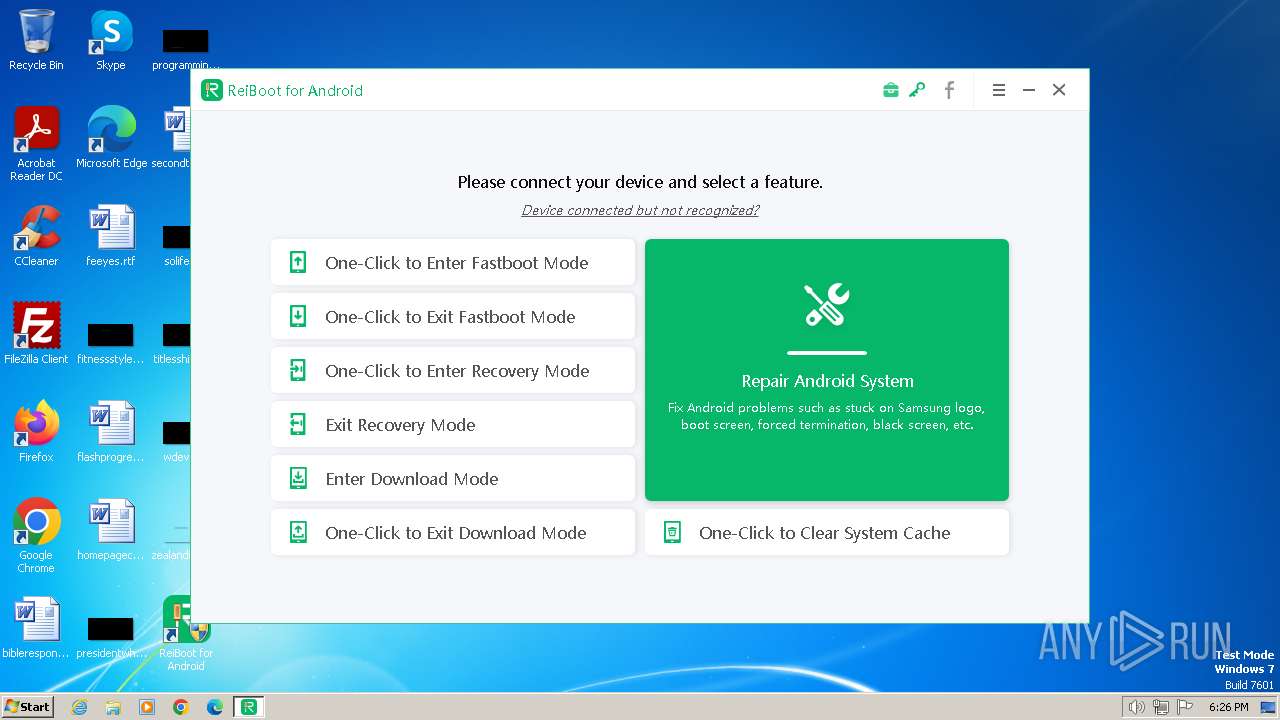
| File name: | reiboot-for-android.exe |
| Full analysis: | https://app.any.run/tasks/6594e5b6-0f39-4af7-b431-14f415ed3d6c |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2024, 18:22:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | DEB9A371B713547898A18A44BF2B2F89 |
| SHA1: | 1B00D97D1DF288BC7F0A0247A381043387D088D8 |
| SHA256: | 2E8B0749A2846D176BA40C52692CB84C772460C38E705214C0758CF8E41F7A03 |
| SSDEEP: | 98304:lSFLSo83jLaluX8+FPdcxsta+eI2X5eraGW40M1kuQ9/SLEjZFEXVjxgy9jj17HT:6eATI |
MALICIOUS
Drops the executable file immediately after the start
- reiboot-for-android.exe (PID: 3772)
- reibootforandroid_ts_2.1.21.exe (PID: 2904)
- ReibootForAndroid.exe (PID: 2244)
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
- DPInst32.exe (PID: 552)
- drvinst.exe (PID: 2376)
- drvinst.exe (PID: 2120)
- drvinst.exe (PID: 3456)
- drvinst.exe (PID: 3136)
- drvinst.exe (PID: 3100)
Connects to the CnC server
- reiboot-for-android.exe (PID: 3772)
Creates a writable file in the system directory
- drvinst.exe (PID: 2376)
- drvinst.exe (PID: 2120)
- drvinst.exe (PID: 3136)
- drvinst.exe (PID: 3456)
- drvinst.exe (PID: 3100)
SUSPICIOUS
Reads security settings of Internet Explorer
- reiboot-for-android.exe (PID: 3772)
- Start.exe (PID: 980)
- ReibootForAndroid.exe (PID: 2244)
Reads settings of System Certificates
- reiboot-for-android.exe (PID: 3772)
- ReibootForAndroid.exe (PID: 2244)
- rundll32.exe (PID: 784)
- rundll32.exe (PID: 3276)
Reads the Internet Settings
- reiboot-for-android.exe (PID: 3772)
- Start.exe (PID: 980)
- ReibootForAndroid.exe (PID: 2244)
Checks for external IP
- reiboot-for-android.exe (PID: 3772)
Checks Windows Trust Settings
- reiboot-for-android.exe (PID: 3772)
- drvinst.exe (PID: 2376)
- ReibootForAndroid.exe (PID: 2244)
- drvinst.exe (PID: 2120)
- drvinst.exe (PID: 3456)
- drvinst.exe (PID: 3136)
- drvinst.exe (PID: 3100)
Executable content was dropped or overwritten
- reibootforandroid_ts_2.1.21.exe (PID: 2904)
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
- ReibootForAndroid.exe (PID: 2244)
- DPInst32.exe (PID: 552)
- drvinst.exe (PID: 2376)
- drvinst.exe (PID: 2120)
- drvinst.exe (PID: 3136)
- drvinst.exe (PID: 3456)
- drvinst.exe (PID: 3100)
Reads the Windows owner or organization settings
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
Process drops legitimate windows executable
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
- DPInst32.exe (PID: 552)
- drvinst.exe (PID: 2376)
- drvinst.exe (PID: 2120)
- drvinst.exe (PID: 3136)
The process drops C-runtime libraries
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
Drops 7-zip archiver for unpacking
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
- ReibootForAndroid.exe (PID: 2244)
Drops a system driver (possible attempt to evade defenses)
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
- drvinst.exe (PID: 3456)
- DPInst32.exe (PID: 552)
- drvinst.exe (PID: 3100)
Process drops legitimate windows executable (CertUtil.exe)
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
Creates a software uninstall entry
- reiboot-for-android.exe (PID: 3772)
- ReibootForAndroid.exe (PID: 2244)
- DPInst32.exe (PID: 552)
Searches for installed software
- ReibootForAndroid.exe (PID: 2244)
Changes Internet Explorer settings (feature browser emulation)
- ReibootForAndroid.exe (PID: 2244)
Creates files in the driver directory
- drvinst.exe (PID: 2376)
- drvinst.exe (PID: 2120)
- drvinst.exe (PID: 3136)
- drvinst.exe (PID: 3456)
- drvinst.exe (PID: 3100)
Starts CMD.EXE for commands execution
- ReibootForAndroid.exe (PID: 2244)
Executes as Windows Service
- VSSVC.exe (PID: 2616)
Application launched itself
- adb.exe (PID: 2996)
- adb.exe (PID: 2928)
INFO
Reads the computer name
- reiboot-for-android.exe (PID: 3772)
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
- Start.exe (PID: 980)
- ReibootForAndroid.exe (PID: 2244)
- fastboot.exe (PID: 1540)
- fastboot.exe (PID: 924)
- drvinst.exe (PID: 2376)
- DPInst32.exe (PID: 552)
- fastboot.exe (PID: 2308)
- fastboot.exe (PID: 1652)
- fastboot.exe (PID: 1836)
- fastboot.exe (PID: 1632)
- fastboot.exe (PID: 3052)
- fastboot.exe (PID: 3684)
- fastboot.exe (PID: 2848)
- drvinst.exe (PID: 2120)
- fastboot.exe (PID: 1404)
- fastboot.exe (PID: 3260)
- fastboot.exe (PID: 2520)
- fastboot.exe (PID: 584)
- fastboot.exe (PID: 3752)
- fastboot.exe (PID: 1072)
- fastboot.exe (PID: 2380)
- drvinst.exe (PID: 3136)
- drvinst.exe (PID: 3456)
- fastboot.exe (PID: 3692)
- fastboot.exe (PID: 3164)
- drvinst.exe (PID: 3100)
- adb.exe (PID: 3608)
- adb.exe (PID: 3260)
- fastboot.exe (PID: 2520)
- fastboot.exe (PID: 3440)
- fastboot.exe (PID: 2160)
- fastboot.exe (PID: 2980)
- fastboot.exe (PID: 2016)
- fastboot.exe (PID: 1172)
- fastboot.exe (PID: 3900)
- fastboot.exe (PID: 2652)
- wmpnscfg.exe (PID: 2032)
- fastboot.exe (PID: 3396)
- fastboot.exe (PID: 3140)
- fastboot.exe (PID: 2440)
- fastboot.exe (PID: 1652)
- fastboot.exe (PID: 584)
- fastboot.exe (PID: 1072)
- fastboot.exe (PID: 2980)
- fastboot.exe (PID: 2136)
- fastboot.exe (PID: 3656)
- fastboot.exe (PID: 1424)
- fastboot.exe (PID: 1936)
- fastboot.exe (PID: 3536)
- fastboot.exe (PID: 3396)
- fastboot.exe (PID: 1192)
- fastboot.exe (PID: 2332)
- fastboot.exe (PID: 3052)
- fastboot.exe (PID: 3244)
- fastboot.exe (PID: 3612)
- fastboot.exe (PID: 3824)
- fastboot.exe (PID: 3076)
- fastboot.exe (PID: 3876)
- fastboot.exe (PID: 1636)
- fastboot.exe (PID: 2648)
- fastboot.exe (PID: 1344)
- fastboot.exe (PID: 3256)
- fastboot.exe (PID: 2844)
- fastboot.exe (PID: 2032)
- fastboot.exe (PID: 2572)
- fastboot.exe (PID: 3996)
- fastboot.exe (PID: 116)
- fastboot.exe (PID: 3200)
- fastboot.exe (PID: 2476)
- fastboot.exe (PID: 2268)
- fastboot.exe (PID: 3032)
- fastboot.exe (PID: 980)
- fastboot.exe (PID: 2232)
- fastboot.exe (PID: 2068)
- fastboot.exe (PID: 3000)
- fastboot.exe (PID: 924)
- fastboot.exe (PID: 2104)
- fastboot.exe (PID: 3232)
- fastboot.exe (PID: 908)
- fastboot.exe (PID: 2020)
- fastboot.exe (PID: 2592)
- fastboot.exe (PID: 3496)
- fastboot.exe (PID: 2788)
- fastboot.exe (PID: 2108)
- fastboot.exe (PID: 4012)
- fastboot.exe (PID: 4048)
- fastboot.exe (PID: 1628)
- fastboot.exe (PID: 3232)
- fastboot.exe (PID: 4008)
- fastboot.exe (PID: 3536)
- fastboot.exe (PID: 1836)
- fastboot.exe (PID: 452)
- fastboot.exe (PID: 3652)
- fastboot.exe (PID: 2572)
- fastboot.exe (PID: 2096)
- fastboot.exe (PID: 1352)
- fastboot.exe (PID: 3936)
- fastboot.exe (PID: 1860)
- fastboot.exe (PID: 2892)
- fastboot.exe (PID: 3740)
- fastboot.exe (PID: 1072)
- fastboot.exe (PID: 3036)
- fastboot.exe (PID: 4088)
- fastboot.exe (PID: 1576)
- fastboot.exe (PID: 2848)
- fastboot.exe (PID: 1352)
- fastboot.exe (PID: 1932)
- fastboot.exe (PID: 3372)
- fastboot.exe (PID: 2424)
- fastboot.exe (PID: 3040)
- fastboot.exe (PID: 1812)
- fastboot.exe (PID: 1264)
- fastboot.exe (PID: 1792)
- fastboot.exe (PID: 3256)
- fastboot.exe (PID: 2292)
- fastboot.exe (PID: 3068)
- fastboot.exe (PID: 1316)
- fastboot.exe (PID: 3820)
- fastboot.exe (PID: 2580)
- fastboot.exe (PID: 2744)
- fastboot.exe (PID: 2532)
- fastboot.exe (PID: 3476)
- fastboot.exe (PID: 2892)
- fastboot.exe (PID: 3432)
- fastboot.exe (PID: 876)
- fastboot.exe (PID: 3412)
- fastboot.exe (PID: 1056)
- fastboot.exe (PID: 3840)
- fastboot.exe (PID: 1784)
- fastboot.exe (PID: 3932)
- fastboot.exe (PID: 2752)
- fastboot.exe (PID: 2372)
- fastboot.exe (PID: 548)
- fastboot.exe (PID: 3536)
- fastboot.exe (PID: 3584)
- fastboot.exe (PID: 2448)
- fastboot.exe (PID: 452)
- fastboot.exe (PID: 3492)
- fastboot.exe (PID: 3664)
- fastboot.exe (PID: 3780)
- fastboot.exe (PID: 2832)
- fastboot.exe (PID: 3836)
- fastboot.exe (PID: 2788)
- fastboot.exe (PID: 2036)
- fastboot.exe (PID: 3448)
- fastboot.exe (PID: 3728)
- fastboot.exe (PID: 2072)
- fastboot.exe (PID: 3476)
- fastboot.exe (PID: 3548)
- fastboot.exe (PID: 2088)
- fastboot.exe (PID: 3944)
- fastboot.exe (PID: 3460)
- fastboot.exe (PID: 2976)
- fastboot.exe (PID: 2376)
- fastboot.exe (PID: 696)
- fastboot.exe (PID: 3268)
- fastboot.exe (PID: 3740)
- fastboot.exe (PID: 680)
- fastboot.exe (PID: 1368)
- fastboot.exe (PID: 3000)
- fastboot.exe (PID: 4052)
- fastboot.exe (PID: 3484)
- fastboot.exe (PID: 1652)
- fastboot.exe (PID: 2636)
- fastboot.exe (PID: 2568)
- fastboot.exe (PID: 2688)
- fastboot.exe (PID: 3240)
- fastboot.exe (PID: 1112)
- fastboot.exe (PID: 3516)
- fastboot.exe (PID: 4024)
- fastboot.exe (PID: 1848)
- fastboot.exe (PID: 2512)
- fastboot.exe (PID: 3008)
- fastboot.exe (PID: 3768)
- fastboot.exe (PID: 1544)
- fastboot.exe (PID: 2052)
- fastboot.exe (PID: 3704)
- fastboot.exe (PID: 3228)
- fastboot.exe (PID: 2156)
- fastboot.exe (PID: 1900)
- fastboot.exe (PID: 1020)
- fastboot.exe (PID: 1424)
- fastboot.exe (PID: 2228)
- fastboot.exe (PID: 3256)
- fastboot.exe (PID: 2096)
- fastboot.exe (PID: 3308)
- fastboot.exe (PID: 2500)
- fastboot.exe (PID: 3212)
- fastboot.exe (PID: 2736)
- fastboot.exe (PID: 3820)
- fastboot.exe (PID: 1976)
- fastboot.exe (PID: 2136)
- fastboot.exe (PID: 3180)
- fastboot.exe (PID: 2036)
- fastboot.exe (PID: 1624)
- fastboot.exe (PID: 3140)
- fastboot.exe (PID: 2892)
- fastboot.exe (PID: 4004)
- fastboot.exe (PID: 1772)
- fastboot.exe (PID: 4080)
- fastboot.exe (PID: 3432)
- fastboot.exe (PID: 1560)
- fastboot.exe (PID: 1852)
- fastboot.exe (PID: 3460)
- fastboot.exe (PID: 2308)
- fastboot.exe (PID: 1832)
- fastboot.exe (PID: 1928)
- fastboot.exe (PID: 3236)
- fastboot.exe (PID: 4012)
- fastboot.exe (PID: 2980)
- fastboot.exe (PID: 3960)
- fastboot.exe (PID: 2052)
- fastboot.exe (PID: 3472)
- fastboot.exe (PID: 3148)
- fastboot.exe (PID: 240)
- fastboot.exe (PID: 3672)
- fastboot.exe (PID: 884)
- fastboot.exe (PID: 4072)
- fastboot.exe (PID: 3664)
- fastboot.exe (PID: 3668)
Checks proxy server information
- reiboot-for-android.exe (PID: 3772)
- ReibootForAndroid.exe (PID: 2244)
Checks supported languages
- reiboot-for-android.exe (PID: 3772)
- reibootforandroid_ts_2.1.21.exe (PID: 2904)
- ReibootForAndroid.exe (PID: 2244)
- Start.exe (PID: 980)
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
- fastboot.exe (PID: 1540)
- InstallAndDriver.exe (PID: 3556)
- repair.exe (PID: 296)
- fastboot.exe (PID: 924)
- DPInst32.exe (PID: 552)
- drvinst.exe (PID: 2376)
- fastboot.exe (PID: 2308)
- fastboot.exe (PID: 1652)
- fastboot.exe (PID: 3684)
- fastboot.exe (PID: 1836)
- fastboot.exe (PID: 3052)
- fastboot.exe (PID: 1632)
- fastboot.exe (PID: 2848)
- drvinst.exe (PID: 2120)
- fastboot.exe (PID: 1404)
- fastboot.exe (PID: 3260)
- fastboot.exe (PID: 2520)
- fastboot.exe (PID: 3752)
- fastboot.exe (PID: 584)
- fastboot.exe (PID: 1072)
- drvinst.exe (PID: 3136)
- fastboot.exe (PID: 2380)
- drvinst.exe (PID: 3456)
- fastboot.exe (PID: 3692)
- drvinst.exe (PID: 3100)
- adb.exe (PID: 2996)
- fastboot.exe (PID: 3164)
- adb.exe (PID: 2928)
- fastboot.exe (PID: 2520)
- fastboot.exe (PID: 3440)
- adb.exe (PID: 4028)
- fastboot.exe (PID: 2160)
- adb.exe (PID: 4016)
- adb.exe (PID: 3608)
- adb.exe (PID: 3260)
- adb.exe (PID: 3216)
- fastboot.exe (PID: 2980)
- adb.exe (PID: 1112)
- fastboot.exe (PID: 3396)
- fastboot.exe (PID: 3900)
- fastboot.exe (PID: 1172)
- fastboot.exe (PID: 2016)
- fastboot.exe (PID: 2652)
- wmpnscfg.exe (PID: 2032)
- adb.exe (PID: 3244)
- fastboot.exe (PID: 2440)
- fastboot.exe (PID: 3140)
- fastboot.exe (PID: 1652)
- fastboot.exe (PID: 1424)
- fastboot.exe (PID: 584)
- fastboot.exe (PID: 1072)
- fastboot.exe (PID: 2980)
- fastboot.exe (PID: 3244)
- fastboot.exe (PID: 3656)
- fastboot.exe (PID: 2136)
- fastboot.exe (PID: 3396)
- fastboot.exe (PID: 3612)
- fastboot.exe (PID: 1192)
- fastboot.exe (PID: 2332)
- fastboot.exe (PID: 3536)
- fastboot.exe (PID: 3824)
- fastboot.exe (PID: 3052)
- fastboot.exe (PID: 1936)
- fastboot.exe (PID: 3876)
- fastboot.exe (PID: 3076)
- fastboot.exe (PID: 1636)
- fastboot.exe (PID: 3996)
- fastboot.exe (PID: 1344)
- fastboot.exe (PID: 3256)
- fastboot.exe (PID: 2648)
- fastboot.exe (PID: 2032)
- fastboot.exe (PID: 2572)
- fastboot.exe (PID: 924)
- fastboot.exe (PID: 116)
- fastboot.exe (PID: 3200)
- fastboot.exe (PID: 2844)
- fastboot.exe (PID: 2476)
- fastboot.exe (PID: 3032)
- fastboot.exe (PID: 2232)
- fastboot.exe (PID: 2068)
- fastboot.exe (PID: 3000)
- fastboot.exe (PID: 2104)
- fastboot.exe (PID: 3232)
- fastboot.exe (PID: 2268)
- fastboot.exe (PID: 980)
- fastboot.exe (PID: 2592)
- fastboot.exe (PID: 4048)
- fastboot.exe (PID: 2108)
- fastboot.exe (PID: 2788)
- fastboot.exe (PID: 3496)
- fastboot.exe (PID: 1628)
- fastboot.exe (PID: 4012)
- fastboot.exe (PID: 2572)
- fastboot.exe (PID: 908)
- fastboot.exe (PID: 2020)
- fastboot.exe (PID: 2096)
- fastboot.exe (PID: 4008)
- fastboot.exe (PID: 3536)
- fastboot.exe (PID: 3652)
- fastboot.exe (PID: 1836)
- fastboot.exe (PID: 3232)
- fastboot.exe (PID: 452)
- fastboot.exe (PID: 1352)
- fastboot.exe (PID: 2892)
- fastboot.exe (PID: 1576)
- fastboot.exe (PID: 3740)
- fastboot.exe (PID: 2848)
- fastboot.exe (PID: 1072)
- fastboot.exe (PID: 1860)
- fastboot.exe (PID: 3036)
- fastboot.exe (PID: 1264)
- fastboot.exe (PID: 4088)
- fastboot.exe (PID: 3936)
- fastboot.exe (PID: 1792)
- fastboot.exe (PID: 1352)
- fastboot.exe (PID: 1932)
- fastboot.exe (PID: 2424)
- fastboot.exe (PID: 2532)
- fastboot.exe (PID: 3040)
- fastboot.exe (PID: 1812)
- fastboot.exe (PID: 3372)
- fastboot.exe (PID: 3068)
- fastboot.exe (PID: 1316)
- fastboot.exe (PID: 3820)
- fastboot.exe (PID: 1784)
- fastboot.exe (PID: 2744)
- fastboot.exe (PID: 2580)
- fastboot.exe (PID: 3476)
- fastboot.exe (PID: 3256)
- fastboot.exe (PID: 2292)
- fastboot.exe (PID: 3932)
- fastboot.exe (PID: 3412)
- fastboot.exe (PID: 876)
- fastboot.exe (PID: 1056)
- fastboot.exe (PID: 3432)
- fastboot.exe (PID: 3840)
- fastboot.exe (PID: 3664)
- fastboot.exe (PID: 2892)
- fastboot.exe (PID: 2752)
- fastboot.exe (PID: 3780)
- fastboot.exe (PID: 548)
- fastboot.exe (PID: 2448)
- fastboot.exe (PID: 3584)
- fastboot.exe (PID: 452)
- fastboot.exe (PID: 3492)
- fastboot.exe (PID: 2372)
- fastboot.exe (PID: 3536)
- fastboot.exe (PID: 2832)
- fastboot.exe (PID: 3836)
- fastboot.exe (PID: 2788)
- fastboot.exe (PID: 2036)
- fastboot.exe (PID: 3448)
- fastboot.exe (PID: 2072)
- fastboot.exe (PID: 3728)
- fastboot.exe (PID: 3476)
- fastboot.exe (PID: 3548)
- fastboot.exe (PID: 2976)
- fastboot.exe (PID: 3944)
- fastboot.exe (PID: 3460)
- fastboot.exe (PID: 2376)
- fastboot.exe (PID: 696)
- fastboot.exe (PID: 3268)
- fastboot.exe (PID: 3740)
- fastboot.exe (PID: 680)
- fastboot.exe (PID: 2088)
- fastboot.exe (PID: 1368)
- fastboot.exe (PID: 4052)
- fastboot.exe (PID: 3000)
- fastboot.exe (PID: 3240)
- fastboot.exe (PID: 3484)
- fastboot.exe (PID: 1652)
- fastboot.exe (PID: 2636)
- fastboot.exe (PID: 2568)
- fastboot.exe (PID: 2688)
- fastboot.exe (PID: 1112)
- fastboot.exe (PID: 3516)
- fastboot.exe (PID: 1848)
- fastboot.exe (PID: 3008)
- fastboot.exe (PID: 3768)
- fastboot.exe (PID: 1544)
- fastboot.exe (PID: 4024)
- fastboot.exe (PID: 2052)
- fastboot.exe (PID: 2512)
- fastboot.exe (PID: 2096)
- fastboot.exe (PID: 3704)
- fastboot.exe (PID: 1900)
- fastboot.exe (PID: 1424)
- fastboot.exe (PID: 2228)
- fastboot.exe (PID: 3228)
- fastboot.exe (PID: 3256)
- fastboot.exe (PID: 3180)
- fastboot.exe (PID: 2156)
- fastboot.exe (PID: 1020)
- fastboot.exe (PID: 3212)
- fastboot.exe (PID: 3820)
- fastboot.exe (PID: 1976)
- fastboot.exe (PID: 2136)
- fastboot.exe (PID: 3308)
- fastboot.exe (PID: 2500)
- fastboot.exe (PID: 2036)
- fastboot.exe (PID: 2736)
- fastboot.exe (PID: 3460)
- fastboot.exe (PID: 2892)
- fastboot.exe (PID: 4004)
- fastboot.exe (PID: 3140)
- fastboot.exe (PID: 3432)
- fastboot.exe (PID: 1772)
- fastboot.exe (PID: 4080)
- fastboot.exe (PID: 1560)
- fastboot.exe (PID: 1852)
- fastboot.exe (PID: 1624)
- fastboot.exe (PID: 2308)
- fastboot.exe (PID: 3472)
- fastboot.exe (PID: 1832)
- fastboot.exe (PID: 1928)
- fastboot.exe (PID: 3236)
- fastboot.exe (PID: 4012)
- fastboot.exe (PID: 2980)
- fastboot.exe (PID: 2052)
- fastboot.exe (PID: 3960)
- fastboot.exe (PID: 3148)
- fastboot.exe (PID: 3672)
- fastboot.exe (PID: 4072)
- fastboot.exe (PID: 884)
- fastboot.exe (PID: 3664)
- fastboot.exe (PID: 3668)
- fastboot.exe (PID: 240)
Reads the machine GUID from the registry
- reiboot-for-android.exe (PID: 3772)
- ReibootForAndroid.exe (PID: 2244)
- DPInst32.exe (PID: 552)
- drvinst.exe (PID: 2376)
- drvinst.exe (PID: 2120)
- drvinst.exe (PID: 3136)
- drvinst.exe (PID: 3456)
- drvinst.exe (PID: 3100)
- adb.exe (PID: 3260)
- adb.exe (PID: 3608)
Reads Environment values
- reiboot-for-android.exe (PID: 3772)
- ReibootForAndroid.exe (PID: 2244)
Create files in a temporary directory
- reiboot-for-android.exe (PID: 3772)
- reibootforandroid_ts_2.1.21.exe (PID: 2904)
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
- ReibootForAndroid.exe (PID: 2244)
- DPInst32.exe (PID: 552)
- adb.exe (PID: 3260)
Reads the software policy settings
- reiboot-for-android.exe (PID: 3772)
- ReibootForAndroid.exe (PID: 2244)
- drvinst.exe (PID: 2376)
- rundll32.exe (PID: 784)
- drvinst.exe (PID: 2120)
- rundll32.exe (PID: 3276)
- drvinst.exe (PID: 3456)
- drvinst.exe (PID: 3136)
- drvinst.exe (PID: 3100)
Creates files in the program directory
- reiboot-for-android.exe (PID: 3772)
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
- Start.exe (PID: 980)
- ReibootForAndroid.exe (PID: 2244)
Creates files or folders in the user directory
- reiboot-for-android.exe (PID: 3772)
- ReibootForAndroid.exe (PID: 2244)
Creates a software uninstall entry
- reibootforandroid_ts_2.1.21.tmp (PID: 3072)
Manual execution by a user
- msedge.exe (PID: 2524)
- msedge.exe (PID: 3472)
- wmpnscfg.exe (PID: 2032)
- msedge.exe (PID: 3324)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 784)
- rundll32.exe (PID: 3276)
Application launched itself
- msedge.exe (PID: 896)
- msedge.exe (PID: 2524)
- msedge.exe (PID: 2296)
- msedge.exe (PID: 3472)
- msedge.exe (PID: 3324)
- msedge.exe (PID: 2364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:06:27 03:11:21+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 1802240 |
| InitializedDataSize: | 241664 |
| UninitializedDataSize: | 2187264 |
| EntryPoint: | 0x3ce820 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.7.11.0 |
| ProductVersionNumber: | 2.7.11.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Tenorshare Co., Ltd. |
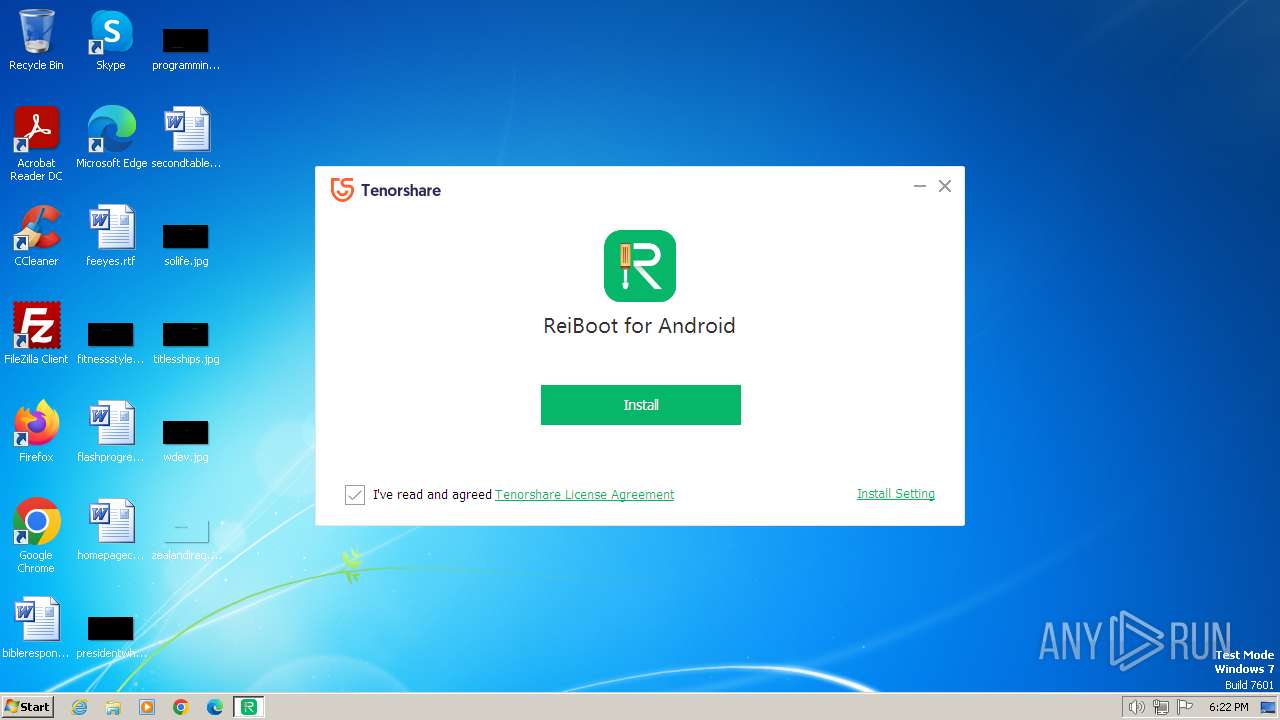
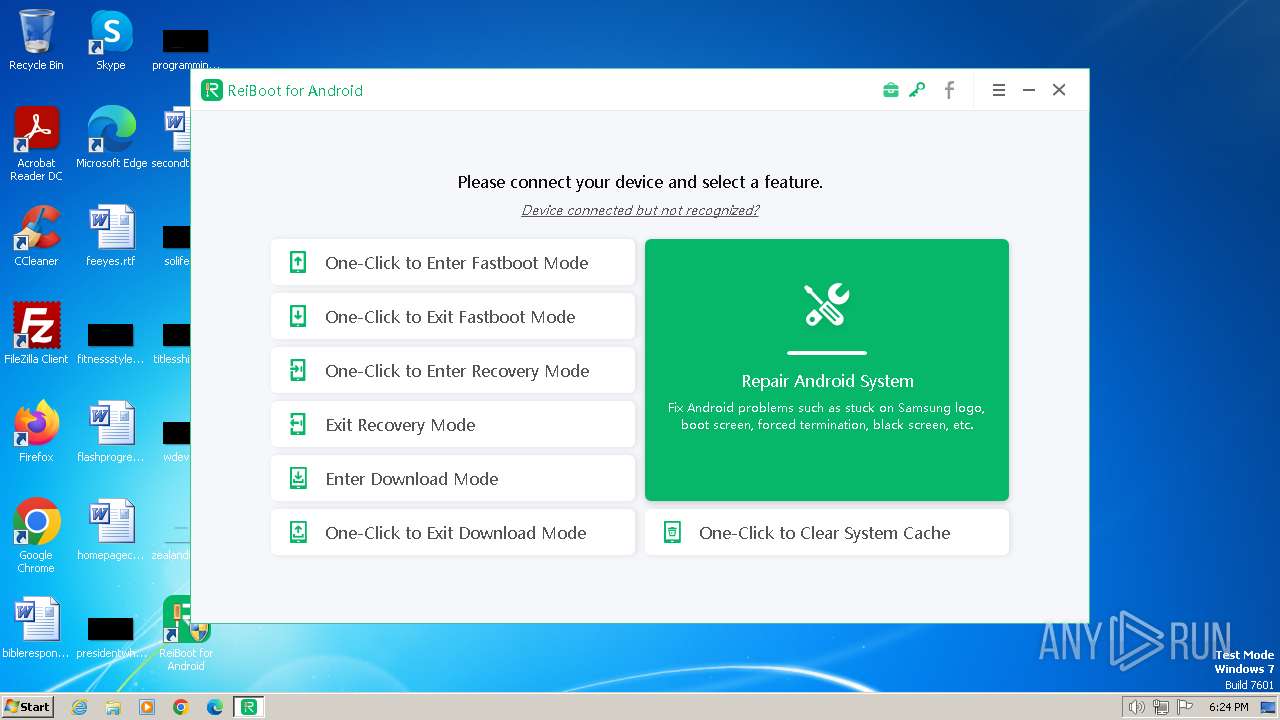
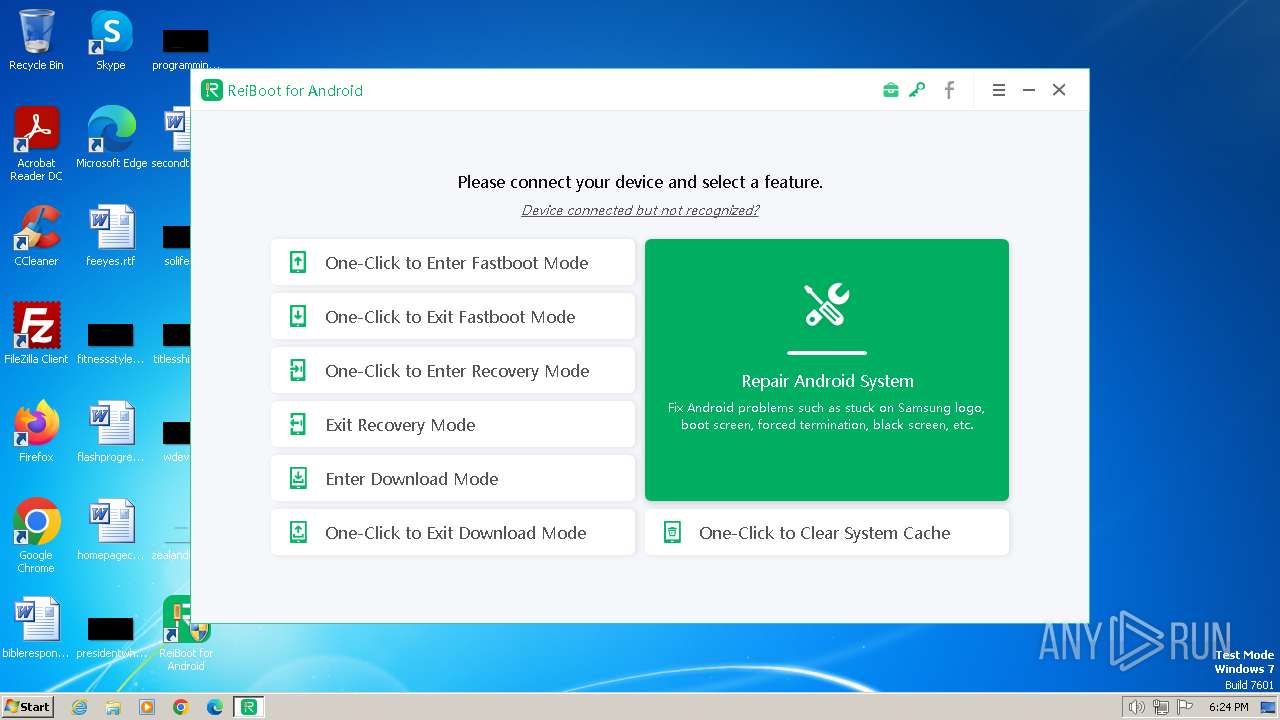
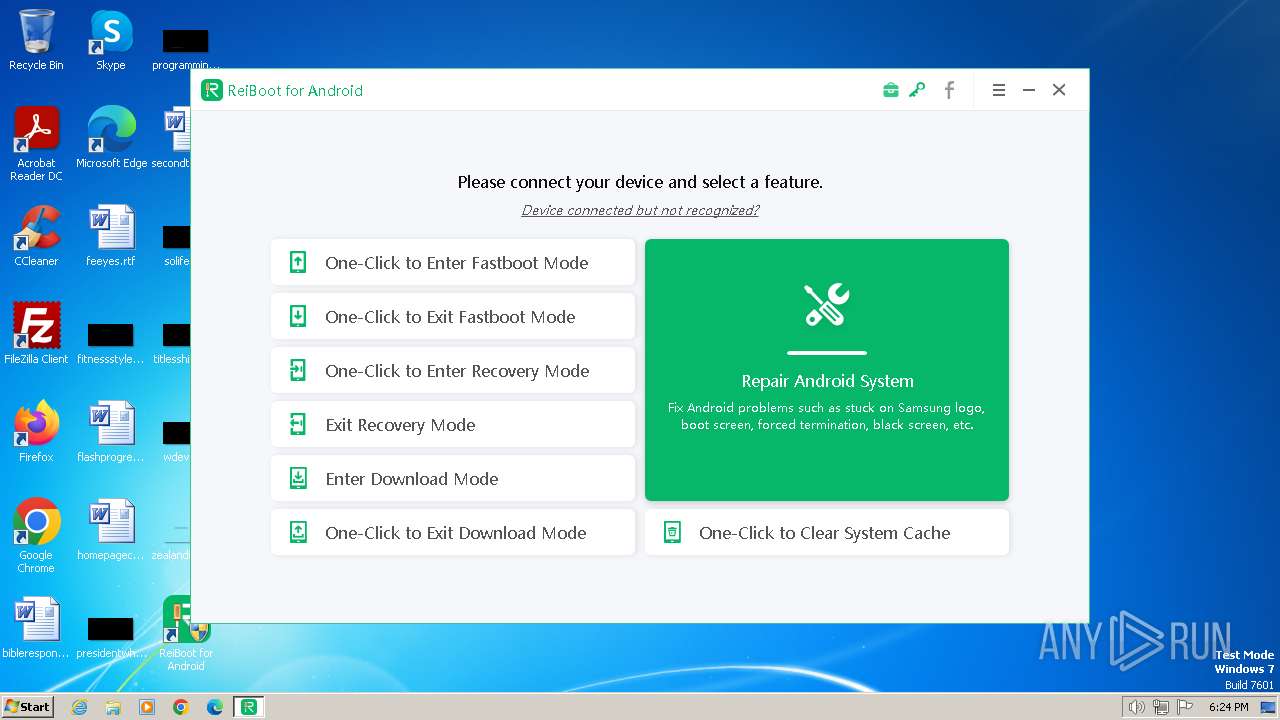
| FileDescription: | ReiBoot for Android |
| FileVersion: | 2.7.11.0 |
| LegalCopyright: | Copyright © 2007-2023 Tenorshare Co.,Ltd. |
| ProductName: | 20230627111056 |
| ProductVersion: | 2.7.11.0 |
Total processes
763
Monitored processes
503
Malicious processes
13
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 240 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 268 | "cmd.exe" /C "C:\tenorshare\adb\fastboot.exe" devices | C:\Windows\System32\cmd.exe | — | ReibootForAndroid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 268 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3848 --field-trial-handle=1284,i,8244457642628466432,4313857978834653277,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 296 | "C:\Program Files\Tenorshare\ReiBoot for Android\repair.exe" | C:\Program Files\Tenorshare\ReiBoot for Android\repair.exe | — | ReibootForAndroid.exe | |||||||||||
User: admin Company: Samsung Electronics Co., Ltd. Integrity Level: HIGH Description: Odin Downloader Exit code: 0 Version: 2017.10.18.1 Modules
| |||||||||||||||
| 324 | "cmd.exe" /C "C:\tenorshare\adb\fastboot.exe" devices | C:\Windows\System32\cmd.exe | — | ReibootForAndroid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 452 | "cmd.exe" /C "C:\tenorshare\adb\fastboot.exe" devices | C:\Windows\System32\cmd.exe | — | ReibootForAndroid.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 452 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3612 --field-trial-handle=1324,i,8283290480293021917,15204910297641279914,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 452 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 452 | C:\tenorshare\adb\fastboot.exe devices | C:\tenorshare\adb\fastboot.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
81 573
Read events
80 828
Write events
707
Delete events
38
Modification events
| (PID) Process: | (3772) reiboot-for-android.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Tenorshare\Downloader2.5.0 |
| Operation: | write | Name: | GA_PC |
Value: 1 | |||
| (PID) Process: | (3772) reiboot-for-android.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3772) reiboot-for-android.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (3772) reiboot-for-android.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (3772) reiboot-for-android.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (3772) reiboot-for-android.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (3772) reiboot-for-android.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3772) reiboot-for-android.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3772) reiboot-for-android.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3772) reiboot-for-android.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
386
Suspicious files
186
Text files
265
Unknown types
191
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3772 | reiboot-for-android.exe | C:\Users\admin\AppData\Local\Temp\reibootforandroid_ts\reibootforandroid_ts_2.1.21.exe | — | |
MD5:— | SHA256:— | |||
| 3772 | reiboot-for-android.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\0862UO6N.txt | text | |
MD5:820219A2634D6387B28F27F1A248091E | SHA256:38FCE2C2BFD48DD14C6984798BA1866933056C3C5716DE0404435A4F657BB902 | |||
| 3772 | reiboot-for-android.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_EB10CBE5F5A4C34C11B6616190391C99 | binary | |
MD5:F572EED29AE5F68322A2577DA16CBAA3 | SHA256:297F487DDC3429FBC217190A17E51A24D3BF7F6621591991ACB8A94A4F92589F | |||
| 3772 | reiboot-for-android.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_FB287BEB63DB9E8D59A799779773B97C | binary | |
MD5:E110D7E9FD42BB02A914A1FF4CB94477 | SHA256:8A68117880D2626632BC039F84F449F53EF4D16F38DFF348B7C231B883BE0E8E | |||
| 3772 | reiboot-for-android.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\1S5YPBZJ.txt | text | |
MD5:2B2721642349146EF2F6686594144E97 | SHA256:6C8AF1235DBC8D65FDD3C2520B8EE9535934AE7B3A459C7C84DD97FE8E4C2247 | |||
| 3072 | reibootforandroid_ts_2.1.21.tmp | C:\Program Files\Tenorshare\ReiBoot for Android\is-E459Q.tmp | executable | |
MD5:C3756557DA17AA37945192D3B72DDCDB | SHA256:7142AE144CC9C917BA8BCCB7F16C2BFF6A0E2B3280DA7549682C549A9D090832 | |||
| 3772 | reiboot-for-android.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3E3E9689537B6B136ECF210088069D55_EF6C9357BB54DDB629FD2D79F1594F95 | binary | |
MD5:EAD903924FCFC1E9DE7F7D609265368A | SHA256:5786CBB5CF6ACB019FA89BEA321014B4DD7F5BB7C48AFD610D13B7588F841358 | |||
| 3772 | reiboot-for-android.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_EB10CBE5F5A4C34C11B6616190391C99 | binary | |
MD5:98AD204FDA86BD5FE7C1E67B944EC034 | SHA256:76AE82F49CECCBFC6AADCC92784B0320192180FCAF733CA556C11DC1B00A223B | |||
| 3772 | reiboot-for-android.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3E3E9689537B6B136ECF210088069D55_EF6C9357BB54DDB629FD2D79F1594F95 | der | |
MD5:FED1AAB0EE1ADE64768A29191DC32A0D | SHA256:5294D3AF72F86C4DD77FF8613F9466932495A1D73819B635C01771067B15E2D7 | |||
| 2904 | reibootforandroid_ts_2.1.21.exe | C:\Users\admin\AppData\Local\Temp\is-Q328J.tmp\reibootforandroid_ts_2.1.21.tmp | executable | |
MD5:C3756557DA17AA37945192D3B72DDCDB | SHA256:7142AE144CC9C917BA8BCCB7F16C2BFF6A0E2B3280DA7549682C549A9D090832 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
222
DNS requests
219
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3772 | reiboot-for-android.exe | GET | 301 | 104.17.192.141:80 | http://www.tenorshare.com/downloads/service/softwarelog.txt | unknown | html | 245 b | unknown |
3772 | reiboot-for-android.exe | GET | 304 | 184.24.77.199:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?04b2dea8abd60a79 | unknown | — | — | unknown |
3772 | reiboot-for-android.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAhflMAthXvozBT%2FU%2B2iPio%3D | unknown | binary | 471 b | unknown |
3772 | reiboot-for-android.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/csv | unknown | text | 172 b | unknown |
3772 | reiboot-for-android.exe | POST | 200 | 142.250.185.78:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
3772 | reiboot-for-android.exe | POST | 200 | 142.250.185.78:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
3772 | reiboot-for-android.exe | POST | 200 | 142.250.185.78:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
3772 | reiboot-for-android.exe | POST | 200 | 142.250.185.78:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
3772 | reiboot-for-android.exe | POST | 200 | 142.250.185.78:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
3772 | reiboot-for-android.exe | POST | 200 | 142.250.185.78:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3772 | reiboot-for-android.exe | 104.17.192.141:80 | www.tenorshare.com | CLOUDFLARENET | — | unknown |
3772 | reiboot-for-android.exe | 104.17.192.141:443 | www.tenorshare.com | CLOUDFLARENET | — | unknown |
3772 | reiboot-for-android.exe | 184.24.77.199:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3772 | reiboot-for-android.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3772 | reiboot-for-android.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
3772 | reiboot-for-android.exe | 142.250.185.78:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
3772 | reiboot-for-android.exe | 104.18.25.249:443 | update.tenorshare.com | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.tenorshare.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ip-api.com |
| shared |
www.google-analytics.com |
| whitelisted |
update.tenorshare.com |
| unknown |
download.tenorshare.com |
| unknown |
apiw.tenorshare.com |
| unknown |
analytics.afirstsoft.cn |
| unknown |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3772 | reiboot-for-android.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
3772 | reiboot-for-android.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
3772 | reiboot-for-android.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3772 | reiboot-for-android.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3772 | reiboot-for-android.exe | Possibly Unwanted Program Detected | ET ADWARE_PUP Tensorshare Google Analytics Checkin |
2244 | ReibootForAndroid.exe | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
ReibootForAndroid.exe | log4net:ERROR XmlHierarchyConfigurator: No appender named [ConsoleAppender] could be found.
|
ReibootForAndroid.exe | log4net:ERROR Appender named [ConsoleAppender] not found.
|
ReibootForAndroid.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\Tenorshare\ReiBoot for Android\x86\SQLite.Interop.dll"...
|