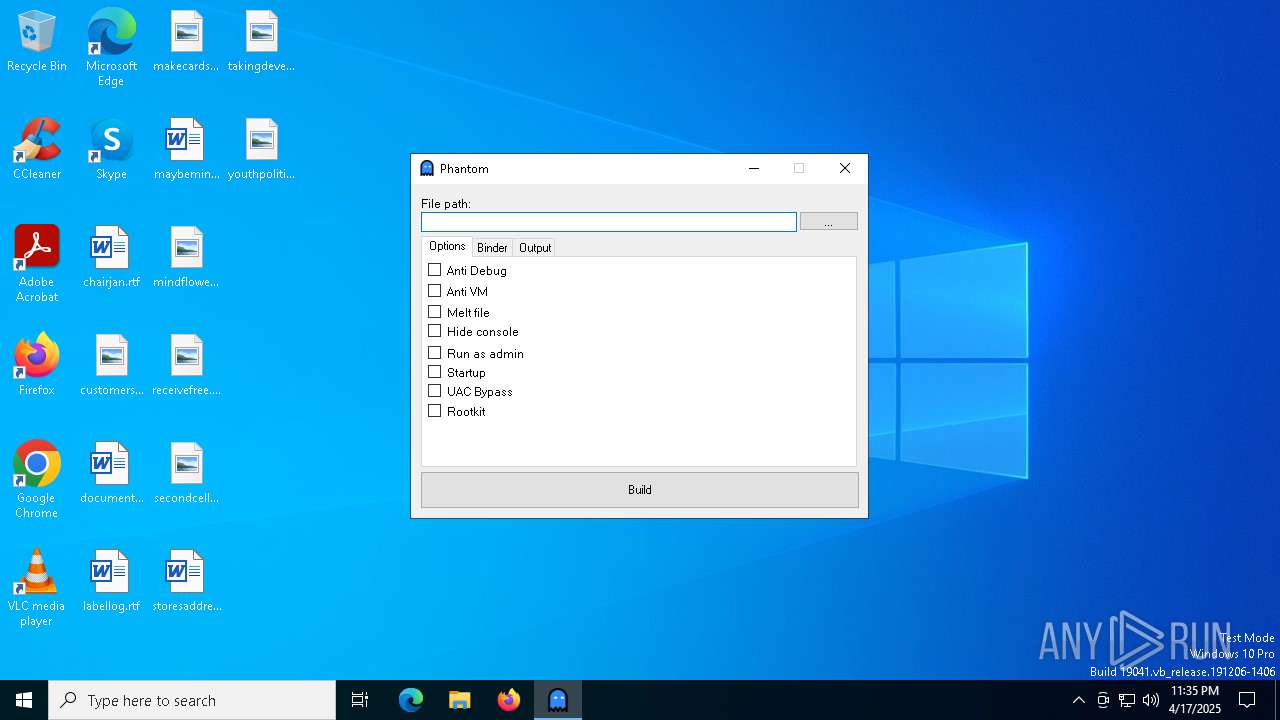
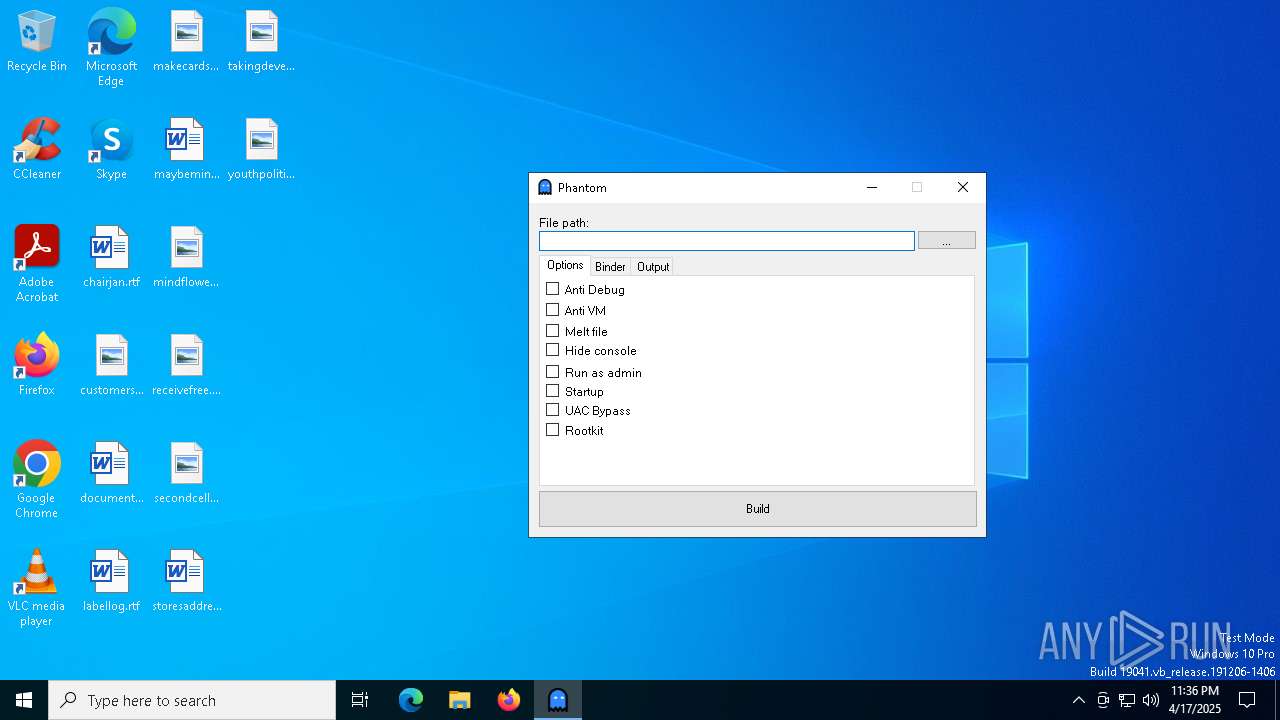
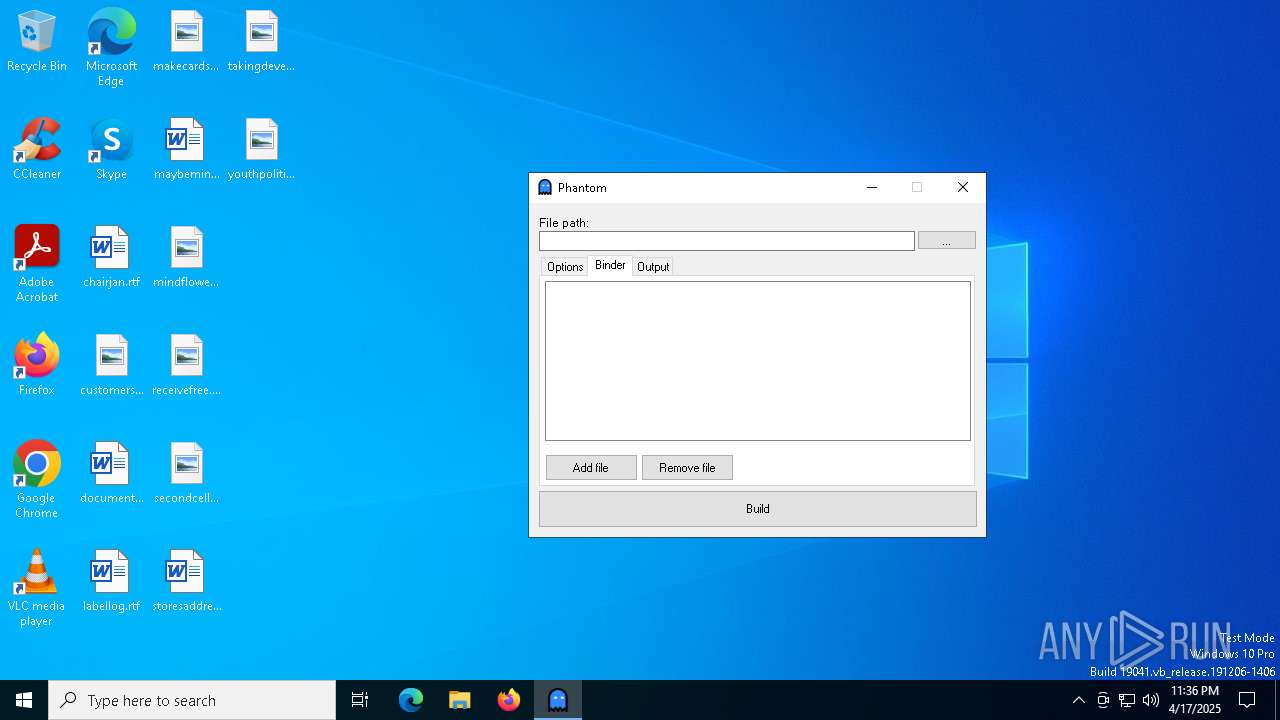
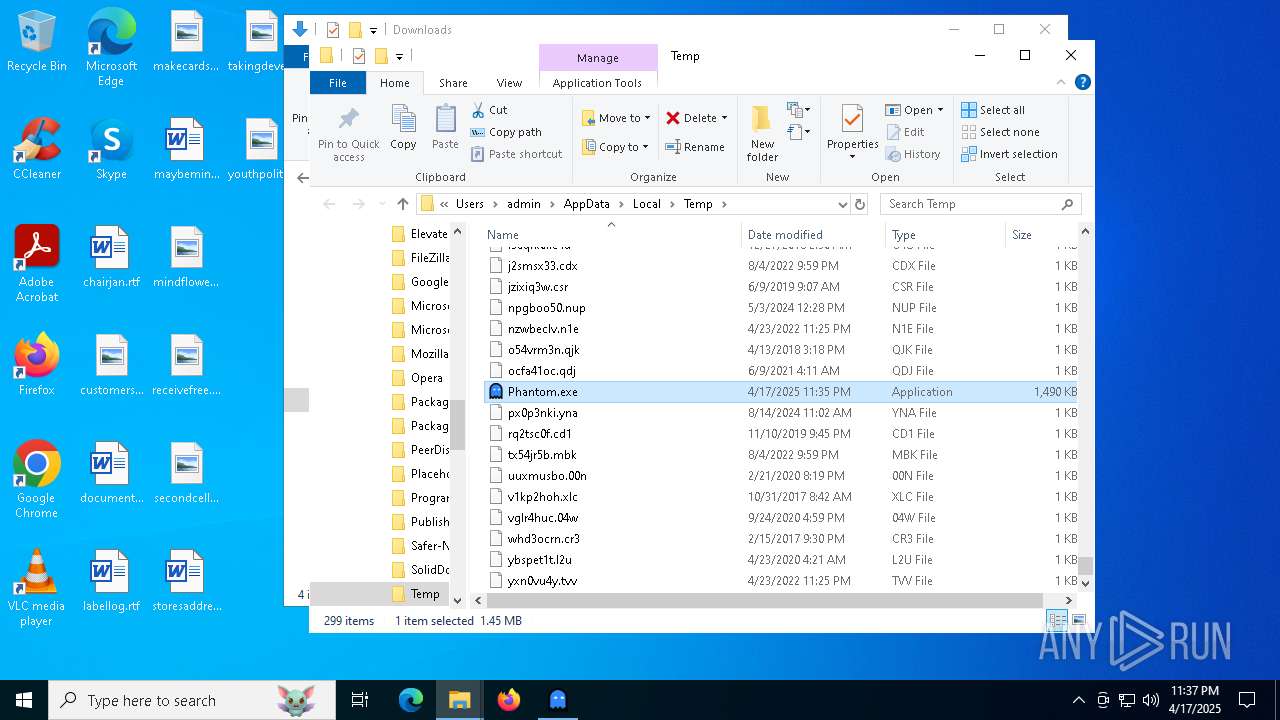
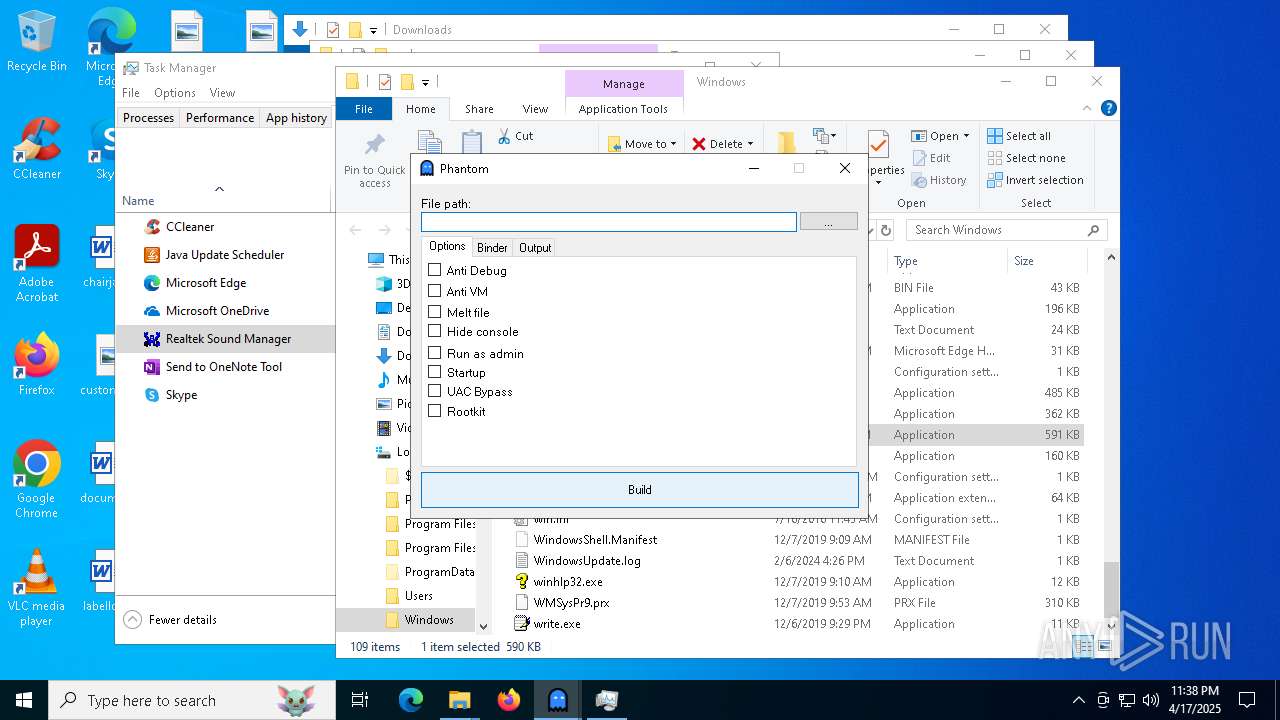
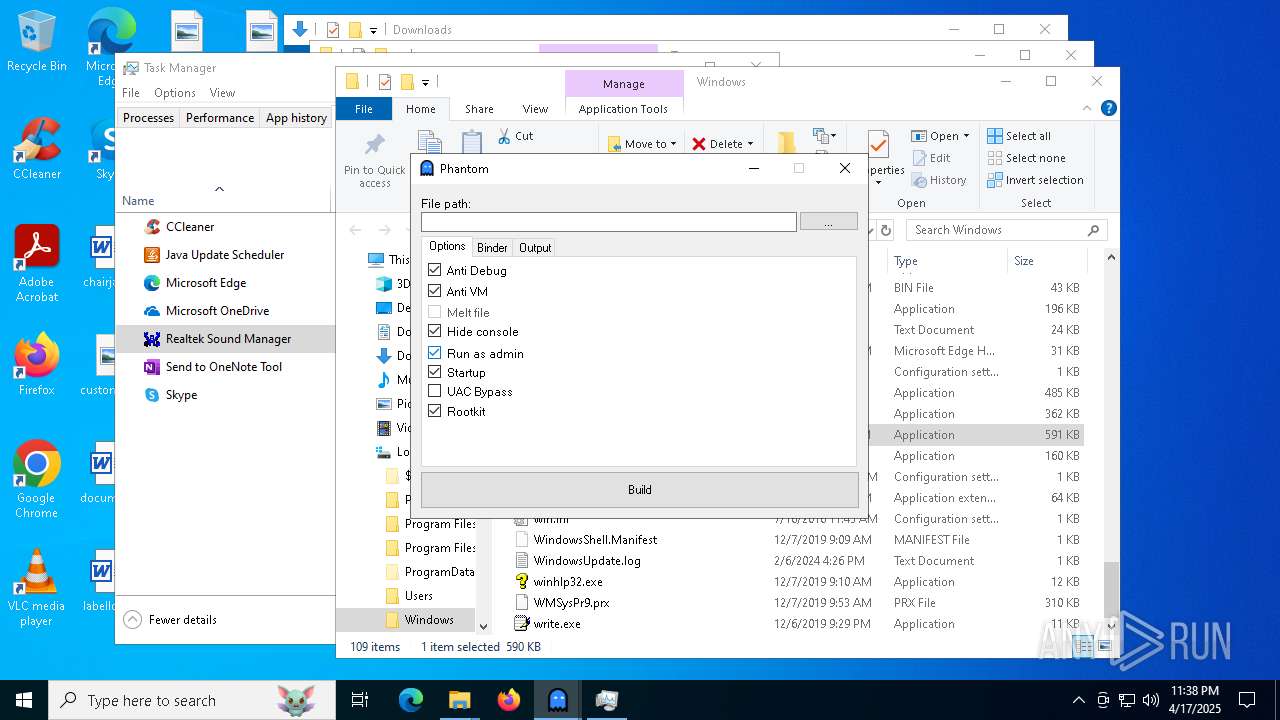
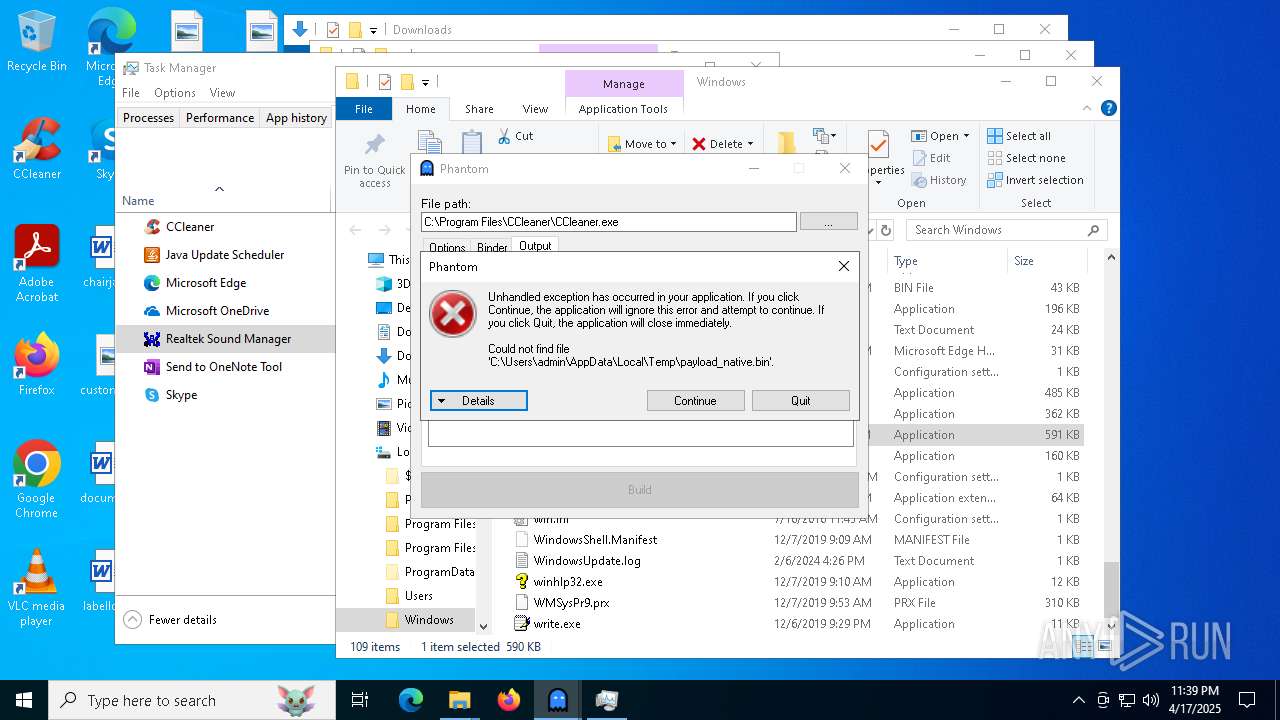
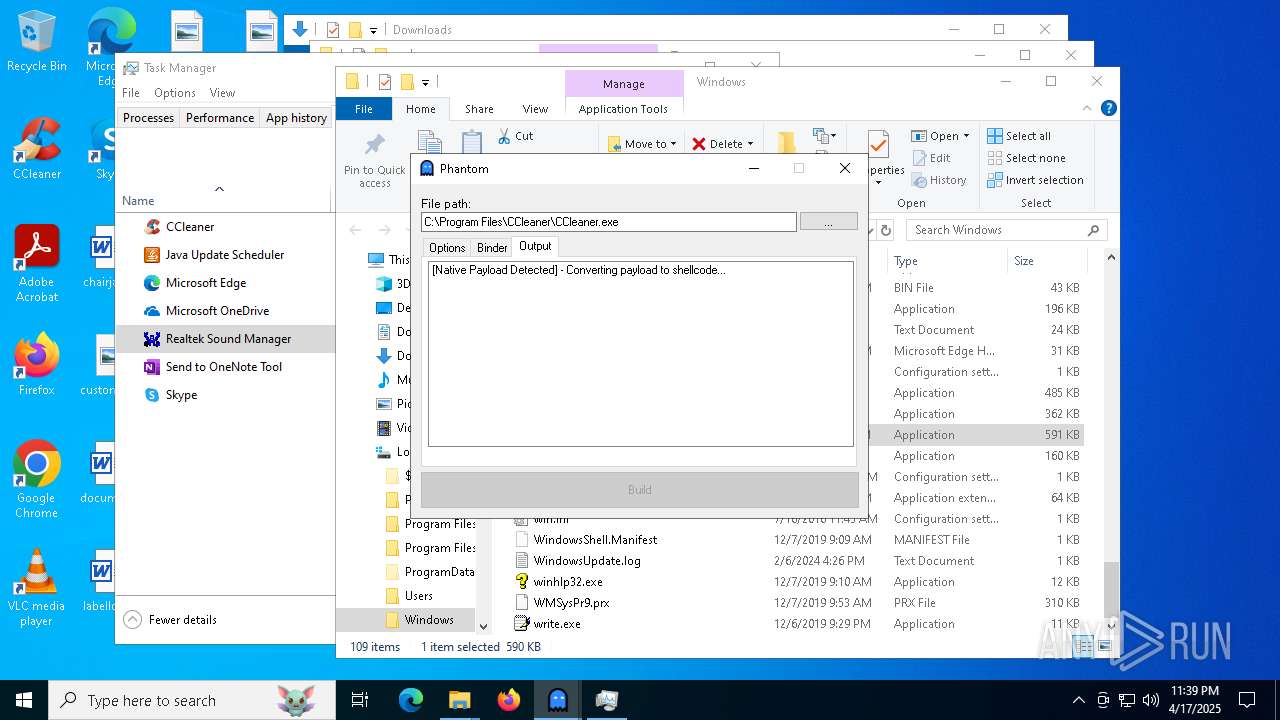
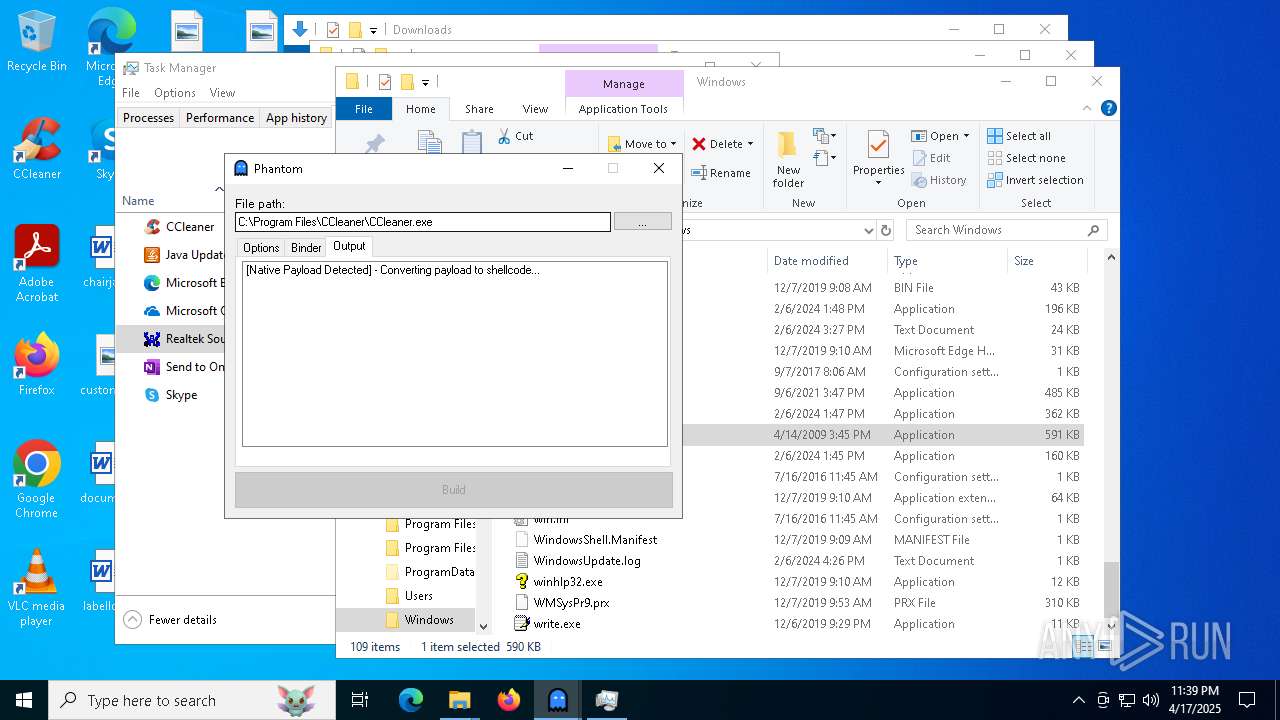
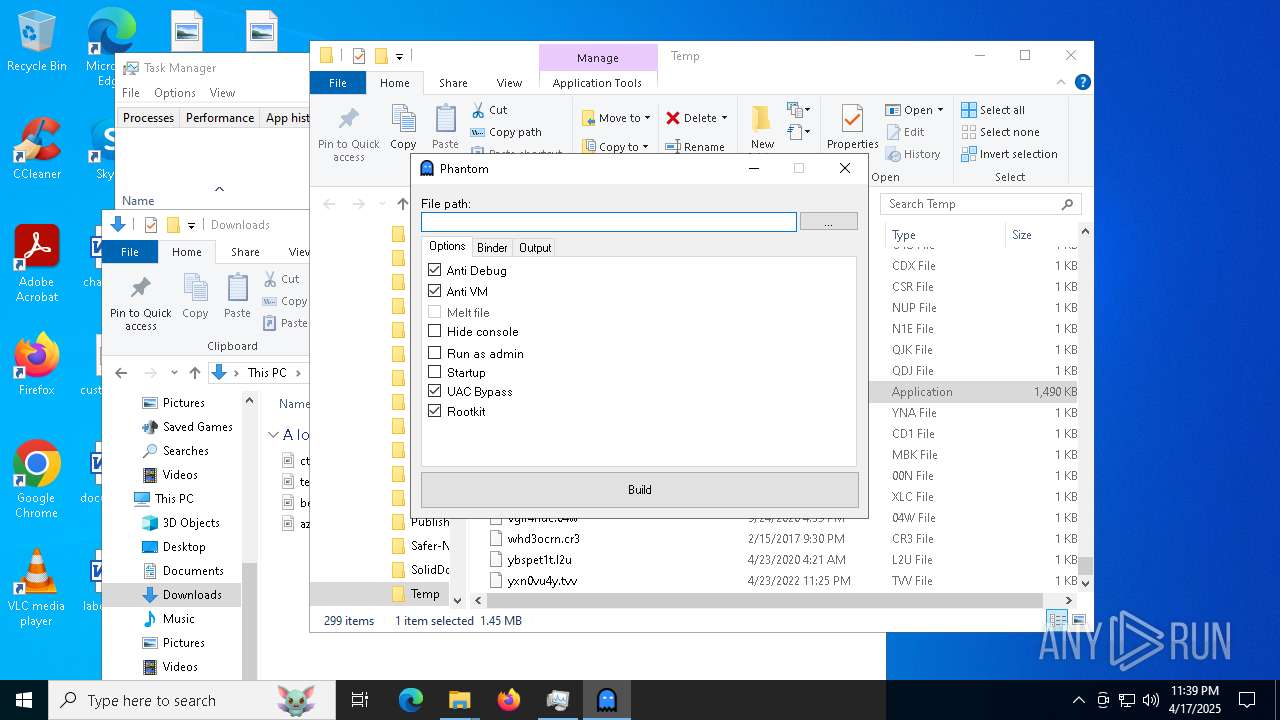
| File name: | Phantom.exe |
| Full analysis: | https://app.any.run/tasks/8df22910-14f9-473c-b2f8-c46dd0db6381 |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2025, 23:35:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 77447F97BEDAFE2DC903866AD18E25D6 |
| SHA1: | AEF3C31376A39C2FFF32A5C0EE7807257E9F6108 |
| SHA256: | 2D32E99C12044E303025702F893FF65CF9A1A3CBC4991129F8188EE055D943F4 |
| SSDEEP: | 49152:NbPFhQiT7JCX7O8tI4rEKWCkSoFEy1dk8Ztm39Kbbg5GU66TDnFYHy2LZix3/KJn:Nb8iT7cyHBfby8XoKbk5gQYHyQZoiJGs |
MALICIOUS
GENERIC has been found (auto)
- Phantom.exe (PID: 2192)
SUSPICIOUS
Reads security settings of Internet Explorer
- Phantom.exe (PID: 5428)
- Phantom.exe (PID: 2192)
- ShellExperienceHost.exe (PID: 900)
Creates file in the systems drive root
- Phantom.exe (PID: 2192)
Executable content was dropped or overwritten
- Phantom.exe (PID: 2192)
Starts CMD.EXE for commands execution
- Phantom.exe (PID: 2192)
The executable file from the user directory is run by the CMD process
- donut.exe (PID: 2104)
INFO
Reads the software policy settings
- slui.exe (PID: 5124)
- Phantom.exe (PID: 5428)
- Phantom.exe (PID: 2192)
- slui.exe (PID: 1512)
- Phantom.exe (PID: 6468)
Create files in a temporary directory
- Phantom.exe (PID: 5428)
- Phantom.exe (PID: 2192)
- Phantom.exe (PID: 6468)
Manual execution by a user
- Phantom.exe (PID: 2192)
- Taskmgr.exe (PID: 2084)
- Taskmgr.exe (PID: 6572)
- Phantom.exe (PID: 6468)
Checks supported languages
- Phantom.exe (PID: 5428)
- Phantom.exe (PID: 2192)
- ShellExperienceHost.exe (PID: 900)
- donut.exe (PID: 2104)
- Phantom.exe (PID: 6468)
Checks proxy server information
- Phantom.exe (PID: 5428)
- Phantom.exe (PID: 2192)
- slui.exe (PID: 1512)
- Phantom.exe (PID: 6468)
Reads the machine GUID from the registry
- Phantom.exe (PID: 5428)
- Phantom.exe (PID: 2192)
- Phantom.exe (PID: 6468)
Reads the computer name
- Phantom.exe (PID: 5428)
- Phantom.exe (PID: 2192)
- ShellExperienceHost.exe (PID: 900)
- Phantom.exe (PID: 6468)
Disables trace logs
- Phantom.exe (PID: 5428)
- Phantom.exe (PID: 2192)
- Phantom.exe (PID: 6468)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6572)
The sample compiled with english language support
- Phantom.exe (PID: 2192)
Process checks computer location settings
- Phantom.exe (PID: 2192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2073:04:06 12:41:48+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1492480 |
| InitializedDataSize: | 32256 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16e47e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Phantom |
| FileVersion: | 1.0.0.0 |
| InternalName: | Phantom.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | Phantom.exe |
| ProductName: | Phantom |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
151
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
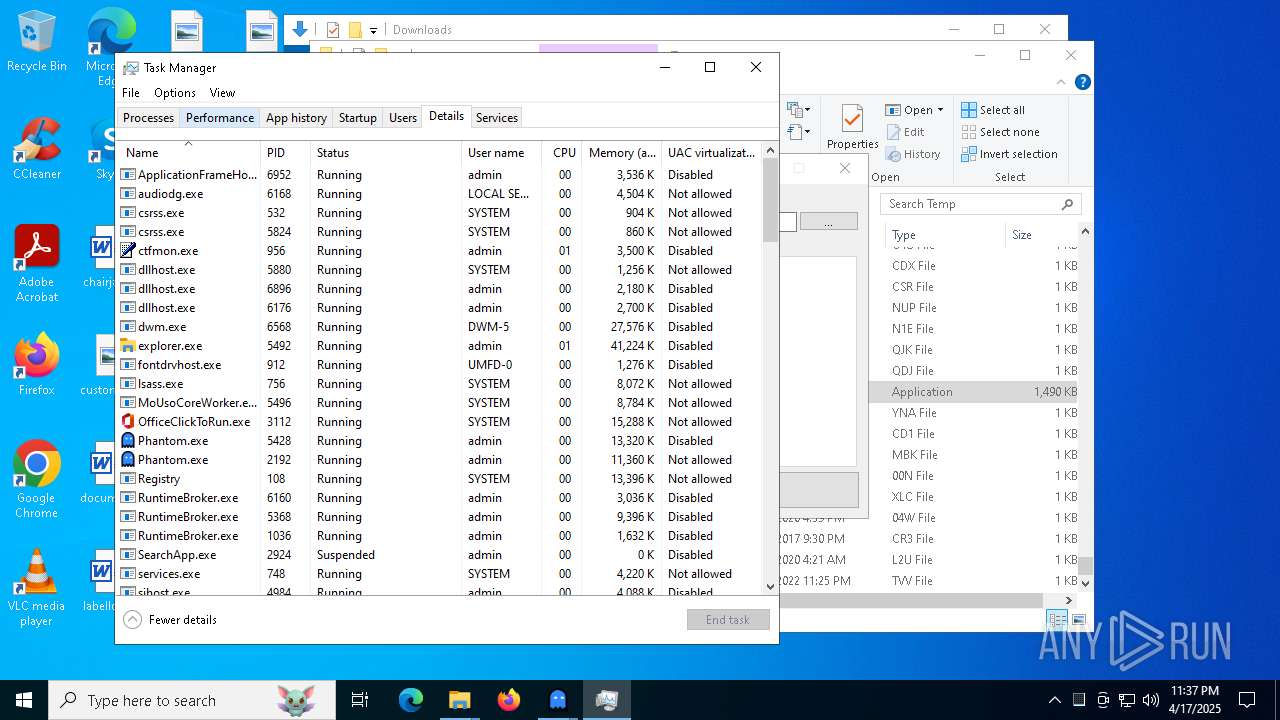
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2104 | donut.exe -a 2 -o "payload_native.bin" -i "payload_native.exe" -b 1 -k 2 -x 3 | C:\Users\admin\AppData\Local\Temp\donut.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Donut shellcode generator Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 2192 | "C:\Users\admin\AppData\Local\Temp\Phantom.exe" | C:\Users\admin\AppData\Local\Temp\Phantom.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Phantom Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2776 | "C:\Windows\System32\cmd.exe" /C donut.exe -a 2 -o "payload_native.bin" -i "payload_native.exe" -b 1 -k 2 -x 3 & exit | C:\Windows\SysWOW64\cmd.exe | — | Phantom.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4016 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5124 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 463
Read events
16 099
Write events
349
Delete events
15
Modification events
| (PID) Process: | (5428) Phantom.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Phantom_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5428) Phantom.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Phantom_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5428) Phantom.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Phantom_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5428) Phantom.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Phantom_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5428) Phantom.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Phantom_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5428) Phantom.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Phantom_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5428) Phantom.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Phantom_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5428) Phantom.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Phantom_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5428) Phantom.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Phantom_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5428) Phantom.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Phantom_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
1
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2192 | Phantom.exe | C:\Users\admin\AppData\Local\Temp\payload_native.exe | — | |
MD5:— | SHA256:— | |||
| 6572 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 5428 | Phantom.exe | C:\Users\admin\AppData\Local\Temp\bin\latestversion | text | |
MD5:F619991470DF8B3A8AD907BE8BC5FBD4 | SHA256:7F98E71C92F0055050A542C8A53E348320C6812CBFE33C12C53C1B153080A2B8 | |||
| 2192 | Phantom.exe | C:\Users\admin\AppData\Local\Temp\donut.exe | executable | |
MD5:2A516C444620354C81FD32EF1B498D1B | SHA256:EE68D7DEB7CEFDFCA66C078D6036D7AA3AA7AFCC62B282999034B4A1FAED890D | |||
| 2192 | Phantom.exe | C:\Users\admin\AppData\Local\Temp\bin\settings.json | binary | |
MD5:E82B857EB97215C3D8A4EDAB82B8BE64 | SHA256:7375C8E752DB2293B7D20EA2F18CD802A1F216BF5F41105DE03785D0287D0C9A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
37
DNS requests
21
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3784 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3784 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5428 | Phantom.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |