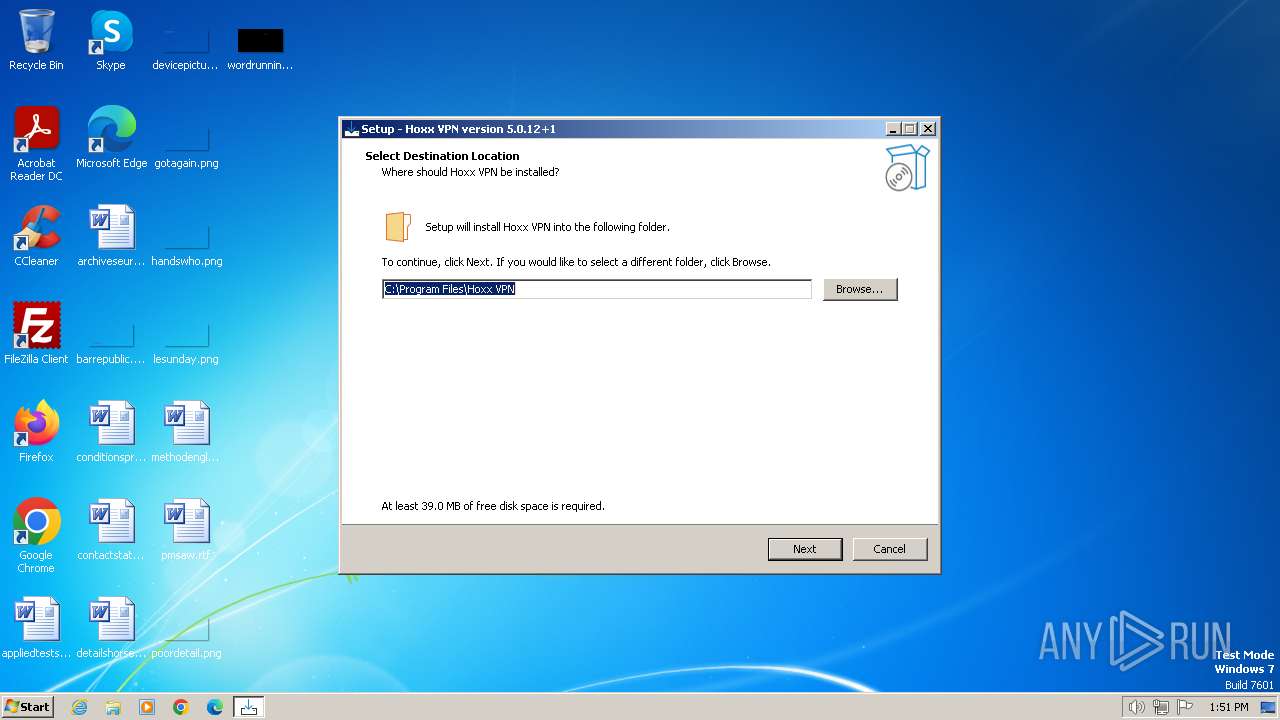
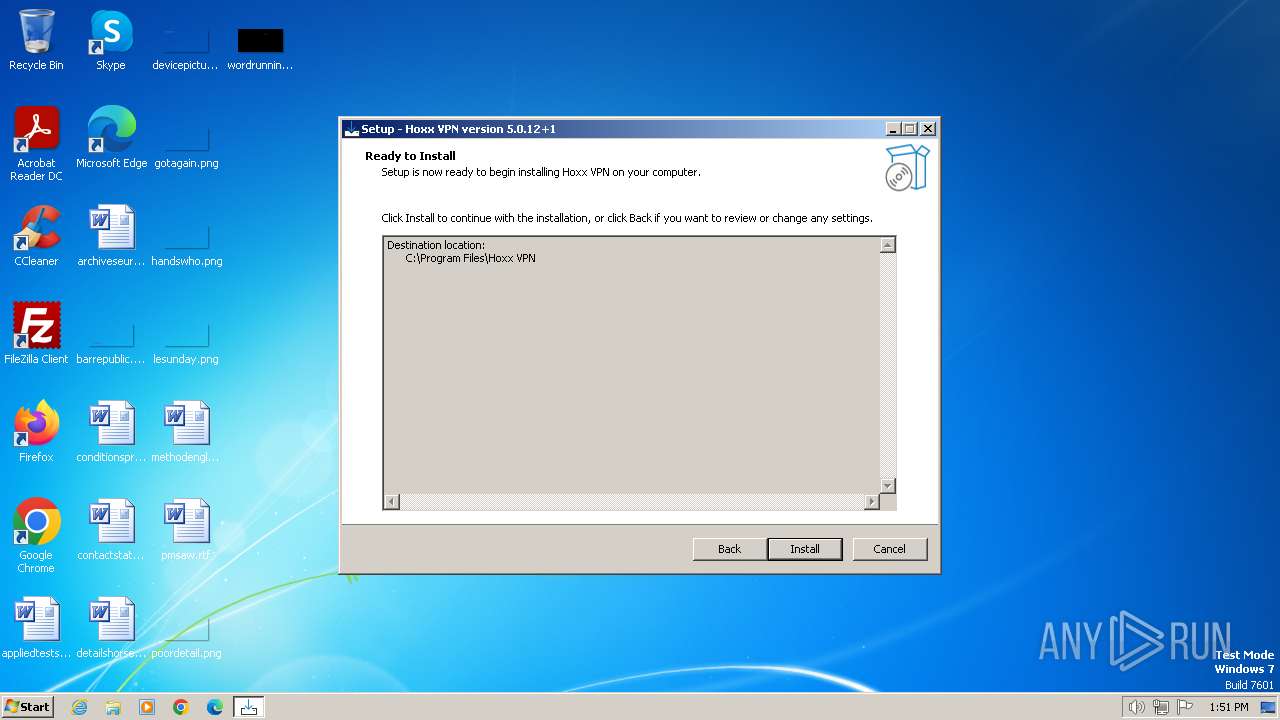
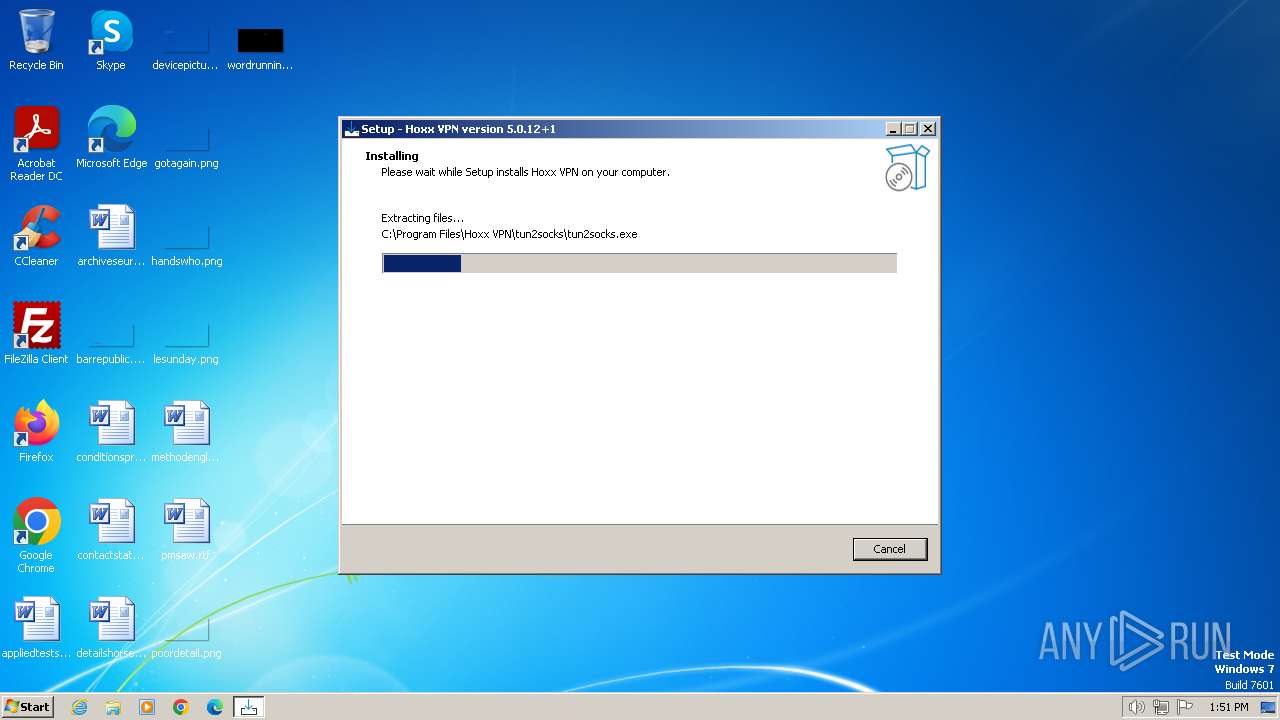
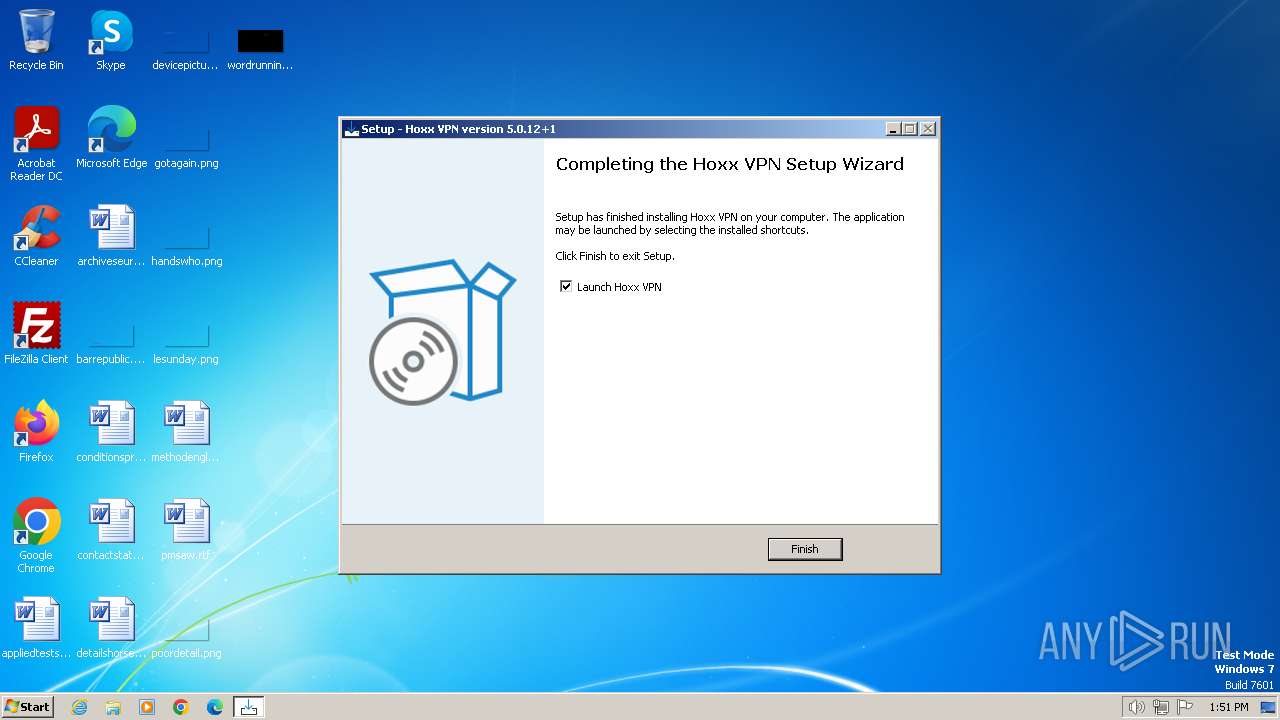
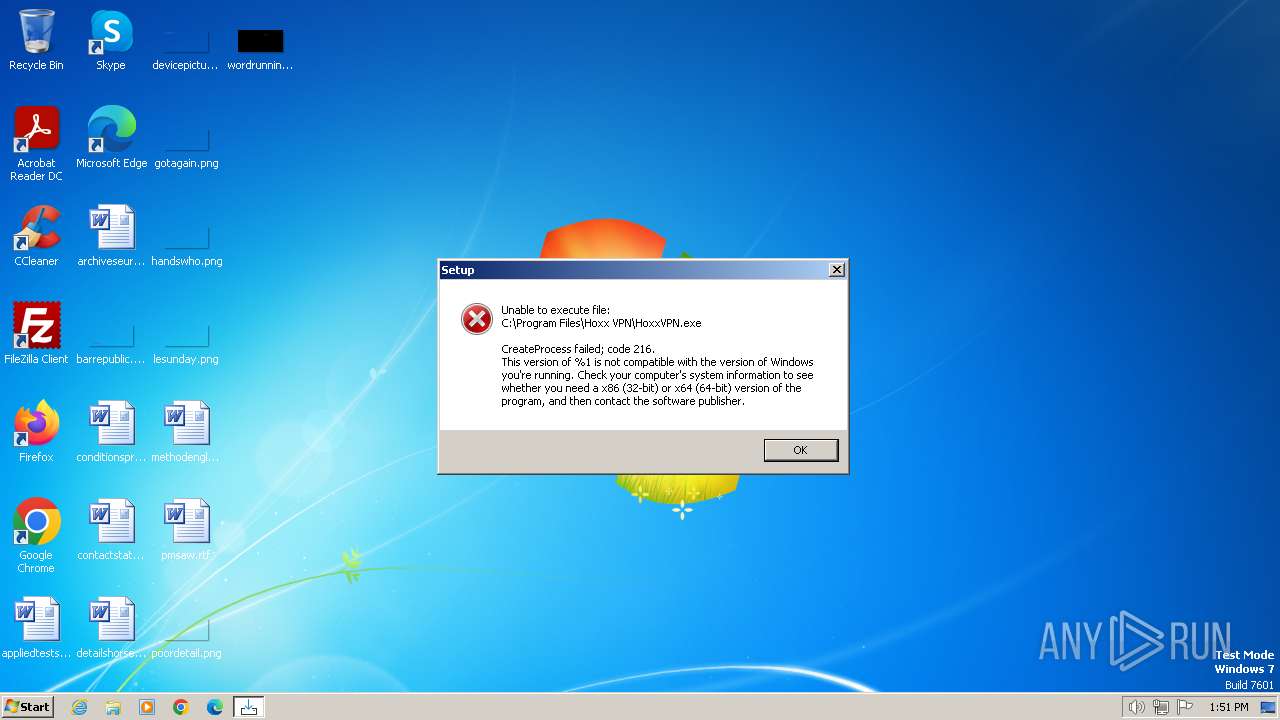
| File name: | HoxxVPN.exe |
| Full analysis: | https://app.any.run/tasks/ed538aff-9829-4c2d-8266-695a36943e7b |
| Verdict: | Malicious activity |
| Analysis date: | March 18, 2024, 13:51:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 47FFC2D4C1D245C0389A35C239330FB4 |
| SHA1: | 0CAAFE722071E068E501C2B601260FB0B99C3034 |
| SHA256: | 2D186F5614D371744FF1D63D9B5FD7EDE2F3F9DC1E64EC9660686965C2CC3007 |
| SSDEEP: | 98304:9+cD4dnyF0+Ek3YHg44kjCzpOLKHZ/jUzCbeORcdIJQF1d2X8y87AjqlAbqAwtF9:uDI+wL5iguKQGlvXro7PiA0x6wOClm |
MALICIOUS
Drops the executable file immediately after the start
- HoxxVPN.exe (PID: 4008)
- HoxxVPN.exe (PID: 3180)
- HoxxVPN.tmp (PID: 2792)
- tapinstall.exe (PID: 1848)
- drvinst.exe (PID: 2772)
- drvinst.exe (PID: 2416)
Starts NET.EXE for service management
- cmd.exe (PID: 1808)
- net.exe (PID: 2488)
- net.exe (PID: 2968)
- HoxxVPN.tmp (PID: 2792)
- net.exe (PID: 240)
Creates a writable file in the system directory
- drvinst.exe (PID: 2772)
- drvinst.exe (PID: 2416)
Changes the autorun value in the registry
- drvinst.exe (PID: 2416)
SUSPICIOUS
Executable content was dropped or overwritten
- HoxxVPN.exe (PID: 4008)
- HoxxVPN.exe (PID: 3180)
- tapinstall.exe (PID: 1848)
- drvinst.exe (PID: 2772)
- drvinst.exe (PID: 2416)
- HoxxVPN.tmp (PID: 2792)
Reads the Windows owner or organization settings
- HoxxVPN.tmp (PID: 2792)
Uses TASKKILL.EXE to kill process
- HoxxVPN.tmp (PID: 2792)
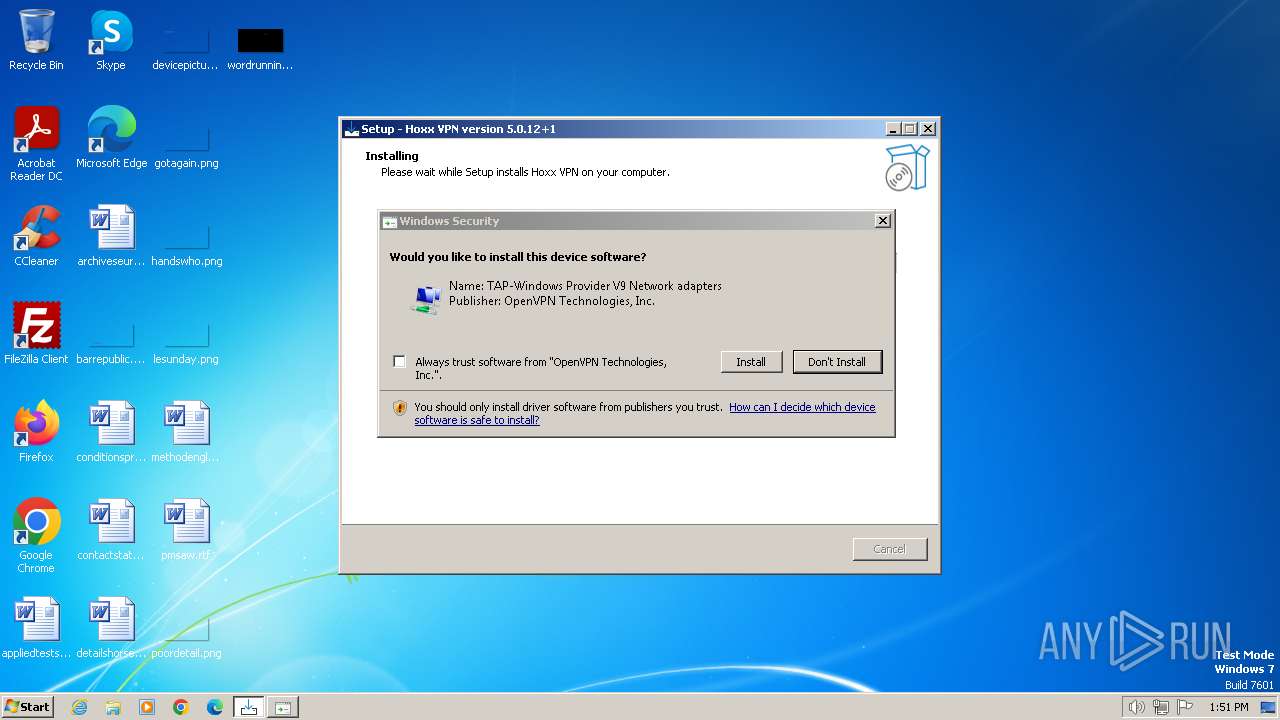
Drops a system driver (possible attempt to evade defenses)
- HoxxVPN.tmp (PID: 2792)
- tapinstall.exe (PID: 1848)
- drvinst.exe (PID: 2772)
- drvinst.exe (PID: 2416)
Process drops legitimate windows executable
- HoxxVPN.tmp (PID: 2792)
The process drops C-runtime libraries
- HoxxVPN.tmp (PID: 2792)
Reads the Internet Settings
- HoxxVPN.tmp (PID: 2792)
- powershell.exe (PID: 4056)
Starts CMD.EXE for commands execution
- HoxxVPN.tmp (PID: 2792)
- cmd.exe (PID: 1236)
Reads security settings of Internet Explorer
- HoxxVPN.tmp (PID: 2792)
- tapinstall.exe (PID: 1848)
Executing commands from a ".bat" file
- HoxxVPN.tmp (PID: 2792)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 1236)
Starts SC.EXE for service management
- cmd.exe (PID: 1808)
- cmd.exe (PID: 1484)
Executes as Windows Service
- HoxxVPNService.exe (PID: 2780)
- VSSVC.exe (PID: 2640)
Reads settings of System Certificates
- tapinstall.exe (PID: 1848)
- rundll32.exe (PID: 1792)
Checks Windows Trust Settings
- tapinstall.exe (PID: 1848)
- drvinst.exe (PID: 2772)
- drvinst.exe (PID: 2416)
Creates files in the driver directory
- drvinst.exe (PID: 2772)
- drvinst.exe (PID: 2416)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1236)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1236)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1236)
Application launched itself
- cmd.exe (PID: 1236)
Process uses powershell cmdlet to discover network configuration
- cmd.exe (PID: 1236)
Non-standard symbols in registry
- HoxxVPN.tmp (PID: 2792)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 4056)
INFO
Create files in a temporary directory
- HoxxVPN.exe (PID: 4008)
- HoxxVPN.exe (PID: 3180)
- tapinstall.exe (PID: 1848)
Reads the computer name
- HoxxVPN.tmp (PID: 1692)
- HoxxVPN.tmp (PID: 2792)
- HoxxVPNService.exe (PID: 2780)
- tapinstall.exe (PID: 1848)
- drvinst.exe (PID: 2416)
- drvinst.exe (PID: 2772)
- wmpnscfg.exe (PID: 2244)
Checks supported languages
- HoxxVPN.exe (PID: 4008)
- HoxxVPN.exe (PID: 3180)
- HoxxVPN.tmp (PID: 1692)
- HoxxVPN.tmp (PID: 2792)
- HoxxVPNService.exe (PID: 2780)
- tapinstall.exe (PID: 1848)
- drvinst.exe (PID: 2772)
- drvinst.exe (PID: 2416)
- wmpnscfg.exe (PID: 2244)
Creates files in the program directory
- HoxxVPN.tmp (PID: 2792)
Creates a software uninstall entry
- HoxxVPN.tmp (PID: 2792)
Reads the machine GUID from the registry
- tapinstall.exe (PID: 1848)
- drvinst.exe (PID: 2772)
- HoxxVPNService.exe (PID: 2780)
- drvinst.exe (PID: 2416)
Reads the software policy settings
- tapinstall.exe (PID: 1848)
- drvinst.exe (PID: 2772)
- rundll32.exe (PID: 1792)
- drvinst.exe (PID: 2416)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 1792)
Reads Environment values
- drvinst.exe (PID: 2416)
Application launched itself
- iexplore.exe (PID: 2820)
Manual execution by a user
- wmpnscfg.exe (PID: 2244)
- iexplore.exe (PID: 2820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.0.12.1 |
| ProductVersionNumber: | 5.0.12.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Hoxx VPN, Inc. |
| FileDescription: | Hoxx VPN Setup |
| FileVersion: | 5.0.12.1 |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Hoxx VPN |
| ProductVersion: | 5.0.12+1 |
Total processes
95
Monitored processes
48
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "net" stop HoxxVPNService | C:\Windows\System32\net.exe | — | HoxxVPN.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | C:\Windows\system32\cmd.exe /c type ""C:\Users\admin\AppData\Local\Temp\netadapters.txt"" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 884 | reg query HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Network\{4D36E972-E325-11CE-BFC1-08002BE10318}\{666053B8-8CCD-4235-8E63-DEC78EF9E7CA}\Connection /v "Name" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 980 | sc delete HoxxVPNService | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | findstr "HKEY.*\\[0-9][0-9][0-9][0-9]f7f81a39-5f63-5b42-9efd-1f13b5431005quot; | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1236 | "C:\Windows\system32\cmd.exe" /C "C:\Program Files\Hoxx VPN\add_tap_hx_device.bat" | C:\Windows\System32\cmd.exe | — | HoxxVPN.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1336 | C:\Windows\system32\net1 stop HoxxVPNService | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1376 | C:\Windows\system32\cmd.exe /c reg query HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Network\{4D36E972-E325-11CE-BFC1-08002BE10318}\{666053B8-8CCD-4235-8E63-DEC78EF9E7CA}\Connection /v "Name" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1484 | "C:\Windows\system32\cmd.exe" /C sc query HoxxVPNService | C:\Windows\System32\cmd.exe | — | HoxxVPN.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1572 | C:\Windows\system32\net1 stop HoxxVPNService | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
53 807
Read events
52 645
Write events
1 083
Delete events
79
Modification events
| (PID) Process: | (2792) HoxxVPN.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: E80A00007CCAE2593B79DA01 | |||
| (PID) Process: | (2792) HoxxVPN.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 7AE70910DE708A1CCD239D886071C80E29B22551EB6C3F6830507D2C18FA983F | |||
| (PID) Process: | (2792) HoxxVPN.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2792) HoxxVPN.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.myp\OpenWithProgids |
| Operation: | write | Name: | HoxxVPNFile.myp |
Value: | |||
| (PID) Process: | (2792) HoxxVPN.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\HoxxVPN.exe\SupportedTypes |
| Operation: | write | Name: | .myp |
Value: | |||
| (PID) Process: | (2792) HoxxVPN.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Hoxx VPN_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (2792) HoxxVPN.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Hoxx VPN_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Hoxx VPN | |||
| (PID) Process: | (2792) HoxxVPN.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Hoxx VPN_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Hoxx VPN\ | |||
| (PID) Process: | (2792) HoxxVPN.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Hoxx VPN_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (2792) HoxxVPN.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Hoxx VPN_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
54
Suspicious files
59
Text files
559
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2792 | HoxxVPN.tmp | C:\Program Files\Hoxx VPN\is-H10TD.tmp | text | |
MD5:CDFABEAE415EB1154A786635E9D87AB7 | SHA256:026B9A80ECE2E892DB472F57FA7F37DF9D7576D09B51539FA7B415DE71AE783F | |||
| 2792 | HoxxVPN.tmp | C:\Program Files\Hoxx VPN\is-9NTU0.tmp | executable | |
MD5:5D1E390249713E7A920BAE501C110FC0 | SHA256:69C4F083E09D3394065355CBAEDE698D9AFFEF41E7B16BD92FFDA99E6ED5D7A9 | |||
| 2792 | HoxxVPN.tmp | C:\Program Files\Hoxx VPN\tap-windows6\is-6359M.tmp | executable | |
MD5:F49967C396969B71C3A72537DB03A68B | SHA256:3B1FF5252012D6E8A7DD6E4621EC43812510DCA1A25A9A2E07288800F445DD41 | |||
| 2792 | HoxxVPN.tmp | C:\Program Files\Hoxx VPN\unins000.exe | executable | |
MD5:5D1E390249713E7A920BAE501C110FC0 | SHA256:69C4F083E09D3394065355CBAEDE698D9AFFEF41E7B16BD92FFDA99E6ED5D7A9 | |||
| 3180 | HoxxVPN.exe | C:\Users\admin\AppData\Local\Temp\is-S2SFO.tmp\HoxxVPN.tmp | executable | |
MD5:5D1E390249713E7A920BAE501C110FC0 | SHA256:69C4F083E09D3394065355CBAEDE698D9AFFEF41E7B16BD92FFDA99E6ED5D7A9 | |||
| 2792 | HoxxVPN.tmp | C:\Program Files\Hoxx VPN\tap-windows6\is-V75IK.tmp | binary | |
MD5:41884571579F88540326252B81D0A9F8 | SHA256:A461B764E248D3E59A1A730FF94AF7E61121F5A02004E02B3B866AC8FD1689BE | |||
| 2792 | HoxxVPN.tmp | C:\Program Files\Hoxx VPN\tap-windows6\is-EC1PT.tmp | executable | |
MD5:F8578C73BA8BBC356B13F28CE00396AA | SHA256:ADDE2601408DC3CAA3450E1B7D86A8D434C4B3EAA9654C7E69E0F33122C37DA6 | |||
| 2792 | HoxxVPN.tmp | C:\Program Files\Hoxx VPN\tap-windows6\is-U67L3.tmp | binary | |
MD5:AD8A5CBEC4F83AE4F850C793713EE770 | SHA256:878C1B205887B61906F6F4F8DA5783D2BB8756D0A39359288D09F65F983B27C2 | |||
| 2792 | HoxxVPN.tmp | C:\Program Files\Hoxx VPN\tap-windows6\OemVista.inf | binary | |
MD5:41884571579F88540326252B81D0A9F8 | SHA256:A461B764E248D3E59A1A730FF94AF7E61121F5A02004E02B3B866AC8FD1689BE | |||
| 2792 | HoxxVPN.tmp | C:\Program Files\Hoxx VPN\tap-windows6\tap0901.cat | binary | |
MD5:AD8A5CBEC4F83AE4F850C793713EE770 | SHA256:878C1B205887B61906F6F4F8DA5783D2BB8756D0A39359288D09F65F983B27C2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
38
DNS requests
21
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2820 | iexplore.exe | GET | 304 | 173.222.108.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c6068a55e9009b7c | unknown | — | — | unknown |
2820 | iexplore.exe | GET | 304 | 173.222.108.210:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53cb56c193829b96 | unknown | — | — | unknown |
2820 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
1080 | svchost.exe | GET | 304 | 173.222.108.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?44b9e679153a488c | unknown | compressed | 67.5 Kb | unknown |
2820 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 173.222.108.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?03219f268fa049c1 | unknown | compressed | 67.5 Kb | unknown |
3428 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
2820 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
2820 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
3428 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2836 | netsh.exe | 1.1.1.1:53 | — | CLOUDFLARENET | — | unknown |
3876 | netsh.exe | 9.9.9.9:53 | — | QUAD9-AS-1 | US | unknown |
2820 | iexplore.exe | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | unknown |
2820 | iexplore.exe | 173.222.108.210:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
2820 | iexplore.exe | 173.222.108.226:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
2820 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |