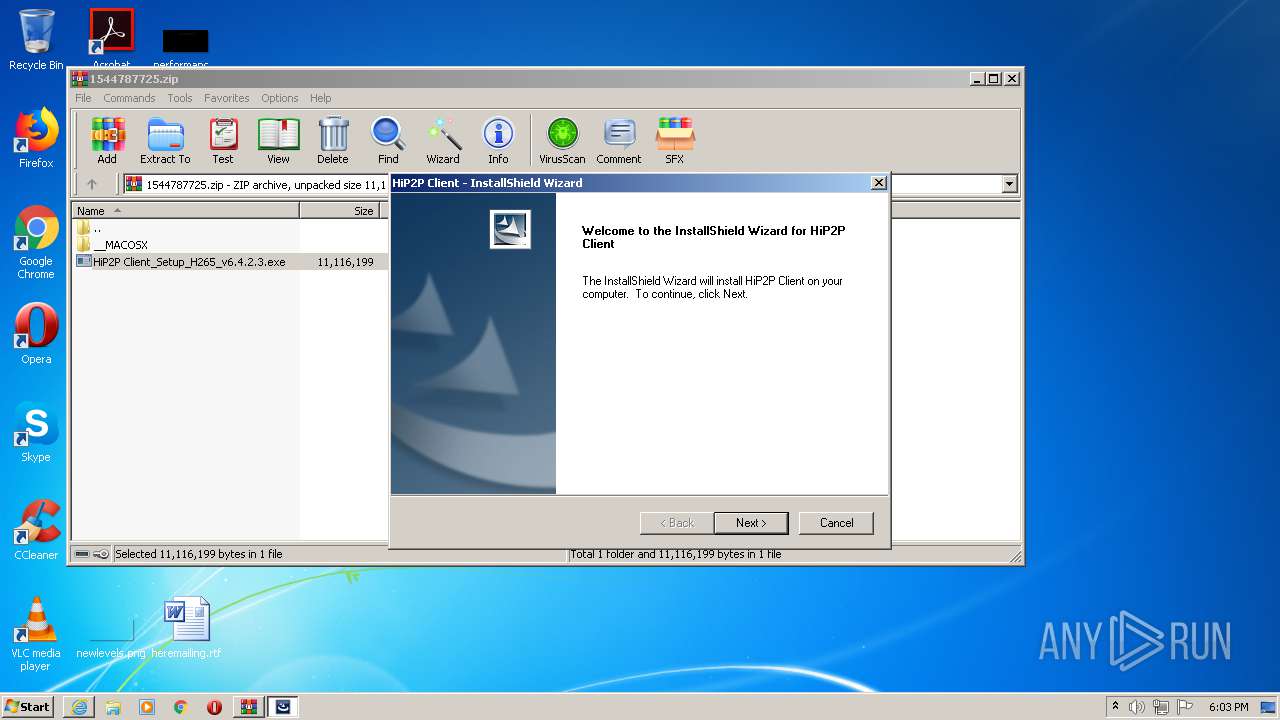
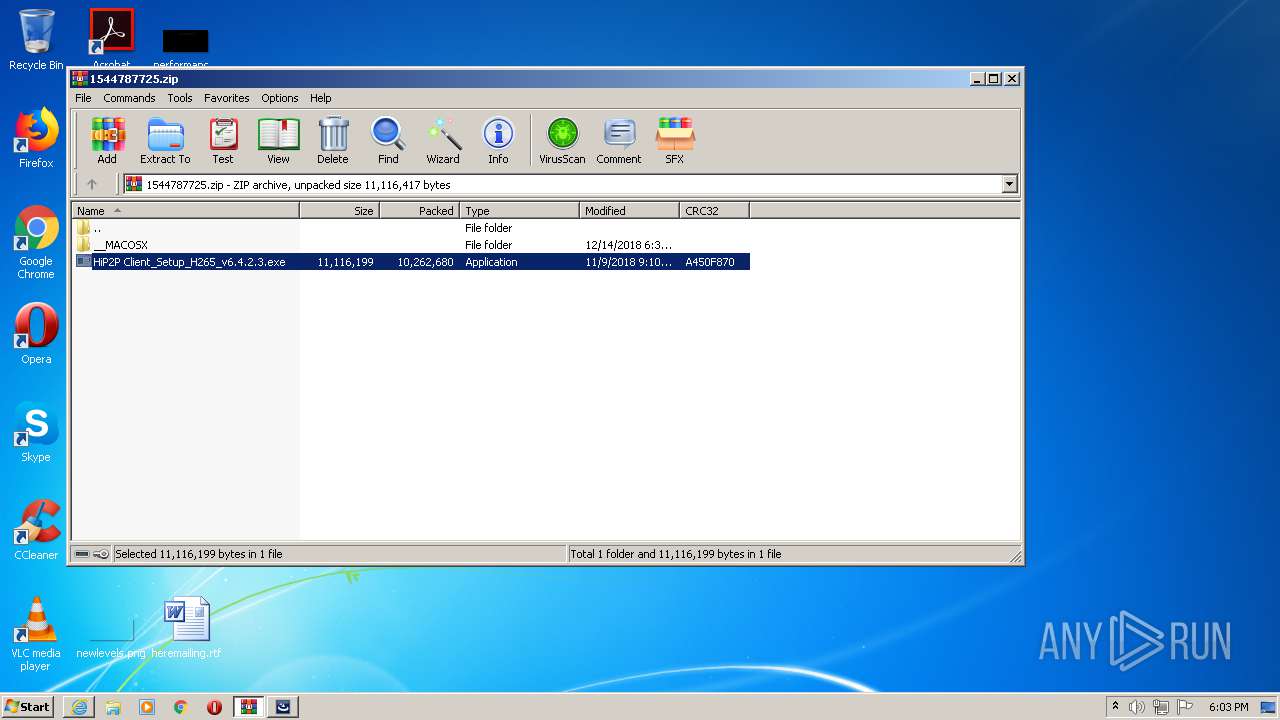
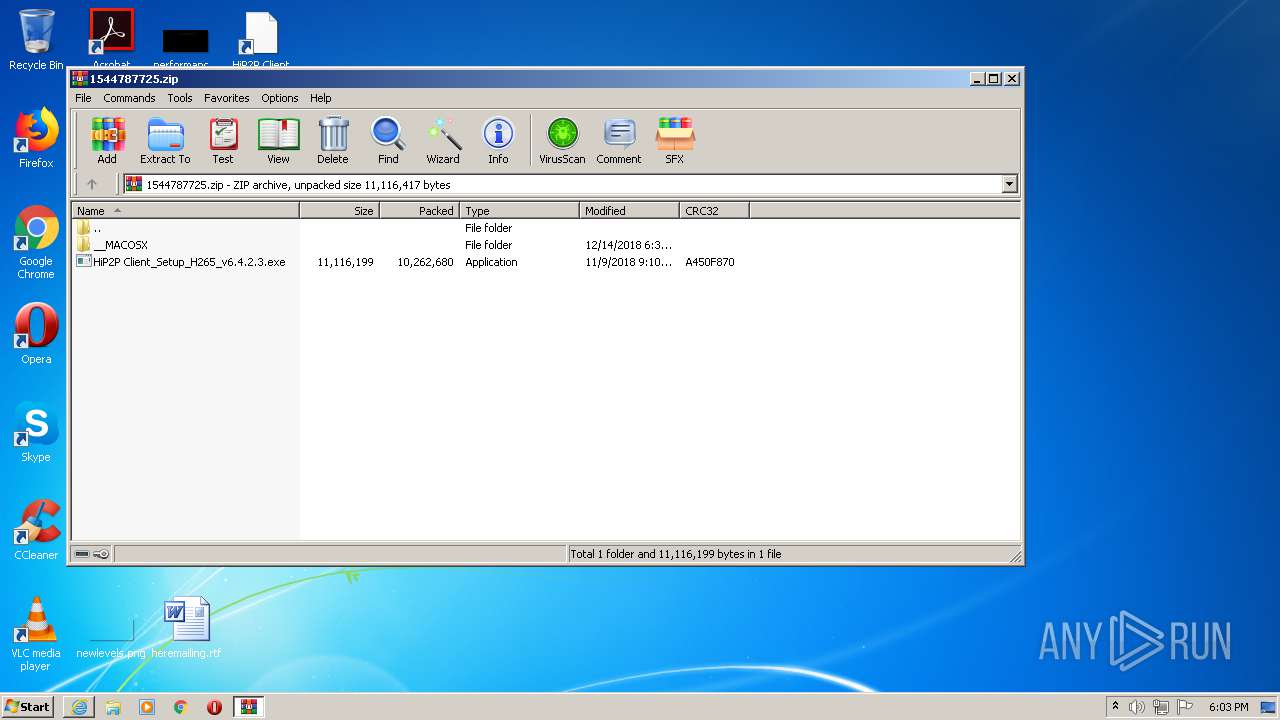
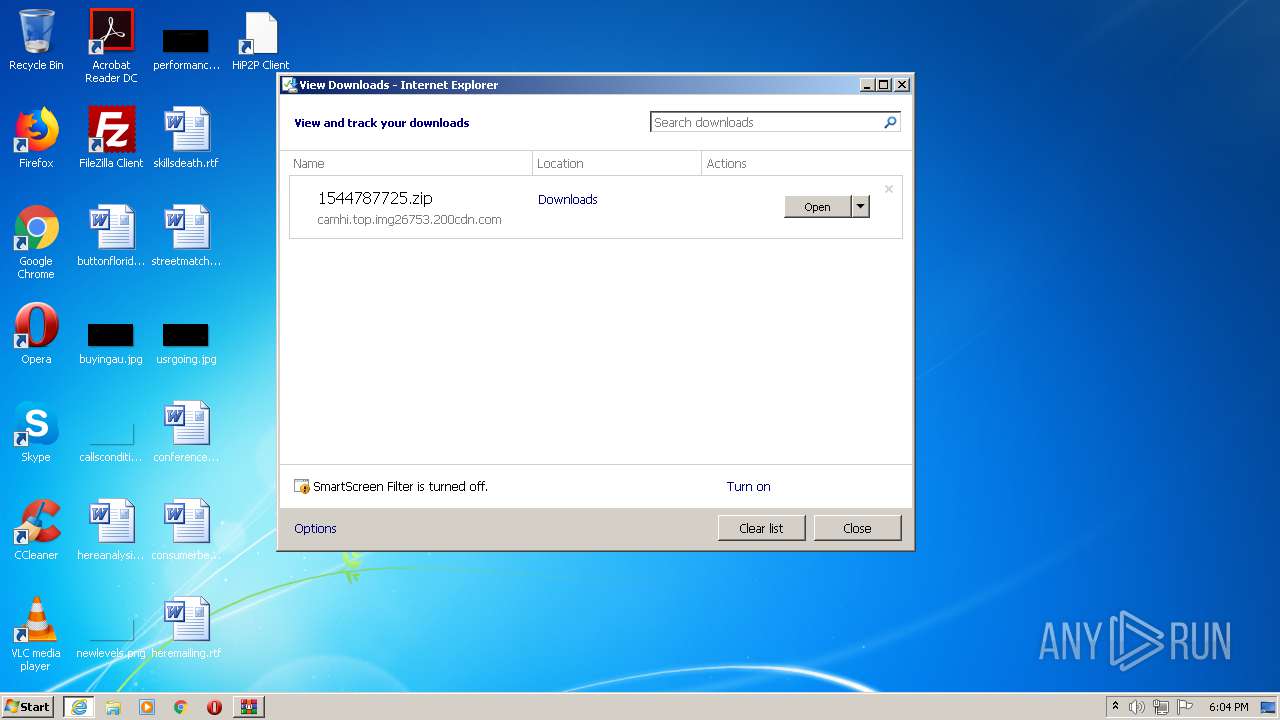
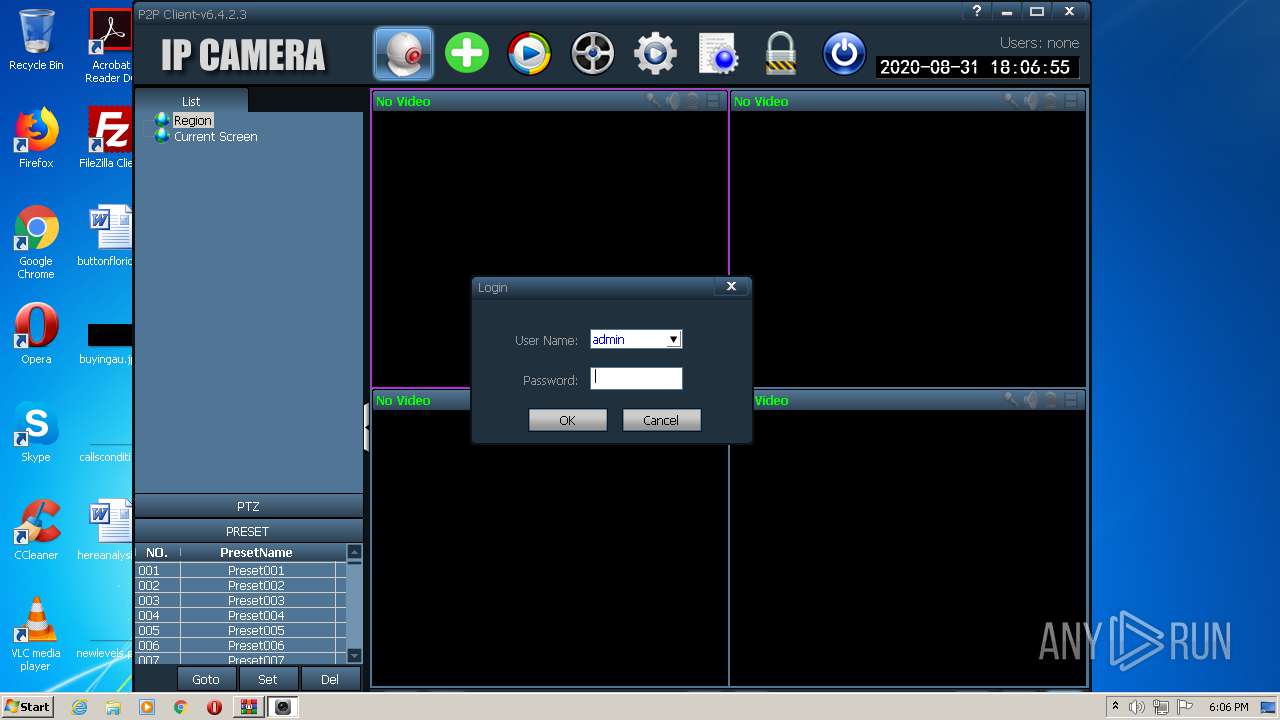
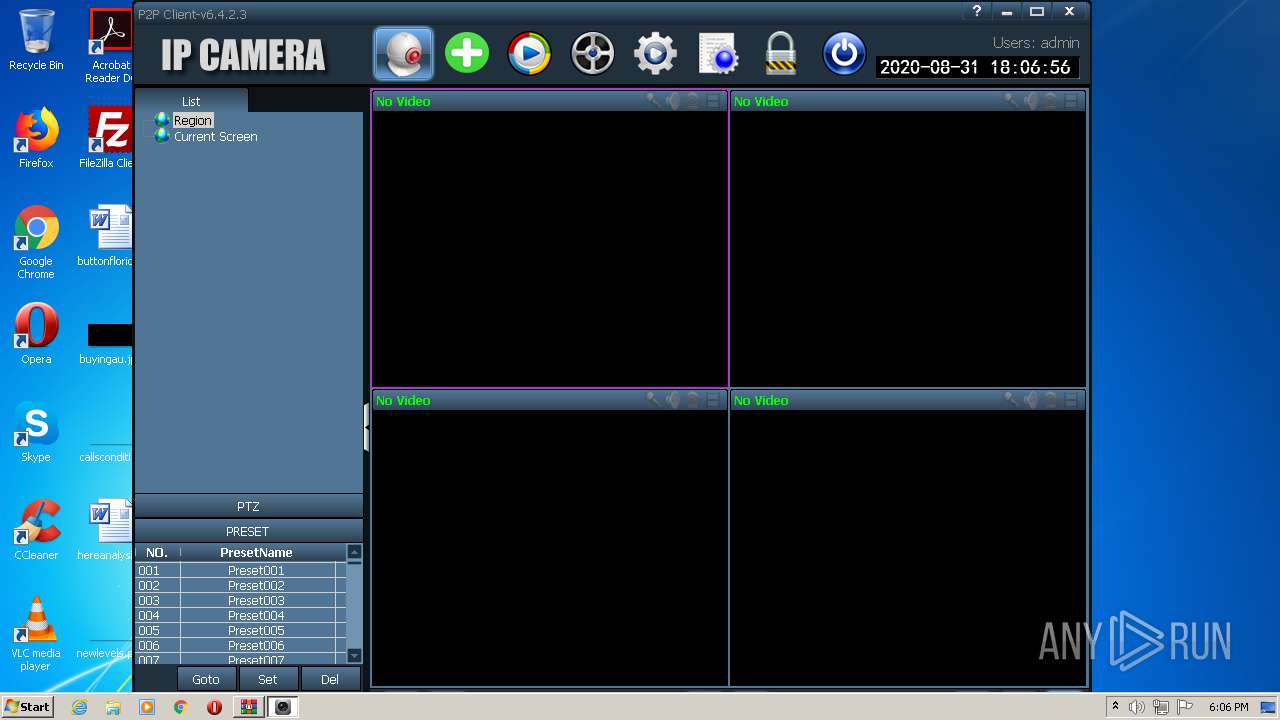
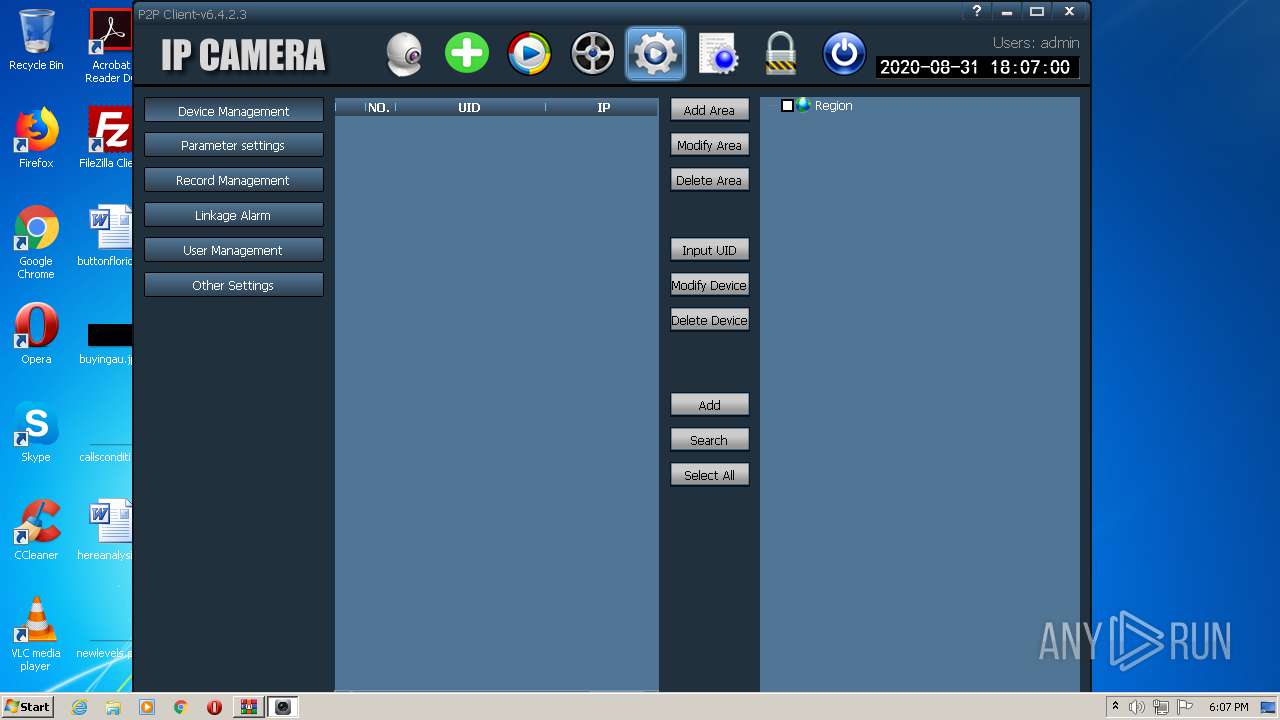
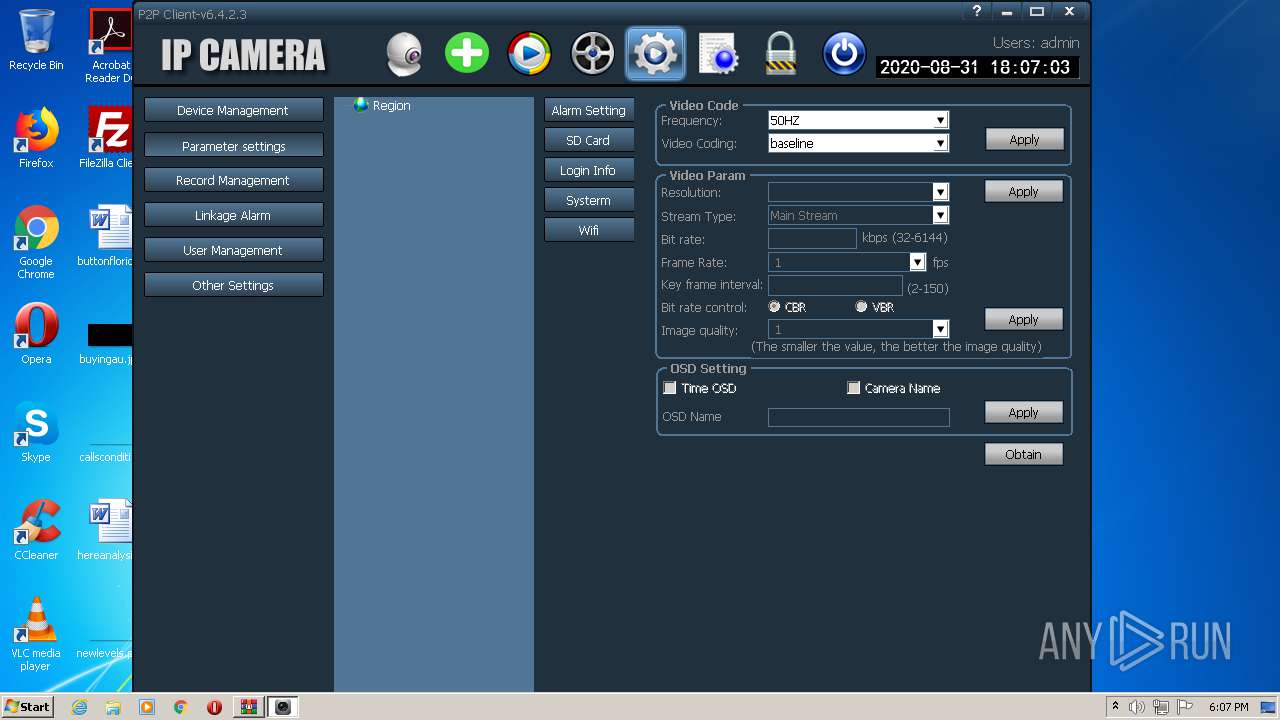
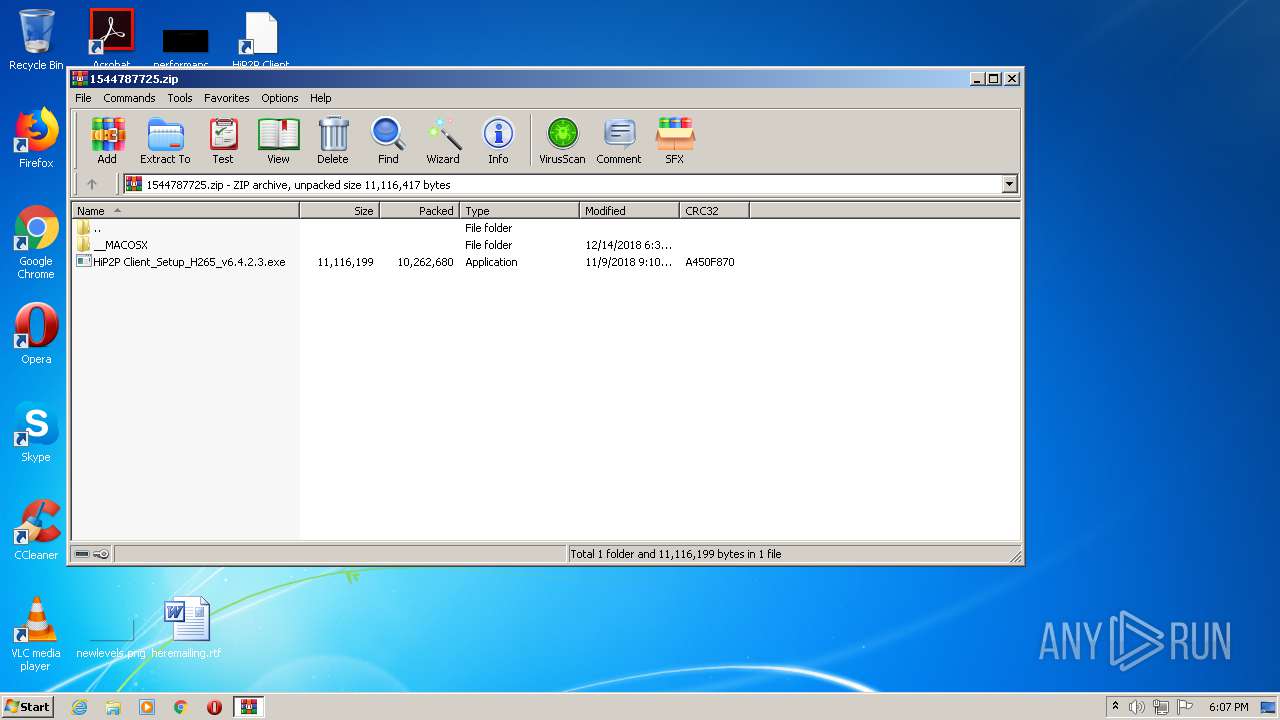
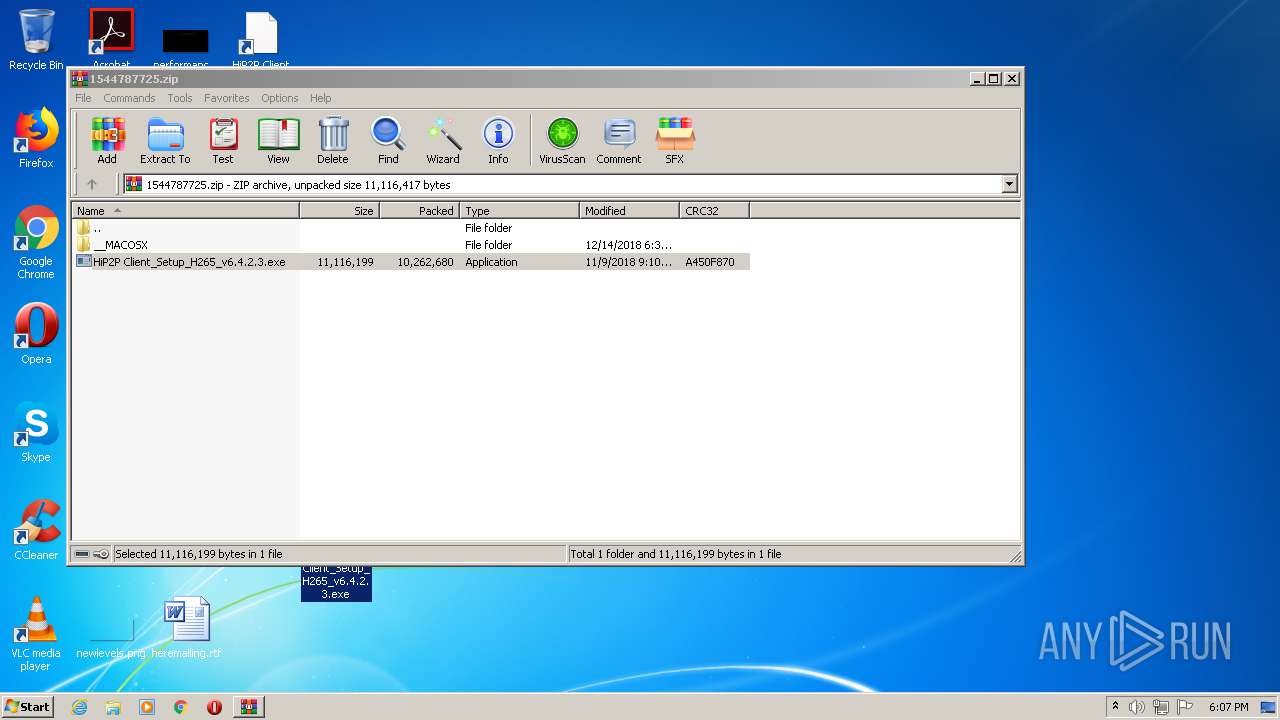
| URL: | http://camhi.top/uploads/soft/20181214/1544787725.zip |
| Full analysis: | https://app.any.run/tasks/2ed0ddf1-a555-4c4d-8bfc-01202c713c3f |
| Verdict: | Malicious activity |
| Analysis date: | August 31, 2020, 17:02:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3936BDF60DEE22A0259FCEF97941305C |
| SHA1: | 8DEC497202E2AAC9FAC0C1E7E429CBA2E7498240 |
| SHA256: | 2D3DAFA2EAF3ACBBD08D4F0FF4E550DCB6088518B16062BFAE6CB4727C751DF5 |
| SSDEEP: | 3:N1KdE5LRKVPNYX+d2RRQufUn:CG5LRKVP6S2RQQUn |
MALICIOUS
Application was dropped or rewritten from another process
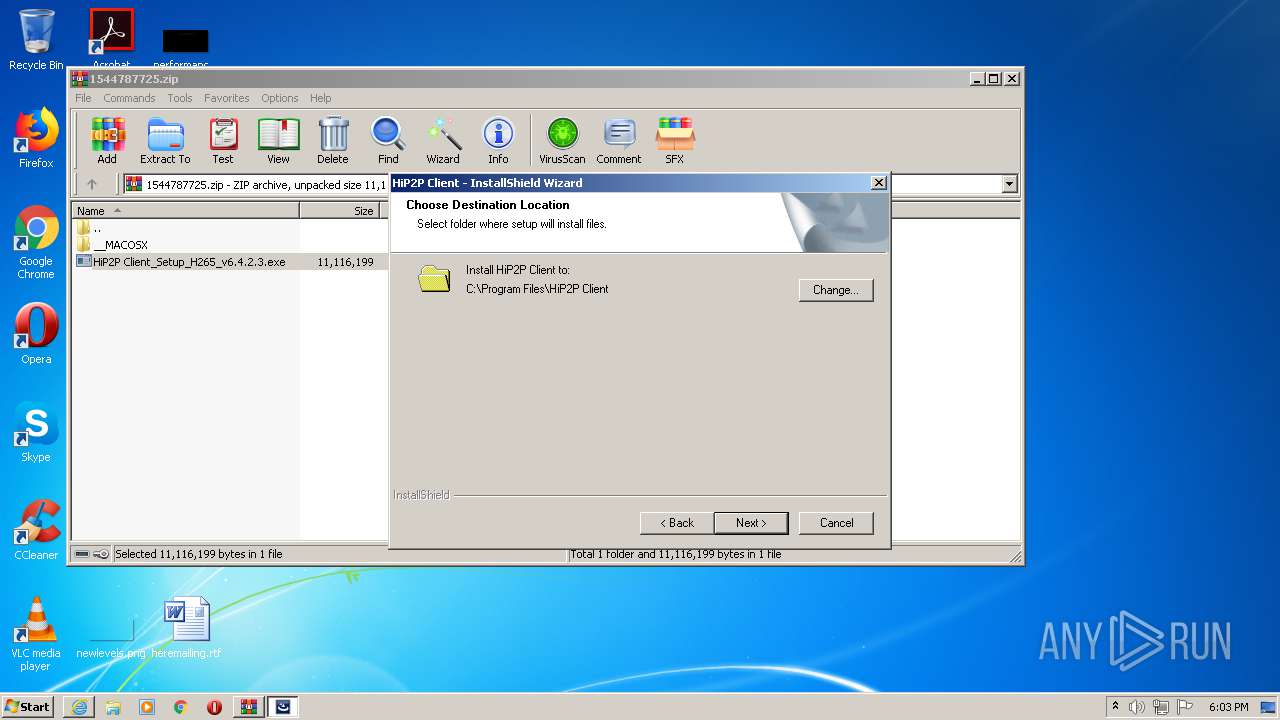
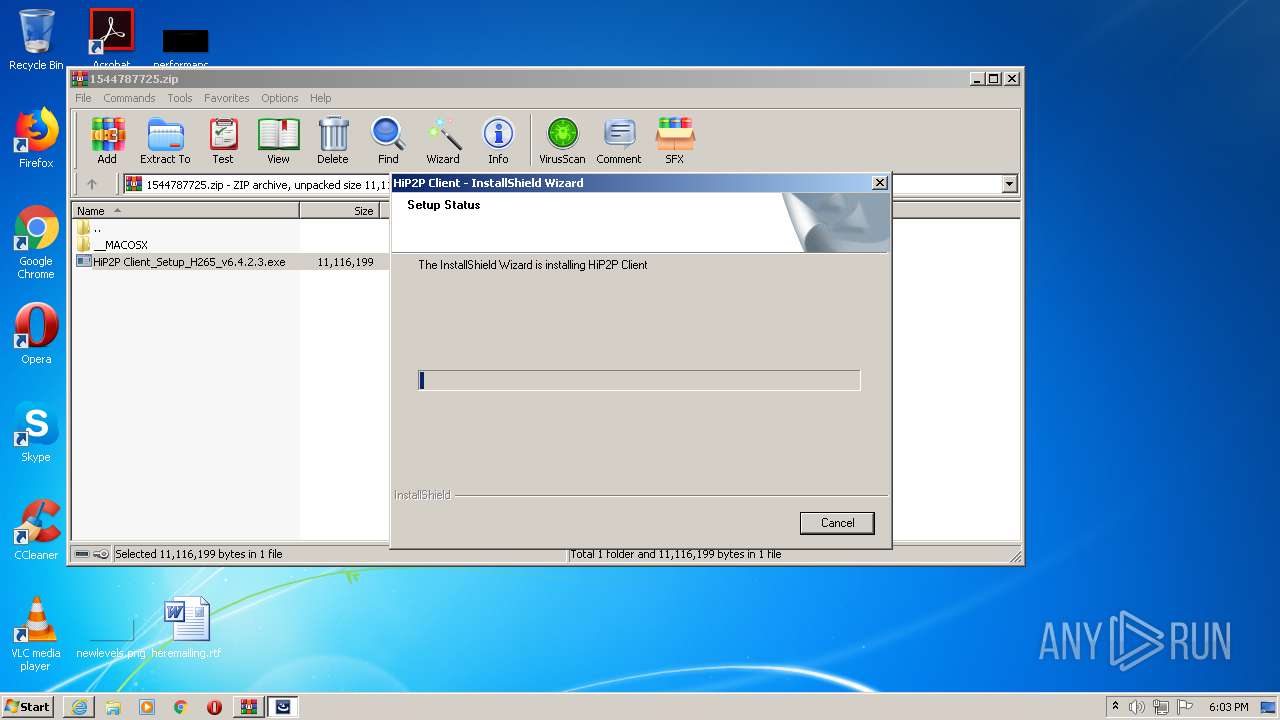
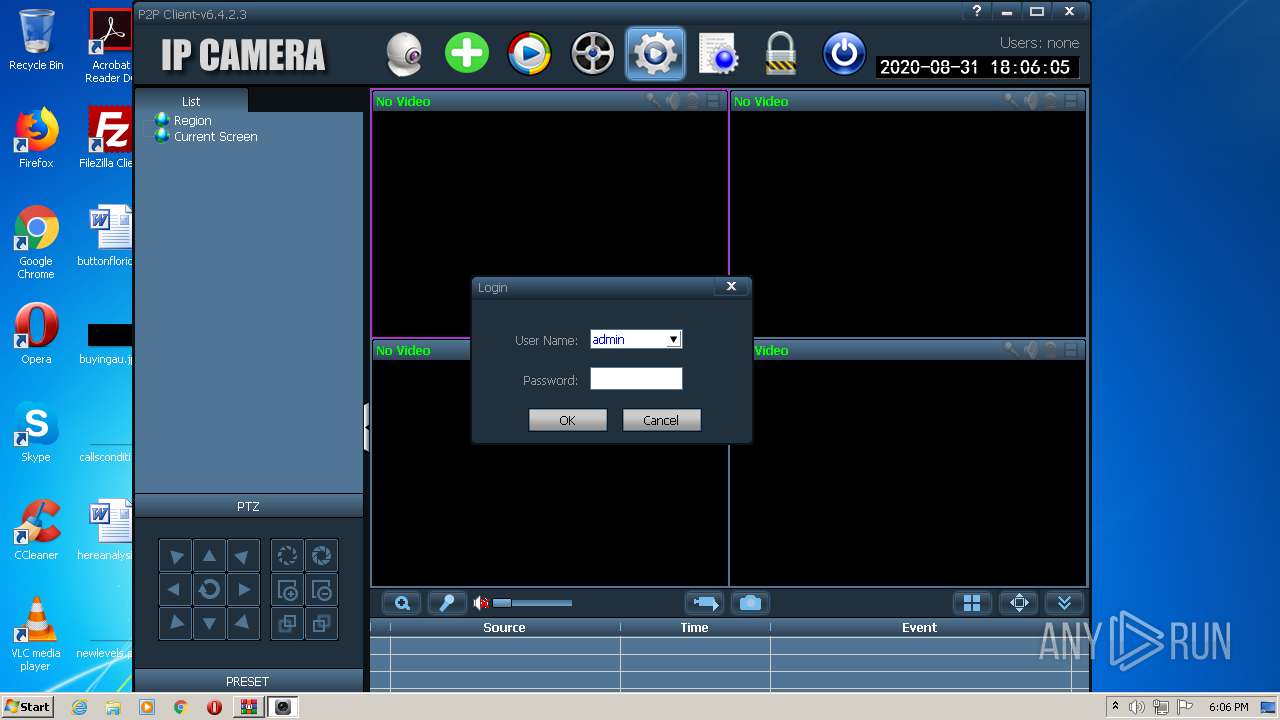
- HiP2P Client_Setup_H265_v6.4.2.3.exe (PID: 1332)
- HiP2P Client_Setup_H265_v6.4.2.3.exe (PID: 3608)
- P2PClient.exe (PID: 2452)
- P2PClient.exe (PID: 4056)
Loads dropped or rewritten executable
- HiP2P Client_Setup_H265_v6.4.2.3.exe (PID: 3608)
- P2PClient.exe (PID: 4056)
- P2PClient.exe (PID: 2452)
SUSPICIOUS
Executable content was dropped or overwritten
- HiP2P Client_Setup_H265_v6.4.2.3.exe (PID: 3608)
- WinRAR.exe (PID: 4088)
Modifies the open verb of a shell class
- HiP2P Client_Setup_H265_v6.4.2.3.exe (PID: 3608)
Searches for installed software
- HiP2P Client_Setup_H265_v6.4.2.3.exe (PID: 3608)
Creates a software uninstall entry
- HiP2P Client_Setup_H265_v6.4.2.3.exe (PID: 3608)
Executed via COM
- DllHost.exe (PID: 1116)
Creates files in the program directory
- HiP2P Client_Setup_H265_v6.4.2.3.exe (PID: 3608)
- P2PClient.exe (PID: 4056)
- P2PClient.exe (PID: 2452)
Reads internet explorer settings
- hh.exe (PID: 2140)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2068)
- iexplore.exe (PID: 2320)
Changes internet zones settings
- iexplore.exe (PID: 2068)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2068)
Application launched itself
- iexplore.exe (PID: 2068)
Changes settings of System certificates
- iexplore.exe (PID: 2068)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2068)
Reads settings of System Certificates
- iexplore.exe (PID: 2068)
Creates files in the user directory
- iexplore.exe (PID: 2068)
Manual execution by user
- P2PClient.exe (PID: 2452)
- P2PClient.exe (PID: 4056)
Dropped object may contain Bitcoin addresses
- HiP2P Client_Setup_H265_v6.4.2.3.exe (PID: 3608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
57
Monitored processes
9
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1116 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1332 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4088.23727\HiP2P Client_Setup_H265_v6.4.2.3.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4088.23727\HiP2P Client_Setup_H265_v6.4.2.3.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Macrovision Corporation Integrity Level: MEDIUM Description: Setup.exe Exit code: 3221226540 Version: 14.0.162 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Internet Explorer\iexplore.exe" http://camhi.top/uploads/soft/20181214/1544787725.zip | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2140 | "C:\Windows\hh.exe" C:\Program Files\HiP2P Client\helpEn.chm | C:\Windows\hh.exe | — | P2PClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 3221225547 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2320 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2068 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
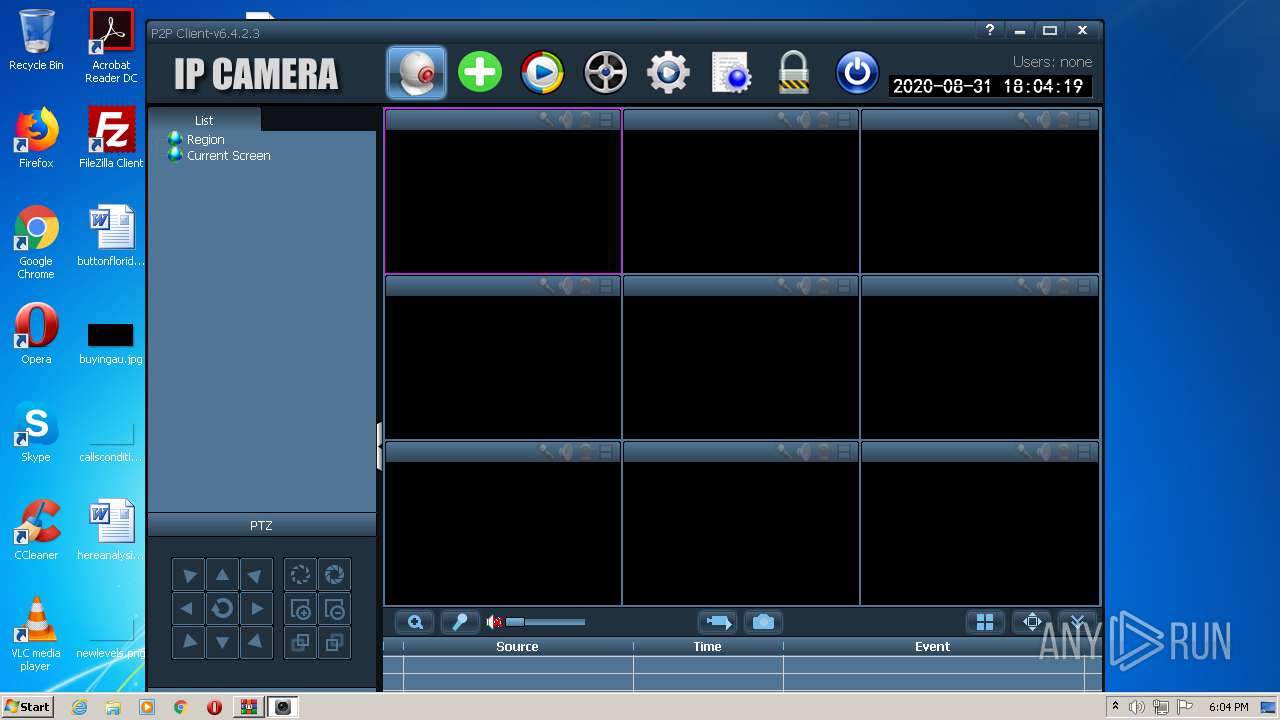
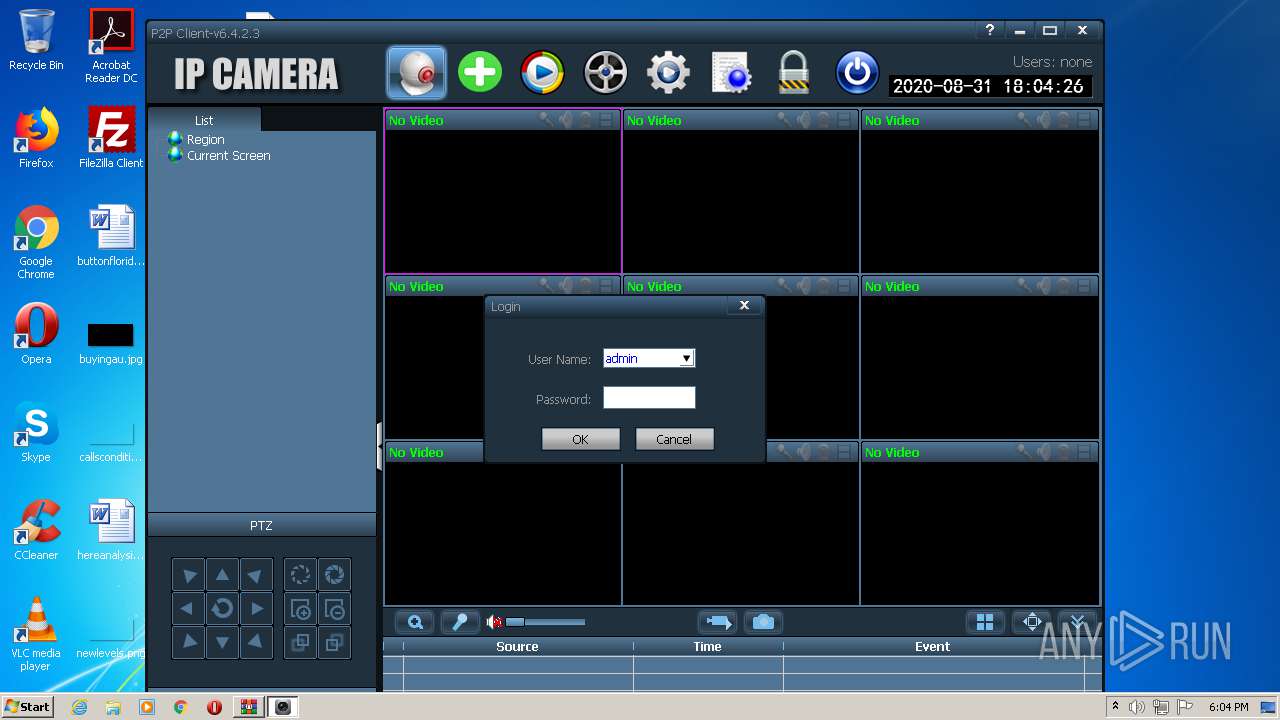
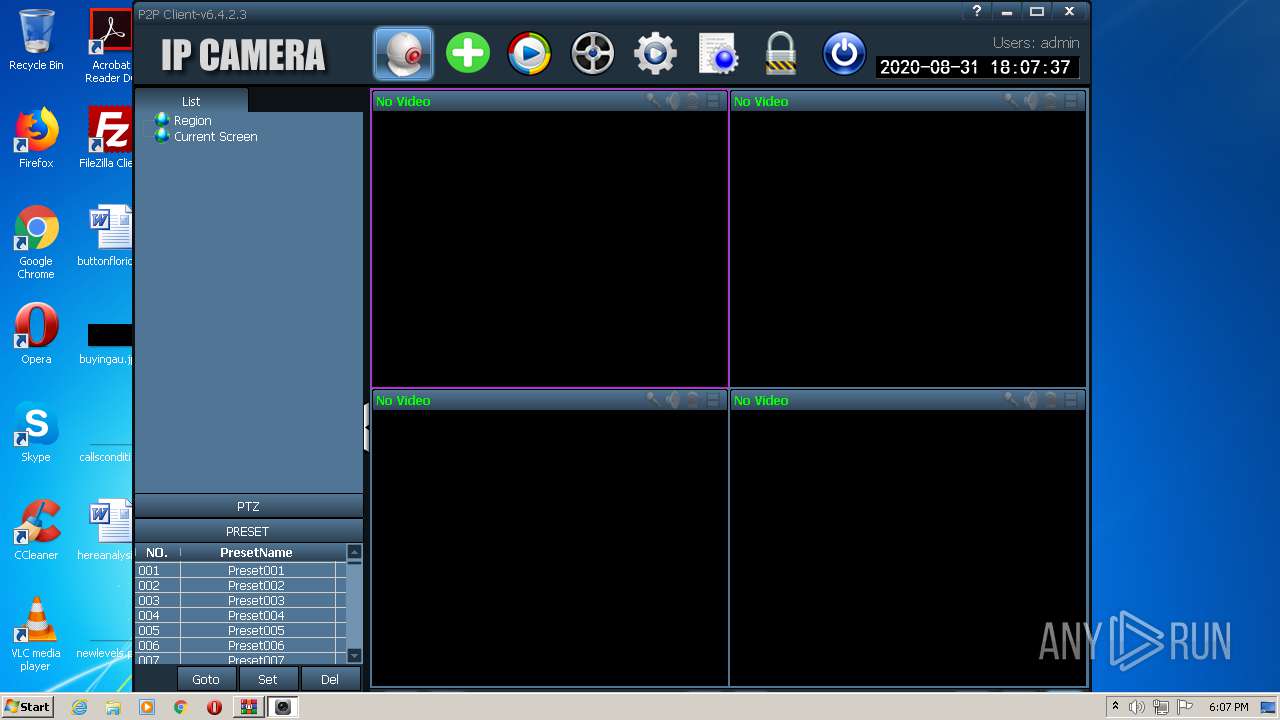
| 2452 | "C:\Program Files\HiP2P Client\P2PClient.exe" | C:\Program Files\HiP2P Client\P2PClient.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: P2P Client Exit code: 0 Version: 3, 0, 3, 0 Modules
| |||||||||||||||
| 3608 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4088.23727\HiP2P Client_Setup_H265_v6.4.2.3.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4088.23727\HiP2P Client_Setup_H265_v6.4.2.3.exe | WinRAR.exe | ||||||||||||
User: admin Company: Macrovision Corporation Integrity Level: HIGH Description: Setup.exe Exit code: 0 Version: 14.0.162 Modules
| |||||||||||||||
| 4056 | "C:\Program Files\HiP2P Client\P2PClient.exe" | C:\Program Files\HiP2P Client\P2PClient.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: P2P Client Exit code: 0 Version: 3, 0, 3, 0 Modules
| |||||||||||||||
| 4088 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\1544787725.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 921
Read events
1 759
Write events
156
Delete events
6
Modification events
| (PID) Process: | (2068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2761981664 | |||
| (PID) Process: | (2068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30834616 | |||
| (PID) Process: | (2068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
29
Suspicious files
26
Text files
33
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\1544787725[1].zip | — | |
MD5:— | SHA256:— | |||
| 2068 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF8DFC6C527EBE960C.TMP | — | |
MD5:— | SHA256:— | |||
| 2068 | iexplore.exe | C:\Users\admin\Downloads\1544787725.zip.57ny71r.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 2068 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab4EE0.tmp | — | |
MD5:— | SHA256:— | |||
| 2068 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar4EE1.tmp | — | |
MD5:— | SHA256:— | |||
| 3608 | HiP2P Client_Setup_H265_v6.4.2.3.exe | C:\Users\admin\AppData\Local\Temp\{4626692A-D6FD-44C4-A3F2-36D37CFC244F}\{2F3762A1-58CA-43A8-9854-88BCC34C6D2F}\setu5161.rra | — | |
MD5:— | SHA256:— | |||
| 2068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{D05AB747-EBAB-11EA-90BC-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 3608 | HiP2P Client_Setup_H265_v6.4.2.3.exe | C:\Users\admin\AppData\Local\Temp\{4626692A-D6FD-44C4-A3F2-36D37CFC244F}\{2F3762A1-58CA-43A8-9854-88BCC34C6D2F}\lice5161.rra | — | |
MD5:— | SHA256:— | |||
| 3608 | HiP2P Client_Setup_H265_v6.4.2.3.exe | C:\Users\admin\AppData\Local\Temp\{C9485C6B-A5A8-451F-8AD4-AEF179B057A5}\Disk1\data1.cab | compressed | |
MD5:— | SHA256:— | |||
| 3608 | HiP2P Client_Setup_H265_v6.4.2.3.exe | C:\Users\admin\AppData\Local\Temp\{4626692A-D6FD-44C4-A3F2-36D37CFC244F}\{2F3762A1-58CA-43A8-9854-88BCC34C6D2F}\_ISU5161.rra | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
20
DNS requests
16
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2320 | iexplore.exe | GET | 200 | 124.173.109.73:9898 | http://camhi.top.img26753.200cdn.com:9898/uploads/soft/20181214/1544787725.zip | CN | compressed | 9.79 Mb | unknown |
2320 | iexplore.exe | GET | 302 | 113.10.147.176:80 | http://camhi.top/uploads/soft/20181214/1544787725.zip | HK | html | 154 b | suspicious |
2068 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2068 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2068 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2068 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2068 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 123.57.136.155:32100 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
— | — | 123.56.143.156:32100 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
2452 | P2PClient.exe | 52.221.17.159:32100 | — | Amazon.com, Inc. | SG | unknown |
4056 | P2PClient.exe | 52.221.17.159:32100 | — | Amazon.com, Inc. | SG | unknown |
— | — | 52.8.0.180:32100 | — | Amazon.com, Inc. | US | unknown |
2320 | iexplore.exe | 113.10.147.176:80 | camhi.top | AS number for New World Telephone Ltd. | HK | suspicious |
2320 | iexplore.exe | 124.173.109.73:9898 | camhi.top.img26753.200cdn.com | CHINANET Guangdong province network | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
camhi.top |
| suspicious |
camhi.top.img26753.200cdn.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1044 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2320 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |