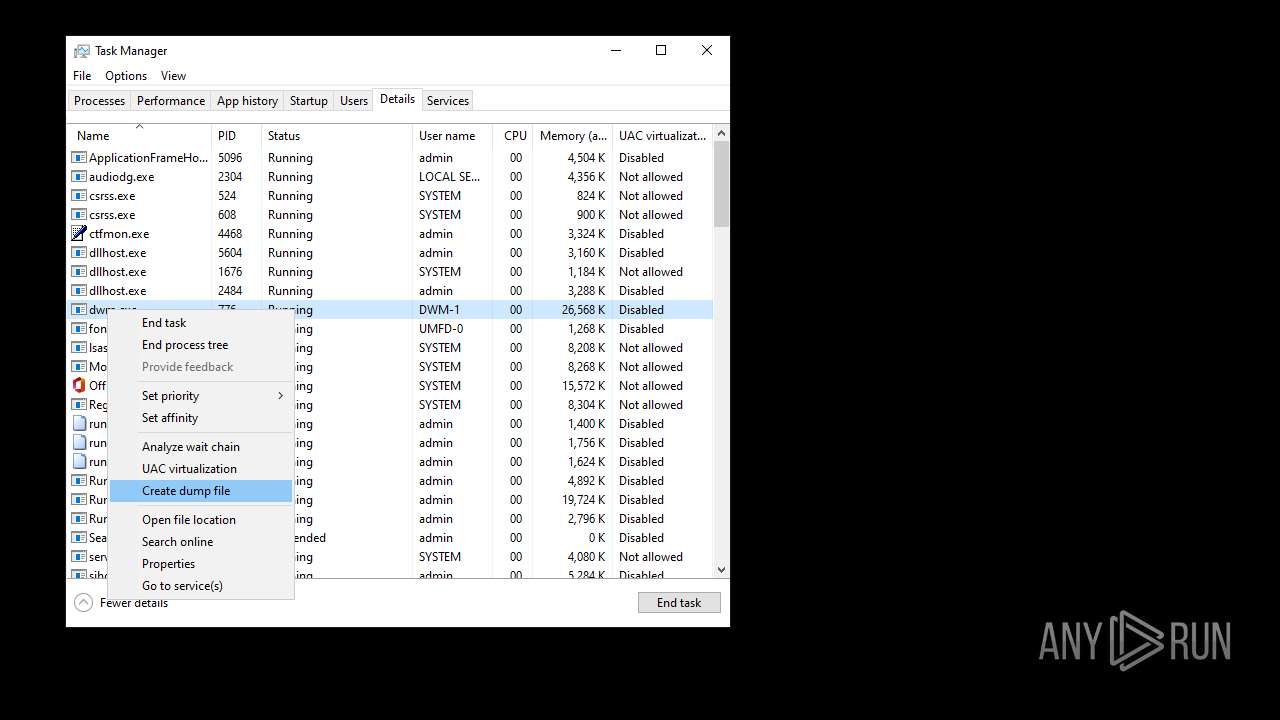
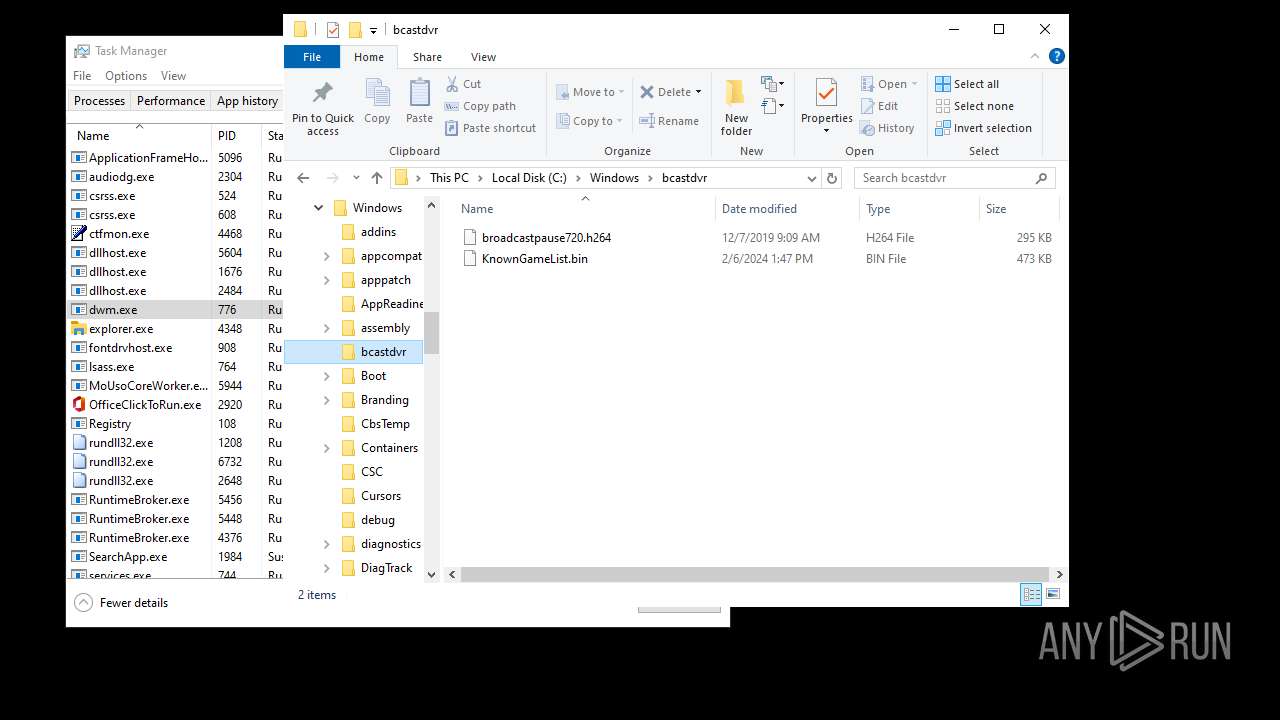
| File name: | .exe |
| Full analysis: | https://app.any.run/tasks/d049a62a-9f90-4627-9528-f3af29660dd5 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 18:34:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 5 sections |
| MD5: | 5941D0550CA95007DEFA7DD2542F3D87 |
| SHA1: | 3074B38531B1DCA2E822FCE46492B828E10C8C06 |
| SHA256: | 2D20E8C7EC69A445479656870236715088B17B495206A102AB7ECE00F5B135DE |
| SSDEEP: | 24576:WilbsHTGz18+hm9mnYP5MpATf+0EzFnRbsQ4DW9ionote/+Zh7wfBjwPQjkj:WilbsHTGz18Wm9MYPqpATf+0EzFnRbsb |
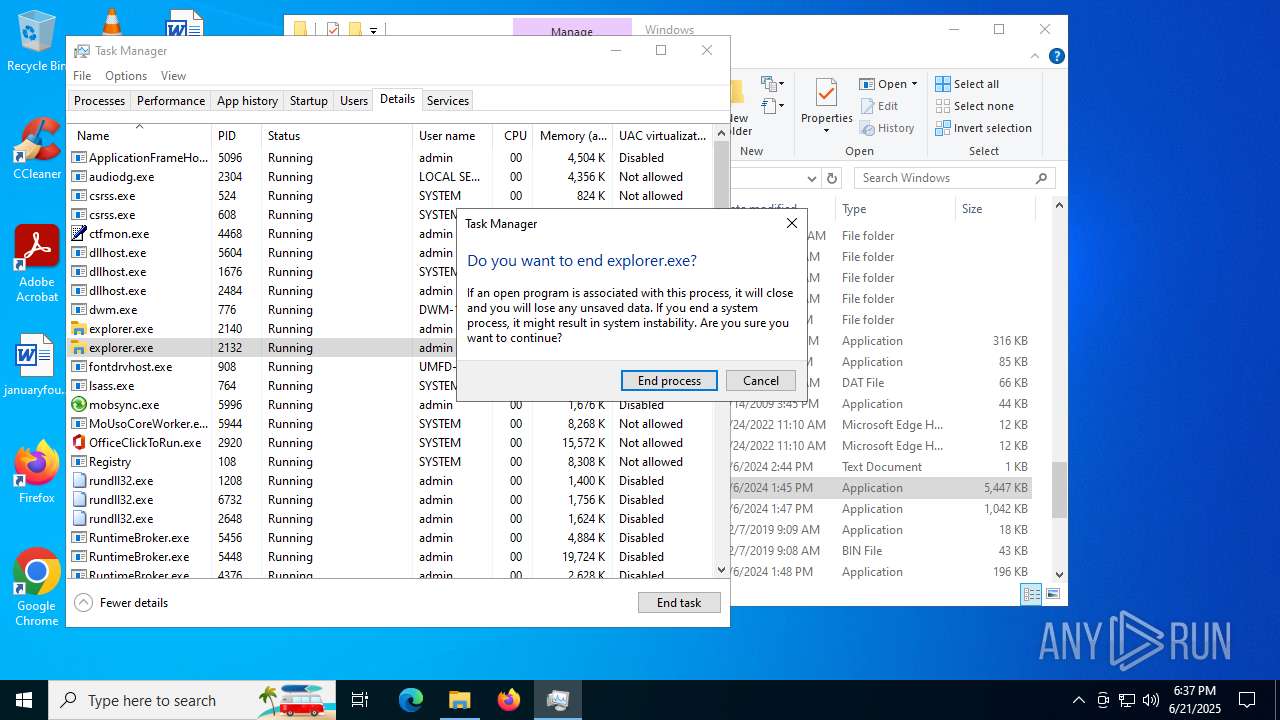
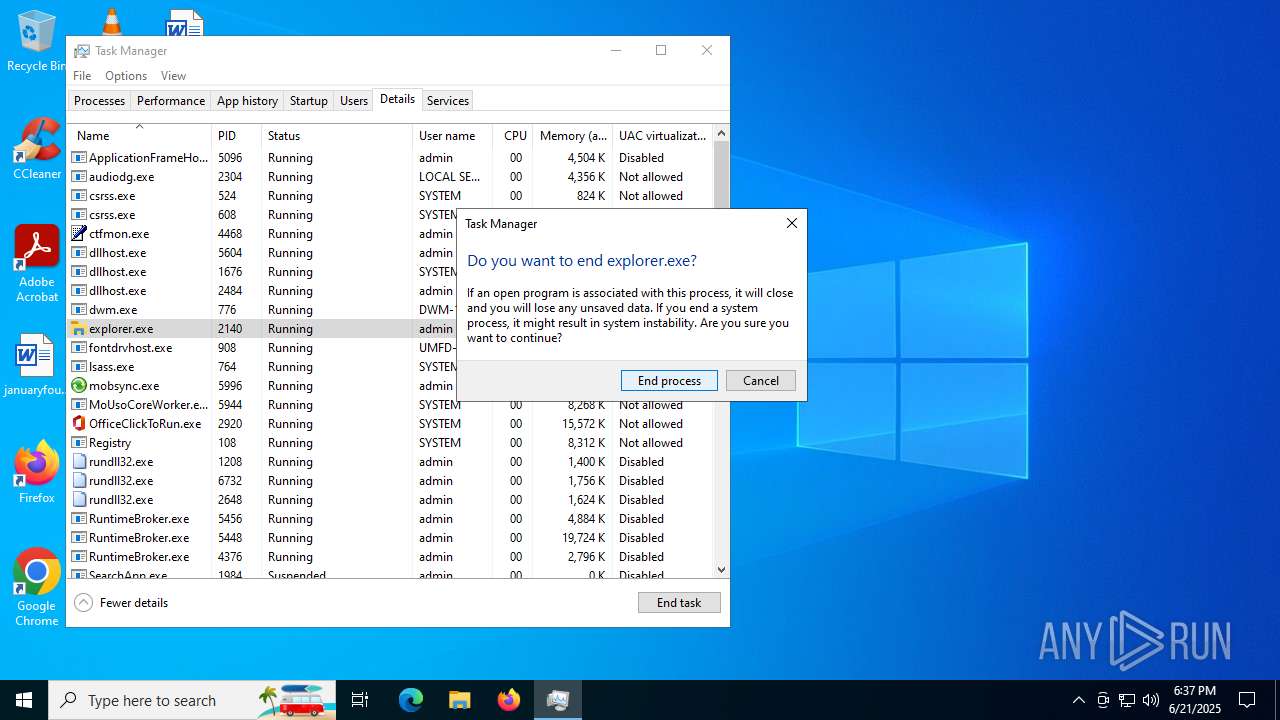
MALICIOUS
Application was injected by another process
- svchost.exe (PID: 4248)
- svchost.exe (PID: 4204)
- StartMenuExperienceHost.exe (PID: 5160)
- RuntimeBroker.exe (PID: 5224)
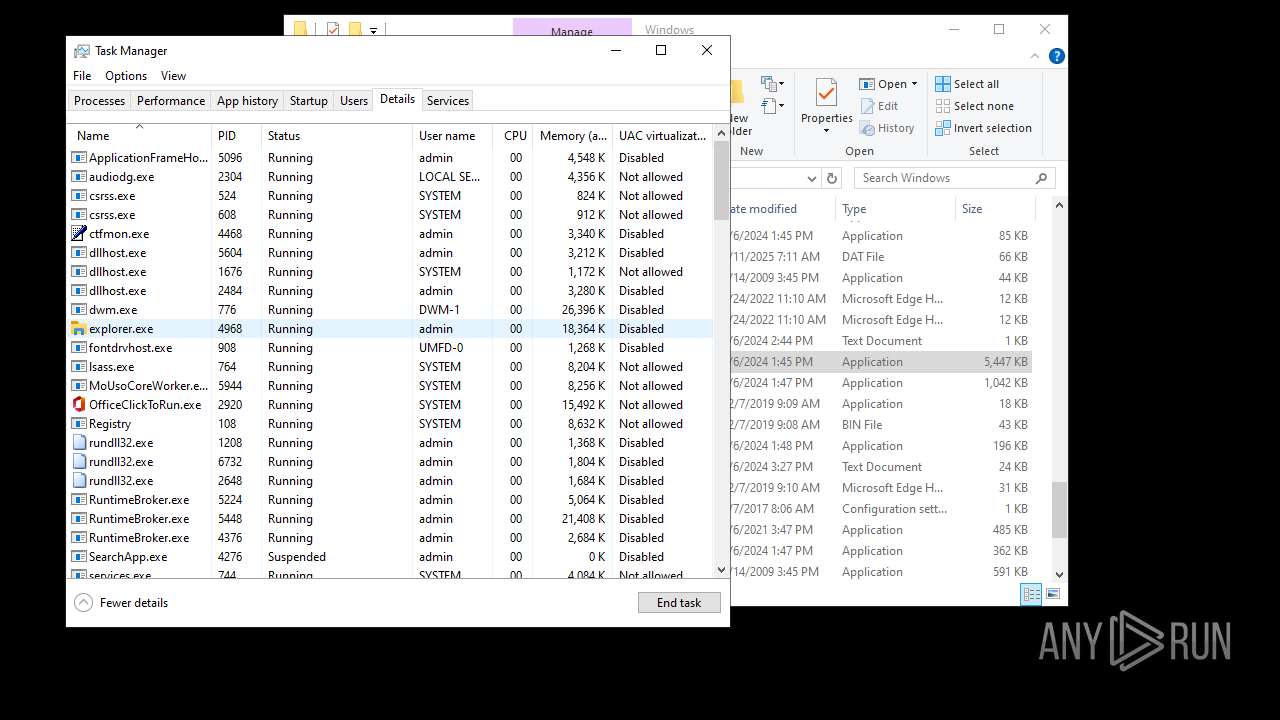
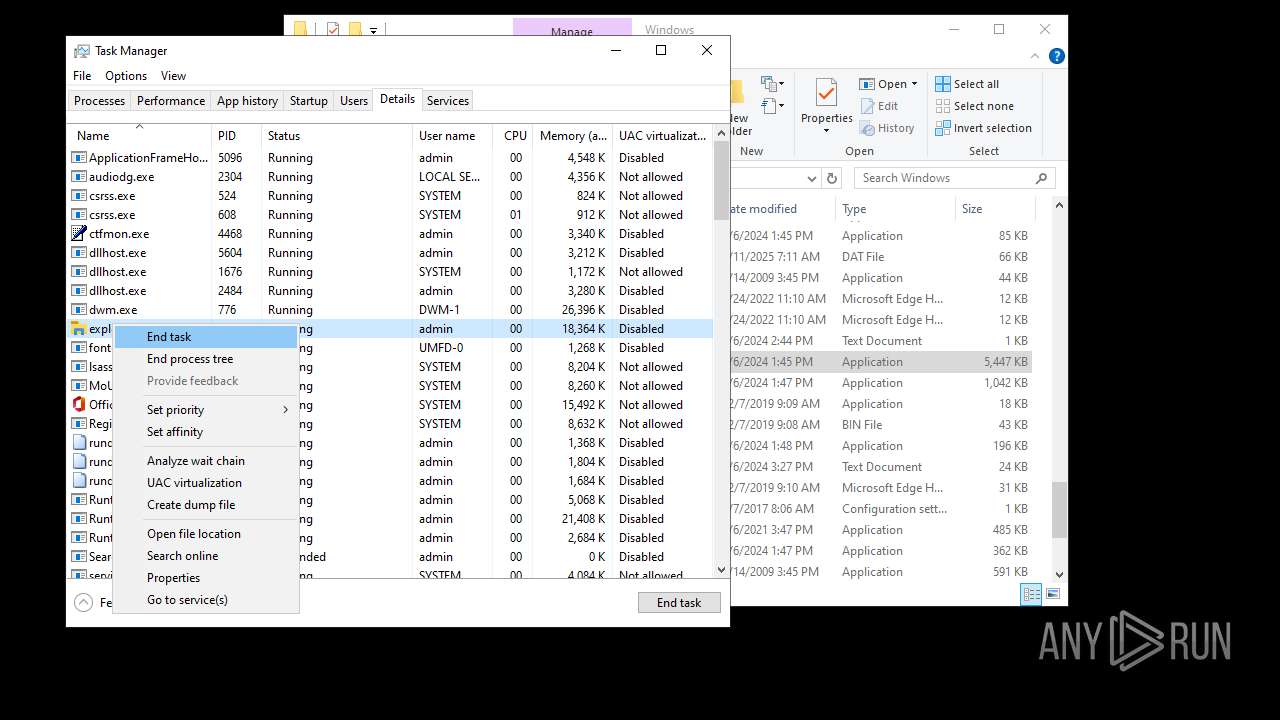
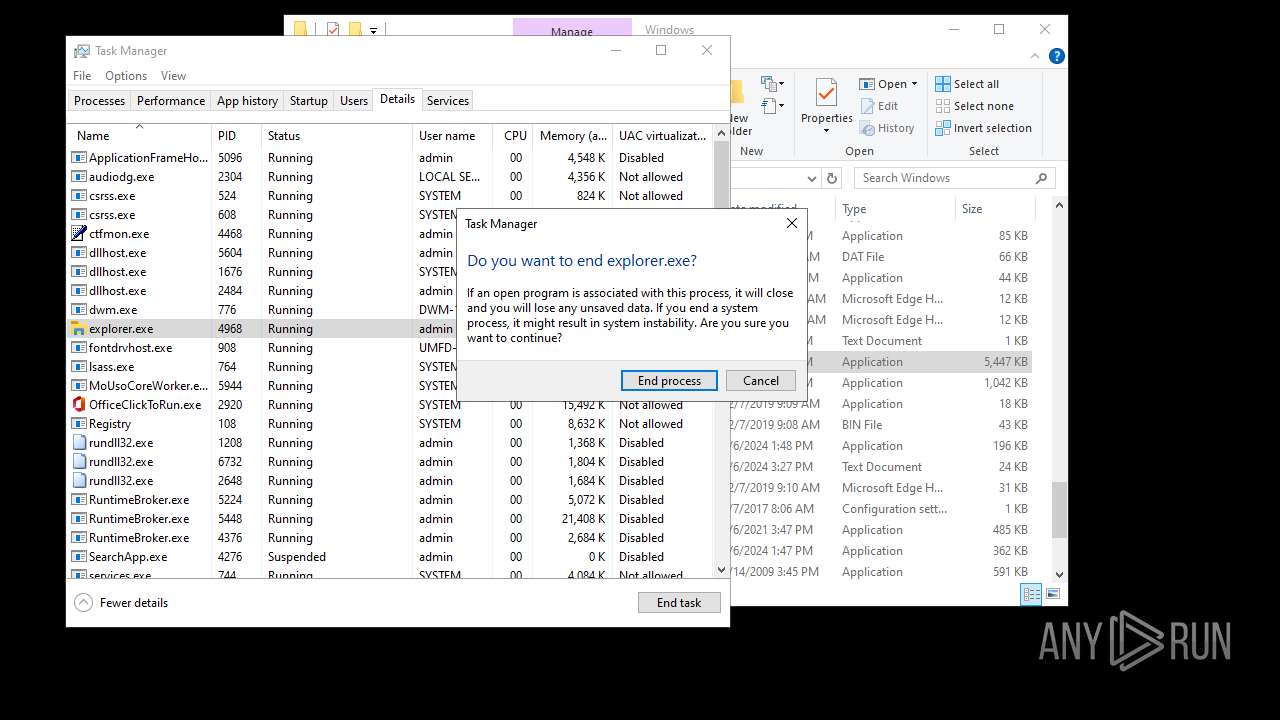
- explorer.exe (PID: 4772)
- svchost.exe (PID: 5048)
- RuntimeBroker.exe (PID: 5448)
- sihost.exe (PID: 4180)
- SearchApp.exe (PID: 5328)
- dllhost.exe (PID: 5604)
- RuntimeBroker.exe (PID: 4376)
- ApplicationFrameHost.exe (PID: 5096)
- svchost.exe (PID: 6984)
- TextInputHost.exe (PID: 2772)
- dllhost.exe (PID: 2484)
- UserOOBEBroker.exe (PID: 5936)
Runs injected code in another process
- d049a62a-9f90-4627-9528-f3af29660dd5.exe (PID: 6004)
Changes the autorun value in the registry
- d049a62a-9f90-4627-9528-f3af29660dd5.exe (PID: 6004)
- explorer.exe (PID: 4772)
- explorer.exe (PID: 4968)
- explorer.exe (PID: 1180)
- explorer.exe (PID: 6584)
- explorer.exe (PID: 2132)
- explorer.exe (PID: 4348)
DIAMOTRIX has been detected (SURICATA)
- explorer.exe (PID: 4772)
- explorer.exe (PID: 1180)
- explorer.exe (PID: 6584)
- explorer.exe (PID: 2132)
- explorer.exe (PID: 4348)
SUSPICIOUS
Found regular expressions for crypto-addresses (YARA)
- d049a62a-9f90-4627-9528-f3af29660dd5.exe (PID: 6004)
- explorer.exe (PID: 5724)
Connects to the server without a host name
- explorer.exe (PID: 4772)
- explorer.exe (PID: 4968)
- explorer.exe (PID: 1180)
- explorer.exe (PID: 6584)
- explorer.exe (PID: 2132)
- explorer.exe (PID: 4348)
Executable content was dropped or overwritten
- d049a62a-9f90-4627-9528-f3af29660dd5.exe (PID: 6004)
Creates file in the systems drive root
- explorer.exe (PID: 4968)
- explorer.exe (PID: 1180)
- explorer.exe (PID: 6584)
- explorer.exe (PID: 2132)
- explorer.exe (PID: 4348)
Application launched itself
- explorer.exe (PID: 4968)
- explorer.exe (PID: 2132)
- explorer.exe (PID: 4348)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 1984)
- SearchApp.exe (PID: 4276)
- StartMenuExperienceHost.exe (PID: 5316)
- SearchApp.exe (PID: 1984)
- SearchApp.exe (PID: 3640)
- StartMenuExperienceHost.exe (PID: 7072)
Reads security settings of Internet Explorer
- StartMenuExperienceHost.exe (PID: 1984)
- StartMenuExperienceHost.exe (PID: 5316)
- StartMenuExperienceHost.exe (PID: 7072)
INFO
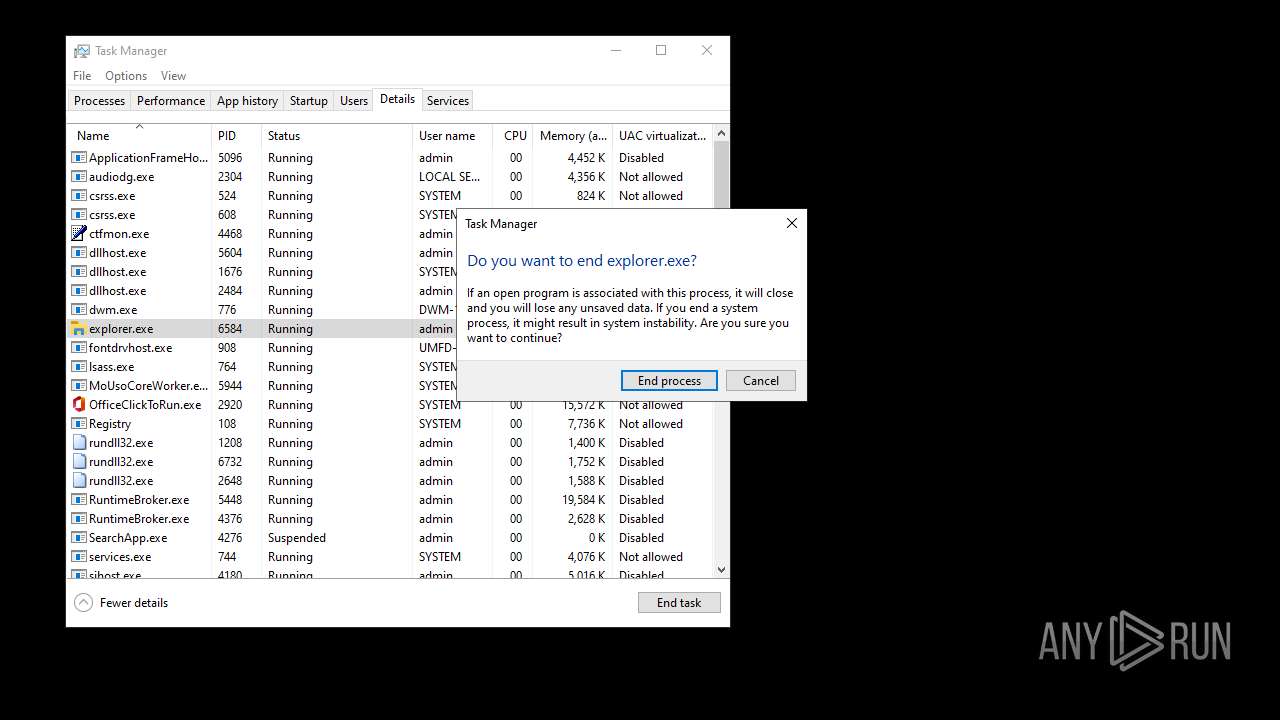
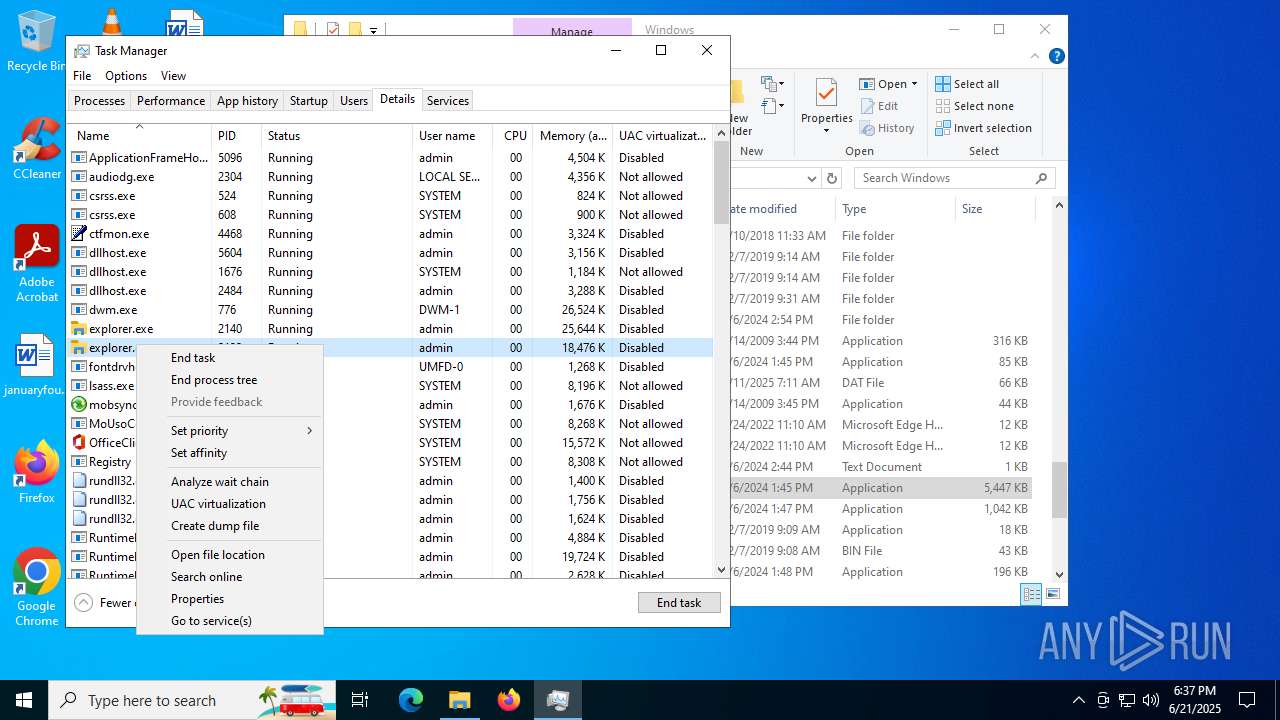
Manual execution by a user
- Taskmgr.exe (PID: 6360)
- Taskmgr.exe (PID: 1644)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
- Taskmgr.exe (PID: 6360)
- explorer.exe (PID: 5724)
- explorer.exe (PID: 4968)
- explorer.exe (PID: 1180)
- RuntimeBroker.exe (PID: 5224)
- explorer.exe (PID: 6584)
- explorer.exe (PID: 2132)
- explorer.exe (PID: 2140)
- explorer.exe (PID: 4348)
- explorer.exe (PID: 1012)
- RuntimeBroker.exe (PID: 5448)
Checks supported languages
- d049a62a-9f90-4627-9528-f3af29660dd5.exe (PID: 6004)
- TextInputHost.exe (PID: 6620)
- StartMenuExperienceHost.exe (PID: 1984)
- SearchApp.exe (PID: 4276)
- StartMenuExperienceHost.exe (PID: 5316)
- SearchApp.exe (PID: 1984)
- TextInputHost.exe (PID: 3504)
- StartMenuExperienceHost.exe (PID: 7072)
- SearchApp.exe (PID: 3640)
- TextInputHost.exe (PID: 2708)
Reads the computer name
- d049a62a-9f90-4627-9528-f3af29660dd5.exe (PID: 6004)
- TextInputHost.exe (PID: 6620)
- StartMenuExperienceHost.exe (PID: 1984)
- SearchApp.exe (PID: 4276)
- TextInputHost.exe (PID: 3504)
- StartMenuExperienceHost.exe (PID: 5316)
- SearchApp.exe (PID: 1984)
- SearchApp.exe (PID: 3640)
- TextInputHost.exe (PID: 2708)
- StartMenuExperienceHost.exe (PID: 7072)
Reads the machine GUID from the registry
- StartMenuExperienceHost.exe (PID: 5160)
- d049a62a-9f90-4627-9528-f3af29660dd5.exe (PID: 6004)
- TextInputHost.exe (PID: 2772)
- SearchApp.exe (PID: 4276)
- SearchApp.exe (PID: 1984)
- SearchApp.exe (PID: 3640)
Creates files in the program directory
- d049a62a-9f90-4627-9528-f3af29660dd5.exe (PID: 6004)
Launching a file from a Registry key
- d049a62a-9f90-4627-9528-f3af29660dd5.exe (PID: 6004)
- explorer.exe (PID: 4772)
- explorer.exe (PID: 4968)
- explorer.exe (PID: 1180)
- explorer.exe (PID: 6584)
- explorer.exe (PID: 2132)
- explorer.exe (PID: 4348)
Checks proxy server information
- explorer.exe (PID: 4772)
- explorer.exe (PID: 4968)
- explorer.exe (PID: 1180)
- slui.exe (PID: 1740)
- SearchApp.exe (PID: 4276)
- explorer.exe (PID: 5724)
- explorer.exe (PID: 2132)
- explorer.exe (PID: 6584)
- SearchApp.exe (PID: 1984)
- explorer.exe (PID: 4348)
- explorer.exe (PID: 2140)
- SearchApp.exe (PID: 3640)
- explorer.exe (PID: 1012)
Process checks computer location settings
- SearchApp.exe (PID: 4276)
- StartMenuExperienceHost.exe (PID: 1984)
- StartMenuExperienceHost.exe (PID: 5316)
- SearchApp.exe (PID: 1984)
- StartMenuExperienceHost.exe (PID: 7072)
- SearchApp.exe (PID: 3640)
Creates files or folders in the user directory
- dllhost.exe (PID: 5604)
- explorer.exe (PID: 5724)
- explorer.exe (PID: 2140)
Reads Environment values
- SearchApp.exe (PID: 4276)
- SearchApp.exe (PID: 1984)
- SearchApp.exe (PID: 3640)
Reads the software policy settings
- slui.exe (PID: 1740)
- SearchApp.exe (PID: 4276)
- SearchApp.exe (PID: 1984)
- SearchApp.exe (PID: 3640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:21 18:36:12+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 55808 |
| InitializedDataSize: | 541184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e78 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
169
Monitored processes
44
Malicious processes
8
Suspicious processes
15
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\explorer.exe /factory,{682159d9-c321-47ca-b3f1-30e36b2ec8b9} -Embedding | C:\Windows\explorer.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {3eef301f-b596-4c0b-bd92-013beafce793} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1644 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1984 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1984 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | C:\WINDOWS\explorer.exe /factory,{682159d9-c321-47ca-b3f1-30e36b2ec8b9} -Embedding | C:\Windows\explorer.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
148 734
Read events
147 640
Write events
1 030
Delete events
64
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000040302 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 58FB566800000000 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | write | Name: | Classes |
Value: .accdb | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\ShellNew |
| Operation: | write | Name: | ~reserved~ |
Value: 0800000000000600 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | Mode |
Value: 1 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | LogicalViewMode |
Value: 3 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconSize |
Value: 48 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | Sort |
Value: 0000000000000000000000000000000000000000 | |||
Executable files
5
Suspicious files
51
Text files
124
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 4276 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\Q84V0JUH\6hU_LneafI_NFLeDvM367ebFaKQ[1].js | binary | |
MD5:C6C21B7634D82C53FB86080014D86E66 | SHA256:D39E9BA92B07F4D50B11A49965E9B162452D7B9C9F26D9DCB07825727E31057E | |||
| 4276 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\-M-8YWX0KlEtdAHVrkTvKQHOghs[1].js | binary | |
MD5:32EE4742328DFB725F3A96641B93B344 | SHA256:061E63AF37D22CCEF7FB5BB9BEABA0DF2F36B64F985BB8A408638846C895D0A7 | |||
| 4276 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:E94E94EE341E842F4BF5A9B0B72A1CC7 | SHA256:361BE048702D2711E5A76B8C6AA6EC3FC6E29642028890B5CC02C7E60A22D4B5 | |||
| 4276 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\FgBbpIj0thGWZOh_xFnM9i4O7ek[1].css | text | |
MD5:908111EB0FFB1360D5DD61279C21703E | SHA256:1ED87CF425DED994B05A842271AB4D28A76F399E571688CF2E7B186F70DC3059 | |||
| 4276 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:5814FB3283BA2E87B2905F398EC4820F | SHA256:327AF313367DC72913A0386E74F1BA9A86F479E9DAA551E48C75533EDAC3C3C2 | |||
| 6360 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 4276 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\3-X3h7uDMtfcne46mFDSZyqDAWs.br[1].js | binary | |
MD5:E766B650487DC4BC853C0DF56D828A34 | SHA256:5294321F5371681E306FE4FB2D8FD9E6E4829BB27FB6338C6F3FABF19DF2FCBA | |||
| 4276 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\AptopUBu7_oVDubJxwvaIprW-lI[1].css | text | |
MD5:4E0E75684C84C0102CED12948B95609B | SHA256:4D18E491B2DE4DA34F6C15F0574911613E902F791FE72501E4404802760D1BCA | |||
| 4276 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\NajusmjIqB4kdLn9FmVxeS4xi2o[1].css | text | |
MD5:73D1CEBD8E3B6C7246F422D624EDF803 | SHA256:0674786CF9978A1F9065F57D98E986070C7CBB5177F154F40E8A924C0E0C13F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
49
DNS requests
23
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2292 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3608 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3608 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4968 | explorer.exe | POST | 200 | 185.156.72.89:80 | http://185.156.72.89/nzcwzue/pqrfxn.php | unknown | — | — | unknown |
4772 | explorer.exe | POST | 200 | 185.156.72.89:80 | http://185.156.72.89/nzcwzue/pqrfxn.php | unknown | — | — | unknown |
4276 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
6584 | explorer.exe | POST | 200 | 185.156.72.89:80 | http://185.156.72.89/nzcwzue/pqrfxn.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1512 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2292 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2292 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4772 | explorer.exe | A Network Trojan was detected | ET MALWARE Diamotrix POST Request M3 |
1180 | explorer.exe | A Network Trojan was detected | ET MALWARE Diamotrix POST Request M3 |
6584 | explorer.exe | A Network Trojan was detected | ET MALWARE Diamotrix POST Request M3 |
2132 | explorer.exe | A Network Trojan was detected | ET MALWARE Diamotrix POST Request M3 |
4348 | explorer.exe | A Network Trojan was detected | ET MALWARE Diamotrix POST Request M3 |
4348 | explorer.exe | A Network Trojan was detected | ET MALWARE Diamotrix POST Request M3 |