| File name: | KMSPico.exe |
| Full analysis: | https://app.any.run/tasks/5ba96b77-c274-404d-b0a2-ca8aaa771499 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2024, 14:44:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | B1881F6380807EA9BAC4C3F5BC68428F |
| SHA1: | 07C5AE44CE8D03215752DA0D177BE1CEE5B26993 |
| SHA256: | 2E1AC85DD7F9BBA349476B999A3D0DBFE8C79C70CBC3DA470ABF75211D801706 |
| SSDEEP: | 98304:mrq3BdwbGHXyd5ejSpdrCIYG5ts4tGUWBTBWzjwJd7gDm9ejykll/9O9UJ+2QtF/:UHXArpgWq47SpFEcM5 |
MALICIOUS
Executing a file with an untrusted certificate
- KMSpico_setup.exe (PID: 2728)
- WindowsDefender.exe (PID: 5604)
- AutoPico.exe (PID: 4036)
- KMSELDI.exe (PID: 2408)
- KMSpico_setup.exe (PID: 4264)
- WindowsDefender.exe (PID: 2380)
Adds extension to the Windows Defender exclusion list
- WindowsDefender.exe (PID: 5604)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 5712)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1400)
SUSPICIOUS
Executable content was dropped or overwritten
- KMSPico.exe (PID: 4708)
- KMSPico.exe (PID: 3836)
- KMSpico_setup.exe (PID: 4264)
- KMSpico_setup.tmp (PID: 5888)
- KMSpico_setup.exe (PID: 2728)
- WindowsDefender.exe (PID: 5604)
- KMSELDI.exe (PID: 2408)
- KMSPico.tmp (PID: 3508)
Reads security settings of Internet Explorer
- KMSPico.tmp (PID: 5208)
- KMSpico_setup.tmp (PID: 1704)
Reads the Windows owner or organization settings
- KMSPico.tmp (PID: 3508)
- KMSpico_setup.tmp (PID: 5888)
Starts POWERSHELL.EXE for commands execution
- WindowsDefender.exe (PID: 2380)
- WindowsDefender.exe (PID: 5604)
Starts process via Powershell
- powershell.exe (PID: 2356)
Process drops legitimate windows executable
- KMSpico_setup.tmp (PID: 5888)
Script adds exclusion path to Windows Defender
- WindowsDefender.exe (PID: 5604)
Script adds exclusion extension to Windows Defender
- WindowsDefender.exe (PID: 5604)
Starts CMD.EXE for commands execution
- WindowsDefender.exe (PID: 5604)
- KMSpico_setup.tmp (PID: 5888)
Starts SC.EXE for service management
- WindowsDefender.exe (PID: 5604)
- cmd.exe (PID: 3688)
Invokes assembly entry point (POWERSHELL)
- powershell.exe (PID: 5576)
Uses powercfg.exe to modify the power settings
- WindowsDefender.exe (PID: 5604)
The process executes via Task Scheduler
- powershell.exe (PID: 5576)
Found strings related to reading or modifying Windows Defender settings
- WindowsDefender.exe (PID: 5604)
Executing commands from ".cmd" file
- KMSpico_setup.tmp (PID: 5888)
Manipulates environment variables
- powershell.exe (PID: 4624)
Process uninstalls Windows update
- wusa.exe (PID: 932)
Possibly patching Antimalware Scan Interface function (YARA)
- KMSELDI.exe (PID: 2408)
INFO
Create files in a temporary directory
- KMSPico.exe (PID: 4708)
- KMSPico.exe (PID: 3836)
- KMSPico.tmp (PID: 3508)
- KMSpico_setup.exe (PID: 4264)
- KMSpico_setup.tmp (PID: 5888)
- KMSpico_setup.exe (PID: 2728)
Checks supported languages
- KMSPico.exe (PID: 4708)
- KMSPico.tmp (PID: 5208)
- KMSPico.exe (PID: 3836)
- KMSpico_setup.exe (PID: 4264)
- WindowsDefender.exe (PID: 2380)
- KMSpico_setup.tmp (PID: 1704)
- KMSpico_setup.exe (PID: 2728)
- KMSpico_setup.tmp (PID: 5888)
- KMSPico.tmp (PID: 3508)
Process checks computer location settings
- KMSPico.tmp (PID: 5208)
- KMSpico_setup.tmp (PID: 1704)
Reads the computer name
- KMSPico.tmp (PID: 5208)
- KMSPico.exe (PID: 3836)
- KMSPico.tmp (PID: 3508)
- KMSpico_setup.tmp (PID: 1704)
- KMSpico_setup.tmp (PID: 5888)
The process uses the downloaded file
- powershell.exe (PID: 2356)
Creates files in the program directory
- KMSPico.tmp (PID: 3508)
Creates a software uninstall entry
- KMSPico.tmp (PID: 3508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:12 07:26:53+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 685056 |
| InitializedDataSize: | 159744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa83bc |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
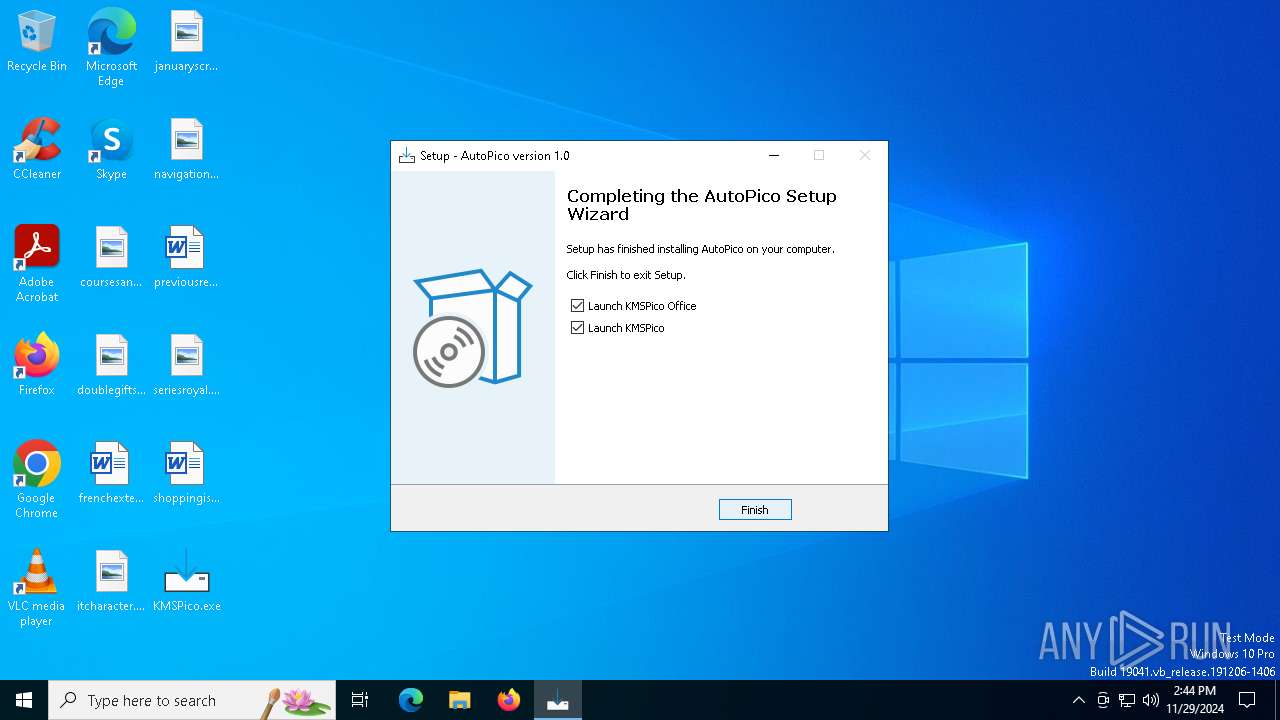
| CompanyName: | AutoPico |
| FileDescription: | AutoPico Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | AutoPico |
| ProductVersion: | 1.0 |
Total processes
183
Monitored processes
56
Malicious processes
9
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | C:\WINDOWS\system32\sc.exe stop bits | C:\Windows\System32\sc.exe | — | WindowsDefender.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 932 | wusa /uninstall /kb:890830 /quiet /norestart | C:\Windows\System32\wusa.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Update Standalone Installer Exit code: 87 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | C:\WINDOWS\system32\powercfg.exe /x -standby-timeout-ac 0 | C:\Windows\System32\powercfg.exe | — | WindowsDefender.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1400 | "C:\WINDOWS\system32\cmd.exe" /C ""C:\Program Files\KMSpico\scripts\Install_Task.cmd"" | C:\Windows\System32\cmd.exe | — | KMSpico_setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1416 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1512 | C:\WINDOWS\system32\sc.exe stop wuauserv | C:\Windows\System32\sc.exe | — | WindowsDefender.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1704 | "C:\Users\admin\AppData\Local\Temp\is-OIA0V.tmp\KMSpico_setup.tmp" /SL5="$302F2,2952592,69120,C:\Program Files (x86)\AutoPico\KMSpico_setup.exe" | C:\Users\admin\AppData\Local\Temp\is-OIA0V.tmp\KMSpico_setup.tmp | — | KMSpico_setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
15 118
Read events
15 095
Write events
23
Delete events
0
Modification events
| (PID) Process: | (3508) KMSPico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AutoPico_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.3.3 | |||
| (PID) Process: | (3508) KMSPico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AutoPico_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\AutoPico | |||
| (PID) Process: | (3508) KMSPico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AutoPico_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\AutoPico\ | |||
| (PID) Process: | (3508) KMSPico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AutoPico_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (3508) KMSPico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AutoPico_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (3508) KMSPico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AutoPico_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: default | |||
| (PID) Process: | (3508) KMSPico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AutoPico_is1 |
| Operation: | write | Name: | DisplayName |
Value: AutoPico version 1.0 | |||
| (PID) Process: | (3508) KMSPico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AutoPico_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\AutoPico\unins000.exe" | |||
| (PID) Process: | (3508) KMSPico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AutoPico_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files (x86)\AutoPico\unins000.exe" /SILENT | |||
| (PID) Process: | (3508) KMSPico.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AutoPico_is1 |
| Operation: | write | Name: | DisplayVersion |
Value: 1.0 | |||
Executable files
36
Suspicious files
38
Text files
722
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4708 | KMSPico.exe | C:\Users\admin\AppData\Local\Temp\is-B90FK.tmp\KMSPico.tmp | executable | |
MD5:9828D19B5CDA0970BFC09BC1CBE2D7F3 | SHA256:F1FAE0E179140969825A78B79E0E22F2B70BE3A83F22F4E20FD10951FB54398B | |||
| 3836 | KMSPico.exe | C:\Users\admin\AppData\Local\Temp\is-GNFU0.tmp\KMSPico.tmp | executable | |
MD5:9828D19B5CDA0970BFC09BC1CBE2D7F3 | SHA256:F1FAE0E179140969825A78B79E0E22F2B70BE3A83F22F4E20FD10951FB54398B | |||
| 4624 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kntspw5r.ypm.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3508 | KMSPico.tmp | C:\Program Files (x86)\AutoPico\WindowsDefender.exe | executable | |
MD5:DC7090E5881A1255E747AA562E6B6A16 | SHA256:E492C77D4584E952218E5183B68AACAB3CBC0D46AD5A08863DAA1ADA03AA5443 | |||
| 3508 | KMSPico.tmp | C:\Users\admin\AppData\Local\Temp\is-OCKEG.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 3508 | KMSPico.tmp | C:\Program Files (x86)\AutoPico\is-KRI4G.tmp | executable | |
MD5:8E34C5942B6D976A0B6ADE26C07D5FA3 | SHA256:C5AF0E9D4BD80FBA2CFB9B9E22CD055785F2561C3205E2206CE8D37F96923AAC | |||
| 3508 | KMSPico.tmp | C:\Program Files (x86)\AutoPico\KMSpico_setup.exe | executable | |
MD5:A02164371A50C5FF9FA2870EF6E8CFA3 | SHA256:64C731ADBE1B96CB5765203B1E215093DCF268D020B299445884A4AE62ED2D3A | |||
| 3508 | KMSPico.tmp | C:\Program Files (x86)\AutoPico\is-NJQAL.tmp | executable | |
MD5:A02164371A50C5FF9FA2870EF6E8CFA3 | SHA256:64C731ADBE1B96CB5765203B1E215093DCF268D020B299445884A4AE62ED2D3A | |||
| 3508 | KMSPico.tmp | C:\Program Files (x86)\AutoPico\is-RHE2P.tmp | executable | |
MD5:DC7090E5881A1255E747AA562E6B6A16 | SHA256:E492C77D4584E952218E5183B68AACAB3CBC0D46AD5A08863DAA1ADA03AA5443 | |||
| 2356 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_eeyam3gj.nsw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
732 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
732 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 104.126.37.171:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
732 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
732 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
732 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
0.pool.ntp.org |
| whitelisted |
www.bing.com |
| whitelisted |
3.pool.ntp.org |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |