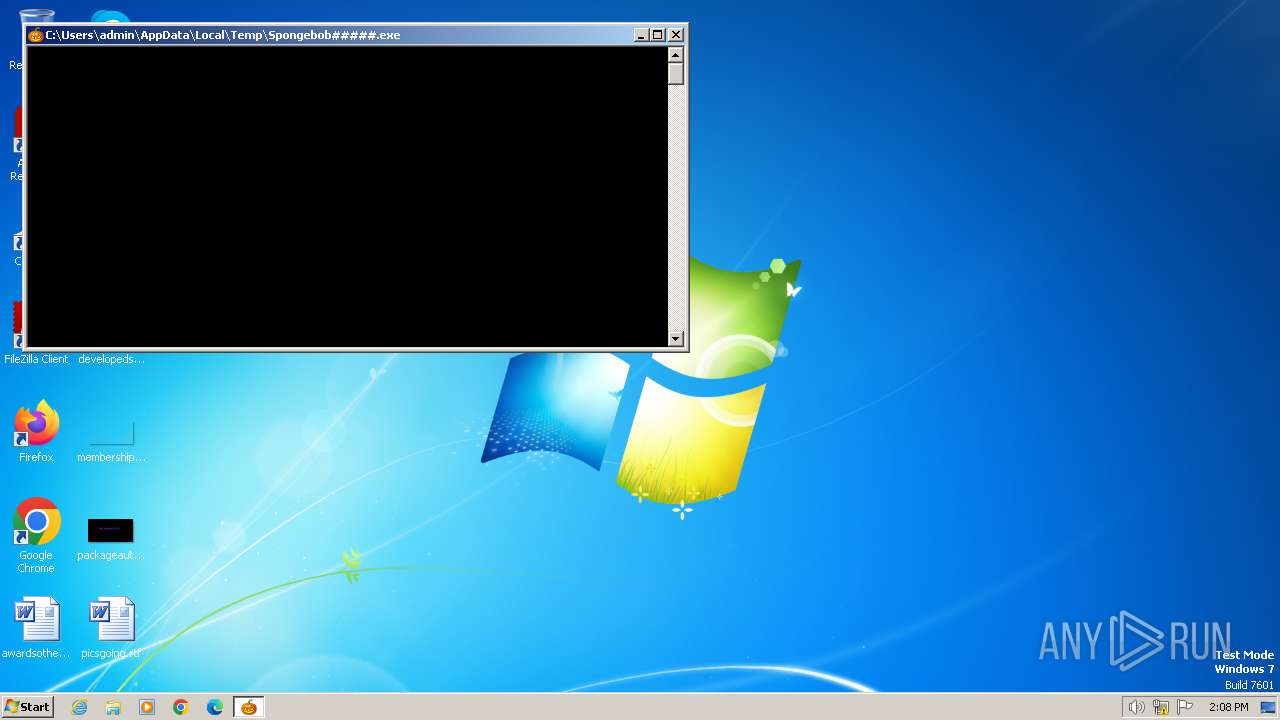
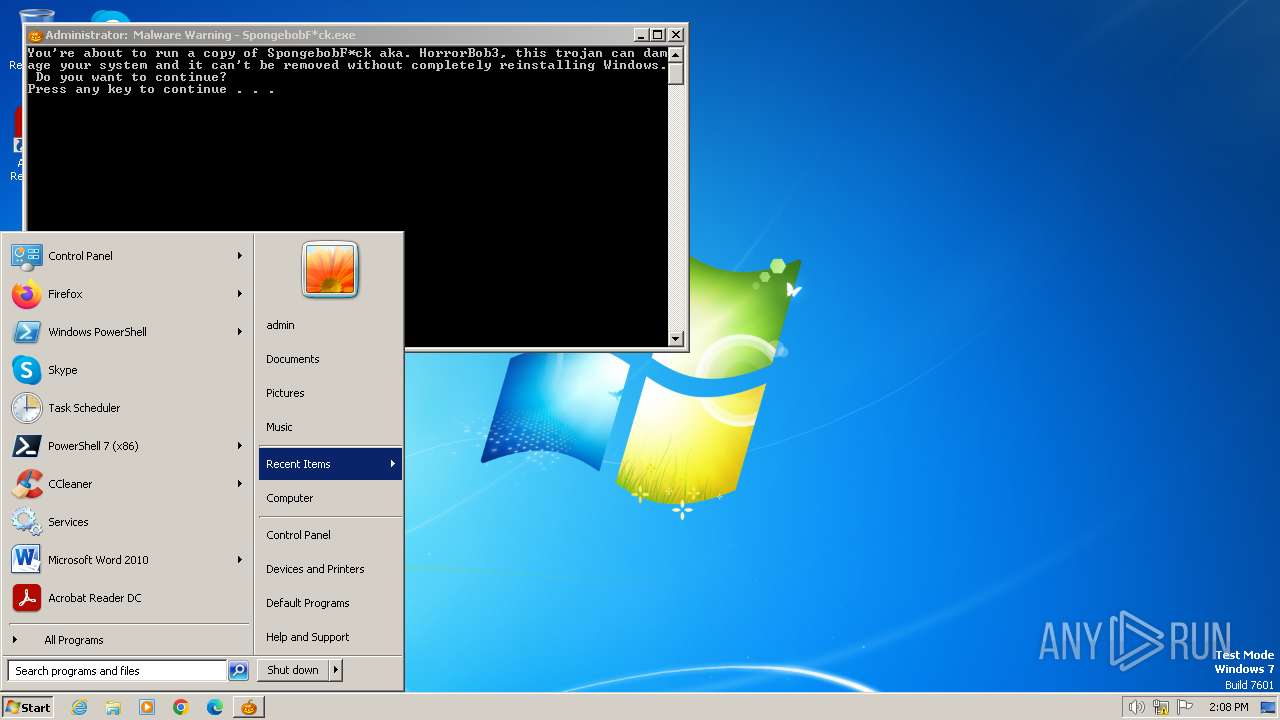
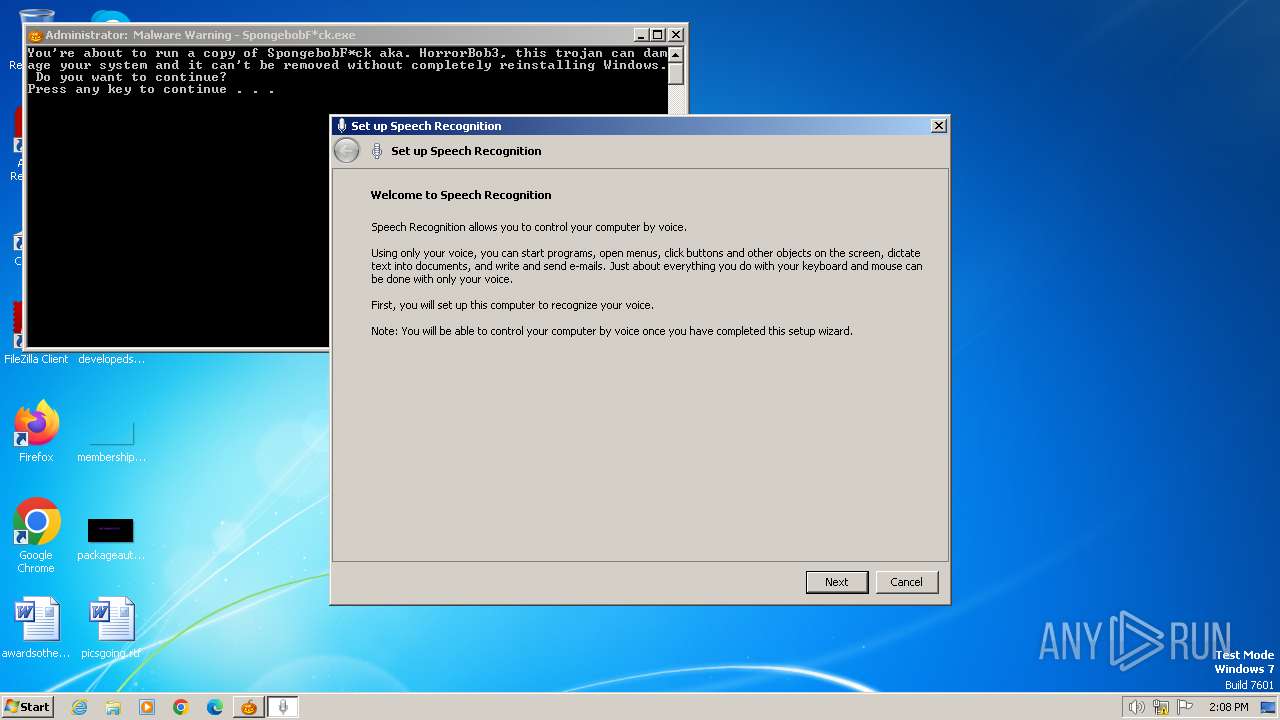
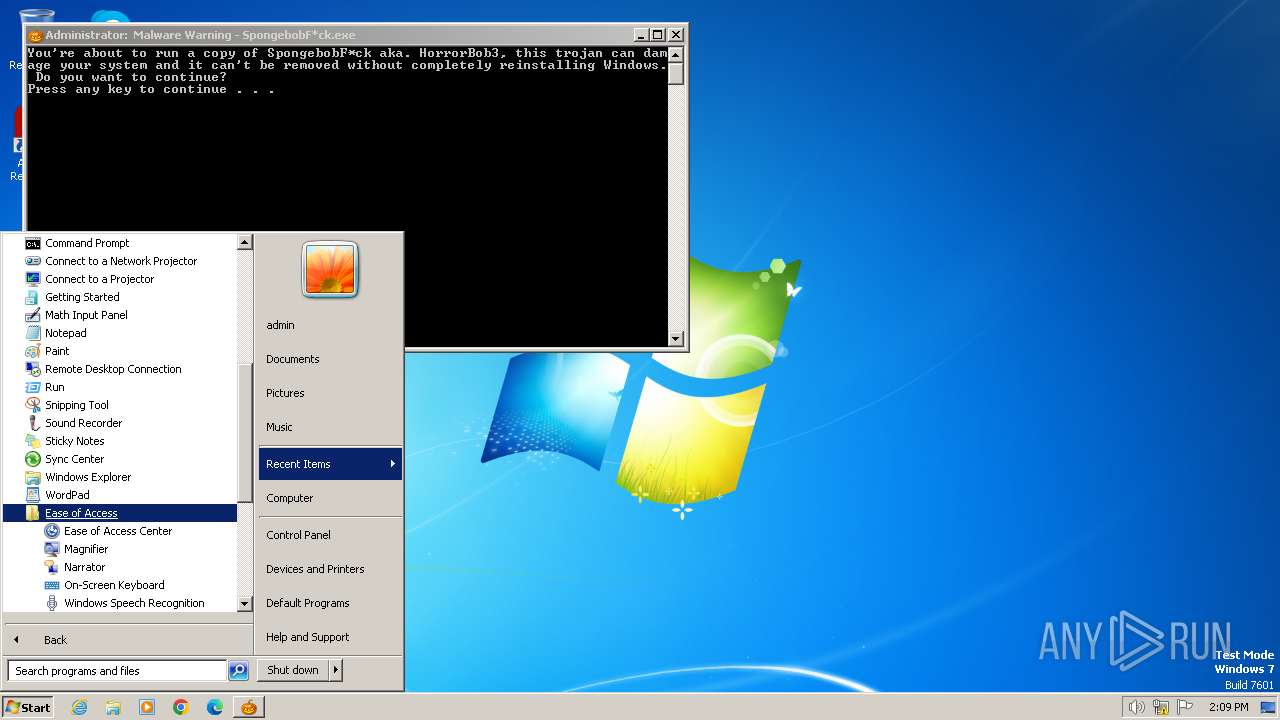
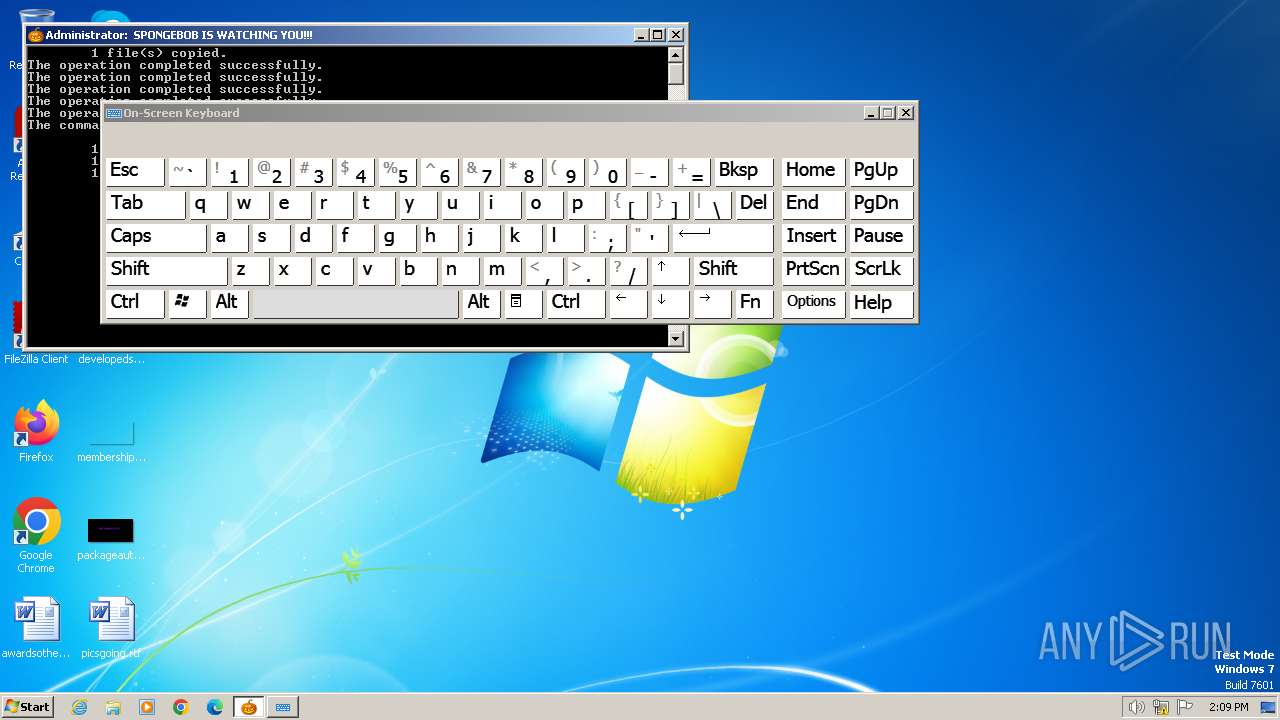
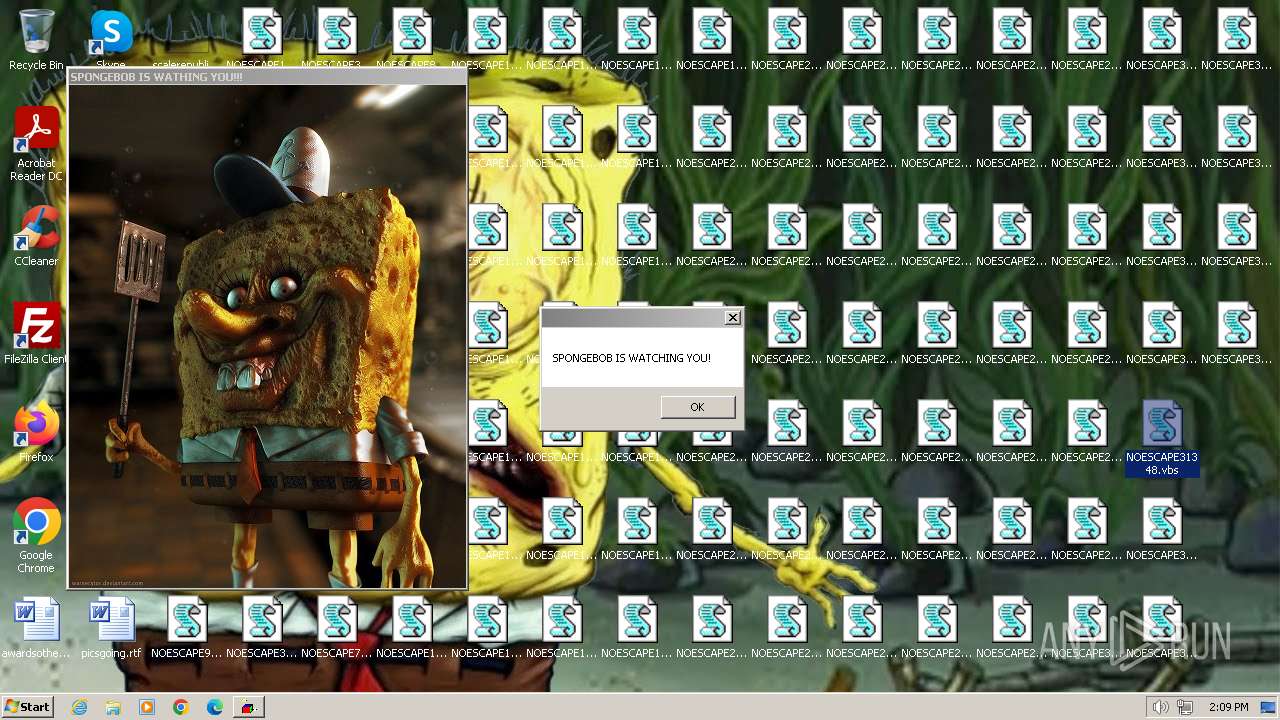
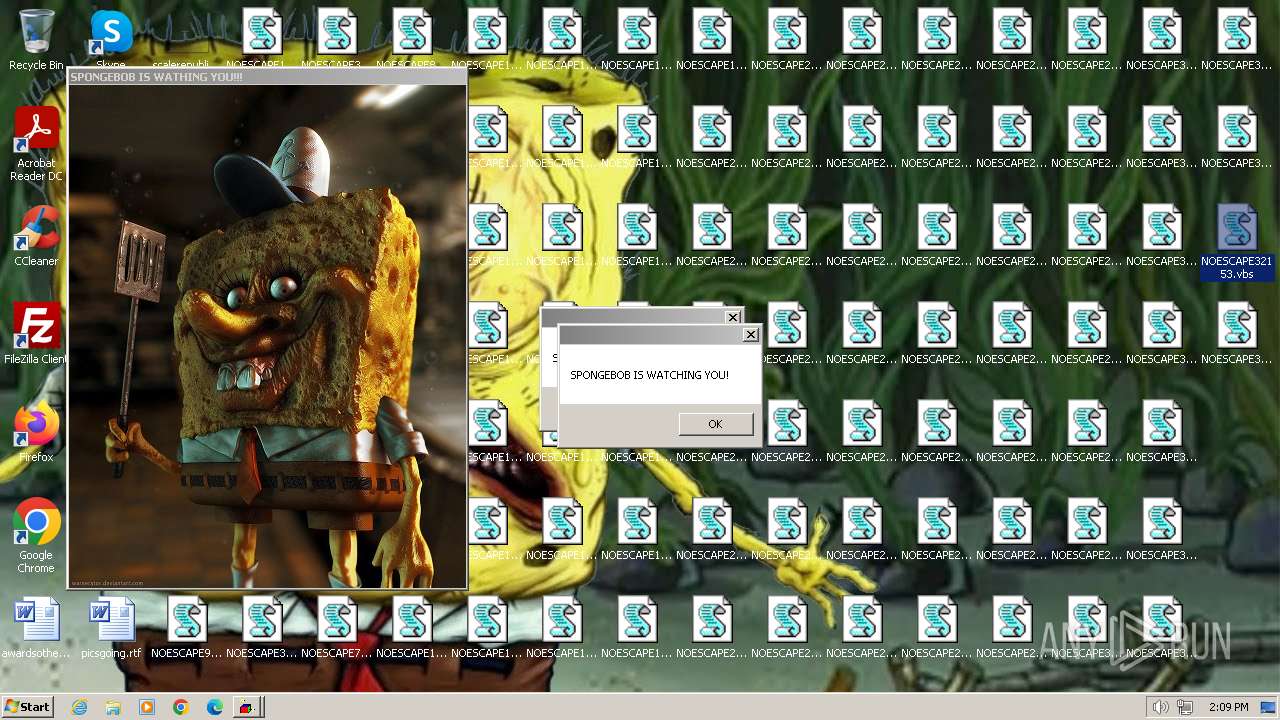
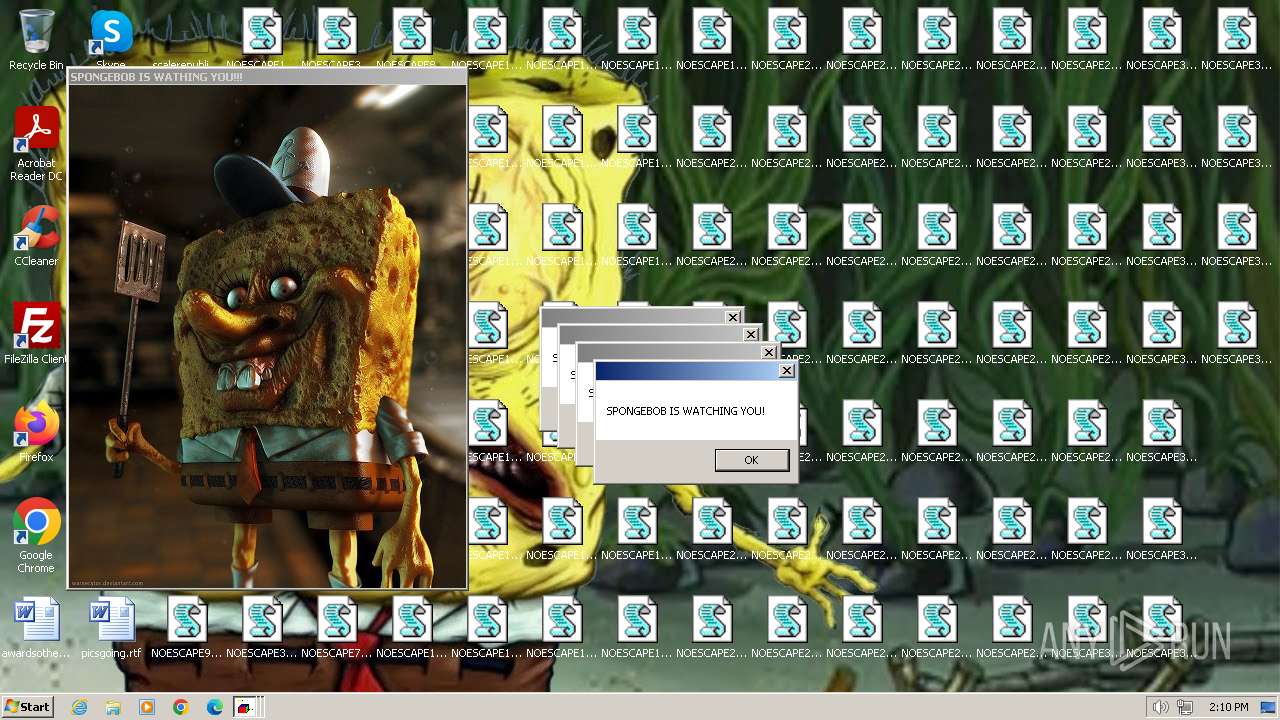
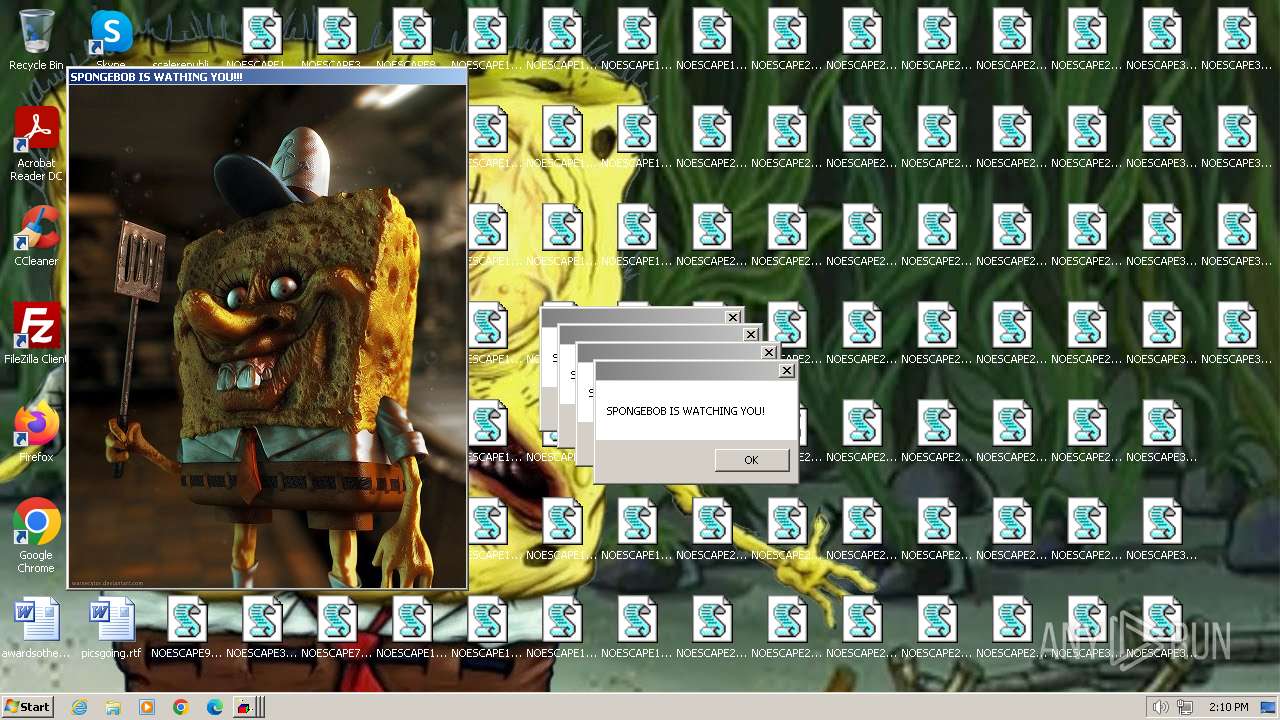
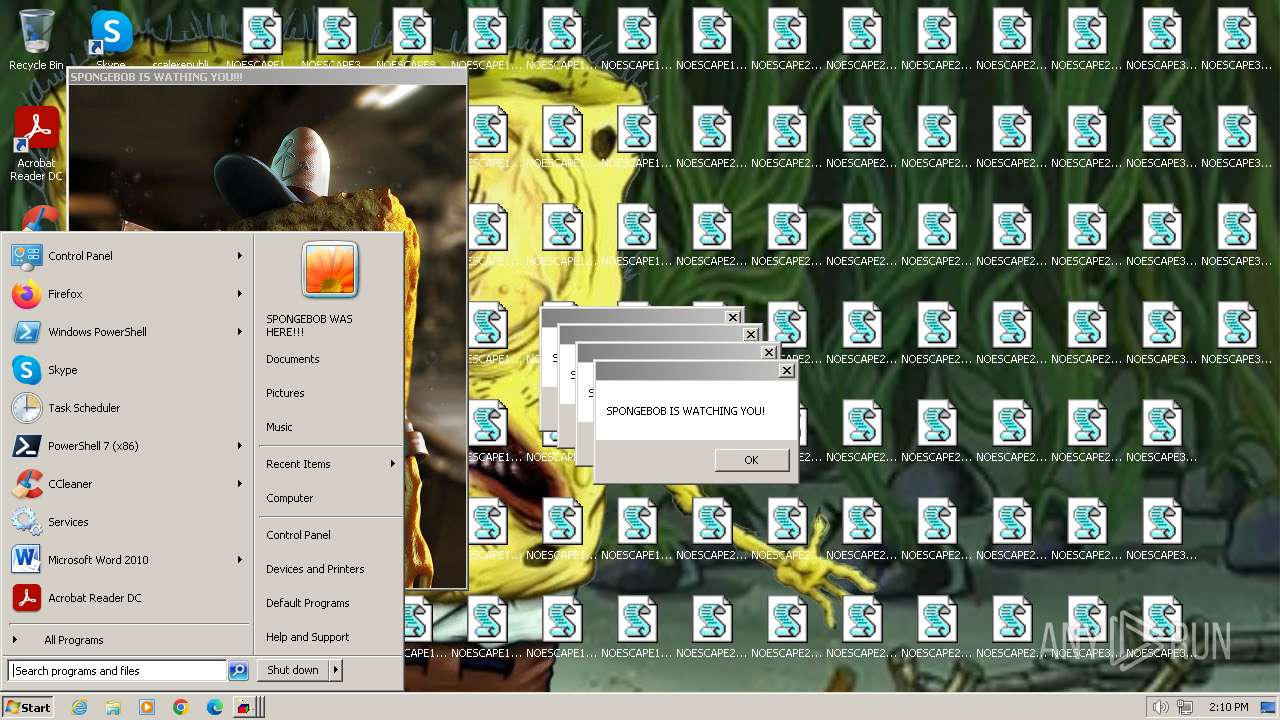
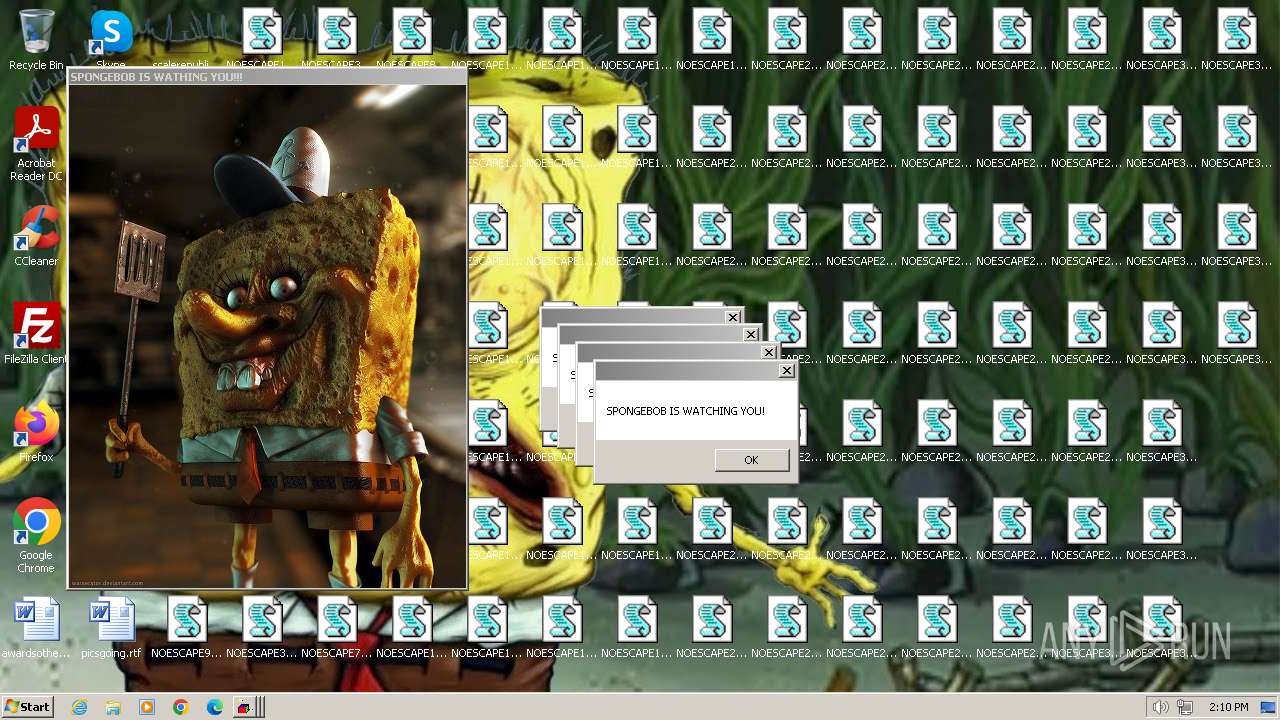
| File name: | Spongebob#####.exe |
| Full analysis: | https://app.any.run/tasks/277e0014-d0d8-498a-8061-1a858760f89e |
| Verdict: | Malicious activity |
| Analysis date: | November 09, 2024, 14:07:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | FF4A17C39D21C1142B374BB10958EB26 |
| SHA1: | 16FFA640CDC8C5D379D3D0F1EA99B8AE3F37013E |
| SHA256: | 2D6A69E59A296086964F4F1B54A6EC0F63C804754839996735F0DCE4CDD853F2 |
| SSDEEP: | 49152:Rti/NQprhknubdpvBZNLs67pOCAayKQydrZebinz9KMxjfjzgdFHPNL:S/6prh7fBZN4AICvyKnubinzthfjzgXl |
MALICIOUS
Create files in the Startup directory
- cmd.exe (PID: 1368)
Disables Windows Defender
- reg.exe (PID: 3436)
UAC/LUA settings modification
- reg.exe (PID: 3492)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 1368)
- net.exe (PID: 1468)
SUSPICIOUS
Executable content was dropped or overwritten
- Spongebob#####.exe (PID: 3684)
- cmd.exe (PID: 1368)
Starts CMD.EXE for commands execution
- Spongebob#####.exe (PID: 3684)
Executing commands from ".cmd" file
- Spongebob#####.exe (PID: 3684)
Reads security settings of Internet Explorer
- sapisvr.exe (PID: 1008)
- sapisvr.exe (PID: 3012)
Reads the Internet Settings
- sapisvr.exe (PID: 3012)
- sipnotify.exe (PID: 292)
- sapisvr.exe (PID: 1008)
Creates file in the systems drive root
- cmd.exe (PID: 1368)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1368)
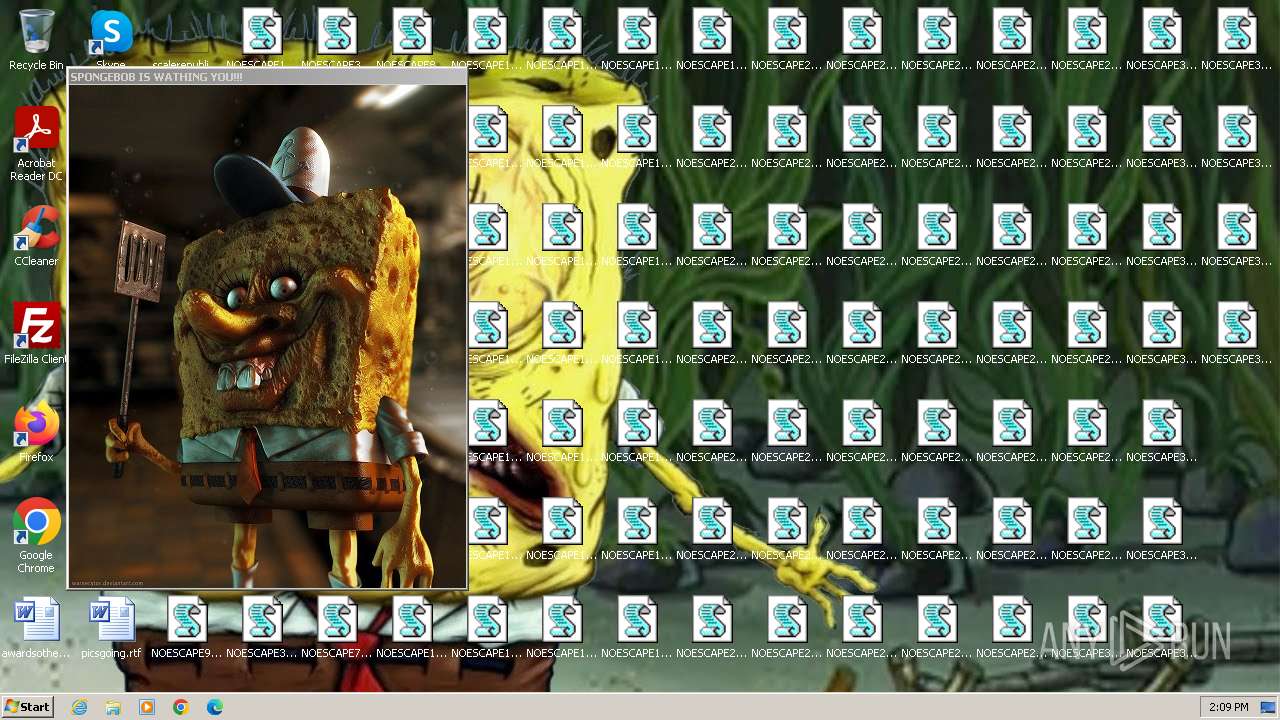
Changes the desktop background image
- reg.exe (PID: 4024)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 1368)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1628)
- sipnotify.exe (PID: 292)
The system shut down or reboot
- cmd.exe (PID: 1368)
Reads settings of System Certificates
- sipnotify.exe (PID: 292)
Likely accesses (executes) a file from the Public directory
- wscript.exe (PID: 2604)
- wscript.exe (PID: 2940)
- wscript.exe (PID: 3160)
- wscript.exe (PID: 3188)
INFO
UPX packer has been detected
- Spongebob#####.exe (PID: 3684)
Create files in a temporary directory
- Spongebob#####.exe (PID: 3684)
Checks supported languages
- Spongebob#####.exe (PID: 3684)
- sapisvr.exe (PID: 3012)
- IMEKLMG.EXE (PID: 2124)
- IMEKLMG.EXE (PID: 2132)
- MainWindow.exe (PID: 2172)
- wmpnscfg.exe (PID: 2584)
- wmpnscfg.exe (PID: 2560)
- sapisvr.exe (PID: 1008)
Manual execution by a user
- sapisvr.exe (PID: 2828)
- sapisvr.exe (PID: 3408)
- sapisvr.exe (PID: 1008)
- sapisvr.exe (PID: 3012)
- osk.exe (PID: 3868)
- osk.exe (PID: 2400)
- IMEKLMG.EXE (PID: 2124)
- IMEKLMG.EXE (PID: 2132)
- MainWindow.exe (PID: 2172)
- wscript.exe (PID: 2152)
- osk.exe (PID: 2184)
- wmpnscfg.exe (PID: 2560)
- wscript.exe (PID: 2604)
- wscript.exe (PID: 2940)
- wscript.exe (PID: 3160)
- wscript.exe (PID: 3188)
- wmpnscfg.exe (PID: 2584)
Reads the computer name
- sapisvr.exe (PID: 1008)
- sapisvr.exe (PID: 3012)
- IMEKLMG.EXE (PID: 2124)
- IMEKLMG.EXE (PID: 2132)
- wmpnscfg.exe (PID: 2560)
- wmpnscfg.exe (PID: 2584)
Creates files or folders in the user directory
- sapisvr.exe (PID: 1008)
The process uses the downloaded file
- sapisvr.exe (PID: 1008)
- sapisvr.exe (PID: 3012)
Reads the time zone
- net1.exe (PID: 1796)
Creates files in the program directory
- cmd.exe (PID: 1368)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2124)
- IMEKLMG.EXE (PID: 2132)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 292)
Reads the software policy settings
- sipnotify.exe (PID: 292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:08 13:12:00+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 2199552 |
| InitializedDataSize: | 221184 |
| UninitializedDataSize: | 1503232 |
| EntryPoint: | 0x388370 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 3.6.6.6 |
| ProductVersionNumber: | 3.6.6.6 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | HorrorTrojan |
| FileDescription: | SPONGEBOB WAS HERE!!! |
| FileVersion: | 3,6,6,6 |
| ProductName: | SpongebobF*ck |
| InternalName: | SPONGEBOB IS WATCHING YOU!!! |
| ProductVersion: | 3,6,6,6 |
| LegalCopyright: | 2022 |
Total processes
129
Monitored processes
33
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 980 | "C:\Windows\system32\Speech\SpeechUX\SpeechUXWiz.exe" UserEnrollment,en-US,HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech\RecoProfiles\Tokens\{1C89B5D5-512A-45FE-8726-F63999D05769},65552,0,"" | C:\Windows\System32\Speech\SpeechUX\SpeechUXWiz.exe | — | sapisvr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Speech UX Configuration Exit code: 3221225547 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1008 | "C:\Windows\Speech\Common\sapisvr.exe" -SpeechUX | C:\Windows\Speech\Common\sapisvr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Speech Recognition Exit code: 3221225547 Version: 5.3.11513.00 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1368 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\C389.tmp\SpongebobFuck.cmd"" | C:\Windows\System32\cmd.exe | Spongebob#####.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1468 | net user admin /fullname:"SPONGEBOB WAS HERE!!!" | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1628 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1796 | C:\Windows\system32\net1 user admin /fullname:"SPONGEBOB WAS HERE!!!" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2060 | "C:\Windows\system32\Speech\SpeechUX\SpeechUXWiz.exe" UserEnrollment,en-US,HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech\RecoProfiles\Tokens\{1C89B5D5-512A-45FE-8726-F63999D05769},65552,0,"" | C:\Windows\System32\Speech\SpeechUX\SpeechUXWiz.exe | — | sapisvr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Speech UX Configuration Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2132 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
Total events
10 125
Read events
9 568
Write events
556
Delete events
1
Modification events
| (PID) Process: | (1008) sapisvr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\Recognizers |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech\Recognizers\Tokens\MS-1033-80-DESK | |||
| (PID) Process: | (1008) sapisvr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\Recognizers\LanguageDefaults |
| Operation: | write | Name: | 409 |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech\Recognizers\Tokens\MS-1033-80-DESK | |||
| (PID) Process: | (1008) sapisvr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\CurrentUserLexicon |
| Operation: | write | Name: | CLSID |
Value: {C9E37C15-DF92-4727-85D6-72E5EEB6995A} | |||
| (PID) Process: | (1008) sapisvr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\CurrentUserLexicon\{C9E37C15-DF92-4727-85D6-72E5EEB6995A}\Files |
| Operation: | write | Name: | Datafile |
Value: %1a%\Microsoft\Speech\Files\UserLexicons\SP_F66E5290272047C7990D4484C4517E39.dat | |||
| (PID) Process: | (1008) sapisvr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\CurrentUserLexicon |
| Operation: | write | Name: | Generation |
Value: 0 | |||
| (PID) Process: | (1008) sapisvr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\CurrentUserShortcut |
| Operation: | write | Name: | CLSID |
Value: {C9E37C15-DF92-4727-85D6-72E5EEB6995A} | |||
| (PID) Process: | (1008) sapisvr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\CurrentUserShortcut\{C9E37C15-DF92-4727-85D6-72E5EEB6995A}\Files |
| Operation: | write | Name: | Datafile |
Value: %1a%\Microsoft\Speech\Files\UserShortcuts\SP_9660E07A03BA4DAE9A79BD191DB6E014.dat | |||
| (PID) Process: | (1008) sapisvr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\AudioInput\TokenEnums\MMAudioIn\{0.0.1.00000000}.{cd6427a6-e7dd-4b3e-8516-c9fd3e17e7b1} |
| Operation: | write | Name: | CLSID |
Value: {CF3D2E50-53F2-11D2-960C-00C04F8EE628} | |||
| (PID) Process: | (1008) sapisvr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\AudioInput\TokenEnums\MMAudioIn\{0.0.1.00000000}.{cd6427a6-e7dd-4b3e-8516-c9fd3e17e7b1} |
| Operation: | write | Name: | DeviceName |
Value: Line In (Realtek AC'97 Audio) | |||
| (PID) Process: | (1008) sapisvr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\AudioInput\TokenEnums\MMAudioIn\{0.0.1.00000000}.{cd6427a6-e7dd-4b3e-8516-c9fd3e17e7b1} |
| Operation: | write | Name: | DeviceId |
Value: {0.0.1.00000000}.{cd6427a6-e7dd-4b3e-8516-c9fd3e17e7b1} | |||
Executable files
4
Suspicious files
3
Text files
110
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3684 | Spongebob#####.exe | C:\Users\admin\AppData\Local\Temp\C389.tmp\SpongebobFuck.cmd | text | |
MD5:7A918ED93F7FB297E05464EDCCC46756 | SHA256:82FCB47B437DC1BEDB77648755770B7CD9A29342FD2AB972C8BD063968D04604 | |||
| 1368 | cmd.exe | C:\bg.bmp | image | |
MD5:CE45A70D3CC2941A147C09264FC1CDA5 | SHA256:ECEEDADFDE8506A73650CFA9A936E6A8FFF7FFB664C9602BB14432AA2F8109AC | |||
| 1368 | cmd.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\bobspeak.vbs | text | |
MD5:8884A25E47D799F6BD3D4EC20F05A3B7 | SHA256:5A68437EDD63BD826A1F1557121D4C05114C608FD8A18A0C9C156A60D90BD0C1 | |||
| 3684 | Spongebob#####.exe | C:\Users\admin\AppData\Local\Temp\C389.tmp\mover.exe | executable | |
MD5:C1978E4080D1EC7E2EDF49D6C9710045 | SHA256:C9E2A7905501745C304FFC5A70B290DB40088D9DC10C47A98A953267468284A8 | |||
| 1368 | cmd.exe | C:\Users\Public\Desktop\NOESCAPE19878.vbs | text | |
MD5:7C0B3EF9968D114404D5CB1EF66EAE49 | SHA256:B765F9B09B6C3D040C96E9B09ECA1ED1A8BC3F980BA09BEABC0A8DF726181BBF | |||
| 1368 | cmd.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\mover.exe | executable | |
MD5:C1978E4080D1EC7E2EDF49D6C9710045 | SHA256:C9E2A7905501745C304FFC5A70B290DB40088D9DC10C47A98A953267468284A8 | |||
| 1008 | sapisvr.exe | C:\Users\admin\AppData\Roaming\Microsoft\Speech\Files\UserLexicons\SP_F66E5290272047C7990D4484C4517E39.dat | binary | |
MD5:04A5B620DA44BE1C3C31B55170259ECF | SHA256:70165566368F45051EA79B67C8757D507DFACC8A20C003C6B82C0DF1459ECDC9 | |||
| 1368 | cmd.exe | C:\Users\Public\Desktop\NOESCAPE20480.vbs | text | |
MD5:7C0B3EF9968D114404D5CB1EF66EAE49 | SHA256:B765F9B09B6C3D040C96E9B09ECA1ED1A8BC3F980BA09BEABC0A8DF726181BBF | |||
| 1368 | cmd.exe | C:\Users\Public\Desktop\NOESCAPE5314.vbs | text | |
MD5:7C0B3EF9968D114404D5CB1EF66EAE49 | SHA256:B765F9B09B6C3D040C96E9B09ECA1ED1A8BC3F980BA09BEABC0A8DF726181BBF | |||
| 1368 | cmd.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\MainWindow.exe | executable | |
MD5:03D8B31DB1ED1294334B872F756AD1A1 | SHA256:7E17DCAAFC07877E720B3FC0E666AC69E2DCE8E7458AE9B23902BCF5F8F2A40A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
15
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
292 | sipnotify.exe | HEAD | 200 | 23.207.104.5:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133756349793120000 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
1100 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1460 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
292 | sipnotify.exe | 23.207.104.5:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | JP | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |