| File name: | 10.5.0.1_TIC_120844_DriversOnly.exe |
| Full analysis: | https://app.any.run/tasks/4d050316-3060-426d-916e-9de6714dc93b |
| Verdict: | Malicious activity |
| Analysis date: | October 24, 2024, 19:53:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | BC59CF055DF39E4EA3911D5D38C238F1 |
| SHA1: | 830FAFF629543C830BA0D3136B6286506B3D3199 |
| SHA256: | 2ECEB000C685A343BF0D6FD1ECCA66CDBED3FB76D3AA7BA52C2AE861D24E5C5A |
| SSDEEP: | 98304:5v3f49XBO4S8IVJ33MVrTDbs1JS6nZAFCUwDidswCEDLkfIiDCJ3y2RjDMWvS+eu:q6Oc1thkaOnY8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- 10.5.0.1_TIC_120844_DriversOnly.exe (PID: 5944)
Drops a system driver (possible attempt to evade defenses)
- 10.5.0.1_TIC_120844_DriversOnly.exe (PID: 5944)
Executable content was dropped or overwritten
- 10.5.0.1_TIC_120844_DriversOnly.exe (PID: 5944)
INFO
Checks supported languages
- 10.5.0.1_TIC_120844_DriversOnly.exe (PID: 5944)
Create files in a temporary directory
- 10.5.0.1_TIC_120844_DriversOnly.exe (PID: 5944)
Reads the computer name
- 10.5.0.1_TIC_120844_DriversOnly.exe (PID: 5944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2000:03:27 18:09:58+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 69632 |
| InitializedDataSize: | 98304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x83f7 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.11.15.0 |
| ProductVersionNumber: | 2.11.15.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Intel Corporation |
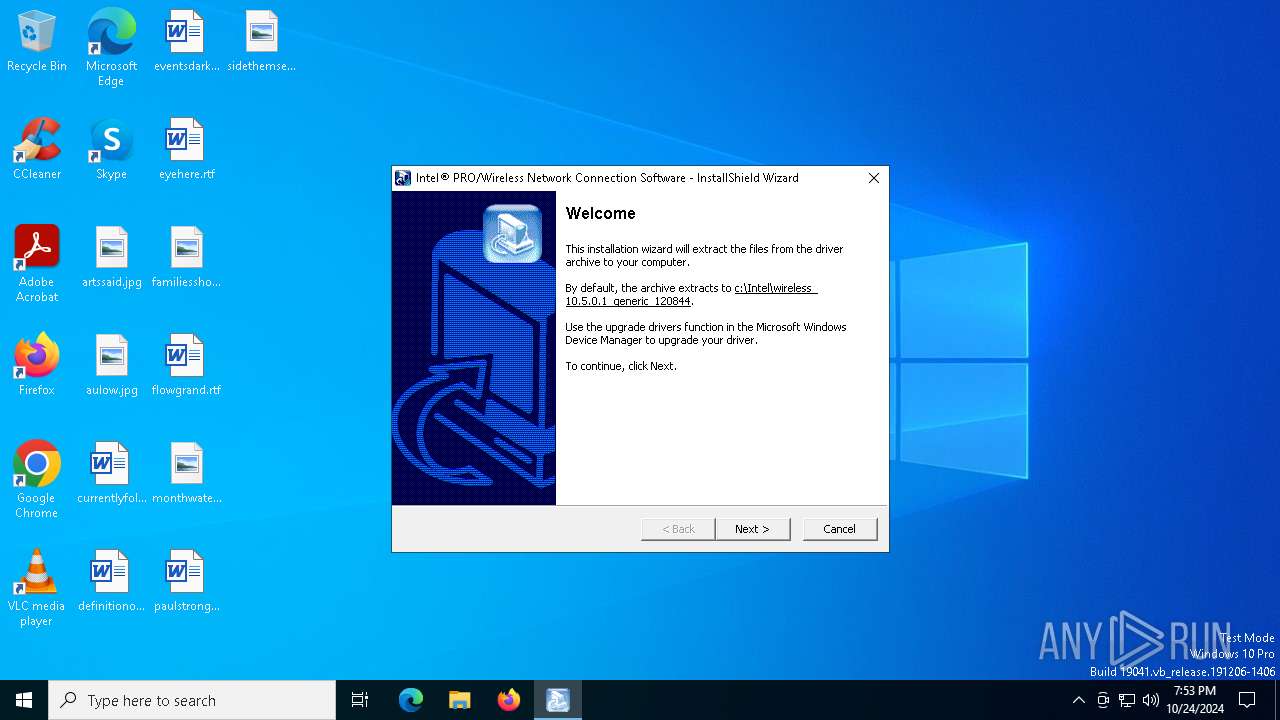
| FileDescription: | Drivers |
| FileVersion: | 10.5.0.1 |
| InternalName: | stub32i.exe |
| LegalCopyright: | Copyright © 1999-2006 Intel Corporation. All rights reserved |
| OriginalFileName: | stub32i.exe |
| ProductName: | Intel® PRO/Wireless Network Connection Software |
| ProductVersion: | 10.5.0.1 |
Total processes
131
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5920 | "C:\Users\admin\AppData\Local\Temp\10.5.0.1_TIC_120844_DriversOnly.exe" | C:\Users\admin\AppData\Local\Temp\10.5.0.1_TIC_120844_DriversOnly.exe | — | explorer.exe | |||||||||||
User: admin Company: Intel Corporation Integrity Level: MEDIUM Description: Drivers Exit code: 3221226540 Version: 10.5.0.1 Modules
| |||||||||||||||
| 5944 | "C:\Users\admin\AppData\Local\Temp\10.5.0.1_TIC_120844_DriversOnly.exe" | C:\Users\admin\AppData\Local\Temp\10.5.0.1_TIC_120844_DriversOnly.exe | explorer.exe | ||||||||||||
User: admin Company: Intel Corporation Integrity Level: HIGH Description: Drivers Exit code: 0 Version: 10.5.0.1 Modules
| |||||||||||||||
| 6172 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
56
Read events
56
Write events
0
Delete events
0
Modification events
Executable files
17
Suspicious files
4
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5944 | 10.5.0.1_TIC_120844_DriversOnly.exe | C:\Users\admin\AppData\Local\Temp\pftF818~tmp\pftw1.pkg | — | |
MD5:— | SHA256:— | |||
| 5944 | 10.5.0.1_TIC_120844_DriversOnly.exe | C:\Users\admin\AppData\Local\Temp\plfD00C.tmp | ini | |
MD5:414378BEE661B0DF11BDB2BE32E15B84 | SHA256:F9EFB3E6FE099C649FB4CC20AC6F9B7E90D3F60B8D98F48FB5D167F1A0B1B7F2 | |||
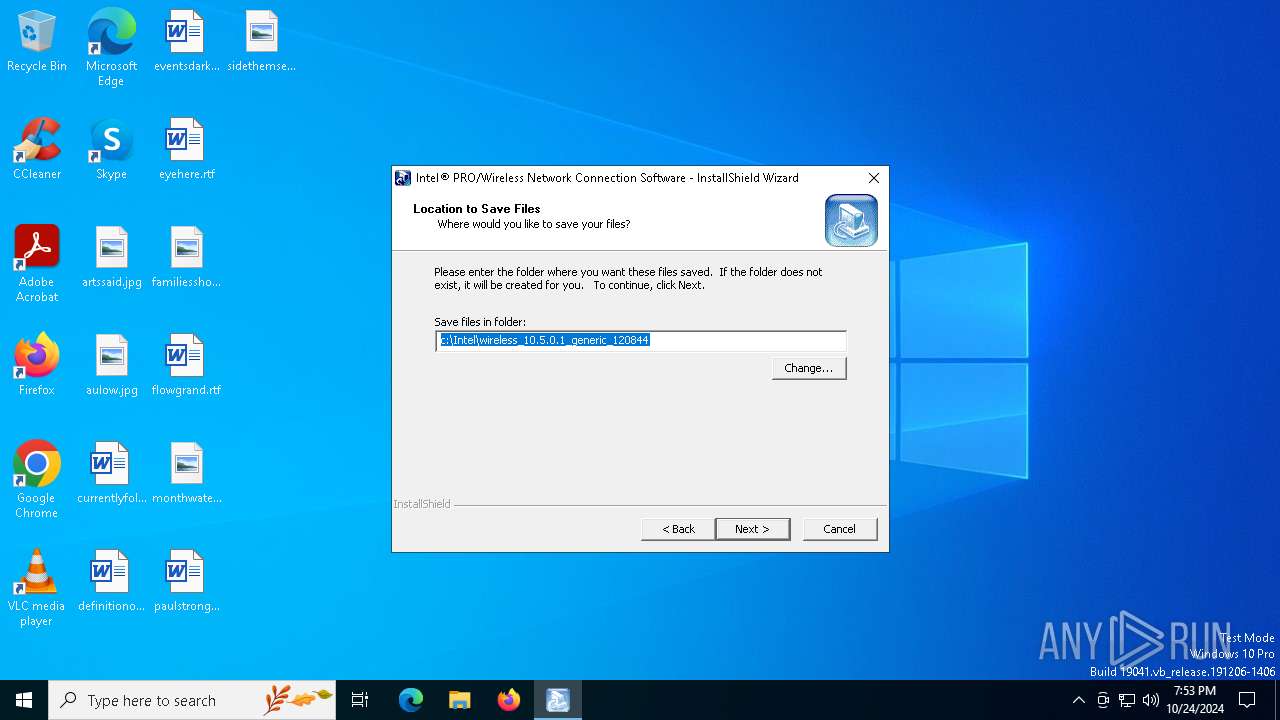
| 5944 | 10.5.0.1_TIC_120844_DriversOnly.exe | C:\Intel\wireless_10.5.0.1_generic_120844\10_5_0_0_TIC_119670_DriversOnly\NETw2c32.DLL | executable | |
MD5:8E6C08392D788656CF48FF4737A7133B | SHA256:C6EFDAEE38D8B09299DA6070F80424AFC223BF2AD6FA928040C4FA5CFD0FA231 | |||
| 5944 | 10.5.0.1_TIC_120844_DriversOnly.exe | C:\Intel\wireless_10.5.0.1_generic_120844\10_5_0_0_TIC_119670_DriversOnly\iProdifx.EXE | executable | |
MD5:0C8C93AB7F09963FE163AB917C8A4414 | SHA256:E15D1F74E8798B03058FB3CD83E097D516BC011D53E9514E261EF44AEAA6F5D3 | |||
| 5944 | 10.5.0.1_TIC_120844_DriversOnly.exe | C:\Users\admin\AppData\Local\Temp\extCFFC.tmp | text | |
MD5:BD2D1986B8BE61AA96484C684687ECDF | SHA256:C6AB1D0D28D673CF0753343F871ABF124152FCD93D38BC005FF8F1109D1D428F | |||
| 5944 | 10.5.0.1_TIC_120844_DriversOnly.exe | C:\Intel\wireless_10.5.0.1_generic_120844\10_5_0_0_TIC_119670_DriversOnly\NETw3c64.DLL | executable | |
MD5:5D48B84AB380221C2BA99248C72DC6D7 | SHA256:094898C23D8BD6764EB95538EB9C687EF388E0BF9221FD42FBF6E32E3DDB1659 | |||
| 5944 | 10.5.0.1_TIC_120844_DriversOnly.exe | C:\Intel\wireless_10.5.0.1_generic_120844\10_5_0_0_TIC_119670_DriversOnly\NETw2c64.DLL | executable | |
MD5:9D6D79427FD3A9030B3225CBBFE54ABD | SHA256:D144E475C00FF8A35E305F6A793080E0AEFF4F15AE892F25F4A0A82674952552 | |||
| 5944 | 10.5.0.1_TIC_120844_DriversOnly.exe | C:\Intel\wireless_10.5.0.1_generic_120844\10_5_0_0_TIC_119670_DriversOnly\DPInst64.exe | executable | |
MD5:7CE61B7C402728CE373FBC0DC9214066 | SHA256:5B8F31594F208E1BD15BA972B13B3142E7EFB78560B8B3674AB6C09E589ECE4E | |||
| 5944 | 10.5.0.1_TIC_120844_DriversOnly.exe | C:\Intel\wireless_10.5.0.1_generic_120844\10_5_0_0_TIC_119670_DriversOnly\NETw39x5.CAT | binary | |
MD5:A8DDB7BAC0D64D0B7D60DE65A4C55581 | SHA256:3F5E01649351F1605F30A2CA858BE869640FDFE9B054ED6E2A58A99CA8F59AD4 | |||
| 5944 | 10.5.0.1_TIC_120844_DriversOnly.exe | C:\Intel\wireless_10.5.0.1_generic_120844\10_5_0_0_TIC_119670_DriversOnly\NETw2r32.DLL | executable | |
MD5:C4080AC875F0EF60CCFD0592CB75EA91 | SHA256:6BA0546A6FA921369C73CA8831E109CDD7FAC5630AD5CED2BA0231A100D2FE78 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
44
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1952 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5600 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1952 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6964 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 104.126.37.185:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5600 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5600 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |