| File name: | directx 12 setup.exe |
| Full analysis: | https://app.any.run/tasks/d378fa08-1544-48d1-b533-0decff1cab93 |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2025, 17:12:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, MS CAB-Installer self-extracting archive, 3 sections |
| MD5: | 2CBD6AD183914A0C554F0739069E77D7 |
| SHA1: | 7BF35F2AFCA666078DB35CA95130BEB2E3782212 |
| SHA256: | 2CF71D098C608C56E07F4655855A886C3102553F648DF88458DF616B26FD612F |
| SSDEEP: | 6144:kWK8fc2liXmrLxcdRDLiH1vVRGVOhMp421/7YQV:VcvgLARDI1KIOzO0 |
MALICIOUS
Changes the autorun value in the registry
- directx 12 setup.exe (PID: 6540)
SUSPICIOUS
Process drops legitimate windows executable
- directx 12 setup.exe (PID: 6540)
- dxwsetup.exe (PID: 6668)
Starts a Microsoft application from unusual location
- directx 12 setup.exe (PID: 6388)
- directx 12 setup.exe (PID: 6540)
- dxwsetup.exe (PID: 6668)
Executable content was dropped or overwritten
- directx 12 setup.exe (PID: 6540)
- dxwsetup.exe (PID: 6668)
Reads security settings of Internet Explorer
- dxwsetup.exe (PID: 6668)
Checks Windows Trust Settings
- dxwsetup.exe (PID: 6668)
INFO
The sample compiled with english language support
- directx 12 setup.exe (PID: 6540)
- dxwsetup.exe (PID: 6668)
Checks supported languages
- directx 12 setup.exe (PID: 6540)
- dxwsetup.exe (PID: 6668)
Create files in a temporary directory
- directx 12 setup.exe (PID: 6540)
- dxwsetup.exe (PID: 6668)
Reads the computer name
- dxwsetup.exe (PID: 6668)
Checks proxy server information
- dxwsetup.exe (PID: 6668)
Reads the machine GUID from the registry
- dxwsetup.exe (PID: 6668)
Creates files or folders in the user directory
- dxwsetup.exe (PID: 6668)
Reads the software policy settings
- dxwsetup.exe (PID: 6668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2001:08:18 01:42:57+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7 |
| CodeSize: | 34816 |
| InitializedDataSize: | 250368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5a5e |
| OSVersion: | 5.1 |
| ImageVersion: | 5.1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.2600.0 |
| ProductVersionNumber: | 6.0.2600.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
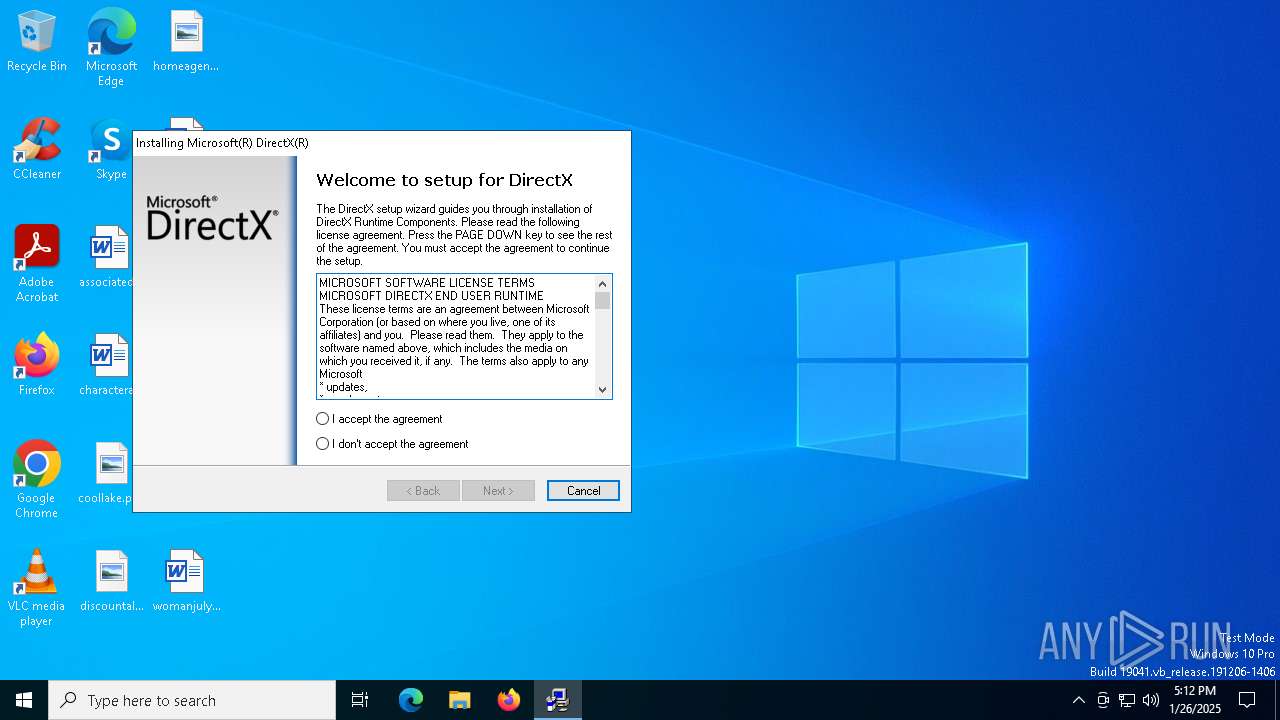
| FileDescription: | DirectX 9.0 Web setup |
| FileVersion: | 9.29.1974.0 |
| InternalName: | DXWebSetup |
| LegalCopyright: | Copyright (c) Microsoft Corporation. All rights reserved. |
| OriginalFileName: | dxwebsetup.exe |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 9.29.1974.0 |
Total processes
131
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6388 | "C:\Users\admin\AppData\Local\Temp\directx 12 setup.exe" | C:\Users\admin\AppData\Local\Temp\directx 12 setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DirectX 9.0 Web setup Exit code: 3221226540 Version: 9.29.1974.0 Modules
| |||||||||||||||
| 6540 | "C:\Users\admin\AppData\Local\Temp\directx 12 setup.exe" | C:\Users\admin\AppData\Local\Temp\directx 12 setup.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DirectX 9.0 Web setup Version: 9.29.1974.0 Modules
| |||||||||||||||
| 6668 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.exe | directx 12 setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DirectX Setup Version: 4.9.0.0904 Modules
| |||||||||||||||
Total events
3 964
Read events
3 960
Write events
4
Delete events
0
Modification events
| (PID) Process: | (6540) directx 12 setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
| (PID) Process: | (6668) dxwsetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6668) dxwsetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6668) dxwsetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
11
Suspicious files
227
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6540 | directx 12 setup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dsetup32.dll | executable | |
MD5:A5412A144F63D639B47FCC1BA68CB029 | SHA256:8A011DA043A4B81E2B3D41A332E0FF23A65D546BD7636E8BC74885E8746927D6 | |||
| 6540 | directx 12 setup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.cif | text | |
MD5:7B1FBE9F5F43B2261234B78FE115CF8E | SHA256:762FF640013DB2BD4109D7DF43A867303093815751129BD1E33F16BF02E52CCE | |||
| 6668 | dxwsetup.exe | C:\Windows\msdownld.tmp\AS1374B6.tmp\dxupdate.cab | compressed | |
MD5:4AFD7F5C0574A0EFD163740ECB142011 | SHA256:6E39B3FDB6722EA8AA0DC8F46AE0D8BD6496DD0F5F56BAC618A0A7DD22D6CFB2 | |||
| 6540 | directx 12 setup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.exe | executable | |
MD5:AC3A5F7BE8CD13A863B50AB5FE00B71C | SHA256:8F5E89298E3DC2E22D47515900C37CCA4EE121C5BA06A6D962D40AD6E1A595DA | |||
| 6668 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\SET57B8.tmp | executable | |
MD5:984CAD22FA542A08C5D22941B888D8DC | SHA256:57BC22850BB8E0BCC511A9B54CD3DA18EEC61F3088940C07D63B9B74E7FE2308 | |||
| 6540 | directx 12 setup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.inf | text | |
MD5:AD8982EAA02C7AD4D7CDCBC248CAA941 | SHA256:D63C35E9B43EB0F28FFC28F61C9C9A306DA9C9DE3386770A7EB19FAA44DBFC00 | |||
| 6668 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\filelist.dat | text | |
MD5:CC85D7649546D3C0B1607F761B73FEC2 | SHA256:E1C85577FEE77B7535AF5918DE16479D5B38F08D7AADBF1B3613D275C7797920 | |||
| 6668 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\dsetup.dll | executable | |
MD5:984CAD22FA542A08C5D22941B888D8DC | SHA256:57BC22850BB8E0BCC511A9B54CD3DA18EEC61F3088940C07D63B9B74E7FE2308 | |||
| 6668 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\SET57C9.tmp | executable | |
MD5:A5412A144F63D639B47FCC1BA68CB029 | SHA256:8A011DA043A4B81E2B3D41A332E0FF23A65D546BD7636E8BC74885E8746927D6 | |||
| 6668 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\dsetup32.dll | executable | |
MD5:A5412A144F63D639B47FCC1BA68CB029 | SHA256:8A011DA043A4B81E2B3D41A332E0FF23A65D546BD7636E8BC74885E8746927D6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
81
TCP/UDP connections
37
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6668 | dxwsetup.exe | GET | 302 | 104.119.108.209:80 | http://download.microsoft.com/download/1/7/1/1718CCC4-6315-4D8E-9543-8E28A4E18C4C/dxupdate.cab | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6668 | dxwsetup.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6668 | dxwsetup.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
6668 | dxwsetup.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6620 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6668 | dxwsetup.exe | GET | 302 | 104.119.108.209:80 | http://download.microsoft.com/download/1/7/1/1718CCC4-6315-4D8E-9543-8E28A4E18C4C/Apr2006_xinput_x86.cab | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6092 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
download.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
Process | Message |
|---|---|
dxwsetup.exe | Invalid parameter passed to C runtime function.
|
dxwsetup.exe | DLL_PROCESS_ATTACH |
dxwsetup.exe | Invalid parameter passed to C runtime function.
|
dxwsetup.exe | DLL_PROCESS_ATTACH |
dxwsetup.exe | DLL_PROCESS_DETACH |
dxwsetup.exe | DLL_PROCESS_DETACH |