| File name: | RADMIN21.EXE (S7-13-043861) |
| Full analysis: | https://app.any.run/tasks/a7dbcf2a-5fbd-450e-a83b-e268f6393567 |
| Verdict: | Malicious activity |
| Analysis date: | July 23, 2024, 13:29:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 407449F2A326A81163B76B7354CAE031 |
| SHA1: | FB0F643C5D5E4A030D1228AE64F814A9DAA122FD |
| SHA256: | 2E27E349E8D1F9EC51B4A1DACD958B941BDFC0308AD9E68B0037A31B4880BDFF |
| SSDEEP: | 49152:QlktLdTkc1jbh1GFj/dl54RvgfXil63T7cDGUEo/pLDivR665IPrV7VjSVrd3Vqx:QlktLV1jrU/dle2Xz3TS1RLDivg6+DVv |
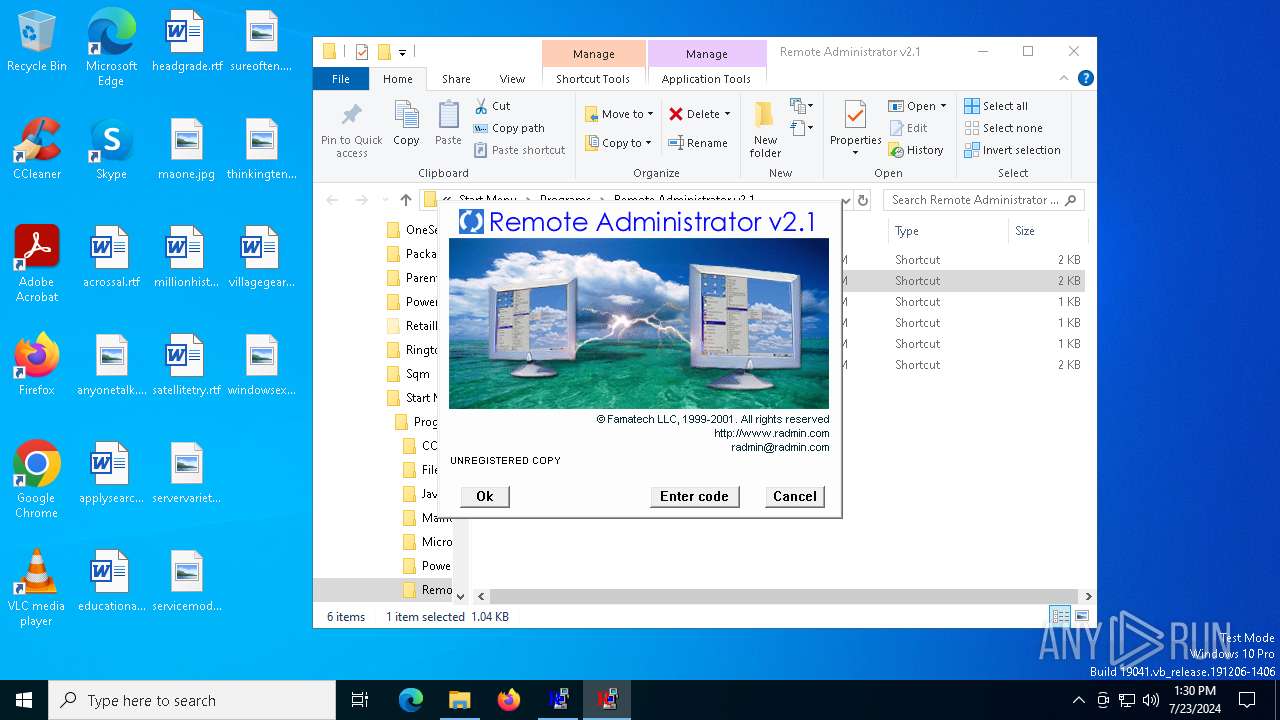
MALICIOUS
Drops the executable file immediately after the start
- RADMIN21.EXE (S7-13-043861).exe (PID: 324)
SUSPICIOUS
Creates file in the systems drive root
- RADMIN21.EXE (S7-13-043861).exe (PID: 324)
Reads security settings of Internet Explorer
- RADMIN21.EXE (S7-13-043861).exe (PID: 324)
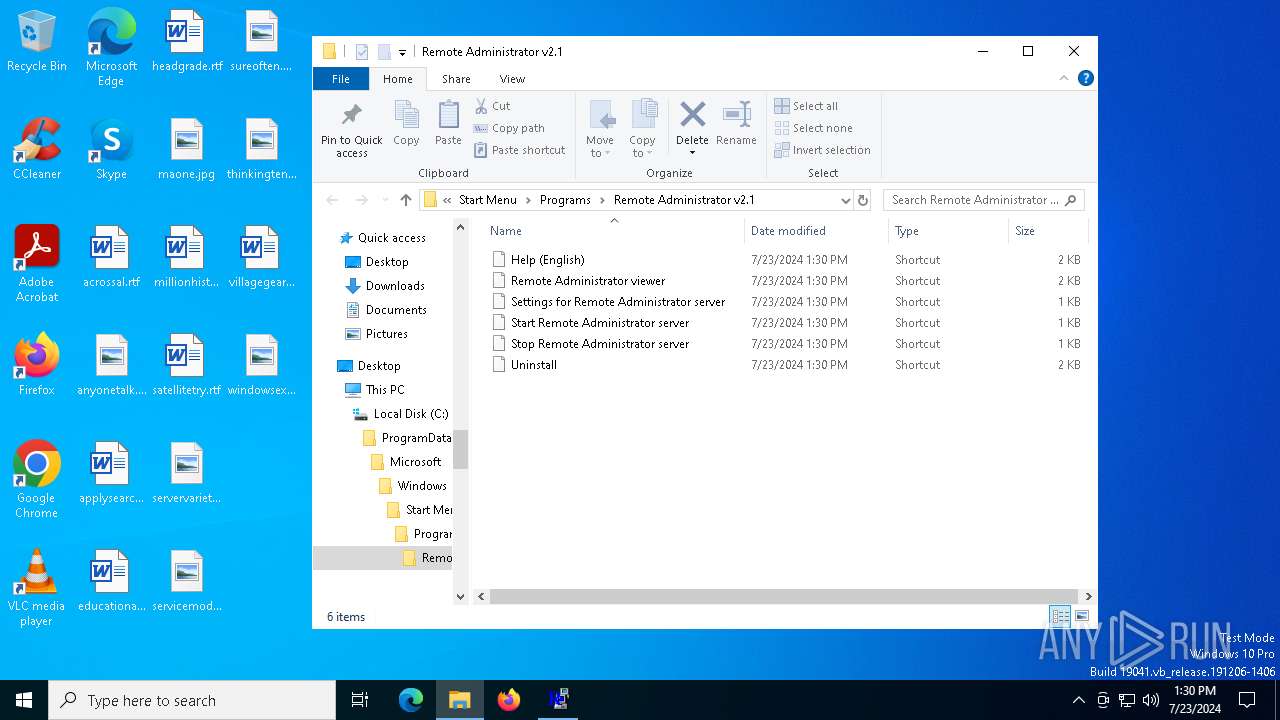
Creates a software uninstall entry
- RADMIN21.EXE (S7-13-043861).exe (PID: 324)
Executable content was dropped or overwritten
- RADMIN21.EXE (S7-13-043861).exe (PID: 324)
INFO
Reads the computer name
- RADMIN21.EXE (S7-13-043861).exe (PID: 324)
- r_server.exe (PID: 5680)
- radmin.exe (PID: 5244)
- r_server.exe (PID: 6484)
- r_server.exe (PID: 1080)
Checks supported languages
- RADMIN21.EXE (S7-13-043861).exe (PID: 324)
- r_server.exe (PID: 5680)
- radmin.exe (PID: 5244)
- r_server.exe (PID: 6484)
- r_server.exe (PID: 1080)
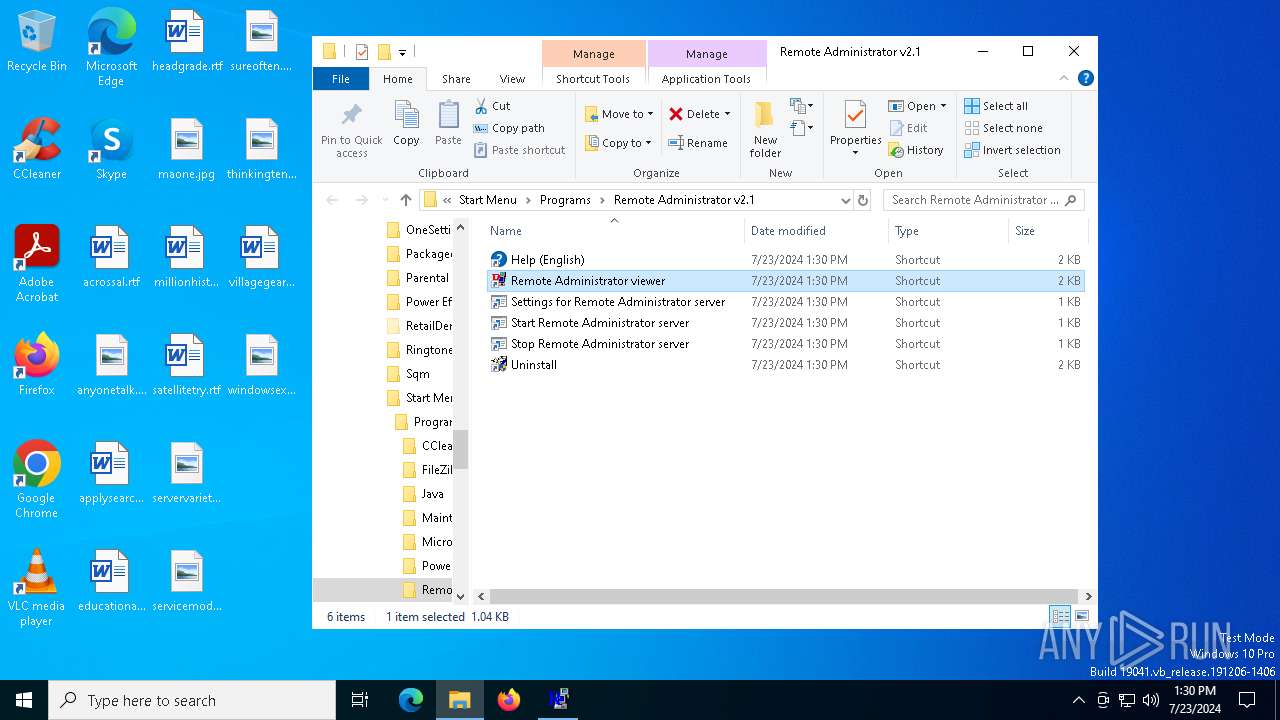
Creates files in the program directory
- RADMIN21.EXE (S7-13-043861).exe (PID: 324)
Manual execution by a user
- radmin.exe (PID: 5244)
- r_server.exe (PID: 6484)
- r_server.exe (PID: 1080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (50.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.6) |
| .exe | | | Win32 Executable (generic) (5.2) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1999:10:06 10:33:39+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 3 |
| CodeSize: | 2560 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1020 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
140
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Users\admin\AppData\Local\Temp\RADMIN21.EXE (S7-13-043861).exe" | C:\Users\admin\AppData\Local\Temp\RADMIN21.EXE (S7-13-043861).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1080 | "C:\Windows\SysWOW64\r_server.exe" /start | C:\Windows\SysWOW64\r_server.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 4136 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | "C:\Program Files (x86)\Radmin\radmin.exe" | C:\Program Files (x86)\Radmin\radmin.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5680 | C:\WINDOWS\system32\r_server.exe /intsetup | C:\Windows\SysWOW64\r_server.exe | — | RADMIN21.EXE (S7-13-043861).exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6228 | "C:\Users\admin\AppData\Local\Temp\RADMIN21.EXE (S7-13-043861).exe" | C:\Users\admin\AppData\Local\Temp\RADMIN21.EXE (S7-13-043861).exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6228 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6484 | "C:\Windows\SysWOW64\r_server.exe" /start | C:\Windows\SysWOW64\r_server.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
2 466
Read events
2 464
Write events
2
Delete events
0
Modification events
| (PID) Process: | (324) RADMIN21.EXE (S7-13-043861).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Remote Administrator v2.1 |
| Operation: | write | Name: | DisplayName |
Value: Remote Administrator v2.1 | |||
| (PID) Process: | (324) RADMIN21.EXE (S7-13-043861).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Remote Administrator v2.1 |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\Radmin\uninstal.exe | |||
Executable files
9
Suspicious files
0
Text files
7
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 324 | RADMIN21.EXE (S7-13-043861).exe | C:\temp\license.txt | text | |
MD5:7019746D6D89EFFEB872BD2CB5C44B7E | SHA256:6FE7B8B79695F749376812DDDBBE0A079445D14295DB285583A0EBF3E394457D | |||
| 324 | RADMIN21.EXE (S7-13-043861).exe | C:\temp\Default.bmp | image | |
MD5:F372B11FF99BFFED4CD279C0155ADEDE | SHA256:D9D5E28EB445E7986BDEF4D409868AF205D525F2F0729427DFE3E33A7251B15D | |||
| 324 | RADMIN21.EXE (S7-13-043861).exe | C:\Program Files (x86)\Radmin\AdmDll.dll | executable | |
MD5:C915181E93FE3D4C41B1963180D3C535 | SHA256:D8FC5D545E684A4D5001004463F762D190BEE478EB3A329F65998BAD53D3C958 | |||
| 324 | RADMIN21.EXE (S7-13-043861).exe | C:\Program Files (x86)\Radmin\help.hlp | hlp | |
MD5:310D3659F70C8160E5A4972546B27991 | SHA256:60DAF73D57A1B37585ADEC9686EA8542378105BDC138D5992B3DE809411662CC | |||
| 324 | RADMIN21.EXE (S7-13-043861).exe | C:\Program Files (x86)\Radmin\raddrv.dll | executable | |
MD5:B50D22AB0323CBD0FEDFDF4689BC1301 | SHA256:970786CAF18EF731B0E1A562E7155C7B7FE525FC000C14A6156AC19292922BC0 | |||
| 324 | RADMIN21.EXE (S7-13-043861).exe | C:\Program Files (x86)\Radmin\radmin.exe | executable | |
MD5:A4FD3C0387F587DA36A6838117C7C6B5 | SHA256:4BE8A275655DE01600BE147B9E69DB6DB8F71ACC9BDCBF996611F6FCA6E83FCD | |||
| 324 | RADMIN21.EXE (S7-13-043861).exe | C:\temp\0readme.txt | text | |
MD5:87ED9E4141F028CD468DCA088F7CF1F0 | SHA256:8D4C3C66F55E4A8AFFDED9BDFD443C0170584E7371A3E373B39204EFA5F45257 | |||
| 324 | RADMIN21.EXE (S7-13-043861).exe | C:\ginstall.dll | executable | |
MD5:38A9142BA7B74DB9A68B3691C970BD89 | SHA256:ED866C7802EDC00235BD25AA2AE2EC6658EB8CB74301B930A96AB9AB42ED93A2 | |||
| 324 | RADMIN21.EXE (S7-13-043861).exe | C:\Program Files (x86)\Radmin\README.TXT | text | |
MD5:2EEA3438E9D6F045E4F7BDA0B4EBE53E | SHA256:2AFEAB6567E67D4B09A1E2F643D07FD4F10F8A3F19D47C31F7E5E4B430F038FF | |||
| 324 | RADMIN21.EXE (S7-13-043861).exe | C:\Program Files (x86)\Radmin\help.cnt | text | |
MD5:82806DFB63E7DA606E140ED4C57DF04F | SHA256:64EA140CBC44E9BCA334CAD892F0691BAF6ACB7F08D511A6A24BCFF336D670BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
39
DNS requests
17
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.23.209.168:443 | — | Akamai International B.V. | GB | unknown |
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4204 | svchost.exe | 4.209.33.156:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5368 | SearchApp.exe | 92.123.104.9:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5272 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5436 | backgroundTaskHost.exe | 92.123.104.9:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3296 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |