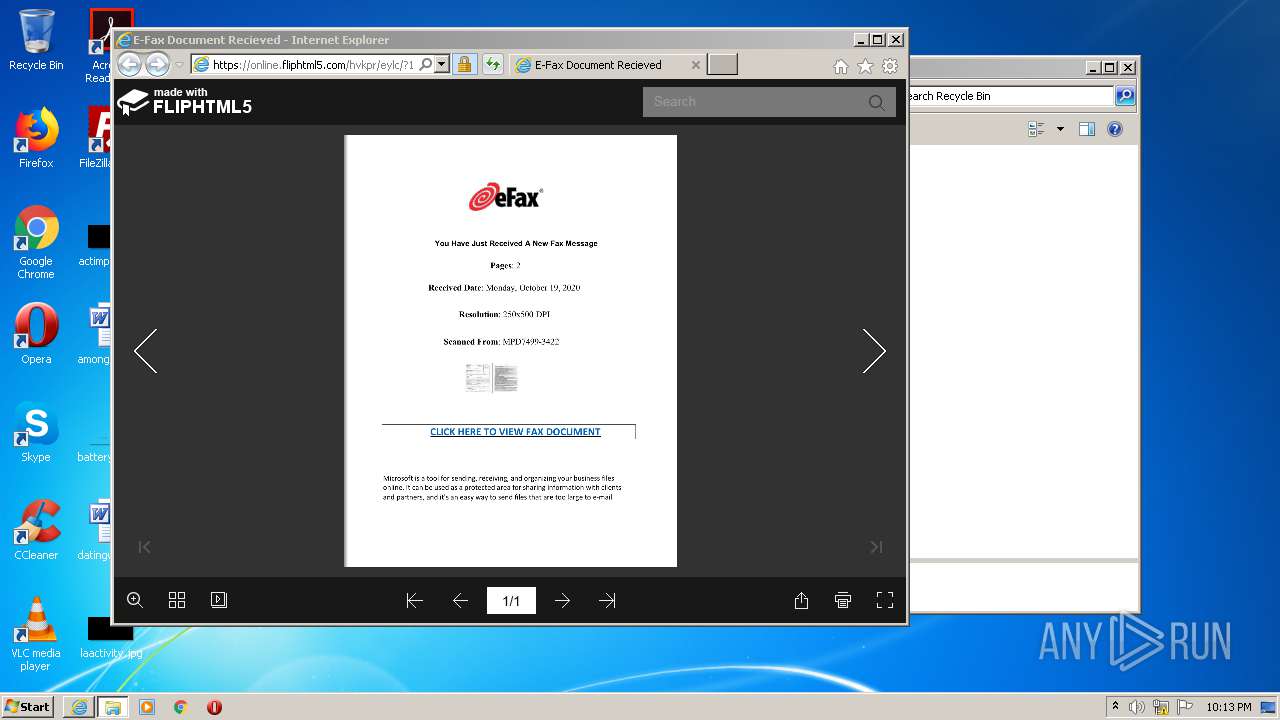
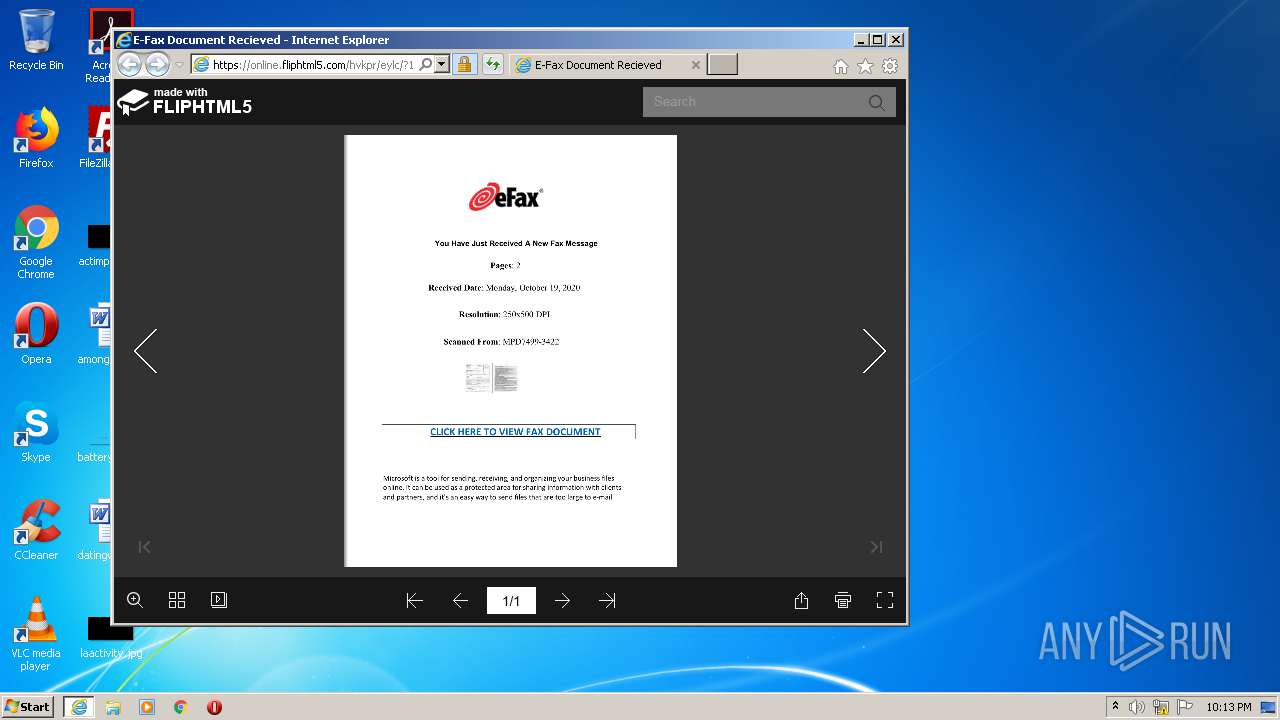
| URL: | https://online.fliphtml5.com/hvkpr/eylc/?1603125917770 |
| Full analysis: | https://app.any.run/tasks/92370ee3-59fb-4f93-9331-c5b9c0ebf42a |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2020, 21:12:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 15F2BFFE76B9E5FB7E073CF6F4DC57BF |
| SHA1: | DFEC7D134A1770349133268DFB17467EBEEF5511 |
| SHA256: | 2D181987319F891646F6952EA01CCC2A46BF882883ABCC367A2882F7AB67D67E |
| SSDEEP: | 3:N8CIIrWTOgZWOQKV:2ChLl2 |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 800)
SUSPICIOUS
Creates files in the user directory
- Skype.exe (PID: 2072)
- Skype.exe (PID: 676)
- Skype.exe (PID: 1468)
Uses REG.EXE to modify Windows registry
- Skype.exe (PID: 2072)
Reads CPU info
- Skype.exe (PID: 2072)
Application launched itself
- Skype.exe (PID: 676)
- Skype.exe (PID: 2072)
- Skype.exe (PID: 1468)
Modifies the open verb of a shell class
- Skype.exe (PID: 2072)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1292)
- iexplore.exe (PID: 928)
Application launched itself
- iexplore.exe (PID: 1292)
- chrome.exe (PID: 3920)
Reads settings of System Certificates
- iexplore.exe (PID: 928)
- iexplore.exe (PID: 1292)
- Skype.exe (PID: 2072)
Changes internet zones settings
- iexplore.exe (PID: 1292)
Manual execution by user
- Skype.exe (PID: 2072)
- chrome.exe (PID: 3920)
Reads internet explorer settings
- iexplore.exe (PID: 928)
Changes settings of System certificates
- iexplore.exe (PID: 1292)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1292)
Reads the hosts file
- Skype.exe (PID: 2072)
- chrome.exe (PID: 3920)
- chrome.exe (PID: 3184)
Dropped object may contain Bitcoin addresses
- Skype.exe (PID: 2072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
58
Monitored processes
20
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 676 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --service-pipe-token=E8F722EA92E6B6D7903398474C917FE8 --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\Preload.js" --context-id=2 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=E8F722EA92E6B6D7903398474C917FE8 --renderer-client-id=3 --mojo-platform-channel-handle=1584 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 800 | C:\Windows\system32\reg.exe ADD HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v "Skype for Desktop" /t REG_SZ /d "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" /f | C:\Windows\system32\reg.exe | Skype.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 928 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1292 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1292 | "C:\Program Files\Internet Explorer\iexplore.exe" https://online.fliphtml5.com/hvkpr/eylc/?1603125917770 | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=renderer --ms-disable-indexeddb-transaction-timeout --no-sandbox --service-pipe-token=3E0568B3417AF6786998958E96CF797C --lang=en-US --app-user-model-id=Microsoft.Skype.SkypeDesktop --app-path="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar" --node-integration=false --webview-tag=true --no-sandbox --preload="C:\Program Files\Microsoft\Skype for Desktop\resources\app.asar\Preload.js" --context-id=1 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=3E0568B3417AF6786998958E96CF797C --renderer-client-id=4 --mojo-platform-channel-handle=2616 /prefetch:1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 1472 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2644 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | explorer.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 0 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2080 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | Skype.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 2 Version: 8.29.0.50 Modules
| |||||||||||||||
| 2348 | C:\Windows\system32\reg.exe QUERY HKCU\Software\Microsoft\Skype /v RestartForUpdate | C:\Windows\system32\reg.exe | — | Skype.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 282
Read events
1 149
Write events
127
Delete events
6
Modification events
| (PID) Process: | (1292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2974247132 | |||
| (PID) Process: | (1292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30844508 | |||
| (PID) Process: | (1292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1292) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
48
Text files
98
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1292 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabB907.tmp | — | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarB918.tmp | — | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | der | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\DE813224C2AD6BA52F6E21228A0770E1 | binary | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | binary | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\book_config[1].js | text | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\DE813224C2AD6BA52F6E21228A0770E1 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
47
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
928 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
928 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
928 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
928 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
928 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEkwRzBFMEMwQTAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCE0inEJqQoMM | US | der | 1.74 Kb | whitelisted |
928 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
928 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAT%2FaBG%2BJBrPQTGNtW7lyUM%3D | US | der | 471 b | whitelisted |
1292 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
928 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEkwRzBFMEMwQTAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCE0inEJqQoMM | US | der | 1.74 Kb | whitelisted |
928 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAT%2FaBG%2BJBrPQTGNtW7lyUM%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
928 | iexplore.exe | 99.86.7.19:443 | online.fliphtml5.com | AT&T Services, Inc. | US | malicious |
— | — | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
928 | iexplore.exe | 99.86.7.34:443 | online.fliphtml5.com | AT&T Services, Inc. | US | suspicious |
928 | iexplore.exe | 192.124.249.23:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
928 | iexplore.exe | 192.124.249.36:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
928 | iexplore.exe | 192.124.249.41:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
928 | iexplore.exe | 99.86.7.23:443 | static.fliphtml5.com | AT&T Services, Inc. | US | whitelisted |
928 | iexplore.exe | 185.60.216.19:443 | connect.facebook.net | Facebook, Inc. | IE | whitelisted |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1292 | iexplore.exe | 99.86.7.34:443 | online.fliphtml5.com | AT&T Services, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
online.fliphtml5.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
crl.godaddy.com |
| whitelisted |
static.fliphtml5.com |
| whitelisted |
connect.facebook.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Skype.exe | [536:1396:1019/221342.424:VERBOSE1:crash_service.cc(145)] window handle is 000201D2
|
Skype.exe | [536:1396:1019/221342.425:VERBOSE1:crash_service.cc(304)] checkpoint is C:\Users\admin\AppData\Local\Temp\skype-preview Crashes\crash_checkpoint.txt
server is https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload
maximum 128 reports/day
reporter is electron-crash-service
|
Skype.exe | [536:1396:1019/221342.424:VERBOSE1:crash_service.cc(300)] pipe name is \\.\pipe\skype-preview Crash Service
dumps at C:\Users\admin\AppData\Local\Temp\skype-preview Crashes
|
Skype.exe | [536:1396:1019/221342.424:VERBOSE1:crash_service.cc(145)] window handle is 000201D2
|
Skype.exe | [536:1396:1019/221342.425:VERBOSE1:crash_service_main.cc(94)] Ready to process crash requests
|
Skype.exe | [536:1252:1019/221342.426:VERBOSE1:crash_service.cc(333)] client start. pid = 2072
|
Skype.exe | [536:1252:1019/221345.118:VERBOSE1:crash_service.cc(333)] client start. pid = 676
|
Skype.exe | [2448:3228:1019/221345.309:VERBOSE1:crash_service_main.cc(78)] Session start. cmdline is [--reporter-url=https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload --application-name=skype-preview "--crashes-directory=C:\Users\admin\AppData\Local\Temp\skype-preview Crashes" --v=1]
|
Skype.exe | [2448:3228:1019/221345.311:VERBOSE1:crash_service.cc(304)] checkpoint is C:\Users\admin\AppData\Local\Temp\skype-preview Crashes\crash_checkpoint.txt
server is https://rink.hockeyapp.net/api/2/apps/a741743329d94bc08826af367733939d/crashes/upload
maximum 128 reports/day
reporter is electron-crash-service
|
Skype.exe | [2448:3228:1019/221345.311:VERBOSE1:crash_service.cc(145)] window handle is 0002023E
|