| URL: | https://cloud2023-heap-393-partition.s3.ap-southeast-2.amazonaws.com/VVIOBSvwqEFd |
| Full analysis: | https://app.any.run/tasks/167a7daa-e359-44e4-bb09-e40562b915be |
| Verdict: | Malicious activity |
| Analysis date: | June 17, 2025, 18:05:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D5DF5A549DF8A31109541EB2C9AD66B6 |
| SHA1: | 521245CF1E24031AE7A644B79D7619B1A2E12F39 |
| SHA256: | 2D653D2B3B6F5E767764BD545944940815EFB57BCE1414BBD549BB733FA5DE21 |
| SSDEEP: | 3:N8ULBXLh1cWZnC2N2Q7Wtfsqn/n:2UVh1c2Cezq/n |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for external IP
- Reader_br_install.exe (PID: 5708)
- svchost.exe (PID: 2200)
- Reader_br_install.exe (PID: 4808)
- 8b4a73da.exe (PID: 9172)
- 8b4a73da.exe (PID: 8744)
- 8b4a73da.exe (PID: 4444)
- 8b4a73da.exe (PID: 8496)
- 8b4a73da.exe (PID: 8940)
- 8b4a73da.exe (PID: 8324)
- 8b4a73da.exe (PID: 9136)
- 8b4a73da.exe (PID: 9208)
- 8b4a73da.exe (PID: 7272)
- 8b4a73da.exe (PID: 3788)
Executable content was dropped or overwritten
- Reader_br_install.exe (PID: 5708)
- Reader_br_install.exe (PID: 4808)
Reads the date of Windows installation
- Reader_br_install.exe (PID: 5708)
Application launched itself
- Reader_br_install.exe (PID: 5708)
- 8b4a73da.exe (PID: 8744)
- 8b4a73da.exe (PID: 9172)
- 8b4a73da.exe (PID: 8496)
- 8b4a73da.exe (PID: 4444)
- 8b4a73da.exe (PID: 8940)
- 8b4a73da.exe (PID: 9136)
- 8b4a73da.exe (PID: 8324)
- 8b4a73da.exe (PID: 7272)
- 8b4a73da.exe (PID: 3788)
Reads Microsoft Outlook installation path
- Reader_br_install.exe (PID: 2132)
Reads security settings of Internet Explorer
- Reader_br_install.exe (PID: 5708)
- Reader_br_install.exe (PID: 2132)
There is functionality for taking screenshot (YARA)
- AcroCEF.exe (PID: 8112)
Starts itself from another location
- Reader_br_install.exe (PID: 4808)
Reads Internet Explorer settings
- Reader_br_install.exe (PID: 2132)
INFO
Application launched itself
- chrome.exe (PID: 3884)
- msedge.exe (PID: 2072)
- Acrobat.exe (PID: 6960)
- msedge.exe (PID: 4984)
- msedge.exe (PID: 2064)
- AcroCEF.exe (PID: 7288)
Checks supported languages
- Reader_br_install.exe (PID: 5708)
- Reader_br_install.exe (PID: 2132)
- Reader_br_install.exe (PID: 4808)
Reads product name
- Reader_br_install.exe (PID: 5708)
- Reader_br_install.exe (PID: 4808)
Reads the computer name
- Reader_br_install.exe (PID: 5708)
- Reader_br_install.exe (PID: 2132)
- Reader_br_install.exe (PID: 4808)
Reads Environment values
- Reader_br_install.exe (PID: 5708)
- Reader_br_install.exe (PID: 4808)
Executable content was dropped or overwritten
- chrome.exe (PID: 3884)
Create files in a temporary directory
- Reader_br_install.exe (PID: 5708)
- Reader_br_install.exe (PID: 4808)
- Reader_br_install.exe (PID: 2132)
Process checks computer location settings
- Reader_br_install.exe (PID: 5708)
Checks proxy server information
- Reader_br_install.exe (PID: 2132)
The sample compiled with english language support
- Reader_br_install.exe (PID: 4808)
Manual execution by a user
- msedge.exe (PID: 2064)
Reads the machine GUID from the registry
- Reader_br_install.exe (PID: 2132)
Creates files or folders in the user directory
- Reader_br_install.exe (PID: 2132)
Reads the software policy settings
- Reader_br_install.exe (PID: 2132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
228
Monitored processes
79
Malicious processes
4
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --always-read-main-dll --field-trial-handle=5332,i,4027356075075693166,10126627503688402287,262144 --variations-seed-version --mojo-platform-channel-handle=5268 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1100 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=4600,i,15960328038773383167,14829349200356227007,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4636 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1100 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --string-annotations --field-trial-handle=5816,i,15960328038773383167,14829349200356227007,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5828 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2464,i,4027356075075693166,10126627503688402287,262144 --variations-seed-version --mojo-platform-channel-handle=2456 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=5240,i,15960328038773383167,14829349200356227007,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5728 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2492,i,4027356075075693166,10126627503688402287,262144 --variations-seed-version --mojo-platform-channel-handle=2780 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1712 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x298,0x29c,0x2a0,0x28c,0x290,0x7ffc4544f208,0x7ffc4544f214,0x7ffc4544f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1944 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --disable-quic --flag-switches-end --do-not-de-elevate --single-argument https://get.adobe.com/reader/completion/adm/?exitcode=-1&type=install&preinstalled=1&workflow=64 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
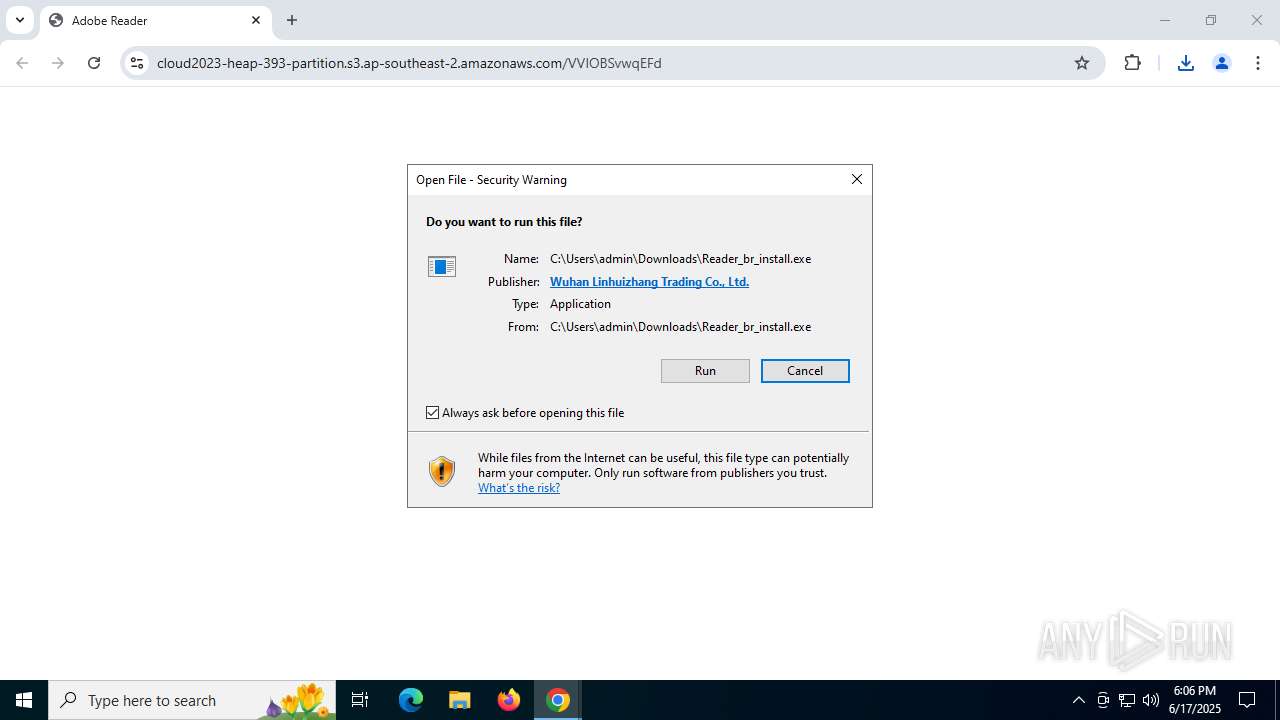
| 2072 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://get.adobe.com/reader/completion/adm/?exitcode=-1&type=install&preinstalled=1&workflow=64 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | Reader_br_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
38 723
Read events
38 555
Write events
154
Delete events
14
Modification events
| (PID) Process: | (3884) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3884) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3884) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3884) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3884) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3884) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3884) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2132) Reader_br_install.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2132) Reader_br_install.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2132) Reader_br_install.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
5
Suspicious files
310
Text files
101
Unknown types
56
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF176b1e.TMP | — | |
MD5:— | SHA256:— | |||
| 3884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF176b1e.TMP | — | |
MD5:— | SHA256:— | |||
| 3884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF176b3d.TMP | — | |
MD5:— | SHA256:— | |||
| 3884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF176b3d.TMP | — | |
MD5:— | SHA256:— | |||
| 3884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF176b3d.TMP | — | |
MD5:— | SHA256:— | |||
| 3884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF176b5c.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
91
TCP/UDP connections
169
DNS requests
160
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2596 | chrome.exe | GET | 200 | 142.250.186.78:80 | http://clients2.google.com/time/1/current?cup2key=8:WMo56bKQ-rH4E7MFnwCXmvumOhXS_FB5KaYlra-Rvso&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
5080 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2124 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2124 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5708 | Reader_br_install.exe | GET | 200 | 208.95.112.1:80 | http://208.95.112.1:80/json | unknown | — | — | unknown |
4808 | Reader_br_install.exe | GET | 200 | 208.95.112.1:80 | http://208.95.112.1:80/json | unknown | — | — | unknown |
3884 | chrome.exe | GET | 200 | 151.101.194.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
3884 | chrome.exe | GET | 200 | 151.101.194.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDGmDVsVnPDYjdUp7Mg%3D%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5528 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2596 | chrome.exe | 52.95.129.86:443 | cloud2023-heap-393-partition.s3.ap-southeast-2.amazonaws.com | AMAZON-02 | AU | shared |
2596 | chrome.exe | 142.250.186.74:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
2596 | chrome.exe | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2596 | chrome.exe | 142.250.186.78:80 | clients2.google.com | GOOGLE | US | whitelisted |
2596 | chrome.exe | 3.33.143.57:443 | rebrand.ly | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
cloud2023-heap-393-partition.s3.ap-southeast-2.amazonaws.com |
| shared |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
rebrand.ly |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2596 | chrome.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (rebrand .ly) |
2596 | chrome.exe | Misc activity | INFO [ANY.RUN] Possible short link service (rebrand .ly) |
2596 | chrome.exe | Misc activity | INFO [ANY.RUN] Possible short link service (rebrand .ly) |
2596 | chrome.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (rebrand .ly) |
2596 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2596 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2200 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2200 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
5708 | Reader_br_install.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
4808 | Reader_br_install.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |