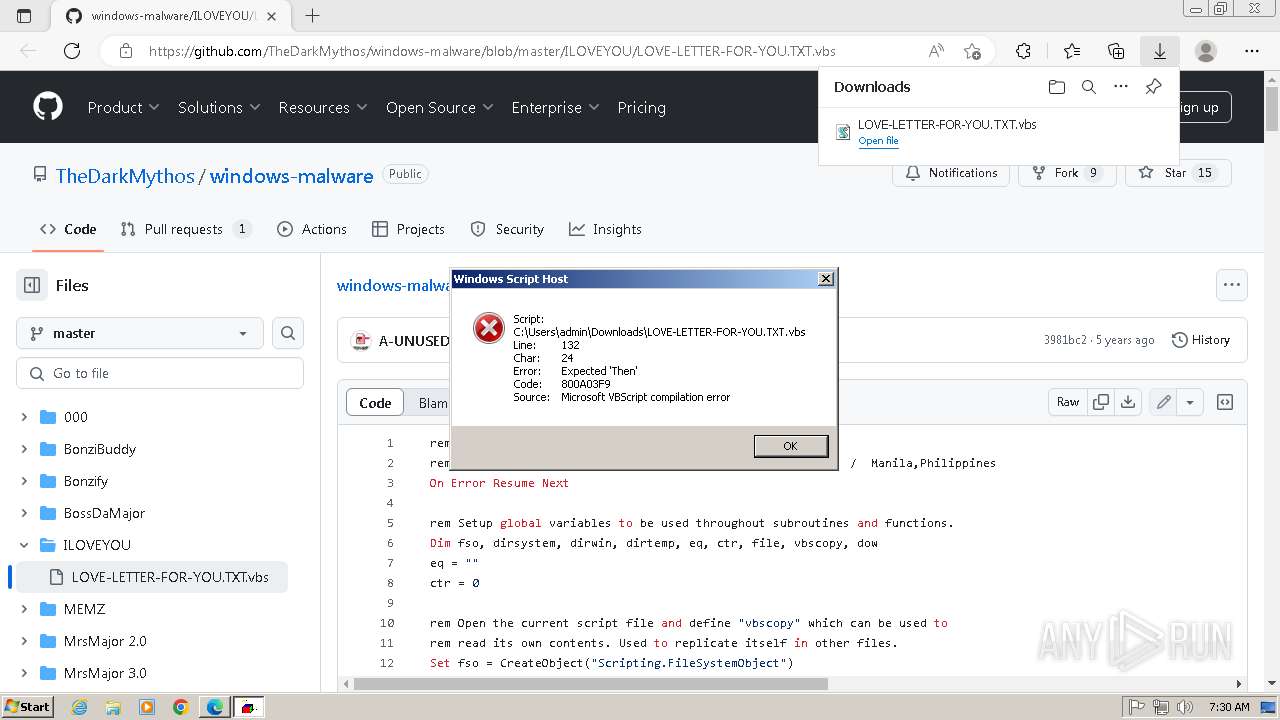
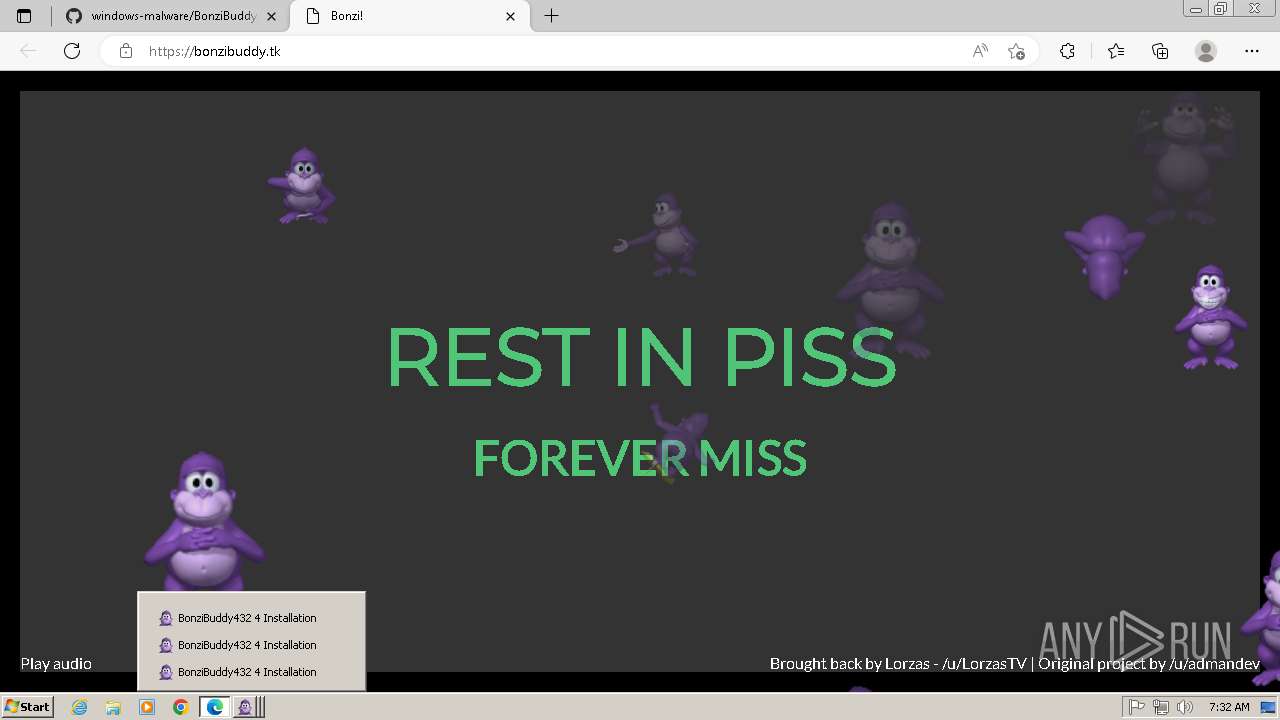
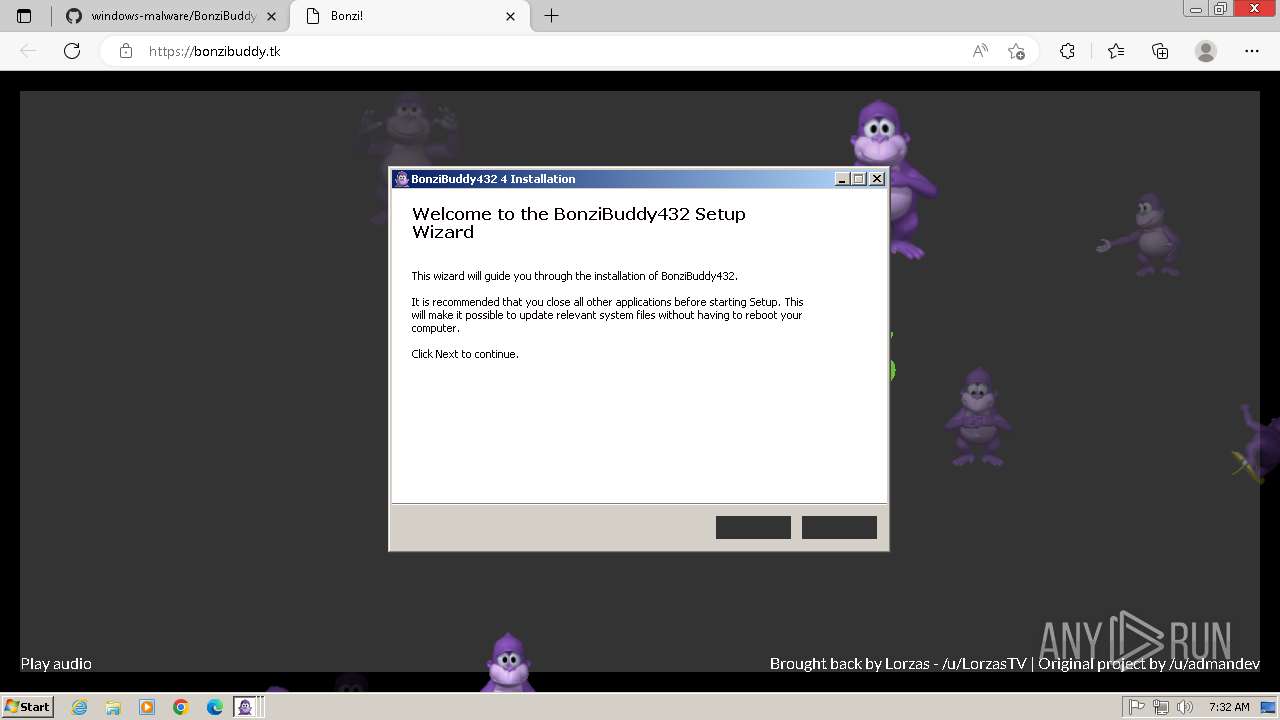
| URL: | https://github.com/TheDarkMythos/windows-malware/blob/master/ILOVEYOU/LOVE-LETTER-FOR-YOU.TXT.vbs |
| Full analysis: | https://app.any.run/tasks/f3245058-6b85-4b39-8bd3-3dff5b06f8f7 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 07:30:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 97E29D8592C1C1B76B723A853FFC0CA2 |
| SHA1: | 5B219FC527DCE39A1F84D444778B66904C48A09A |
| SHA256: | 2EF8F14DF9DFEBC52DC0BCEA5DCFA3D143DE1CE1A4CBAA9F6AB18CD7C4B00E4B |
| SSDEEP: | 3:N8tEdy/BzEvJcTEHEM0ydxbjq48Lwn:2u4/BzL+EEzK43n |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- MSAGENT.EXE (PID: 1544)
- tv_enua.exe (PID: 2480)
Executing a file with an untrusted certificate
- MSAGENT.EXE (PID: 1544)
- tv_enua.exe (PID: 2480)
Changes the autorun value in the registry
- tv_enua.exe (PID: 2480)
SUSPICIOUS
The process executes VB scripts
- msedge.exe (PID: 3480)
There is functionality for taking screenshot (YARA)
- BonziBuddy432.exe (PID: 1656)
- BonziBuddy432.exe (PID: 2488)
- BonziBuddy432.exe (PID: 3900)
- BonziBuddy432.exe (PID: 3892)
Creates a software uninstall entry
- BonziBuddy432.exe (PID: 2488)
- tv_enua.exe (PID: 2480)
Reads the Internet Settings
- BonziBuddy432.exe (PID: 2488)
Reads security settings of Internet Explorer
- BonziBuddy432.exe (PID: 2488)
Executable content was dropped or overwritten
- BonziBuddy432.exe (PID: 2488)
- MSAGENT.EXE (PID: 1544)
- tv_enua.exe (PID: 2480)
Process drops legitimate windows executable
- BonziBuddy432.exe (PID: 2488)
- MSAGENT.EXE (PID: 1544)
- tv_enua.exe (PID: 2480)
Creates/Modifies COM task schedule object
- BonziBuddy432.exe (PID: 2488)
- regsvr32.exe (PID: 2420)
- regsvr32.exe (PID: 2024)
- regsvr32.exe (PID: 2748)
- regsvr32.exe (PID: 1396)
- regsvr32.exe (PID: 2952)
- regsvr32.exe (PID: 952)
- regsvr32.exe (PID: 2772)
- regsvr32.exe (PID: 3232)
- regsvr32.exe (PID: 3344)
Executing commands from a ".bat" file
- BonziBuddy432.exe (PID: 2488)
Starts CMD.EXE for commands execution
- BonziBuddy432.exe (PID: 2488)
INFO
Application launched itself
- msedge.exe (PID: 3480)
- msedge.exe (PID: 3272)
Autorun file from Downloads
- msedge.exe (PID: 3480)
- msedge.exe (PID: 3292)
- msedge.exe (PID: 3084)
Checks supported languages
- BonziBuddy432.exe (PID: 3900)
- BonziBuddy432.exe (PID: 1656)
- BonziBuddy432.exe (PID: 3892)
- BonziBuddy432.exe (PID: 2488)
- MSAGENT.EXE (PID: 1544)
- tv_enua.exe (PID: 2480)
- AgentSvr.exe (PID: 3224)
- BonziBDY_4.EXE (PID: 3260)
- BonziBDY_35.EXE (PID: 3432)
- BonziBDY_2.EXE (PID: 2860)
Reads the computer name
- BonziBuddy432.exe (PID: 3892)
- BonziBuddy432.exe (PID: 3900)
- BonziBuddy432.exe (PID: 1656)
- BonziBuddy432.exe (PID: 2488)
- MSAGENT.EXE (PID: 1544)
- tv_enua.exe (PID: 2480)
Create files in a temporary directory
- BonziBuddy432.exe (PID: 1656)
- BonziBuddy432.exe (PID: 3900)
- BonziBuddy432.exe (PID: 2488)
- MSAGENT.EXE (PID: 1544)
- tv_enua.exe (PID: 2480)
Creates files or folders in the user directory
- BonziBuddy432.exe (PID: 2488)
Reads mouse settings
- BonziBuddy432.exe (PID: 2488)
Creates files in the program directory
- BonziBuddy432.exe (PID: 2488)
The sample compiled with english language support
- BonziBuddy432.exe (PID: 2488)
- MSAGENT.EXE (PID: 1544)
- tv_enua.exe (PID: 2480)
Manual execution by a user
- BonziBDY_4.EXE (PID: 3260)
- BonziBDY_35.EXE (PID: 3432)
- BonziBDY_2.EXE (PID: 2860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
95
Monitored processes
55
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1664 --field-trial-handle=1252,i,11055911708876039895,7097607087486091142,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1532 --field-trial-handle=1252,i,11055911708876039895,7097607087486091142,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 948 | grpconv.exe -o | C:\Windows\System32\grpconv.exe | — | MSAGENT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | regsvr32 /s "C:\Windows\msagent\AgentSR.dll" | C:\Windows\System32\regsvr32.exe | — | MSAGENT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 960 | "C:\Users\admin\Downloads\BonziBuddy432.exe" | C:\Users\admin\Downloads\BonziBuddy432.exe | — | msedge.exe | |||||||||||
User: admin Company: Bonzi Software Integrity Level: MEDIUM Description: BonziBuddy432 4 Installation Exit code: 3221226540 Version: 4 Modules
| |||||||||||||||
| 1372 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=25 --mojo-platform-channel-handle=4032 --field-trial-handle=1252,i,11055911708876039895,7097607087486091142,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1396 | regsvr32 /s "C:\Windows\msagent\AgentDP2.dll" | C:\Windows\System32\regsvr32.exe | — | MSAGENT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1544 | MSAGENT.EXE | C:\Program Files\BonziBuddy432\Runtimes\MSAGENT.EXE | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 4.71.1015.0 Modules
| |||||||||||||||
| 1656 | "C:\Users\admin\Downloads\BonziBuddy432.exe" | C:\Users\admin\Downloads\BonziBuddy432.exe | msedge.exe | ||||||||||||
User: admin Company: Bonzi Software Integrity Level: HIGH Description: BonziBuddy432 4 Installation Exit code: 0 Version: 4 Modules
| |||||||||||||||
| 1800 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1420 --field-trial-handle=1252,i,11055911708876039895,7097607087486091142,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
9 240
Read events
8 717
Write events
424
Delete events
99
Modification events
| (PID) Process: | (3480) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\IEToEdge |
| Operation: | delete value | Name: | DisabledPendingAutoUpdateConsent |
Value: | |||
| (PID) Process: | (3480) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3480) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3480) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3480) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3480) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3480) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3480) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3480) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: E0CAC0FABB8F2F00 | |||
| (PID) Process: | (3480) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
Executable files
84
Suspicious files
297
Text files
173
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF182778.TMP | — | |
MD5:— | SHA256:— | |||
| 3480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1827c6.TMP | — | |
MD5:— | SHA256:— | |||
| 3480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1828d0.TMP | — | |
MD5:— | SHA256:— | |||
| 3480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2812 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 3480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old~RF1827b7.TMP | text | |
MD5:D6E3A4A682F60FDD61EA5512284171EC | SHA256:8B8EB180A896C63D5112F8DE6EA7CB016296FAB862F8EEEAC5EB2A1462A53332 | |||
| 3480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State~RF1825d2.TMP | binary | |
MD5:3787BB5ED93139FAD65D1B55F4B44E03 | SHA256:B177D9E79D97792B47AB36D3B19B63D802CA492EA9509AD69FFBDAD396B96496 | |||
| 3480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Platform Notifications\LOG.old~RF182a18.TMP | text | |
MD5:2EC139710F1BF406CD11DCEF20BF6FD1 | SHA256:524DE59920694F2D54BC9D21C08AA2403019C7674A1368FCF7CFA153E7A2E3E6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
38
DNS requests
47
Threats
10
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1800 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3480 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1800 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1800 | msedge.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
1800 | msedge.exe | 185.199.108.154:443 | github.githubassets.com | FASTLY | US | whitelisted |
1800 | msedge.exe | 185.199.108.133:443 | avatars.githubusercontent.com | FASTLY | US | whitelisted |
1800 | msedge.exe | 2.19.122.11:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| whitelisted |
user-images.githubusercontent.com |
| whitelisted |
www.bing.com |
| whitelisted |
collector.github.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1800 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1800 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1800 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
1800 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
1800 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
1800 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
1800 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
1800 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
1800 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
1800 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
Process | Message |
|---|---|
msedge.exe | [0325/073212.795:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|