| download: | /forticlient/win/vpnagent |
| Full analysis: | https://app.any.run/tasks/869a3b6f-76a3-4000-83a0-ca5d6907b1b1 |
| Verdict: | Malicious activity |
| Analysis date: | October 23, 2024, 09:19:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 11BFC265FC53AC4756E4EF2759CA10EB |
| SHA1: | E3D2BF11618C39DFD036BB33EA96AA5F989FED25 |
| SHA256: | 2E520FAA2B71BA56643153B77C2908C0D6DA34A2F6F9ABAA7CBADAB9278DC99E |
| SSDEEP: | 98304:Fvs0nKhLE+vtgITiwgX672SJGqa1sI8XOcup2xvHdXPSmU8mdLRhQCX:c/2nL0a |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- scheduler.exe (PID: 7152)
Starts NET.EXE for service management
- net.exe (PID: 6940)
- FortiSSLVPNdaemon.exe (PID: 5420)
SUSPICIOUS
Reads security settings of Internet Explorer
- vpnagent.exe (PID: 6436)
Application launched itself
- vpnagent.exe (PID: 6436)
- VC_redist.x64.exe (PID: 6232)
- VC_redist.x64.exe (PID: 6804)
- VC_redist.x86.exe (PID: 1180)
- FortiClient.exe (PID: 6940)
- VC_redist.x86.exe (PID: 4304)
Creates/Modifies COM task schedule object
- vpnagent.exe (PID: 3276)
Executable content was dropped or overwritten
- FortiClientVPN.exe (PID: 1712)
- drvinst.exe (PID: 4060)
- drvinst.exe (PID: 4556)
- drvinst.exe (PID: 5196)
- drvinst.exe (PID: 6644)
- drvinst.exe (PID: 4144)
- VC_redist.x64.exe (PID: 3532)
- VC_redist.x64.exe (PID: 1376)
- VC_redist.x64.exe (PID: 4080)
- VC_redist.x64.exe (PID: 6804)
- VC_redist.x64.exe (PID: 6664)
- VC_redist.x86.exe (PID: 7156)
- VC_redist.x86.exe (PID: 4308)
- VC_redist.x86.exe (PID: 1452)
- VC_redist.x86.exe (PID: 4304)
- update_task.exe (PID: 2632)
- VC_redist.x86.exe (PID: 5048)
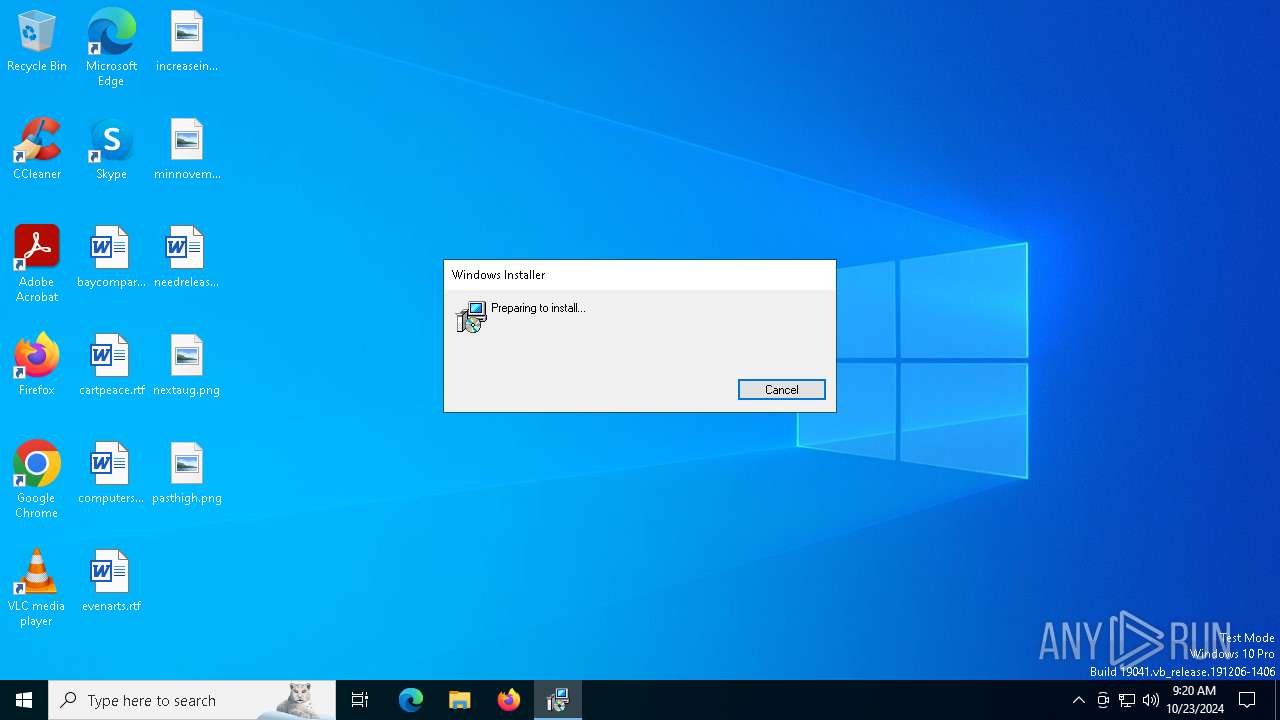
Process drops legitimate windows executable
- msiexec.exe (PID: 4808)
- msiexec.exe (PID: 3432)
- VC_redist.x64.exe (PID: 3532)
- VC_redist.x64.exe (PID: 1376)
- VC_redist.x64.exe (PID: 4080)
- VC_redist.x86.exe (PID: 4308)
- VC_redist.x64.exe (PID: 6664)
- VC_redist.x86.exe (PID: 7156)
- VC_redist.x86.exe (PID: 1452)
- VC_redist.x86.exe (PID: 5048)
- update_task.exe (PID: 2632)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 4808)
- drvinst.exe (PID: 4060)
- drvinst.exe (PID: 5196)
- drvinst.exe (PID: 4144)
Starts itself from another location
- VC_redist.x64.exe (PID: 1376)
- VC_redist.x86.exe (PID: 4308)
The process drops C-runtime libraries
- msiexec.exe (PID: 3432)
- msiexec.exe (PID: 4808)
Starts a Microsoft application from unusual location
- VC_redist.x64.exe (PID: 1376)
- VC_redist.x64.exe (PID: 4080)
- VC_redist.x86.exe (PID: 4308)
- VC_redist.x86.exe (PID: 1452)
Executes as Windows Service
- VSSVC.exe (PID: 6976)
- scheduler.exe (PID: 7152)
Starts CMD.EXE for commands execution
- FortiClient.exe (PID: 6940)
INFO
Process checks whether UAC notifications are on
- vpnagent.exe (PID: 6436)
Create files in a temporary directory
- vpnagent.exe (PID: 6436)
- vpnagent.exe (PID: 3276)
Checks supported languages
- vpnagent.exe (PID: 6436)
- vpnagent.exe (PID: 3276)
Process checks computer location settings
- vpnagent.exe (PID: 6436)
The process uses the downloaded file
- vpnagent.exe (PID: 6436)
Reads the computer name
- vpnagent.exe (PID: 6436)
- vpnagent.exe (PID: 3276)
Application launched itself
- msiexec.exe (PID: 4808)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4808)
- msiexec.exe (PID: 3432)
Manages system restore points
- SrTasks.exe (PID: 5584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:05:31 22:26:46+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.37 |
| CodeSize: | 1854464 |
| InitializedDataSize: | 951296 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6fd60 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
193
Monitored processes
53
Malicious processes
4
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1084 | -s FC_{73EFB30F-1CAD-4a7a-AE2E-150282B6CE25}_000008 | C:\Program Files\Fortinet\FortiClient\FortiTray.exe | — | scheduler.exe | |||||||||||
User: admin Company: Fortinet Inc. Integrity Level: MEDIUM Description: FortiClient System Tray Controller Version: 7.4.0.1658 | |||||||||||||||
| 1180 | "C:\ProgramData\Package Cache\{410c0ee1-00bb-41b6-9772-e12c2828b02f}\VC_redist.x86.exe" -uninstall -quiet -burn.related.upgrade -burn.ancestors={46c3b171-c15c-4137-8e1d-67eeb2985b44} -burn.filehandle.self=920 -burn.embedded BurnPipe.{4F7A919D-DBC2-43BD-A318-3913C913ABA6} {2D17EB9C-CCCD-4862-BCF7-0C8FD431D419} 1452 | C:\ProgramData\Package Cache\{410c0ee1-00bb-41b6-9772-e12c2828b02f}\VC_redist.x86.exe | — | VC_redist.x86.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Visual C++ 2015-2022 Redistributable (x86) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 | |||||||||||||||
| 1376 | "C:\WINDOWS\Temp\{2A89E50C-26C1-42A1-A5D0-6B0EDADBF266}\.cr\VC_redist.x64.exe" -burn.clean.room="C:\Program Files\Common Files\Fortinet\FortiClient\VC_redist.x64.exe" -burn.filehandle.attached=884 -burn.filehandle.self=888 /install /quiet /norestart | C:\Windows\Temp\{2A89E50C-26C1-42A1-A5D0-6B0EDADBF266}\.cr\VC_redist.x64.exe | VC_redist.x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.38.33135 Exit code: 3010 Version: 14.38.33135.0 Modules
| |||||||||||||||
| 1396 | C:\WINDOWS\system32\cmd.exe /d /s /c "uname -v" | C:\Windows\System32\cmd.exe | — | FortiClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1452 | "C:\WINDOWS\Temp\{798472C0-F604-4B36-BB6E-C21DC70E1245}\.be\VC_redist.x86.exe" -q -burn.elevated BurnPipe.{33E24BB0-D113-4F5E-B229-67C478E78A8E} {7E567070-D269-4B66-A0E7-EFECBB0D88F3} 4308 | C:\Windows\Temp\{798472C0-F604-4B36-BB6E-C21DC70E1245}\.be\VC_redist.x86.exe | VC_redist.x86.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Visual C++ 2015-2022 Redistributable (x86) - 14.38.33135 Exit code: 0 Version: 14.38.33135.0 | |||||||||||||||
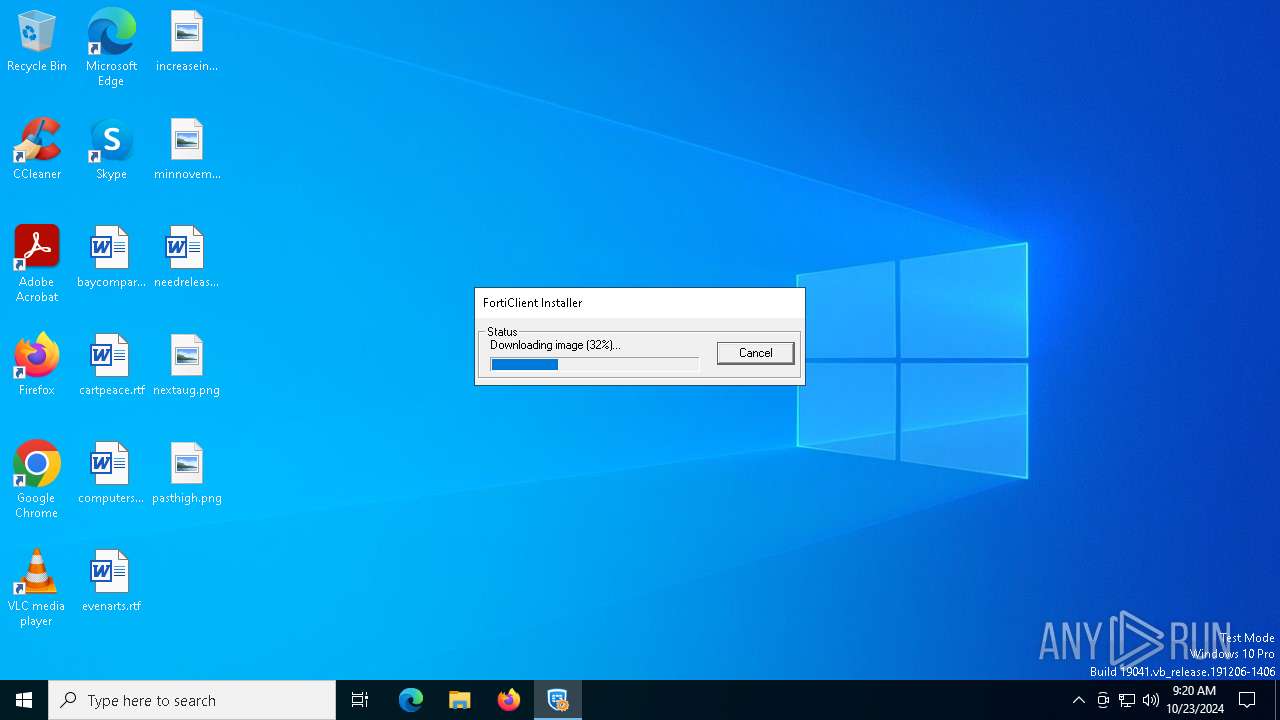
| 1712 | C:\Users\admin\AppData\Local\Temp\FortiClientVPN.exe | C:\Users\admin\AppData\Local\Temp\FortiClientVPN.exe | vpnagent.exe | ||||||||||||
User: admin Company: Fortinet Inc. Integrity Level: HIGH Description: FortiClient Installer Exit code: 0 Version: 7.4.0.1658 Modules
| |||||||||||||||
| 1744 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files\Fortinet\FortiClient\FortiCliSh.Dll" | C:\Windows\System32\regsvr32.exe | — | scheduler.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2632 | update_task.exe -s FC_{73EFB30F-1CAD-4a7a-AE2E-150282B6CE25}_001000 | C:\Program Files\Fortinet\FortiClient\update_task.exe | scheduler.exe | ||||||||||||
User: SYSTEM Company: Fortinet Inc. Integrity Level: SYSTEM Description: update_task Exit code: 0 Version: 7.4.0.1658 | |||||||||||||||
| 3028 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3276 | "C:\Users\admin\AppData\Local\Temp\vpnagent.exe" | C:\Users\admin\AppData\Local\Temp\vpnagent.exe | vpnagent.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
29 837
Read events
28 898
Write events
913
Delete events
26
Modification events
| (PID) Process: | (3276) vpnagent.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{8052F904-874D-4d28-9380-AA9BDBF13AFD}\InProcServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: diskcopy.dll | |||
| (PID) Process: | (3276) vpnagent.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{8052F904-874D-4d28-9380-AA9BDBF13AFD}\InProcServer32 |
| Operation: | write | Name: | AppID |
Value: {F25B3DB8-063A-4118-BF42-F86D98D24986} | |||
| (PID) Process: | (1712) FortiClientVPN.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (1712) FortiClientVPN.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (1712) FortiClientVPN.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (1712) FortiClientVPN.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (4808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (4808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\9dbfd.rbs |
Value: 31139116 | |||
| (PID) Process: | (4808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\9dbfd.rbsLow |
Value: | |||
| (PID) Process: | (4808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\D8CB2D1BB5E89594398CF30B3D667629 |
| Operation: | write | Name: | 06715CD07BF43F1498763DED9C3D02BE |
Value: C:\Program Files\Common Files\Fortinet\FortiClient\VC_redist.x64.exe | |||
Executable files
288
Suspicious files
283
Text files
159
Unknown types
27
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3276 | vpnagent.exe | C:\Users\admin\AppData\Local\Temp\FortiClientVPN.exe | — | |
MD5:— | SHA256:— | |||
| 1712 | FortiClientVPN.exe | C:\Users\admin\AppData\Local\Temp\FCT_{625BC4BA-AC3E-4E4B-9996-EEED9D4287C3}\{478238F5-7DC3-4287-8703-8A6CF188038D}\FortiClient.msi | — | |
MD5:— | SHA256:— | |||
| 1712 | FortiClientVPN.exe | C:\ProgramData\Applications\Cache\{0DC51760-4FB7-41F3-8967-D3DEC9D320EB}\7.4.0.1658\FortiClient.msi | — | |
MD5:— | SHA256:— | |||
| 4808 | msiexec.exe | C:\Windows\Installer\9dbfc.msi | — | |
MD5:— | SHA256:— | |||
| 4808 | msiexec.exe | C:\Windows\Installer\MSIE64E.tmp | executable | |
MD5:32EFBFFDA3376EE49D78BAFF6BCE3CC5 | SHA256:F64E2CAD4CDCC53694CA3DBD78B941039064D31EA5892D4DED3A533F0FED627A | |||
| 1712 | FortiClientVPN.exe | C:\Users\admin\AppData\Local\Temp\FortiClient00000.log | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 4808 | msiexec.exe | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngen.log | text | |
MD5:3F842A89CDCEEDFBD4106FE049B48C2C | SHA256:4A9B9A820B19431D787BB47F9F4FA4A37CD2FDF19CB8FF4E0A6012CB33CFBCB2 | |||
| 1712 | FortiClientVPN.exe | C:\Users\admin\AppData\Local\Temp\~DFFE8EBC1E2D7617DE.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 3276 | vpnagent.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:92CF419EFC962B25B29C5686EEE93864 | SHA256:2F157E7A6AEA4797558C70E5334C397A8A5DF9BFE960C3F79E8696D577F7F27D | |||
| 3276 | vpnagent.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:28977B150221DC782227FA7288EF7415 | SHA256:1D2AE9F26491E68EF5BABA5BE29A30B1EAFA3B58243C1767BE53898604E5A1C3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
92
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3276 | vpnagent.exe | POST | 200 | 208.184.237.75:80 | http://208.184.237.75/fdsupdate | unknown | — | — | unknown |
3276 | vpnagent.exe | POST | 200 | 208.184.237.75:80 | http://208.184.237.75/fdsupdate | unknown | — | — | unknown |
6944 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3276 | vpnagent.exe | POST | — | 208.184.237.75:80 | http://208.184.237.75/fdsupdate | unknown | — | — | unknown |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
692 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2576 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2576 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5508 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5700 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3276 | vpnagent.exe | 208.184.237.75:80 | forticlient.fortinet.net | FORTINET | US | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 104.126.37.162:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
forticlient.fortinet.net |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |