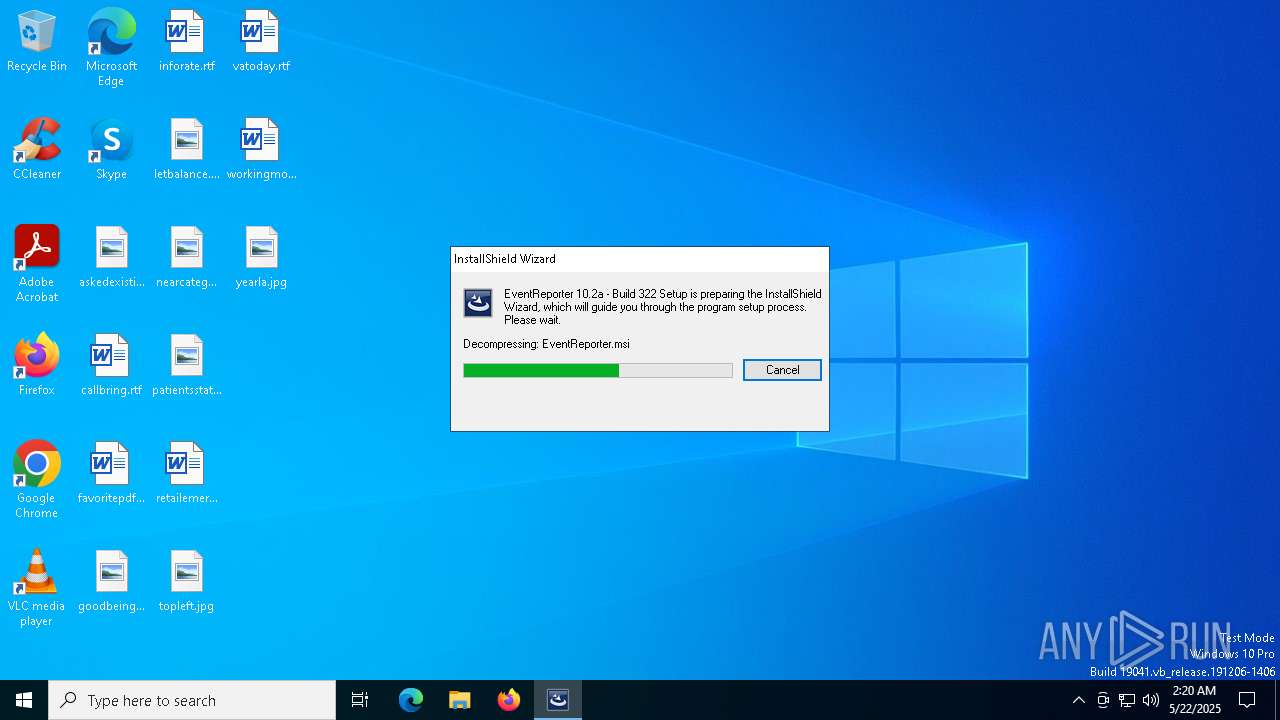
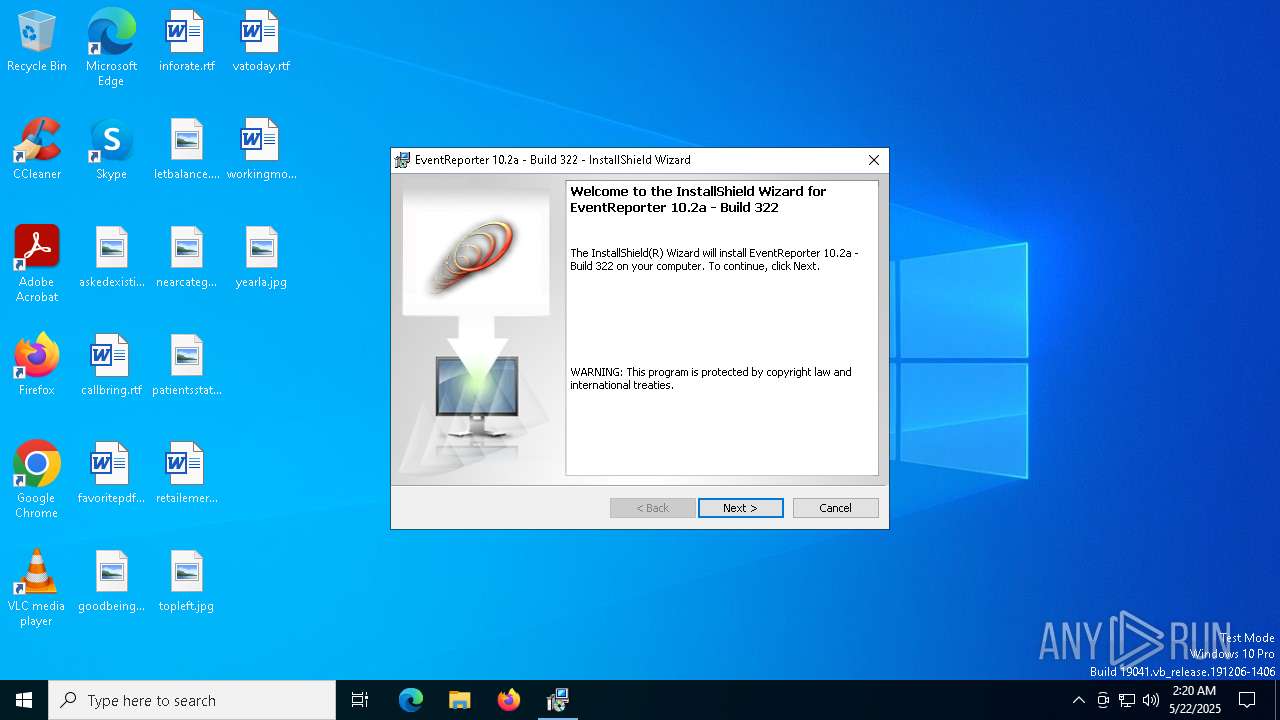
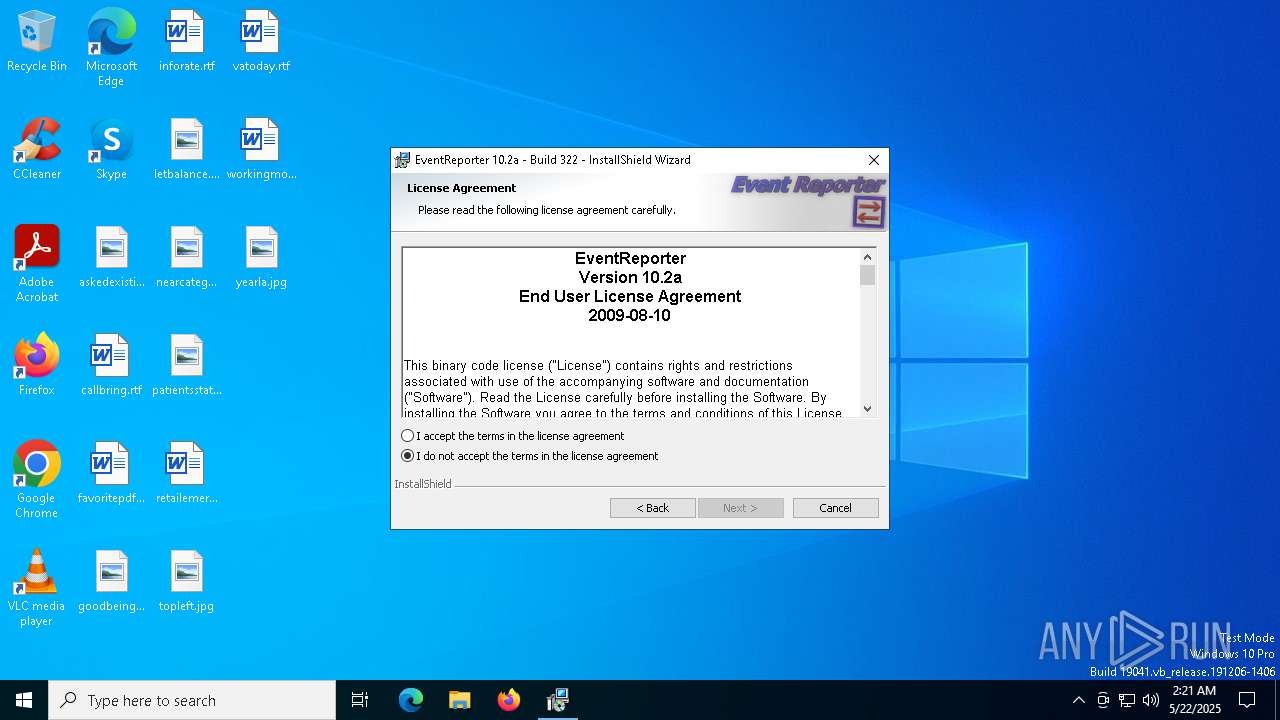
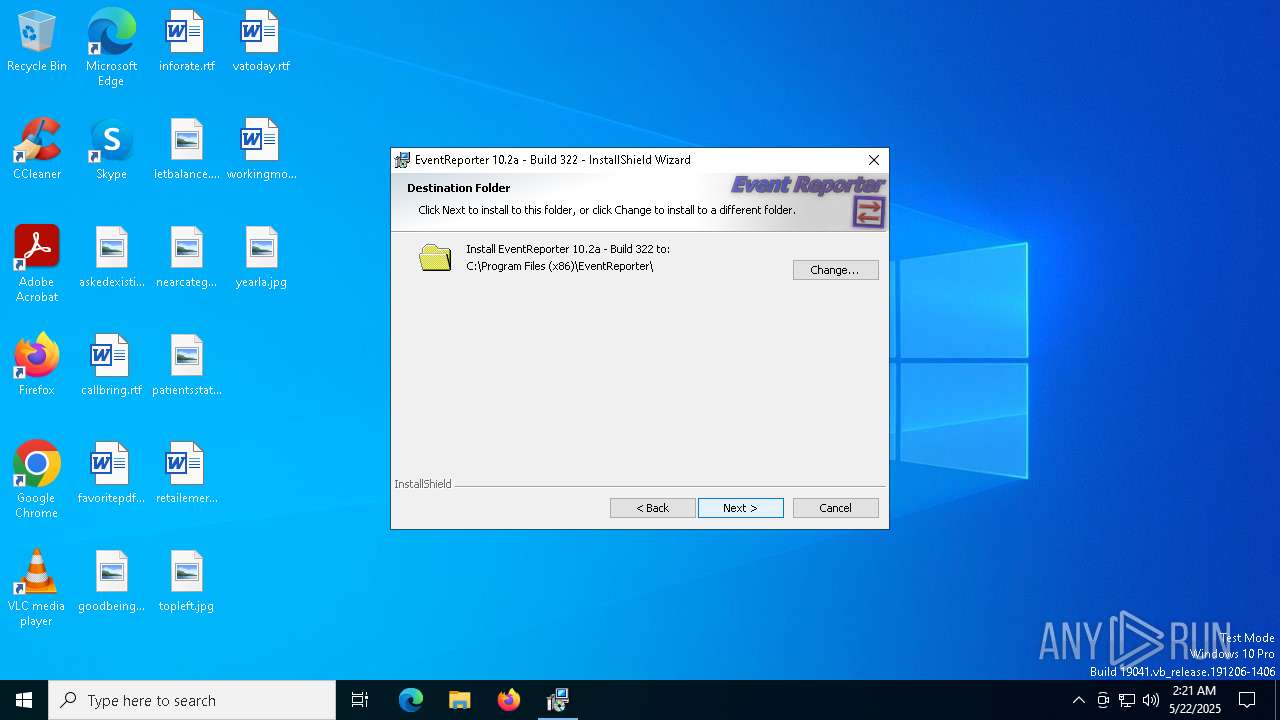
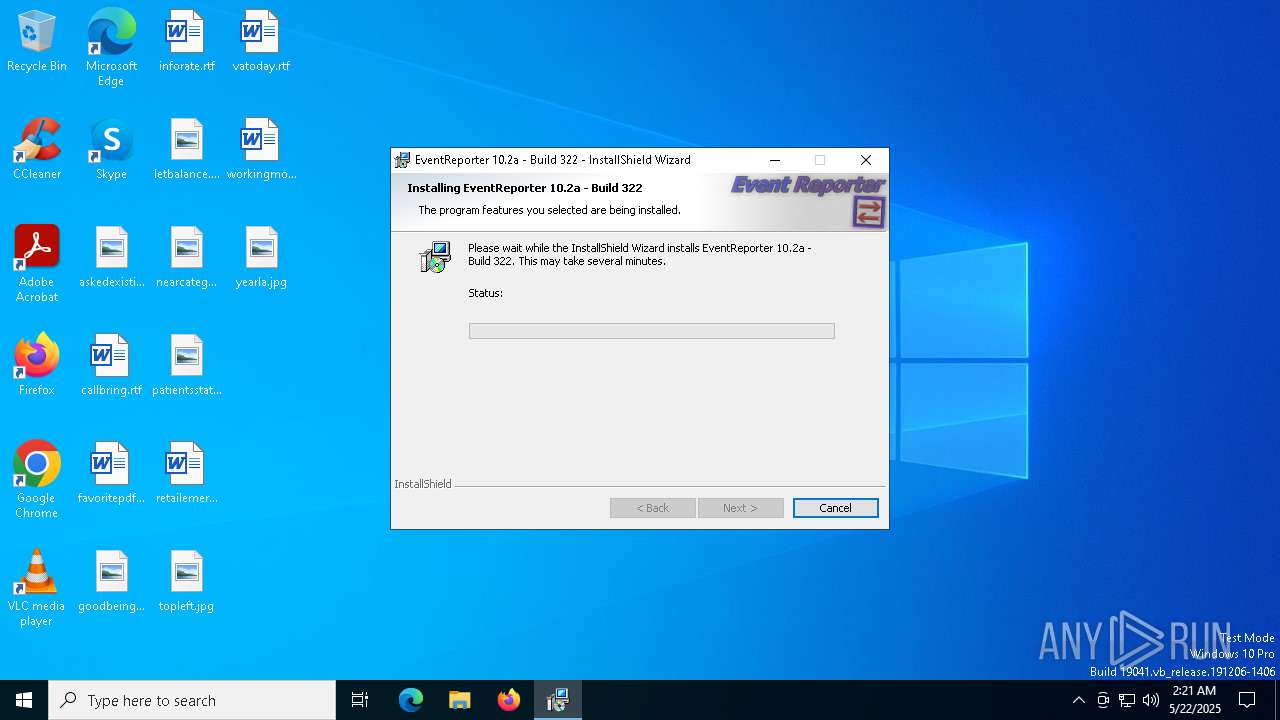
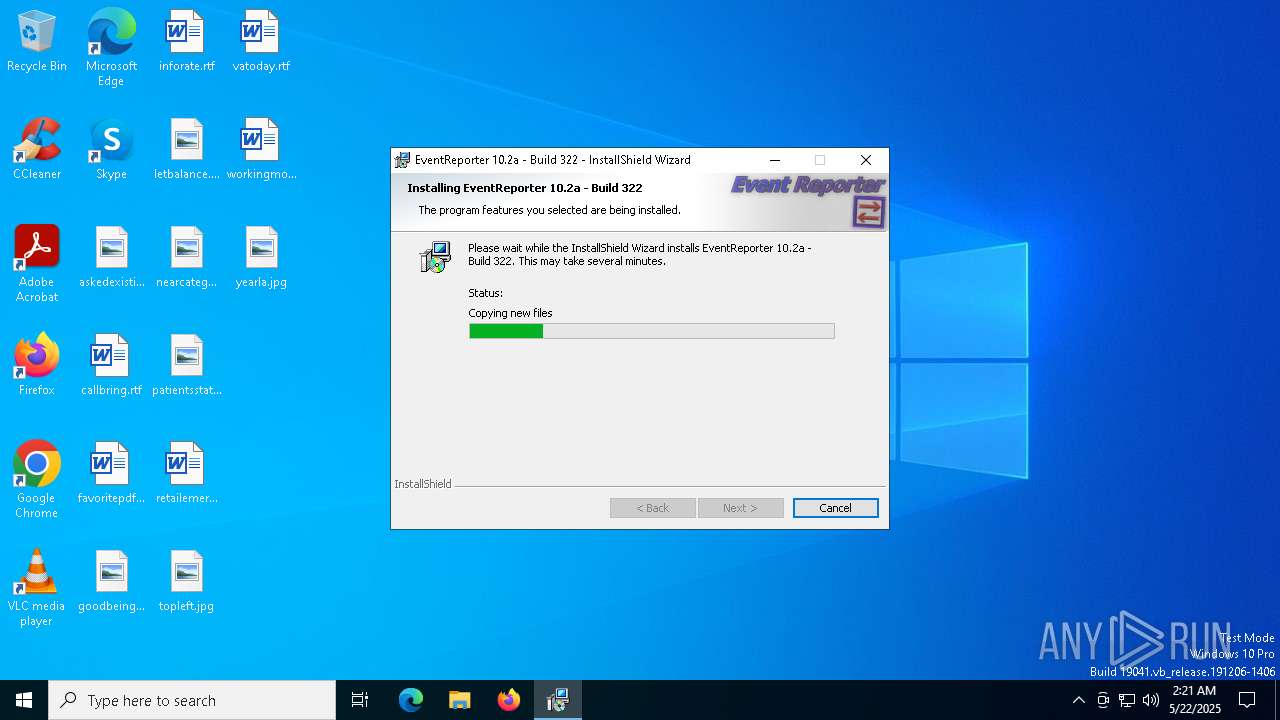
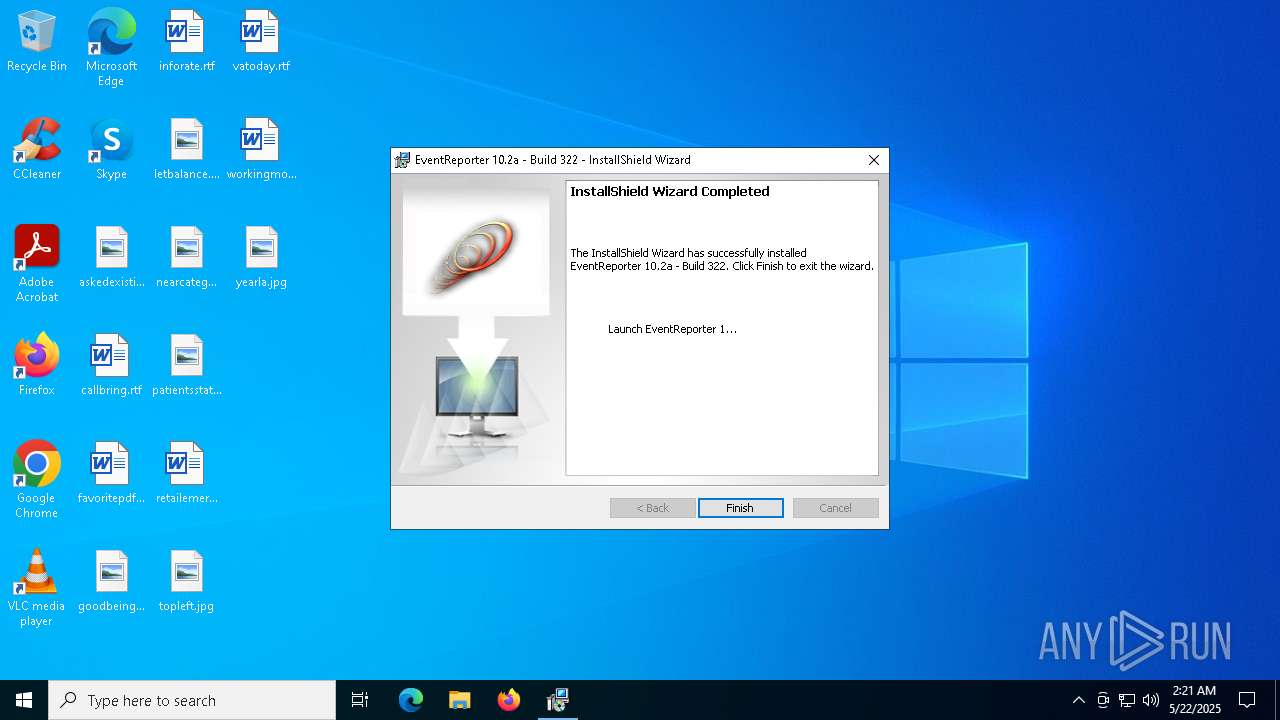
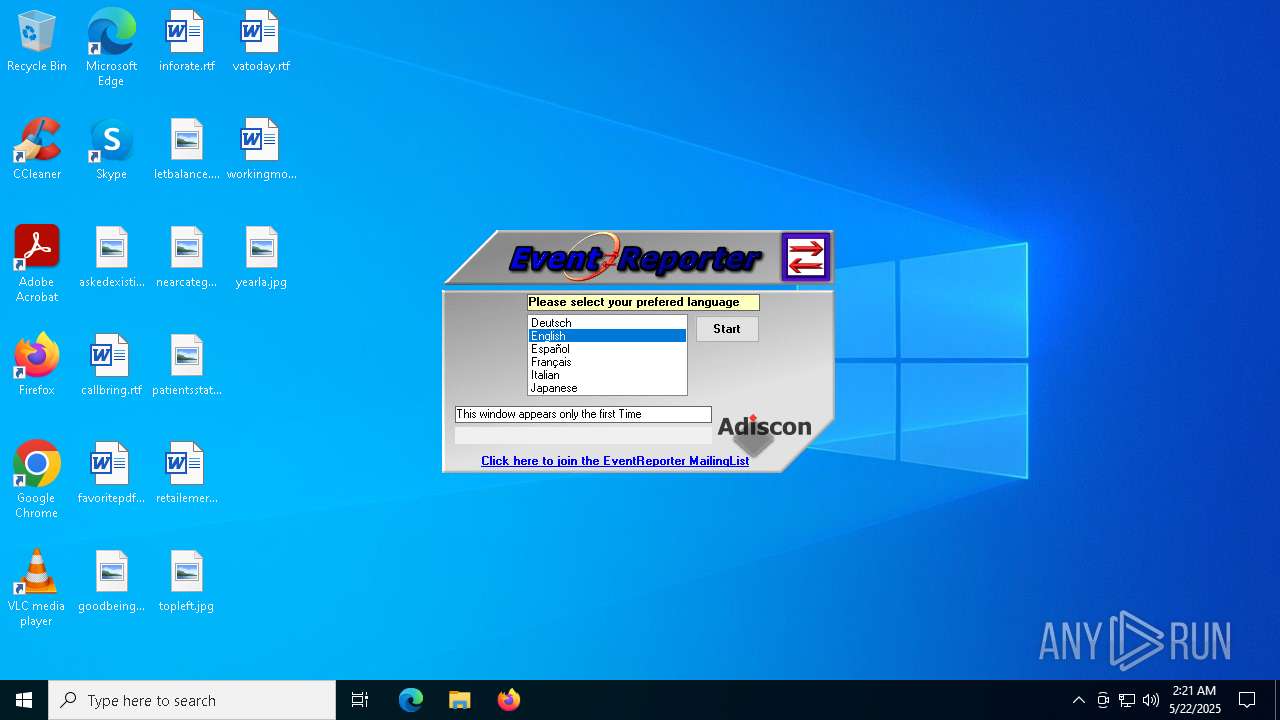
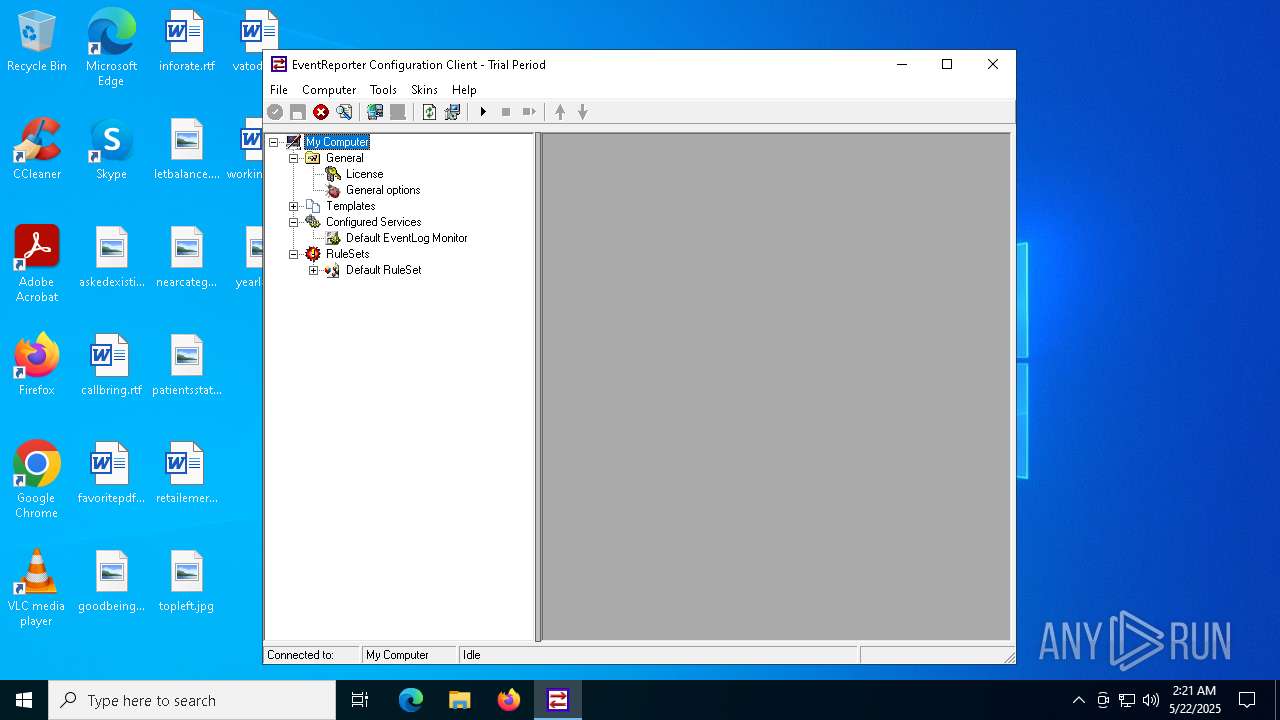
| File name: | evtrpt102a.exe |
| Full analysis: | https://app.any.run/tasks/c12cfe82-b92f-421f-a1fa-3e52c47252e3 |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2025, 02:20:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 85327802A11182985378229509D20274 |
| SHA1: | 9FD09DDAB34463FD330F0B70CB7C828C35F9E254 |
| SHA256: | 2E5901226686EDD9B679ED8A5424071B8B6505DFAB5B0F7A5799D15A41ABEA89 |
| SSDEEP: | 196608:OoiCooxJdPF2ehpHG5l7Gu8jH/pYIzUQvBdCWd:O7CoE2eoQzjHtIQvBp |
MALICIOUS
Executing a file with an untrusted certificate
- evtrpt102a.exe (PID: 6656)
- evtrpt102a.exe (PID: 5508)
- ISBEW64.exe (PID: 5596)
- ISBEW64.exe (PID: 6816)
- CFGEvntSLog.exe (PID: 1764)
SUSPICIOUS
Adds/modifies Windows certificates
- msiexec.exe (PID: 5164)
There is functionality for taking screenshot (YARA)
- evtrpt102a.exe (PID: 5508)
Executes as Windows Service
- VSSVC.exe (PID: 5984)
Process drops legitimate windows executable
- TiWorker.exe (PID: 4164)
- msiexec.exe (PID: 6668)
- msiexec.exe (PID: 664)
Starts application with an unusual extension
- msiexec.exe (PID: 6208)
The process drops C-runtime libraries
- msiexec.exe (PID: 664)
- TiWorker.exe (PID: 4164)
Executable content was dropped or overwritten
- TiWorker.exe (PID: 4164)
INFO
The sample compiled with english language support
- evtrpt102a.exe (PID: 5508)
- msiexec.exe (PID: 5164)
- msiexec.exe (PID: 6668)
- msiexec.exe (PID: 664)
- TiWorker.exe (PID: 4164)
Creates files in the program directory
- evtrpt102a.exe (PID: 5508)
Checks supported languages
- evtrpt102a.exe (PID: 5508)
- msiexec.exe (PID: 664)
- msiexec.exe (PID: 1672)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5164)
Reads the software policy settings
- msiexec.exe (PID: 5164)
Create files in a temporary directory
- evtrpt102a.exe (PID: 5508)
Reads the computer name
- evtrpt102a.exe (PID: 5508)
- msiexec.exe (PID: 664)
- msiexec.exe (PID: 1672)
Checks proxy server information
- msiexec.exe (PID: 5164)
Creates files or folders in the user directory
- msiexec.exe (PID: 5164)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5164)
- msiexec.exe (PID: 6668)
- msiexec.exe (PID: 664)
Manages system restore points
- SrTasks.exe (PID: 2268)
Starts application with an unusual extension
- msiexec.exe (PID: 664)
The sample compiled with german language support
- msiexec.exe (PID: 664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (38.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (34.3) |
| .scr | | | Windows screen saver (16.2) |
| .exe | | | Win32 Executable (generic) (5.6) |
| .exe | | | Generic Win/DOS Executable (2.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:09:11 05:55:59+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 425984 |
| InitializedDataSize: | 200704 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x36327 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 15.0.0.591 |
| ProductVersionNumber: | 15.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Adiscon GmbH |
| FileDescription: | Setup Launcher |
| FileVersion: | 10.2.0.322 |
| InternalName: | Setup |
| LegalCopyright: | Copyright (C) 2008 Acresso Software Inc. and/or InstallShield Co. Inc. All Rights Reserved. |
| OriginalFileName: | Setup.exe |
| ProductName: | EventReporter 10.2a - Build 322 |
| ProductVersion: | 10.2.0.322 |
| InternalBuildNumber: | 82160 |
Total processes
155
Monitored processes
21
Malicious processes
3
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | C:\Windows\syswow64\MsiExec.exe -Embedding B0ADF813D5DC083BADCFC79E205EB181 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | "C:\Program Files (x86)\EventReporter\CFGEvntSLog.exe" | C:\Program Files (x86)\EventReporter\CFGEvntSLog.exe | — | msiexec.exe | |||||||||||
User: admin Company: Adiscon GmbH Integrity Level: HIGH Version: 10.02.0360 Modules
| |||||||||||||||
| 2108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4408 | "C:\WINDOWS\Installer\MSI690F.tmp" | C:\Windows\Installer\MSI690F.tmp | — | msiexec.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4452 | C:\Windows\syswow64\MsiExec.exe -Embedding 862E50492CB51CA3BE20D69DA22240BB M Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5164 | MSIEXEC.EXE /i "C:\ProgramData\{88336AD7-C2F3-422A-8282-A62841F86EC1}\EventReporter.msi" SETUPEXEDIR="C:\Users\admin\AppData\Local\Temp" SETUPEXENAME="evtrpt102a.exe" | C:\Windows\SysWOW64\msiexec.exe | evtrpt102a.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 867
Read events
18 873
Write events
921
Delete events
73
Modification events
| (PID) Process: | (5164) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 627F8D7827656399D27D7F9044C9FEB3F33EFA9A |
Value: | |||
| (PID) Process: | (5164) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\627F8D7827656399D27D7F9044C9FEB3F33EFA9A |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000069F6979166690021B8C8CA2C3076F3A0B000000010000000E00000074006800610077007400650000001400000001000000140000005FF3246C8F9124AF9B5F3EB0346AF42D5CA85DCC620000000100000020000000AB7036365C7154AA29C2C29F5D4191163B162A2225011357D56D07FFA7BC1F721900000001000000100000005DC45E2CD1845791BDDE7600050AF510030000000100000014000000627F8D7827656399D27D7F9044C9FEB3F33EFA9A0F00000001000000100000005F3D1AA6F471A760663EB7EF254281EF53000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C0090000000100000016000000301406082B0601050507030306082B060105050703011D0000000100000010000000D4803AC36C256817D4EC5936F29BC4E76800000001000000080000000000876ACE99D10120000000010000002B0300003082032730820290A003020102020101300D06092A864886F70D01010405003081CE310B3009060355040613025A41311530130603550408130C5765737465726E204361706531123010060355040713094361706520546F776E311D301B060355040A131454686177746520436F6E73756C74696E6720636331283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E3121301F06035504031318546861777465205072656D69756D205365727665722043413128302606092A864886F70D01090116197072656D69756D2D736572766572407468617774652E636F6D301E170D3936303830313030303030305A170D3230313233313233353935395A3081CE310B3009060355040613025A41311530130603550408130C5765737465726E204361706531123010060355040713094361706520546F776E311D301B060355040A131454686177746520436F6E73756C74696E6720636331283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E3121301F06035504031318546861777465205072656D69756D205365727665722043413128302606092A864886F70D01090116197072656D69756D2D736572766572407468617774652E636F6D30819F300D06092A864886F70D010101050003818D0030818902818100D236366A8BD7C25B9EDA8141628F38EE490455D6D0EF1C1B951647EF1848353A52F42B6A068F3B2FEA56E3AF868D9E17F79EB46575024DEFCB09A22151D89BD067D0BA0D92061473D493CB972A009C5C4E0CBCFA1552FCF2446EDA114A6E089F2F2DE3F9AA3A8673B6465358C88905BD8311B8733FAA078DF4424DE7409D1C370203010001A3133011300F0603551D130101FF040530030101FF300D06092A864886F70D01010405000381810026482C16C258FAE816740CAAAA5F543FF2D7C978605E5E6E37632277367EB217C434B9F50885FCC90138FF4DBEF2164243E7BB5A46FBC1C6111FF14AB02846C9C3C4427DBCFAAB596ED5B7518811E3A485196B824CA40C12ADE9A4AE3FF1C349659A8CC5C83E25B79499BB92327107F0865EED5027A60DA623F9BBCBA6071442 | |||
| (PID) Process: | (5164) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\627F8D7827656399D27D7F9044C9FEB3F33EFA9A |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000000400006800000001000000080000000000876ACE99D1011D0000000100000010000000D4803AC36C256817D4EC5936F29BC4E7090000000100000016000000301406082B0601050507030306082B0601050507030153000000010000002500000030233021060B6086480186F8450107300130123010060A2B0601040182373C0101030200C00F00000001000000100000005F3D1AA6F471A760663EB7EF254281EF030000000100000014000000627F8D7827656399D27D7F9044C9FEB3F33EFA9A1900000001000000100000005DC45E2CD1845791BDDE7600050AF510620000000100000020000000AB7036365C7154AA29C2C29F5D4191163B162A2225011357D56D07FFA7BC1F721400000001000000140000005FF3246C8F9124AF9B5F3EB0346AF42D5CA85DCC0B000000010000000E0000007400680061007700740065000000040000000100000010000000069F6979166690021B8C8CA2C3076F3A20000000010000002B0300003082032730820290A003020102020101300D06092A864886F70D01010405003081CE310B3009060355040613025A41311530130603550408130C5765737465726E204361706531123010060355040713094361706520546F776E311D301B060355040A131454686177746520436F6E73756C74696E6720636331283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E3121301F06035504031318546861777465205072656D69756D205365727665722043413128302606092A864886F70D01090116197072656D69756D2D736572766572407468617774652E636F6D301E170D3936303830313030303030305A170D3230313233313233353935395A3081CE310B3009060355040613025A41311530130603550408130C5765737465726E204361706531123010060355040713094361706520546F776E311D301B060355040A131454686177746520436F6E73756C74696E6720636331283026060355040B131F43657274696669636174696F6E205365727669636573204469766973696F6E3121301F06035504031318546861777465205072656D69756D205365727665722043413128302606092A864886F70D01090116197072656D69756D2D736572766572407468617774652E636F6D30819F300D06092A864886F70D010101050003818D0030818902818100D236366A8BD7C25B9EDA8141628F38EE490455D6D0EF1C1B951647EF1848353A52F42B6A068F3B2FEA56E3AF868D9E17F79EB46575024DEFCB09A22151D89BD067D0BA0D92061473D493CB972A009C5C4E0CBCFA1552FCF2446EDA114A6E089F2F2DE3F9AA3A8673B6465358C88905BD8311B8733FAA078DF4424DE7409D1C370203010001A3133011300F0603551D130101FF040530030101FF300D06092A864886F70D01010405000381810026482C16C258FAE816740CAAAA5F543FF2D7C978605E5E6E37632277367EB217C434B9F50885FCC90138FF4DBEF2164243E7BB5A46FBC1C6111FF14AB02846C9C3C4427DBCFAAB596ED5B7518811E3A485196B824CA40C12ADE9A4AE3FF1C349659A8CC5C83E25B79499BB92327107F0865EED5027A60DA623F9BBCBA6071442 | |||
| (PID) Process: | (5164) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (5164) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (5164) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (5164) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000C162B32DC0CADB019802000070190000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000C162B32DC0CADB019802000070190000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (664) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000E7C6B52DC0CADB019802000070190000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
78
Suspicious files
58
Text files
45
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5508 | evtrpt102a.exe | C:\Users\admin\AppData\Local\Temp\_isB607.tmp | — | |
MD5:— | SHA256:— | |||
| 5508 | evtrpt102a.exe | C:\Users\admin\AppData\Local\Temp\{7B04A177-45DE-4B96-8425-FD1BB93F9D39}\EventReporter.msi | — | |
MD5:— | SHA256:— | |||
| 5508 | evtrpt102a.exe | C:\ProgramData\{88336AD7-C2F3-422A-8282-A62841F86EC1}\EventReporter.msi | — | |
MD5:— | SHA256:— | |||
| 5508 | evtrpt102a.exe | C:\Users\admin\AppData\Local\Temp\_isB548.tmp | binary | |
MD5:5B89F7DBF0C63354C26115696B68B0C9 | SHA256:19B61A4840B2D6E92B91334A60AFB32B6FA45E7E6D57B740D7E3A38461B3A8FC | |||
| 664 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 664 | msiexec.exe | C:\Windows\Installer\115d5f.msi | — | |
MD5:— | SHA256:— | |||
| 5508 | evtrpt102a.exe | C:\Users\admin\AppData\Local\Temp\_isB57A.tmp | binary | |
MD5:5B89F7DBF0C63354C26115696B68B0C9 | SHA256:19B61A4840B2D6E92B91334A60AFB32B6FA45E7E6D57B740D7E3A38461B3A8FC | |||
| 5508 | evtrpt102a.exe | C:\Users\admin\AppData\Local\Temp\{7B04A177-45DE-4B96-8425-FD1BB93F9D39}\_ISMSIDEL.INI | text | |
MD5:BC8BD1A103DAA0BAEE81C925423D7CF6 | SHA256:4F645E15999F63F80DBD08B972C7C304CA279A77AD4F3E866E9C75AA1D193ACB | |||
| 5164 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSID7B6.tmp | executable | |
MD5:8A33CCD179F5C998017CE0083943E420 | SHA256:B1F19818E52E4B6ACE51388148CBA47783491D25CBC3BC3A3D3B292B674D17AD | |||
| 664 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{d43a6bb5-8ef6-447d-b7ef-42cc413005d7}_OnDiskSnapshotProp | binary | |
MD5:9BF06D1530B4D838F7BD533EE85BF19F | SHA256:E6E61F3C36BBC52E95AA9BA6C89D6DC77866A82BF252C59E4FE41968BB2F202F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
31
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5164 | msiexec.exe | GET | 200 | 2.17.189.192:80 | http://crl.thawte.com/ThawtePremiumServerCA.crl | unknown | — | — | whitelisted |
5164 | msiexec.exe | GET | 200 | 2.17.189.192:80 | http://crl.thawte.com/ThawtePremiumServerCA.crl | unknown | — | — | whitelisted |
5164 | msiexec.exe | GET | 200 | 2.17.189.192:80 | http://ocsp.thawte.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSDXMN22sHhCJ%2BQ8WDKToovi3RuCgQUxe2TXys4R35Y01fH%2F0XFREHhX78CEAmyW%2FFVaSfmAYR%2FLp8SFGQ%3D | unknown | — | — | whitelisted |
5164 | msiexec.exe | GET | 200 | 2.17.189.192:80 | http://ocsp.thawte.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSDXMN22sHhCJ%2BQ8WDKToovi3RuCgQUxe2TXys4R35Y01fH%2F0XFREHhX78CEAmyW%2FFVaSfmAYR%2FLp8SFGQ%3D | unknown | — | — | whitelisted |
5164 | msiexec.exe | GET | 200 | 2.17.189.192:80 | http://crl.thawte.com/ThawteCodeSigningCA.crl | unknown | — | — | whitelisted |
6644 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
— | — | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.thawte.com |
| whitelisted |
ocsp.thawte.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |