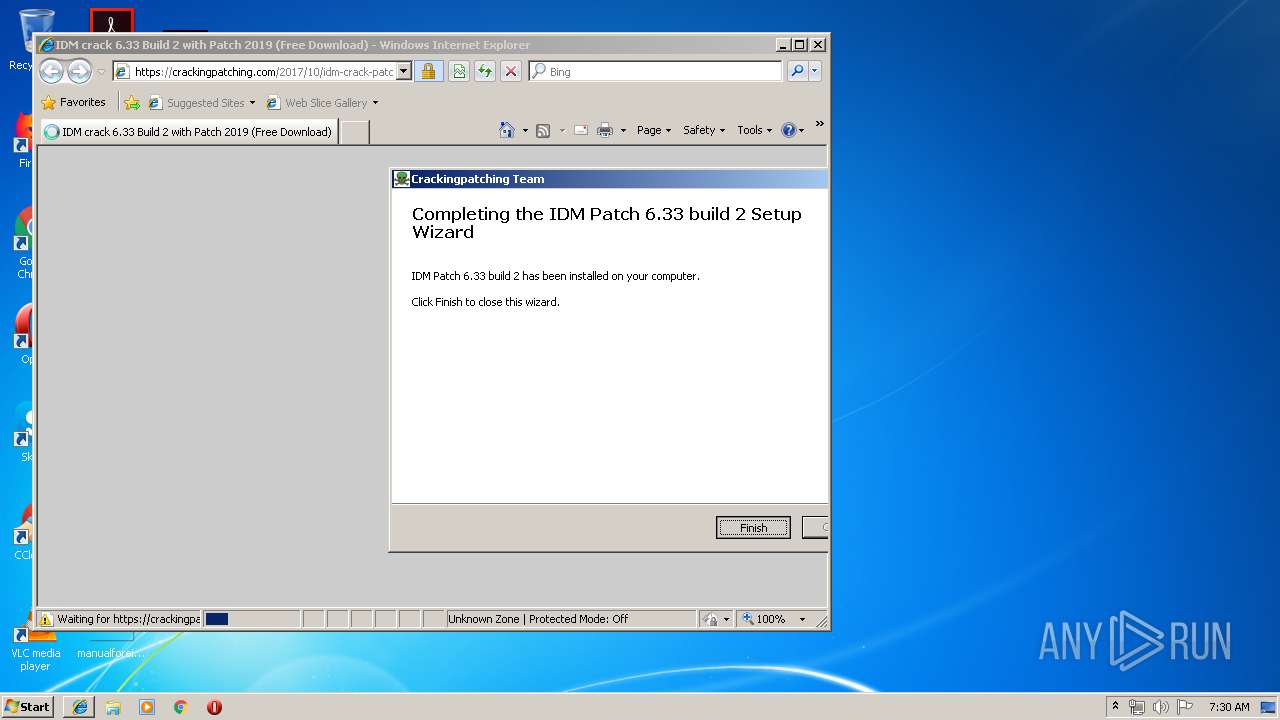
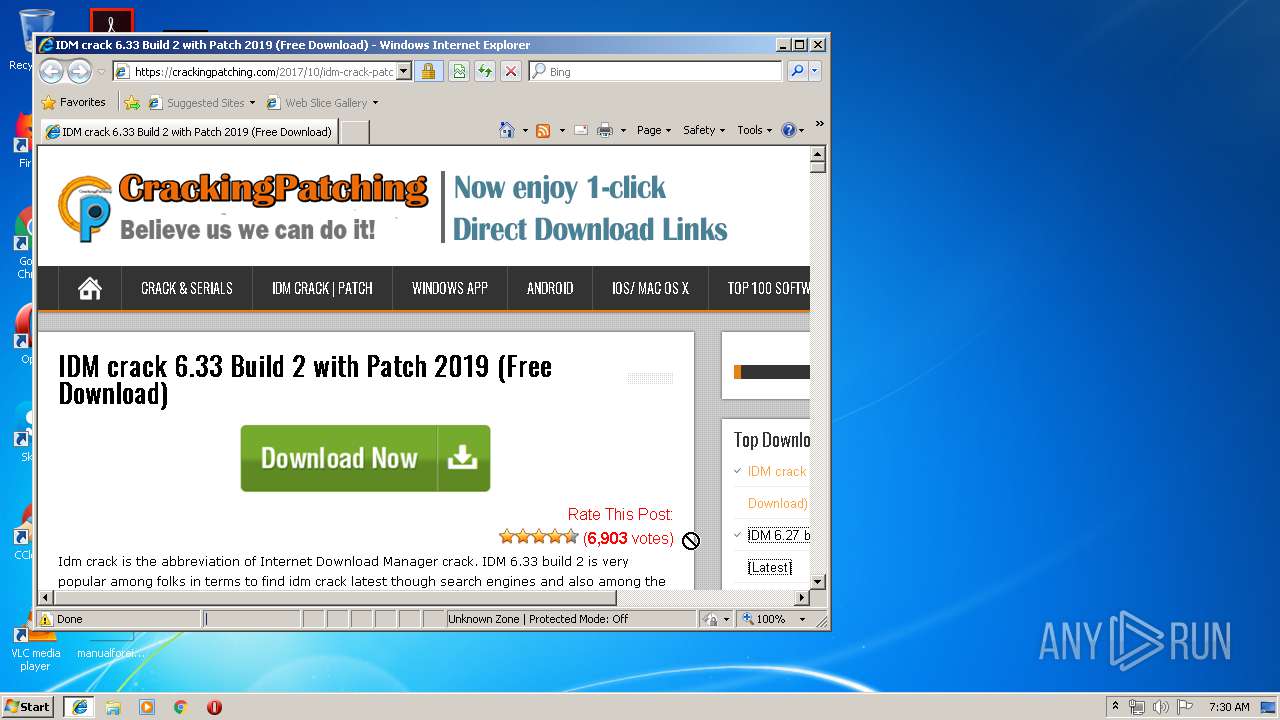
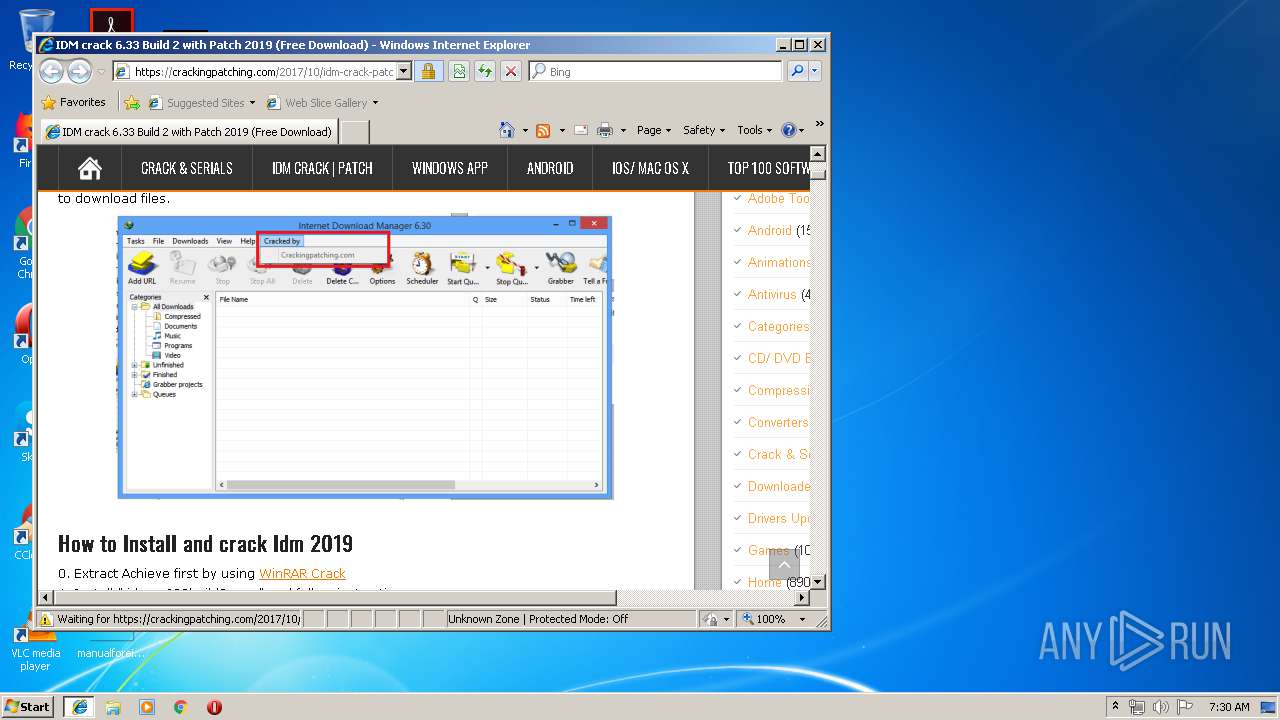
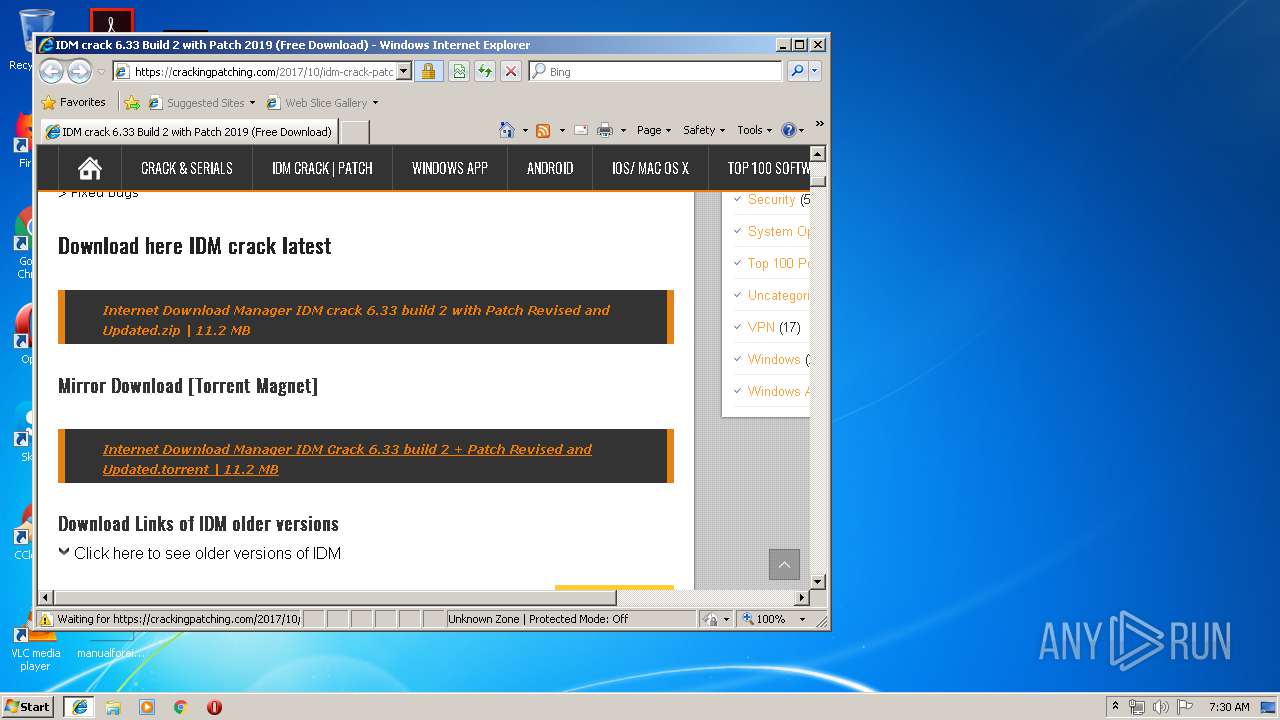
| File name: | 64bit Patch build 2.exe |
| Full analysis: | https://app.any.run/tasks/cc6b701e-089b-418e-bf73-4210c8e0e87e |
| Verdict: | Suspicious activity |
| Analysis date: | May 17, 2019, 06:29:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 72E461E757D7CD281A5FF723D37C934E |
| SHA1: | 95247A55125BF754FAF0A002F4FCB61AD4C0E758 |
| SHA256: | 2CFC7273B4FD2FA6E93300B38F2FBC6653BF2D60BB3583CB2966411193BE7489 |
| SSDEEP: | 49152:OAI+l1h6AlDjNMvKSXFMHZexSoXG+SV0fwAfOsSm:OAI+fhXDjGvKSXFMUwoFDSm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- 64bit Patch build 2.exe (PID: 3232)
Creates a software uninstall entry
- 64bit Patch build 2.exe (PID: 3232)
Starts Internet Explorer
- 64bit Patch build 2.exe (PID: 3232)
Creates files in the program directory
- 64bit Patch build 2.exe (PID: 3232)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 304)
Creates files in the user directory
- iexplore.exe (PID: 304)
Changes internet zones settings
- iexplore.exe (PID: 2944)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 304)
Application launched itself
- iexplore.exe (PID: 2944)
Changes settings of System certificates
- iexplore.exe (PID: 304)
Reads Internet Cache Settings
- iexplore.exe (PID: 304)
Adds / modifies Windows certificates
- iexplore.exe (PID: 304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (37.4) |
|---|---|---|
| .scr | | | Windows screen saver (34.5) |
| .exe | | | Win32 Executable (generic) (11.9) |
| .exe | | | Win16/32 Executable Delphi generic (5.4) |
| .exe | | | Generic Win/DOS Executable (5.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 148992 |
| InitializedDataSize: | 314880 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25468 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | - |
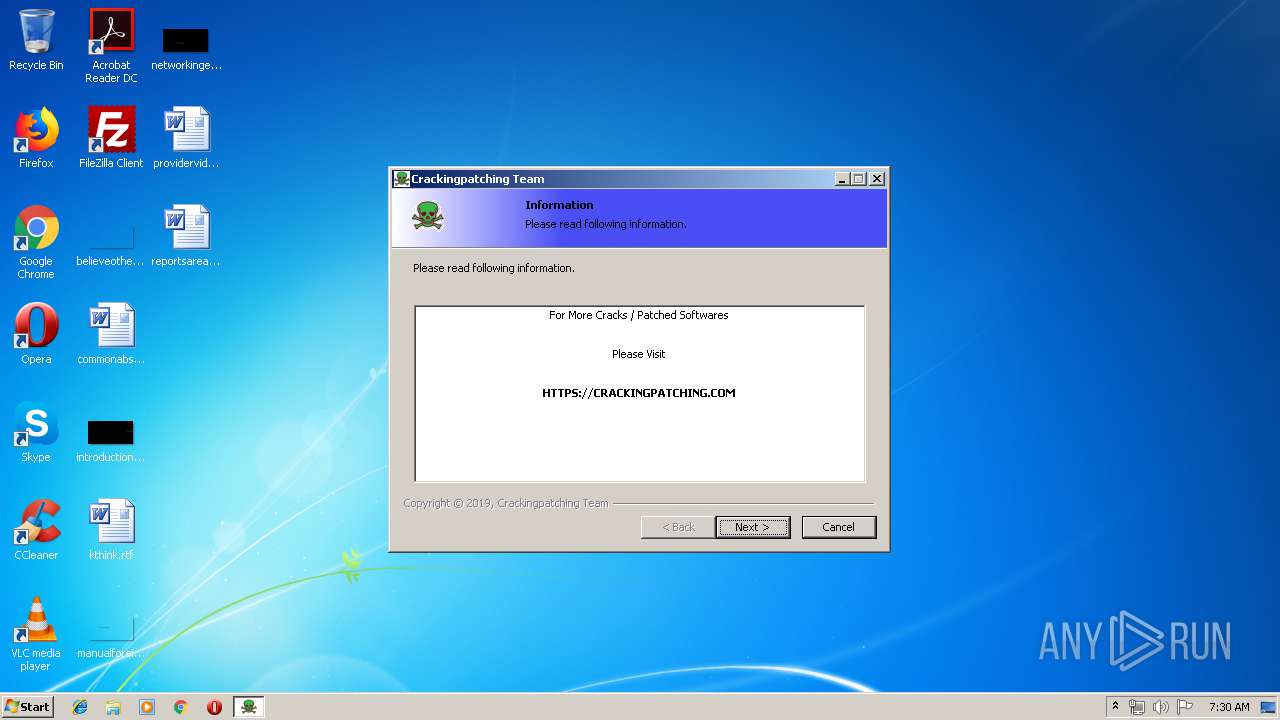
| CompanyName: | Crackingpatching.com Team |
| FileDescription: | IDM Patch 6.33 build 2 6.33 build 2 Installation |
| FileVersion: | 6.33 build 2 |
| LegalCopyright: | Crackingpatching.com Team |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
| Comments: | - |
| CompanyName: | Crackingpatching.com Team |
| FileDescription: | IDM Patch 6.33 build 2 6.33 build 2 Installation |
| FileVersion: | 6.33 build 2 |
| LegalCopyright: | Crackingpatching.com Team |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x000244CC | 0x00024600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.59443 |
DATA | 0x00026000 | 0x00002894 | 0x00002A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.79376 |
BSS | 0x00029000 | 0x000010F5 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x0002B000 | 0x00001798 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.88555 |
.tls | 0x0002D000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0002E000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0.204488 |
.reloc | 0x0002F000 | 0x00001884 | 0x00001A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 6.58665 |
.rsrc | 0x00031000 | 0x00046F60 | 0x00047000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 4.14043 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.93923 | 886 | UNKNOWN | Russian - Russia | RT_MANIFEST |
50 | 5.24025 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
51 | 4.94231 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
52 | 4.73718 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
53 | 4.51902 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
54 | 4.05378 | 270376 | UNKNOWN | UNKNOWN | RT_ICON |
DVCLAL | 4 | 16 | UNKNOWN | UNKNOWN | RT_RCDATA |
PACKAGEINFO | 5.28362 | 272 | UNKNOWN | UNKNOWN | RT_RCDATA |
MAINICON | 2.75922 | 76 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
advapi32.dll |
cabinet.dll |
comctl32.dll |
gdi32.dll |
kernel32.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
user32.dll |
winmm.dll |
Total processes
40
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2944 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2944 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | 64bit Patch build 2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2956 | "C:\Users\admin\AppData\Local\Temp\64bit Patch build 2.exe" | C:\Users\admin\AppData\Local\Temp\64bit Patch build 2.exe | — | explorer.exe | |||||||||||
User: admin Company: Crackingpatching.com Team Integrity Level: MEDIUM Description: IDM Patch 6.33 build 2 6.33 build 2 Installation Exit code: 3221226540 Version: 6.33 build 2 Modules
| |||||||||||||||
| 3232 | "C:\Users\admin\AppData\Local\Temp\64bit Patch build 2.exe" | C:\Users\admin\AppData\Local\Temp\64bit Patch build 2.exe | explorer.exe | ||||||||||||
User: admin Company: Crackingpatching.com Team Integrity Level: HIGH Description: IDM Patch 6.33 build 2 6.33 build 2 Installation Exit code: 0 Version: 6.33 build 2 Modules
| |||||||||||||||
Total events
519
Read events
409
Write events
109
Delete events
1
Modification events
| (PID) Process: | (3232) 64bit Patch build 2.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager |
| Operation: | write | Name: | FName |
Value: CrackingPatching | |||
| (PID) Process: | (3232) 64bit Patch build 2.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager |
| Operation: | write | Name: | LName |
Value: com | |||
| (PID) Process: | (3232) 64bit Patch build 2.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager |
| Operation: | write | Name: | |
Value: info@tonec.com | |||
| (PID) Process: | (3232) 64bit Patch build 2.exe | Key: | HKEY_CURRENT_USER\Software\DownloadManager |
| Operation: | write | Name: | Serial |
Value: 9QNBL-L2641-Y7WVE-QEN3I | |||
| (PID) Process: | (3232) 64bit Patch build 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\DownloadManager |
| Operation: | write | Name: | FName |
Value: CP | |||
| (PID) Process: | (3232) 64bit Patch build 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\DownloadManager |
| Operation: | write | Name: | LName |
Value: com | |||
| (PID) Process: | (3232) 64bit Patch build 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\DownloadManager |
| Operation: | write | Name: | |
Value: info@karanpc.com | |||
| (PID) Process: | (3232) 64bit Patch build 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\DownloadManager |
| Operation: | write | Name: | Serial |
Value: 9QNBL-L2641-Y7WVE-QEN3I | |||
| (PID) Process: | (3232) 64bit Patch build 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\DownloadManager |
| Operation: | write | Name: | FName |
Value: CP | |||
| (PID) Process: | (3232) 64bit Patch build 2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\DownloadManager |
| Operation: | write | Name: | LName |
Value: com | |||
Executable files
3
Suspicious files
3
Text files
96
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3232 | 64bit Patch build 2.exe | C:\Users\admin\AppData\Local\Temp\$inst\temp_0.tmp | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2944 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3232 | 64bit Patch build 2.exe | C:\Users\admin\AppData\Local\Temp\$inst\16.tmp | text | |
MD5:— | SHA256:— | |||
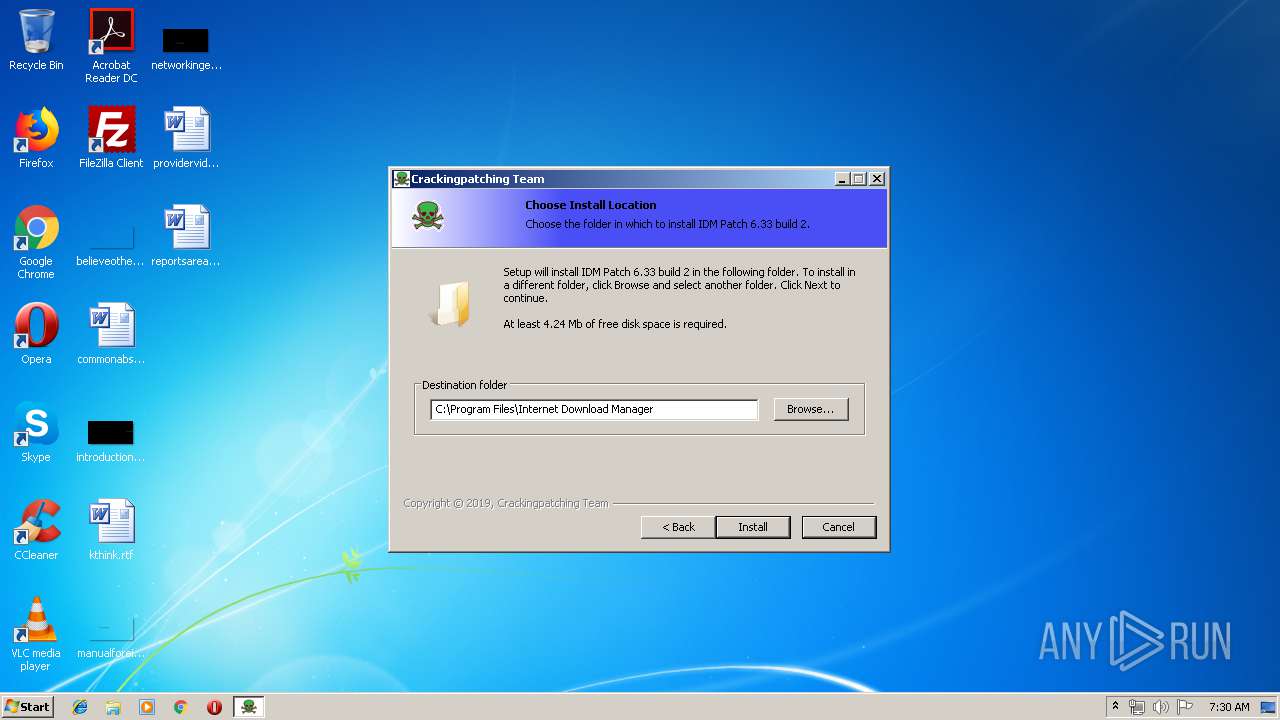
| 3232 | 64bit Patch build 2.exe | C:\Program Files\Internet Download Manager\IDM Patch Uninstaller 6.33 build 2.exe | executable | |
MD5:— | SHA256:— | |||
| 3232 | 64bit Patch build 2.exe | C:\Users\admin\AppData\Local\Temp\$inst\2.tmp | compressed | |
MD5:— | SHA256:— | |||
| 304 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@crackingpatching[1].txt | text | |
MD5:— | SHA256:— | |||
| 304 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\styles[1].css | text | |
MD5:— | SHA256:— | |||
| 3232 | 64bit Patch build 2.exe | C:\Program Files\Internet Download Manager\IDMan.exe | executable | |
MD5:— | SHA256:— | |||
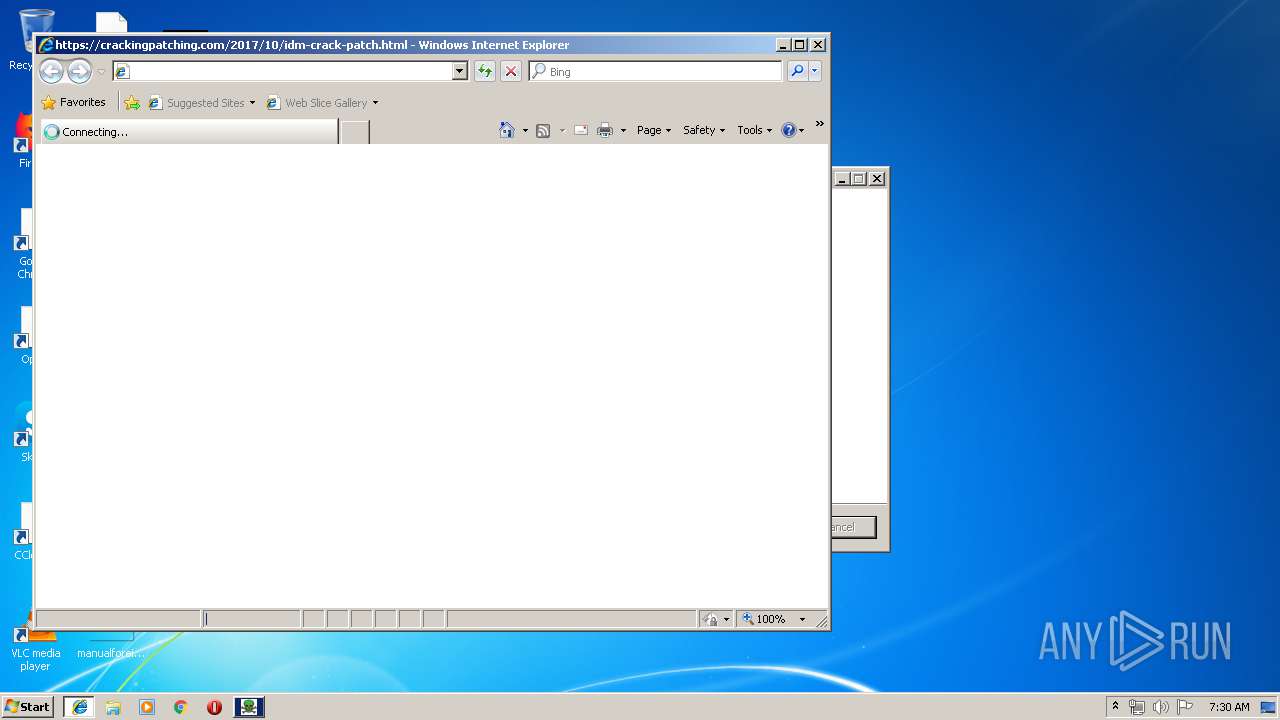
| 304 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\idm-crack-patch[1].html | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
36
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2944 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 172.217.21.206:80 | — | Google Inc. | US | whitelisted |
2944 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
304 | iexplore.exe | 104.18.57.24:443 | crackingpatching.com | Cloudflare Inc | US | shared |
304 | iexplore.exe | 216.58.210.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
304 | iexplore.exe | 172.217.22.2:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
304 | iexplore.exe | 172.217.16.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
304 | iexplore.exe | 192.0.78.17:443 | wordpress.com | Automattic, Inc | US | unknown |
304 | iexplore.exe | 172.217.18.110:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
304 | iexplore.exe | 192.0.77.2:443 | i1.wp.com | Automattic, Inc | US | suspicious |
304 | iexplore.exe | 192.0.77.32:443 | s0.wp.com | Automattic, Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crackingpatching.com |
| malicious |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
wordpress.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
i1.wp.com |
| whitelisted |
i2.wp.com |
| whitelisted |
i0.wp.com |
| whitelisted |