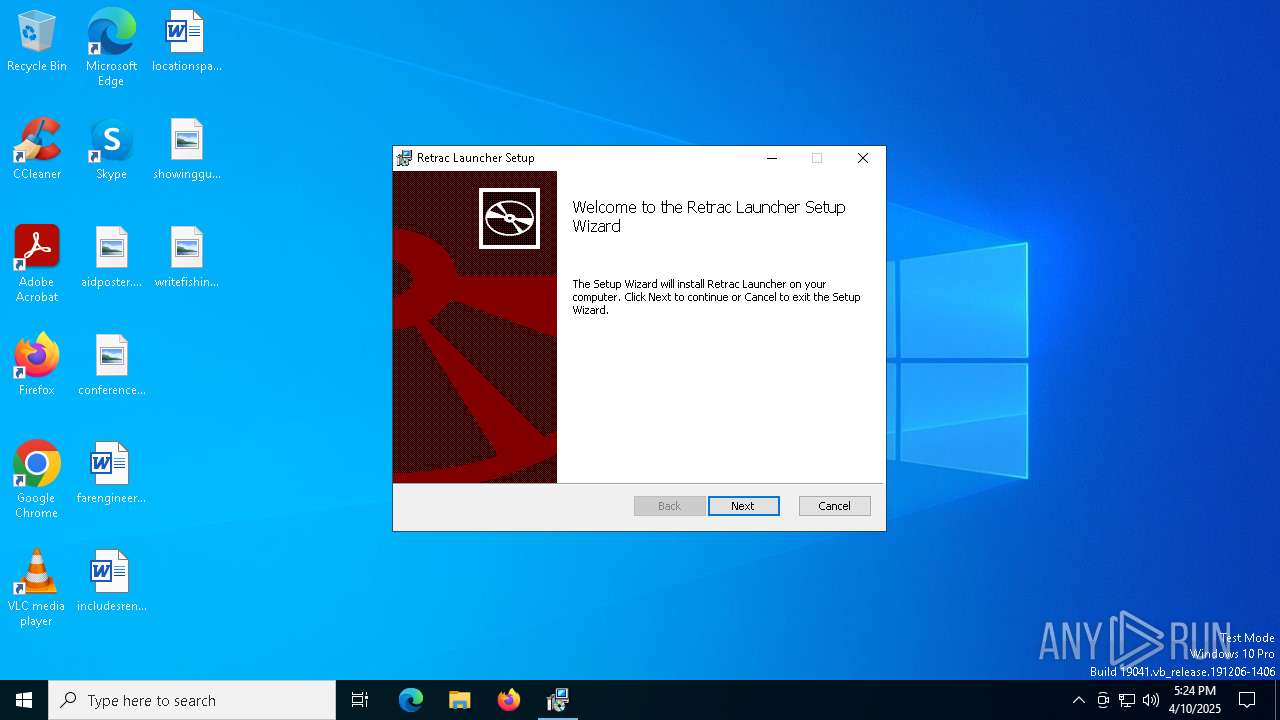
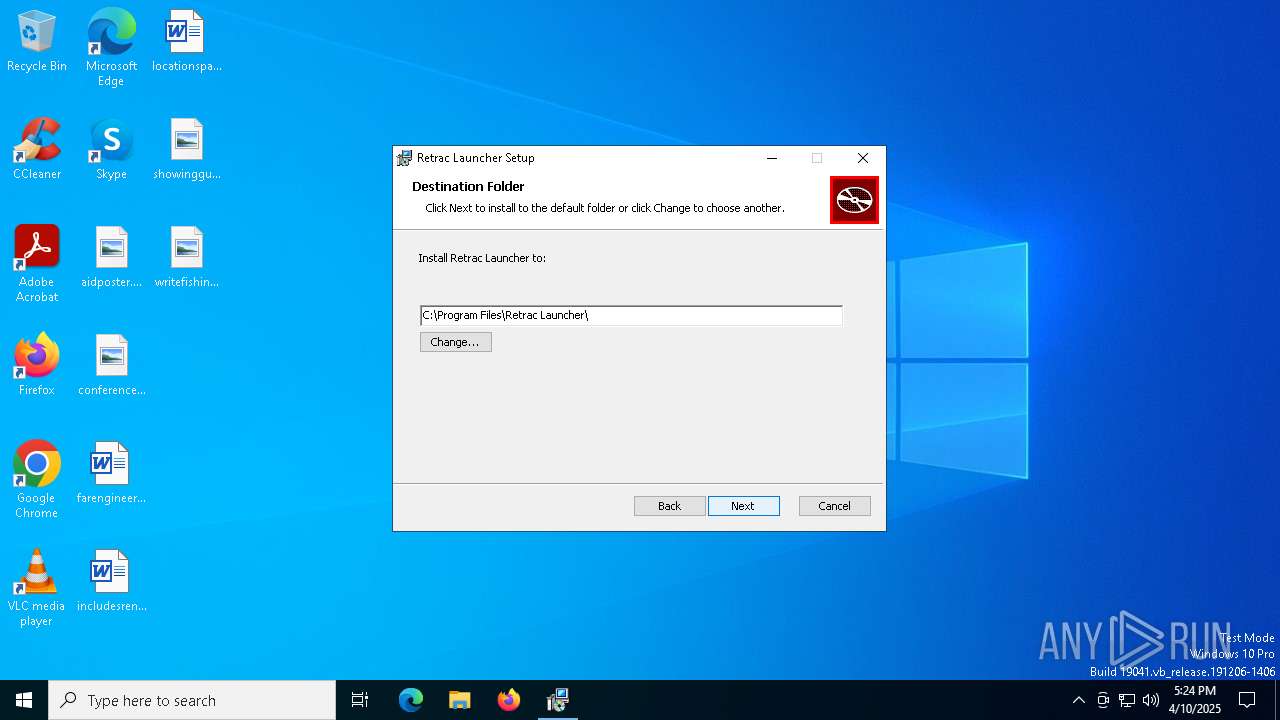
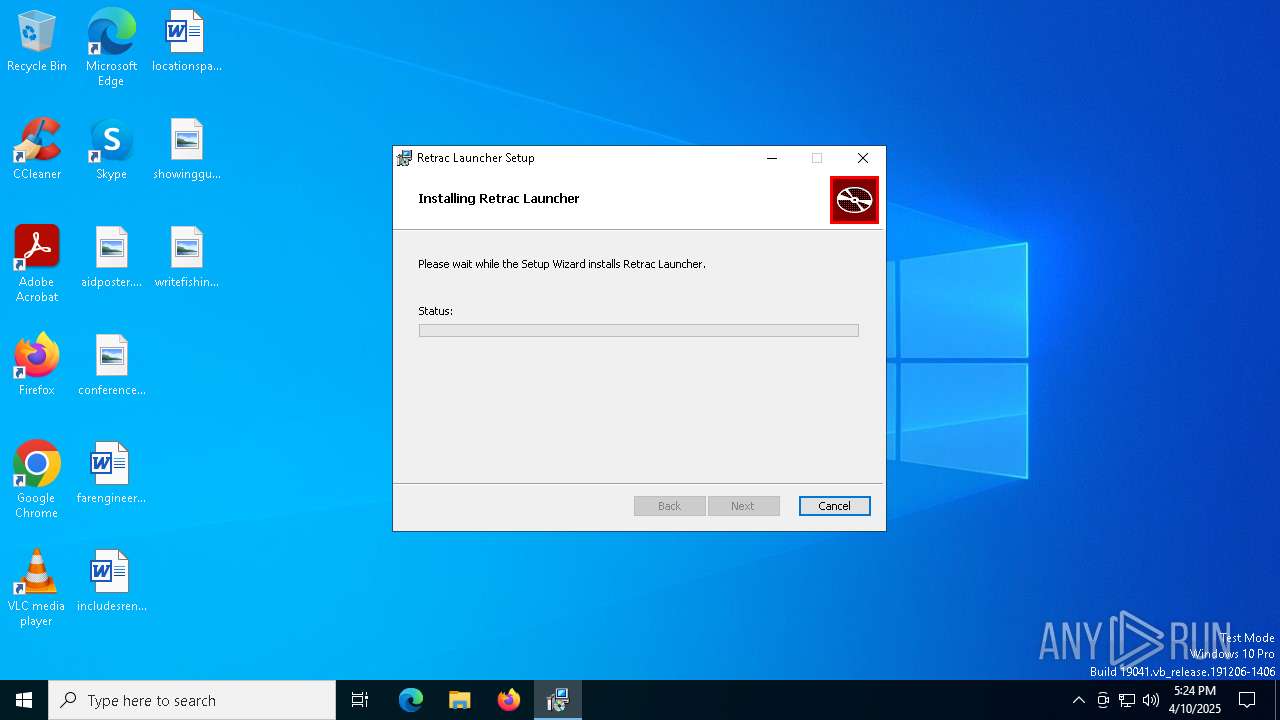
| File name: | Retrac.Launcher_1.0.20_x64_en-US.msi |
| Full analysis: | https://app.any.run/tasks/3ecca0e8-99c9-4ce0-9fd3-3cb6d0022820 |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2025, 17:23:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Retrac Launcher, Author: retrac, Keywords: Installer, Comments: This installer database contains the logic and data required to install Retrac Launcher., Template: x64;0, Revision Number: {9C0108FB-123F-402E-BE6E-952F9675CB5C}, Create Time/Date: Sat Jan 25 15:54:14 2025, Last Saved Time/Date: Sat Jan 25 15:54:14 2025, Number of Pages: 450, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 950D02BAC3C4B74DB88DC490DD532232 |
| SHA1: | 3ABCF285A025772FC8E61F7C0CB04CC4B4A44E0E |
| SHA256: | 2D757F0266C30D807C65301A3D8CF036DB3E7B450A40A1E85AA79894FE138DE3 |
| SSDEEP: | 98304:4z7WBKlkY5FEmybILtDfChesgllZReUPFGZEitv6WLXF/y6p1IGORqLKumDJ8jIa:mLdiNXks |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 4896)
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 5964)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 7708)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7496)
Manipulates environment variables
- powershell.exe (PID: 4896)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 7496)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 7496)
Starts process via Powershell
- powershell.exe (PID: 4896)
Downloads file from URI via Powershell
- powershell.exe (PID: 4896)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 4896)
Executable content was dropped or overwritten
- powershell.exe (PID: 4896)
- MicrosoftEdgeWebview2Setup.exe (PID: 2420)
- MicrosoftEdgeUpdate.exe (PID: 5964)
Process drops legitimate windows executable
- powershell.exe (PID: 4896)
- MicrosoftEdgeUpdate.exe (PID: 5964)
- MicrosoftEdgeWebview2Setup.exe (PID: 2420)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 2420)
- MicrosoftEdgeUpdate.exe (PID: 5964)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 900)
- MicrosoftEdgeUpdate.exe (PID: 1852)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6752)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 4188)
Reads security settings of Internet Explorer
- MicrosoftEdgeUpdate.exe (PID: 5964)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 5964)
INFO
Reads the computer name
- msiexec.exe (PID: 7496)
- msiexec.exe (PID: 7576)
- MicrosoftEdgeUpdate.exe (PID: 5964)
- MicrosoftEdgeUpdate.exe (PID: 1852)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 900)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6752)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 4188)
- MicrosoftEdgeUpdate.exe (PID: 6044)
- MicrosoftEdgeUpdate.exe (PID: 7408)
- MicrosoftEdgeUpdate.exe (PID: 8032)
An automatically generated document
- msiexec.exe (PID: 7440)
Checks supported languages
- msiexec.exe (PID: 7576)
- msiexec.exe (PID: 7496)
- MicrosoftEdgeWebview2Setup.exe (PID: 2420)
- MicrosoftEdgeUpdate.exe (PID: 5964)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 900)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6752)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 4188)
- MicrosoftEdgeUpdate.exe (PID: 6044)
- MicrosoftEdgeUpdate.exe (PID: 1852)
- MicrosoftEdgeUpdate.exe (PID: 7408)
- MicrosoftEdgeUpdate.exe (PID: 8032)
Manages system restore points
- SrTasks.exe (PID: 6712)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7440)
- msiexec.exe (PID: 7496)
Creates a software uninstall entry
- msiexec.exe (PID: 7496)
Disables trace logs
- powershell.exe (PID: 4896)
Checks proxy server information
- powershell.exe (PID: 4896)
- MicrosoftEdgeUpdate.exe (PID: 7408)
The sample compiled with english language support
- powershell.exe (PID: 4896)
- MicrosoftEdgeUpdate.exe (PID: 5964)
- MicrosoftEdgeWebview2Setup.exe (PID: 2420)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 2420)
Create files in a temporary directory
- MicrosoftEdgeWebview2Setup.exe (PID: 2420)
- MicrosoftEdgeUpdate.exe (PID: 5964)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 5964)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 6044)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 5964)
Reads the software policy settings
- MicrosoftEdgeUpdate.exe (PID: 6044)
- MicrosoftEdgeUpdate.exe (PID: 7408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Retrac Launcher |
| Author: | retrac |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Retrac Launcher. |
| Template: | x64;0 |
| RevisionNumber: | {9C0108FB-123F-402E-BE6E-952F9675CB5C} |
| CreateDate: | 2025:01:25 15:54:14 |
| ModifyDate: | 2025:01:25 15:54:14 |
| Pages: | 450 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
156
Monitored processes
19
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 900 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.49\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.49\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.49 Modules
| |||||||||||||||
| 1348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1852 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /regserver | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.49 Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe" /silent /install | C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Setup Version: 1.3.195.49 Modules
| |||||||||||||||
| 4188 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.49\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.49\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.49 Modules
| |||||||||||||||
| 4896 | powershell.exe -NoProfile -windowstyle hidden try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}; Invoke-WebRequest -Uri "https://go.microsoft.com/fwlink/p/?LinkId=2124703" -OutFile "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" ; Start-Process -FilePath "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" -ArgumentList ('/silent', '/install') -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5964 | C:\Users\admin\AppData\Local\Temp\EU2C9B.tmp\MicrosoftEdgeUpdate.exe /silent /install "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=prefers" | C:\Users\admin\AppData\Local\Temp\EU2C9B.tmp\MicrosoftEdgeUpdate.exe | MicrosoftEdgeWebview2Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.195.49 Modules
| |||||||||||||||
| 6044 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /ping PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48cmVxdWVzdCBwcm90b2NvbD0iMy4wIiB1cGRhdGVyPSJPbWFoYSIgdXBkYXRlcnZlcnNpb249IjEuMy4xOTUuNDkiIHNoZWxsX3ZlcnNpb249IjEuMy4xOTUuNDkiIGlzbWFjaGluZT0iMCIgc2Vzc2lvbmlkPSJ7ODE5OTY1OUUtNjVEMi00NjVELThGQ0ItRDE2NTdGRDU1RjIzfSIgdXNlcmlkPSJ7NjFDNjFDRTYtRTlDNC00N0Y5LTgzMUEtMjZEMTM2NDNGOTI1fSIgaW5zdGFsbHNvdXJjZT0ib3RoZXJpbnN0YWxsY21kIiByZXF1ZXN0aWQ9IntCNDIxQzVFQy1BRTgxLTQ5RjUtQkIxMS1CMDlBNkNGMjA5Njh9IiBkZWR1cD0iY3IiIGRvbWFpbmpvaW5lZD0iMCI-PGh3IGxvZ2ljYWxfY3B1cz0iNCIgcGh5c21lbW9yeT0iNCIgZGlza190eXBlPSIyIiBzc2U9IjEiIHNzZTI9IjEiIHNzZTM9IjEiIHNzc2UzPSIxIiBzc2U0MT0iMSIgc3NlNDI9IjEiIGF2eD0iMSIvPjxvcyBwbGF0Zm9ybT0id2luIiB2ZXJzaW9uPSIxMC4wLjE5MDQ1LjQwNDYiIHNwPSIiIGFyY2g9Ing2NCIgcHJvZHVjdF90eXBlPSI0OCIgaXNfd2lwPSIwIiBpc19pbl9sb2NrZG93bl9tb2RlPSIwIi8-PG9lbSBwcm9kdWN0X21hbnVmYWN0dXJlcj0iREVMTCIgcHJvZHVjdF9uYW1lPSJERUxMIi8-PGV4cCBldGFnPSIiLz48YXBwIGFwcGlkPSJ7RjNDNEZFMDAtRUZENS00MDNCLTk1NjktMzk4QTIwRjFCQTRBfSIgdmVyc2lvbj0iIiBuZXh0dmVyc2lvbj0iMS4zLjE5NS40OSIgbGFuZz0iIiBicmFuZD0iIiBjbGllbnQ9IiI-PGV2ZW50IGV2ZW50dHlwZT0iMiIgZXZlbnRyZXN1bHQ9IjEiIGVycm9yY29kZT0iMCIgZXh0cmFjb2RlMT0iMCIgc3lzdGVtX3VwdGltZV90aWNrcz0iOTk2MjQwNTE1NCIgaW5zdGFsbF90aW1lX21zPSI5MjIiLz48L2FwcD48L3JlcXVlc3Q- | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | MicrosoftEdgeUpdate.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.49 Modules
| |||||||||||||||
| 6712 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 892
Read events
10 733
Write events
1 116
Delete events
43
Modification events
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000001E459D5D3DAADB01481D0000D41D0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000001E459D5D3DAADB01481D0000D41D0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000003A001E5E3DAADB01481D0000D41D0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000001EBF0F5E3DAADB01481D0000D41D0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000001EBF0F5E3DAADB01481D0000D41D0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000009A9C1B5E3DAADB01481D0000D41D0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7496) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000004543055F3DAADB01481D0000D41D0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 48000000000000001FBD1A5F3DAADB011C1E0000501F0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7708) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
Executable files
204
Suspicious files
15
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7496 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7496 | msiexec.exe | C:\Windows\Installer\110d5b.msi | — | |
MD5:— | SHA256:— | |||
| 7496 | msiexec.exe | C:\Windows\Installer\110d5d.msi | — | |
MD5:— | SHA256:— | |||
| 7440 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIC3FE.tmp | executable | |
MD5:4FDD16752561CF585FED1506914D73E0 | SHA256:AECD2D2FE766F6D439ACC2BBF1346930ECC535012CF5AD7B3273D2875237B7E7 | |||
| 7496 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{f4d09237-29f2-4ba2-8bc3-ff2d144d8134}_OnDiskSnapshotProp | binary | |
MD5:0A41A9119D7E043B0410CBD021E0042A | SHA256:0FD5D432EDDD8E16635EE9426847DCA89663042F8511F7B824826ED4BB497C4B | |||
| 7496 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:0A41A9119D7E043B0410CBD021E0042A | SHA256:0FD5D432EDDD8E16635EE9426847DCA89663042F8511F7B824826ED4BB497C4B | |||
| 7496 | msiexec.exe | C:\Windows\Installer\{DB60CD67-E332-4FE5-BC15-AC908E8FDF97}\ProductIcon | image | |
MD5:B57F2765879042B033B21C525C289D80 | SHA256:B9F884956C9D614CCE40B8E362F814C279AC9C93BBFBA75601587BCD6B7CD117 | |||
| 7496 | msiexec.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Retrac Launcher\Retrac Launcher.lnk | binary | |
MD5:E95EA3C029E835CAD3090248BAB16B8E | SHA256:DDF5386E995FDF3279E45A29765669A0B9E1DCED13C8D4F8F779031929C80070 | |||
| 7496 | msiexec.exe | C:\Program Files\Retrac Launcher\Retrac Launcher.exe | executable | |
MD5:5FB6C0788B7D173A412CCDAD986D4A6E | SHA256:1C849DCE609B4EF151A3CB352D4003F73A8A65C7F40D41CCB96AF2B60C9814B9 | |||
| 7496 | msiexec.exe | C:\Program Files\Retrac Launcher\Uninstall Retrac Launcher.lnk | binary | |
MD5:815094C77A84CA28B10A12453A5D3847 | SHA256:882413D32142A33948A751A14E33BB334CB0FE18DBEBEDCF3E490BE98502F2C1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
30
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.41:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | — | 208.89.74.31:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2d32fe70-a320-4465-a1ad-5f20197f7f9a?P1=1744910677&P2=404&P3=2&P4=TjrSsszMjFx%2fJ%2bSB%2by6LnjWjDkAtfHvy6nCi9oAJjhjiB9%2b8OXgK6ywknxBTy%2fJE6T%2f7yaKxEQ%2bqMynBvEuFVQ%3d%3d | unknown | — | — | whitelisted |
6944 | svchost.exe | HEAD | 200 | 208.89.74.31:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2d32fe70-a320-4465-a1ad-5f20197f7f9a?P1=1744910677&P2=404&P3=2&P4=TjrSsszMjFx%2fJ%2bSB%2by6LnjWjDkAtfHvy6nCi9oAJjhjiB9%2b8OXgK6ywknxBTy%2fJE6T%2f7yaKxEQ%2bqMynBvEuFVQ%3d%3d | unknown | — | — | whitelisted |
4000 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4000 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.41:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6544 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6488 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6988 | svchost.exe | 95.100.186.9:443 | go.microsoft.com | AKAMAI-AS | FR | whitelisted |
4896 | powershell.exe | 95.100.186.9:443 | go.microsoft.com | AKAMAI-AS | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
msedge.sf.dl.delivery.mp.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6944 | svchost.exe | Misc activity | ET INFO Packed Executable Download |