| File name: | vbehxx.zip |
| Full analysis: | https://app.any.run/tasks/1e66280c-4e66-4550-ae23-04f6e4b47593 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 05:49:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | DFB15C3BDEFF52B5B2D88F8CCA0B76FF |
| SHA1: | 02CE8A26A825CBE44A28820415DB10CF5C75CF27 |
| SHA256: | 2E80059A92E23F07ECE25CD25F4E855CB01C8623A5CA9D8D63756C2273368563 |
| SSDEEP: | 768:YgV76KrqScCf4h4ywSC1/VzXDiAJgwkLF3YwzyrNjP:Yc6Kr27SV1/5z5Hhz |
MALICIOUS
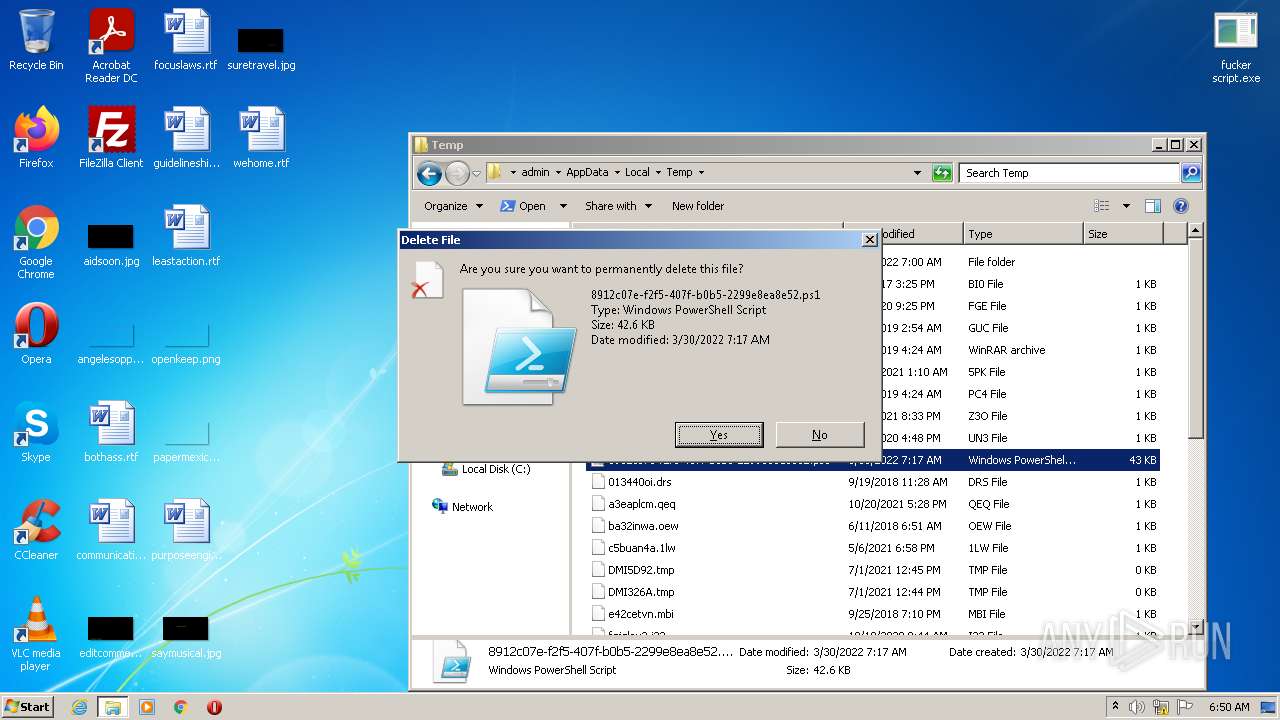
Drops executable file immediately after starts
- WinRAR.exe (PID: 2832)
Application was dropped or rewritten from another process
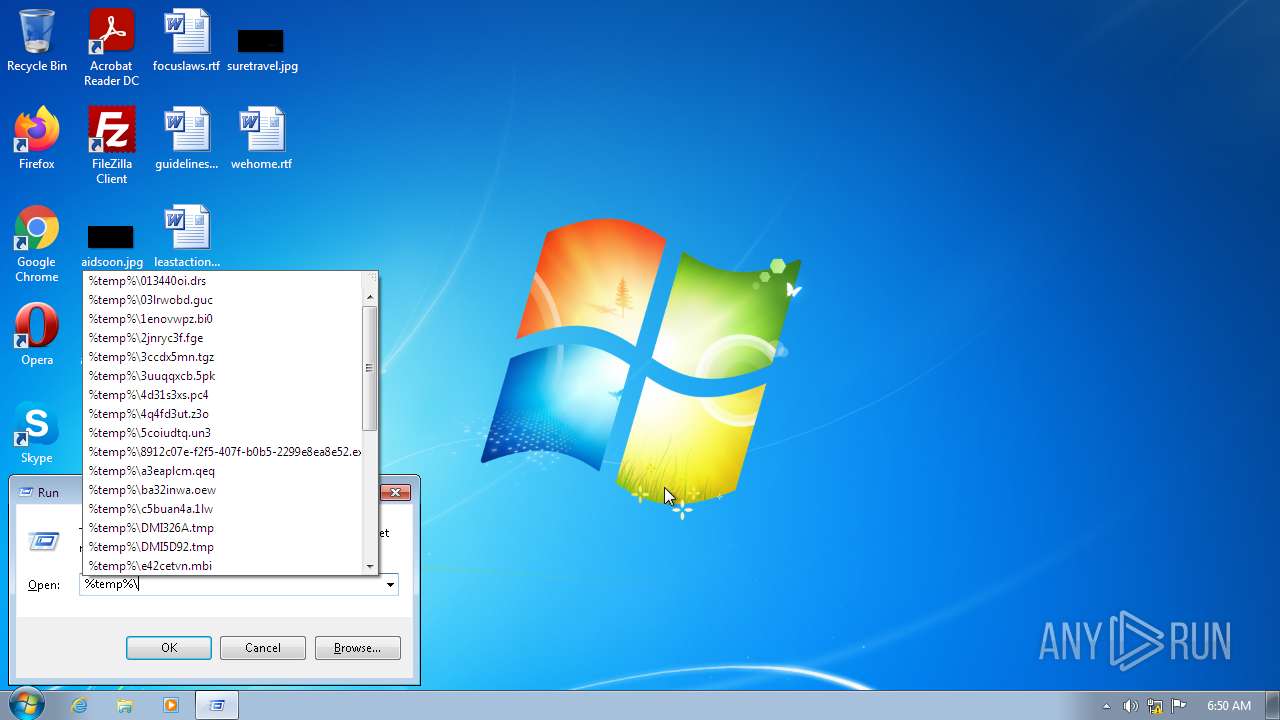
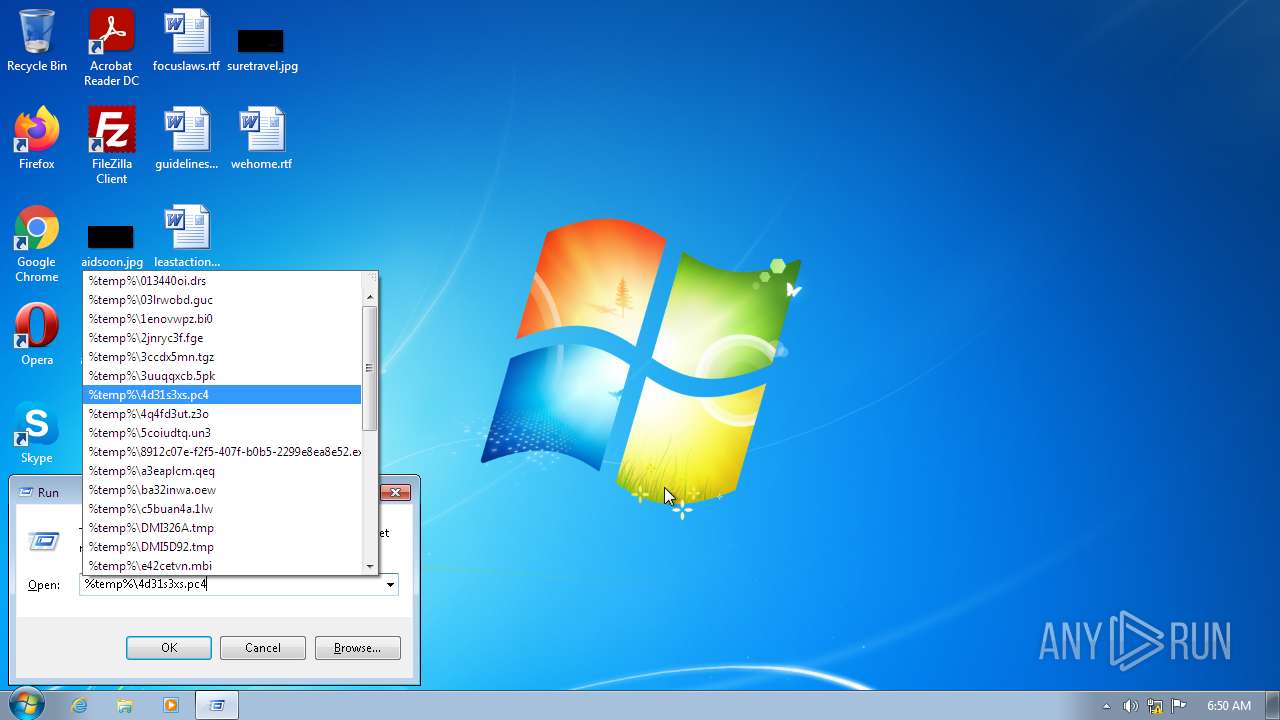
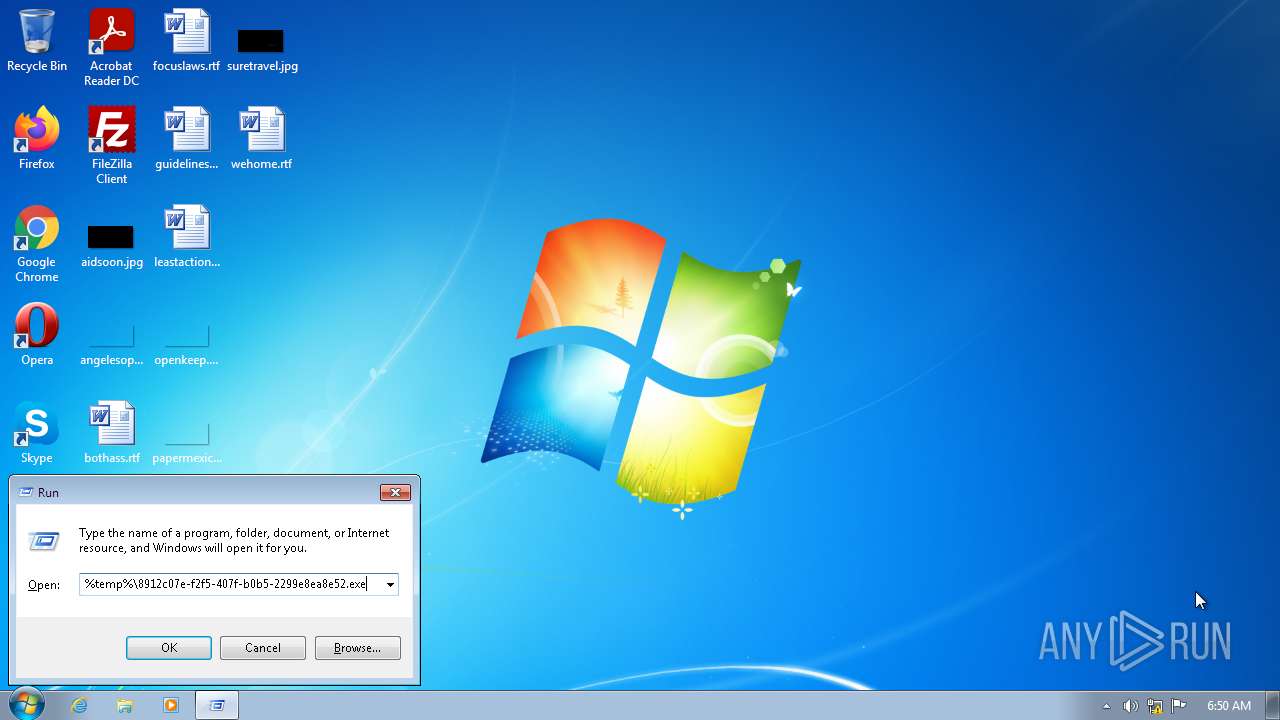
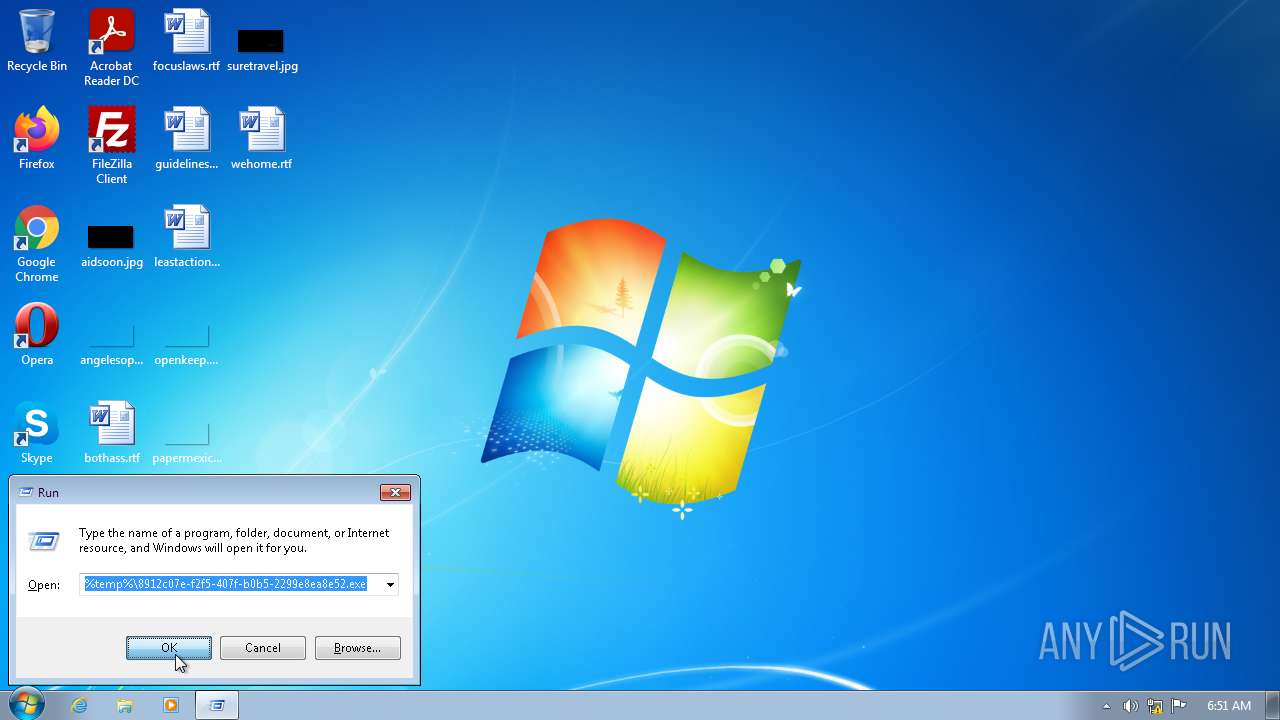
- 8912c07e-f2f5-407f-b0b5-2299e8ea8e52.exe (PID: 2956)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2832)
Checks supported languages
- WinRAR.exe (PID: 2832)
- 8912c07e-f2f5-407f-b0b5-2299e8ea8e52.exe (PID: 2956)
- OUTLOOK.EXE (PID: 3568)
- vlc.exe (PID: 3240)
- vlc.exe (PID: 2244)
- vlc.exe (PID: 3596)
- vlc.exe (PID: 1328)
- OUTLOOK.EXE (PID: 2588)
- OUTLOOK.EXE (PID: 756)
- OUTLOOK.EXE (PID: 1808)
- wmplayer.exe (PID: 3056)
- setup_wm.exe (PID: 2476)
- vlc.exe (PID: 3120)
- OUTLOOK.EXE (PID: 2712)
Reads the computer name
- WinRAR.exe (PID: 2832)
- OUTLOOK.EXE (PID: 3568)
- vlc.exe (PID: 3240)
- vlc.exe (PID: 1328)
- vlc.exe (PID: 2244)
- vlc.exe (PID: 3596)
- wmplayer.exe (PID: 3056)
- setup_wm.exe (PID: 2476)
- vlc.exe (PID: 3120)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2832)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2532)
- OUTLOOK.EXE (PID: 3568)
- iexplore.exe (PID: 3320)
- iexplore.exe (PID: 1040)
- iexplore.exe (PID: 3740)
Reads internet explorer settings
- OUTLOOK.EXE (PID: 3568)
Reads the date of Windows installation
- OUTLOOK.EXE (PID: 3568)
Reads Environment values
- setup_wm.exe (PID: 2476)
INFO
Manual execution by user
- explorer.exe (PID: 3484)
- rundll32.exe (PID: 3468)
- calc.exe (PID: 3384)
- calc.exe (PID: 2004)
- vlc.exe (PID: 1328)
- 8912c07e-f2f5-407f-b0b5-2299e8ea8e52.exe (PID: 2956)
- OUTLOOK.EXE (PID: 3568)
- vlc.exe (PID: 2244)
- vlc.exe (PID: 3240)
- OUTLOOK.EXE (PID: 756)
- calc.exe (PID: 2904)
- vlc.exe (PID: 3596)
- iexplore.exe (PID: 2532)
- calc.exe (PID: 2364)
- OUTLOOK.EXE (PID: 2588)
- explorer.exe (PID: 2628)
- calc.exe (PID: 3332)
- OUTLOOK.EXE (PID: 1808)
- wmplayer.exe (PID: 3056)
- iexplore.exe (PID: 2484)
- vlc.exe (PID: 3120)
- OUTLOOK.EXE (PID: 2712)
- iexplore.exe (PID: 620)
- iexplore.exe (PID: 3364)
Checks supported languages
- explorer.exe (PID: 3484)
- rundll32.exe (PID: 3468)
- calc.exe (PID: 3384)
- calc.exe (PID: 2004)
- calc.exe (PID: 2904)
- iexplore.exe (PID: 2532)
- calc.exe (PID: 2364)
- explorer.exe (PID: 2628)
- calc.exe (PID: 3332)
- iexplore.exe (PID: 3320)
- iexplore.exe (PID: 1040)
- iexplore.exe (PID: 2484)
- iexplore.exe (PID: 3740)
- iexplore.exe (PID: 3364)
- iexplore.exe (PID: 620)
Reads the computer name
- explorer.exe (PID: 3484)
- iexplore.exe (PID: 2532)
- iexplore.exe (PID: 3320)
- explorer.exe (PID: 2628)
- iexplore.exe (PID: 2484)
- iexplore.exe (PID: 1040)
- iexplore.exe (PID: 3740)
- iexplore.exe (PID: 620)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2588)
- OUTLOOK.EXE (PID: 756)
- OUTLOOK.EXE (PID: 1808)
- OUTLOOK.EXE (PID: 3568)
- OUTLOOK.EXE (PID: 2712)
Changes internet zones settings
- iexplore.exe (PID: 2532)
Application launched itself
- iexplore.exe (PID: 2532)
Reads internet explorer settings
- iexplore.exe (PID: 3320)
- iexplore.exe (PID: 1040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
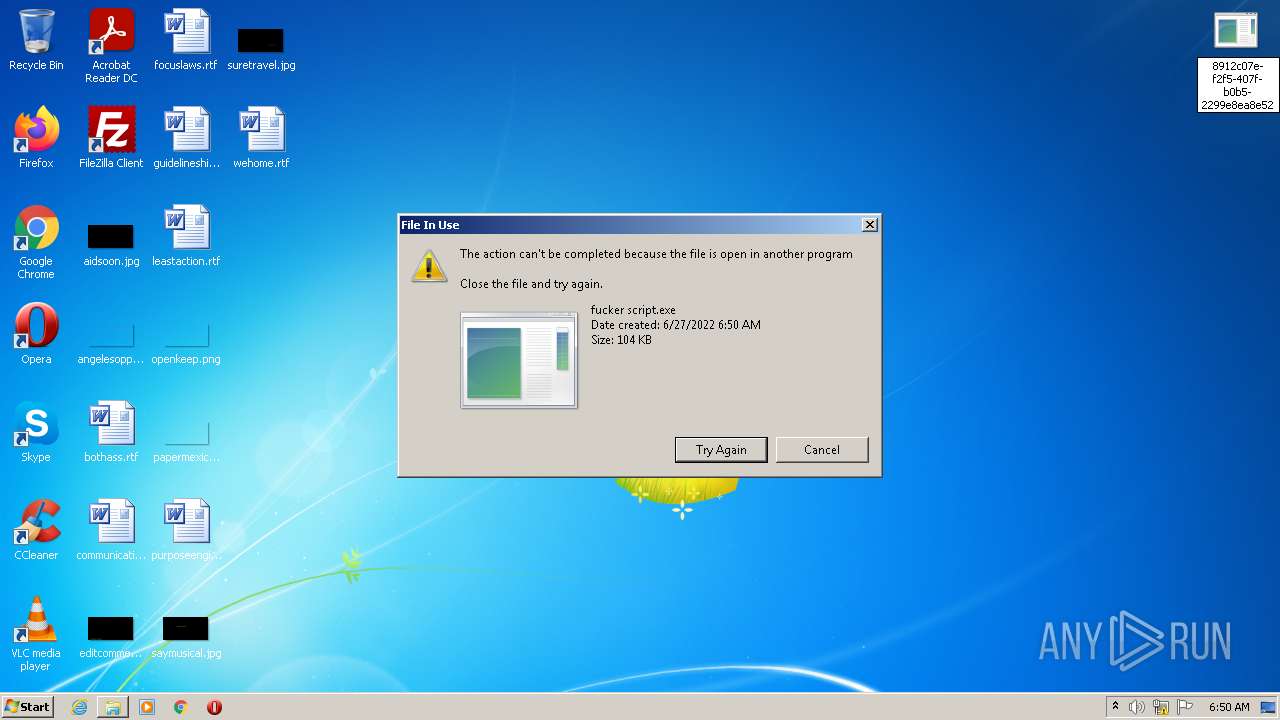
| ZipFileName: | fucker script.exe |
|---|---|
| ZipUncompressedSize: | 107168 |
| ZipCompressedSize: | 34474 |
| ZipCRC: | 0xe6a17274 |
| ZipModifyDate: | 2021:11:01 16:51:27 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
73
Monitored processes
29
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 756 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2532 CREDAT:464139 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1328 | "C:\Program Files\VideoLAN\VLC\vlc.exe" | C:\Program Files\VideoLAN\VLC\vlc.exe | Explorer.EXE | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 1808 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2004 | "C:\Windows\system32\calc.exe" | C:\Windows\system32\calc.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Calculator Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2244 | "C:\Program Files\VideoLAN\VLC\vlc.exe" | C:\Program Files\VideoLAN\VLC\vlc.exe | Explorer.EXE | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 2364 | "C:\Windows\system32\calc.exe" | C:\Windows\system32\calc.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Calculator Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | "C:\Program Files\Windows Media Player\setup_wm.exe" /RunOnce:"C:\Program Files\Windows Media Player\wmplayer.exe" /prefetch:1 | C:\Program Files\Windows Media Player\setup_wm.exe | — | wmplayer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Media Configuration Utility Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2484 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
33 435
Read events
33 068
Write events
366
Delete events
1
Modification events
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\vbehxx.zip | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2832) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
0
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3568 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRDB1B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2588 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE2CB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 756 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE2EB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3568 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1808 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRF356.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2712 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVREDD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3568 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\Microsoft Outlook.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3568 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2832 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2832.15471\fucker script.exe | executable | |
MD5:DB0655EFBE0DBDEF1DF06207F5CB5B5B | SHA256:52972A23AB12B95CD51D71741DB2CF276749E56030C092E2E4F0907DCB1FBD56 | |||
| 3568 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\msoF376.tmp | html | |
MD5:A8934077843220A8E31367C7BBE15E6C | SHA256:A2DB0201D36F07F3F99D1ADF8B8EAFB9CF9BB803D024FCC9327B77AF56346861 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=i686-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x86/contrib/i686-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc error: stale plugins cache: modified C:\Program Files\VideoLAN\VLC\plugins\access\libaccess_concat_plugin.dll
|