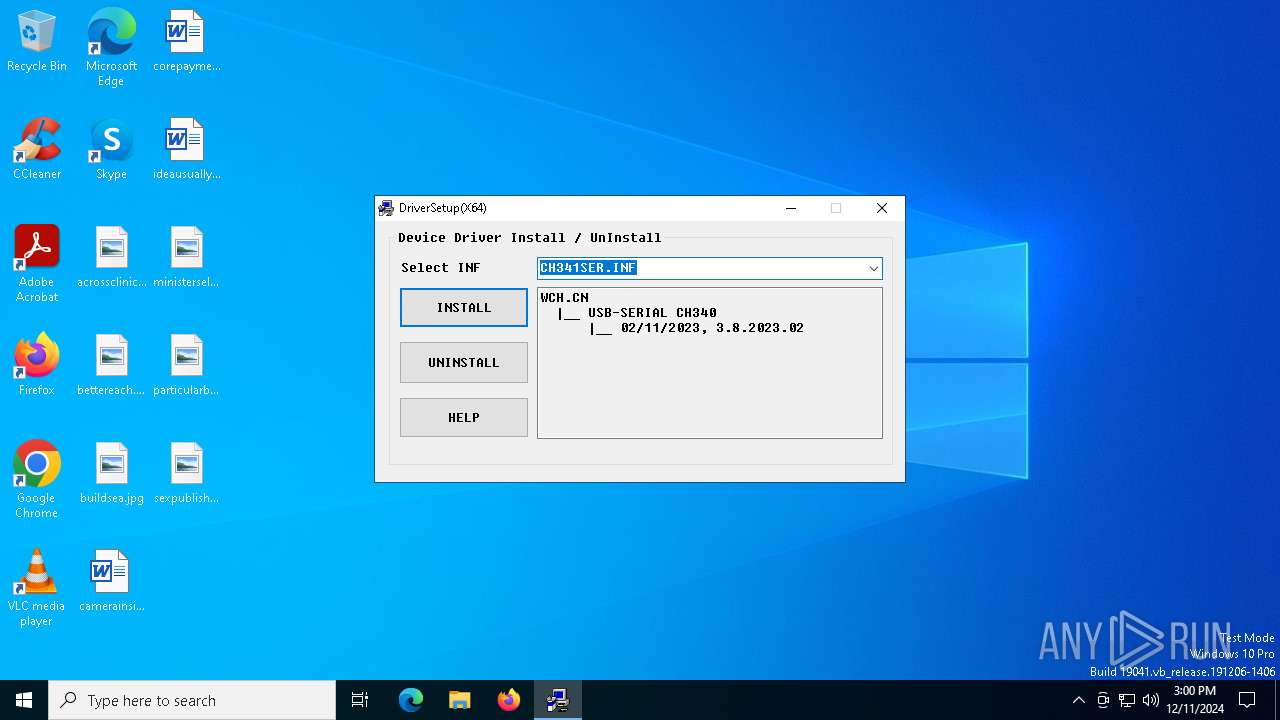
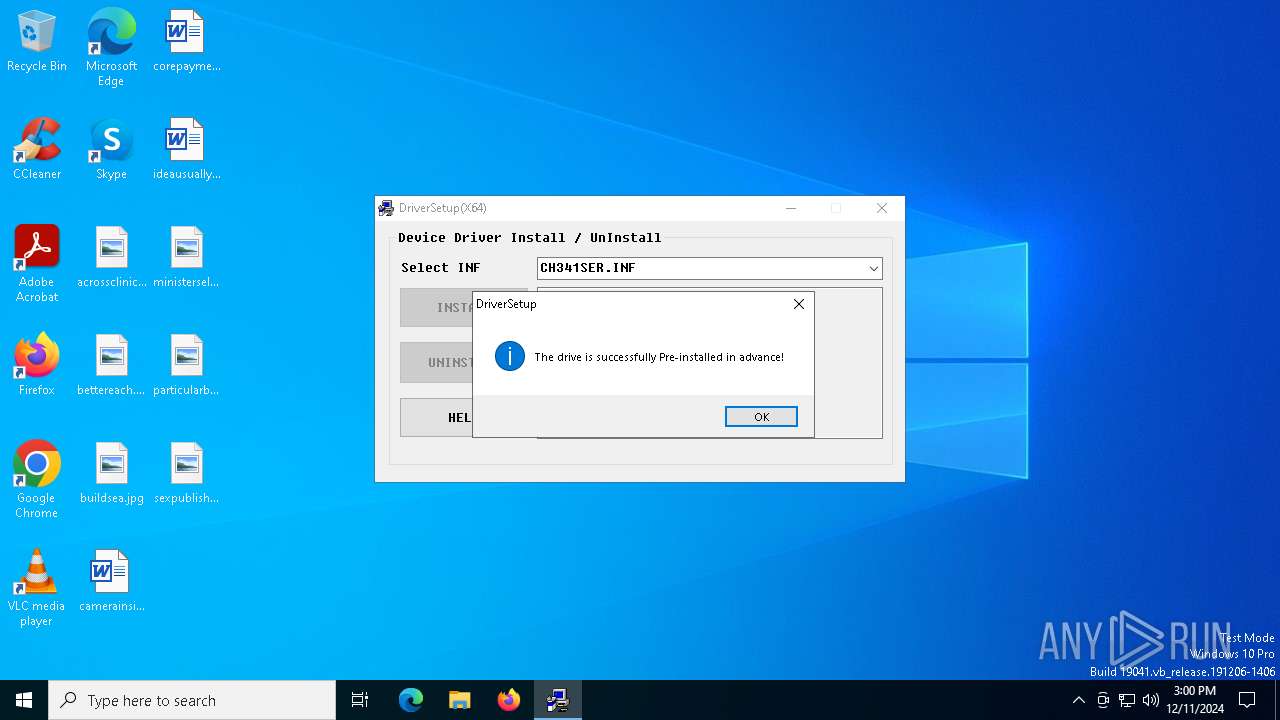
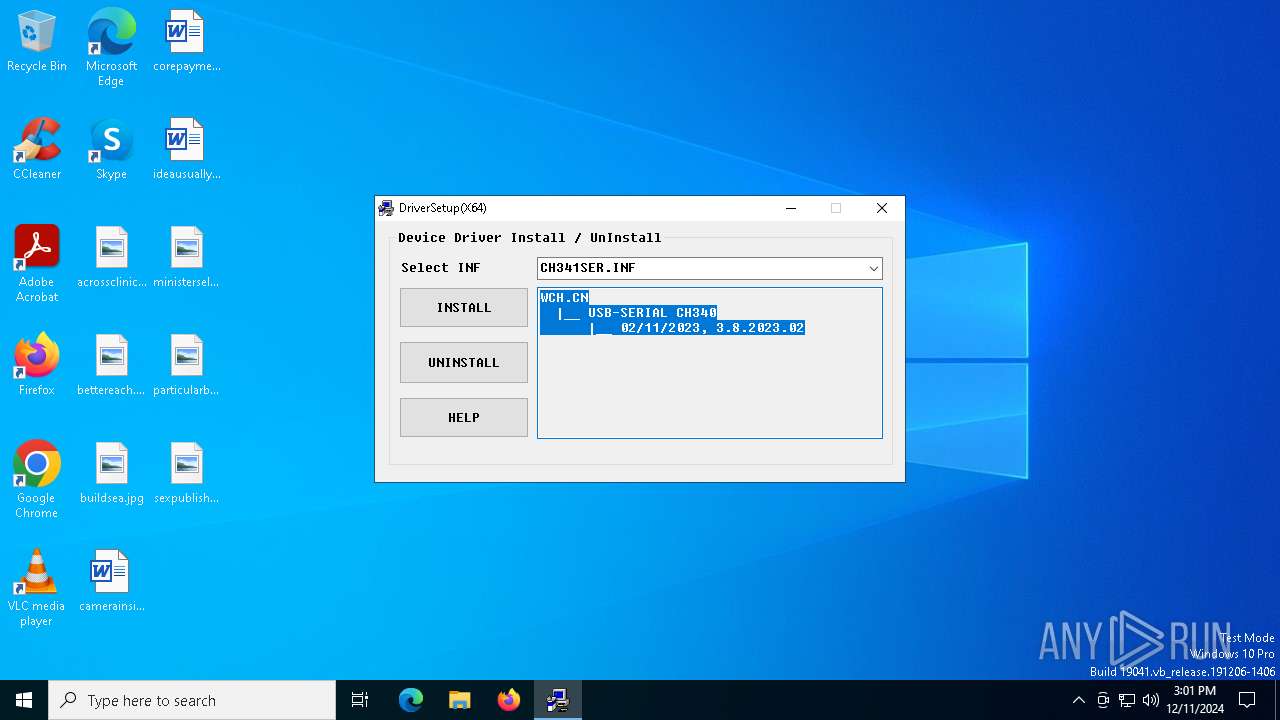
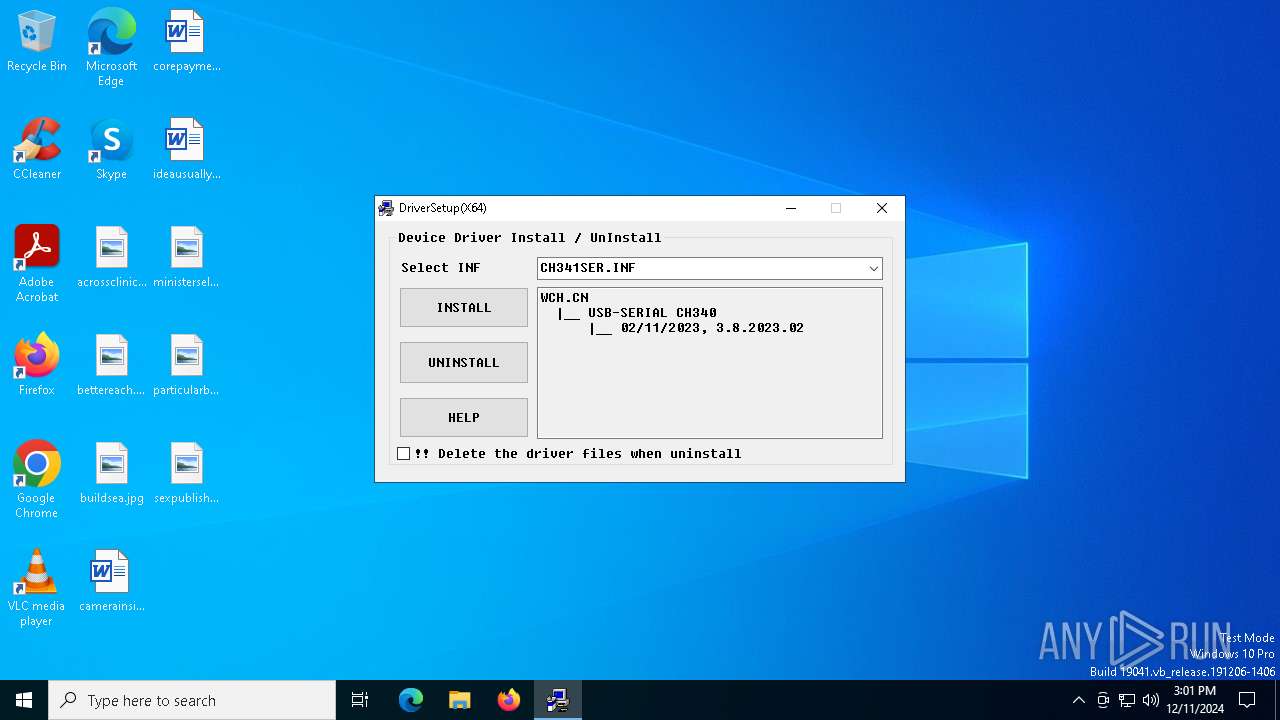
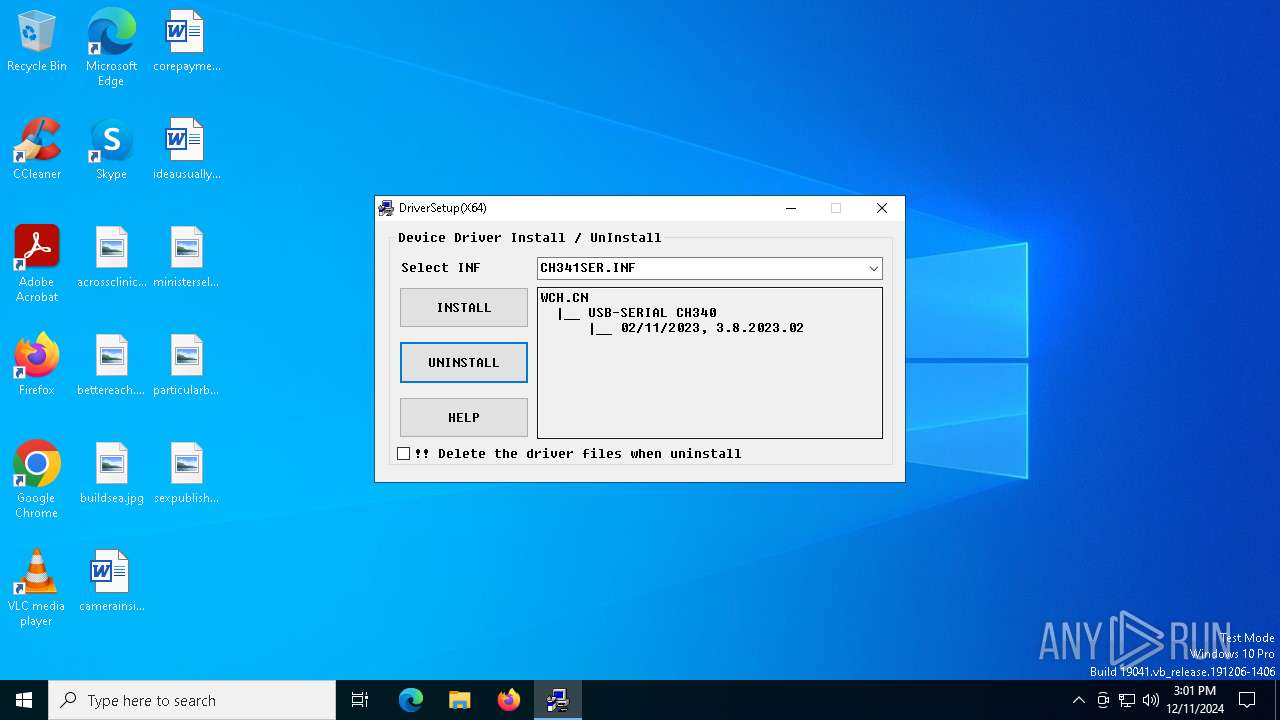
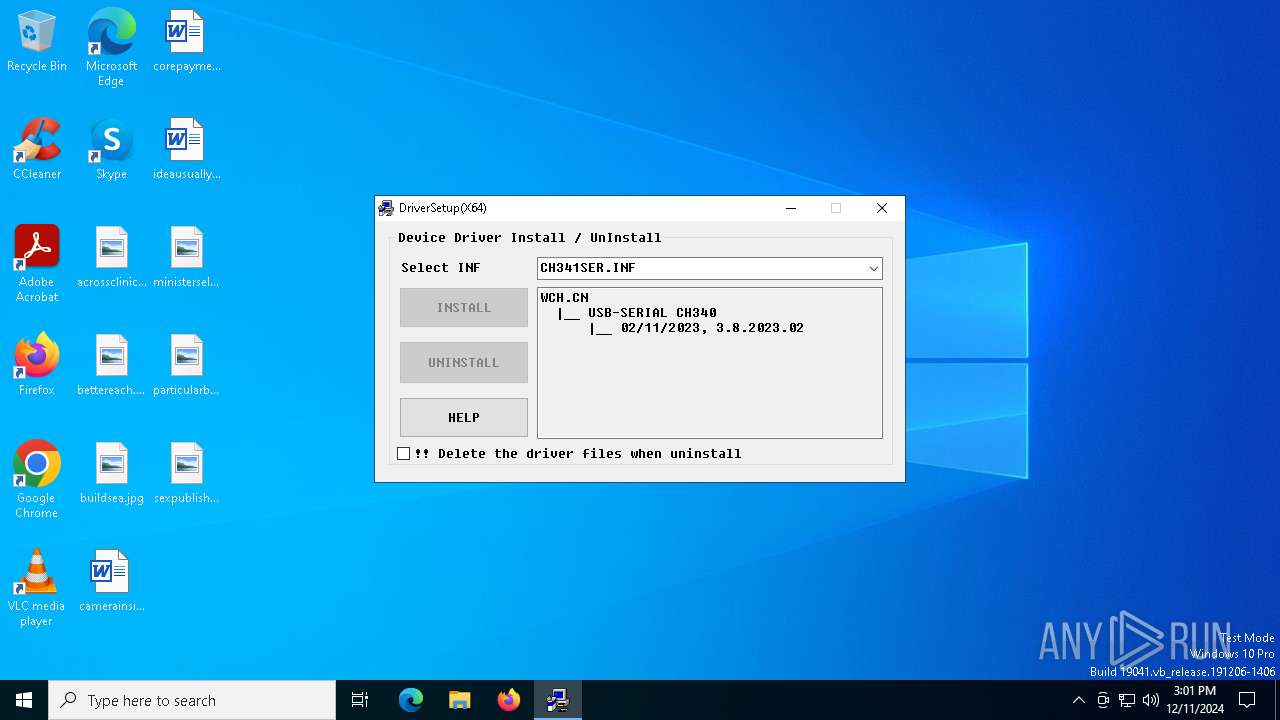
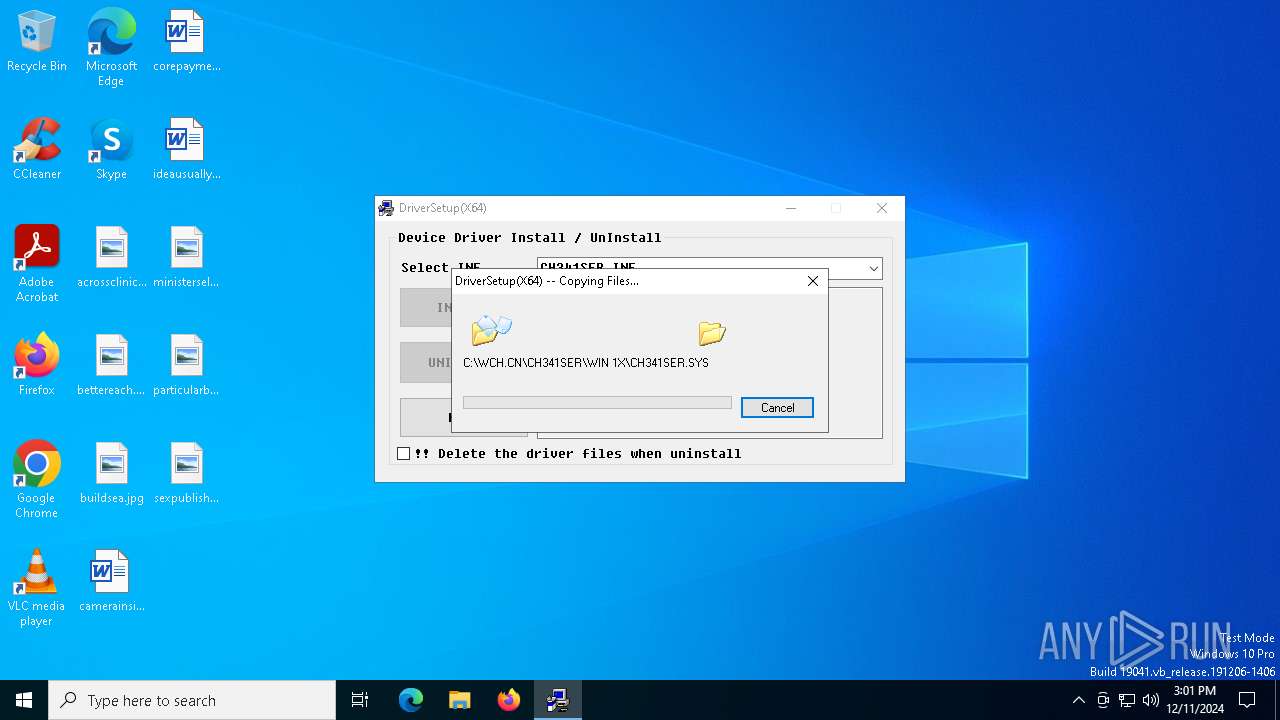
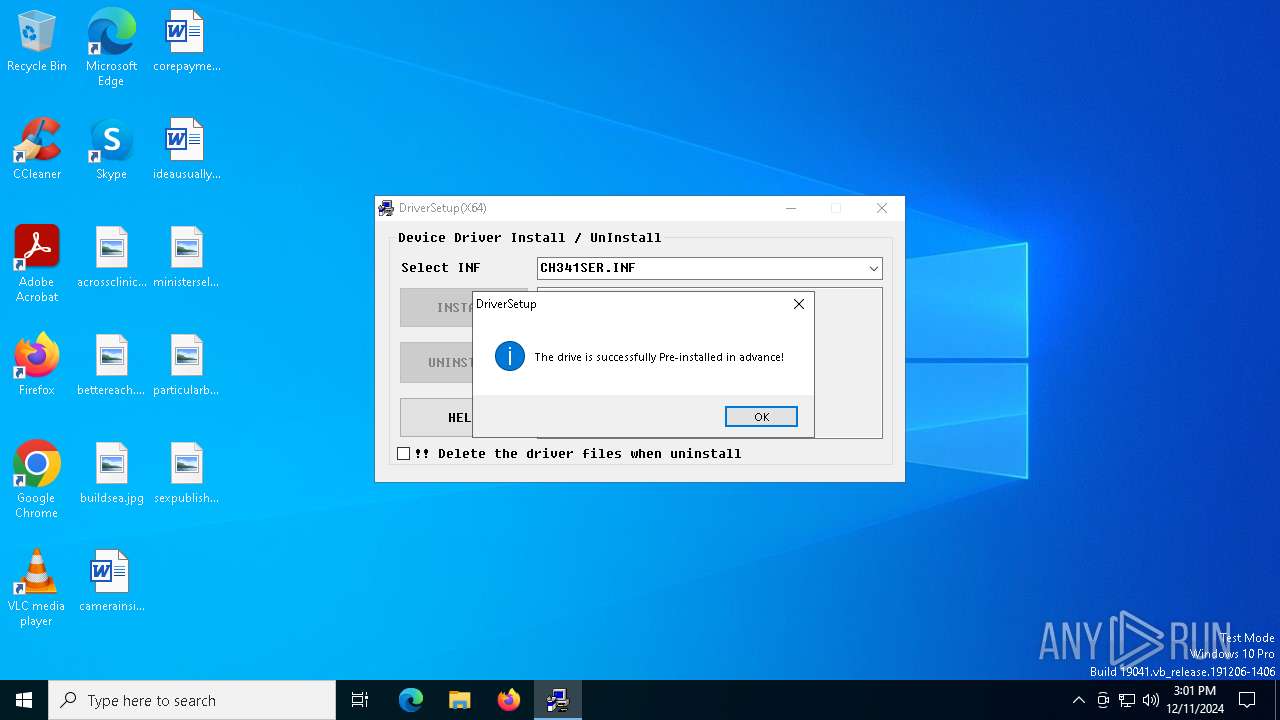
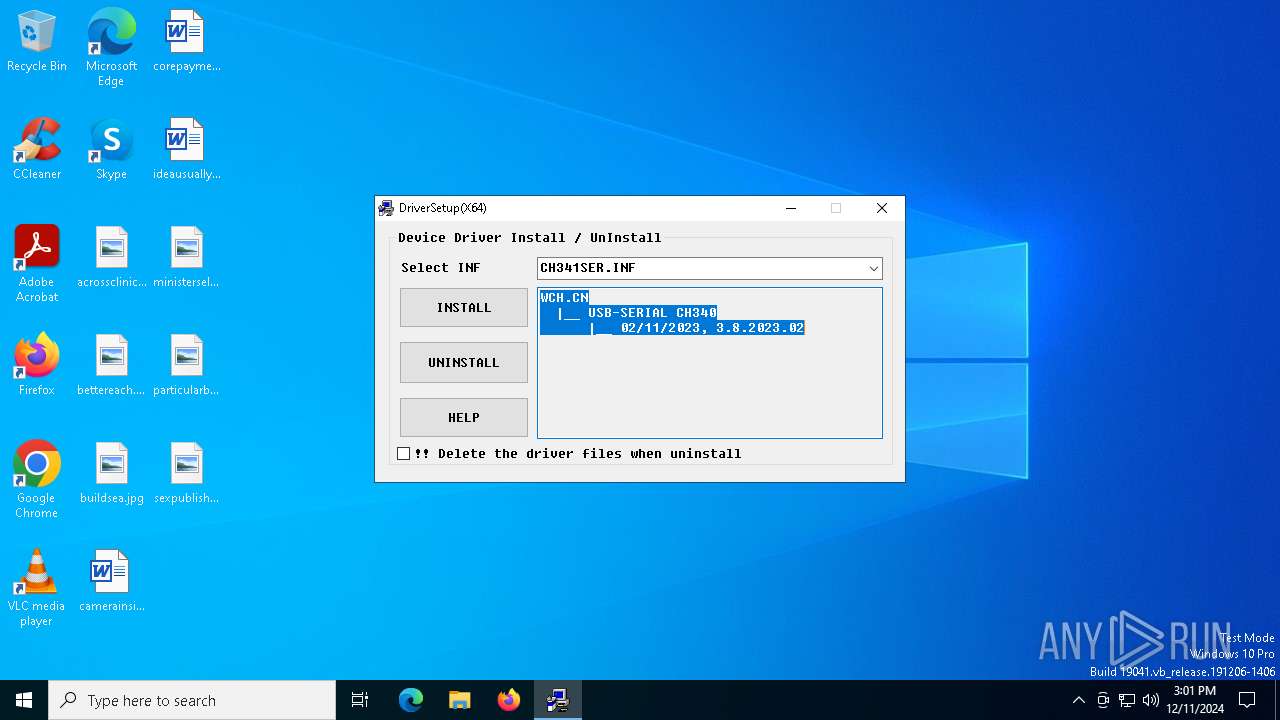
| File name: | CH341SER.EXE |
| Full analysis: | https://app.any.run/tasks/b07c6832-7e77-47ba-8b7f-b9631a1d0180 |
| Verdict: | Malicious activity |
| Analysis date: | December 11, 2024, 15:00:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | C4F8592C377D0BC18F1BC7E077D7B99C |
| SHA1: | 03022EA4317F15332A3220523B9A30F3ABF846D5 |
| SHA256: | 2D9826A2B5FFD6A00ABD9AD5FBD456798037AD5571BC4FE62F014B3FE8065C5A |
| SSDEEP: | 24576:AtfGrRCpfAbq8Id8uGXZfSHjry5UQMHbkjtGOjhs9xRq+bP6S+Pcp9ok0rSa0Det:AtfGrRCpfAbe0SHjry5UQMHbkjtGOjhN |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- CH341SER.EXE.exe (PID: 3608)
- drvinst.exe (PID: 1864)
- DRVSETUP64.exe (PID: 6596)
- ch341ser.exe.exe (PID: 6288)
Starts application with an unusual extension
- CH341SER.EXE.exe (PID: 3608)
Starts itself from another location
- CH341SER.EXE.exe (PID: 3608)
Drops a system driver (possible attempt to evade defenses)
- ch341ser.exe.exe (PID: 6288)
- drvinst.exe (PID: 1864)
- DRVSETUP64.exe (PID: 6596)
Reads security settings of Internet Explorer
- ch341ser.exe.exe (PID: 6288)
INFO
Reads the computer name
- CH341SER.EXE.exe (PID: 3608)
- ch341ser.exe.exe (PID: 6288)
- icsys.icn.exe (PID: 6328)
- DRVSETUP64.exe (PID: 6596)
Checks supported languages
- CH341SER.EXE.exe (PID: 3608)
- ch341ser.exe.exe (PID: 6288)
- icsys.icn.exe (PID: 6328)
- DRVSETUP64.exe (PID: 6596)
- SETUP.EXE (PID: 6572)
The sample compiled with english language support
- CH341SER.EXE.exe (PID: 3608)
- ch341ser.exe.exe (PID: 6288)
- DRVSETUP64.exe (PID: 6596)
- drvinst.exe (PID: 1864)
Create files in a temporary directory
- CH341SER.EXE.exe (PID: 3608)
- icsys.icn.exe (PID: 6328)
Reads the machine GUID from the registry
- drvinst.exe (PID: 1864)
Reads the software policy settings
- drvinst.exe (PID: 1864)
Process checks computer location settings
- ch341ser.exe.exe (PID: 6288)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (42.6) |
|---|---|---|
| .exe | | | InstallShield setup (22.3) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (16.2) |
| .exe | | | Win64 Executable (generic) (14.3) |
| .exe | | | Win32 Executable (generic) (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:06:14 19:01:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 176128 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3670 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft |
| ProductName: | Win |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | Win |
| OriginalFileName: | Win.exe |
Total processes
133
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1864 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{dcad6330-61bf-e44b-ad90-af51e486b90f}\CH341SER.INF" "9" "4c9e2e733" "00000000000001BC" "WinSta0\Default" "00000000000001D4" "208" "C:\WCH.CN\CH341SER\WIN 1X" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | "C:\Users\admin\AppData\Local\Temp\CH341SER.EXE.exe" | C:\Users\admin\AppData\Local\Temp\CH341SER.EXE.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 6288 | c:\users\admin\appdata\local\temp\ch341ser.exe.exe | C:\Users\admin\AppData\Local\Temp\ch341ser.exe.exe | CH341SER.EXE.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6328 | C:\Users\admin\AppData\Local\icsys.icn.exe | C:\Users\admin\AppData\Local\icsys.icn.exe | — | CH341SER.EXE.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 6432 | "C:\WCH.CN\CH341SER\SETUP.EXE" | C:\WCH.CN\CH341SER\SETUP.EXE | — | ch341ser.exe.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: EXE For Driver Installation Exit code: 3221226540 Version: 1, 7, 2, 0 Modules
| |||||||||||||||
| 6572 | "C:\WCH.CN\CH341SER\SETUP.EXE" | C:\WCH.CN\CH341SER\SETUP.EXE | ch341ser.exe.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: EXE For Driver Installation Exit code: 0 Version: 1, 7, 2, 0 Modules
| |||||||||||||||
| 6596 | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.EXE | C:\WCH.CN\CH341SER\DRVSETUP64\DRVSETUP64.exe | SETUP.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: EXE For Driver Installation Version: 1, 7, 2, 0 Modules
| |||||||||||||||
Total events
3 557
Read events
3 552
Write events
5
Delete events
0
Modification events
| (PID) Process: | (3608) CH341SER.EXE.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (6328) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (6288) ch341ser.exe.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR SFX |
| Operation: | write | Name: | C%%WCH.CN%CH341SER |
Value: C:\WCH.CN\CH341SER | |||
| (PID) Process: | (6596) DRVSETUP64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
Executable files
122
Suspicious files
12
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6288 | ch341ser.exe.exe | C:\WCH.CN\CH341SER\CH341PORTS.DLL | executable | |
MD5:5B0E40EED860575D1CAF90CCC580B31B | SHA256:CEA13F1AE4D26880A216F3A5606FA550E133B796C88C7CA24E61F74257D110C7 | |||
| 3608 | CH341SER.EXE.exe | C:\Users\admin\AppData\Local\Temp\ch341ser.exe.exe | executable | |
MD5:31D825E7D64FE4C4D8AD3DED5F62B6A4 | SHA256:74D12019023390D27739625773005ECCCF1BC6C4547E0C46088E86665E519524 | |||
| 3608 | CH341SER.EXE.exe | C:\Users\admin\AppData\Local\icsys.icn.exe | executable | |
MD5:EA0ADBD0E6C78168AD0B1CDAB58C745E | SHA256:2127D7DFE13B8E97C97EF209F7AE4D1A6BF11BA6344BF0BE16F218975F142DC4 | |||
| 6288 | ch341ser.exe.exe | C:\WCH.CN\CH341SER\CH341PORTSA64.DLL | executable | |
MD5:B4473934B81F227AD3AD20D4390CC98D | SHA256:7892887ACDB2FD7B7350B1F839B7451FF5BE37439A8C1699F3C5FCE0A753DEAF | |||
| 6288 | ch341ser.exe.exe | C:\WCH.CN\CH341SER\CH341PTA64.DLL | executable | |
MD5:0A808CC4258B4A38E1FCA2C2436D993E | SHA256:24351288F5E4541C440DA9896AB748924A973CA3A9EC0F772656B818F81EAFDA | |||
| 6288 | ch341ser.exe.exe | C:\WCH.CN\CH341SER\WIN 1X\CH341PORTSA64.DLL | executable | |
MD5:042064358876241D1A425E640A85DB79 | SHA256:A5374B06AE2B35542C243A0F1DAF6F1C921EF668BEBCE8FC08FE8F3DA8008789 | |||
| 6288 | ch341ser.exe.exe | C:\WCH.CN\CH341SER\CH341PT.DLL | executable | |
MD5:D441A6946389C320C0C5B05EEDDC7A83 | SHA256:86C06281480A826FD3BE068F12CCDFBBC4FFF06366763264FD4365DDE43BE5D4 | |||
| 6288 | ch341ser.exe.exe | C:\WCH.CN\CH341SER\CH341SER.INF | binary | |
MD5:78FFBA206BD9552EE20BB91121FE889B | SHA256:2338AF9D0810E0C107683EAE0326CB1A8D00EF13E73D8F4EF0F42261AA9C6EFE | |||
| 6288 | ch341ser.exe.exe | C:\WCH.CN\CH341SER\CH341S64.SYS | executable | |
MD5:40EB04B1C5CB274E28A66DCE0ED083CC | SHA256:A9176E7E47BE89B30A4C834E04F23D362B27CEDE671BD2226F07F940A050B2BB | |||
| 6288 | ch341ser.exe.exe | C:\WCH.CN\CH341SER\CH341S98.SYS | executable | |
MD5:363B7CADD3D533738CBCA4EA8D97758F | SHA256:EF2AFBB2679ADDED712555ED8D99EB79C365526503D646F972BE81899A65154C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6552 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6552 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6220 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |