| File name: | UntitledProject.bat |
| Full analysis: | https://app.any.run/tasks/7e073c64-65e3-4ba8-ab18-1b926176f976 |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2020, 06:01:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 82F6D81512C92F742E1B8830F29548B1 |
| SHA1: | D182C8567ECC1D267088A67114206F48AFD76592 |
| SHA256: | 2E130AB3FE55421BD31E2FC750D577737172E58FAA58D49AF3DA6C58ABBA95A5 |
| SSDEEP: | 3:mKDD4h4bjhaNZIoTjhUd2kn:hm4daoCdZkn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- cmd.exe (PID: 2616)
INFO
Changes internet zones settings
- iexplore.exe (PID: 616)
- iexplore.exe (PID: 3672)
- iexplore.exe (PID: 2372)
- iexplore.exe (PID: 3836)
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 3164)
- iexplore.exe (PID: 2164)
- iexplore.exe (PID: 2756)
Application launched itself
- iexplore.exe (PID: 616)
- iexplore.exe (PID: 2372)
- iexplore.exe (PID: 2164)
- iexplore.exe (PID: 3672)
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 3836)
- iexplore.exe (PID: 3164)
- iexplore.exe (PID: 2756)
Creates files in the user directory
- iexplore.exe (PID: 3604)
- iexplore.exe (PID: 936)
- iexplore.exe (PID: 3348)
- iexplore.exe (PID: 2708)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 3828)
- iexplore.exe (PID: 2752)
Reads settings of System Certificates
- iexplore.exe (PID: 936)
- iexplore.exe (PID: 3672)
- iexplore.exe (PID: 2000)
- iexplore.exe (PID: 3164)
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 3836)
- iexplore.exe (PID: 2756)
- iexplore.exe (PID: 2164)
- iexplore.exe (PID: 292)
Reads internet explorer settings
- iexplore.exe (PID: 936)
- iexplore.exe (PID: 3604)
- iexplore.exe (PID: 2708)
- iexplore.exe (PID: 1516)
- iexplore.exe (PID: 380)
- iexplore.exe (PID: 3052)
- iexplore.exe (PID: 2752)
- iexplore.exe (PID: 1888)
- iexplore.exe (PID: 672)
- iexplore.exe (PID: 4052)
- iexplore.exe (PID: 2000)
Changes settings of System certificates
- iexplore.exe (PID: 3672)
- iexplore.exe (PID: 3164)
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 2164)
- iexplore.exe (PID: 2756)
- iexplore.exe (PID: 3836)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3672)
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 3164)
- iexplore.exe (PID: 3836)
- iexplore.exe (PID: 2164)
- iexplore.exe (PID: 2756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
76
Monitored processes
42
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2756 CREDAT:988419 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 380 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:616 CREDAT:2757894 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
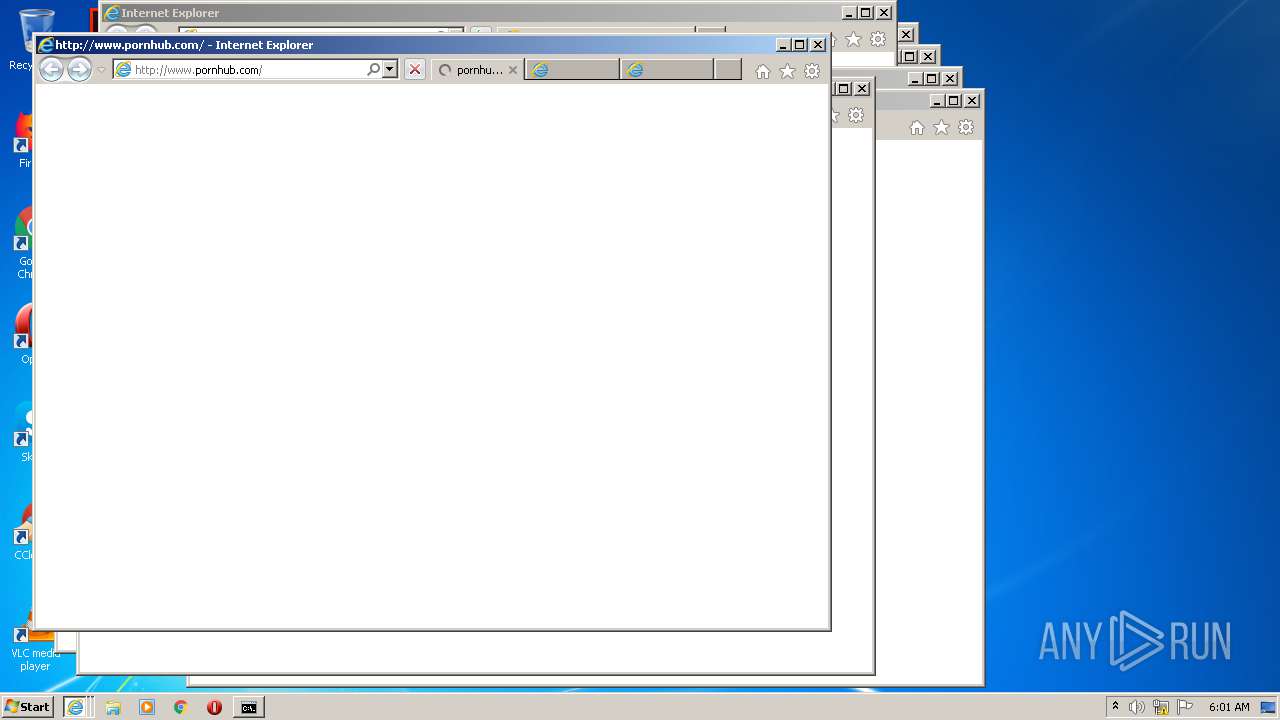
| 616 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.pornhub.com/ | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 672 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2692 CREDAT:3478790 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 936 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3836 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3164 CREDAT:3544327 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.xnxx.com/ | C:\Program Files\Internet Explorer\iexplore.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1516 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2692 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3672 CREDAT:3020038 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1724 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2692 CREDAT:3872006 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
4 620
Read events
3 684
Write events
930
Delete events
6
Modification events
| (PID) Process: | (2616) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {17FE9752-0B5A-4665-84CD-569794602F5C} {7F9185B0-CB92-43C5-80A9-92277A4F7B54} 0xFFFF |
Value: 0100000000000000A0374A4CDEC6D601 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1582432320 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30852830 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A6000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (616) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
34
Text files
117
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2372 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 616 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[2].ico | — | |
MD5:— | SHA256:— | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3672 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3836 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3164 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2756 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2164 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 936 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabD73F.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
136
DNS requests
31
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
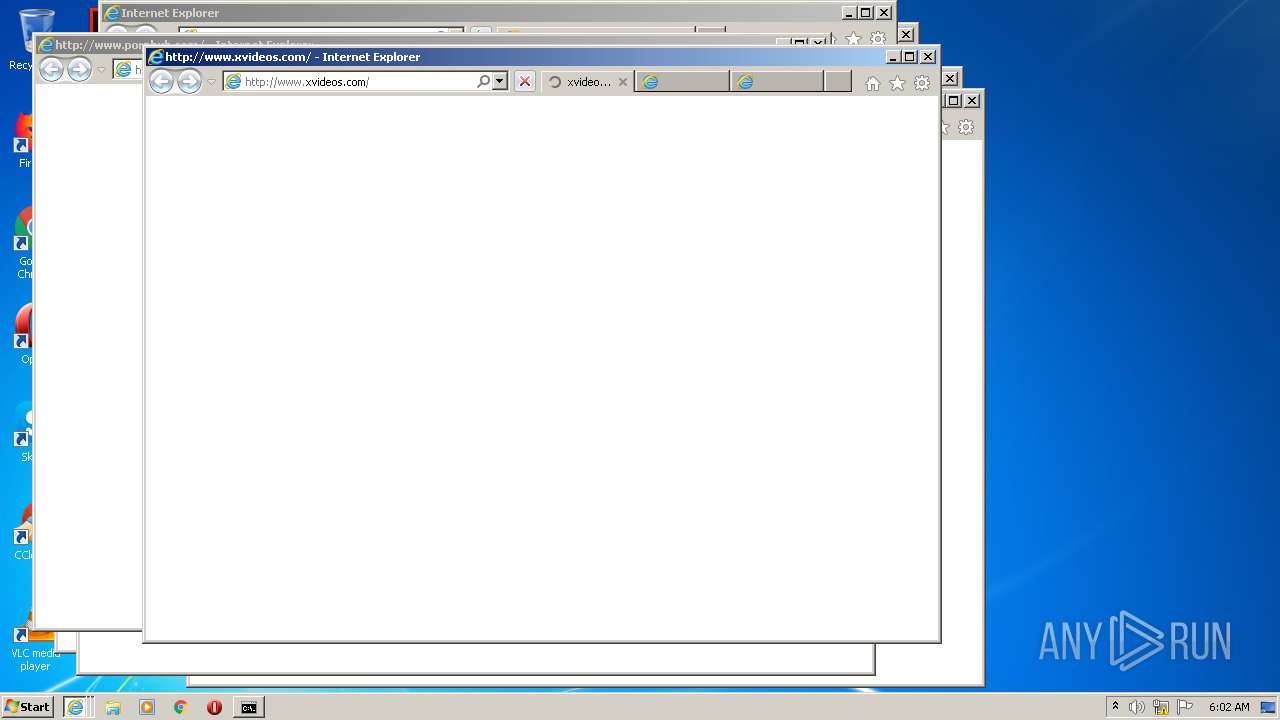
3348 | iexplore.exe | GET | 301 | 185.88.181.5:80 | http://www.xvideos.com/ | NL | — | — | whitelisted |
936 | iexplore.exe | GET | 301 | 185.88.181.5:80 | http://www.xvideos.com/ | NL | — | — | whitelisted |
3236 | iexplore.exe | GET | 301 | 185.88.181.60:80 | http://www.xnxx.com/ | NL | — | — | suspicious |
1516 | iexplore.exe | GET | 301 | 66.254.114.41:80 | http://www.pornhub.com/ | US | — | — | whitelisted |
3052 | iexplore.exe | GET | 301 | 185.88.181.5:80 | http://www.xvideos.com/ | NL | — | — | whitelisted |
380 | iexplore.exe | GET | 301 | 185.88.181.5:80 | http://www.xvideos.com/ | NL | — | — | whitelisted |
2752 | iexplore.exe | GET | 301 | 185.88.181.60:80 | http://www.xnxx.com/ | NL | — | — | suspicious |
3828 | iexplore.exe | GET | 301 | 185.88.181.60:80 | http://www.xnxx.com/ | NL | — | — | suspicious |
3348 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
3236 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3828 | iexplore.exe | 185.88.181.60:80 | www.xnxx.com | ServerStack, Inc. | NL | suspicious |
3604 | iexplore.exe | 66.254.114.41:80 | www.pornhub.com | Reflected Networks, Inc. | US | malicious |
3348 | iexplore.exe | 185.88.181.5:80 | www.xvideos.com | ServerStack, Inc. | NL | suspicious |
936 | iexplore.exe | 185.88.181.5:80 | www.xvideos.com | ServerStack, Inc. | NL | suspicious |
936 | iexplore.exe | 185.88.181.5:443 | www.xvideos.com | ServerStack, Inc. | NL | suspicious |
3236 | iexplore.exe | 185.88.181.60:80 | www.xnxx.com | ServerStack, Inc. | NL | suspicious |
1516 | iexplore.exe | 66.254.114.41:80 | www.pornhub.com | Reflected Networks, Inc. | US | malicious |
2372 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
616 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3348 | iexplore.exe | 66.254.114.41:443 | www.pornhub.com | Reflected Networks, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.pornhub.com |
| whitelisted |
www.xvideos.com |
| whitelisted |
www.xnxx.com |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
status.rapidssl.com |
| shared |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1516 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
3604 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
1056 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |