| File name: | AntiPublic v1.0.10.zip |
| Full analysis: | https://app.any.run/tasks/e0b924f8-6fb7-4200-bc87-7d10ab933afd |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2023, 15:45:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | B0BCF6975ECBFE7541EADABCB400C173 |
| SHA1: | 11EF0364A8C5F2B0C170B403F57184452467C501 |
| SHA256: | 2E9E2A7F2B5C413072AF154915637B48029F6859D49E933D727D1B6057FA40A0 |
| SSDEEP: | 98304:I0++PjY4lJFH4ybCxlTn2py6xyBG5Ksx8OvgU3y3iq8CzImzxm5l0zbD+BbRy0B4:4uY4lbrboncxyBG5plvgZyWzF45mbDkA |
MALICIOUS
Application was dropped or rewritten from another process
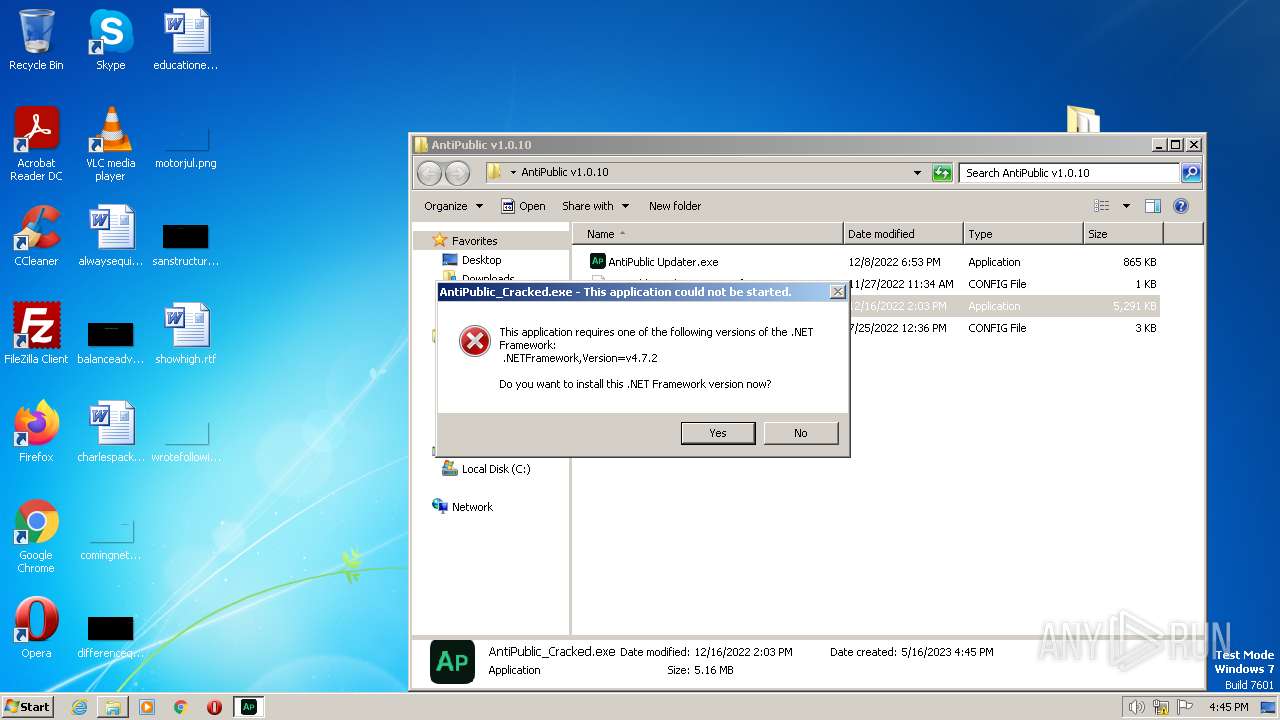
- AntiPublic_Cracked.exe (PID: 2744)
- ndp481-web.exe (PID: 1572)
- ndp481-web.exe (PID: 3924)
SUSPICIOUS
Reads the Internet Settings
- AntiPublic_Cracked.exe (PID: 2744)
Executable content was dropped or overwritten
- ndp481-web.exe (PID: 1572)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3932)
- iexplore.exe (PID: 3660)
- iexplore.exe (PID: 3576)
Application launched itself
- iexplore.exe (PID: 3576)
Create files in a temporary directory
- iexplore.exe (PID: 3576)
- ndp481-web.exe (PID: 1572)
- Setup.exe (PID: 2076)
The process uses the downloaded file
- iexplore.exe (PID: 3576)
Reads the computer name
- ndp481-web.exe (PID: 1572)
- Setup.exe (PID: 2076)
- AntiPublic_Cracked.exe (PID: 2744)
The process checks LSA protection
- ndp481-web.exe (PID: 1572)
- Setup.exe (PID: 2076)
Reads the machine GUID from the registry
- ndp481-web.exe (PID: 1572)
- Setup.exe (PID: 2076)
Checks supported languages
- ndp481-web.exe (PID: 1572)
- AntiPublic_Cracked.exe (PID: 2744)
- Setup.exe (PID: 2076)
Manual execution by a user
- AntiPublic_Cracked.exe (PID: 2744)
- AntiPublic_Cracked.exe (PID: 3772)
Reads Environment values
- Setup.exe (PID: 2076)
Reads CPU info
- Setup.exe (PID: 2076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | AntiPublic v1.0.10/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2022:12:16 17:04:16 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
48
Monitored processes
8
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1572 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\ndp481-web.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\ndp481-web.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.8.1 Setup Exit code: 5100 Version: 4.8.09037.06 Modules
| |||||||||||||||
| 2076 | C:\5d1392298e3df0a8a048cf7467f9\\Setup.exe /x86 /x64 /web | C:\5d1392298e3df0a8a048cf7467f9\Setup.exe | ndp481-web.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Installer Exit code: 5100 Version: 14.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
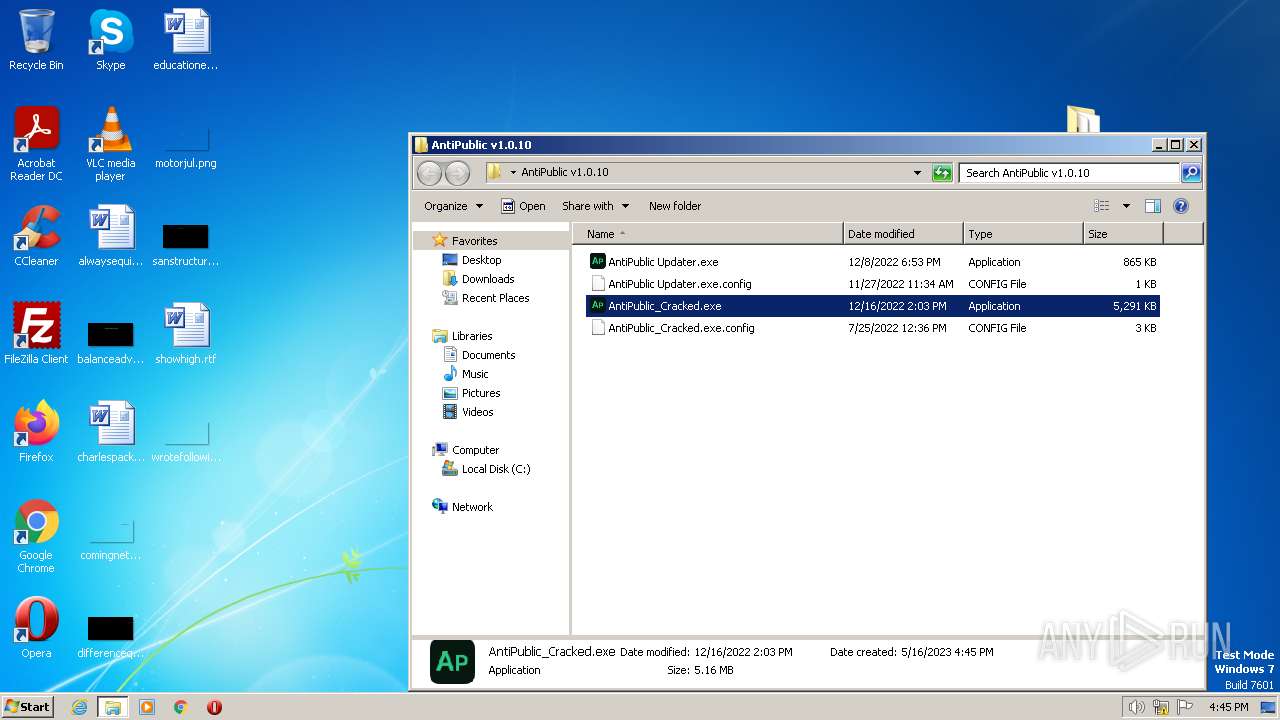
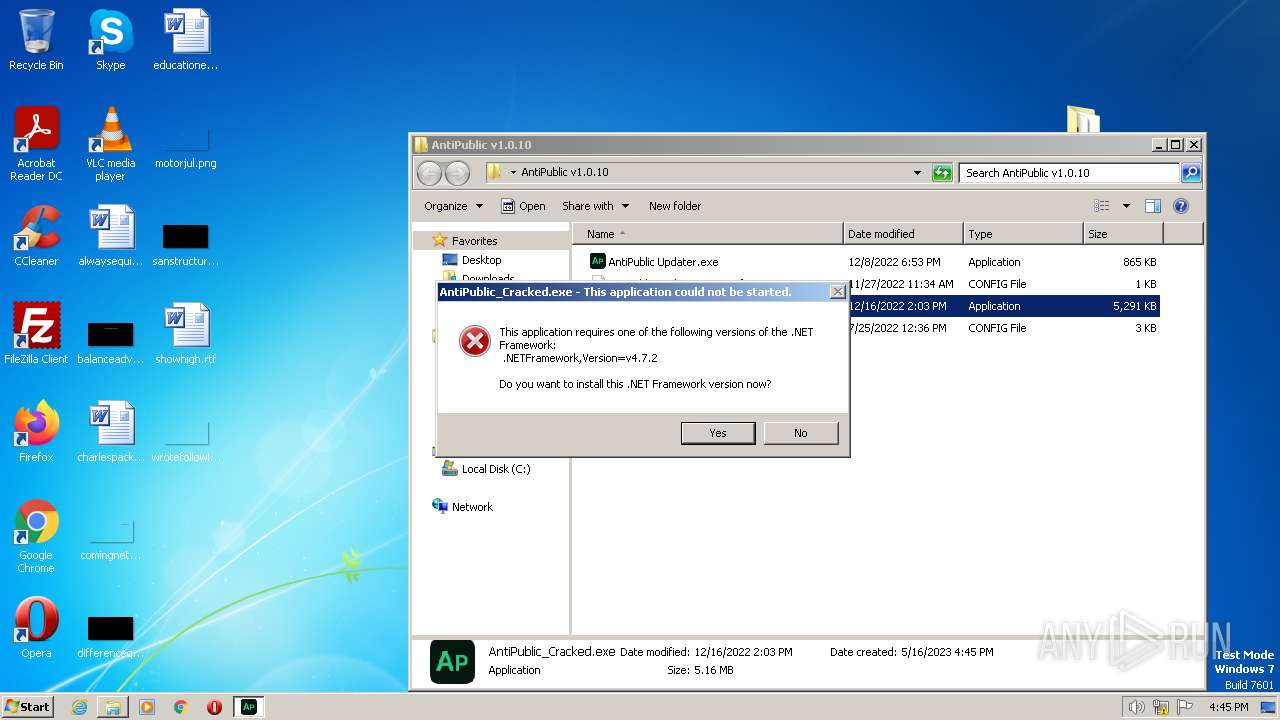
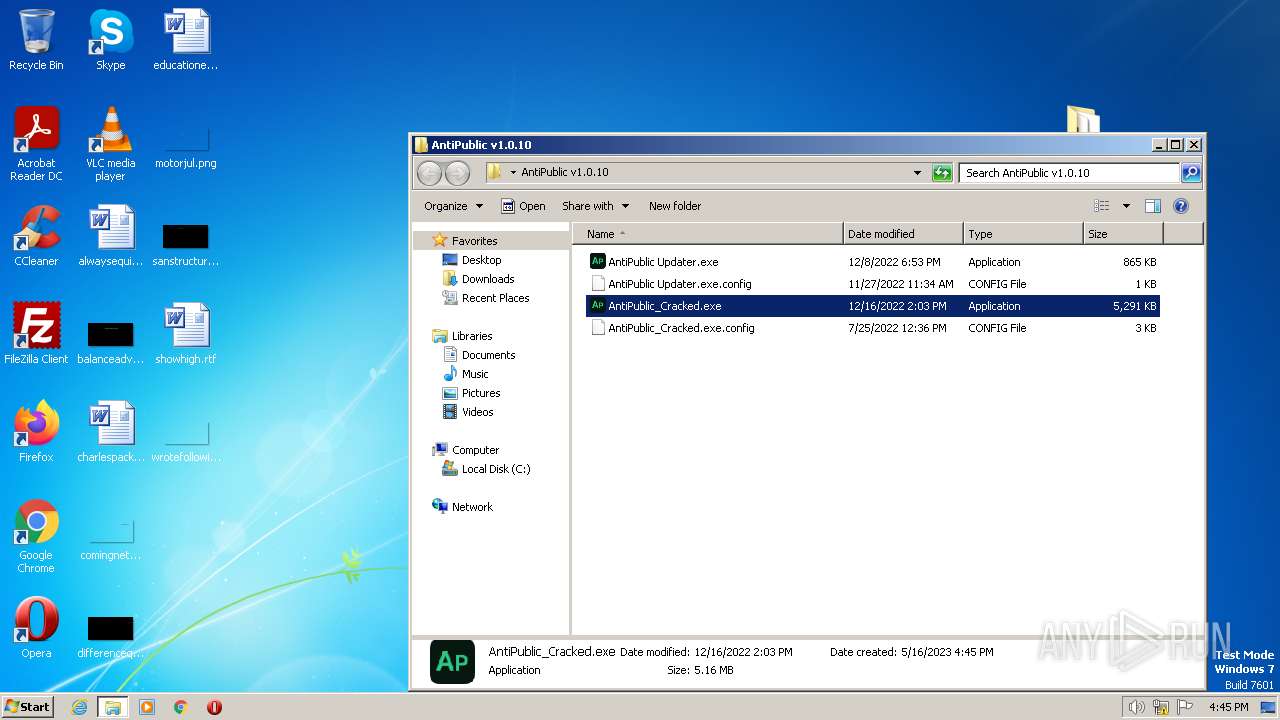
| 2744 | "C:\Users\admin\Desktop\AntiPublic v1.0.10\AntiPublic_Cracked.exe" | C:\Users\admin\Desktop\AntiPublic v1.0.10\AntiPublic_Cracked.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AntiPublic Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
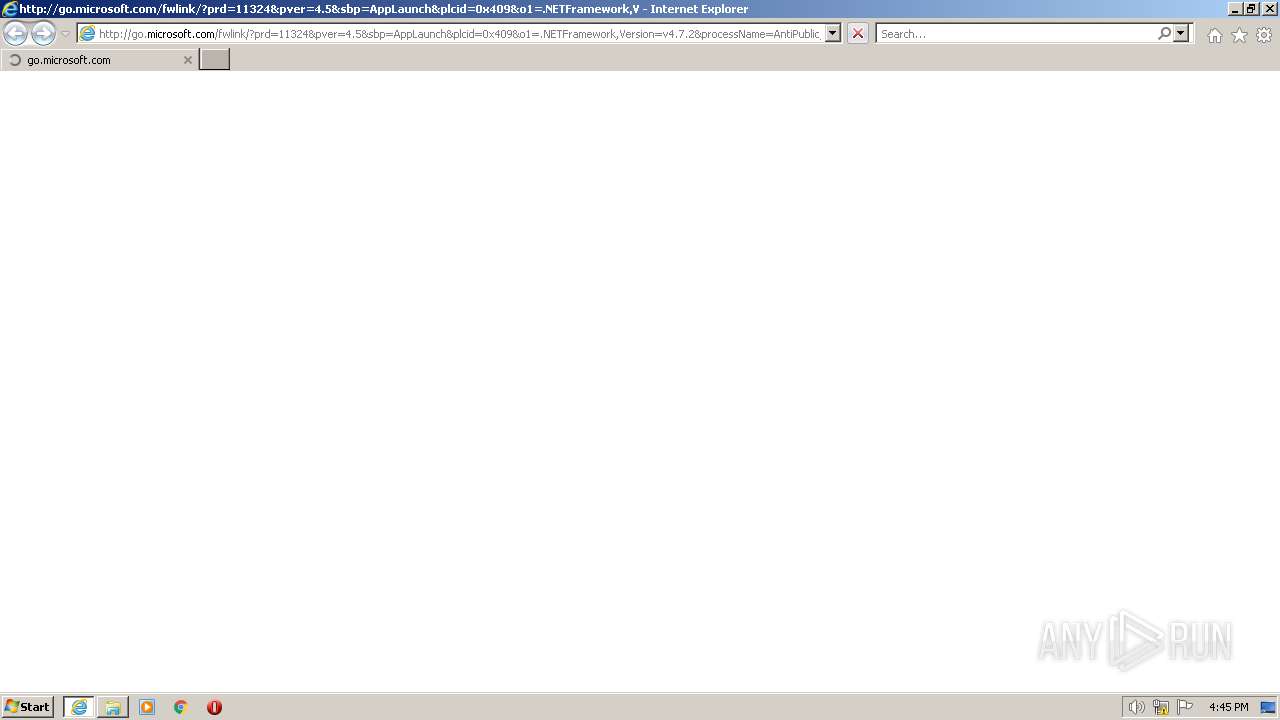
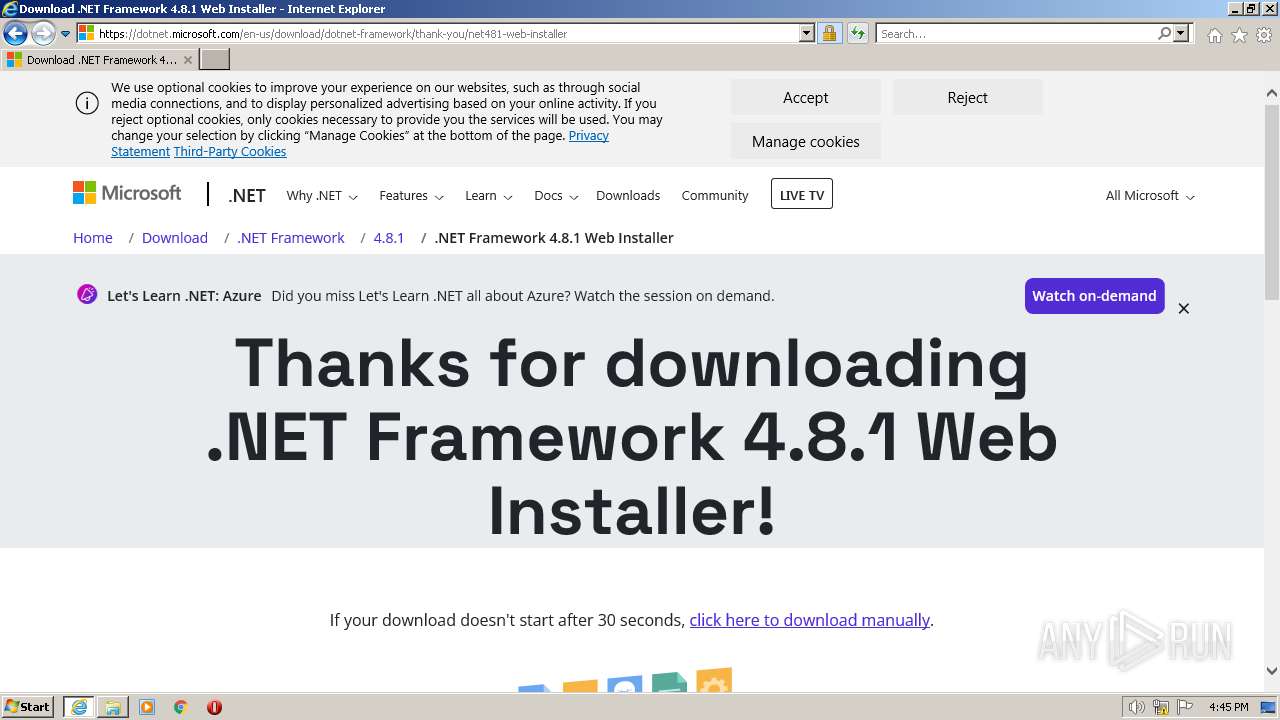
| 3576 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.7.2&processName=AntiPublic_Cracked.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.34209 | C:\Program Files\Internet Explorer\iexplore.exe | AntiPublic_Cracked.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3660 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3576 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3772 | "C:\Users\admin\Desktop\AntiPublic v1.0.10\AntiPublic_Cracked.exe" | C:\Users\admin\Desktop\AntiPublic v1.0.10\AntiPublic_Cracked.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: AntiPublic Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3924 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\ndp481-web.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\ndp481-web.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework 4.8.1 Setup Exit code: 3221226540 Version: 4.8.09037.06 Modules
| |||||||||||||||
| 3932 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\AntiPublic v1.0.10.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
17 959
Read events
17 838
Write events
119
Delete events
2
Modification events
| (PID) Process: | (3932) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3932) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
34
Suspicious files
31
Text files
119
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3932.40513\AntiPublic v1.0.10\AntiPublic Updater.exe | executable | |
MD5:841A41E90F4BBFE3D88FDEC50170E15A | SHA256:A3C3AC5CA3951A328313A470C05BE338E98241C0550979C76DE2636E57E0A354 | |||
| 3932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3932.40513\AntiPublic v1.0.10\AntiPublic Updater.exe.config | xml | |
MD5:21FA0B1D75C0CC7369F1E735FE90C7A9 | SHA256:AD8267122C40D37DCD9D99E1412D763187A1825732F378DB8867F3ECF675CF70 | |||
| 3932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3932.40513\AntiPublic v1.0.10\AntiPublic_Cracked.exe | executable | |
MD5:0301FEA7EA4F3EB6B33D8871F571B26B | SHA256:A7E3C19AEB39D2B59A1146D453855E9D5E1380059EF0305ACFB848F91B41E946 | |||
| 3932 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3932.40513\AntiPublic v1.0.10\AntiPublic_Cracked.exe.config | xml | |
MD5:118F2B6D9E075377768657EDD559AB33 | SHA256:0C018550072A98A38A61365510AC98952BA3878143DF31989E719EE1DA7FC38A | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:1B03804CACDCD4FBDAD96158262B71B1 | SHA256:7316FAC3616A4561D19819657E435040CEA3AFF5D5C8B2449104C8CE2C3C7AAC | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C0427F5F77D9B3A439FC620EDAAB6177 | der | |
MD5:2314C549CA2F3EF3CC259C954966802D | SHA256:D2831170E2C7184DE9F6E30D0775E2659CF1DFD69C96DDF55F731EFBC50EF84E | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_E503B048B745DFA14B81FCFC68D6DECE | der | |
MD5:462CE8E9A1C194AB4E8AF231860847DF | SHA256:22BC2A970E7C4AA80370CB43733802704C3393330B39C9908DF72DA9AC564278 | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\net481[1].htm | html | |
MD5:96B4C01A2F6E092279117C42557B82B7 | SHA256:252330C91BB3AE182AABBD1E183218C4D56161473D0F24426F9825A95F27BB94 | |||
| 3660 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_AD319D6DA1A11BC83AC8B4E4D3638231 | binary | |
MD5:6E4BFB1228B6A2C0BF3BD0E72B985E0E | SHA256:0D7EAA65AA5C28C246A1DB1F3708FA185CB5EAB699D0DD1AECAC87A977FC4EE1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
37
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3660 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | US | binary | 471 b | whitelisted |
3660 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?062b0104441894b8 | US | compressed | 4.70 Kb | whitelisted |
3660 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | binary | 471 b | whitelisted |
3576 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | binary | 1.47 Kb | whitelisted |
3660 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?06f9af50452a25c6 | US | compressed | 4.70 Kb | whitelisted |
3660 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | binary | 471 b | whitelisted |
3660 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
3660 | iexplore.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRS%2FsoQjbTlq1Jokw0nyC%2FyFeJLtQQUAKuR%2FCFiJpeaqHkbYUGQYKliZ%2F0CEzMAftU9k32SHztW2swAAAB%2B1T0%3D | US | binary | 1.74 Kb | whitelisted |
3660 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | binary | 471 b | whitelisted |
3660 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3372 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3660 | iexplore.exe | 104.102.40.139:443 | go.microsoft.com | AKAMAI-AS | DE | malicious |
3660 | iexplore.exe | 23.35.229.160:443 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3660 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3660 | iexplore.exe | 13.107.246.45:443 | dotnet.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | malicious |
3660 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3660 | iexplore.exe | 204.79.197.203:80 | oneocsp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
js.monitor.azure.com |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
wcpstatic.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
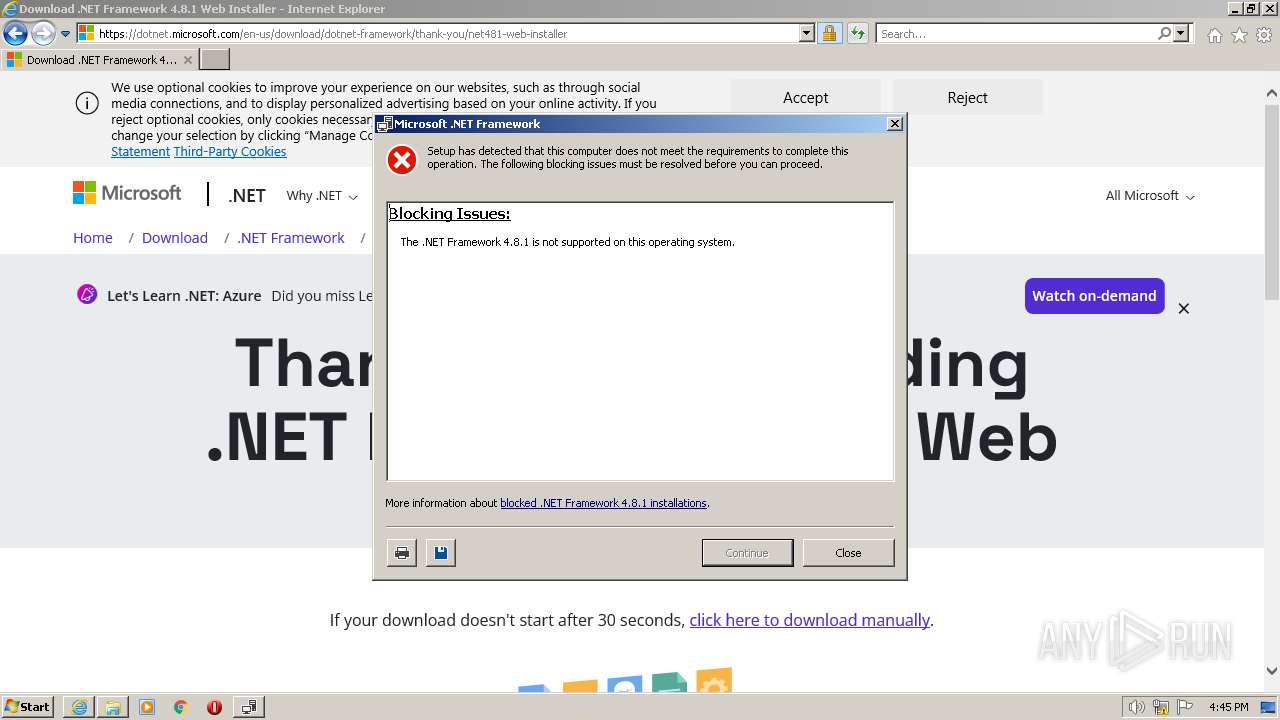
Setup.exe | A StopBlock was hit or a System Requirement was not met. |