| File name: | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe |
| Full analysis: | https://app.any.run/tasks/186934c0-d0a0-4848-a63d-d8ce08adf25e |
| Verdict: | Malicious activity |
| Analysis date: | March 03, 2024, 23:25:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 47FFC2D4C1D245C0389A35C239330FB4 |
| SHA1: | 0CAAFE722071E068E501C2B601260FB0B99C3034 |
| SHA256: | 2D186F5614D371744FF1D63D9B5FD7EDE2F3F9DC1E64EC9660686965C2CC3007 |
| SSDEEP: | 98304:9+cD4dnyF0+Ek3YHg44kjCzpOLKHZ/jUzCbeORcdIJQF1d2X8y87AjqlAbqAwtF9:uDI+wL5iguKQGlvXro7PiA0x6wOClm |
MALICIOUS
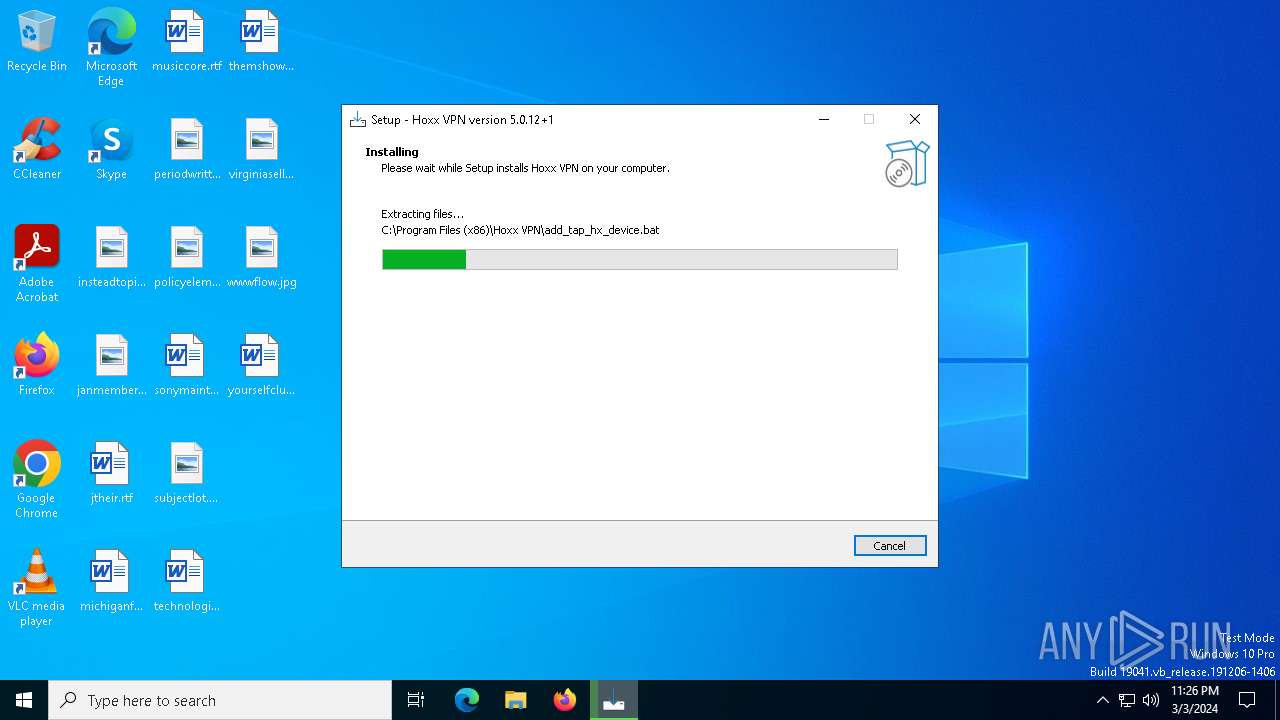
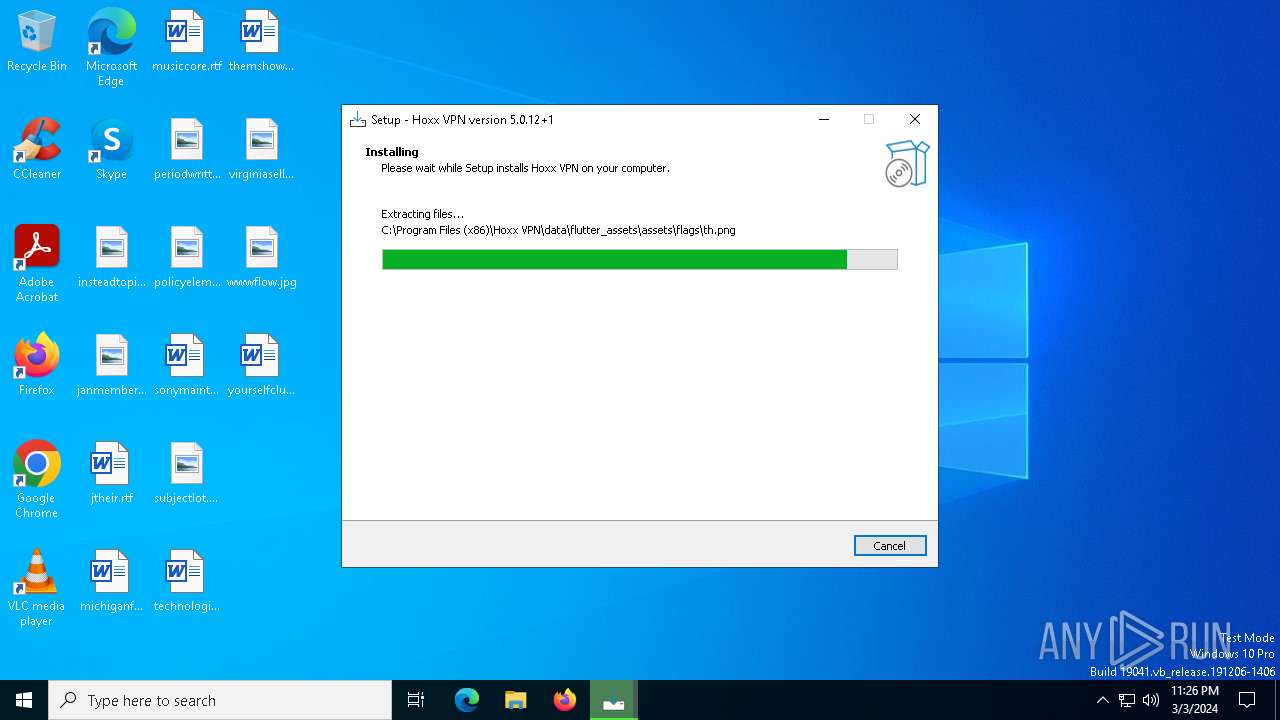
Drops the executable file immediately after the start
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe (PID: 5992)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe (PID: 1392)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
- tapinstall.exe (PID: 4844)
- drvinst.exe (PID: 4136)
- drvinst.exe (PID: 4140)
Starts NET.EXE for service management
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
- net.exe (PID: 5580)
- cmd.exe (PID: 1852)
- net.exe (PID: 4924)
- net.exe (PID: 5396)
Creates a writable file in the system directory
- drvinst.exe (PID: 4136)
- drvinst.exe (PID: 4140)
SUSPICIOUS
Executable content was dropped or overwritten
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe (PID: 5992)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe (PID: 1392)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
- tapinstall.exe (PID: 4844)
- drvinst.exe (PID: 4136)
- drvinst.exe (PID: 4140)
Reads security settings of Internet Explorer
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6004)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
- tapinstall.exe (PID: 4844)
Reads the date of Windows installation
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6004)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
Reads the Windows owner or organization settings
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
Uses TASKKILL.EXE to kill process
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
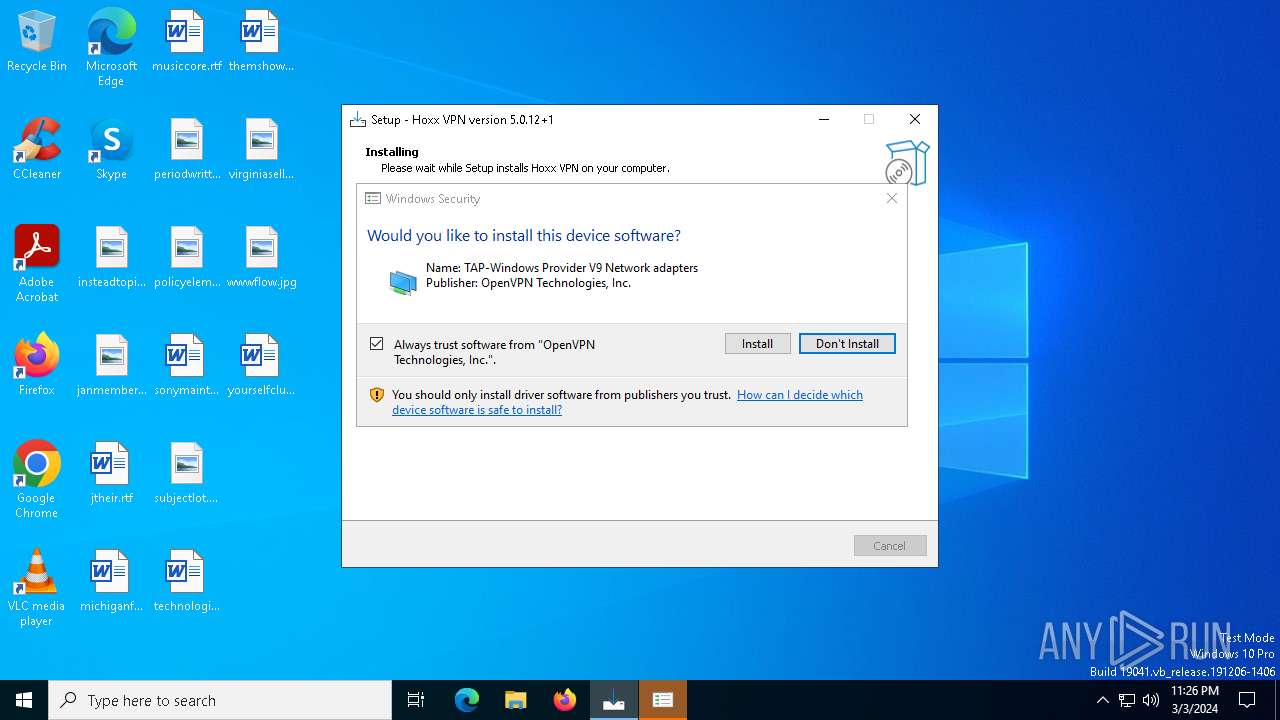
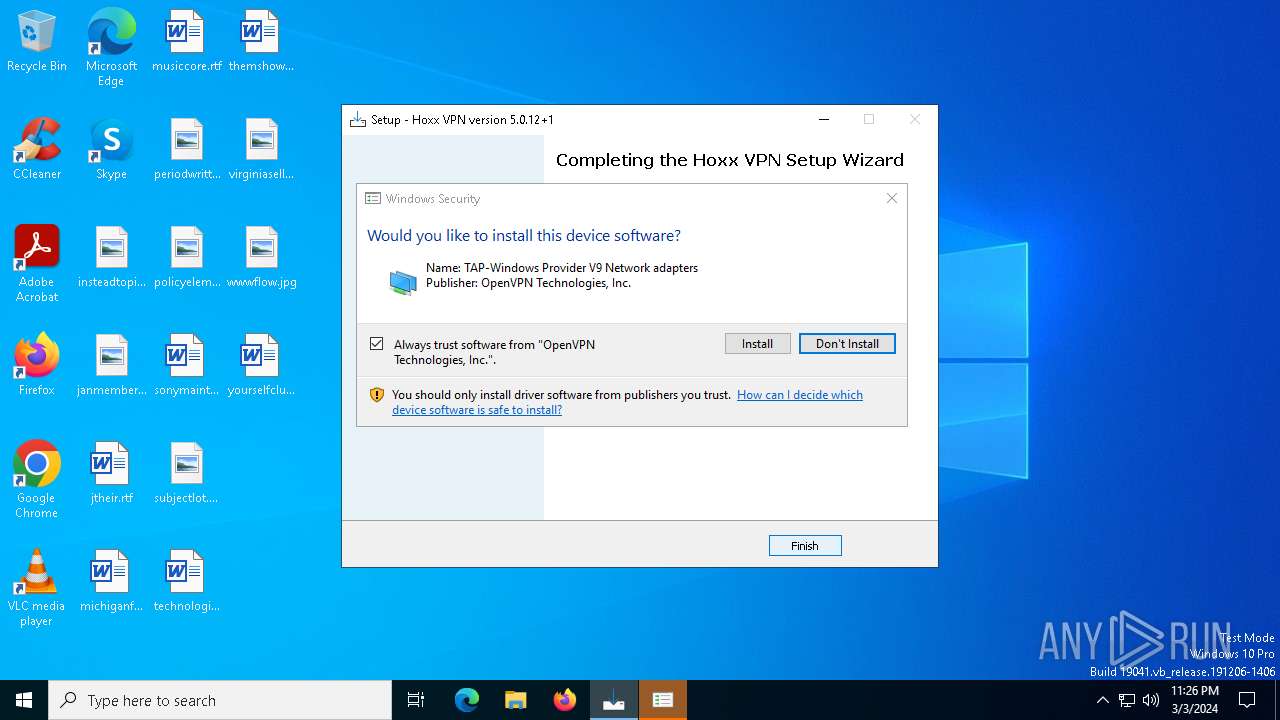
Drops a system driver (possible attempt to evade defenses)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
- tapinstall.exe (PID: 4844)
- drvinst.exe (PID: 4136)
- drvinst.exe (PID: 4140)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 2944)
Process drops legitimate windows executable
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
The process drops C-runtime libraries
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
Starts CMD.EXE for commands execution
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
- cmd.exe (PID: 2944)
Executing commands from a ".bat" file
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
Executes as Windows Service
- HoxxVPNService.exe (PID: 6928)
Checks Windows Trust Settings
- tapinstall.exe (PID: 4844)
- drvinst.exe (PID: 4136)
Creates files in the driver directory
- drvinst.exe (PID: 4136)
- drvinst.exe (PID: 4140)
Creates or modifies Windows services
- drvinst.exe (PID: 4140)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2944)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2944)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2944)
The process creates files with name similar to system file names
- powershell.exe (PID: 2868)
Application launched itself
- cmd.exe (PID: 2944)
Process uses powershell cmdlet to discover network configuration
- cmd.exe (PID: 2944)
INFO
Checks supported languages
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe (PID: 5992)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6004)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe (PID: 1392)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
- tapinstall.exe (PID: 4844)
- HoxxVPNService.exe (PID: 6928)
- drvinst.exe (PID: 4136)
- HoxxVPN.exe (PID: 4856)
- drvinst.exe (PID: 4140)
Create files in a temporary directory
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe (PID: 5992)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe (PID: 1392)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
- tapinstall.exe (PID: 4844)
Reads the computer name
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6004)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
- HoxxVPNService.exe (PID: 6928)
- tapinstall.exe (PID: 4844)
- drvinst.exe (PID: 4136)
- HoxxVPN.exe (PID: 4856)
- drvinst.exe (PID: 4140)
Process checks computer location settings
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6004)
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
Creates files in the program directory
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
Creates a software uninstall entry
- 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp (PID: 6608)
Reads the software policy settings
- tapinstall.exe (PID: 4844)
- drvinst.exe (PID: 4136)
- rundll32.exe (PID: 5428)
- slui.exe (PID: 3872)
Reads the machine GUID from the registry
- drvinst.exe (PID: 4136)
- tapinstall.exe (PID: 4844)
- HoxxVPNService.exe (PID: 6928)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 5428)
Adds/modifies Windows certificates
- drvinst.exe (PID: 4136)
Checks proxy server information
- slui.exe (PID: 3872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.0.12.1 |
| ProductVersionNumber: | 5.0.12.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
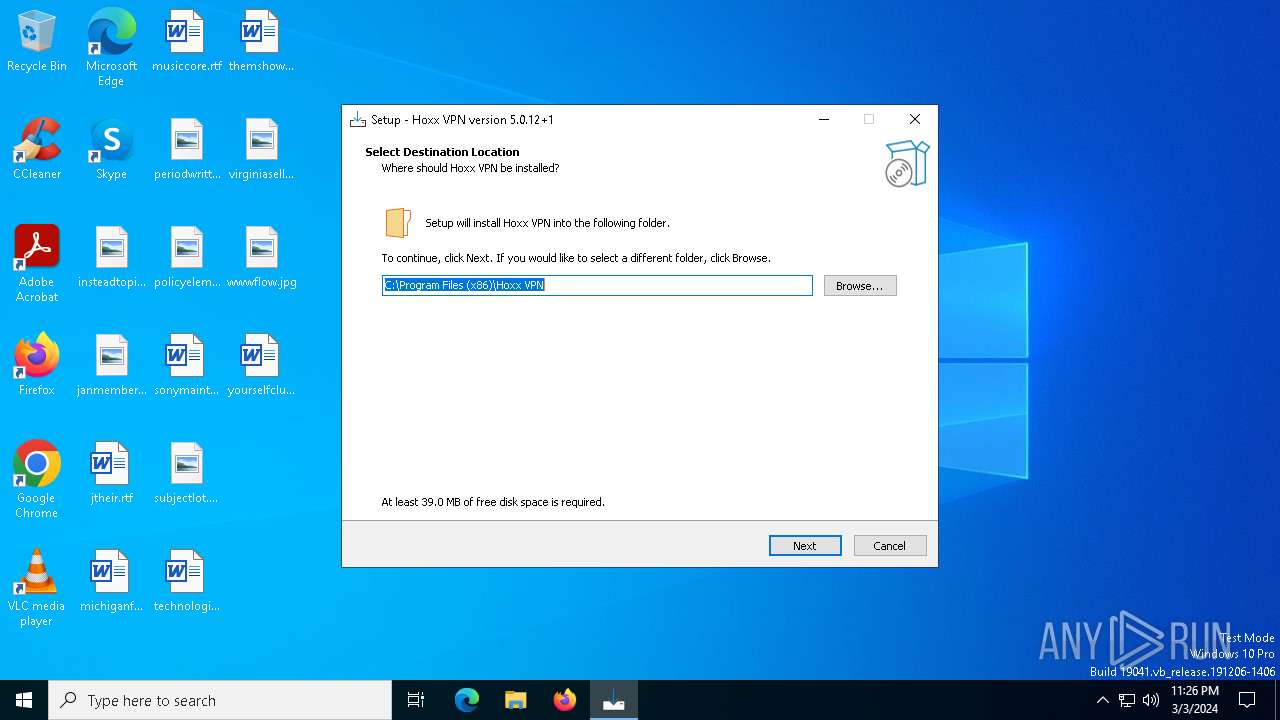
| CompanyName: | Hoxx VPN, Inc. |
| FileDescription: | Hoxx VPN Setup |
| FileVersion: | 5.0.12.1 |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Hoxx VPN |
| ProductVersion: | 5.0.12+1 |
Total processes
193
Monitored processes
52
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1392 | "C:\Users\admin\AppData\Local\Temp\2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe" /SPAWNWND=$7013C /NOTIFYWND=$9017C | C:\Users\admin\AppData\Local\Temp\2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | ||||||||||||
User: admin Company: Hoxx VPN, Inc. Integrity Level: HIGH Description: Hoxx VPN Setup Exit code: 0 Version: 5.0.12.1 Modules
| |||||||||||||||
| 1424 | find "HoxxVPN" | C:\Windows\SysWOW64\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1492 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1504 | netsh interface set interface name="Ethernet" newname="HoxxVPN" | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | netsh interface ip set dnsservers HoxxVPN static address=1.1.1.1 | C:\Windows\SysWOW64\netsh.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1576 | reg query HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Class\{4D36E972-E325-11CE-BFC1-08002BE10318}\0001 /v "NetCfgInstanceId" | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | sc query HoxxVPNService | C:\Windows\SysWOW64\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1724 | netsh interface ip show interfaces | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1744 | findstr "HKEY.*\\[0-9][0-9][0-9][0-9]f7f81a39-5f63-5b42-9efd-1f13b5431005quot; | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1852 | "C:\WINDOWS\system32\cmd.exe" /C "C:\Program Files (x86)\Hoxx VPN\install_windows_hx_service.bat" | C:\Windows\SysWOW64\cmd.exe | — | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
37 238
Read events
37 121
Write events
105
Delete events
12
Modification events
| (PID) Process: | (6608) 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: D01900001A278B33C26DDA01 | |||
| (PID) Process: | (6608) 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 3F9A8B69E3C1735A190968813816C98481CF0C2E245E9674203FF3063C1E3146 | |||
| (PID) Process: | (6608) 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6608) 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.myp\OpenWithProgids |
| Operation: | write | Name: | HoxxVPNFile.myp |
Value: | |||
| (PID) Process: | (6608) 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Applications\HoxxVPN.exe\SupportedTypes |
| Operation: | write | Name: | .myp |
Value: | |||
| (PID) Process: | (6608) 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Hoxx VPN_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (6608) 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Hoxx VPN_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
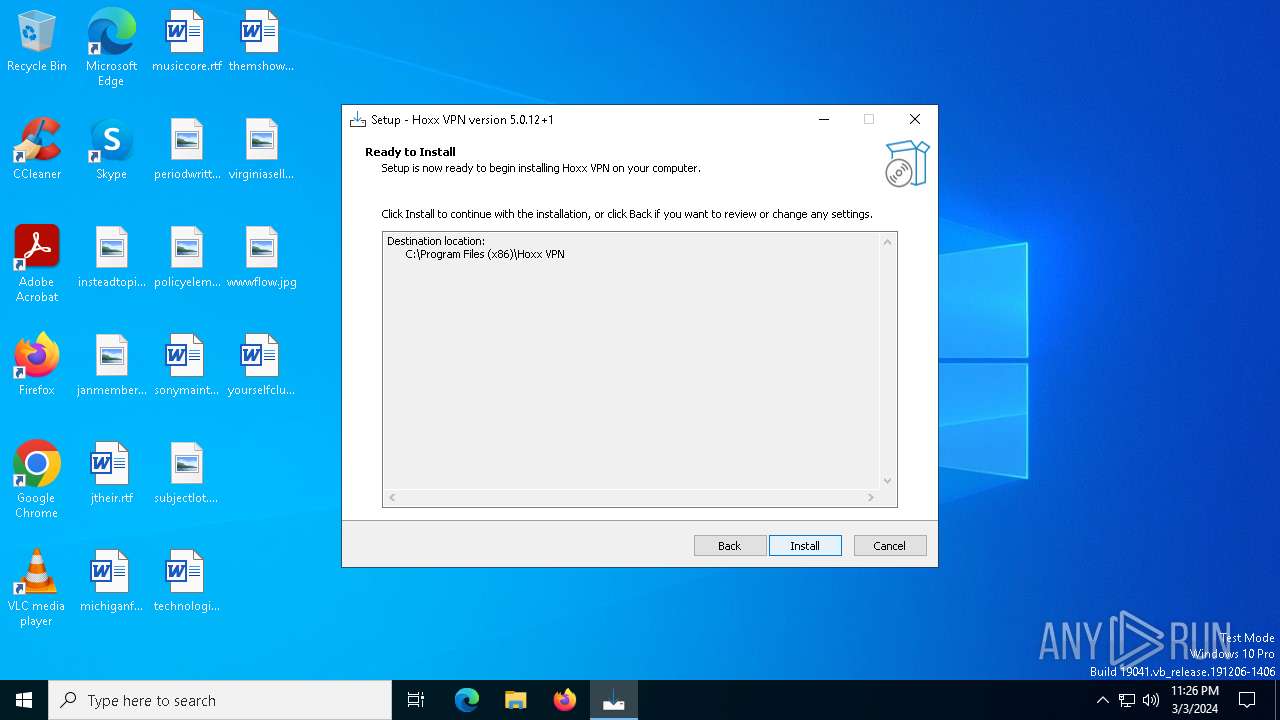
Value: C:\Program Files (x86)\Hoxx VPN | |||
| (PID) Process: | (6608) 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Hoxx VPN_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Hoxx VPN\ | |||
| (PID) Process: | (6608) 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Hoxx VPN_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (6608) 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Hoxx VPN_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
53
Suspicious files
41
Text files
533
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1392 | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe | C:\Users\admin\AppData\Local\Temp\is-D6QKO.tmp\2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | executable | |
MD5:5D1E390249713E7A920BAE501C110FC0 | SHA256:69C4F083E09D3394065355CBAEDE698D9AFFEF41E7B16BD92FFDA99E6ED5D7A9 | |||
| 6608 | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | C:\Program Files (x86)\Hoxx VPN\unins000.exe | executable | |
MD5:5D1E390249713E7A920BAE501C110FC0 | SHA256:69C4F083E09D3394065355CBAEDE698D9AFFEF41E7B16BD92FFDA99E6ED5D7A9 | |||
| 5992 | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.exe | C:\Users\admin\AppData\Local\Temp\is-CGUGA.tmp\2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | executable | |
MD5:5D1E390249713E7A920BAE501C110FC0 | SHA256:69C4F083E09D3394065355CBAEDE698D9AFFEF41E7B16BD92FFDA99E6ED5D7A9 | |||
| 6608 | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | C:\Program Files (x86)\Hoxx VPN\tap-windows6\is-5I44F.tmp | executable | |
MD5:D765F43CBEA72D14C04AF3D2B9C8E54B | SHA256:89C5CA1440DF186497CE158EB71C0C6BF570A75B6BC1880EAC7C87A0250201C0 | |||
| 6608 | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | C:\Program Files (x86)\Hoxx VPN\is-94C6J.tmp | executable | |
MD5:5D1E390249713E7A920BAE501C110FC0 | SHA256:69C4F083E09D3394065355CBAEDE698D9AFFEF41E7B16BD92FFDA99E6ED5D7A9 | |||
| 6608 | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | C:\Program Files (x86)\Hoxx VPN\tap-windows6\is-7QV8E.tmp | binary | |
MD5:87868193626DC756D10885F46D76F42E | SHA256:B5728E42EA12C67577CB9188B472005EE74399B6AC976E7F72B48409BAEE3B41 | |||
| 6608 | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | C:\Program Files (x86)\Hoxx VPN\tap-windows6\OemVista.inf | binary | |
MD5:87868193626DC756D10885F46D76F42E | SHA256:B5728E42EA12C67577CB9188B472005EE74399B6AC976E7F72B48409BAEE3B41 | |||
| 6608 | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | C:\Users\admin\AppData\Local\Temp\is-SPI6F.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6608 | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | C:\Program Files (x86)\Hoxx VPN\tap-windows6\is-CNRNT.tmp | cat | |
MD5:C757503BC0C5A6679E07FE15B93324D6 | SHA256:91EBEA8AD199E97832CF91EA77328ED7FF49A1B5C06DDAACB0E420097A9B079E | |||
| 6608 | 2d186f5614d371744ff1d63d9b5fd7ede2f3f9dc1e64ec9660686965c2cc3007.tmp | C:\Program Files (x86)\Hoxx VPN\tap-windows6\tap0901.sys | executable | |
MD5:D765F43CBEA72D14C04AF3D2B9C8E54B | SHA256:89C5CA1440DF186497CE158EB71C0C6BF570A75B6BC1880EAC7C87A0250201C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
55
DNS requests
35
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
5928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
6904 | svchost.exe | GET | 200 | 184.51.127.41:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
1248 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
1056 | svchost.exe | POST | 502 | 20.231.121.79:80 | http://dmd.metaservices.microsoft.com/metadata.svc | unknown | html | 183 b | unknown |
1056 | svchost.exe | POST | 302 | 184.25.196.202:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
2464 | svchost.exe | GET | 200 | 23.218.185.6:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5184 | SearchApp.exe | 2.18.255.53:443 | — | Akamai International B.V. | IT | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
6904 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6896 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5928 | svchost.exe | 20.190.160.22:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3848 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
5928 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6904 | svchost.exe | 184.51.127.41:80 | crl.microsoft.com | Akamai International B.V. | IT | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
okog.volume.pics |
| unknown |
vsxm.experts.pics |
| unknown |
sublimity.uk |
| unknown |
january2024.uk |
| unknown |
therewego.uk |
| unknown |
eggx.letting.cc |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2136 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2136 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |