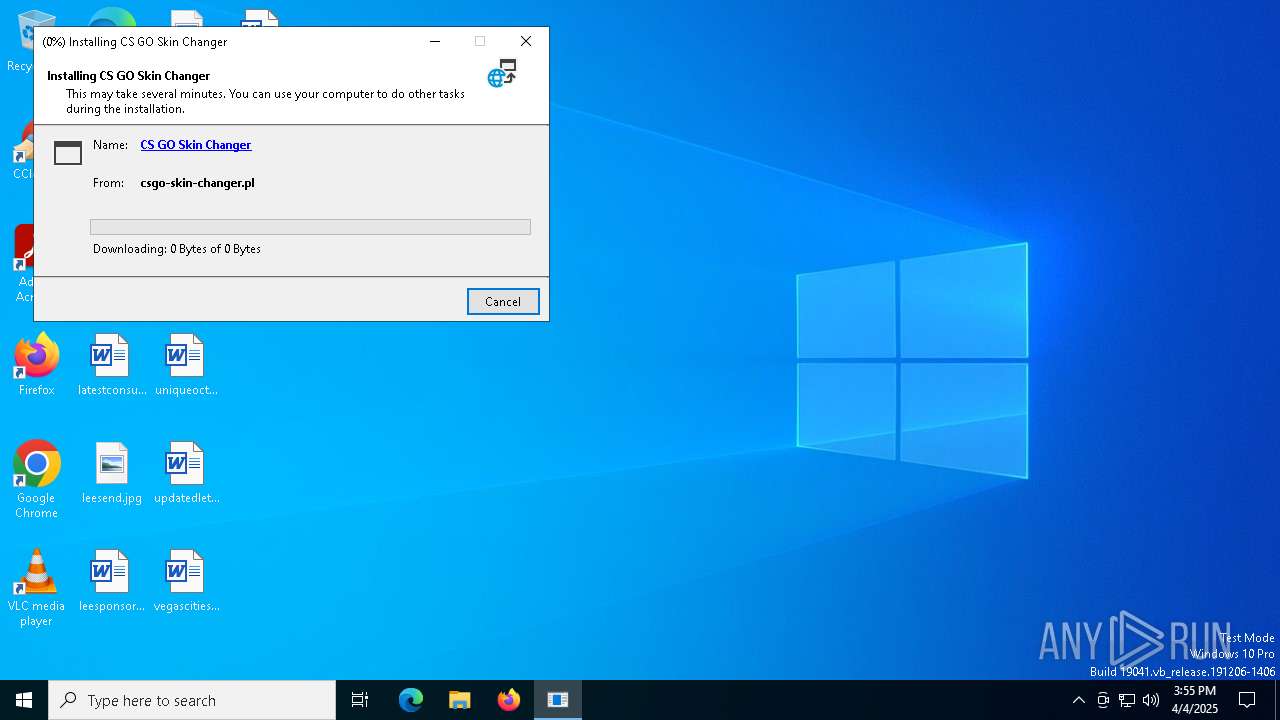
| File name: | setup.exe |
| Full analysis: | https://app.any.run/tasks/1484838f-bbe2-453b-a923-10cee7c8264e |
| Verdict: | Malicious activity |
| Analysis date: | April 04, 2025, 15:55:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | EE1E0A5B4CA042537FCAC87E37D456D6 |
| SHA1: | EAF1847A41931240C2949049423231C0253CA0D4 |
| SHA256: | 2D01B29456354E729D4F3338B21DD451BD346F18A478F80750B7A44E57B48AA7 |
| SSDEEP: | 12288:kMgtMSpKnRYB4gLuDqCOor70TPp3etqZZrAttJVVVVVVVVVVVVVVVVVVVOVVVVVb:kM+pKnRy4Hm3osky9xH |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- setup.exe (PID: 7284)
- dfsvc.exe (PID: 7424)
- CSGOSkinChanger.exe (PID: 5576)
Reads Internet Explorer settings
- dfsvc.exe (PID: 7424)
Searches for installed software
- dfsvc.exe (PID: 7424)
Executable content was dropped or overwritten
- dfsvc.exe (PID: 7424)
Reads the date of Windows installation
- dfsvc.exe (PID: 7424)
Creates a software uninstall entry
- dfsvc.exe (PID: 7424)
INFO
Create files in a temporary directory
- setup.exe (PID: 7284)
- dfsvc.exe (PID: 7424)
Checks supported languages
- setup.exe (PID: 7284)
- dfsvc.exe (PID: 7424)
- CSGOSkinChanger.exe (PID: 5576)
Reads the computer name
- setup.exe (PID: 7284)
- dfsvc.exe (PID: 7424)
- CSGOSkinChanger.exe (PID: 5576)
The sample compiled with english language support
- setup.exe (PID: 7284)
Creates files or folders in the user directory
- setup.exe (PID: 7284)
- dfsvc.exe (PID: 7424)
Reads the machine GUID from the registry
- setup.exe (PID: 7284)
- dfsvc.exe (PID: 7424)
- CSGOSkinChanger.exe (PID: 5576)
Checks proxy server information
- setup.exe (PID: 7284)
- dfsvc.exe (PID: 7424)
- slui.exe (PID: 5116)
Reads the software policy settings
- setup.exe (PID: 7284)
- dfsvc.exe (PID: 7424)
- slui.exe (PID: 7544)
- slui.exe (PID: 5116)
Reads Environment values
- dfsvc.exe (PID: 7424)
Process checks whether UAC notifications are on
- dfsvc.exe (PID: 7424)
Disables trace logs
- dfsvc.exe (PID: 7424)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 4400)
Process checks computer location settings
- dfsvc.exe (PID: 7424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:01:16 18:19:34+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.38 |
| CodeSize: | 382464 |
| InitializedDataSize: | 166912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x36fc0 |
| OSVersion: | 5.1 |
| ImageVersion: | 10 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 17.0.35716.53 |
| ProductVersionNumber: | 17.0.35716.53 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | Setup |
| FileVersion: | 17.0.35716.53 built by: d17.13 |
| InternalName: | setup.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | setup.exe |
| ProductName: | - |
| ProductVersion: | 17.0.35716.53 |
Total processes
143
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4400 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
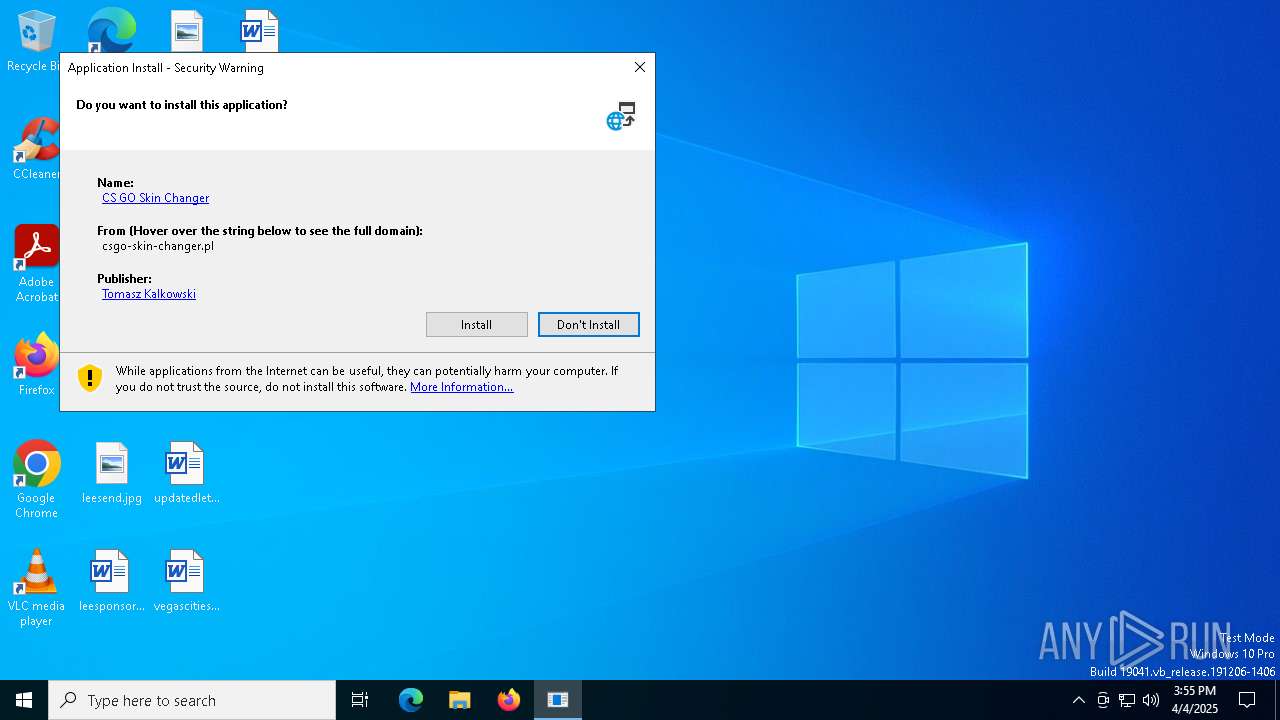
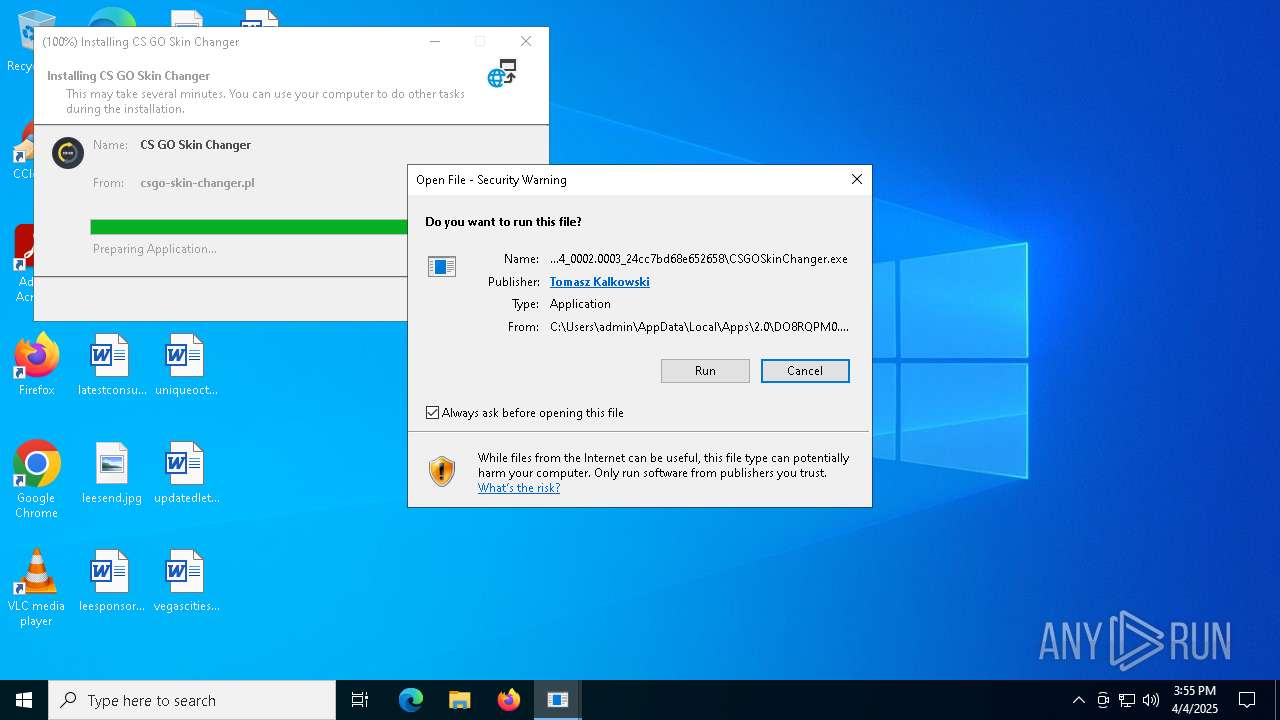
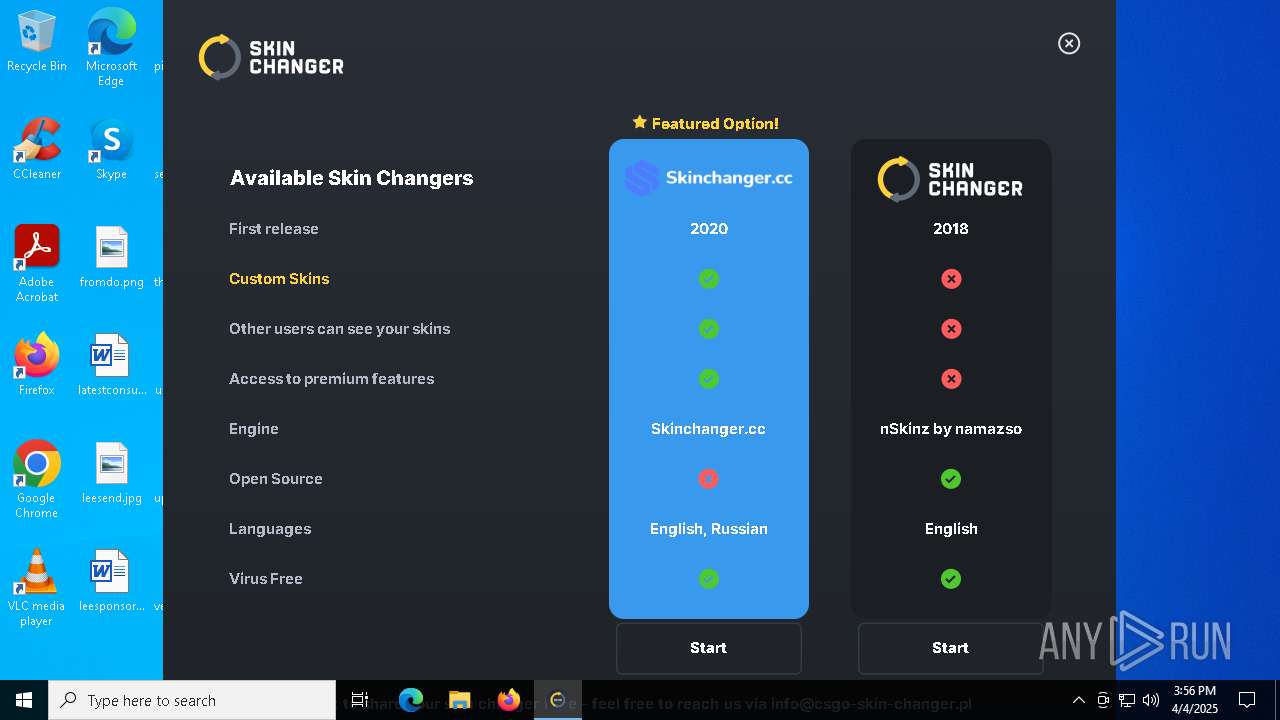
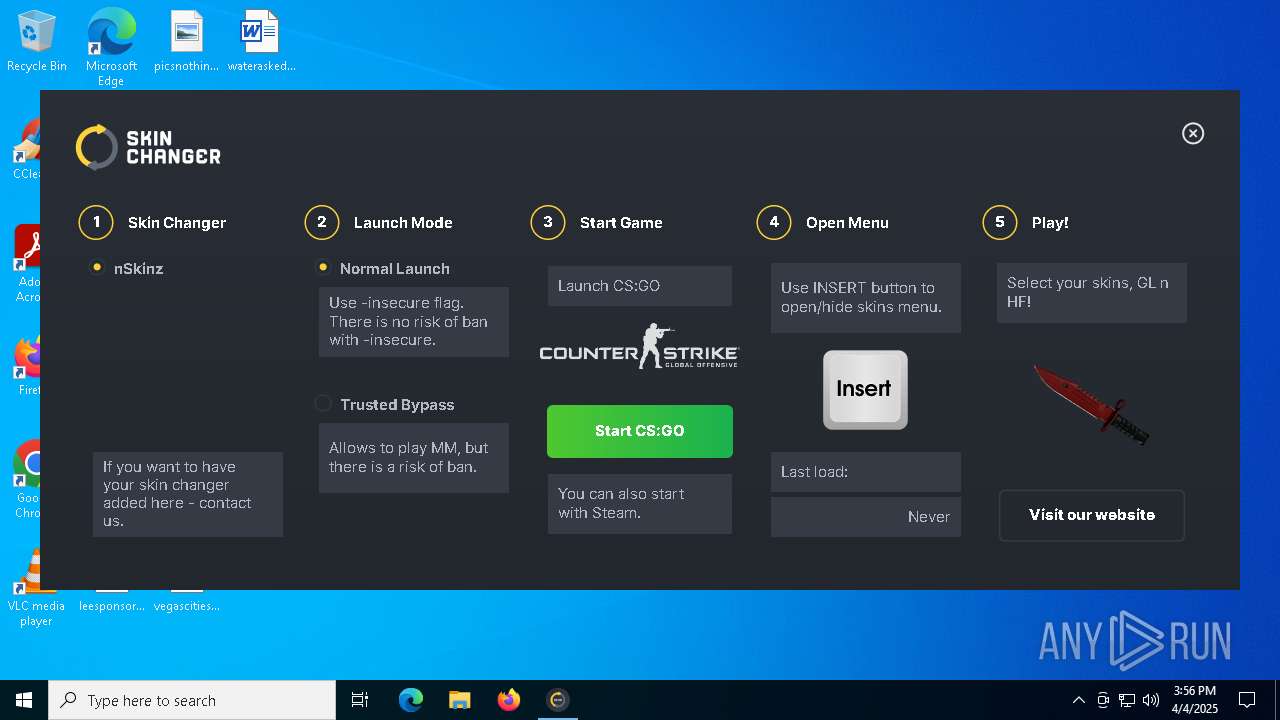
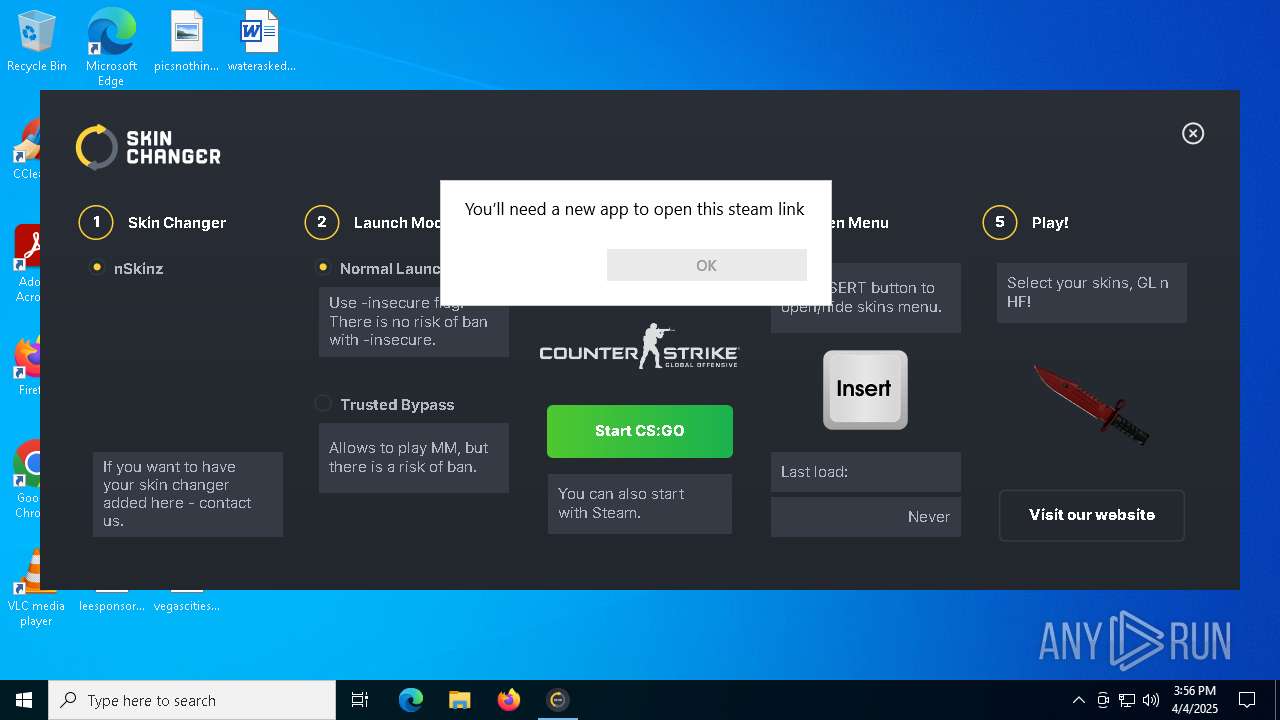
| 5576 | "C:\Users\admin\AppData\Local\Apps\2.0\DO8RQPM0.GER\DAV3HYN7.DD9\csgo..tion_ae950b064f7d37a4_0002.0003_24cc7bd68e652658\CSGOSkinChanger.exe" | C:\Users\admin\AppData\Local\Apps\2.0\DO8RQPM0.GER\DAV3HYN7.DD9\csgo..tion_ae950b064f7d37a4_0002.0003_24cc7bd68e652658\CSGOSkinChanger.exe | — | dfsvc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: CS:GO Skin Changer Version: 2.0.9192.25327 Modules
| |||||||||||||||
| 7284 | "C:\Users\admin\AppData\Local\Temp\setup.exe" | C:\Users\admin\AppData\Local\Temp\setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup Exit code: 0 Version: 17.0.35716.53 built by: d17.13 Modules
| |||||||||||||||
| 7424 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\dfsvc.exe" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\dfsvc.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ClickOnce Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 7512 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7544 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 648
Read events
7 520
Write events
119
Delete events
9
Modification events
| (PID) Process: | (7284) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7284) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7284) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7424) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0 |
| Operation: | write | Name: | ComponentStore_RandomString |
Value: 4CX0XD35E8OYTZ42NH0X8WR0 | |||
| (PID) Process: | (7424) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0 |
| Operation: | delete value | Name: | ComponentStore_RandomString |
Value: 4CX0XD35E8OYTZ42NH0X8WR0 | |||
| (PID) Process: | (7424) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7424) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0 |
| Operation: | write | Name: | ComponentStore_RandomString |
Value: DO8RQPM0GERDAV3HYN7DD9Q6 | |||
| (PID) Process: | (7424) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0\StateManager |
| Operation: | write | Name: | StateStore_RandomString |
Value: 84EO5GT6CXQ8HZK9ND04TLJA | |||
| (PID) Process: | (7424) dfsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dfsvc_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7424) dfsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dfsvc_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
6
Suspicious files
26
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7284 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\844066DE8C71ACFAC1D7FF6BD6849912 | binary | |
MD5:6BB9A8A8336E6CE49A4A0825D8F382F9 | SHA256:27340796F7C7B84AB21AB06990F24D2262B8A0D955FE2FB613EDA39938FF3739 | |||
| 7284 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\844066DE8C71ACFAC1D7FF6BD6849912 | binary | |
MD5:207D47F9EEF9708674F49A6549A513D6 | SHA256:3757AB33F4773AC5ACB0D5F75B29726B3D88378FE0571312CA23F265480AE2DE | |||
| 7284 | setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\CSGOSkinChanger[1].application | xml | |
MD5:359E25185708E5085EBBA5985E1299C7 | SHA256:C4100C868BE745D15585DB7786444A47D38633D6E78BC5114A6B2B2E38F7F94E | |||
| 7424 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\ERKXCWO9.9VQ\QT8GC9T9.YOA.application | xml | |
MD5:359E25185708E5085EBBA5985E1299C7 | SHA256:C4100C868BE745D15585DB7786444A47D38633D6E78BC5114A6B2B2E38F7F94E | |||
| 7424 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_56DB209C155B5A05FCBF555DF7E6D1BB | binary | |
MD5:53B114856F8E86719921A39148DC4503 | SHA256:66846986031759F3295AC36B984A940E05B0DE9AD867D17FAD76CA4A8E78E846 | |||
| 7424 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:5AA02EF5E7D0263FF24B50221DBD4747 | SHA256:50129C7EF37D5C315D6DA567635F3FAF55EB0B77E61B5FF5F89B0600F5DA66EA | |||
| 7424 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:B159324BF97BF0785DF933697D3BD595 | SHA256:9714662A4E28EF139CBC9B80F8D9C5C1E8F172CBA2FBA4AFA90364A384C35E3B | |||
| 7424 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3E3E9689537B6B136ECF210088069D55_E93D4349D1D2AF4AE2F3CBFF382A5C9D | binary | |
MD5:00F7B6A53B6EC655350530372E99114B | SHA256:B1E61E77DEC15363824EDD0A8543878378C1AC3D37308303E3E14E072E5D4EC6 | |||
| 7424 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_56DB209C155B5A05FCBF555DF7E6D1BB | binary | |
MD5:3F1065DD0AE0824AB156C563E11E5669 | SHA256:9C224ED58AB306A3855FE3C9E60CABF92D880BC1519B5A48A6A2E2C720C1C32B | |||
| 7424 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_93702E680A5530C052C8D2BA33A2225F | binary | |
MD5:ECF8D88F66425A22D1EBD49AB06E9EC9 | SHA256:2DFAF5ADC6BD241FA49852F5D83EBE378378C12987789034F9302FEBADCA7096 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
30
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.155:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7284 | setup.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7284 | setup.exe | GET | 200 | 184.24.77.57:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgQvusXlTywu%2BH8LALPzn2Higg%3D%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7424 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
7424 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAc2N7ckVHzYR6z9KGYqXls%3D | unknown | — | — | whitelisted |
7424 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTjzY2p9Pa8oibmj%2BNSMWsz63kmWgQUuhbZbU2FL3MpdpovdYxqII%2BeyG8CEAuuZrxaun%2BVh8b56QTjMwQ%3D | unknown | — | — | whitelisted |
7424 | dfsvc.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
7424 | dfsvc.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
8136 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.155:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
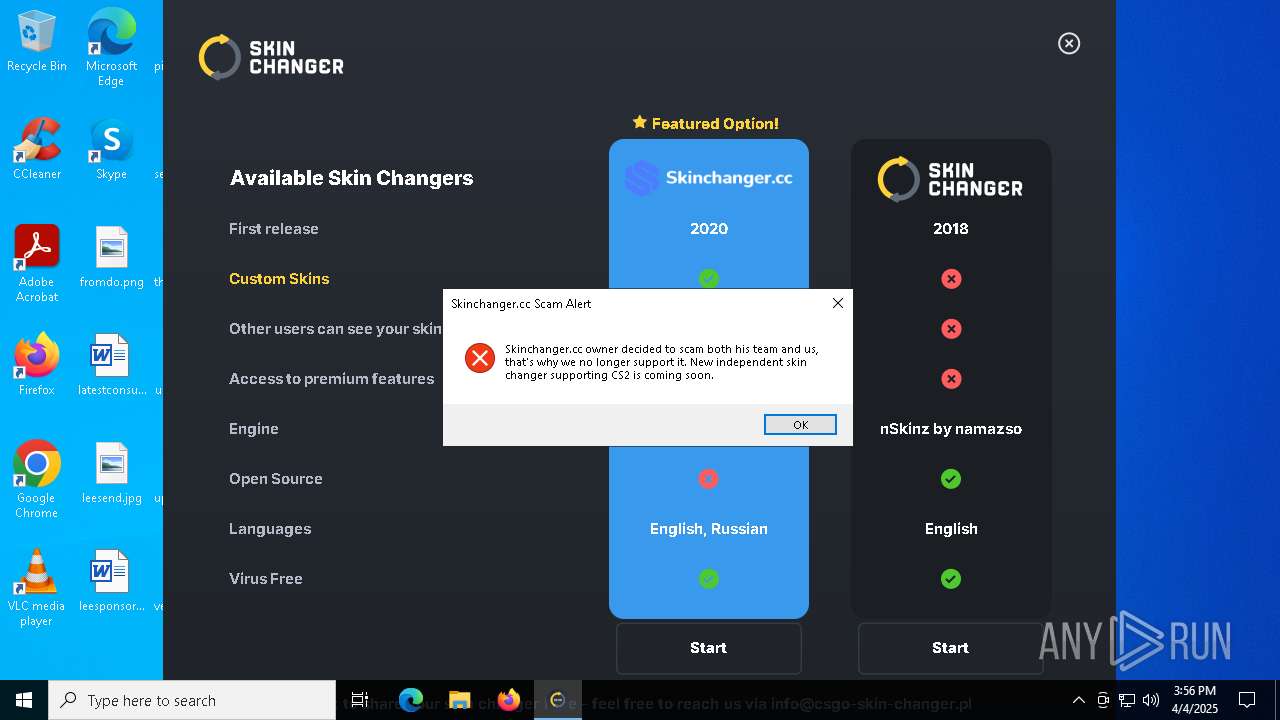
7284 | setup.exe | 31.186.82.38:443 | csgo-skin-changer.pl | Atman Sp. z o.o. | PL | malicious |
7284 | setup.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | whitelisted |
7284 | setup.exe | 184.24.77.57:80 | r11.o.lencr.org | Akamai International B.V. | DE | whitelisted |
7424 | dfsvc.exe | 31.186.82.38:443 | csgo-skin-changer.pl | Atman Sp. z o.o. | PL | malicious |
6544 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
csgo-skin-changer.pl |
| malicious |
x1.c.lencr.org |
| whitelisted |
r11.o.lencr.org |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |