| File name: | Жопа.docx |
| Full analysis: | https://app.any.run/tasks/5288e6ca-487c-45a1-9547-521f48da56d1 |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2019, 19:53:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1251, Author: Artem Korchak, Template: Normal.dotm, Last Saved By: , Revision Number: 2, Name of Creating Application: Microsoft Office Word, Total Editing Time: 05:00, Create Time/Date: Thu Mar 21 19:35:00 2019, Last Saved Time/Date: Thu Mar 21 19:40:00 2019, Number of Pages: 1, Number of Words: 2, Number of Characters: 18, Security: 0 |
| MD5: | C5E3E8219D723414AEF27276669909E7 |
| SHA1: | B5A54CC01F4DE4D28093315BA7577F48C11C2EC6 |
| SHA256: | 2ED68B2F6532274E99E9015257E5D04A2586B53ABE6FE16A9852D57851548A74 |
| SSDEEP: | 1536:ftGVQmWShgdodgCG0sQAeGCCGQCCgCG0sQAiIQy91lbpG717h2Thh9px0E2s:fyzgdPsLe6 |
MALICIOUS
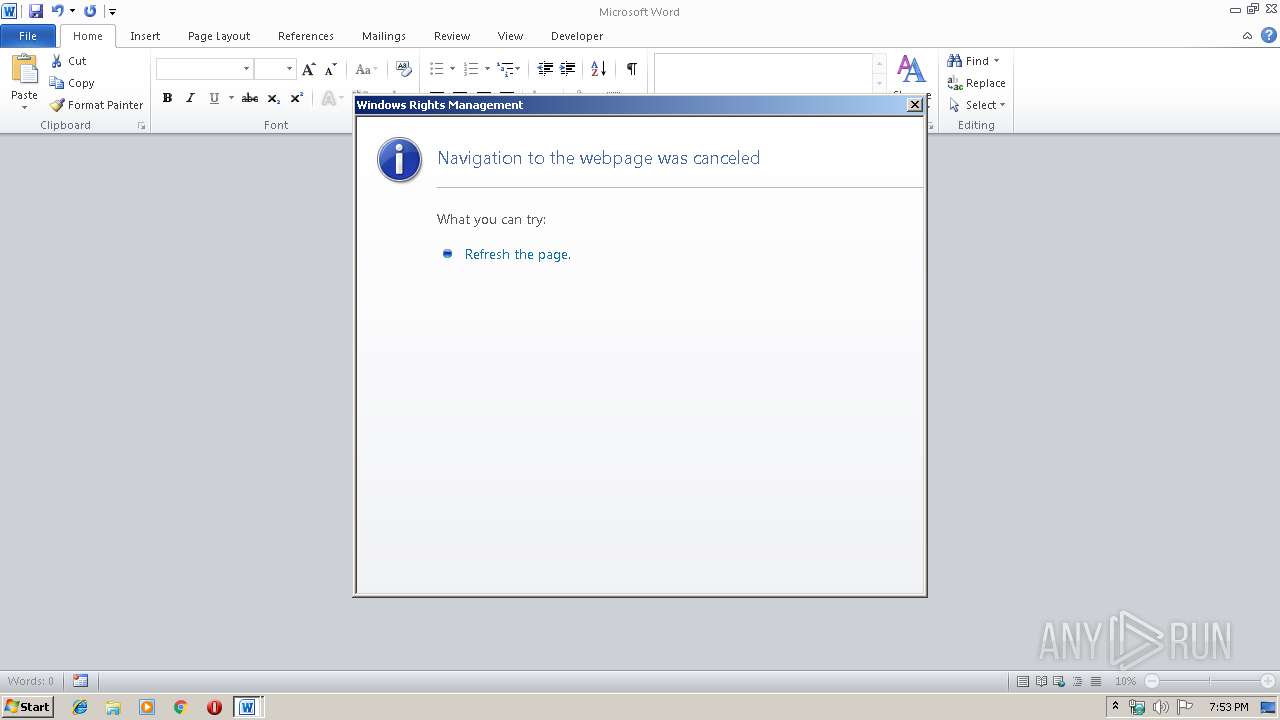
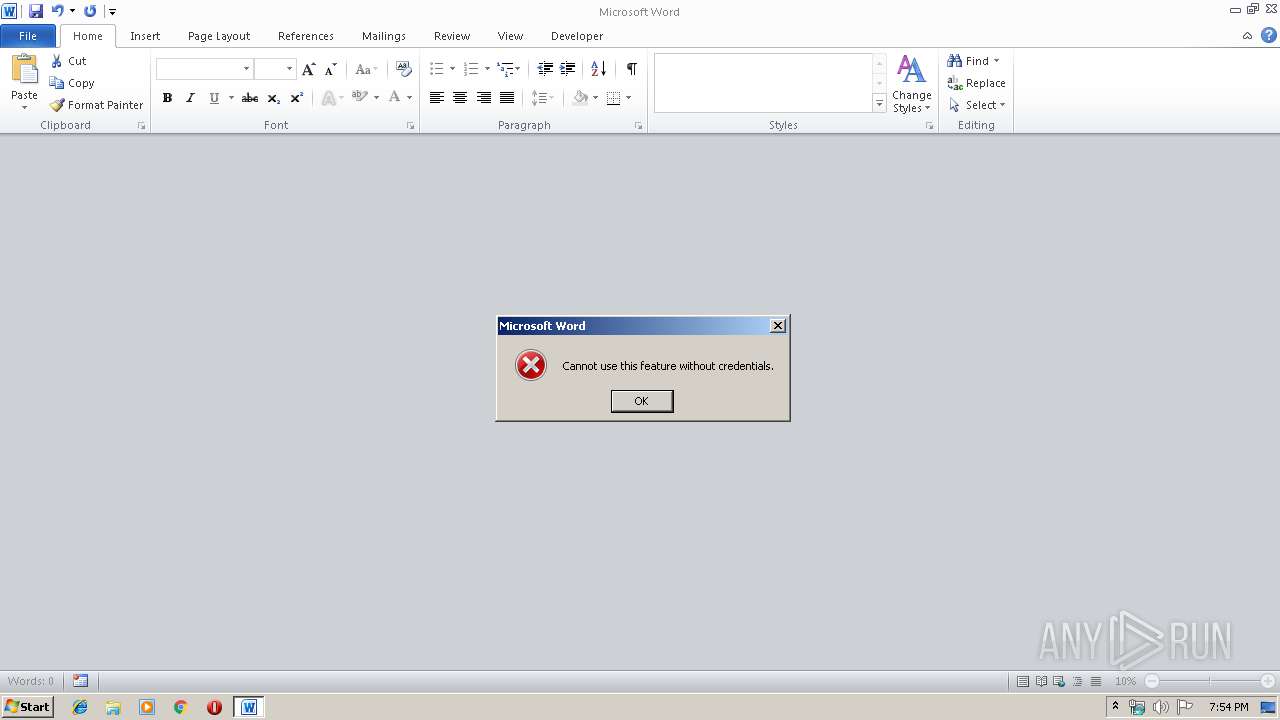
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 688)
SUSPICIOUS
Reads internet explorer settings
- WINWORD.EXE (PID: 688)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 688)
Creates files in the user directory
- WINWORD.EXE (PID: 688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Artem Korchak |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Корчак Артём Сергеевич |
| RevisionNumber: | 2 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 5.0 minutes |
| CreateDate: | 2019:03:21 19:35:00 |
| ModifyDate: | 2019:03:21 19:40:00 |
| Pages: | 1 |
| Words: | 2 |
| Characters: | 18 |
| Security: | None |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 19 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Windows Cyrillic |
| MSIP_Label_3c690079-49de-422d-a19e-fa9ac2582ab2_Enabled: | |
| MSIP_Label_3c690079-49de-422d-a19e-fa9ac2582ab2_SiteId: | 0ac3a7f5-21b0-4a18-82aa-888744bec5b8 |
| MSIP_Label_3c690079-49de-422d-a19e-fa9ac2582ab2_Owner: | a.korchak@QIWI.onmicrosoft.com |
| MSIP_Label_3c690079-49de-422d-a19e-fa9ac2582ab2_SetDate: | 2019-03-21T19:40:11.1525388Z |
| MSIP_Label_3c690079-49de-422d-a19e-fa9ac2582ab2_Name: | Confidential |
| MSIP_Label_3c690079-49de-422d-a19e-fa9ac2582ab2_Application: | Microsoft Azure Information Protection |
| MSIP_Label_3c690079-49de-422d-a19e-fa9ac2582ab2_Extended_MSFT_Method: | Manual |
| MSIP_Label_fec81c06-2398-460b-8d96-29808e0c7ac6_Enabled: | |
| MSIP_Label_fec81c06-2398-460b-8d96-29808e0c7ac6_SiteId: | 0ac3a7f5-21b0-4a18-82aa-888744bec5b8 |
| MSIP_Label_fec81c06-2398-460b-8d96-29808e0c7ac6_Owner: | a.korchak@QIWI.onmicrosoft.com |
| MSIP_Label_fec81c06-2398-460b-8d96-29808e0c7ac6_SetDate: | 2019-03-21T19:40:11.1525388Z |
| MSIP_Label_fec81c06-2398-460b-8d96-29808e0c7ac6_Name: | Finance |
| MSIP_Label_fec81c06-2398-460b-8d96-29808e0c7ac6_Application: | Microsoft Azure Information Protection |
| MSIP_Label_fec81c06-2398-460b-8d96-29808e0c7ac6_Parent: | 3c690079-49de-422d-a19e-fa9ac2582ab2 |
| MSIP_Label_fec81c06-2398-460b-8d96-29808e0c7ac6_Extended_MSFT_Method: | Manual |
| Sensitivity: | Confidential Finance |
Total processes
36
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 688 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Жопа.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1252 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
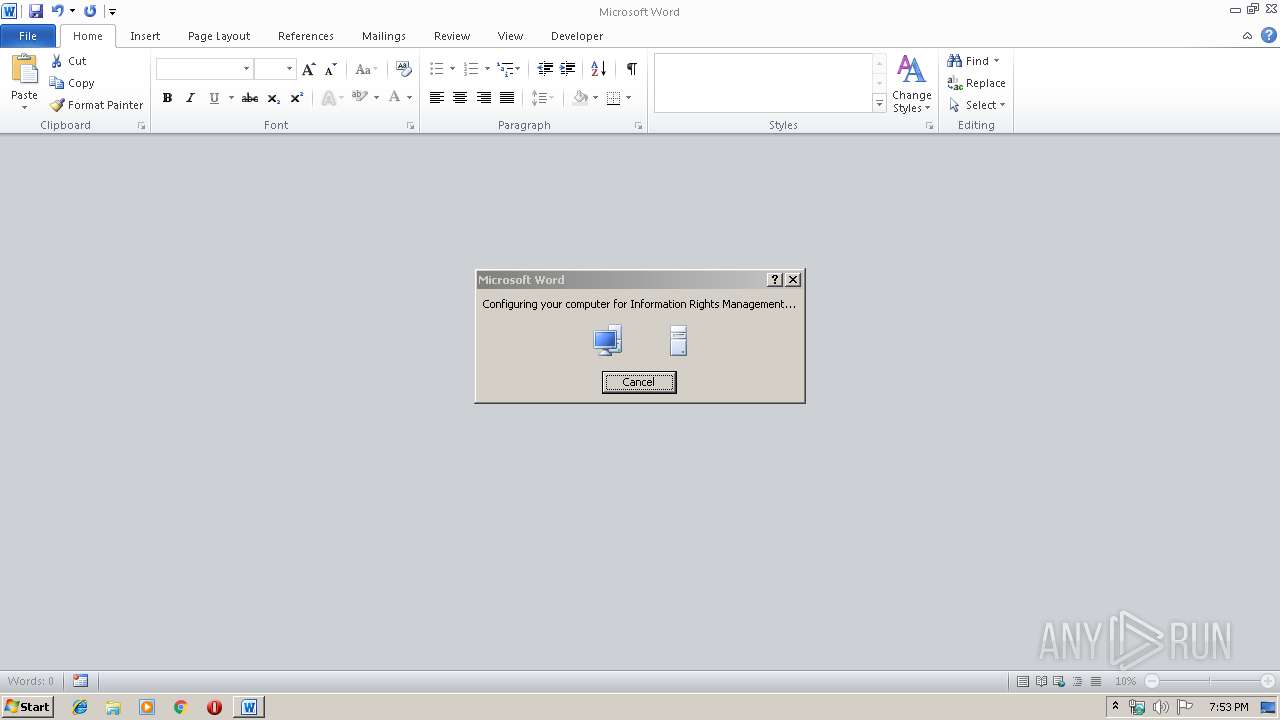
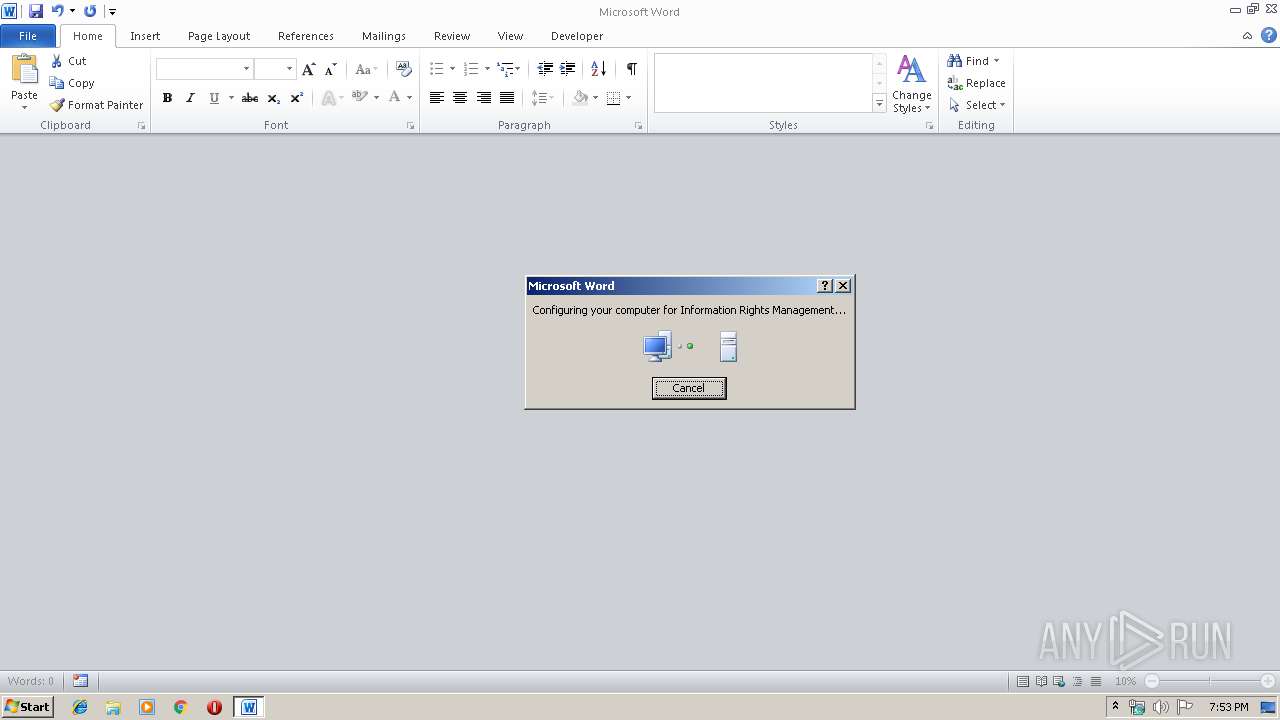
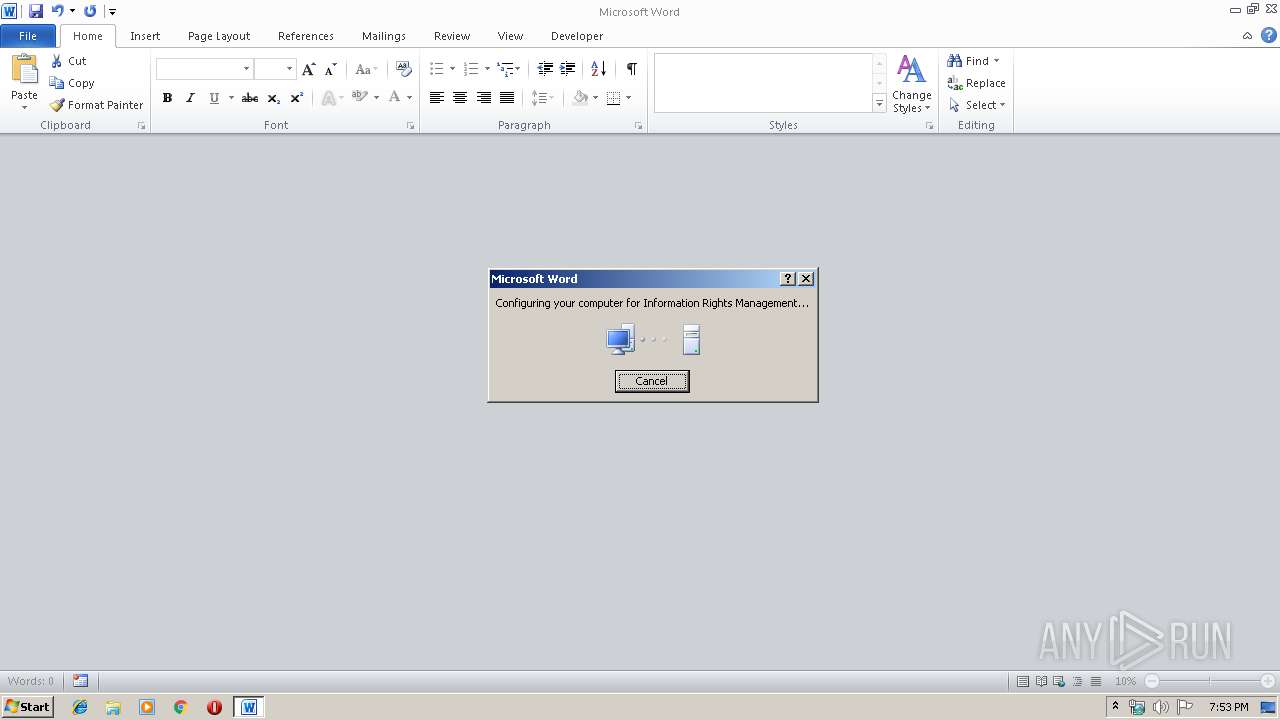
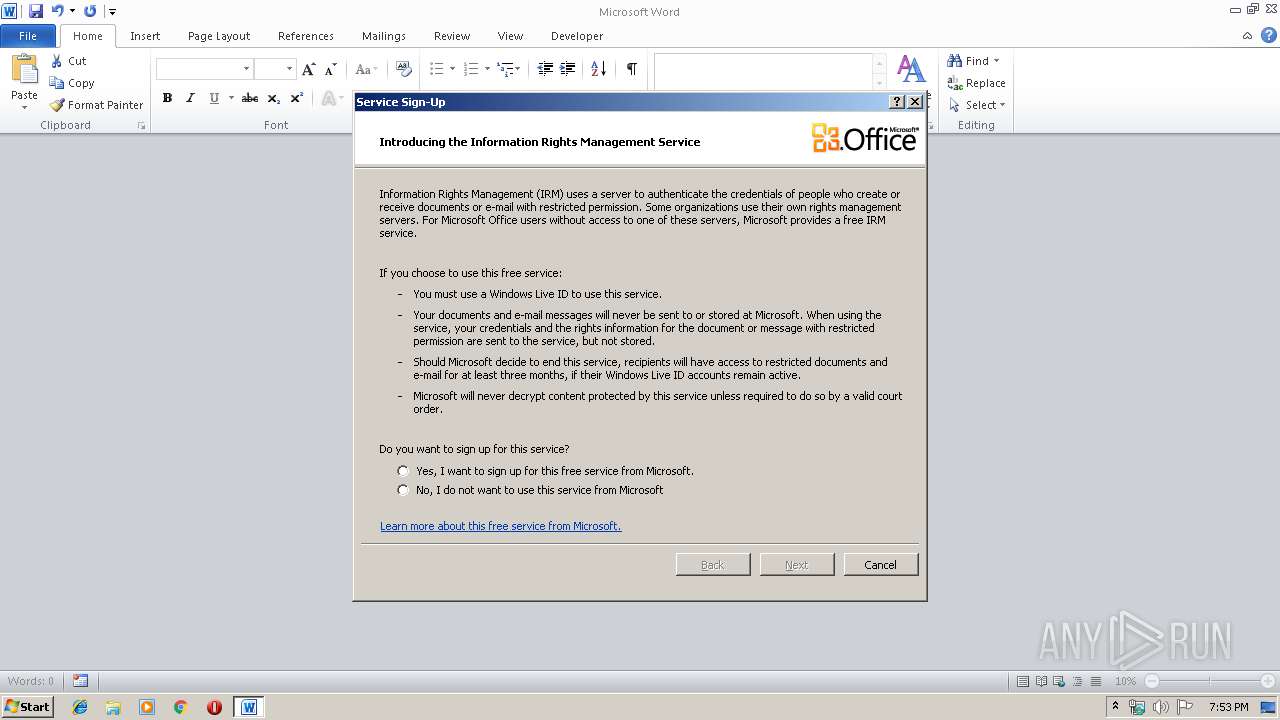
| 1924 | "C:\Windows\system32\rmactivate.exe" | C:\Windows\system32\rmactivate.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Rights Management Services Activation for Desktop Security Processor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
837
Read events
487
Write events
343
Delete events
7
Modification events
| (PID) Process: | (688) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | yv2 |
Value: 79763200B0020000010000000000000000000000 | |||
| (PID) Process: | (688) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (688) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (688) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1316290590 | |||
| (PID) Process: | (688) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1316290704 | |||
| (PID) Process: | (688) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1316290705 | |||
| (PID) Process: | (688) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: B0020000DE2401C61FE0D40100000000 | |||
| (PID) Process: | (688) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | /x2 |
Value: 2F783200B002000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (688) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | /x2 |
Value: 2F783200B002000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (688) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
5
Text files
8
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 688 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR86F9.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 688 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\ServiceLocator[1].asmx | — | |
MD5:— | SHA256:— | |||
| 1924 | rmactivate.exe | C:\Users\admin\AppData\Local\Temp\CabBBB5.tmp | — | |
MD5:— | SHA256:— | |||
| 1924 | rmactivate.exe | C:\Users\admin\AppData\Local\Temp\TarBBB6.tmp | — | |
MD5:— | SHA256:— | |||
| 688 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\ErrorPageTemplate[1] | — | |
MD5:— | SHA256:— | |||
| 688 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\errorPageStrings[1] | — | |
MD5:— | SHA256:— | |||
| 688 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF16C80CD71449465B.TMP | — | |
MD5:— | SHA256:— | |||
| 688 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{79D0D1AD-D394-4288-8013-58CF77D6D807}.tmp | — | |
MD5:— | SHA256:— | |||
| 688 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1924 | rmactivate.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F90F18257CBB4D84216AC1E1F3BB2C76 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
10
DNS requests
5
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
688 | WINWORD.EXE | GET | 302 | 104.109.80.115:80 | http://go.microsoft.com/fwlink/?LinkId=5998&LANGID=1033 | NL | — | — | whitelisted |
1924 | rmactivate.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 550 b | whitelisted |
1924 | rmactivate.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/WinPCA.crl | unknown | der | 530 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
688 | WINWORD.EXE | 52.232.117.200:443 | b17ef168-cf24-4408-9c71-42d88d26961f.rms.eu.aadrm.com | Microsoft Corporation | NL | unknown |
1924 | rmactivate.exe | 2.16.186.120:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
688 | WINWORD.EXE | 104.109.80.115:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
688 | WINWORD.EXE | 65.55.61.29:443 | certification.drm.microsoft.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
b17ef168-cf24-4408-9c71-42d88d26961f.rms.eu.aadrm.com |
| unknown |
crl.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
certification.drm.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
688 | WINWORD.EXE | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |