| File name: | AcWinRT.ps1 |
| Full analysis: | https://app.any.run/tasks/522512f4-c7a4-44d8-9f41-52c994646d22 |
| Verdict: | Malicious activity |
| Analysis date: | October 21, 2024, 11:26:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (65527), with CRLF line terminators |
| MD5: | 764C43128170E2762E2B5B8D5FB89800 |
| SHA1: | 31E232F33AC925B25B26989E0D41667503ED8E65 |
| SHA256: | 2EC59B8763ADC00F41E18D05C25B425BD212AE788CC00EDA99E9C0CEC5FC2D1E |
| SSDEEP: | 24576:5tfWNyLYWbuoq4Ow0lrS1znNnKJeQmRzYAFU8bhqgnTKdrrwBRjJgQHaJs2h61I4:5AN09aS1zNaqUldYBVJmJtFRspsXEhX |
MALICIOUS
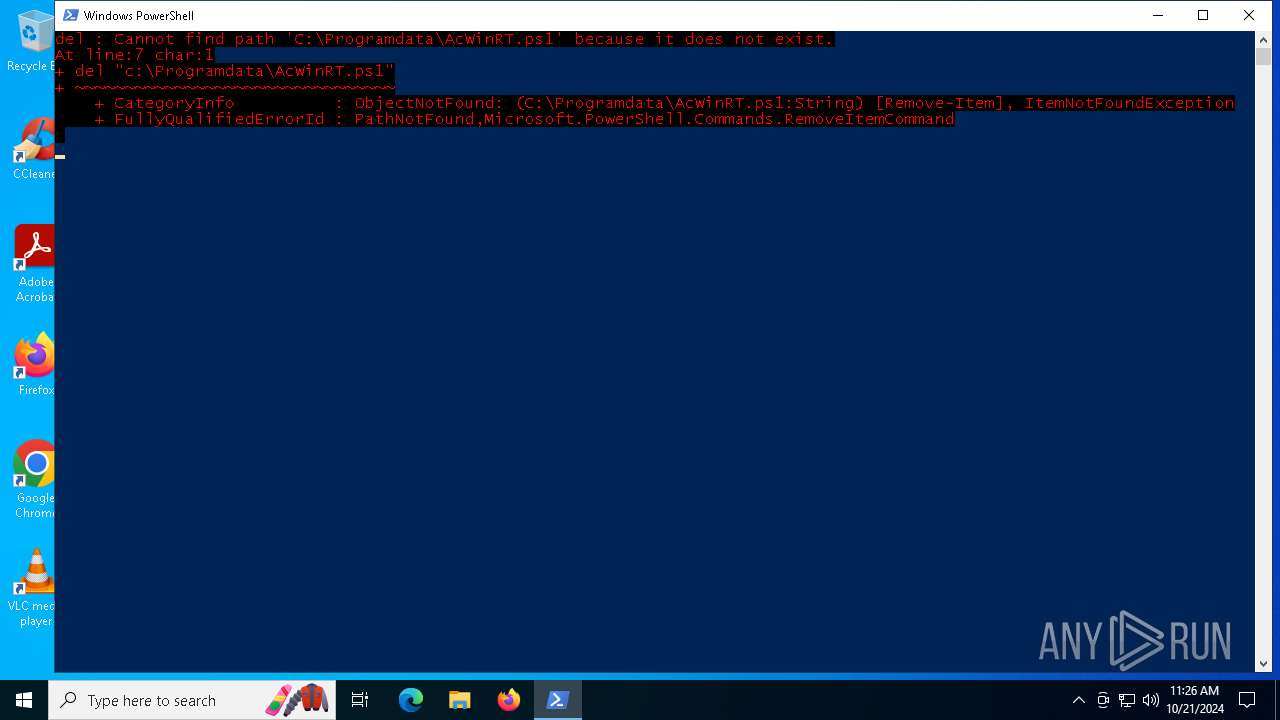
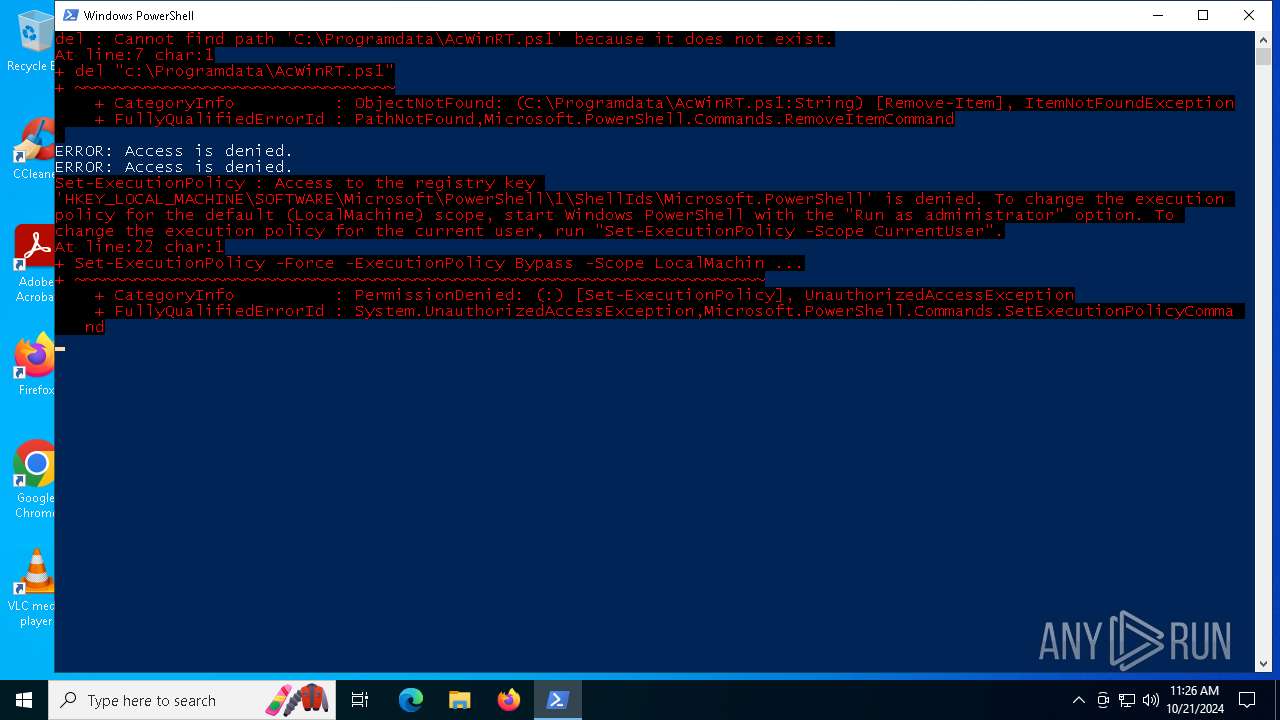
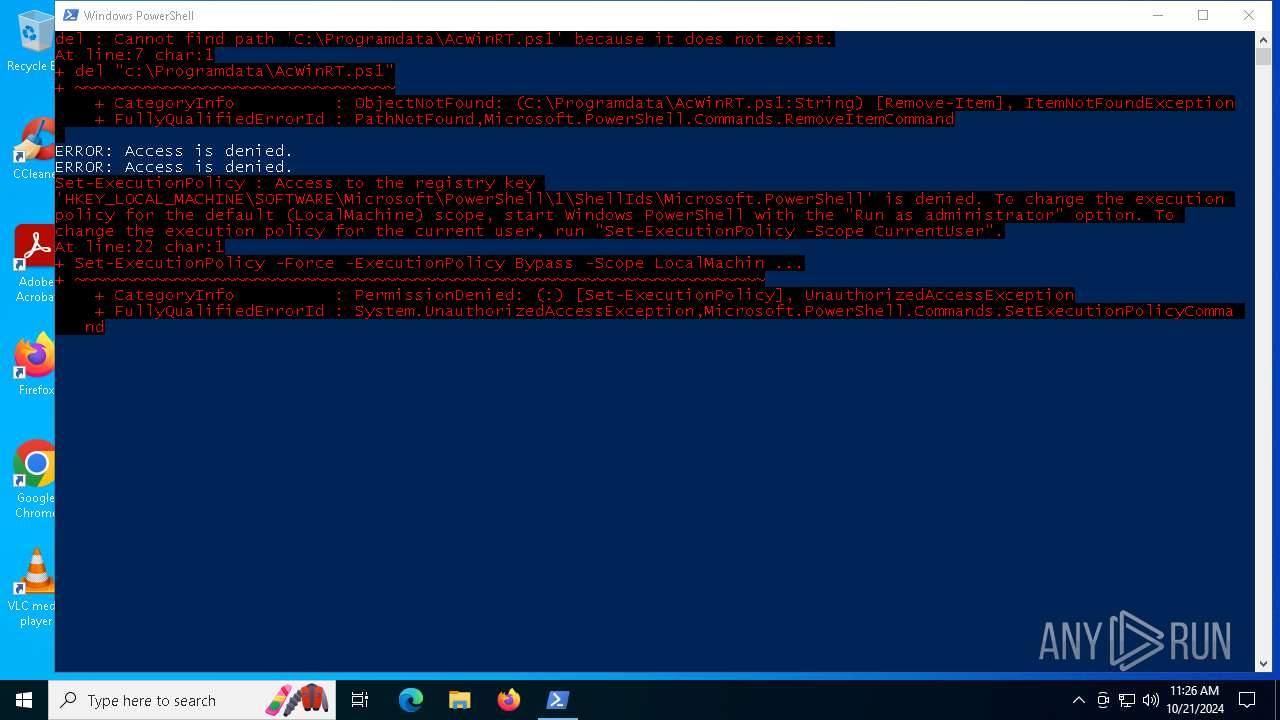
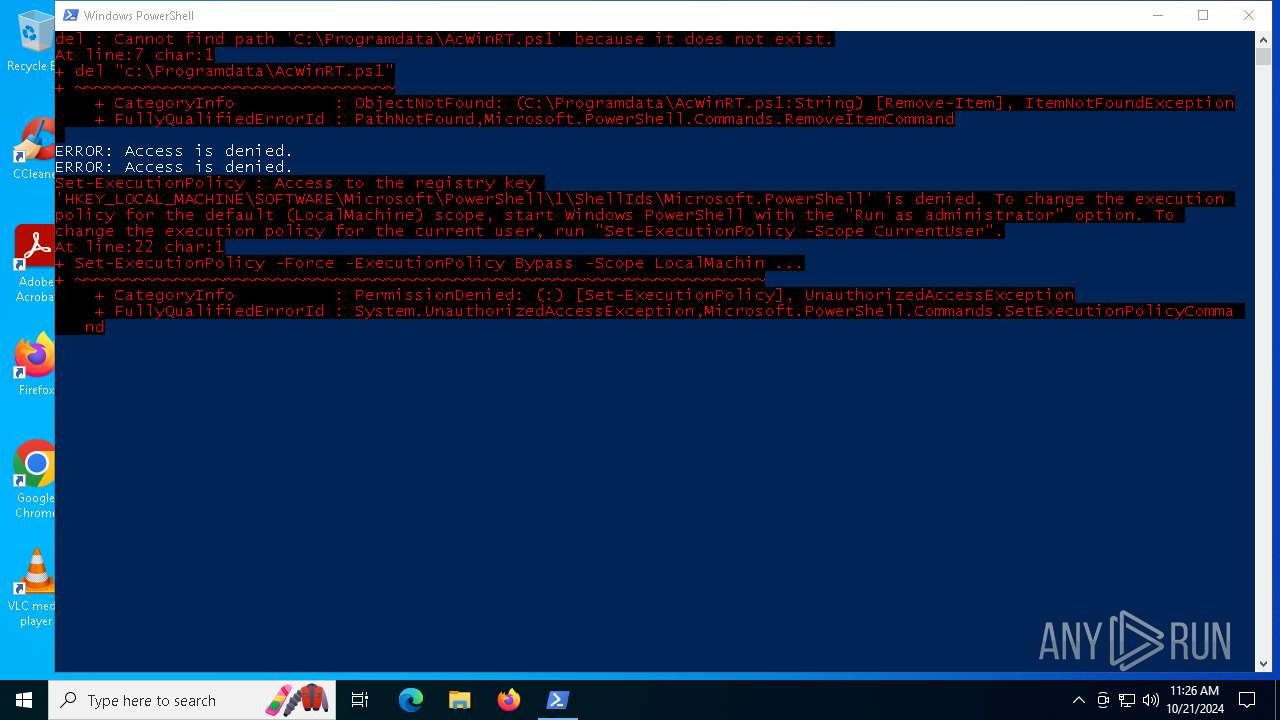
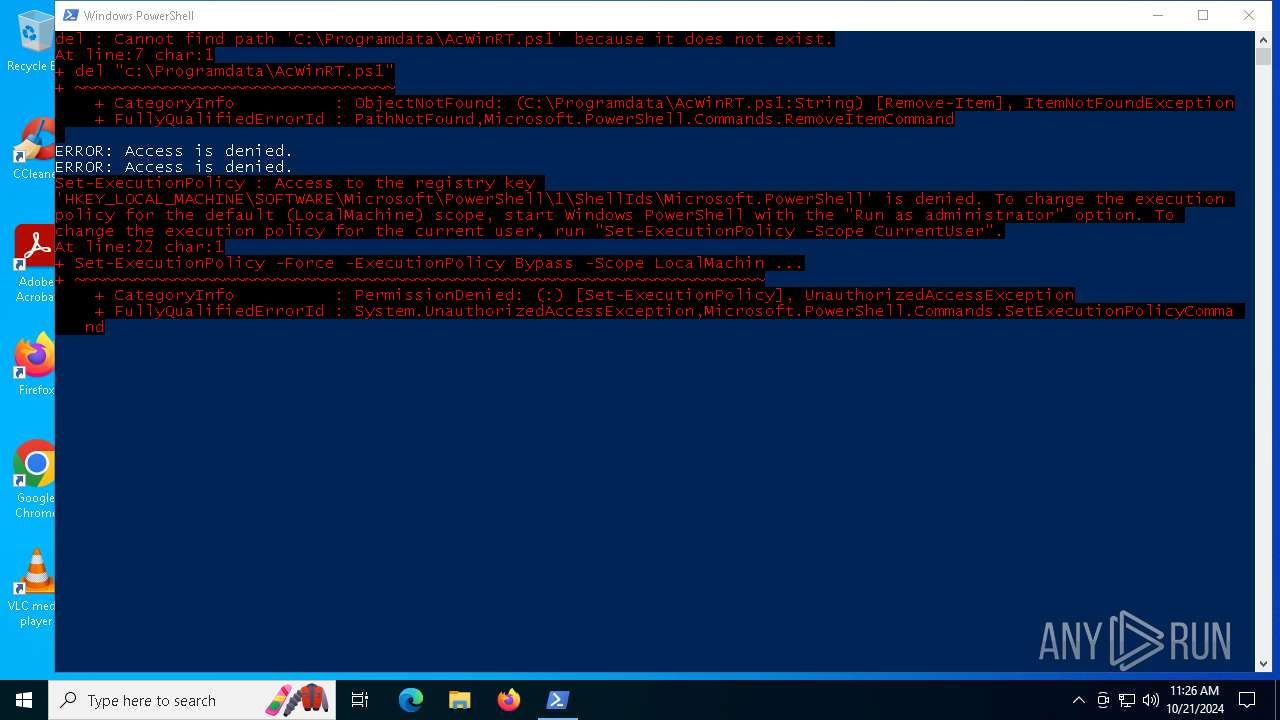
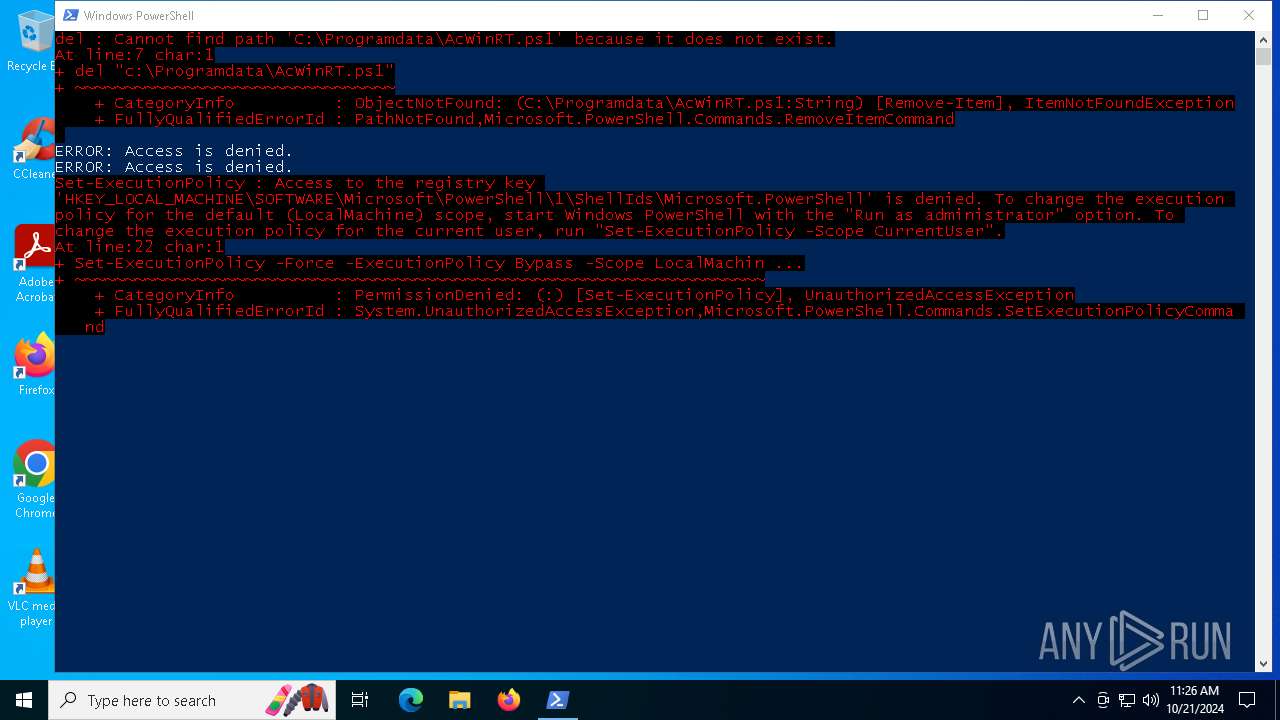
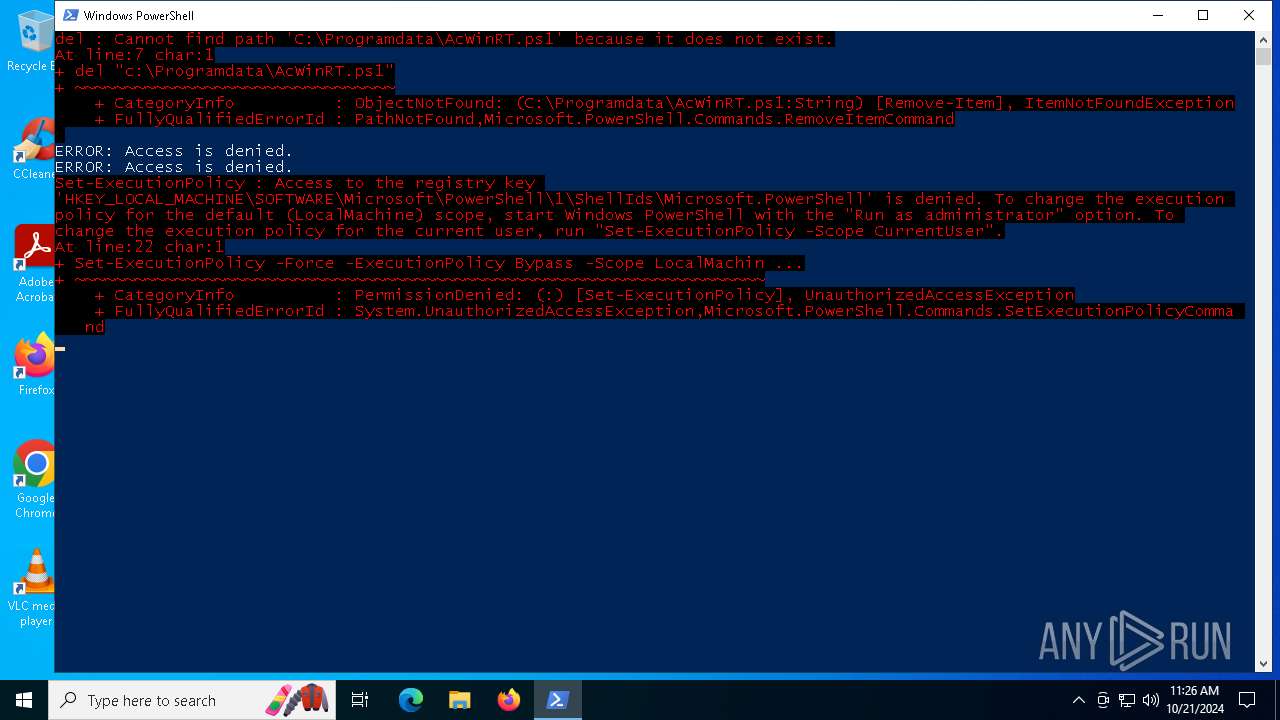
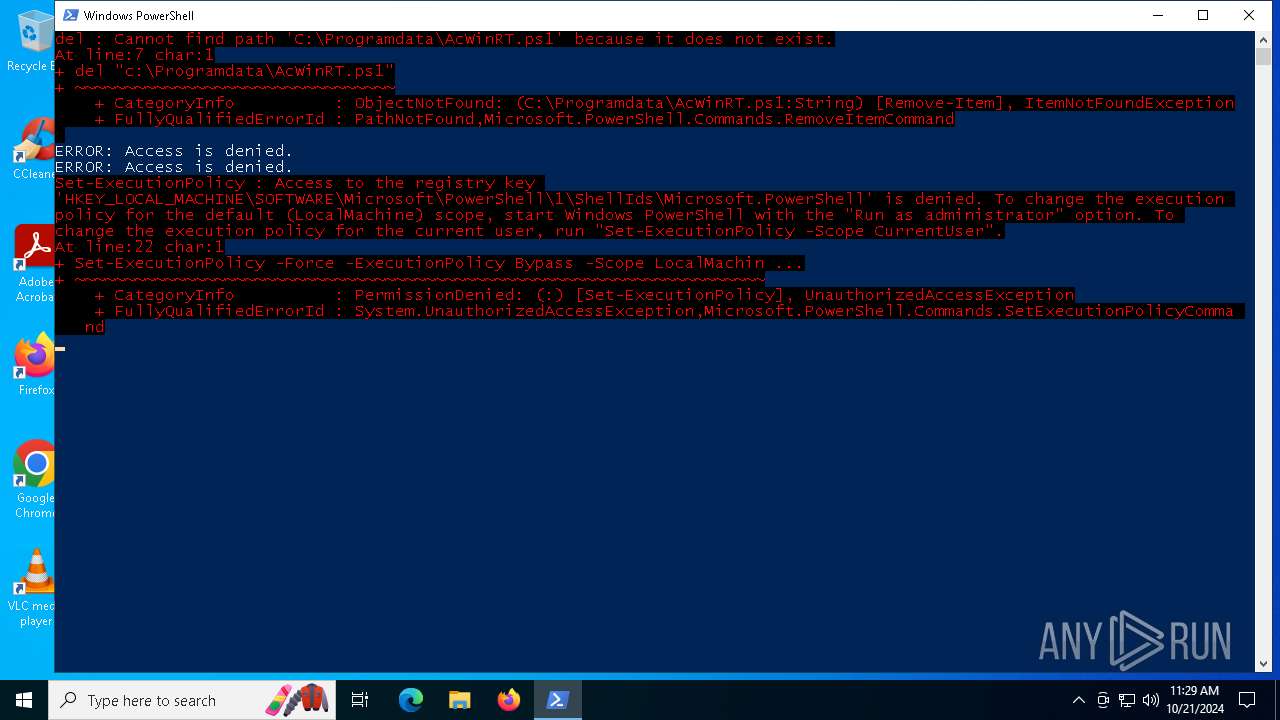
Bypass execution policy to execute commands
- powershell.exe (PID: 5172)
- powershell.exe (PID: 1784)
- powershell.exe (PID: 5444)
- powershell.exe (PID: 7964)
- powershell.exe (PID: 7856)
- powershell.exe (PID: 8064)
- powershell.exe (PID: 7952)
- powershell.exe (PID: 4548)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 4436)
- powershell.exe (PID: 6244)
Changes powershell execution policy (Bypass)
- AcWinRT.exe (PID: 6132)
- powershell.exe (PID: 1784)
Run PowerShell with an invisible window
- powershell.exe (PID: 5444)
- powershell.exe (PID: 7952)
- powershell.exe (PID: 4548)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 4436)
- powershell.exe (PID: 7964)
- powershell.exe (PID: 7856)
- powershell.exe (PID: 8064)
- powershell.exe (PID: 6244)
Deletes shadow copies
- powershell.exe (PID: 7952)
SUSPICIOUS
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 5172)
- powershell.exe (PID: 5444)
Executable content was dropped or overwritten
- powershell.exe (PID: 5172)
Starts POWERSHELL.EXE for commands execution
- AcWinRT.exe (PID: 6132)
- powershell.exe (PID: 1784)
The process executes Powershell scripts
- AcWinRT.exe (PID: 6132)
- powershell.exe (PID: 1784)
The process hide an interactive prompt from the user
- powershell.exe (PID: 1784)
Application launched itself
- powershell.exe (PID: 1784)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 1784)
Likely accesses (executes) a file from the Public directory
- icacls.exe (PID: 7948)
- icacls.exe (PID: 7188)
Uses ICACLS.EXE to modify access control lists
- powershell.exe (PID: 1568)
INFO
UPX packer has been detected
- AcWinRT.exe (PID: 6132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
1 050
Monitored processes
178
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | "C:\Windows\system32\icacls.exe" "X:\*" /grant Everyone:F /q /t /c | C:\Windows\SysWOW64\icacls.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 764 | "C:\WINDOWS\system32\reg.exe" add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender" /f /v DisableAntiSpyware /t REG_DWORD /d 1 | C:\Windows\SysWOW64\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 784 | "C:\WINDOWS\system32\reg.exe" add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender" /f /v DisableAntiSpyware /t REG_DWORD /d 1 | C:\Windows\SysWOW64\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 860 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Exit code: 4294967295 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 1376 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | "C:\WINDOWS\system32\reg.exe" add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender" /f /v DisableAntiSpyware /t REG_DWORD /d 1 | C:\Windows\SysWOW64\reg.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1568 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -w 1 -noninteractive -noprofile -file c:\programdata\APP002.ps1 | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | "C:\WINDOWS\system32\Dism.exe" /online /Disable-Feature /FeatureName:Windows-Defender /Remove /NoRestart /quiet | C:\Windows\SysWOW64\Dism.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Dism Image Servicing Utility Exit code: 740 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1744 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1784 | powershell -exec bypass -file c:\programdata\APP01.ps1 | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | AcWinRT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
54 682
Read events
54 682
Write events
0
Delete events
0
Modification events
Executable files
22
Suspicious files
3 077
Text files
638
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1784 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tje5kvmg.51g.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1784 | powershell.exe | C:\ProgramData\APP001.ps1 | text | |
MD5:6F03D204ECBEF764F94134A0C16580C8 | SHA256:8A22063B69F23F5FBAD3668730E85724EC4DC323790547D2DB4BA06B6A5F8BD0 | |||
| 5172 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ovmok4bp.py5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1784 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kwojsmhr.dxn.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5172 | powershell.exe | C:\ProgramData\icon.ico | image | |
MD5:51A4696865C6E6818EA4404F45A4639C | SHA256:36C84C4D00651D44857F7D8429365B7884821935382C39030934C893D37CE963 | |||
| 5172 | powershell.exe | C:\ProgramData\AcWinRT.exe | executable | |
MD5:D76F118CC37D5F297F651292ADFA4B93 | SHA256:0197970F61EFE6F979C47FD88872CB7D4B6ADE0C417AFD11C398FA9CDF909D7A | |||
| 1784 | powershell.exe | C:\ProgramData\APP004.ps1 | text | |
MD5:176F2A1FEE1A3E303A151213EE45D539 | SHA256:4474E7659A55601F123108403D4EBA63D4A711F02ABDC3A0A21BFA13760A4149 | |||
| 6132 | AcWinRT.exe | C:\ProgramData\APP01.ps1 | text | |
MD5:A5F8678EE153269F935C0122467B4F60 | SHA256:4E06431085633A902C835F1033A7C073930835A9BA0A495770591BBF3C2AA621 | |||
| 1784 | powershell.exe | C:\ProgramData\APP002.ps1 | text | |
MD5:0207CF65889CF4D2ED8CE98154A9E170 | SHA256:670E6989D3956C72E462D81C28D2806402B93131FFB4D431C1BDE1D95567DD57 | |||
| 1784 | powershell.exe | C:\ProgramData\APP005.ps1 | text | |
MD5:17018703B44CC9C30953432D0889E681 | SHA256:C9DBB10B14F69A0C7E345A575C7352CB714C460A26043C55572A46BFA9F313EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
80
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5824 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.33.209.121:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8124 | SIHClient.exe | GET | 200 | 23.212.193.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8124 | SIHClient.exe | GET | 200 | 23.212.193.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4360 | SearchApp.exe | 2.16.110.120:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.33.209.121:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5824 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5824 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |