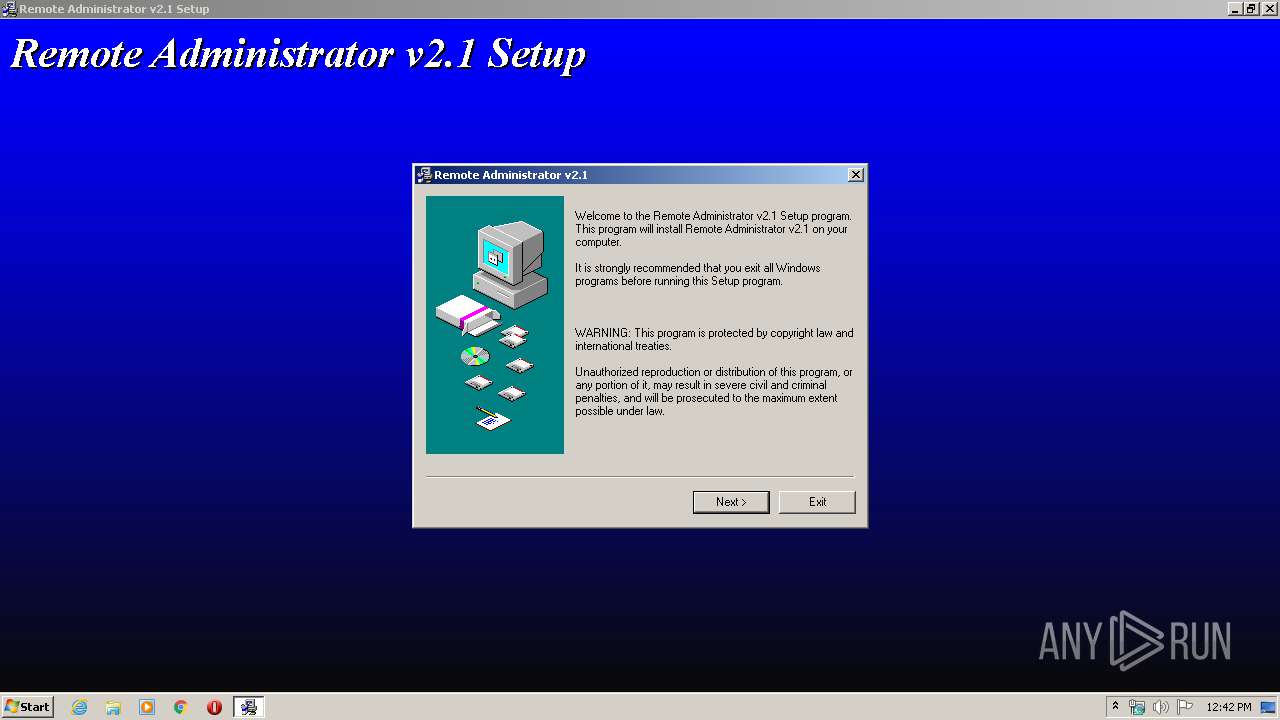
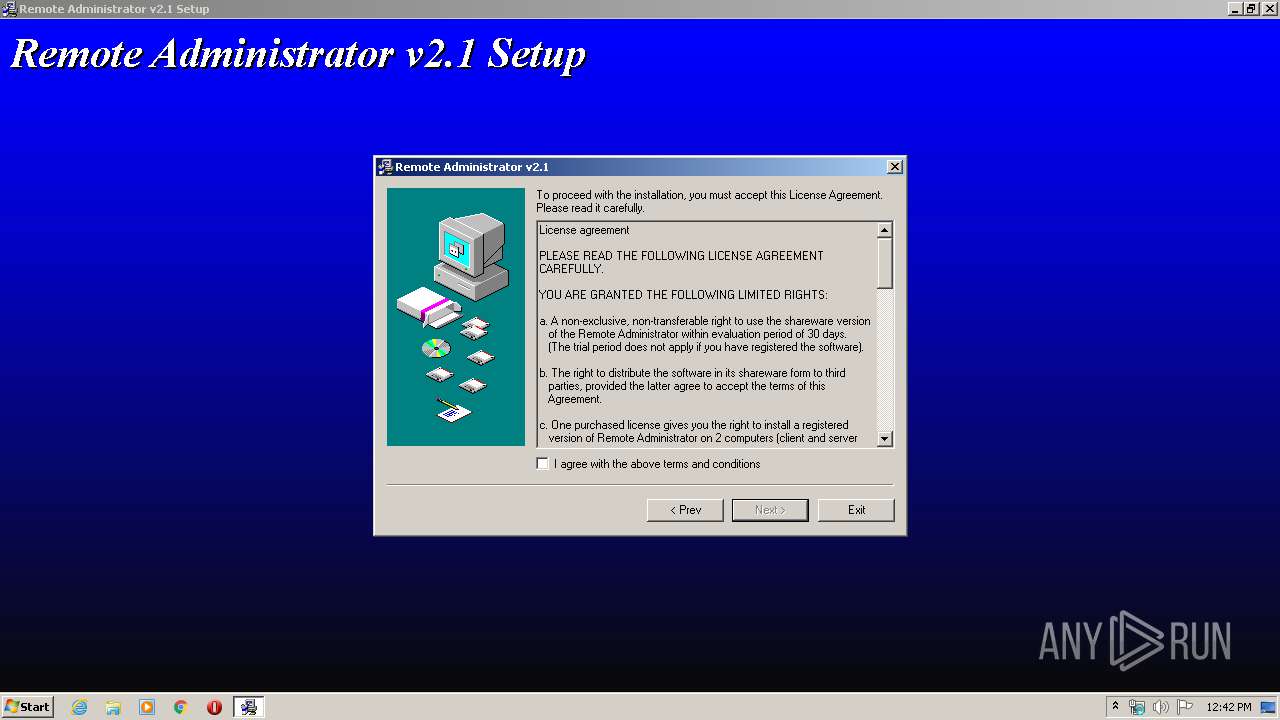
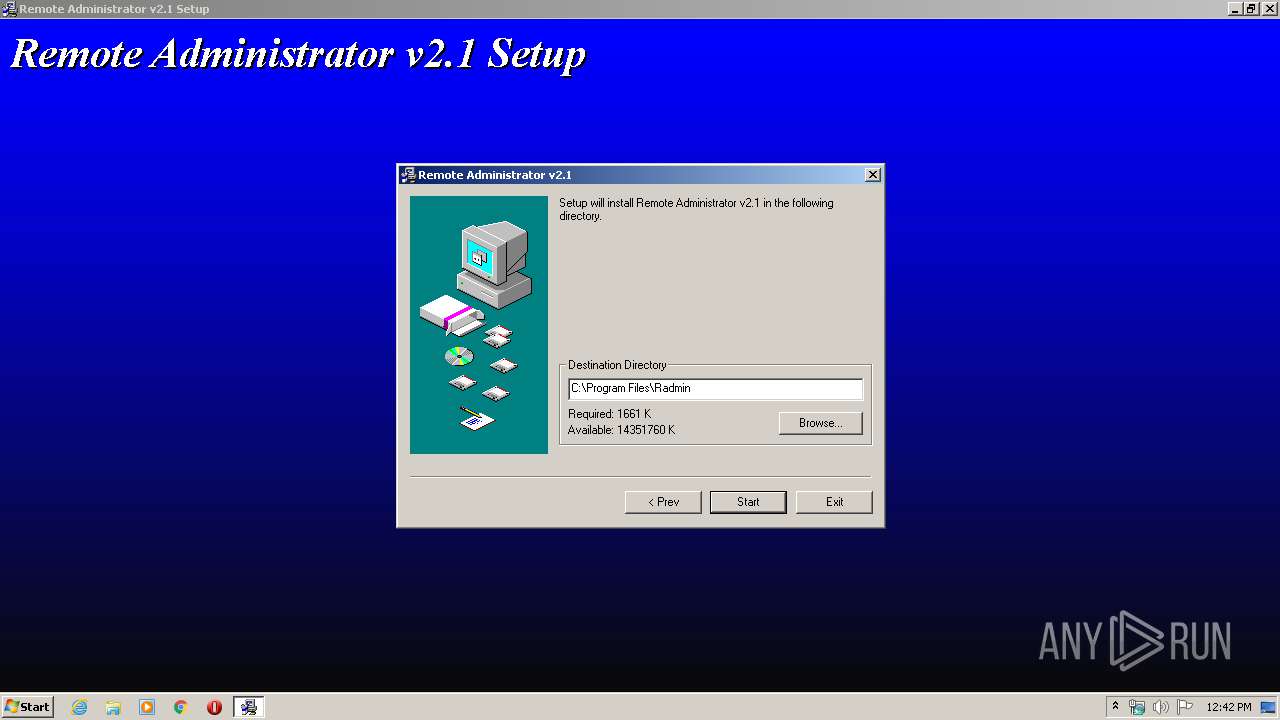
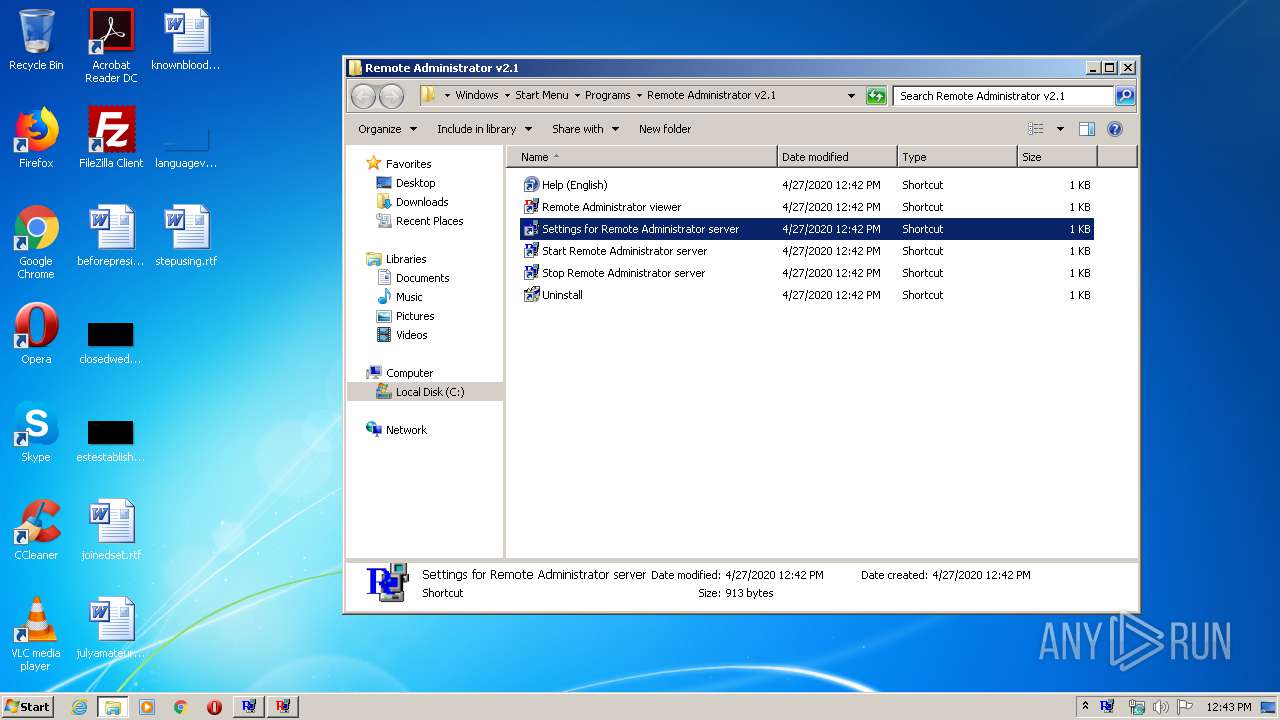
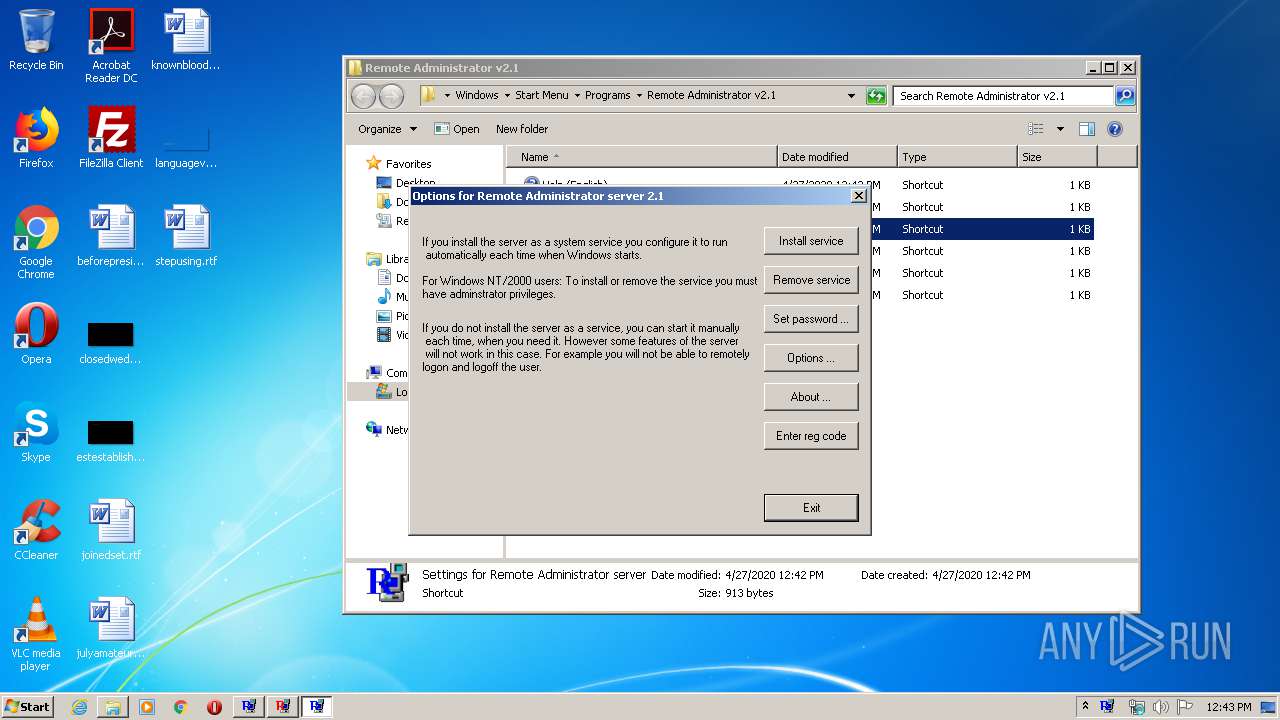
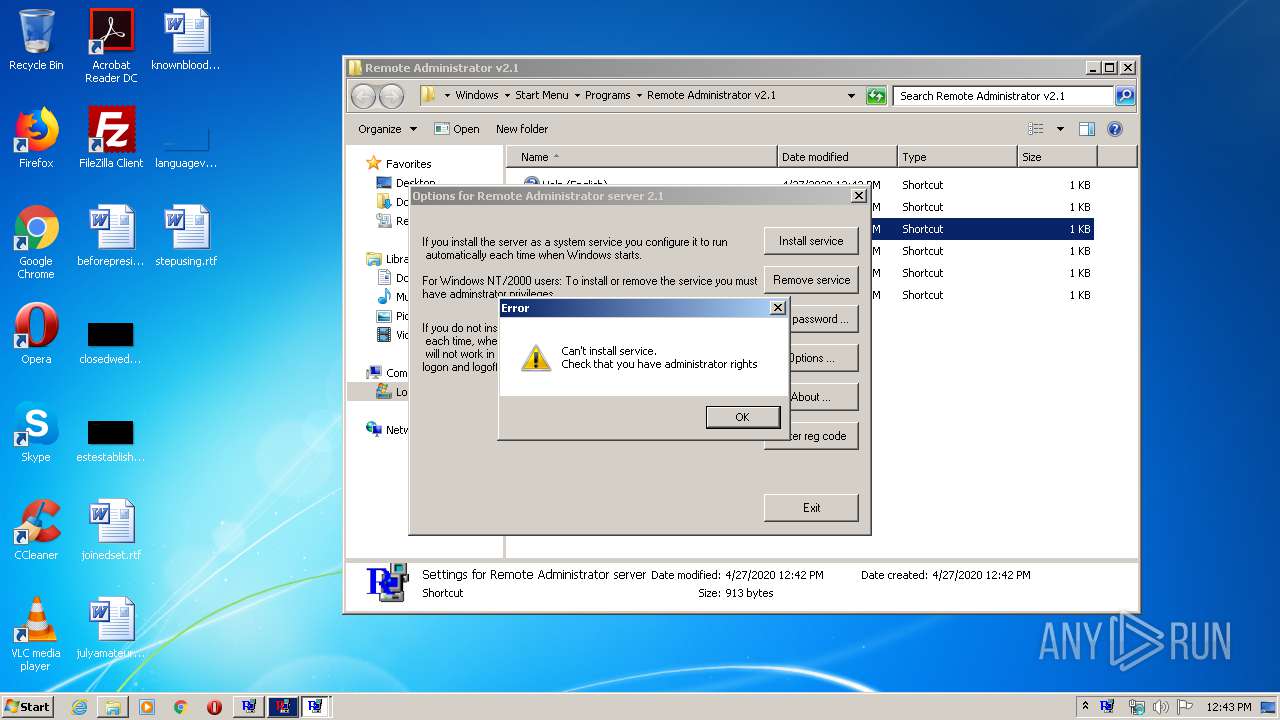
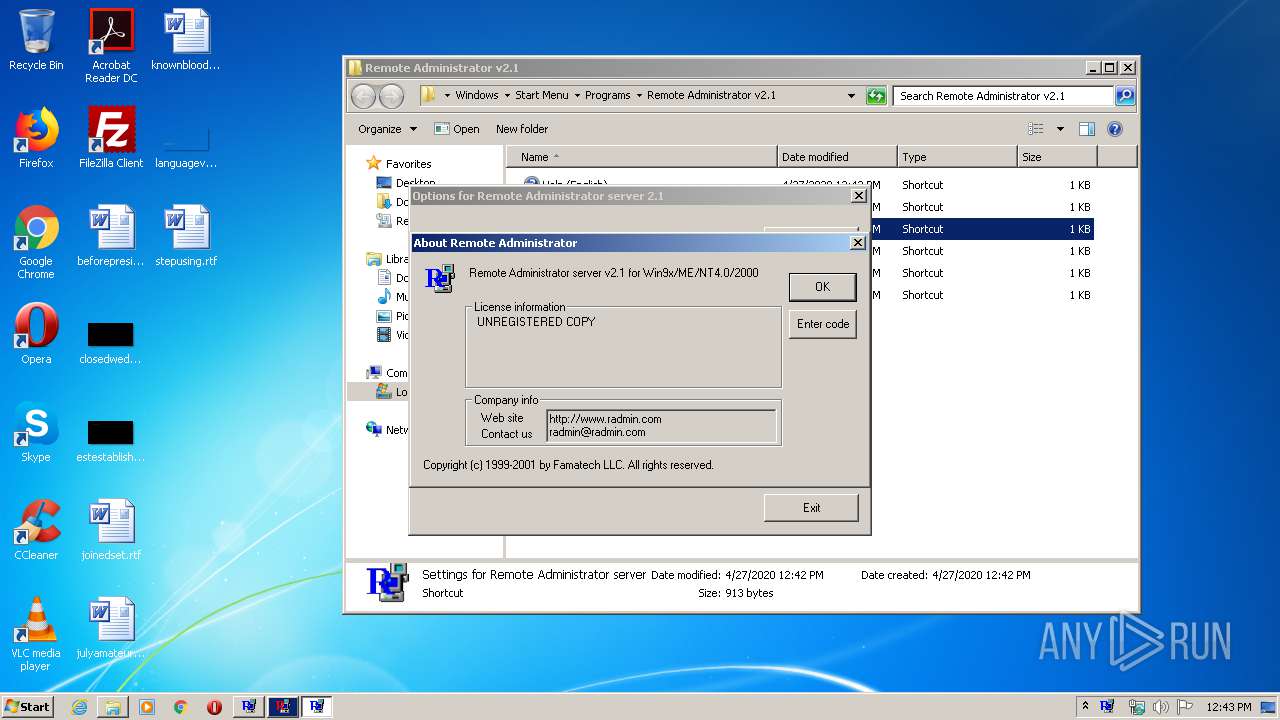
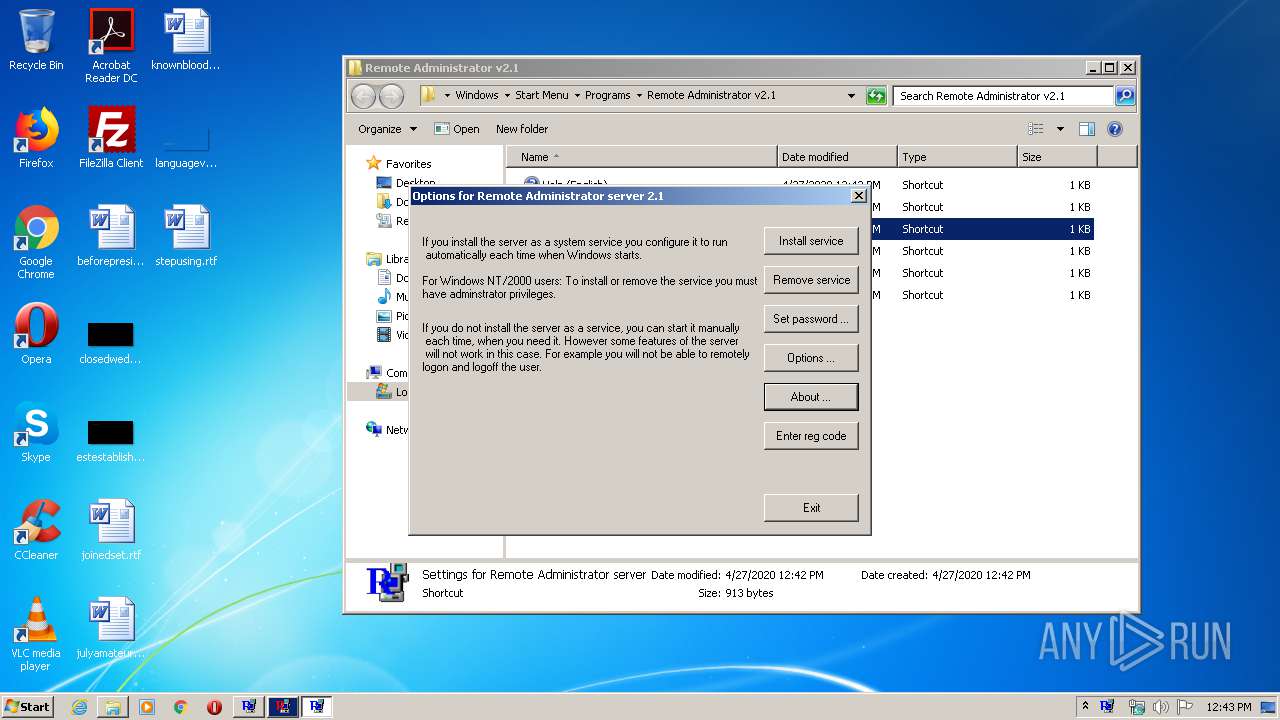
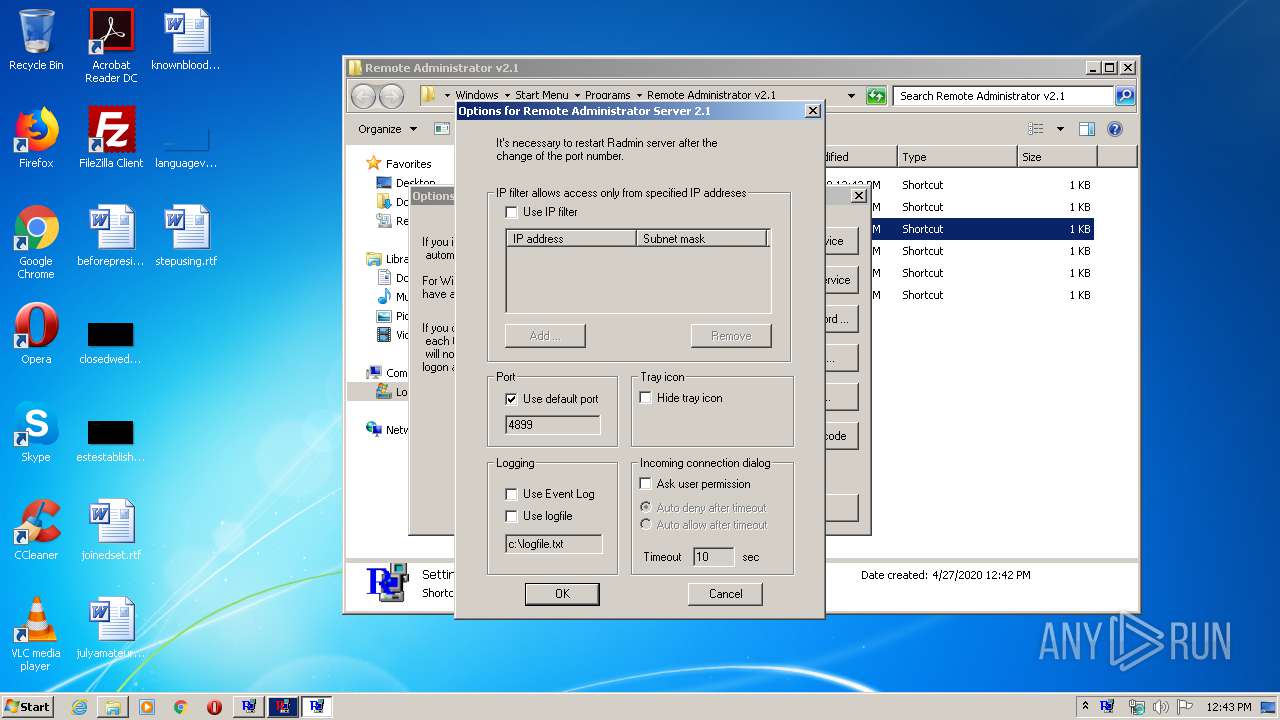
| File name: | Radmin21.exe |
| Full analysis: | https://app.any.run/tasks/9c19d7ba-4dca-4ad6-8b2d-e2ea13517edb |
| Verdict: | Malicious activity |
| Analysis date: | April 27, 2020, 11:42:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 407449F2A326A81163B76B7354CAE031 |
| SHA1: | FB0F643C5D5E4A030D1228AE64F814A9DAA122FD |
| SHA256: | 2E27E349E8D1F9EC51B4A1DACD958B941BDFC0308AD9E68B0037A31B4880BDFF |
| SSDEEP: | 24576:nnqWpxcFsH4FRBlLfZAG+oPiyieMxzxIsPyUQdFnBYLRVQvJiP:nnppUsH4bBltAno6Ltx2sPLQtYLr |
MALICIOUS
Loads dropped or rewritten executable
- Radmin21.exe (PID: 676)
- r_server.exe (PID: 3364)
- r_server.exe (PID: 3128)
- r_server.exe (PID: 2968)
- r_server.exe (PID: 2896)
- radmin.exe (PID: 3148)
- r_server.exe (PID: 3324)
Application was dropped or rewritten from another process
- radmin.exe (PID: 3148)
- r_server.exe (PID: 3364)
- r_server.exe (PID: 3128)
- r_server.exe (PID: 2896)
- r_server.exe (PID: 3324)
- r_server.exe (PID: 2968)
SUSPICIOUS
Creates files in the Windows directory
- Radmin21.exe (PID: 676)
Creates files in the program directory
- Radmin21.exe (PID: 676)
Creates a software uninstall entry
- Radmin21.exe (PID: 676)
Executable content was dropped or overwritten
- Radmin21.exe (PID: 676)
INFO
Manual execution by user
- r_server.exe (PID: 2968)
- r_server.exe (PID: 3128)
- r_server.exe (PID: 2896)
- radmin.exe (PID: 3148)
- r_server.exe (PID: 3324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (50.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.6) |
| .exe | | | Win32 Executable (generic) (5.2) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1999:10:06 12:33:39+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 3 |
| CodeSize: | 2560 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1020 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Oct-1999 10:33:39 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 7 |
| Time date stamp: | 06-Oct-1999 10:33:39 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000009F8 | 0x00000A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.27597 |
.rdata | 0x00002000 | 0x00000004 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.0407808 |
.data | 0x00003000 | 0x0000025C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.07382 |
.idata | 0x00004000 | 0x000002FE | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.83057 |
.Shared | 0x00005000 | 0x00000004 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED, IMAGE_SCN_MEM_WRITE | 0.0659144 |
.rsrc | 0x00006000 | 0x0000039C | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.189 |
.reloc | 0x00007000 | 0x000001B2 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.36734 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.38813 | 744 | UNKNOWN | English - United States | RT_ICON |
101 | 2.16096 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
KERNEL32.dll |
USER32.dll |
Total processes
47
Monitored processes
8
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 676 | "C:\Users\admin\AppData\Local\Temp\Radmin21.exe" | C:\Users\admin\AppData\Local\Temp\Radmin21.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1948 | "C:\Users\admin\AppData\Local\Temp\Radmin21.exe" | C:\Users\admin\AppData\Local\Temp\Radmin21.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2896 | "C:\Windows\System32\r_server.exe" /start | C:\Windows\System32\r_server.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2968 | "C:\Windows\System32\r_server.exe" /stop | C:\Windows\System32\r_server.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3128 | "C:\Windows\System32\r_server.exe" /start | C:\Windows\System32\r_server.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3148 | "C:\Program Files\Radmin\radmin.exe" | C:\Program Files\Radmin\radmin.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3324 | "C:\Windows\System32\r_server.exe" /setup | C:\Windows\System32\r_server.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3364 | C:\Windows\system32\r_server.exe /intsetup | C:\Windows\system32\r_server.exe | — | Radmin21.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
185
Read events
182
Write events
3
Delete events
0
Modification events
| (PID) Process: | (676) Radmin21.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Remote Administrator v2.1 |
| Operation: | write | Name: | DisplayName |
Value: Remote Administrator v2.1 | |||
| (PID) Process: | (676) Radmin21.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Remote Administrator v2.1 |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files\Radmin\uninstal.exe | |||
| (PID) Process: | (3148) radmin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE |
| Operation: | write | Name: | Init |
Value: 3081636A911CD601 | |||
Executable files
9
Suspicious files
0
Text files
7
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 676 | Radmin21.exe | C:\ginstall.dll | executable | |
MD5:38A9142BA7B74DB9A68B3691C970BD89 | SHA256:ED866C7802EDC00235BD25AA2AE2EC6658EB8CB74301B930A96AB9AB42ED93A2 | |||
| 676 | Radmin21.exe | C:\Program Files\Radmin\WhatsNew.txt | text | |
MD5:CCE28D62D669FA30059E3DC9BAAB00A4 | SHA256:9D35E70DE10753E938BE431B6467D96CD0A23779D17D132A93160C230DE4508A | |||
| 676 | Radmin21.exe | C:\Program Files\Radmin\r_server.exe | executable | |
MD5:6A413E4D338FB13E58916E3B8051DBBD | SHA256:B8DEF2D716CCDF506CFE3A2C8C7FA5743AD3032BC8F3A3A212143096C0F54A9B | |||
| 676 | Radmin21.exe | C:\temp\license.txt | text | |
MD5:7019746D6D89EFFEB872BD2CB5C44B7E | SHA256:6FE7B8B79695F749376812DDDBBE0A079445D14295DB285583A0EBF3E394457D | |||
| 676 | Radmin21.exe | C:\temp\0readme.txt | text | |
MD5:87ED9E4141F028CD468DCA088F7CF1F0 | SHA256:8D4C3C66F55E4A8AFFDED9BDFD443C0170584E7371A3E373B39204EFA5F45257 | |||
| 676 | Radmin21.exe | C:\Program Files\Radmin\help.cnt | text | |
MD5:82806DFB63E7DA606E140ED4C57DF04F | SHA256:64EA140CBC44E9BCA334CAD892F0691BAF6ACB7F08D511A6A24BCFF336D670BC | |||
| 676 | Radmin21.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Remote Administrator v2.1\Help (English).lnk | lnk | |
MD5:— | SHA256:— | |||
| 676 | Radmin21.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Remote Administrator v2.1\Remote Administrator viewer.lnk | lnk | |
MD5:— | SHA256:— | |||
| 676 | Radmin21.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Remote Administrator v2.1\Settings for Remote Administrator server.lnk | lnk | |
MD5:— | SHA256:— | |||
| 676 | Radmin21.exe | C:\Program Files\Radmin\radmin.exe | executable | |
MD5:A4FD3C0387F587DA36A6838117C7C6B5 | SHA256:4BE8A275655DE01600BE147B9E69DB6DB8F71ACC9BDCBF996611F6FCA6E83FCD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report