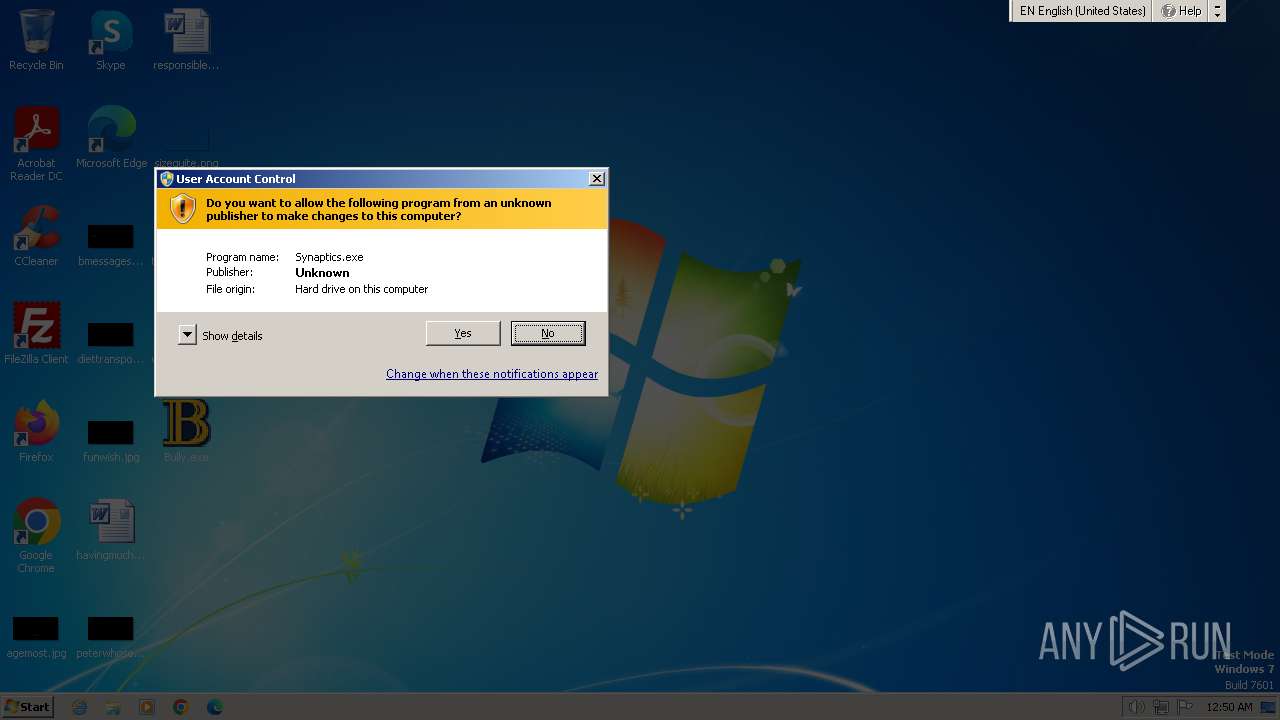
| File name: | Bully.exe |
| Full analysis: | https://app.any.run/tasks/6c3e2ea7-c23f-4fb2-aa55-b2485f8888af |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2024, 00:50:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E8E22D8429AEC80249643BFB7644DC4F |
| SHA1: | C746EE7A474A0188CE40FAA8ECF6C768B4D25E6F |
| SHA256: | 2D7B7B5162BD74990735BAA43F2A4889DAC98180C41FD8255ACBCA0ECE9B5C43 |
| SSDEEP: | 98304:ir7ayGJ6kHOSktuRBrsr/za8sa982nk1Gn0AnFIyNt085fNjv/5BStI4Rf+D5lyA:lTx+7SWTB6A |
MALICIOUS
Drops the executable file immediately after the start
- Bully.exe (PID: 128)
Connects to the CnC server
- Synaptics.exe (PID: 1792)
SUSPICIOUS
Reads the Internet Settings
- Bully.exe (PID: 128)
- Synaptics.exe (PID: 1792)
- Bully.exe (PID: 2588)
Executable content was dropped or overwritten
- Bully.exe (PID: 128)
Reads settings of System Certificates
- Synaptics.exe (PID: 1792)
Reads security settings of Internet Explorer
- Synaptics.exe (PID: 1792)
Checks Windows Trust Settings
- Synaptics.exe (PID: 1792)
INFO
Reads the computer name
- Bully.exe (PID: 128)
- Synaptics.exe (PID: 1792)
- Bully.exe (PID: 2588)
Checks supported languages
- Bully.exe (PID: 128)
- Synaptics.exe (PID: 1792)
- Bully.exe (PID: 2588)
Reads the machine GUID from the registry
- Bully.exe (PID: 128)
- Synaptics.exe (PID: 1792)
- Bully.exe (PID: 2588)
Creates files in the program directory
- Bully.exe (PID: 128)
- Synaptics.exe (PID: 1792)
Checks proxy server information
- Synaptics.exe (PID: 1792)
Manual execution by a user
- Bully.exe (PID: 2588)
Creates files or folders in the user directory
- Synaptics.exe (PID: 1792)
Create files in a temporary directory
- Synaptics.exe (PID: 1792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (90.9) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (5.6) |
| .exe | | | Win32 Executable Delphi generic (1.9) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 629760 |
| InitializedDataSize: | 8345088 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9ab80 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.4 |
| ProductVersionNumber: | 1.0.0.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Turkish |
| CharacterSet: | Windows, Turkish |
| CompanyName: | Synaptics |
| FileDescription: | Synaptics Pointing Device Driver |
| FileVersion: | 1.0.0.4 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Synaptics Pointing Device Driver |
| ProductVersion: | 1.0.0.0 |
| Comments: | - |
Total processes
46
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Users\admin\Desktop\Bully.exe" | C:\Users\admin\Desktop\Bully.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: MEDIUM Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 1036 | "C:\Users\admin\Desktop\._cache_Bully.exe" | C:\Users\admin\Desktop\._cache_Bully.exe | — | Bully.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3222601730 Modules
| |||||||||||||||
| 1404 | "C:\Users\admin\Desktop\._cache_Bully.exe" | C:\Users\admin\Desktop\._cache_Bully.exe | — | Bully.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3222601730 Modules
| |||||||||||||||
| 1792 | "C:\ProgramData\Synaptics\Synaptics.exe" InjUpdate | C:\ProgramData\Synaptics\Synaptics.exe | Bully.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: HIGH Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 2588 | "C:\Users\admin\Desktop\Bully.exe" | C:\Users\admin\Desktop\Bully.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: HIGH Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
Total events
6 603
Read events
6 450
Write events
153
Delete events
0
Modification events
| (PID) Process: | (128) Bully.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (128) Bully.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (128) Bully.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (128) Bully.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (128) Bully.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1792) Synaptics.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1792) Synaptics.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1792) Synaptics.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1792) Synaptics.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1792) Synaptics.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
4
Suspicious files
10
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 128 | Bully.exe | C:\ProgramData\Synaptics\Synaptics.exe | executable | |
MD5:E8E22D8429AEC80249643BFB7644DC4F | SHA256:2D7B7B5162BD74990735BAA43F2A4889DAC98180C41FD8255ACBCA0ECE9B5C43 | |||
| 1792 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E87CE99F124623F95572A696C80EFCAF_ACE741CAE478F9E8195FFCECA66B0544 | binary | |
MD5:DAFE2402B247CED4264F71D7F09755C7 | SHA256:BA955FD1AB377ED6B8C3962A0A761B2BC14E648B0A7BE6DB93D7DF1C85D5E330 | |||
| 1792 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:10BC1463C2326403E6E2A83112554ADD | SHA256:A2B62727608D9216237A6608A2E995C28D3656B72C06EE0B651878F26DF7E8FF | |||
| 1792 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E87CE99F124623F95572A696C80EFCAF_ACE741CAE478F9E8195FFCECA66B0544 | binary | |
MD5:E53071217F4AAE9ED9BA9008738B0E29 | SHA256:1556037EFB0FBD9BD04AFC8F1FC61882C6FBD8A6082CF811DF9D7F65755BDE79 | |||
| 1792 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:41DBDD8F3A73C39F856D542762A2DB73 | SHA256:D5D4D17A05F45DFFF52B9002122325D9FA8E9E9DCCBFF642EC1FAD662007F927 | |||
| 128 | Bully.exe | C:\Users\admin\Desktop\._cache_Bully.exe | executable | |
MD5:05FD0E16D4F3B1054F87121B0DD175F0 | SHA256:3F8565F37E5A70036127FA688B08D1B404CA231C74886F455B0B2E69705BEF80 | |||
| 1792 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1792 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:D5BF78085E01E43C4D7943B27262CB02 | SHA256:95B17B7BEF875519FB01B9308D0A82AAE378EC9CE96F09D5FBB8E00A655C7339 | |||
| 1792 | Synaptics.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\265C0DEB29181DD1891051371C5F863A_921F9AECB814BEF93626AE98C6136F17 | binary | |
MD5:9F39BEE5328B70C5EF8E7D8755B5F424 | SHA256:53EA2F5B650ADEFF0306AD6570E58809AE18C54031526A4FB56E4112324E9BB1 | |||
| 128 | Bully.exe | C:\ProgramData\Synaptics\RCX441.tmp | executable | |
MD5:31E524FEE4A936939916AF7E2CC22196 | SHA256:B41C9FD8F689D49580A80B0E821A29AD5E29456FAE9384C11A4DAF97DCF08EF2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
10
DNS requests
6
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1792 | Synaptics.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8b3221e4b66ea220 | unknown | compressed | 4.66 Kb | unknown |
1792 | Synaptics.exe | GET | 200 | 174.128.246.100:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | text | 31 b | unknown |
1792 | Synaptics.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1792 | Synaptics.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
1792 | Synaptics.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCc21SZGmxMgAqM79mihzX3 | unknown | binary | 472 b | unknown |
1792 | Synaptics.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEkmJh4vi%2F2BCV%2F%2FttUhx%2BQ%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1792 | Synaptics.exe | 174.128.246.100:80 | freedns.afraid.org | ST-BGP | US | unknown |
1792 | Synaptics.exe | 142.250.74.206:443 | docs.google.com | GOOGLE | US | whitelisted |
1792 | Synaptics.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1792 | Synaptics.exe | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1792 | Synaptics.exe | 216.58.206.33:443 | drive.usercontent.google.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
xred.mooo.com |
| unknown |
freedns.afraid.org |
| whitelisted |
docs.google.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
drive.usercontent.google.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to Abused Domain *.mooo.com |
3 ETPRO signatures available at the full report