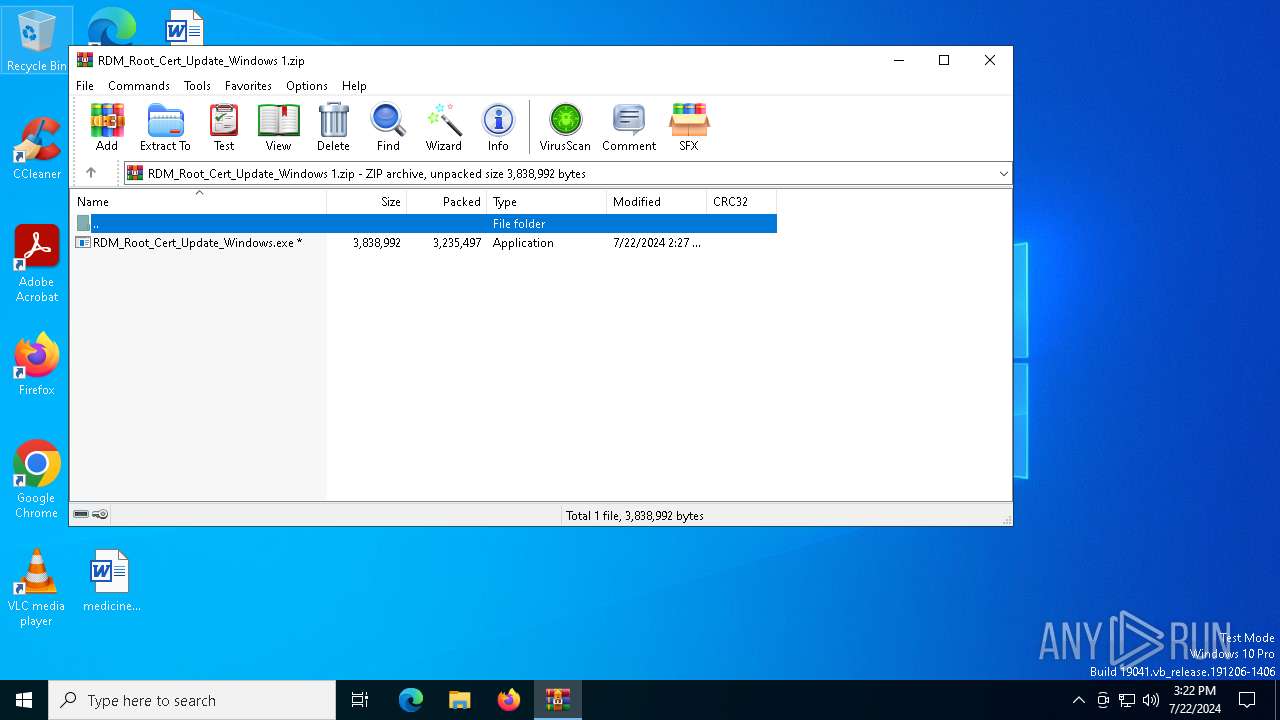
| File name: | RDM_Root_Cert_Update_Windows 1.zip |
| Full analysis: | https://app.any.run/tasks/47356c5e-78c5-4ca4-9e7e-1fa8a511b81d |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2024, 15:22:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 4712C264C63CDA22C8BA1BC7D2E202BC |
| SHA1: | 05460A4BA8FC1515FF858584C83955855D6446A6 |
| SHA256: | 2D46FF3CBAC2B089B1382DD24565E68BFDAC0F627231DAB1B6552A1B3C2B4132 |
| SSDEEP: | 98304:gi3H0pQbmWqNfPGo5XhVyB5MmZ87iA6COH7ZIfKE2vxFZZixOGk2l8/Zx24/6Ijy:ZsBzZuHqj |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3800)
- RDM_Root_Cert_Update_Windows.exe (PID: 7368)
- RDM_Root_Cert_Update_Windows.exe (PID: 5660)
- RDM_Root_Cert_Update_Windows.tmp (PID: 4888)
- RDM_ROOTCERTIFICATE.exe (PID: 3408)
- RDM_ROOTCERTIFICATE.tmp (PID: 5696)
Starts NET.EXE for service management
- RDM_Root_Cert_Update_Windows.tmp (PID: 4888)
- net.exe (PID: 8016)
- net.exe (PID: 7100)
- net.exe (PID: 6892)
- net.exe (PID: 2868)
SUSPICIOUS
Executable content was dropped or overwritten
- RDM_Root_Cert_Update_Windows.exe (PID: 7368)
- RDM_Root_Cert_Update_Windows.exe (PID: 5660)
- RDM_Root_Cert_Update_Windows.tmp (PID: 4888)
- RDM_ROOTCERTIFICATE.exe (PID: 3408)
- RDM_ROOTCERTIFICATE.tmp (PID: 5696)
Reads security settings of Internet Explorer
- RDM_Root_Cert_Update_Windows.tmp (PID: 4984)
Reads the date of Windows installation
- RDM_Root_Cert_Update_Windows.tmp (PID: 4984)
Reads the Windows owner or organization settings
- RDM_Root_Cert_Update_Windows.tmp (PID: 4888)
- RDM_ROOTCERTIFICATE.tmp (PID: 5696)
Application launched itself
- cmd.exe (PID: 4808)
- cmd.exe (PID: 6764)
Starts CMD.EXE for commands execution
- RDM_ROOTCERTIFICATE.tmp (PID: 5696)
- cmd.exe (PID: 6764)
- cmd.exe (PID: 4808)
Process drops legitimate windows executable
- RDM_ROOTCERTIFICATE.tmp (PID: 5696)
Executing commands from a ".bat" file
- RDM_ROOTCERTIFICATE.tmp (PID: 5696)
Starts a Microsoft application from unusual location
- certmgr.exe (PID: 7544)
- certmgr.exe (PID: 68)
- certmgr.exe (PID: 4308)
The executable file from the user directory is run by the CMD process
- certmgr.exe (PID: 68)
- certmgr.exe (PID: 7544)
Adds/modifies Windows certificates
- certmgr.exe (PID: 4308)
- certutil.exe (PID: 2220)
INFO
Checks supported languages
- RDM_Root_Cert_Update_Windows.exe (PID: 7368)
- RDM_Root_Cert_Update_Windows.tmp (PID: 4984)
- RDM_Root_Cert_Update_Windows.exe (PID: 5660)
- RDM_Root_Cert_Update_Windows.tmp (PID: 4888)
- RDM_ROOTCERTIFICATE.tmp (PID: 5696)
- RDM_ROOTCERTIFICATE.exe (PID: 3408)
- certmgr.exe (PID: 7544)
- certmgr.exe (PID: 4308)
- certmgr.exe (PID: 68)
Create files in a temporary directory
- RDM_Root_Cert_Update_Windows.exe (PID: 7368)
- RDM_Root_Cert_Update_Windows.exe (PID: 5660)
- RDM_Root_Cert_Update_Windows.tmp (PID: 4888)
- RDM_ROOTCERTIFICATE.exe (PID: 3408)
- RDM_ROOTCERTIFICATE.tmp (PID: 5696)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3800)
Manual execution by a user
- RDM_Root_Cert_Update_Windows.exe (PID: 7368)
Reads the computer name
- RDM_Root_Cert_Update_Windows.tmp (PID: 4984)
- RDM_Root_Cert_Update_Windows.tmp (PID: 4888)
- RDM_ROOTCERTIFICATE.tmp (PID: 5696)
Process checks computer location settings
- RDM_Root_Cert_Update_Windows.tmp (PID: 4984)
Creates files in the program directory
- RDM_ROOTCERTIFICATE.tmp (PID: 5696)
- RDM_Root_Cert_Update_Windows.tmp (PID: 4888)
- certutil.exe (PID: 2220)
Reads the machine GUID from the registry
- certmgr.exe (PID: 4308)
Reads the software policy settings
- certutil.exe (PID: 2220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
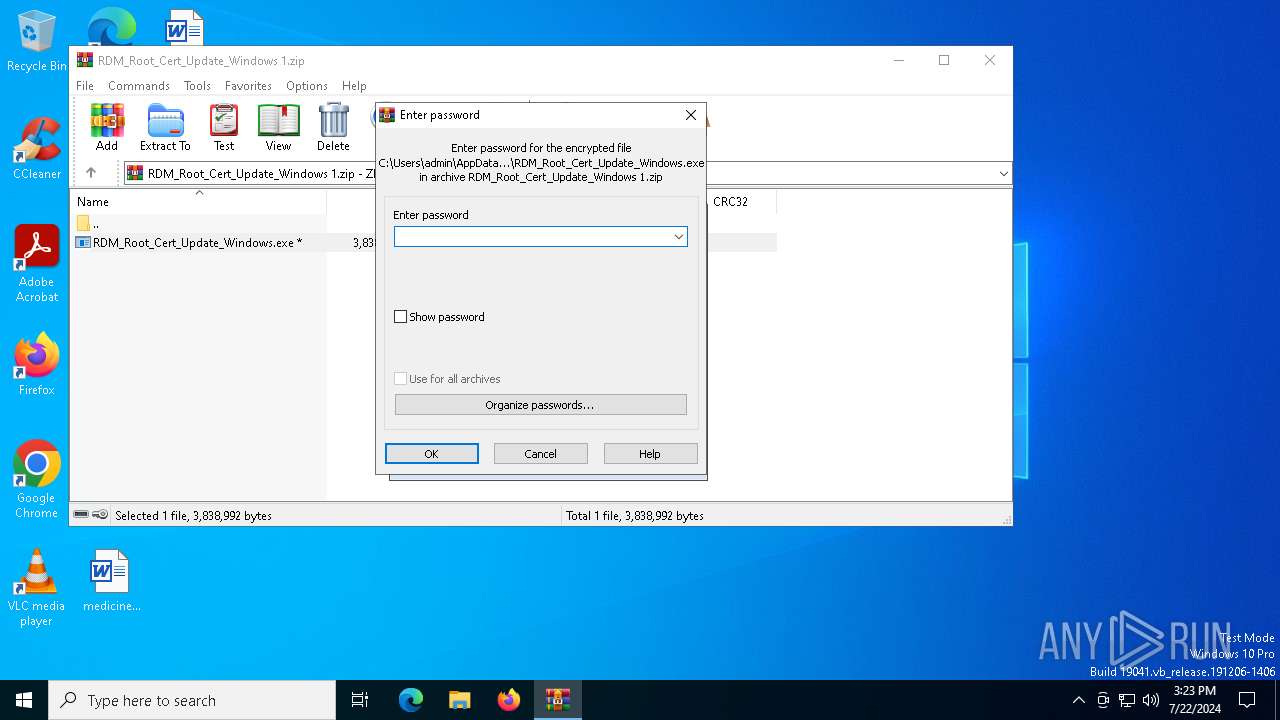
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:07:22 10:27:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 3235497 |
| ZipUncompressedSize: | 3838992 |
| ZipFileName: | RDM_Root_Cert_Update_Windows.exe |
Total processes
172
Monitored processes
34
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | CertMgr.exe -del -c -n "RDM Device Root" -s -r localMachine Root | C:\Users\admin\AppData\Local\Temp\is-JMN6P.tmp\RdmCert\certmgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: ECM Certificate Manager Exit code: 4294967295 Version: 5.131.1863.1 Modules
| |||||||||||||||
| 684 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo 1 " | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1320 | certutil.exe -A -n "RDM_Device" -t "TCu,TCu,TCu" -d "C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\i17fj4h8.default\." -i "C:\Users\admin\AppData\Local\Temp\is-JMN6P.tmp\RdmCert\RDM_RootCA.pem" | C:\Windows\SysWOW64\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2220 | "C:\WINDOWS\system32/certutil.exe" –f –p rdm736 –importpfx "C:\Users\admin\AppData\Local\Temp\is-JMN6P.tmp\RdmCert\rdm.pfx" | C:\Windows\SysWOW64\certutil.exe | — | RDM_ROOTCERTIFICATE.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2276 | C:\WINDOWS\system32\net1 start "Embedthis Rdmappweb" | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2360 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2868 | "C:\WINDOWS\system32\net.exe" start "RDMAppweb" | C:\Windows\SysWOW64\net.exe | — | RDM_Root_Cert_Update_Windows.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3408 | "C:\Users\admin\AppData\Local\Temp\is-GEG8I.tmp\RDM_ROOTCERTIFICATE.exe" /VERYSILENT | C:\Users\admin\AppData\Local\Temp\is-GEG8I.tmp\RDM_ROOTCERTIFICATE.exe | RDM_Root_Cert_Update_Windows.tmp | ||||||||||||
User: admin Company: RDM Corporation Integrity Level: HIGH Description: RDM ROOT CERTIFICATE Setup Exit code: 0 Version: 2.0.0.3 Modules
| |||||||||||||||
| 3724 | C:\WINDOWS\system32\cmd.exe /c dir /B "C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\*.default*" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 922
Read events
18 842
Write events
62
Delete events
18
Modification events
| (PID) Process: | (3800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RDM_Root_Cert_Update_Windows 1.zip | |||
| (PID) Process: | (3800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4888) RDM_Root_Cert_Update_Windows.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 181300002B53D8124BDCDA01 | |||
Executable files
34
Suspicious files
4
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4888 | RDM_Root_Cert_Update_Windows.tmp | C:\Users\admin\AppData\Local\Temp\is-GEG8I.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4888 | RDM_Root_Cert_Update_Windows.tmp | C:\Users\admin\AppData\Local\Temp\is-GEG8I.tmp\RDM_ROOTCERTIFICATE.exe | executable | |
MD5:5DAEC5D62A1B06418E5EAE25B7857748 | SHA256:9F395107A54B5393D98B7AA5D4A039D32BE780E691CACF75EF7D4CE58D074D83 | |||
| 7368 | RDM_Root_Cert_Update_Windows.exe | C:\Users\admin\AppData\Local\Temp\is-P4KTT.tmp\RDM_Root_Cert_Update_Windows.tmp | executable | |
MD5:A5388235BBD3513D95A2A5C172A55680 | SHA256:109DFA3633727AEE046973A9D59DFD493C4F4EDFA50BCBCC37999C4BF020550F | |||
| 5696 | RDM_ROOTCERTIFICATE.tmp | C:\Users\admin\AppData\Local\Temp\is-JMN6P.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4888 | RDM_Root_Cert_Update_Windows.tmp | C:\Users\admin\AppData\Local\Temp\is-GEG8I.tmp\is-NIJBM.tmp | executable | |
MD5:5DAEC5D62A1B06418E5EAE25B7857748 | SHA256:9F395107A54B5393D98B7AA5D4A039D32BE780E691CACF75EF7D4CE58D074D83 | |||
| 3800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3800.9416\RDM_Root_Cert_Update_Windows.exe | executable | |
MD5:D4B2995D38DA119E5B0DB2CB90778224 | SHA256:05A6215FBF82C755B73DCFA297F229BF5B88C879B4A7A2EDF680EBD97A4580AD | |||
| 5696 | RDM_ROOTCERTIFICATE.tmp | C:\Users\admin\AppData\Local\Temp\is-JMN6P.tmp\RdmCert\freebl3.dll | executable | |
MD5:269BEB631B580C6D54DB45B5573B1DE5 | SHA256:FFC7558A61A4E6546CF095BDEABEA19F05247A0DAA02DCA20EA3605E7FC62C77 | |||
| 5696 | RDM_ROOTCERTIFICATE.tmp | C:\Users\admin\AppData\Local\Temp\is-JMN6P.tmp\RdmCert\libnspr4.dll | executable | |
MD5:6E84AF2875700285309DD29294365C6A | SHA256:1C158E680749E642E55F721F60A71314E26E03E785CD92E560BF650B83C4C3C8 | |||
| 5696 | RDM_ROOTCERTIFICATE.tmp | C:\Users\admin\AppData\Local\Temp\is-JMN6P.tmp\RdmCert\is-UQ0II.tmp | executable | |
MD5:5D077A0CDD077C014EEDB768FEB249BA | SHA256:8A830C48C4D78159DD80F4DAD81C0BEBBF9314710026B1A2EF0FFDDDCB24B83D | |||
| 5696 | RDM_ROOTCERTIFICATE.tmp | C:\Users\admin\AppData\Local\Temp\is-JMN6P.tmp\RdmCert\is-608GP.tmp | text | |
MD5:E8C0E44371C4EDCC8908173BB91CA75C | SHA256:30AA7A6E165232DCA4B1B3ADF8C74BEA54A29686F8802C6DE92075EF53B5C1AA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
31
DNS requests
10
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7856 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4716 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.115.3.253:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2760 | svchost.exe | 40.115.3.253:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2992 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7856 | svchost.exe | 4.209.33.156:443 | licensing.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |