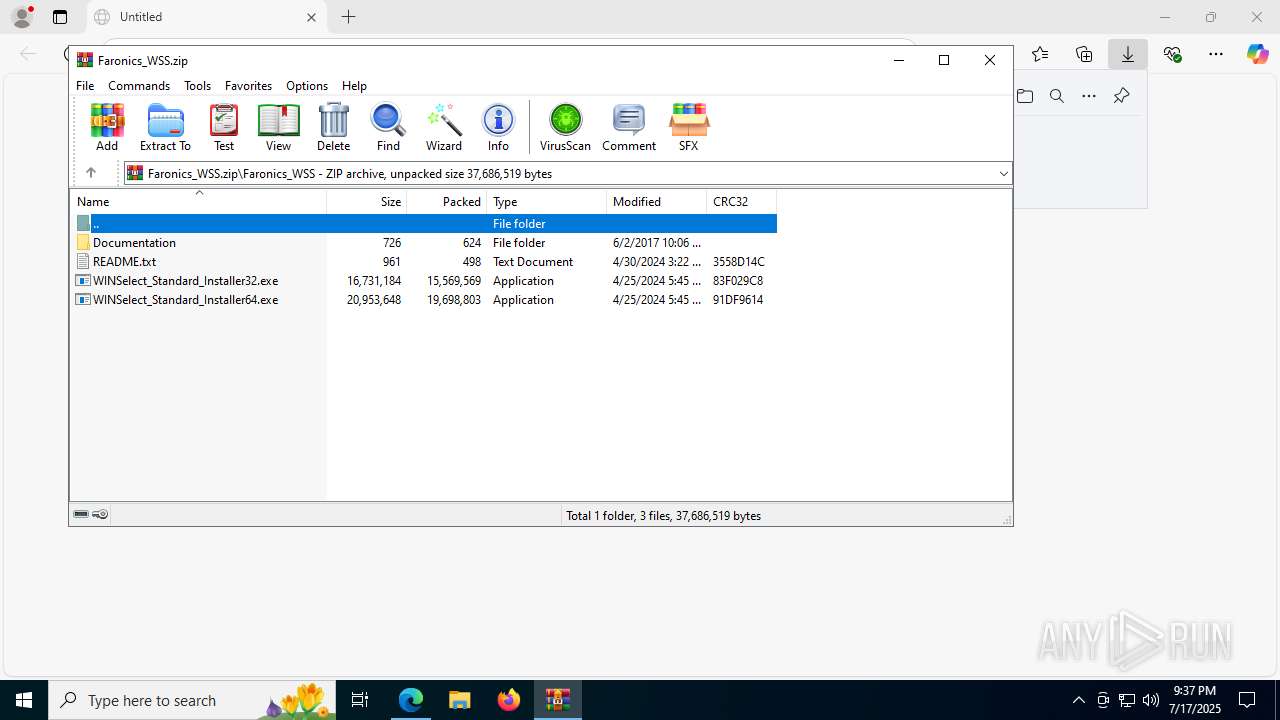
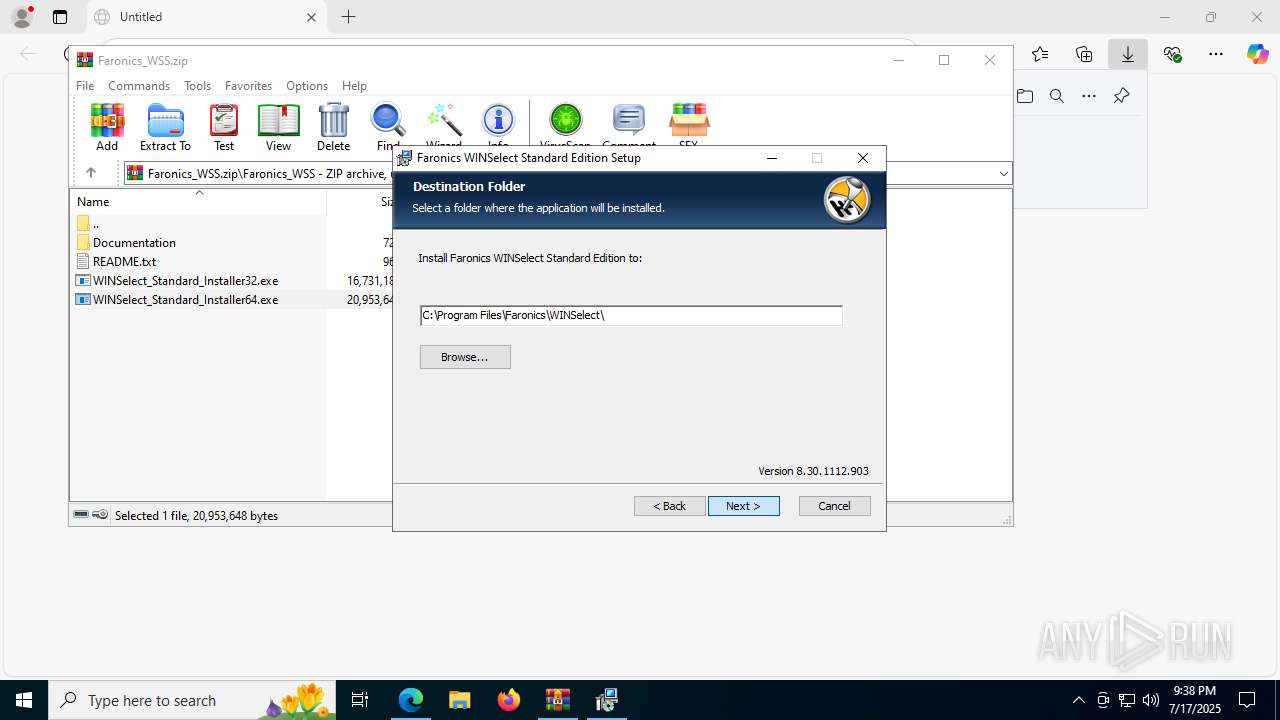
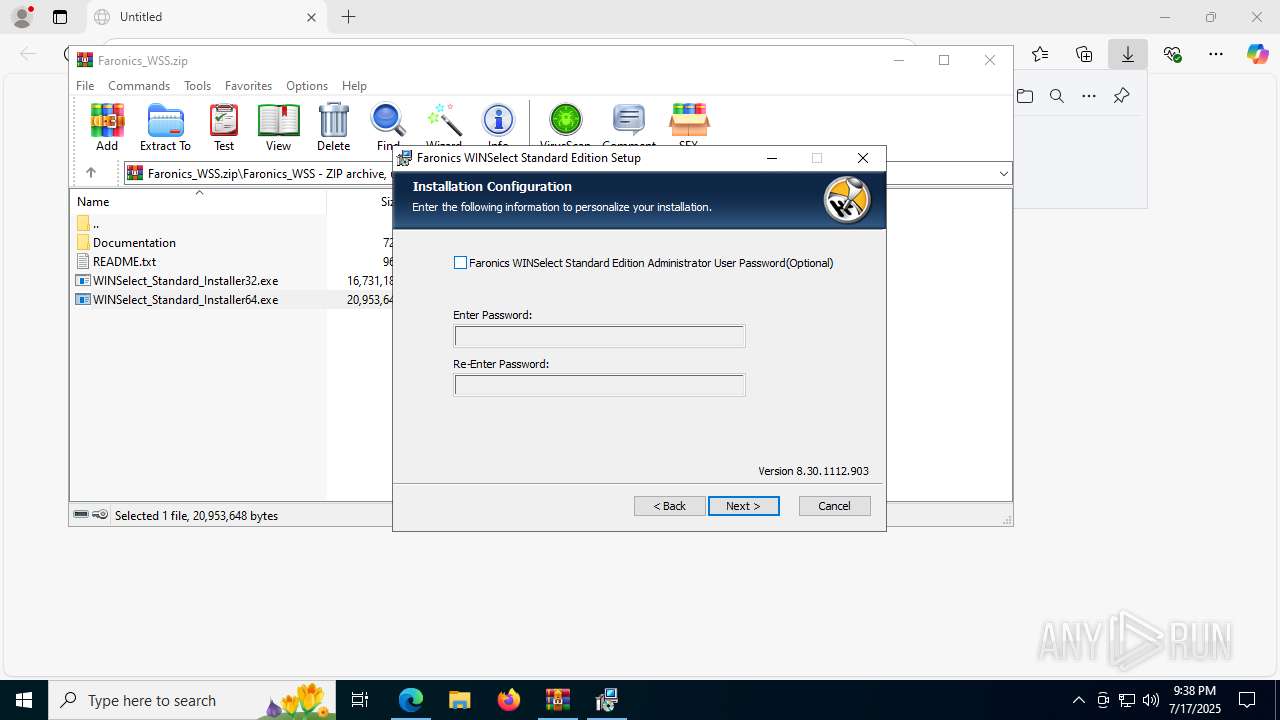
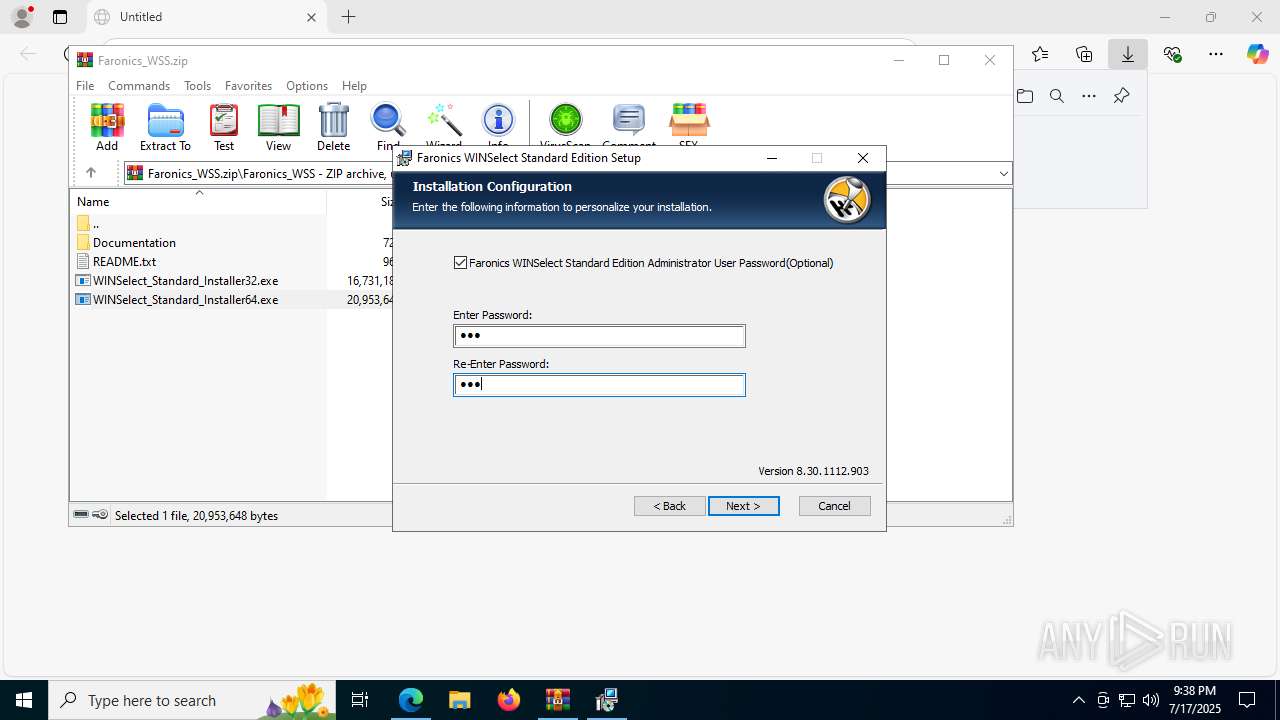
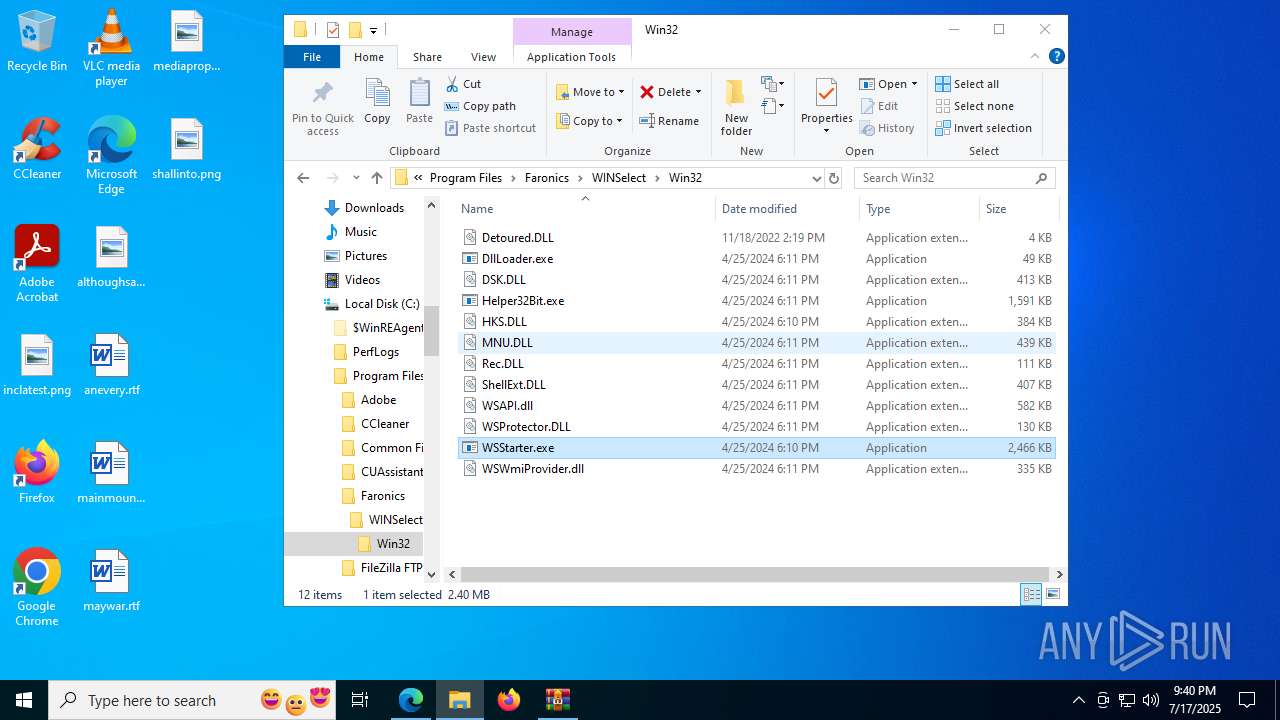
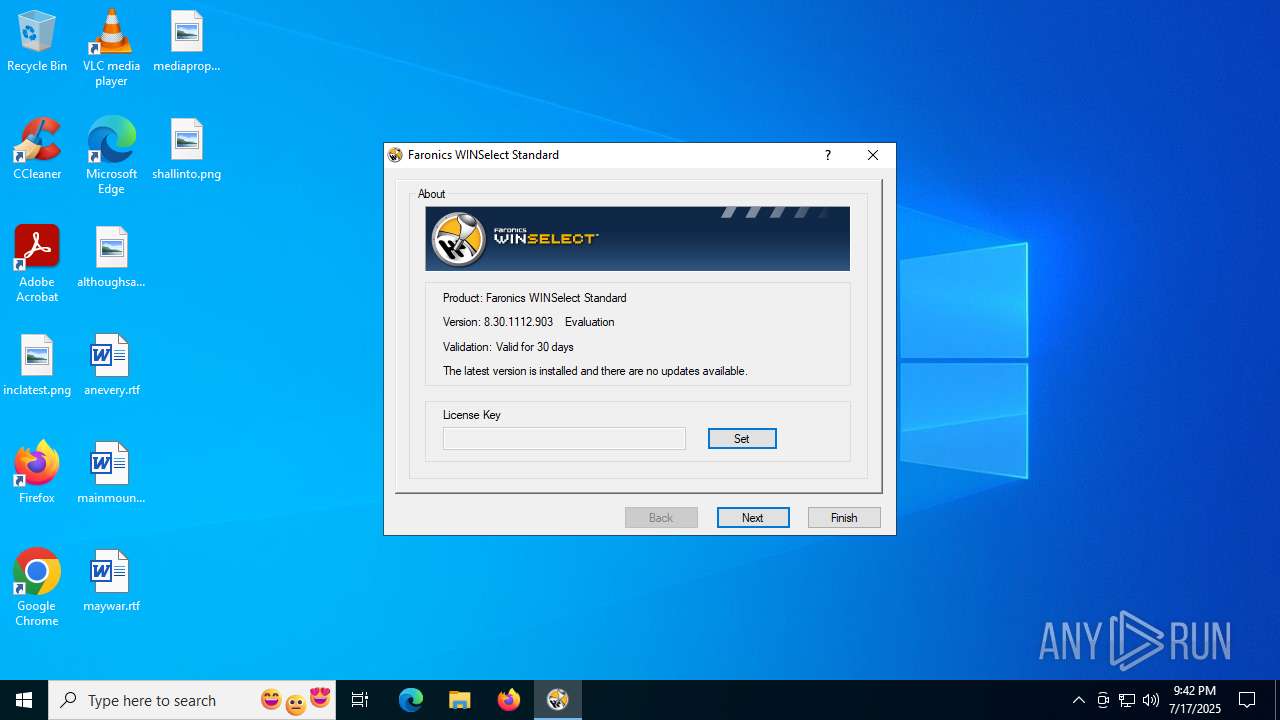
| URL: | https://downloads.faronics.com/Install/Faronics_WSS.zip |
| Full analysis: | https://app.any.run/tasks/1892a27e-935b-4ce2-a7bd-859d4bb51c47 |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2025, 21:37:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | EC99BD6144F77BC311A613DA60A1A378 |
| SHA1: | B3912D25064E840C8F5B7058E414FD94527F0EAD |
| SHA256: | 2DDF60EE093EE18A3246F0DA78E0AC69CF5CC6C6CD5718F0F3F7EBFC697EDF33 |
| SSDEEP: | 3:N8SE4LhoNLBLMa5n:2SCNLBLMO |
MALICIOUS
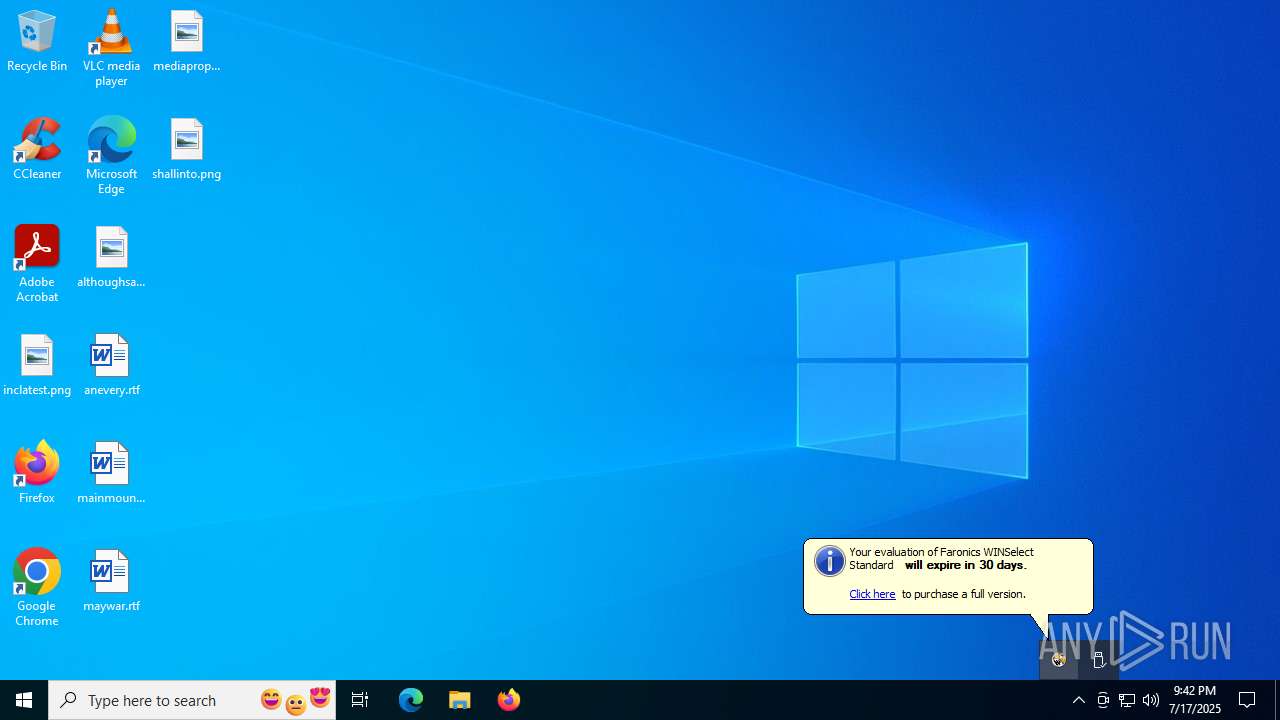
Changes the login/logoff helper path in the registry
- WSStarter.exe (PID: 8004)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7908)
- WINSelect_Standard_Installer64.exe (PID: 8064)
- WINSelect.exe (PID: 4456)
- WSStarter.exe (PID: 4624)
- WINSelect.exe (PID: 5048)
Reads the date of Windows installation
- WINSelect_Standard_Installer64.exe (PID: 8064)
- WINSelect.exe (PID: 4456)
- WINSelect.exe (PID: 5048)
- WSStarter.exe (PID: 4624)
Application launched itself
- msiexec.exe (PID: 5436)
- updater.exe (PID: 4200)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5436)
Process drops legitimate windows executable
- msiexec.exe (PID: 5436)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 7248)
- msiexec.exe (PID: 5436)
- msiexec.exe (PID: 7232)
- msiexec.exe (PID: 7580)
- msiexec.exe (PID: 4768)
Executes as Windows Service
- VSSVC.exe (PID: 4512)
There is functionality for taking screenshot (YARA)
- WINSelect.exe (PID: 4456)
- Helper32Bit.exe (PID: 1068)
- WSStarter.exe (PID: 7724)
The process executes via Task Scheduler
- updater.exe (PID: 4200)
- PLUGScheduler.exe (PID: 4252)
Changes the Home page of Internet Explorer
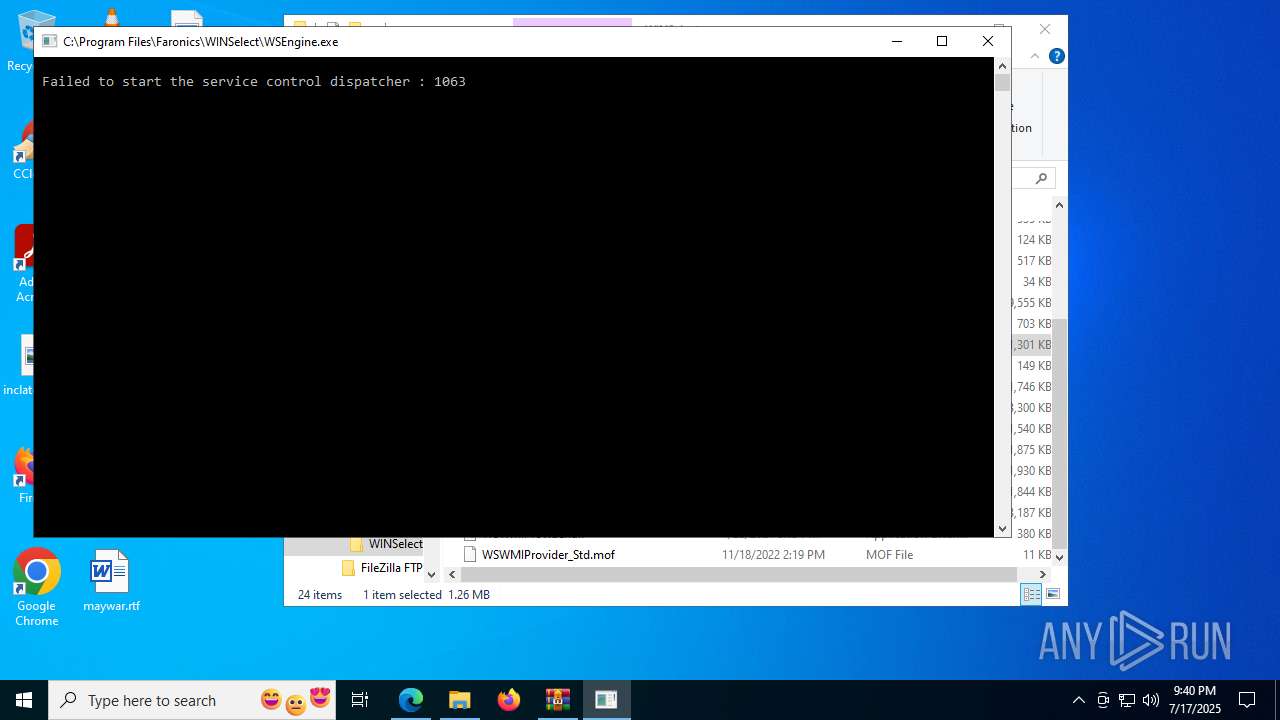
- WSEngine.exe (PID: 2024)
Changes the title of the Internet Explorer window
- WSEngine.exe (PID: 2024)
INFO
Checks supported languages
- identity_helper.exe (PID: 7580)
- WINSelect_Standard_Installer64.exe (PID: 8064)
- msiexec.exe (PID: 5436)
- msiexec.exe (PID: 7252)
- msiexec.exe (PID: 8000)
- msiexec.exe (PID: 5876)
- WSStarter.exe (PID: 4104)
- WSStarter.exe (PID: 8004)
- msiexec.exe (PID: 1752)
- WSEngine.exe (PID: 2976)
- WSEngine.exe (PID: 5252)
- Helper32Bit.exe (PID: 1068)
- WSStarter.exe (PID: 7724)
- WSEngine.exe (PID: 5900)
- WINSelect.exe (PID: 4456)
- WINSelect.exe (PID: 3108)
- WSStarter.exe (PID: 7028)
- WSEngine.exe (PID: 2024)
- DllLoader.exe (PID: 5244)
- updater.exe (PID: 4792)
- PLUGScheduler.exe (PID: 4252)
- updater.exe (PID: 4200)
- WSStarter.exe (PID: 4624)
- WINSelect.exe (PID: 5048)
- Helper32Bit.exe (PID: 4252)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6720)
Reads Environment values
- identity_helper.exe (PID: 7580)
- msiexec.exe (PID: 7252)
- msiexec.exe (PID: 8000)
Application launched itself
- msedge.exe (PID: 6720)
Reads the computer name
- identity_helper.exe (PID: 7580)
- WINSelect_Standard_Installer64.exe (PID: 8064)
- msiexec.exe (PID: 5436)
- msiexec.exe (PID: 7252)
- msiexec.exe (PID: 8000)
- msiexec.exe (PID: 5876)
- WSStarter.exe (PID: 8004)
- WSEngine.exe (PID: 5252)
- msiexec.exe (PID: 1752)
- WSEngine.exe (PID: 2976)
- WINSelect.exe (PID: 4456)
- WSEngine.exe (PID: 5900)
- WSStarter.exe (PID: 7724)
- WSEngine.exe (PID: 2024)
- WSStarter.exe (PID: 7028)
- updater.exe (PID: 4200)
- WSStarter.exe (PID: 4624)
- PLUGScheduler.exe (PID: 4252)
- WINSelect.exe (PID: 5048)
The sample compiled with english language support
- WinRAR.exe (PID: 7908)
- msiexec.exe (PID: 5436)
Create files in a temporary directory
- WINSelect_Standard_Installer64.exe (PID: 8064)
- mofcomp.exe (PID: 7740)
- mofcomp.exe (PID: 4224)
- mofcomp.exe (PID: 7380)
- mofcomp.exe (PID: 7564)
- mofcomp.exe (PID: 7948)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7908)
- msiexec.exe (PID: 5436)
- msiexec.exe (PID: 8168)
Process checks computer location settings
- WINSelect_Standard_Installer64.exe (PID: 8064)
- WINSelect.exe (PID: 4456)
- WSStarter.exe (PID: 4624)
- WINSelect.exe (PID: 5048)
Manages system restore points
- SrTasks.exe (PID: 7052)
Reads the machine GUID from the registry
- WSStarter.exe (PID: 8004)
- WSEngine.exe (PID: 2024)
- WINSelect.exe (PID: 4456)
- WSEngine.exe (PID: 5900)
- DllLoader.exe (PID: 5244)
- Helper32Bit.exe (PID: 4252)
- WINSelect.exe (PID: 5048)
- WSStarter.exe (PID: 4624)
Creates files in the program directory
- WSStarter.exe (PID: 8004)
- WSEngine.exe (PID: 2024)
- PLUGScheduler.exe (PID: 4252)
- WINSelect.exe (PID: 5048)
Creates a software uninstall entry
- msiexec.exe (PID: 5436)
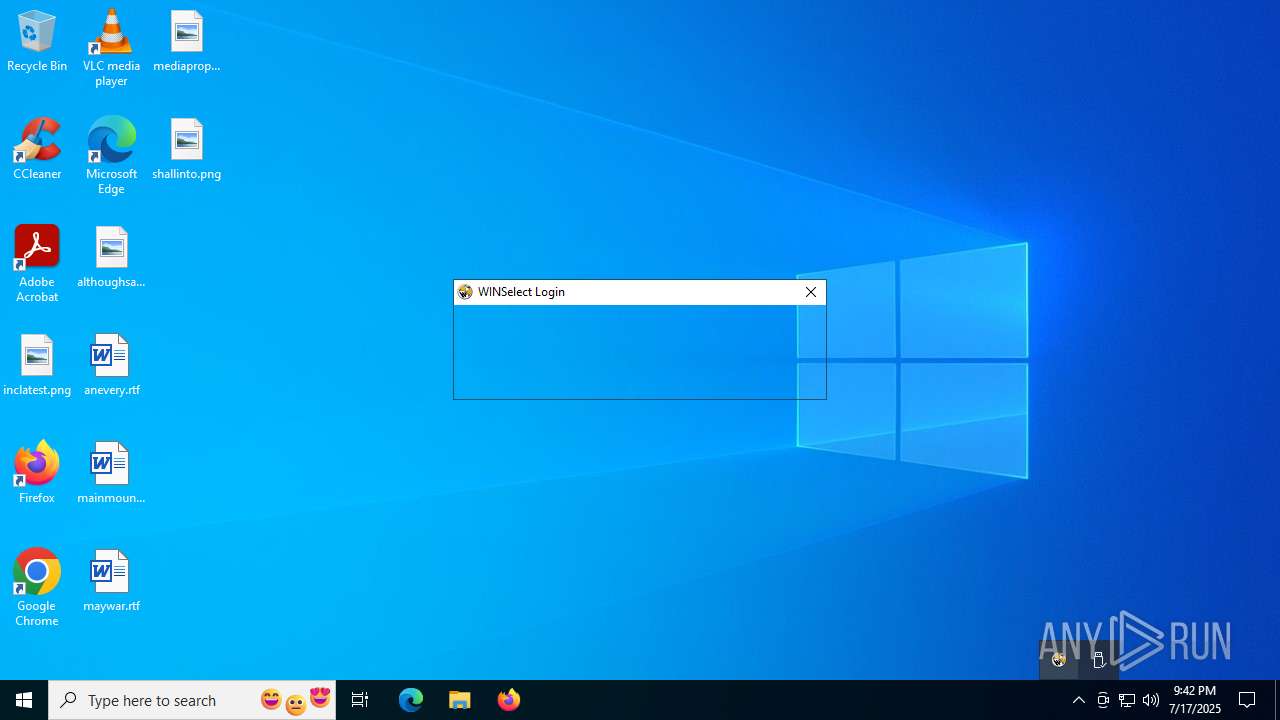
Manual execution by a user
- WINSelect.exe (PID: 7188)
- WSStarter.exe (PID: 7724)
- WSEngine.exe (PID: 5900)
- WINSelect.exe (PID: 4456)
- WINSelect.exe (PID: 3108)
- WSStarter.exe (PID: 7028)
- DllLoader.exe (PID: 5244)
- WINSelect.exe (PID: 4048)
Checks proxy server information
- slui.exe (PID: 7596)
- explorer.exe (PID: 5020)
Reads the software policy settings
- slui.exe (PID: 7596)
Creates files or folders in the user directory
- WSEngine.exe (PID: 5900)
- WINSelect.exe (PID: 5048)
- explorer.exe (PID: 5020)
Process checks whether UAC notifications are on
- updater.exe (PID: 4200)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5020)
Reads the time zone
- runonce.exe (PID: 7044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
366
Monitored processes
93
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 756 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5248,i,17056796630446363770,11864512953991081059,262144 --variations-seed-version --mojo-platform-channel-handle=5780 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1068 | "C:\Program Files\Faronics\WINSelect\win32\Helper32Bit.exe" | C:\Program Files\Faronics\WINSelect\Win32\Helper32Bit.exe | — | WINSelect.exe | |||||||||||
User: admin Company: Faronics Corporation Integrity Level: HIGH Description: Executable used by Faronics WINSelect Workstation Exit code: 0 Version: 8.30.1111.903 Modules
| |||||||||||||||
| 1752 | C:\Windows\System32\MsiExec.exe -Embedding 907222049C2A3B7E7BC0859B32AD25C8 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2024 | "C:\Program Files\Faronics\WINSelect\WSEngine.exe" | C:\Program Files\Faronics\WINSelect\WSEngine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Faronics Corporation Integrity Level: SYSTEM Description: Executable used by Faronics WINSelect Workstation Version: 8.30.1112.903 Modules
| |||||||||||||||
| 2312 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4304,i,17056796630446363770,11864512953991081059,262144 --variations-seed-version --mojo-platform-channel-handle=4324 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2256,i,17056796630446363770,11864512953991081059,262144 --variations-seed-version --mojo-platform-channel-handle=2556 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | WSEngine.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2596 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2692 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=5528,i,17056796630446363770,11864512953991081059,262144 --variations-seed-version --mojo-platform-channel-handle=6012 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2716 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc43c9f208,0x7ffc43c9f214,0x7ffc43c9f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
41 384
Read events
40 113
Write events
526
Delete events
745
Modification events
| (PID) Process: | (6720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6720) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: B77F1E1ABD982F00 | |||
| (PID) Process: | (6720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393976 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {359B0B47-E48E-4243-974E-E9DCAA2970FA} | |||
| (PID) Process: | (6720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (6720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393976 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A87C5AA8-E529-440C-8E6B-DE50F13DFD77} | |||
| (PID) Process: | (6720) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 726C381ABD982F00 | |||
| (PID) Process: | (6720) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
37
Suspicious files
125
Text files
88
Unknown types
90
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF18d2db.TMP | — | |
MD5:— | SHA256:— | |||
| 6720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF18d2eb.TMP | — | |
MD5:— | SHA256:— | |||
| 6720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF18d2eb.TMP | — | |
MD5:— | SHA256:— | |||
| 6720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF18d2eb.TMP | — | |
MD5:— | SHA256:— | |||
| 6720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF18d2fb.TMP | — | |
MD5:— | SHA256:— | |||
| 6720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6720 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF18d329.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
96
DNS requests
74
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2356 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:Ghu9K7KJh4-djQ2SxZ_G4Z9xoJLWHQjh9X5e6c6UYkE&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7116 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3572 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3572 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7416 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1752967575&P2=404&P3=2&P4=RN%2bJKTxIOY0gsrVUTporXtoV%2bsMBr63zqCWUuJ7a14Zeu91oYhdUJ4jJoL8JgIiqgDhDNrxF7%2bIPo0rYf1V%2fbg%3d%3d | unknown | — | — | whitelisted |
7416 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1752967575&P2=404&P3=2&P4=RN%2bJKTxIOY0gsrVUTporXtoV%2bsMBr63zqCWUuJ7a14Zeu91oYhdUJ4jJoL8JgIiqgDhDNrxF7%2bIPo0rYf1V%2fbg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3836 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2356 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2356 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2356 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2356 | msedge.exe | 2.16.241.220:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
2356 | msedge.exe | 18.66.192.88:443 | downloads.faronics.com | AMAZON-02 | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
downloads.faronics.com |
| malicious |
copilot.microsoft.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
www.bing.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
www.googleapis.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WSStarter.exe | $$$$$$$ Fast USer Switch |
WSStarter.exe | $$$$$$ Install Switch |
DllLoader.exe | WS_UNLOAD_DLL_FROM_FIREFOX_EVENT Event Created Sucessfully |
msedge.exe | @@@===>>>> Integrity check by path FAILED!!!! <<<<===@@@ |
msedge.exe | @@@===>>>> Integrity check by path FAILED!!!! <<<<===@@@ |
WinRAR.exe | @@@===>>>> Integrity check by path FAILED!!!! <<<<===@@@ |
WINSelect.exe | Error in CWSWmiWrapper::ExecuteMethod(GetConfig), Unable to execute method. Error Code : 80041002 |