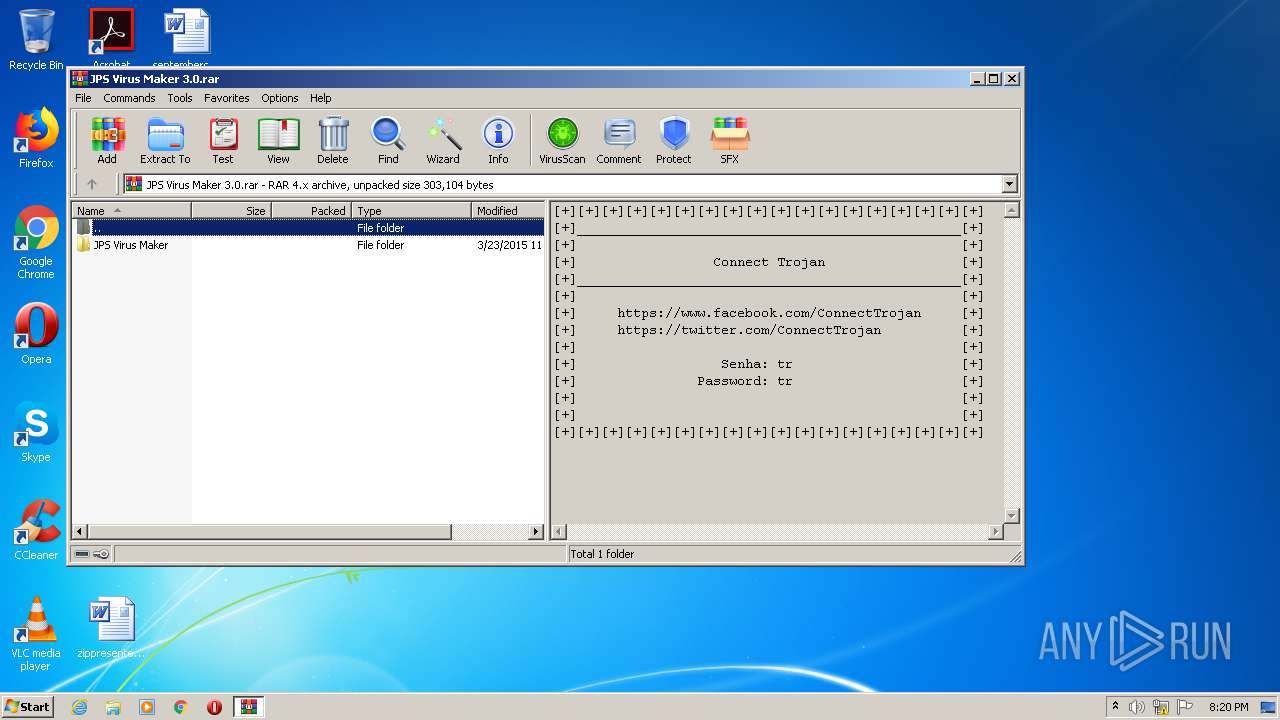
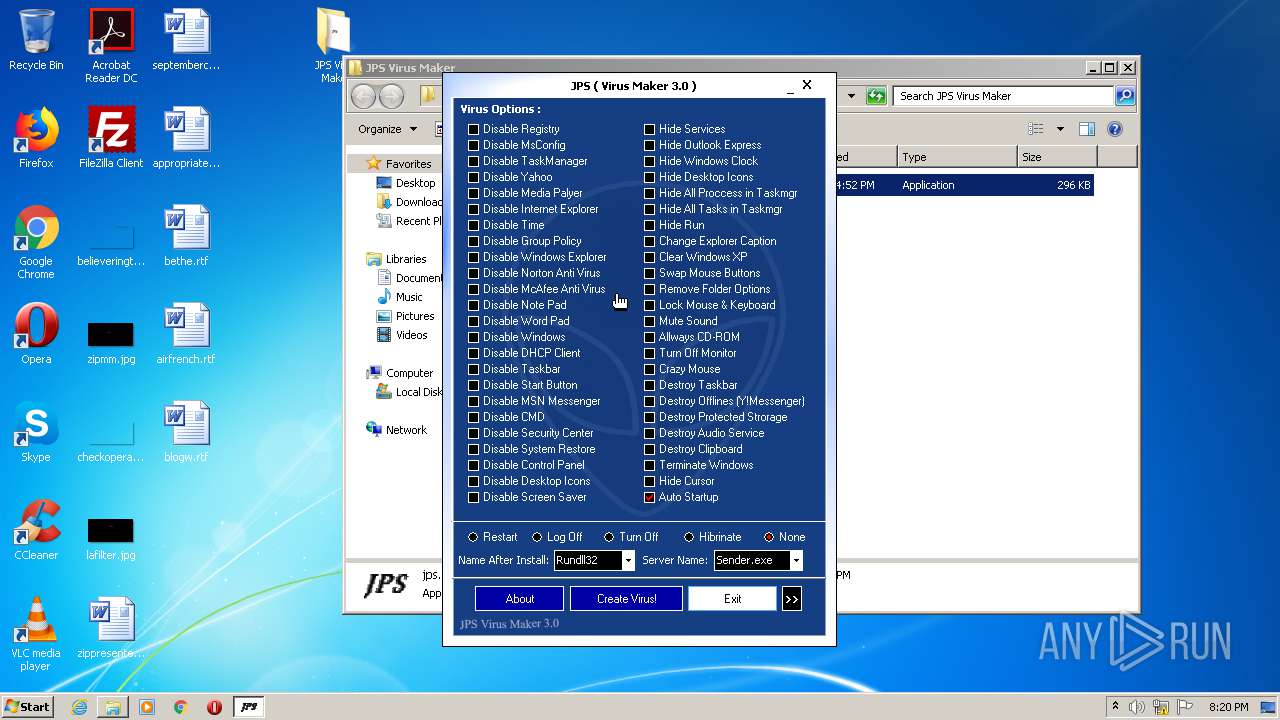
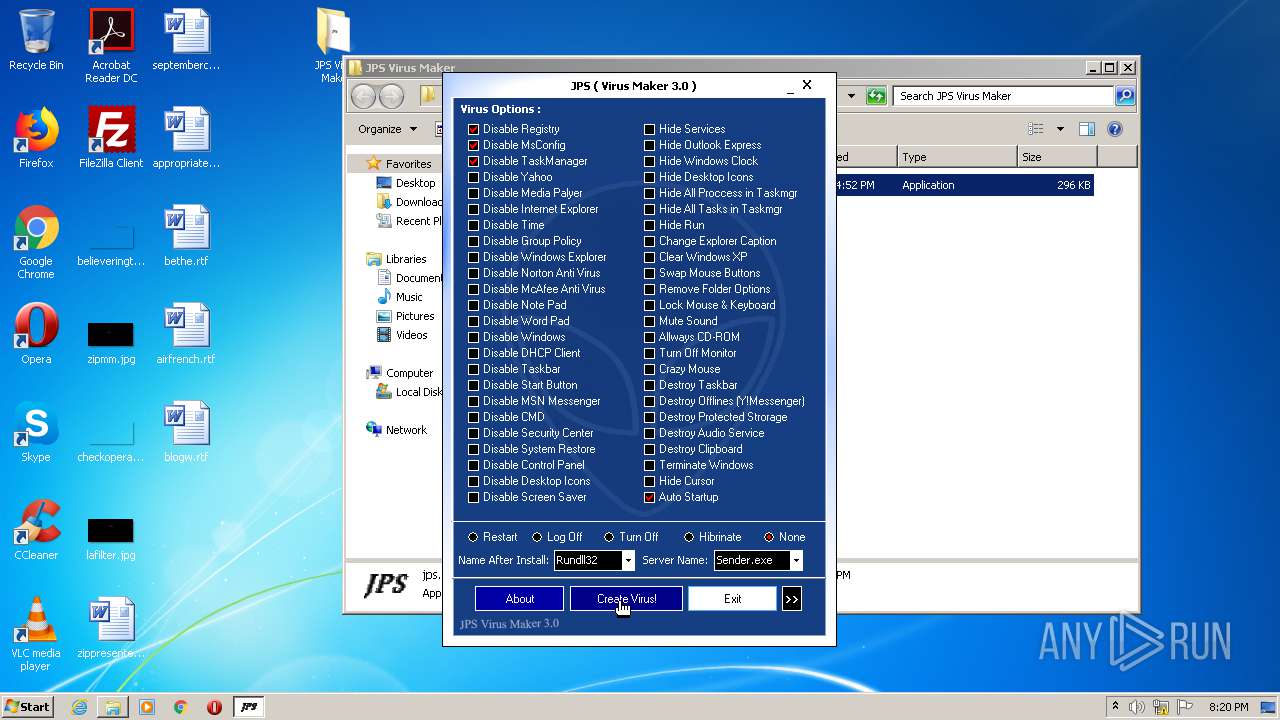
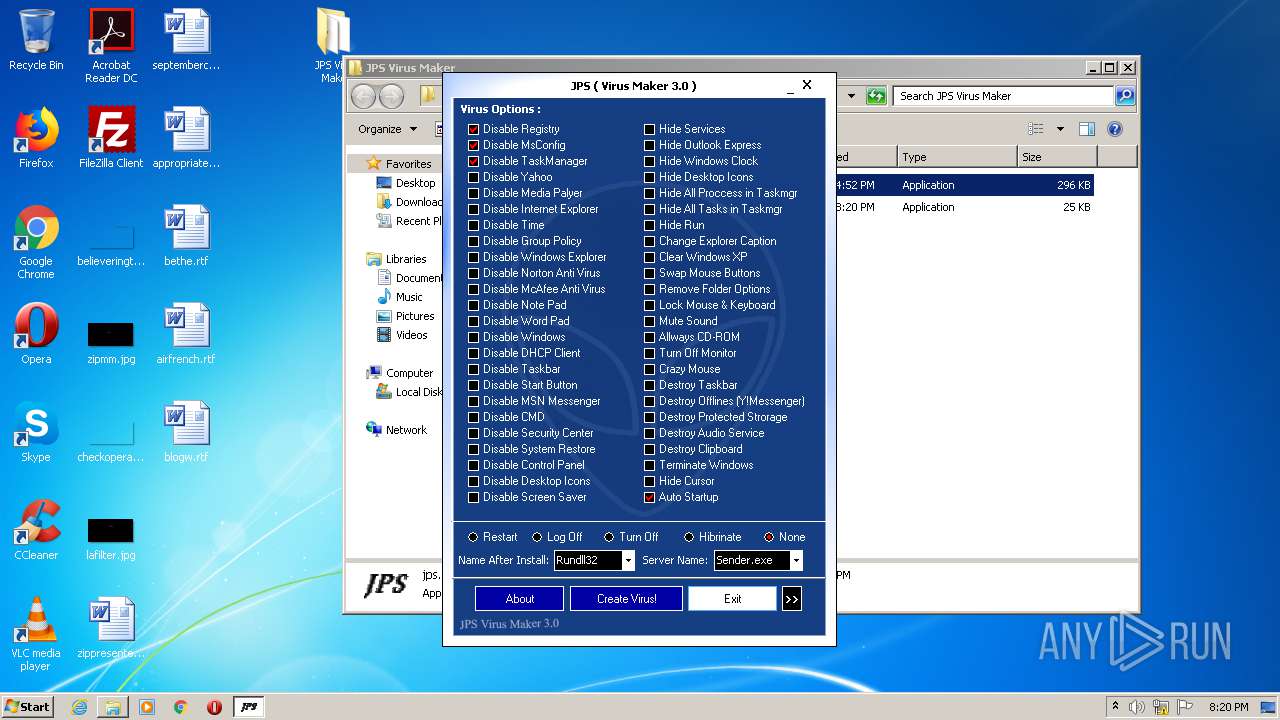
| File name: | JPS Virus Maker 3.0.rar |
| Full analysis: | https://app.any.run/tasks/86c2cbf2-2900-49fb-baae-b05f366f7db0 |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2020, 20:19:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | C5D098D1E3027216EBA278E964AE2004 |
| SHA1: | 69E45799B3B8EBB32D759DE63B8CA0BA931054E9 |
| SHA256: | 2D861C567F6935E8DB5B4E48C29928543257039DA1AC3B653EF40F0DE9DFA87B |
| SSDEEP: | 6144:wNPBREgECaADty0Jg8Bx8roQfB6aT/VPFotC+yZaq1:wJnuuy0Jg8BxjY9PFotZq1 |
MALICIOUS
Application was dropped or rewritten from another process
- Sender.exe (PID: 1916)
- Rundll32.exe (PID: 2812)
Drops executable file immediately after starts
- Sender.exe (PID: 1916)
SUSPICIOUS
Executable content was dropped or overwritten
- jps.exe (PID: 2792)
- Sender.exe (PID: 1916)
Creates files in the Windows directory
- Sender.exe (PID: 1916)
Drops a file with too old compile date
- jps.exe (PID: 2792)
- Sender.exe (PID: 1916)
Starts itself from another location
- Sender.exe (PID: 1916)
INFO
Manual execution by user
- jps.exe (PID: 2792)
- Sender.exe (PID: 1916)
- taskmgr.exe (PID: 992)
- taskmgr.exe (PID: 2080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 296180 |
|---|---|
| UncompressedSize: | 303104 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2007:02:24 16:52:22 |
| PackingMethod: | Normal |
| ArchivedFileName: | JPS Virus Maker\jps.exe |
Total processes
43
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 992 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1916 | "C:\Users\admin\Desktop\JPS Virus Maker\Sender.exe" | C:\Users\admin\Desktop\JPS Virus Maker\Sender.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2080 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2540 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\JPS Virus Maker 3.0.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2792 | "C:\Users\admin\Desktop\JPS Virus Maker\jps.exe" | C:\Users\admin\Desktop\JPS Virus Maker\jps.exe | explorer.exe | ||||||||||||
User: admin Company: www.jeyjey.blogfa.com Integrity Level: MEDIUM Description: Arash Veyskarami Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 2812 | "C:\Windows\system32\config\Rundll32.exe" | C:\Windows\system32\config\Rundll32.exe | — | Sender.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 460
Read events
457
Write events
2 003
Delete events
0
Modification events
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\JPS Virus Maker 3.0.rar | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
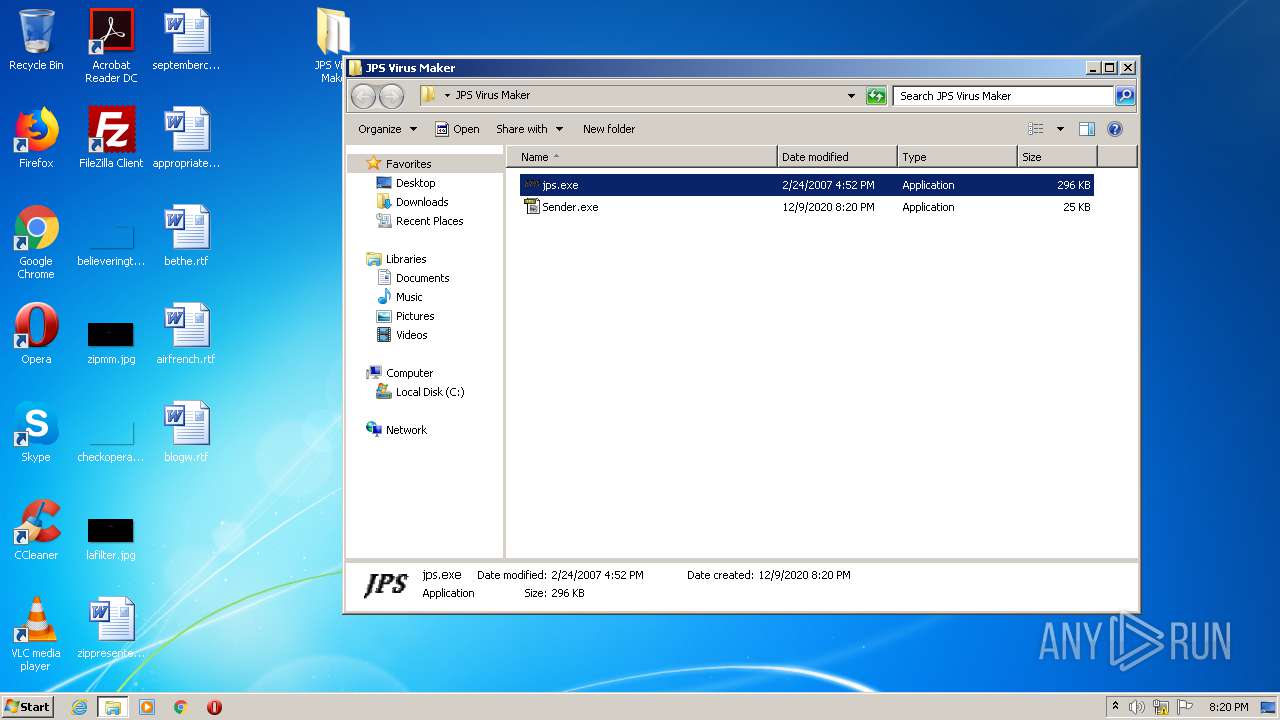
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2540.5573\JPS Virus Maker\jps.exe | — | |
MD5:— | SHA256:— | |||
| 2792 | jps.exe | C:\Users\admin\Desktop\JPS Virus Maker\Sender.exe | executable | |
MD5:— | SHA256:— | |||
| 1916 | Sender.exe | C:\Windows\system32\config\Rundll32.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report