| File name: | Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe |
| Full analysis: | https://app.any.run/tasks/b5dd2200-b421-4b40-933f-71a800800499 |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2023, 23:43:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F846351DDE8AA591FE5DF56E2CF2670A |
| SHA1: | 551BFD7A37B1A73EABB7F2A387BBADE1A76EA44E |
| SHA256: | 2EEC2305E99890AC3A9C14B5B97AB31862EA27CECBE72E2200CDEB32F68A4176 |
| SSDEEP: | 98304:O01WEnCwQwHyf7bkgk3OH57zUz4//7AGow8HdTF8/4hyJ+e/KSVPj1IJJmIgmb38:BkY |
MALICIOUS
Drops the executable file immediately after the start
- Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe (PID: 1764)
Application was dropped or rewritten from another process
- mls.exe (PID: 2428)
- Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe (PID: 1764)
Connects to the CnC server
- mls.exe (PID: 2428)
SUSPICIOUS
Reads the Internet Settings
- Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe (PID: 1764)
- mls.exe (PID: 2428)
INFO
Checks supported languages
- Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe (PID: 1764)
- mls.exe (PID: 2428)
Reads the machine GUID from the registry
- Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe (PID: 1764)
Reads the computer name
- Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe (PID: 1764)
- mls.exe (PID: 2428)
Reads Microsoft Office registry keys
- Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe (PID: 1764)
Create files in a temporary directory
- Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe (PID: 1764)
Creates files or folders in the user directory
- mls.exe (PID: 2428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.6) |
| .exe | | | Win64 Executable (generic) (23.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:02:12 19:50:20+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 602112 |
| InitializedDataSize: | 2542080 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5a8c5 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
40
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1764 | "C:\Users\admin\AppData\Local\Temp\Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe" | C:\Users\admin\AppData\Local\Temp\Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2428 | "C:\Users\admin\AppData\Roaming\RAC\mls.exe" -s | C:\Users\admin\AppData\Roaming\RAC\mls.exe | Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4060 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.pptx" | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | — | Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
Total events
3 288
Read events
3 230
Write events
51
Delete events
7
Modification events
| (PID) Process: | (1764) Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1764) Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1764) Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1764) Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1764) Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4060) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (4060) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (4060) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (4060) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (4060) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
Executable files
6
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4060 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVRC8FB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1764 | Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | C:\Users\admin\AppData\Local\Temp\1235417540.tmp | executable | |
MD5:F846351DDE8AA591FE5DF56E2CF2670A | SHA256:2EEC2305E99890AC3A9C14B5B97AB31862EA27CECBE72E2200CDEB32F68A4176 | |||
| 1764 | Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | C:\Users\admin\AppData\Local\Temp\RCXC61D.tmp | executable | |
MD5:084E5BAA4DE52BB24BB149618E1E9A8C | SHA256:2D028A935DC4B96A70E1FD3F33B23A0C409C78E0A88AAE595899B37D726B034B | |||
| 1764 | Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | C:\Users\admin\AppData\Local\Temp\RCXC4B5.tmp | executable | |
MD5:2DF96F5A4342F3940A56DE19B5F07647 | SHA256:90EA116A96D3AD95A622DC54927BBED3DBDD1C4D21B161AB96DF2DCE4538904F | |||
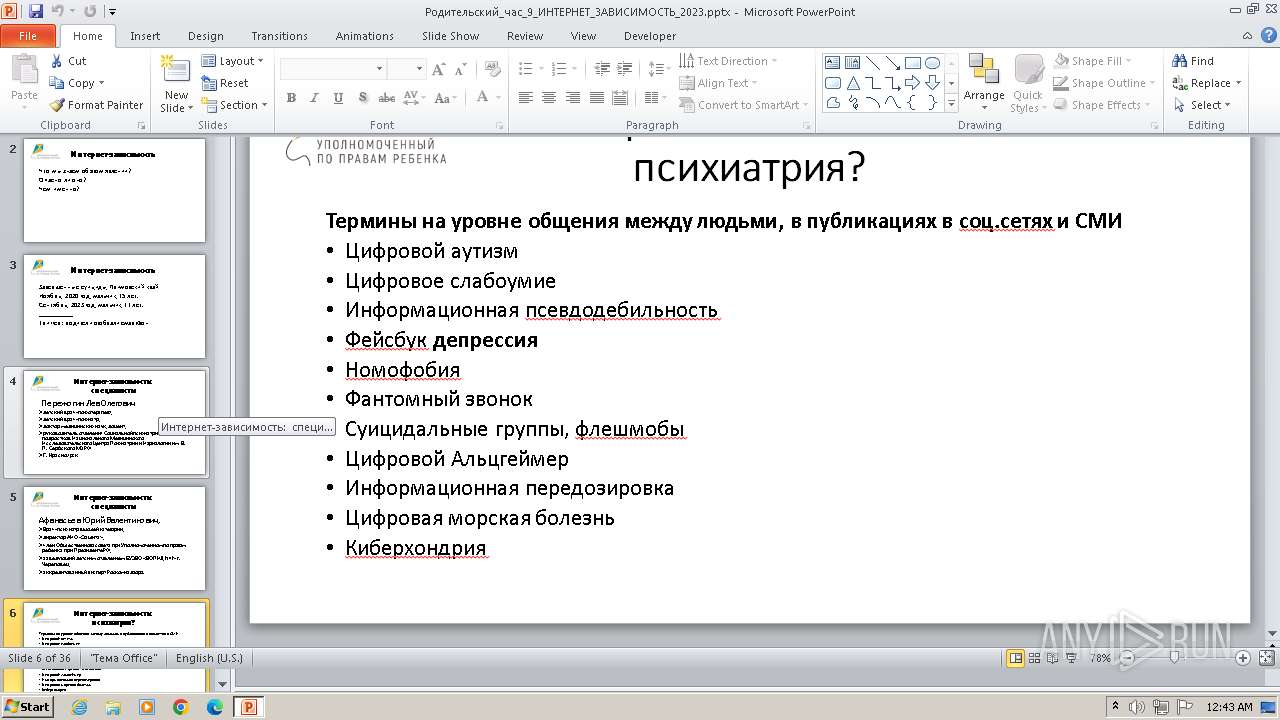
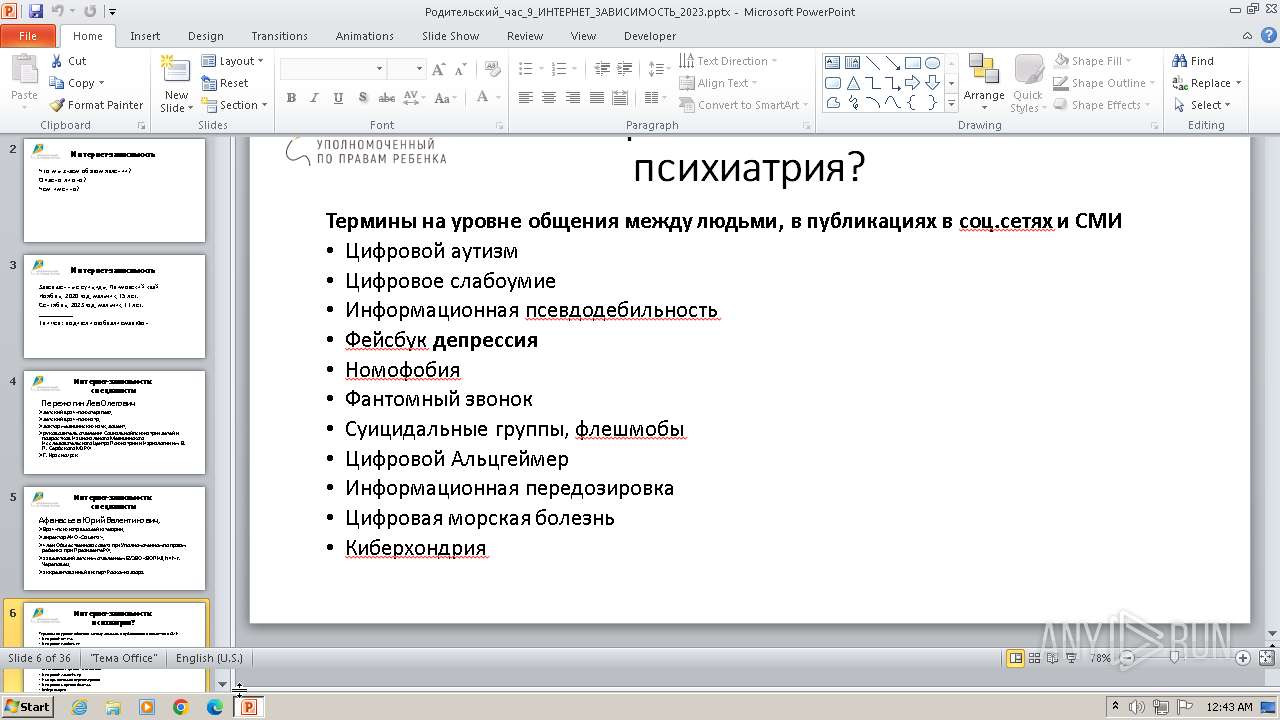
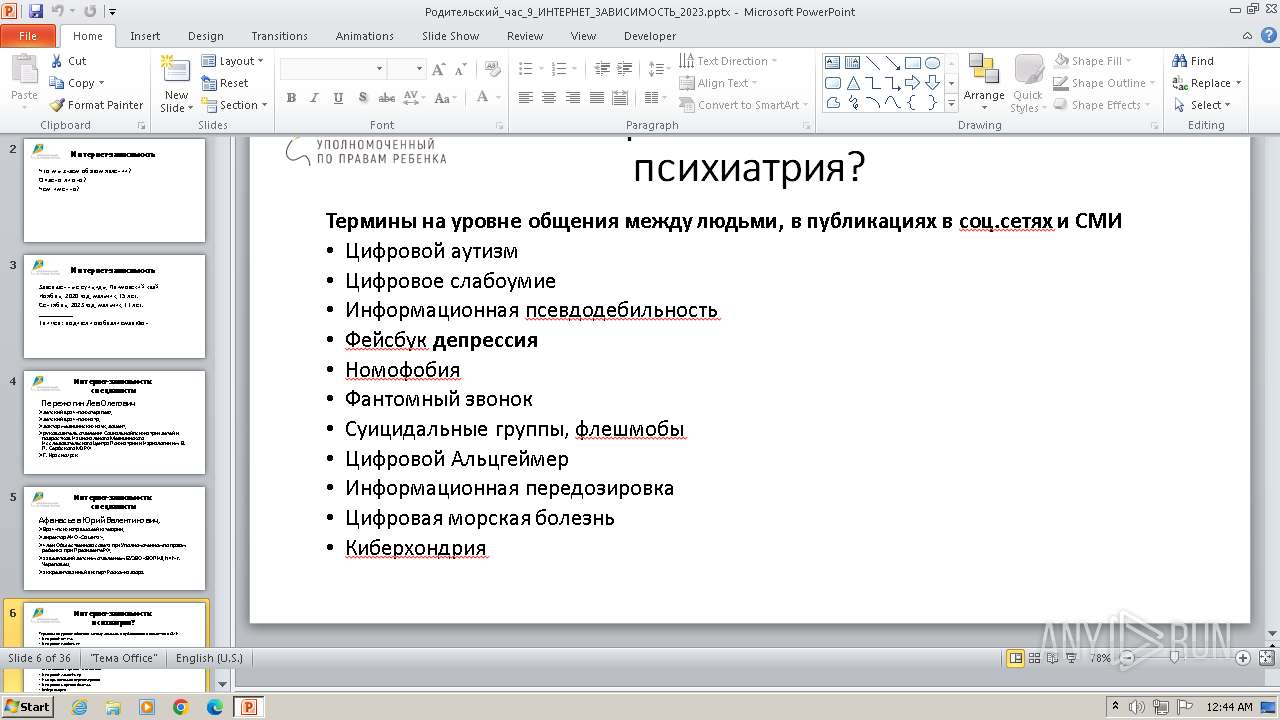
| 1764 | Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | C:\Users\admin\AppData\Local\Temp\Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.pptx | document | |
MD5:AE861D58960ECA15BB9C7A47DC717F3F | SHA256:FA379E293196899999A4E45516786B09EC1B14711F65B2EAA700619CB84C9C89 | |||
| 1764 | Родительский_час_9_ИНТЕРНЕТ_ЗАВИСИМОСТЬ_2023.exe | C:\Users\admin\AppData\Roaming\RAC\mls.exe | executable | |
MD5:084E5BAA4DE52BB24BB149618E1E9A8C | SHA256:2D028A935DC4B96A70E1FD3F33B23A0C409C78E0A88AAE595899B37D726B034B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
1
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2428 | mls.exe | GET | 200 | 34.174.61.199:80 | http://wxanalytics.ru/net.exe.config | unknown | — | — | unknown |
2428 | mls.exe | GET | 200 | 34.174.61.199:80 | http://wxanalytics.ru/net.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2428 | mls.exe | 34.174.61.199:80 | wxanalytics.ru | GOOGLE-CLOUD-PLATFORM | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wxanalytics.ru |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2428 | mls.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2428 | mls.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2428 | mls.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value Snkz |
2428 | mls.exe | A Network Trojan was detected | ET MALWARE Possible Compromised Host AnubisNetworks Sinkhole Cookie Value btst |
1 ETPRO signatures available at the full report