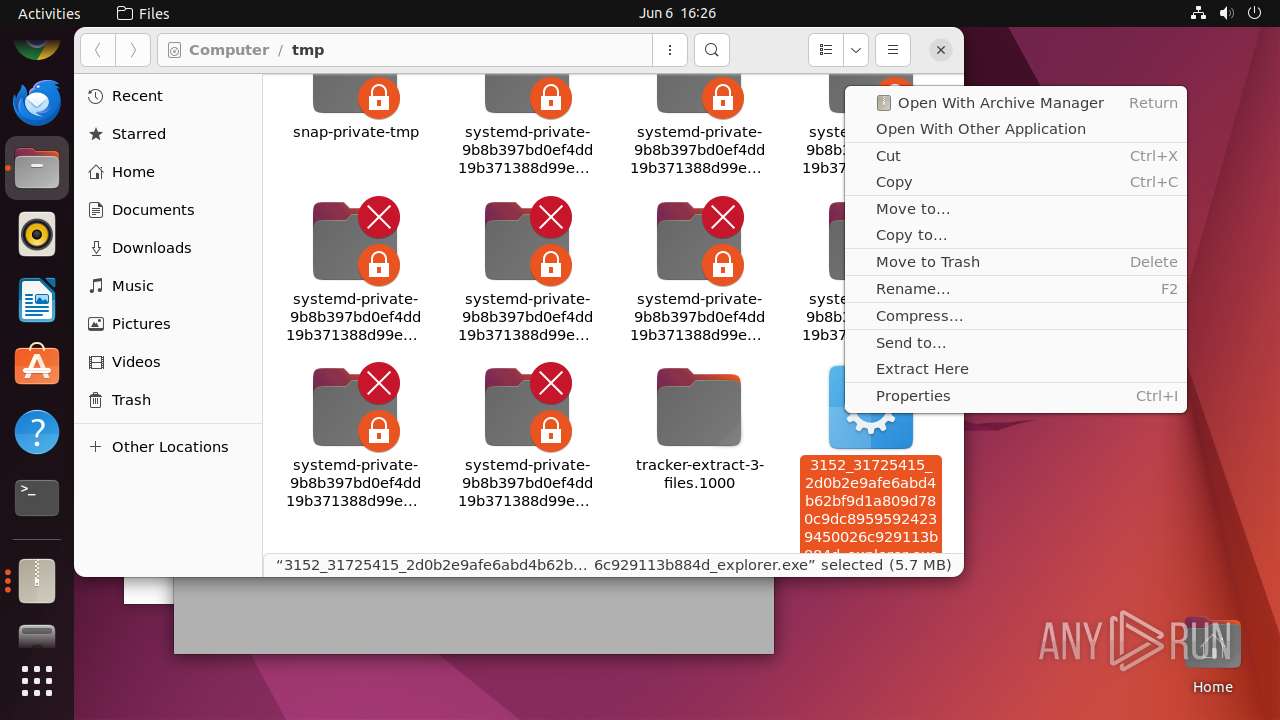
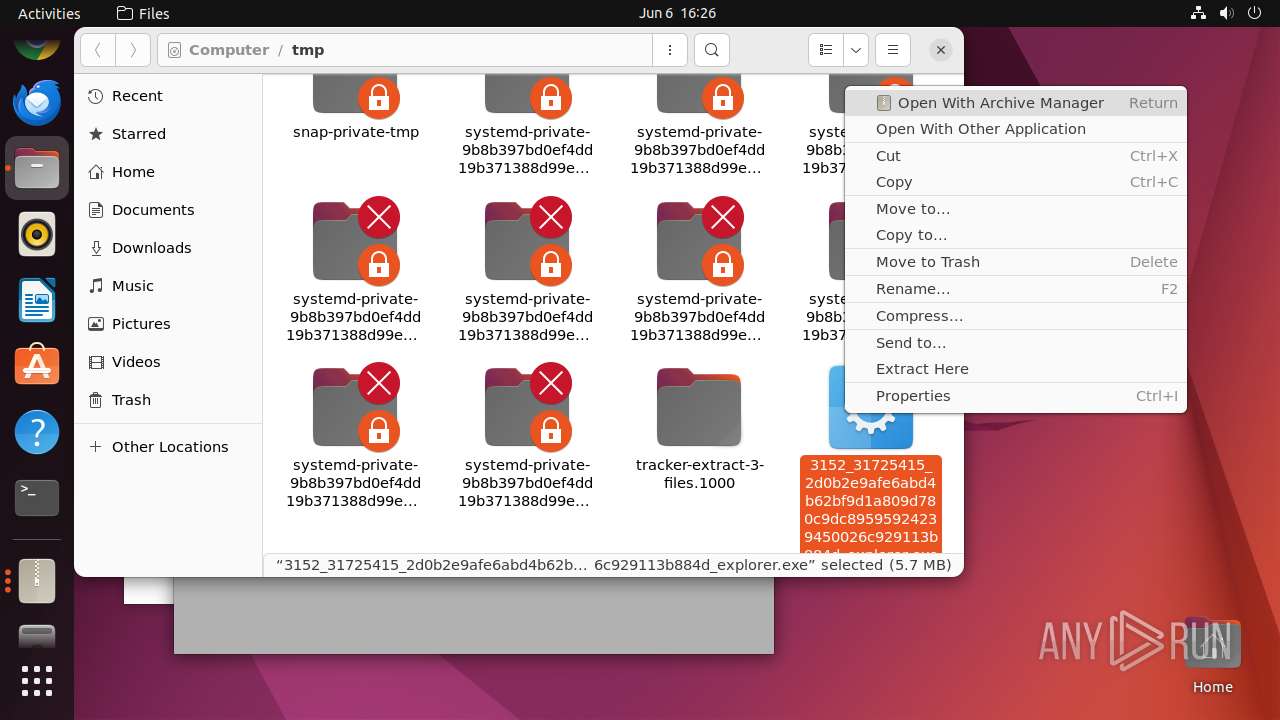
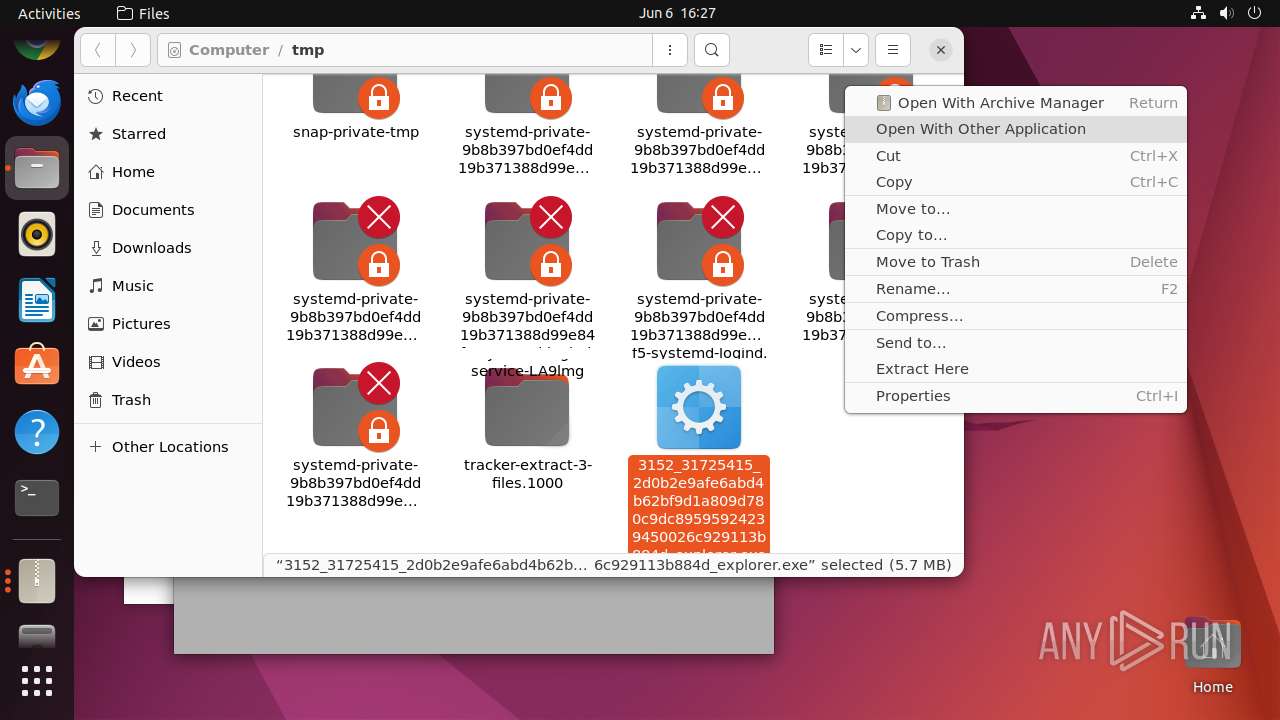
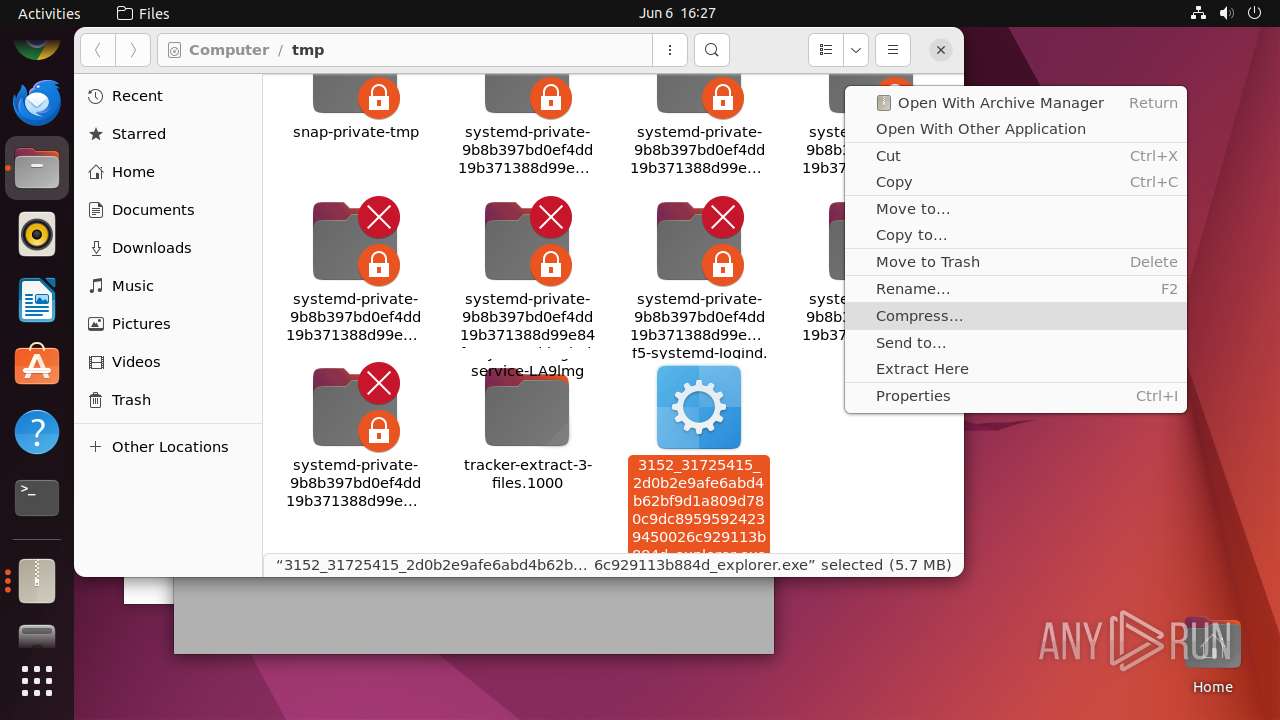
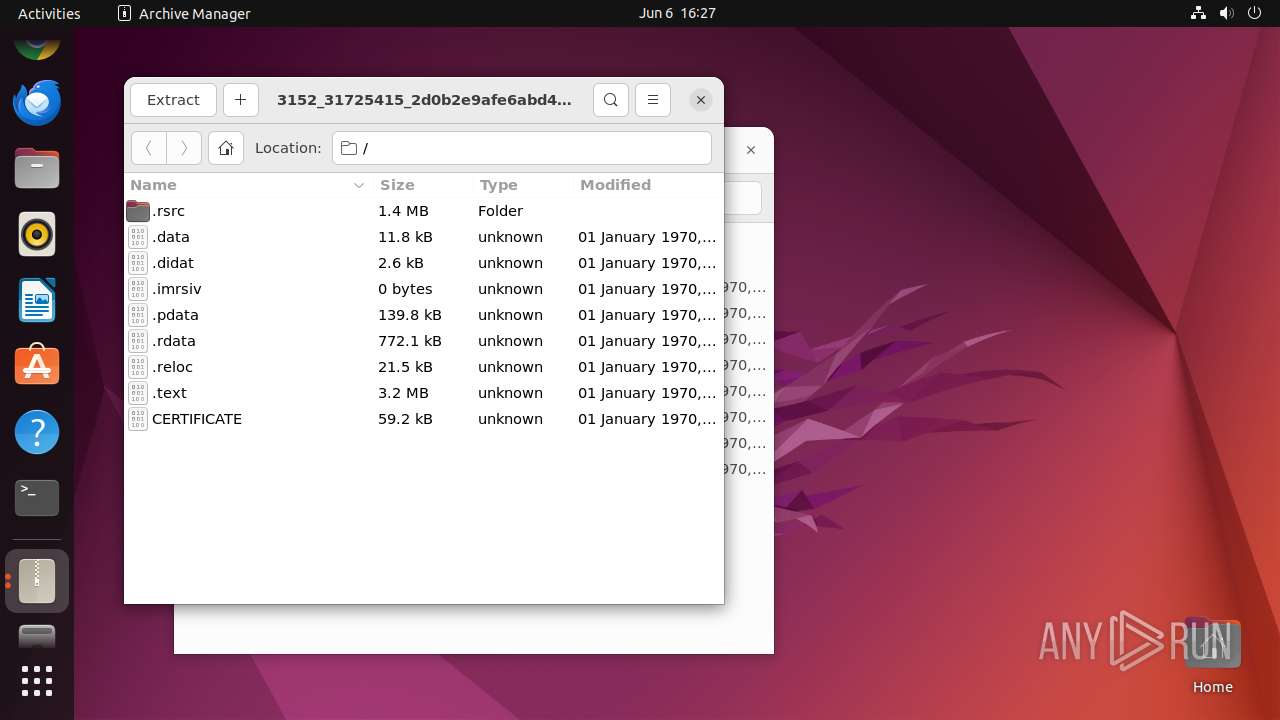
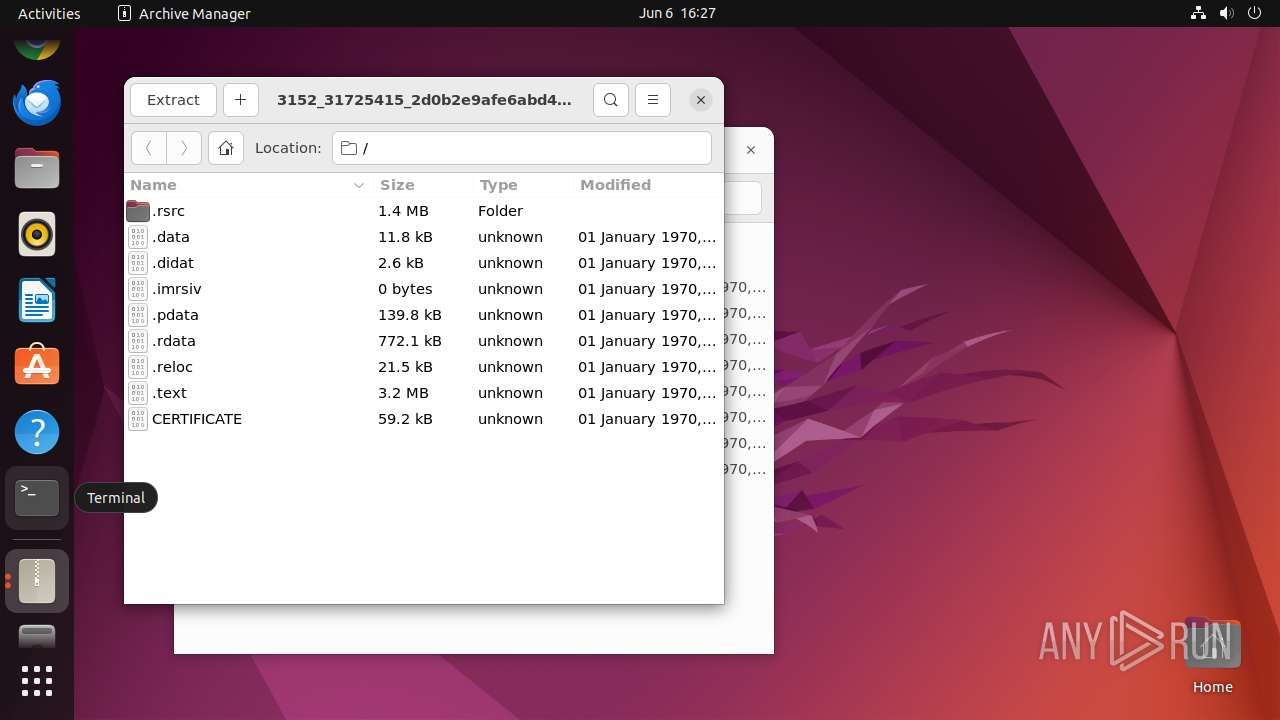
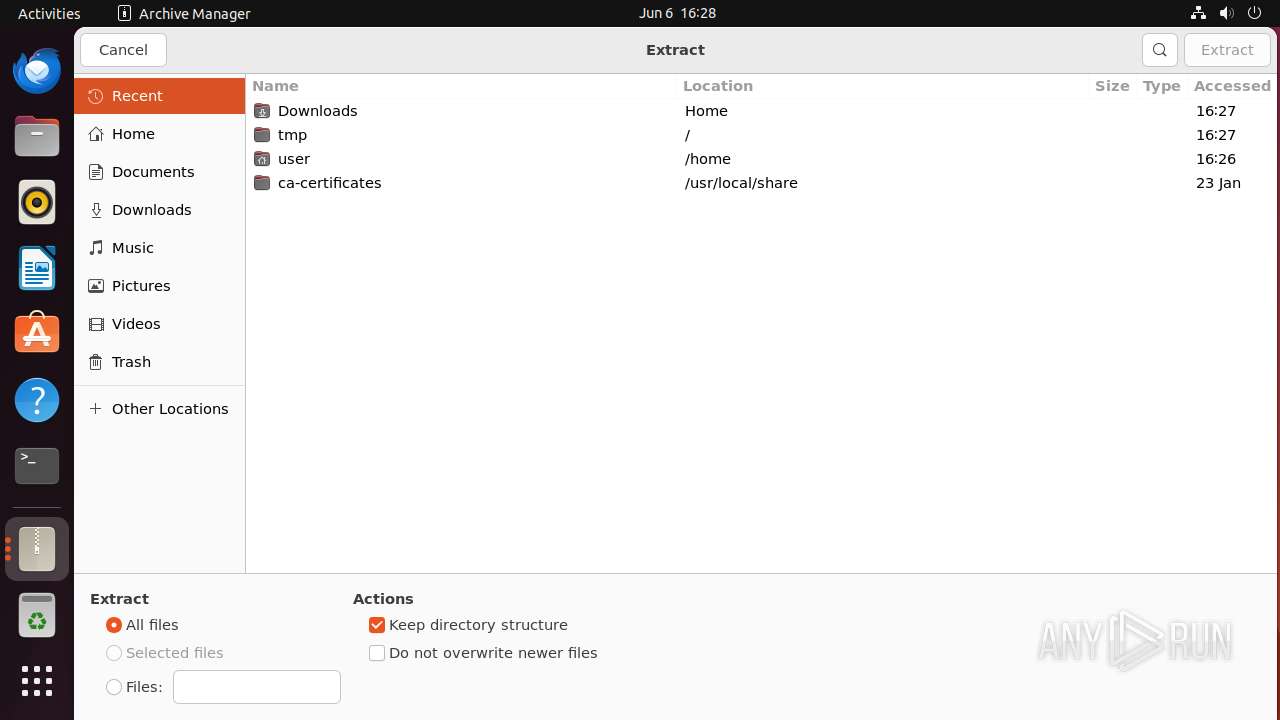
| File name: | 3152_31725415_2d0b2e9afe6abd4b62bf9d1a809d780c9dc89595924239450026c929113b884d_explorer.exe |
| Full analysis: | https://app.any.run/tasks/d4cbcfd7-e0e3-43fd-8e97-9dae57f4b187 |
| Verdict: | Malicious activity |
| Analysis date: | June 06, 2024, 15:25:45 |
| OS: | Ubuntu 22.04.2 |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | ABF5FDD023E5C30434AB72F59D66FB18 |
| SHA1: | 8B6A425A69E0F805291505B3F98B107652C2FA01 |
| SHA256: | 2D0B2E9AFE6ABD4B62BF9D1A809D780C9DC89595924239450026C929113B884D |
| SSDEEP: | 98304:T3ZUIzi++ATOtxryCx7t03+0Nu55zpx/6ShP9pOclyrWYfeipJyMpgMIBbyeolqK:e41kQMuL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks DMI information (probably VM detection)
- systemd-hostnamed (PID: 12577)
- systemd-hostnamed (PID: 12465)
- systemd-hostnamed (PID: 12592)
Executes commands using command-line interpreter
- cron (PID: 12603)
Checks the user who created the process
- cron (PID: 12603)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (50.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.6) |
| .exe | | | Win32 Executable (generic) (5.2) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2059:11:12 23:47:58+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.2 |
| CodeSize: | 3203584 |
| InitializedDataSize: | 2426368 |
| UninitializedDataSize: | 512 |
| EntryPoint: | 0xa33b0 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 10 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.19041.4355 |
| ProductVersionNumber: | 10.0.19041.4355 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Windows Explorer |
| FileVersion: | 10.0.19041.4355 (WinBuild.160101.0800) |
| InternalName: | explorer |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | EXPLORER.EXE |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 10.0.19041.4355 |
Total processes
240
Monitored processes
26
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 12447 | sh -c "file --mime-type /tmp/3152_31725415_2d0b2e9afe6abd4b62bf9d1a809d780c9dc89595924239450026c929113b884d_explorer\.exe" | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12448 | file --mime-type /tmp/3152_31725415_2d0b2e9afe6abd4b62bf9d1a809d780c9dc89595924239450026c929113b884d_explorer.exe | /usr/bin/file | — | sh |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12449 | /bin/sh -c "DISPLAY=:0 sudo -iu user nautilus /tmp/3152_31725415_2d0b2e9afe6abd4b62bf9d1a809d780c9dc89595924239450026c929113b884d_explorer\.exe " | /bin/sh | — | any-guest-agent |
User: user Integrity Level: UNKNOWN Exit code: 12568 | ||||
| 12450 | sudo -iu user nautilus /tmp/3152_31725415_2d0b2e9afe6abd4b62bf9d1a809d780c9dc89595924239450026c929113b884d_explorer.exe | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 12568 | ||||
| 12451 | nautilus /tmp/3152_31725415_2d0b2e9afe6abd4b62bf9d1a809d780c9dc89595924239450026c929113b884d_explorer.exe | /usr/bin/nautilus | — | sudo |
User: user Integrity Level: UNKNOWN Exit code: 12568 | ||||
| 12452 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | nautilus |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12465 | /lib/systemd/systemd-hostnamed | /lib/systemd/systemd-hostnamed | — | systemd |
User: root Integrity Level: UNKNOWN Exit code: 12516 | ||||
| 12474 | nautilus /tmp/3152_31725415_2d0b2e9afe6abd4b62bf9d1a809d780c9dc89595924239450026c929113b884d_explorer.exe | /usr/bin/nautilus | — | nautilus |
User: user Integrity Level: UNKNOWN Exit code: 482 | ||||
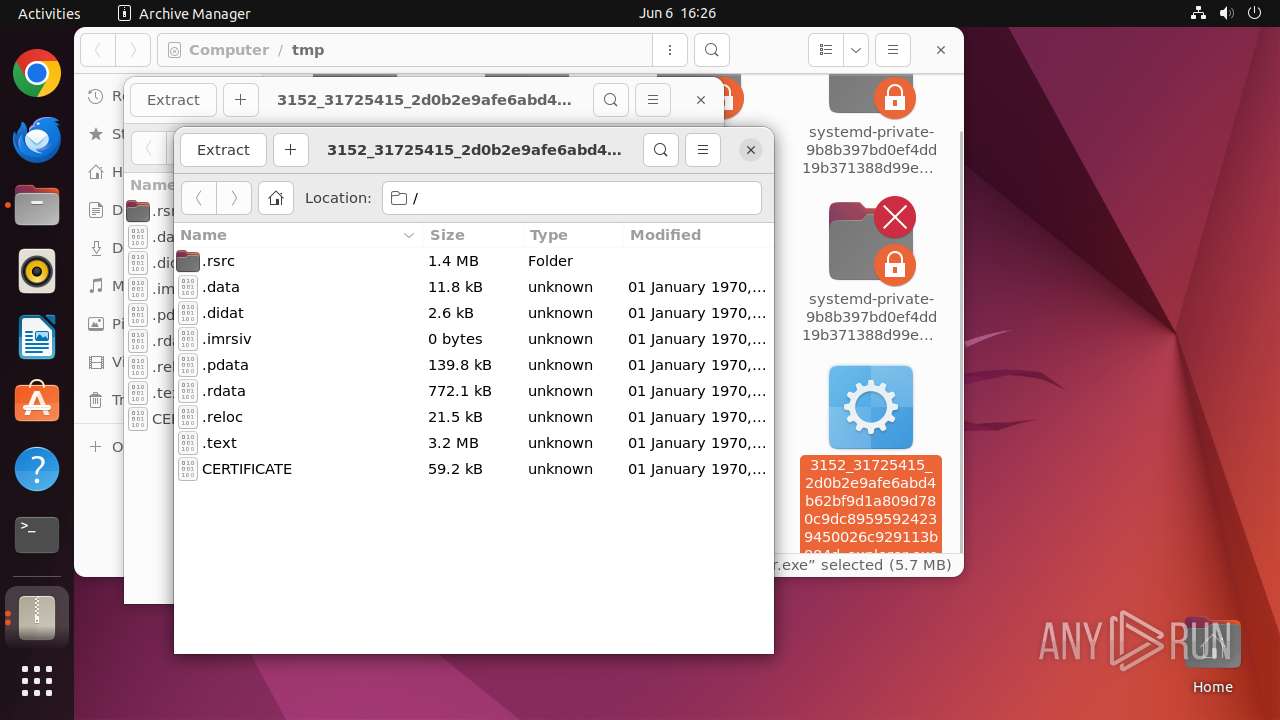
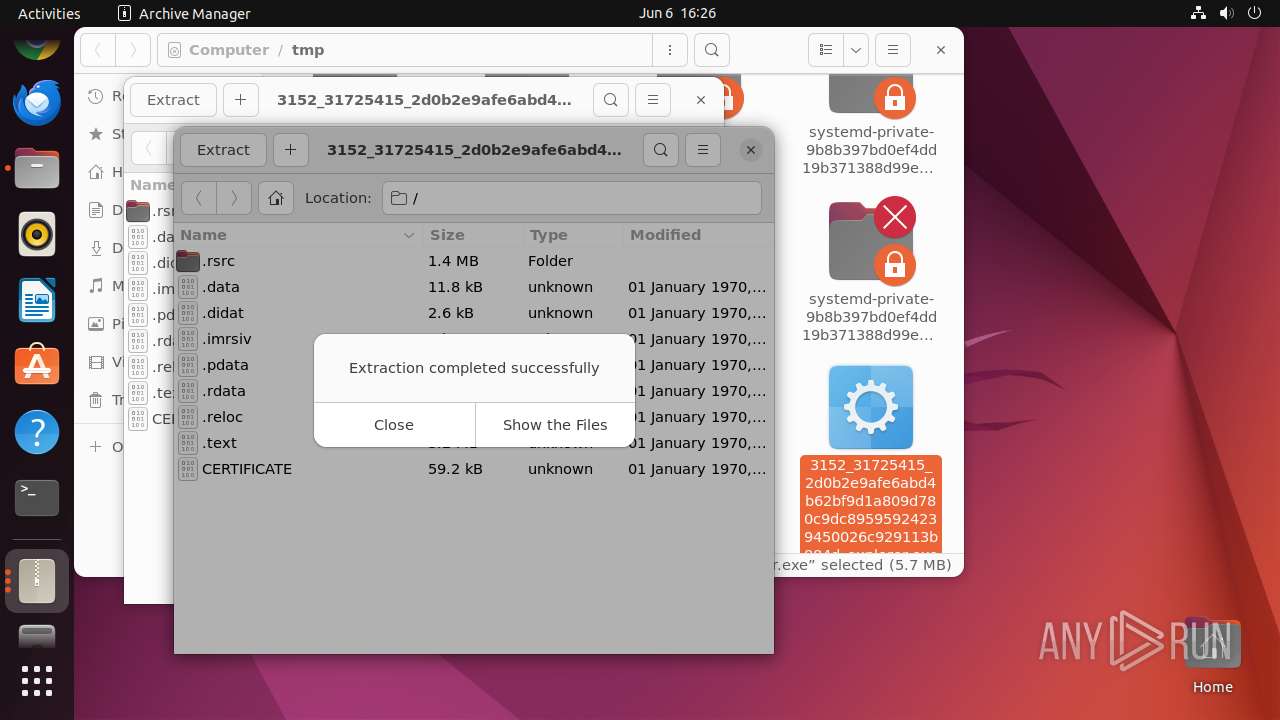
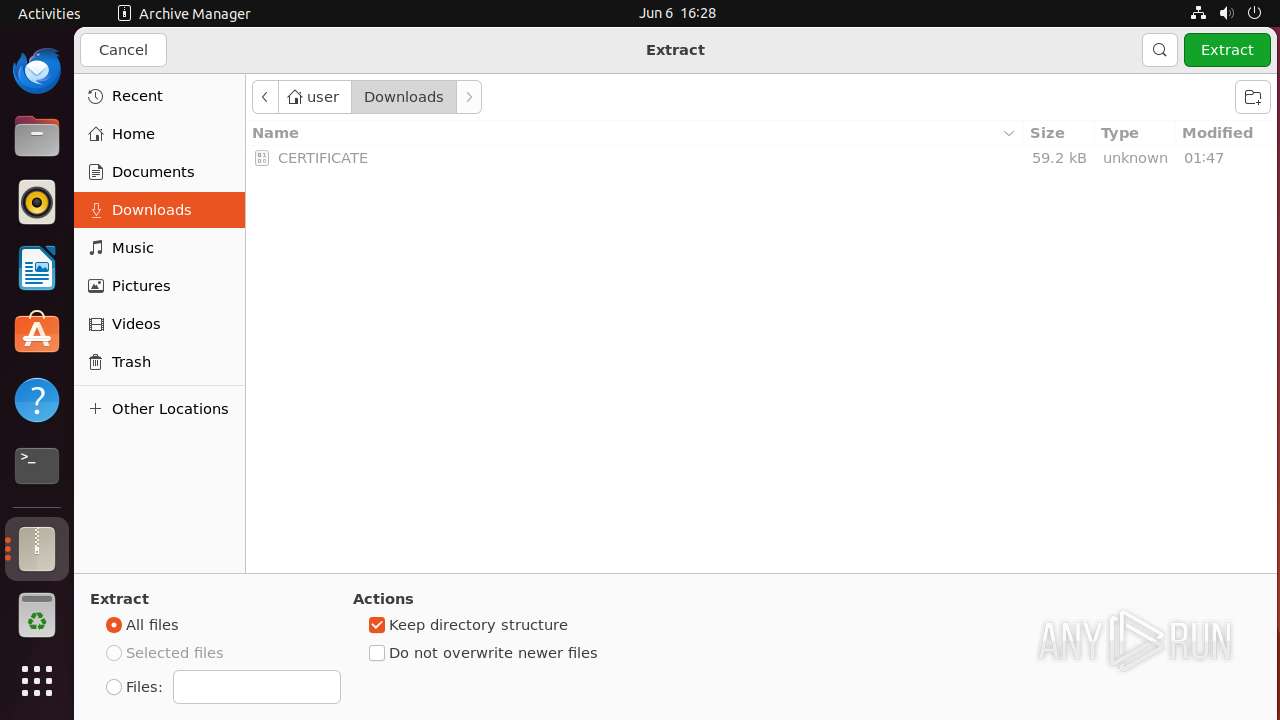
| 12475 | file-roller /tmp/3152_31725415_2d0b2e9afe6abd4b62bf9d1a809d780c9dc89595924239450026c929113b884d_explorer.exe | /usr/bin/file-roller | — | nautilus |
User: user Integrity Level: UNKNOWN | ||||
| 12482 | nautilus /tmp/3152_31725415_2d0b2e9afe6abd4b62bf9d1a809d780c9dc89595924239450026c929113b884d_explorer.exe | /usr/bin/nautilus | — | nautilus |
User: user Integrity Level: UNKNOWN Exit code: 482 | ||||
Executable files
0
Suspicious files
44
Text files
1 236
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 12451 | nautilus | /home/user/.local/share/recently-used.xbel | xml | |
MD5:— | SHA256:— | |||
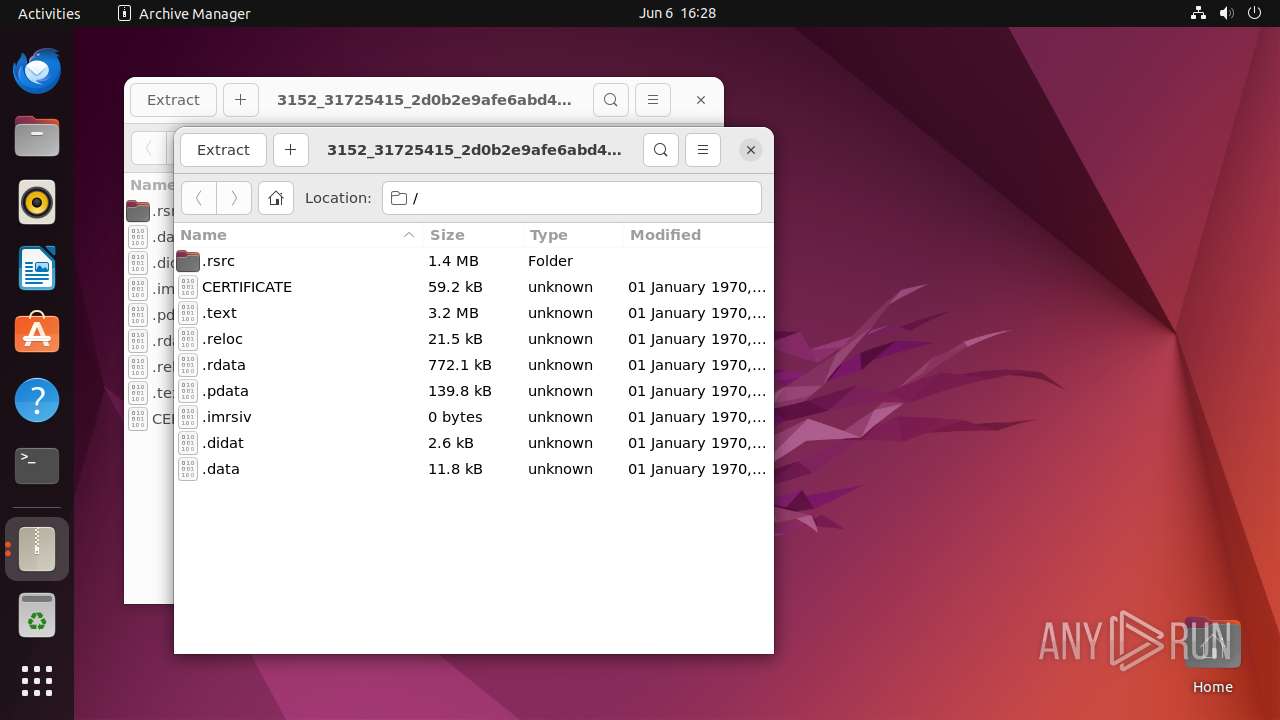
| 12536 | 7z | /home/user/Downloads/.text | binary | |
MD5:— | SHA256:— | |||
| 12536 | 7z | /home/user/Downloads/.rdata | binary | |
MD5:— | SHA256:— | |||
| 12536 | 7z | /home/user/Downloads/.data | binary | |
MD5:— | SHA256:— | |||
| 12536 | 7z | /home/user/Downloads/.pdata | binary | |
MD5:— | SHA256:— | |||
| 12536 | 7z | /home/user/Downloads/.didat | binary | |
MD5:— | SHA256:— | |||
| 12536 | 7z | /home/user/Downloads/.rsrc/version.txt | binary | |
MD5:— | SHA256:— | |||
| 12536 | 7z | /home/user/Downloads/.rsrc/IMAGE/100 | image | |
MD5:— | SHA256:— | |||
| 12536 | 7z | /home/user/Downloads/.rsrc/IMAGE/101 | image | |
MD5:— | SHA256:— | |||
| 12536 | 7z | /home/user/Downloads/.rsrc/IMAGE/102 | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
473 | NetworkManager | GET | 204 | 185.125.190.18:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
470 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
12516 | gvfsd-smb-browse | 192.168.100.255:137 | — | — | — | whitelisted |
485 | snapd | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
473 | NetworkManager | 185.125.190.18:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.snapcraft.io |
| unknown |
190.100.168.192.in-addr.arpa |
| unknown |
connectivity-check.ubuntu.com |
| unknown |