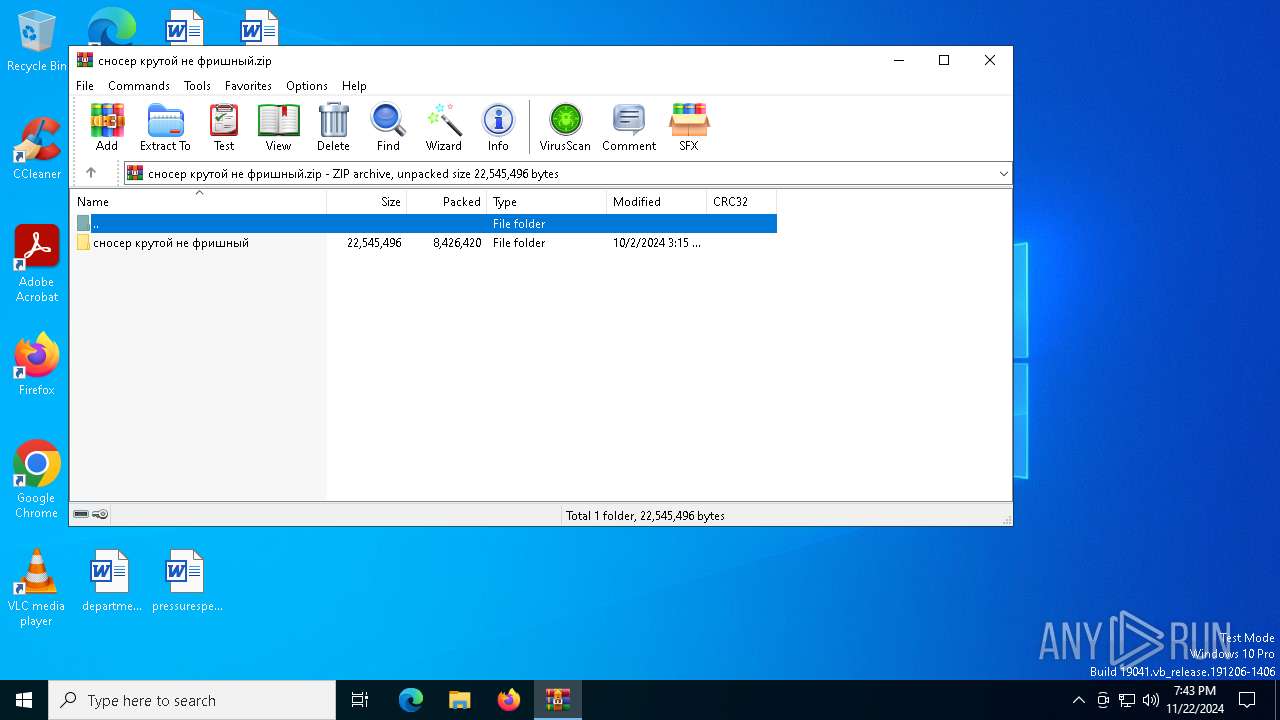
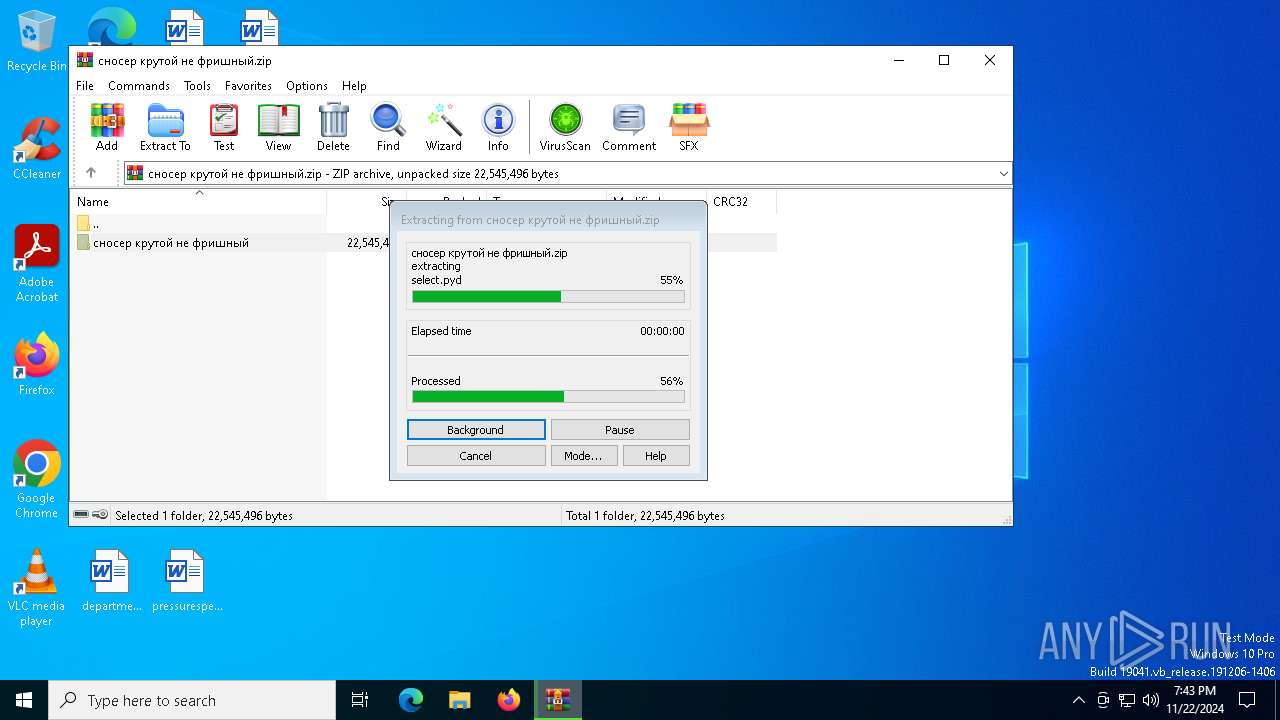
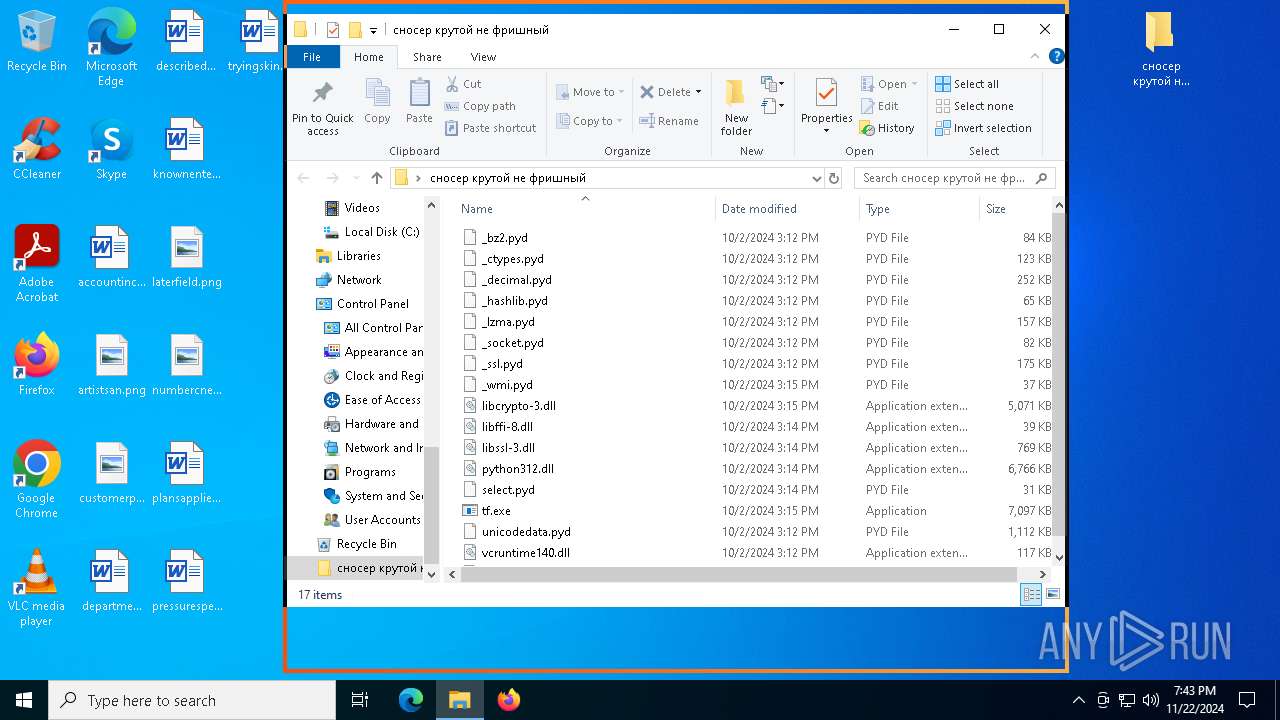
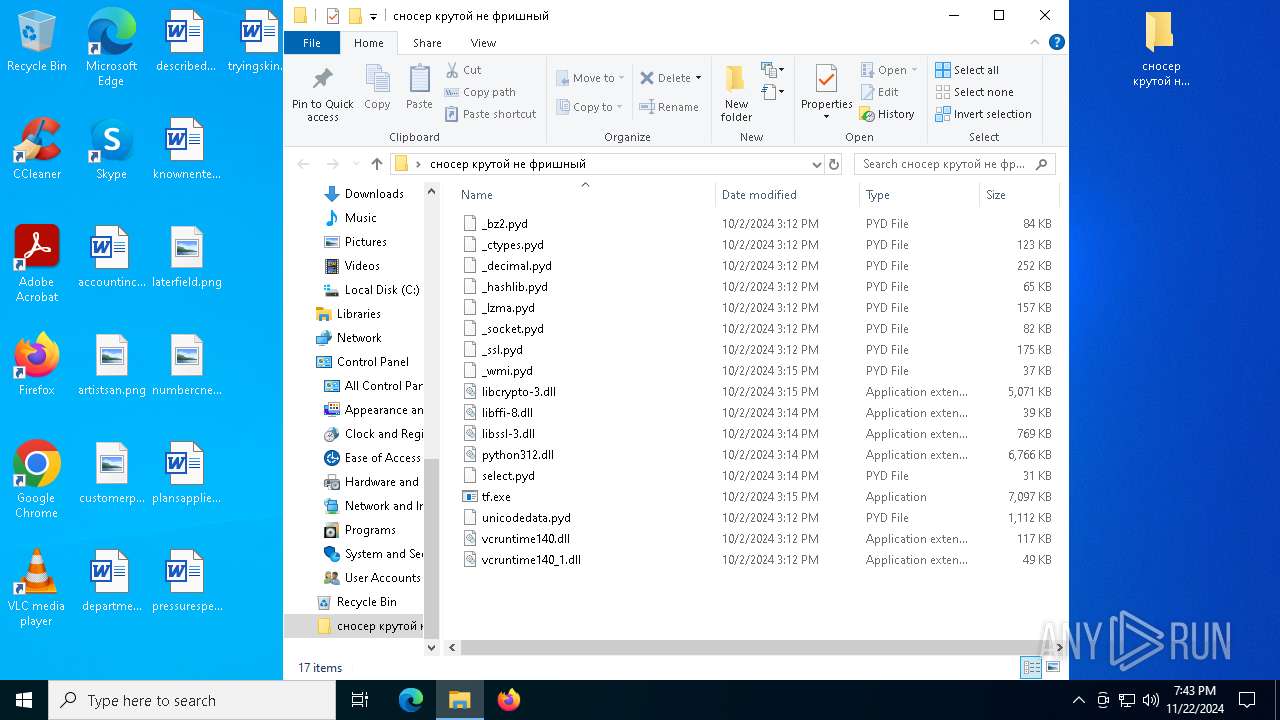
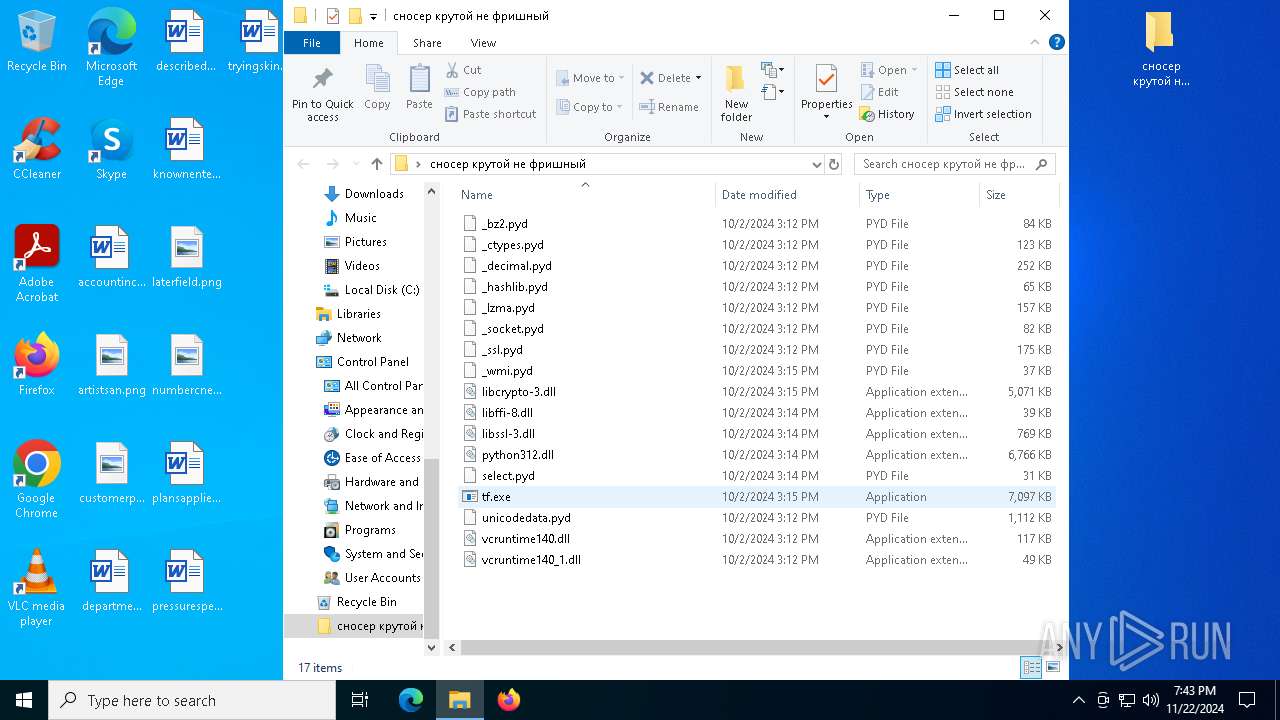
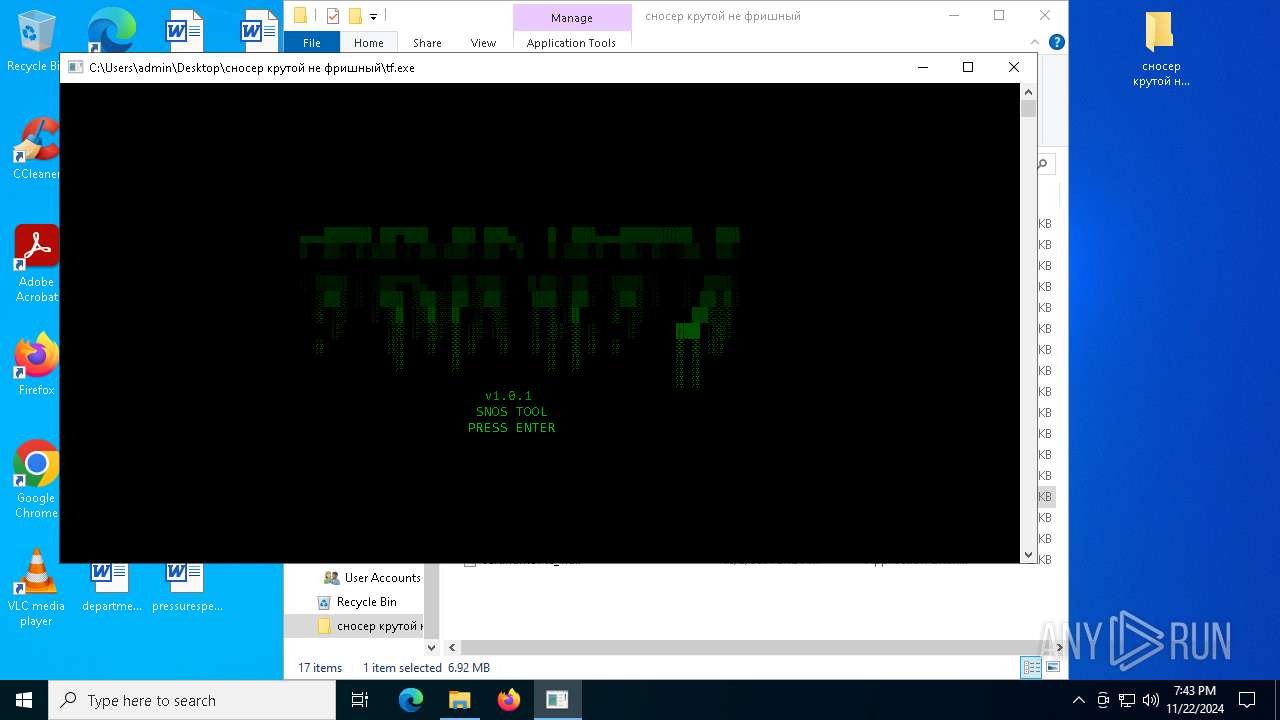
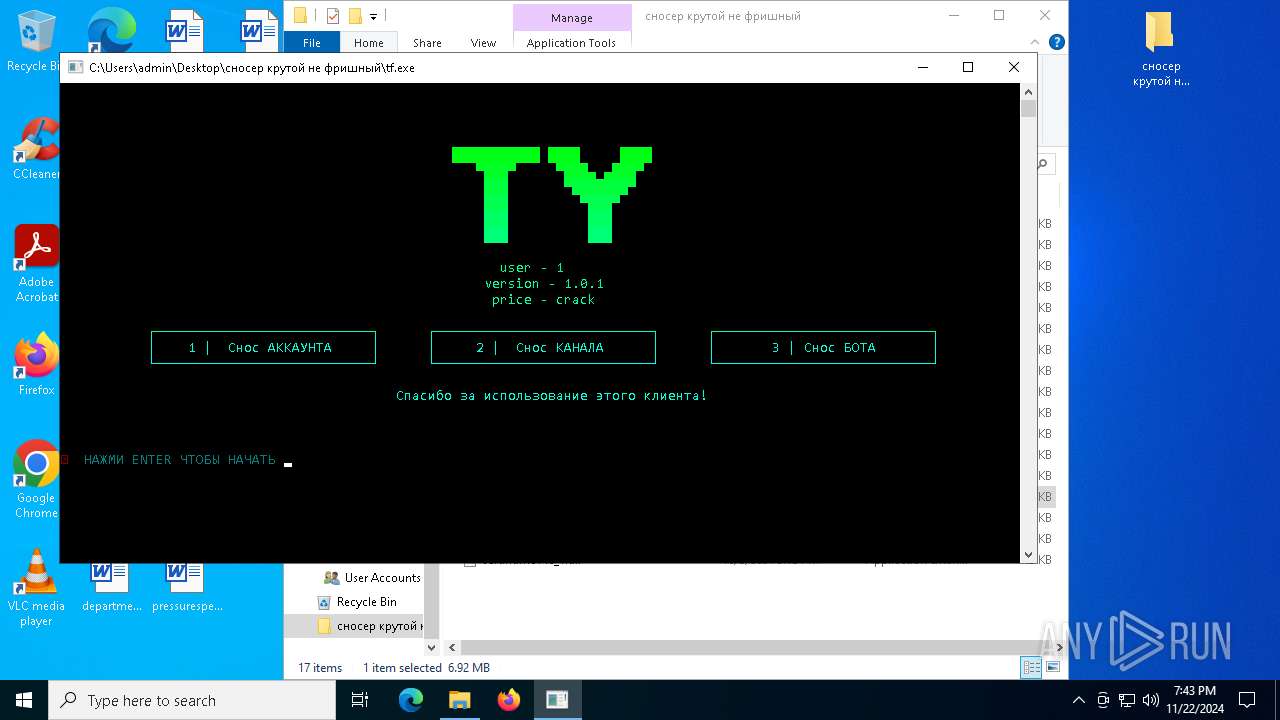
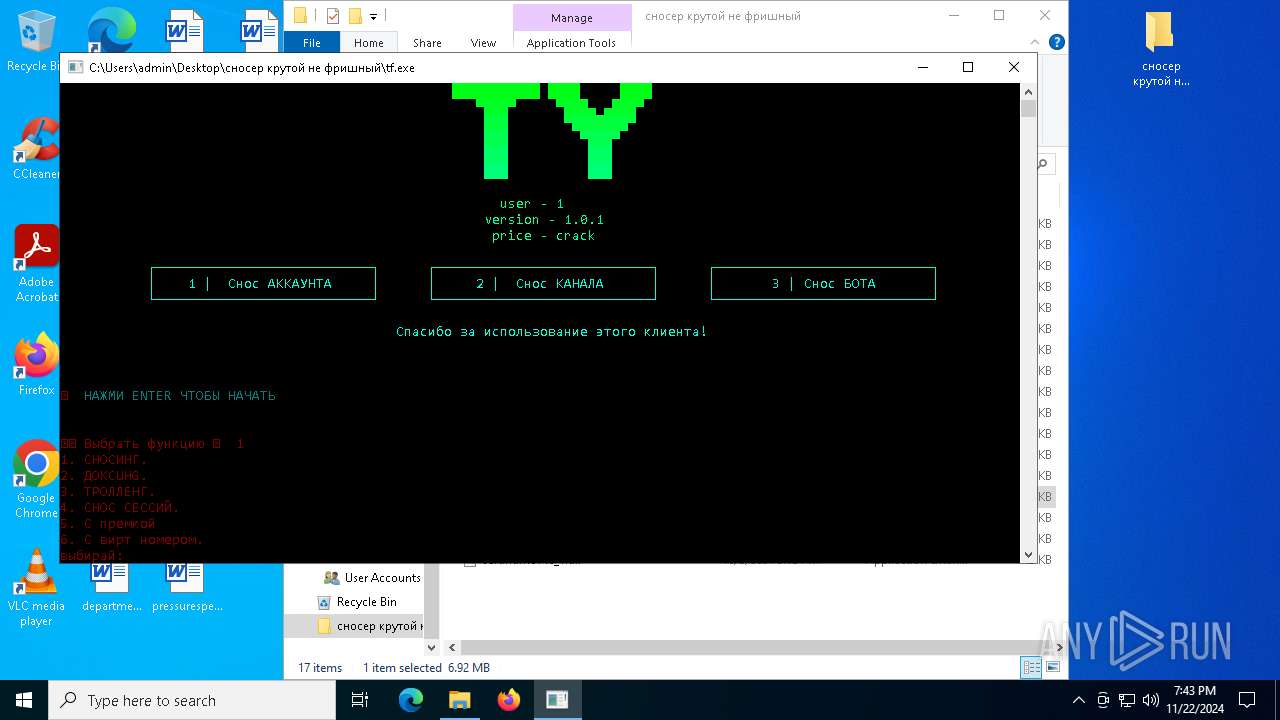
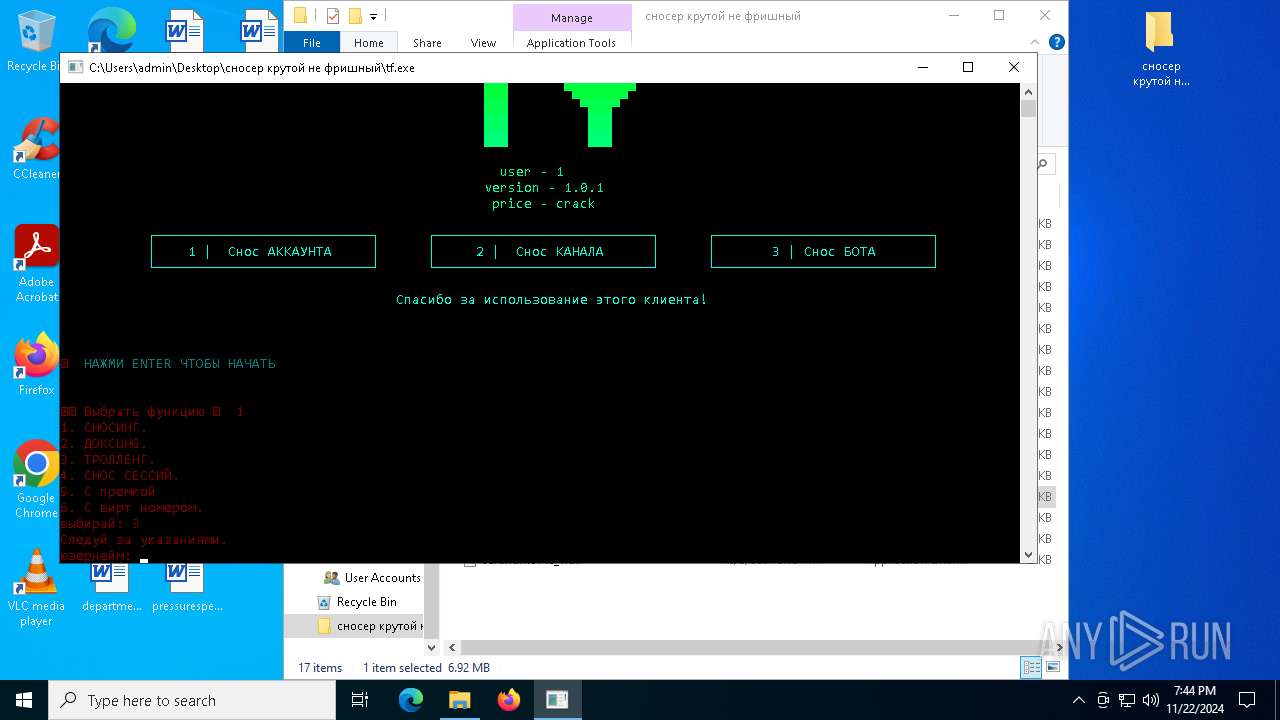
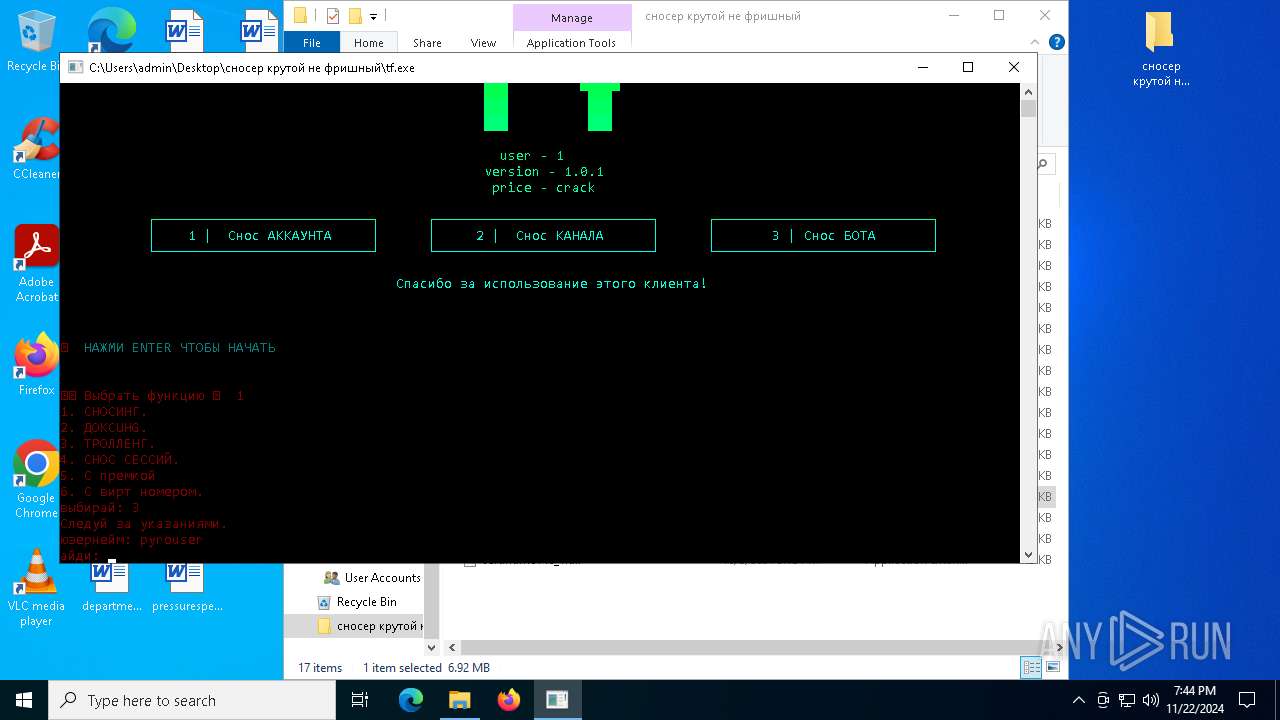
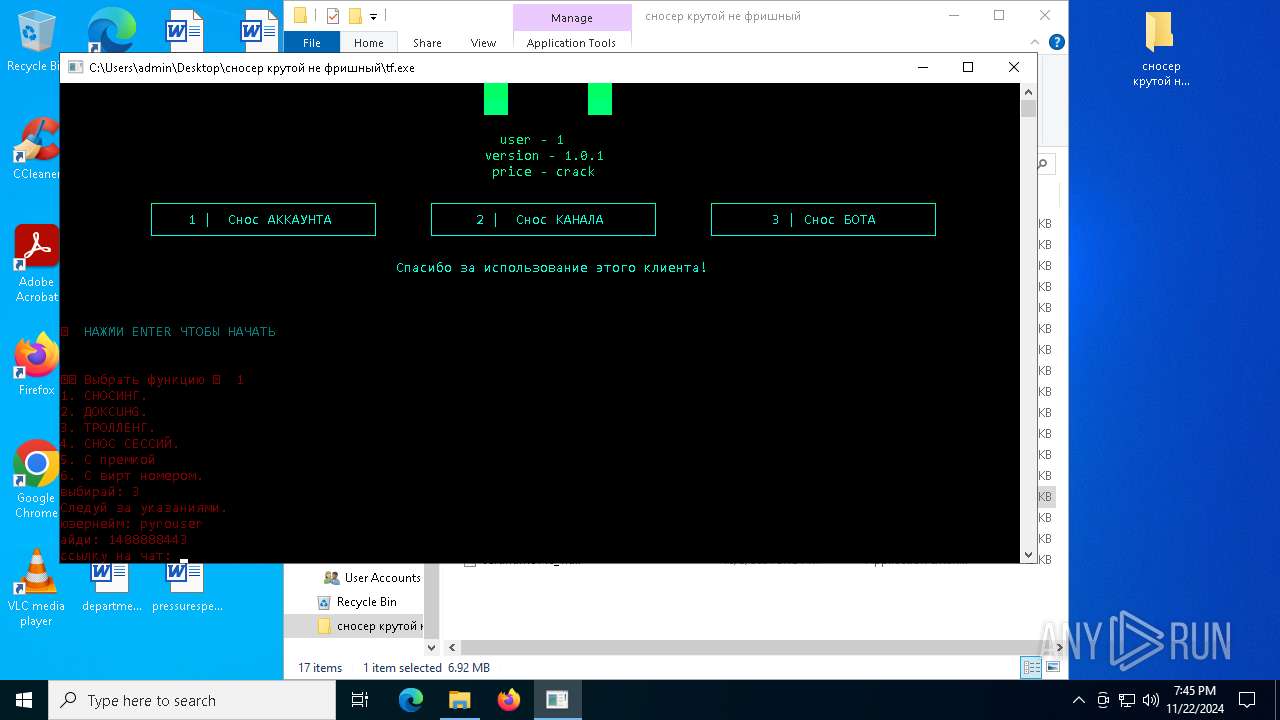
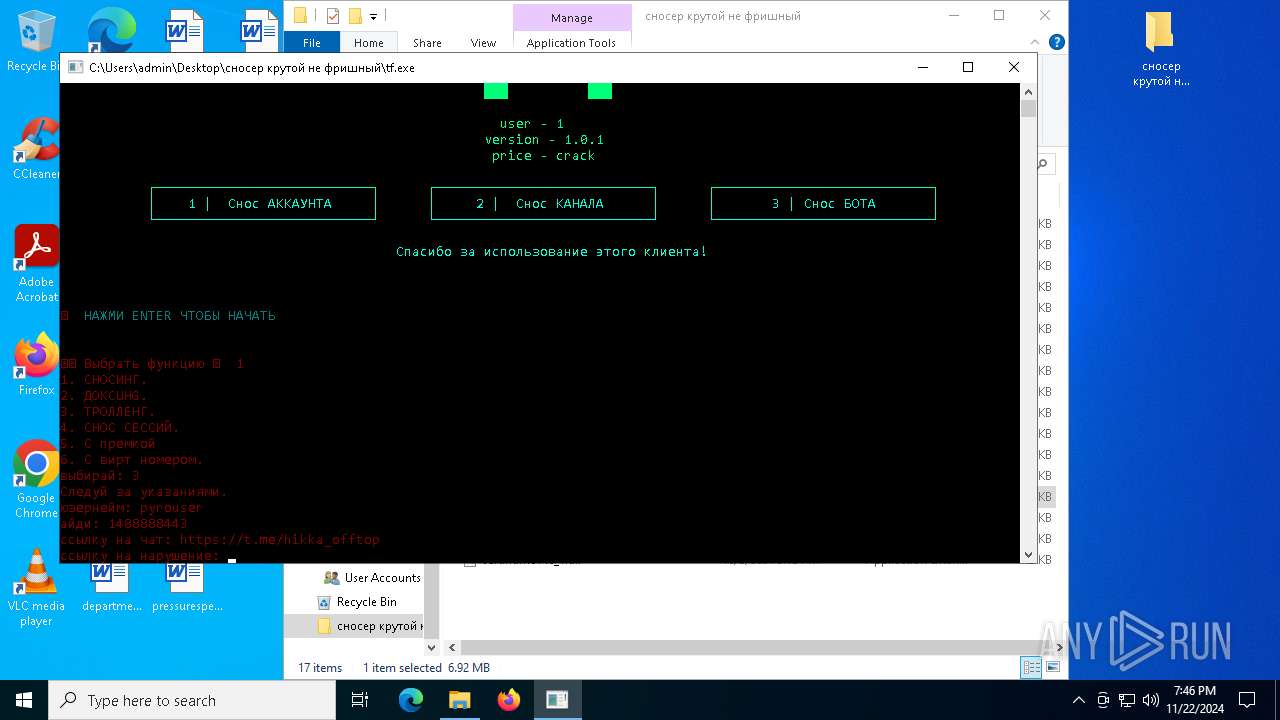
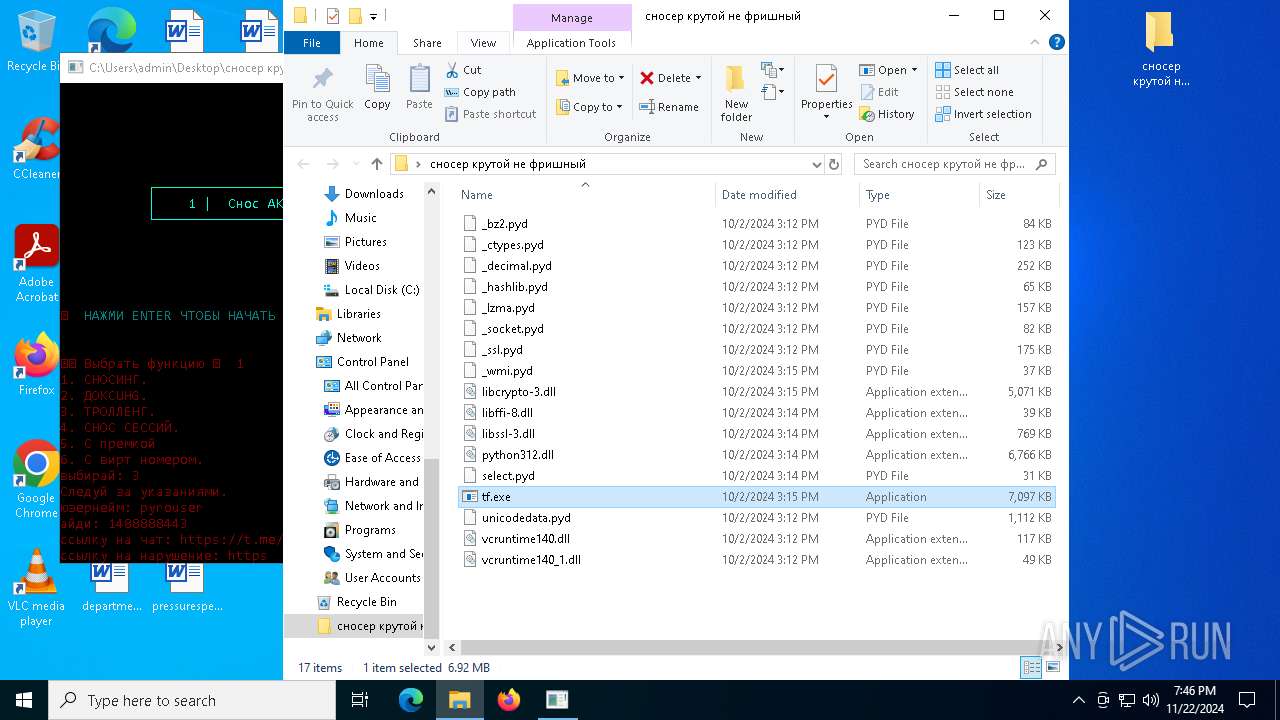
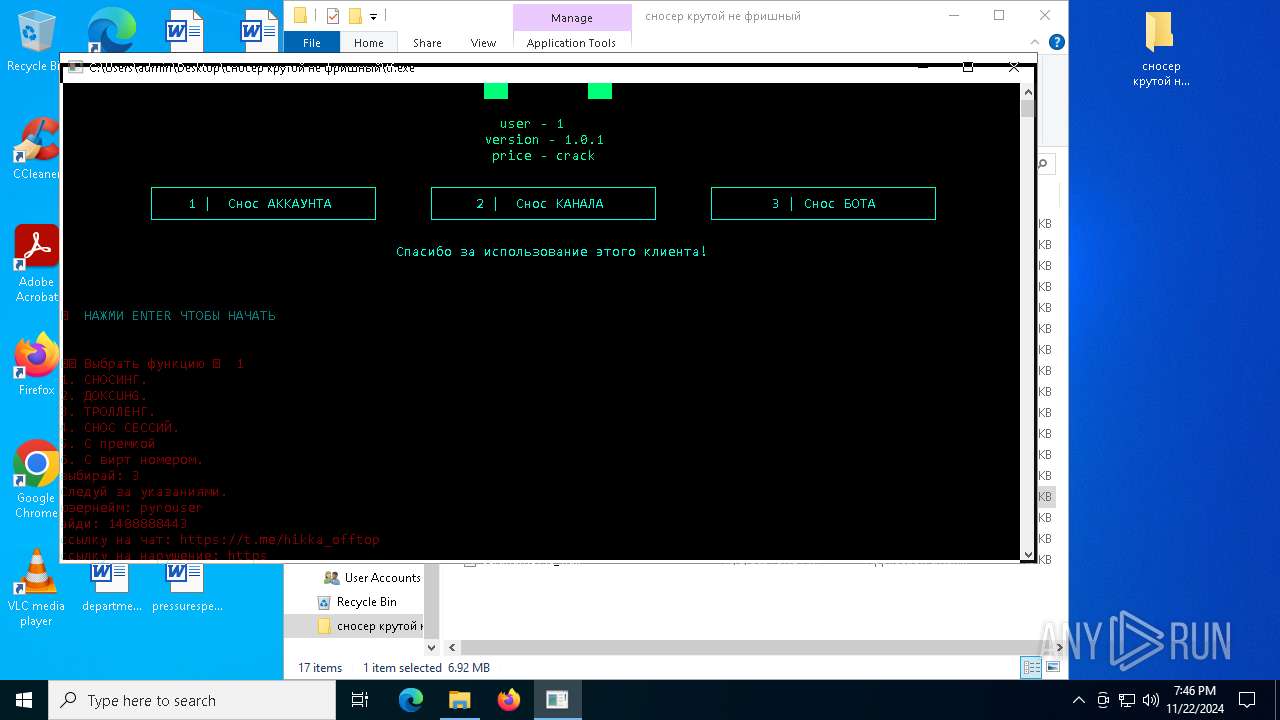
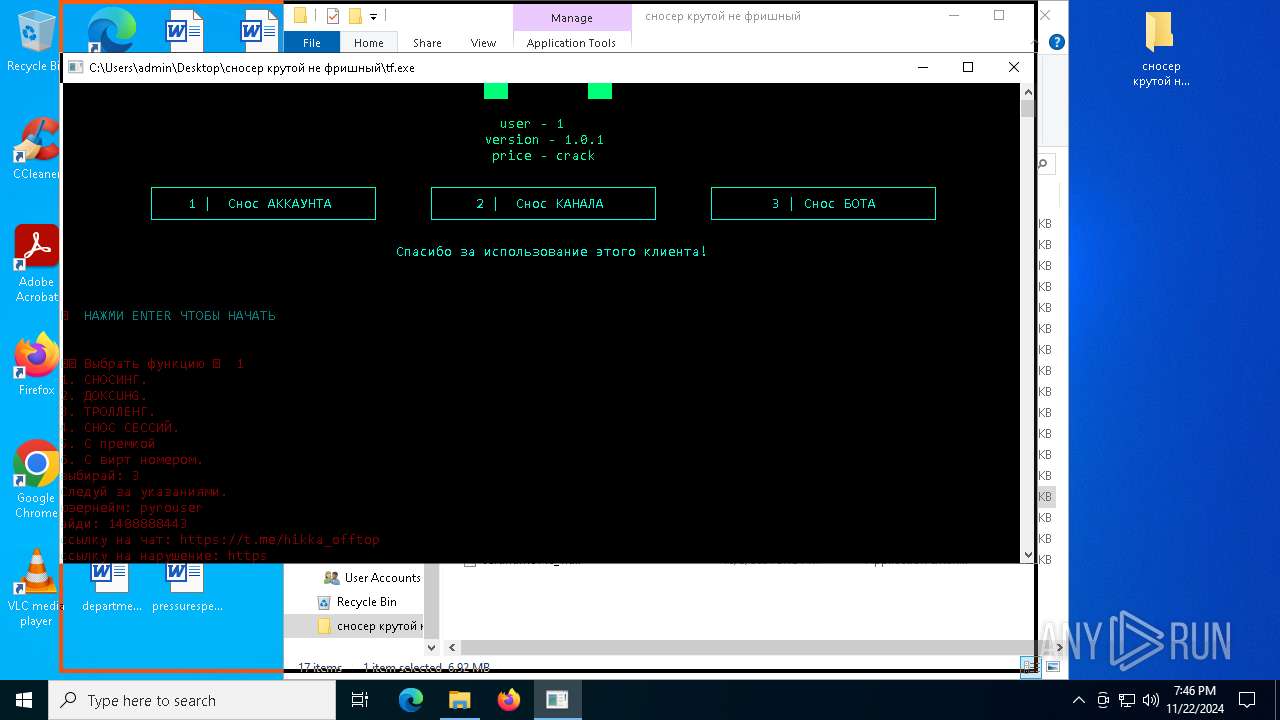
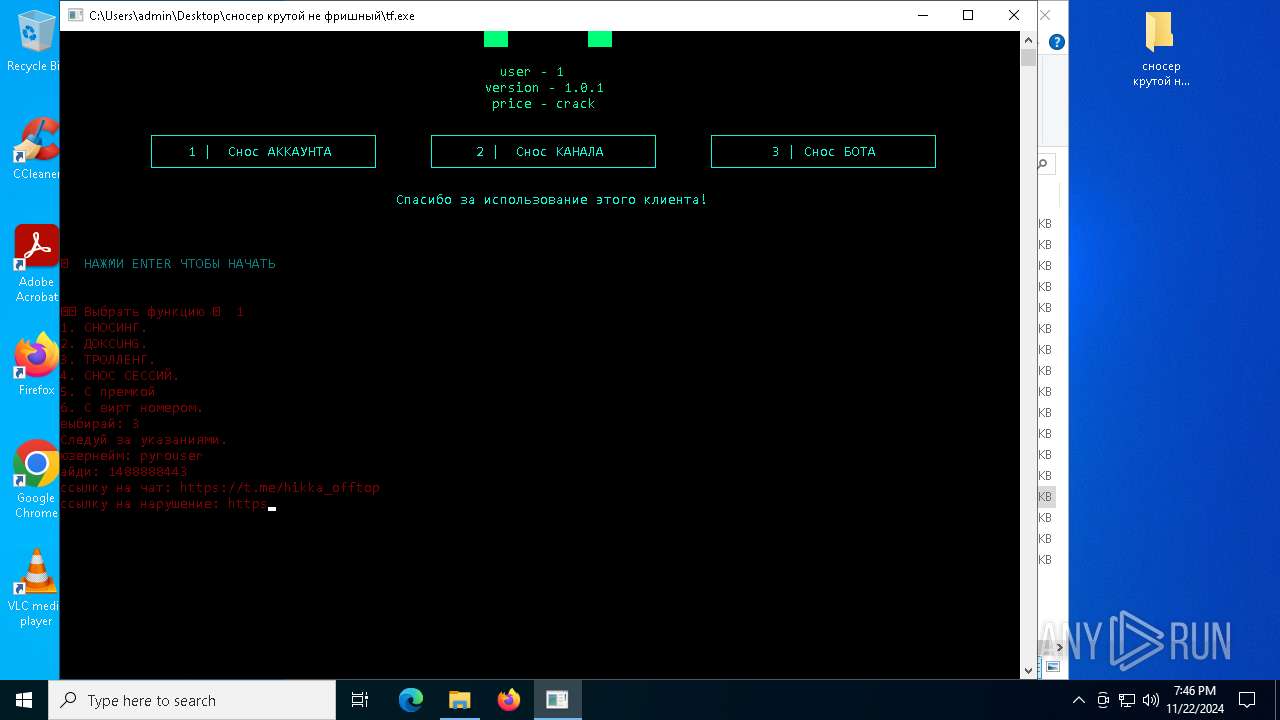
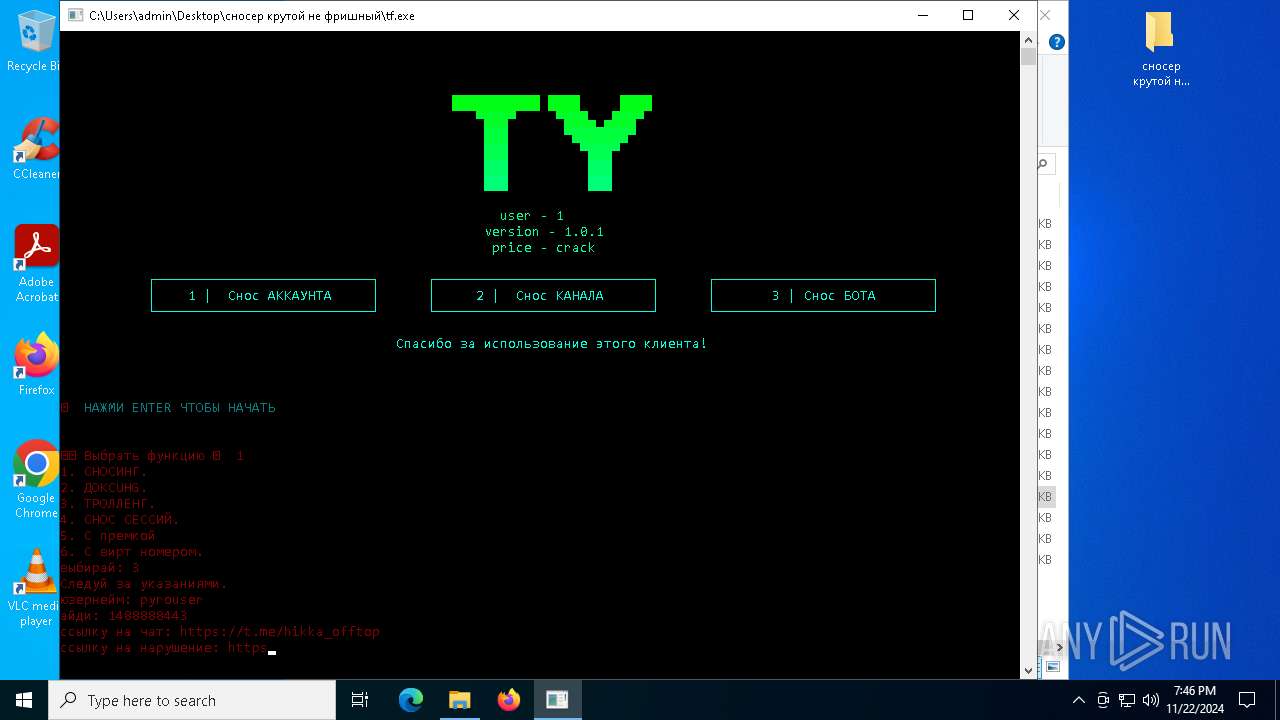
| File name: | сносер крутой не фришный.zip |
| Full analysis: | https://app.any.run/tasks/b34946ad-e38d-4c17-8c4d-e4eaefab340c |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2024, 19:42:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 242CC7DB0C26B2B2964F5B0CA40DF796 |
| SHA1: | A6F054AC8BCB8BF2A5907E4EC8ACD738942CE6F1 |
| SHA256: | 2D24FD9B1B2B9CA670263B5C99659CE50B82A4F00D3C69CE8FE927BD2606C422 |
| SSDEEP: | 98304:C2hbc5ATquRvlv9uZmzAOxJe+f/ZJy9U29ndEUE4z6d2ujPVXovvjq40az7BHI9z:zllf9tYBTw1oKkTY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- WinRAR.exe (PID: 3552)
The process drops C-runtime libraries
- WinRAR.exe (PID: 3552)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3552)
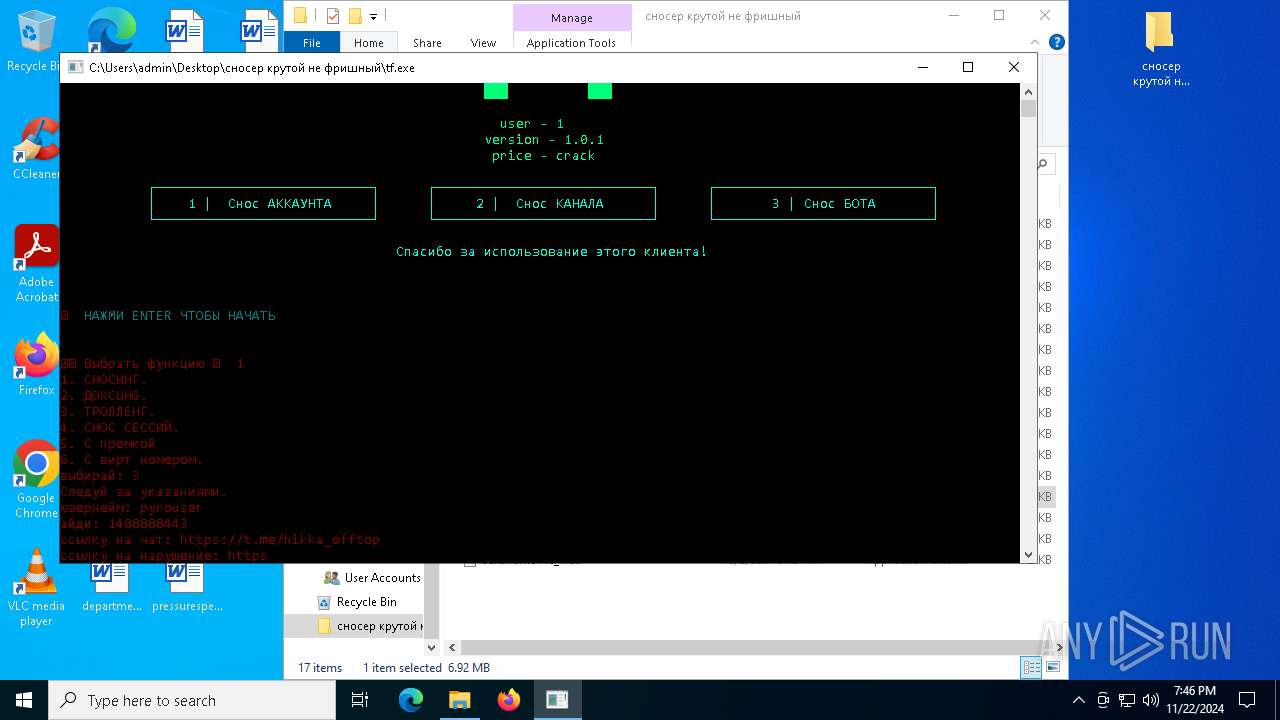
Loads Python modules
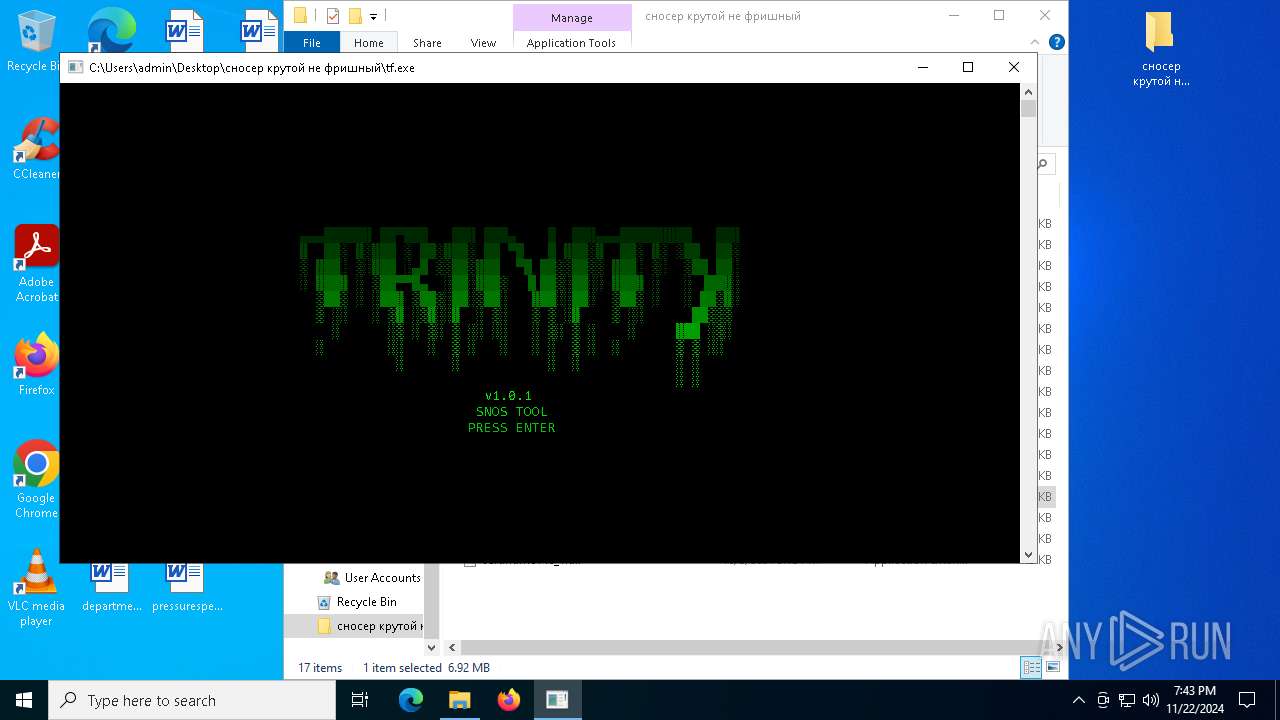
- tf.exe (PID: 4944)
Starts CMD.EXE for commands execution
- tf.exe (PID: 4944)
INFO
Manual execution by a user
- tf.exe (PID: 4944)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3552)
The process uses the downloaded file
- WinRAR.exe (PID: 3552)
Checks supported languages
- tf.exe (PID: 4944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:10:02 18:15:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | ᭮??? ???⮩ ?? ???????/ |
Total processes
168
Monitored processes
45
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | tf.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 244 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | tf.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 512 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | tf.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 512 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | tf.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 512 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | tf.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 648 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | tf.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 716 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | tf.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 936 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | tf.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 936 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | tf.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
| 1480 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | tf.exe | ||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| ||||||||||||||
Total events
2 308
Read events
2 290
Write events
18
Delete events
0
Modification events
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\сносер крутой не фришный.zip | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (3552) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
17
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3552.40174\сносер крутой не фришный\libcrypto-3.dll | executable | |
MD5:E547CF6D296A88F5B1C352C116DF7C0C | SHA256:05FE080EAB7FC535C51E10C1BD76A2F3E6217F9C91A25034774588881C3F99DE | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3552.40174\сносер крутой не фришный\_ssl.pyd | executable | |
MD5:6A2B0F8F50B47D05F96DEFF7883C1270 | SHA256:68DAD60FF6FB36C88EF1C47D1855517BFE8DE0F5DDEA0F630B65B622A645D53A | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3552.40174\сносер крутой не фришный\_lzma.pyd | executable | |
MD5:8CFBAFE65D6E38DDE8E2E8006B66BB3E | SHA256:6D548DB0AB73291F82CF0F4CA9EC0C81460185319C8965E829FAEACAE19444FF | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3552.40174\сносер крутой не фришный\libffi-8.dll | executable | |
MD5:0F8E4992CA92BAAF54CC0B43AACCCE21 | SHA256:EFF52743773EB550FCC6CE3EFC37C85724502233B6B002A35496D828BD7B280A | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3552.40174\сносер крутой не фришный\vcruntime140_1.dll | executable | |
MD5:F8DFA78045620CF8A732E67D1B1EB53D | SHA256:A113F192195F245F17389E6ECBED8005990BCB2476DDAD33F7C4C6C86327AFE5 | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3552.40174\сносер крутой не фришный\_bz2.pyd | executable | |
MD5:DD26ED92888DE9C57660A7AD631BB916 | SHA256:324268786921EC940CBD4B5E2F71DAFD08E578A12E373A715658527E5B211697 | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3552.40174\сносер крутой не фришный\_decimal.pyd | executable | |
MD5:CEA3B419C7CA87140A157629C6DBD299 | SHA256:95B9850E6FB335B235589DD1348E007507C6B28E332C9ABB111F2A0035C358E5 | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3552.40174\сносер крутой не фришный\_ctypes.pyd | executable | |
MD5:C8AFA1EBB28828E1115C110313D2A810 | SHA256:8978972CF341CCD0EDF8435D63909A739DF7EF29EC7DD57ED5CAB64B342891F0 | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3552.40174\сносер крутой не фришный\_hashlib.pyd | executable | |
MD5:D19CB5CA144AE1FD29B6395B0225CF40 | SHA256:F95EC2562A3C70FB1A6E44D72F4223CE3C7A0F0038159D09DCE629F59591D5AA | |||
| 3552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3552.40174\сносер крутой не фришный\_socket.pyd | executable | |
MD5:E43AED7D6A8BCD9DDFC59C2D1A2C4B02 | SHA256:2C2A6A6BA360E38F0C2B5A53B4626F833A3111844D95615EBF35BE0E76B1EF7A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4308 | svchost.exe | GET | 200 | 2.19.198.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.198.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4308 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2672 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5388 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5388 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1200 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.198.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4308 | svchost.exe | 2.19.198.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4308 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |