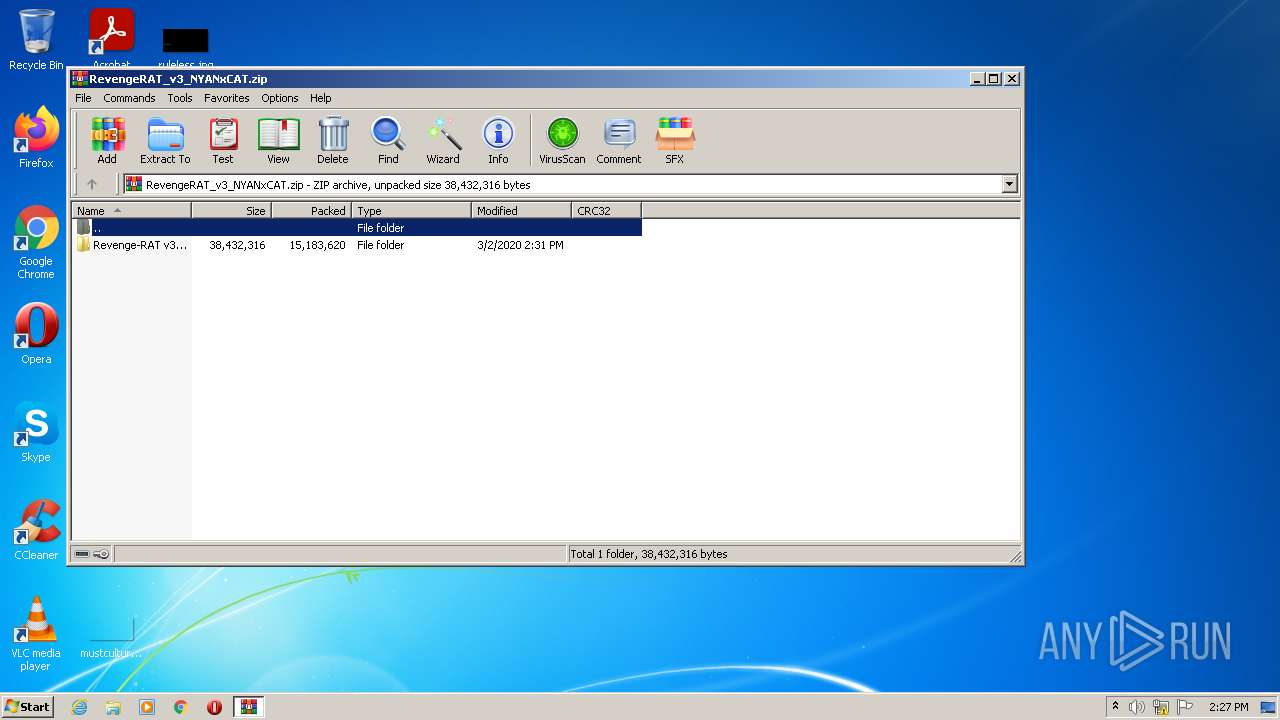
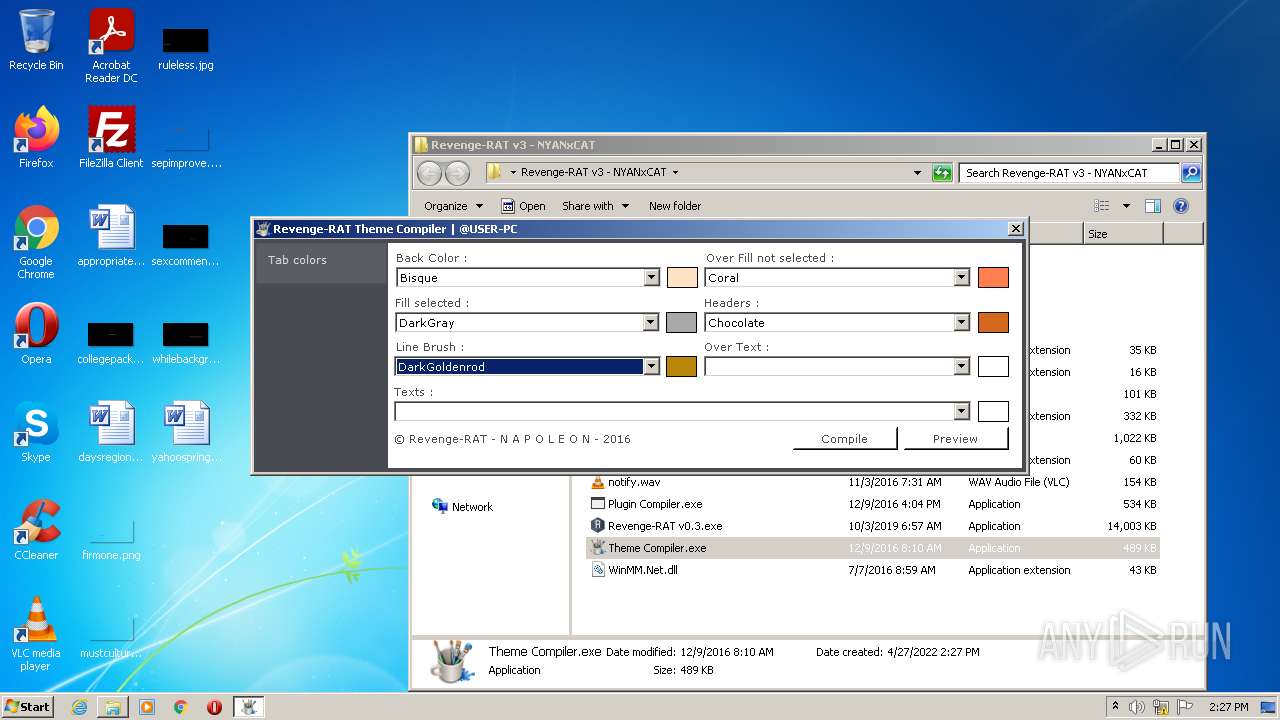
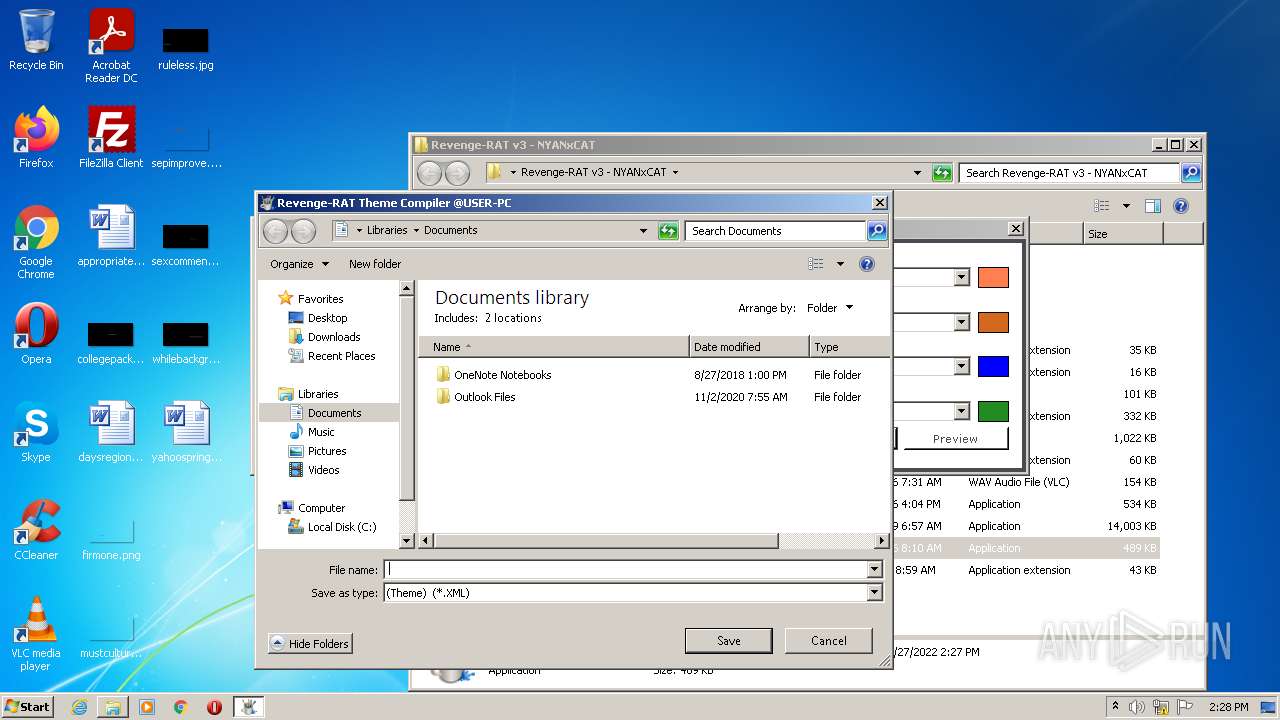
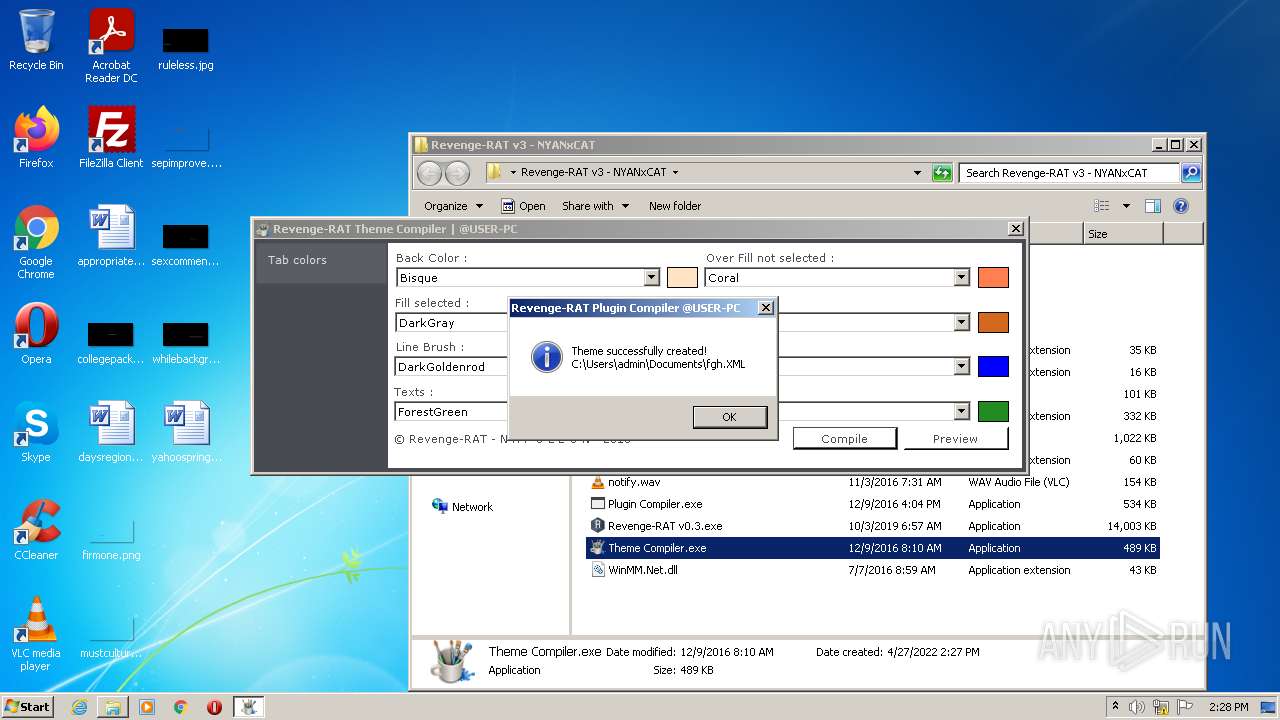
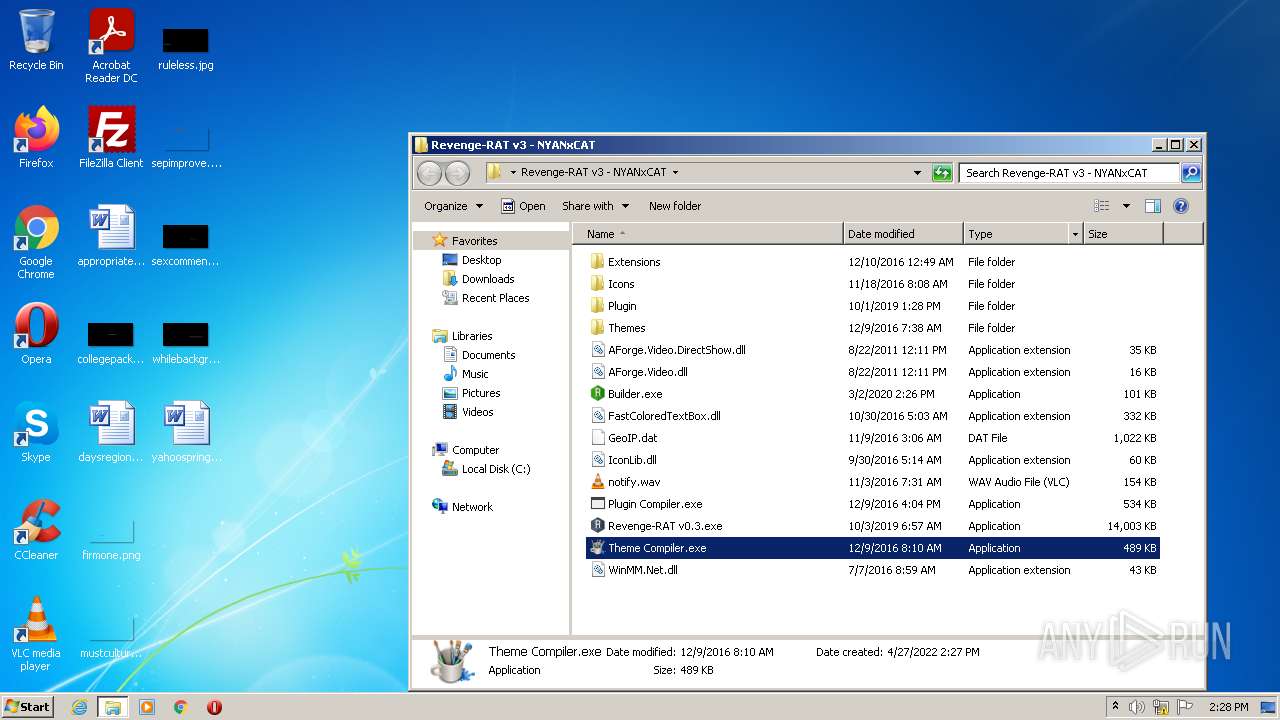
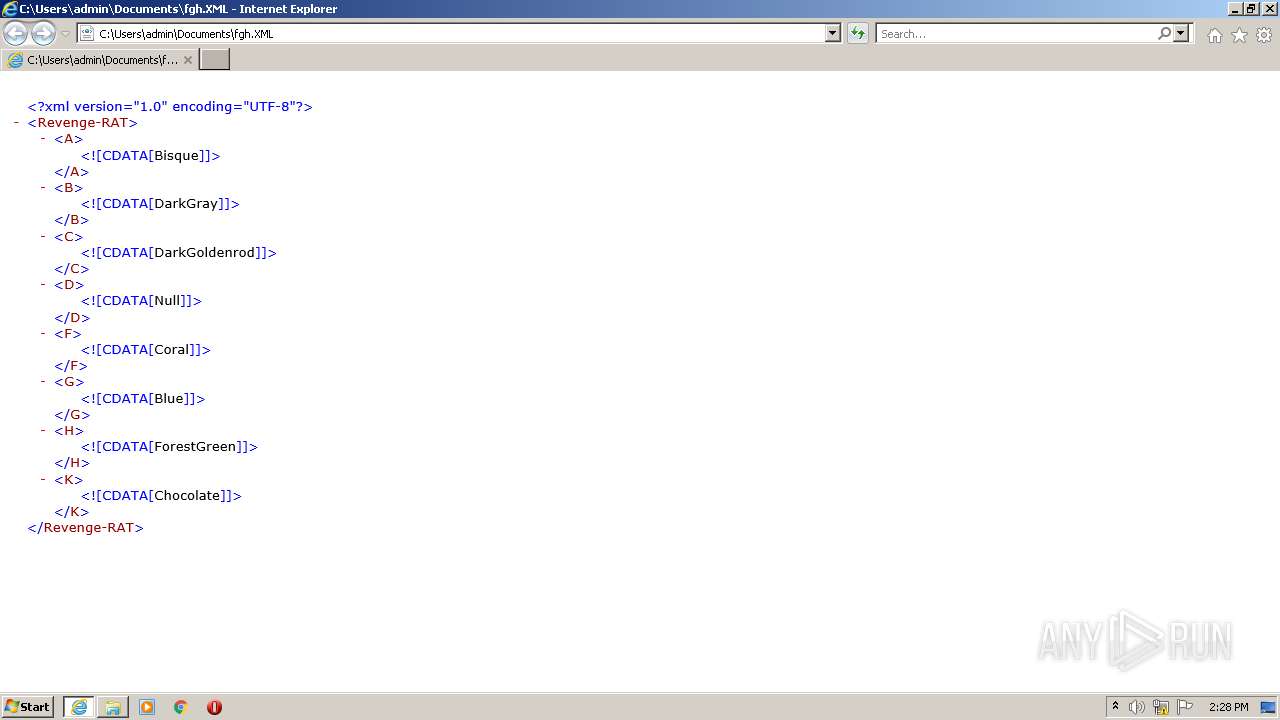
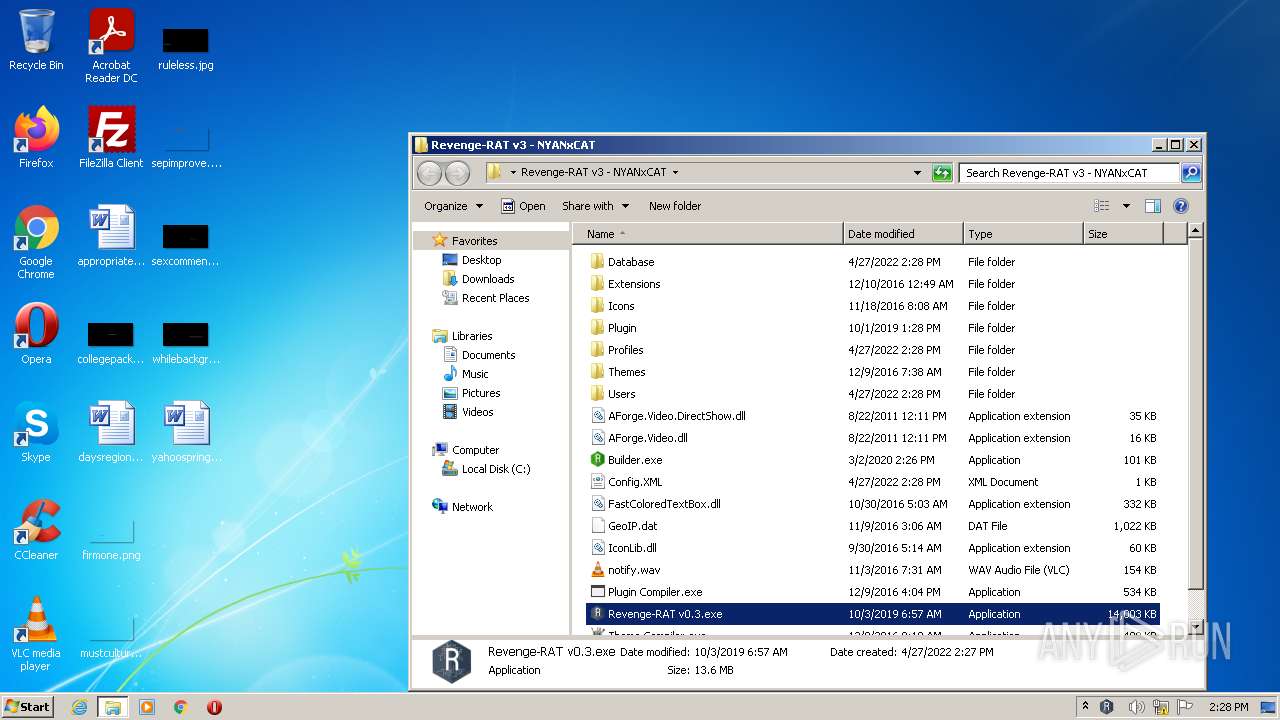
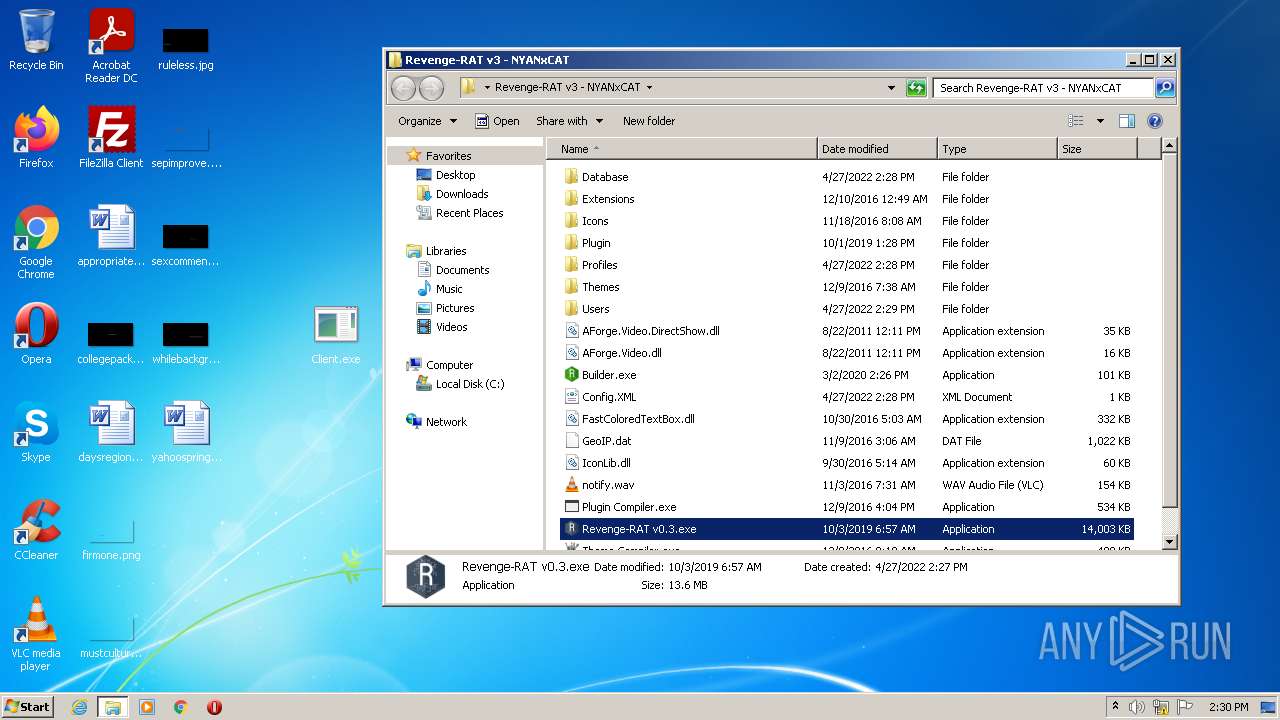
| File name: | RevengeRAT_v3_NYANxCAT.zip |
| Full analysis: | https://app.any.run/tasks/7b954c3b-62ee-4a9f-a2eb-c3e75667044a |
| Verdict: | Malicious activity |
| Analysis date: | April 27, 2022, 13:27:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 92100F76EEC604E09DCCC3F260100376 |
| SHA1: | C6B77D72BDA8CC86675D2A4F970455E4616D7701 |
| SHA256: | 2CF26E5FE9F31386D57170CC51EC46D6E4B73E4760826D65CA1A7AFC8C82ACC2 |
| SSDEEP: | 196608:/tYV4fQ+/n+aYoRlLtSXuio66CLjP6U8TFESmWMQxF5PuPmI54US0uRtigUtqY:lYmf9hJvLcXjPiTFESmK0ec4x0uRt3K |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3444)
- Revenge-RAT v0.3.exe (PID: 2460)
Drops executable file immediately after starts
- WinRAR.exe (PID: 3500)
- csc.exe (PID: 4084)
Application was dropped or rewritten from another process
- Theme Compiler.exe (PID: 2424)
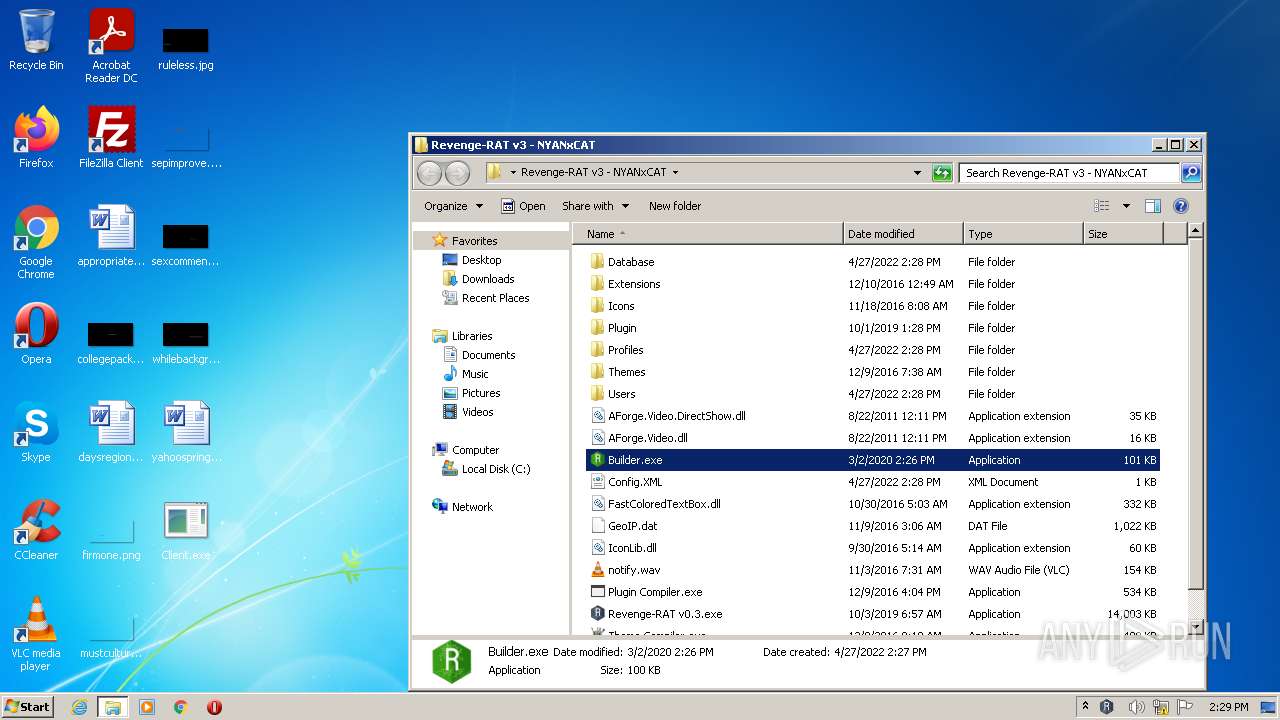
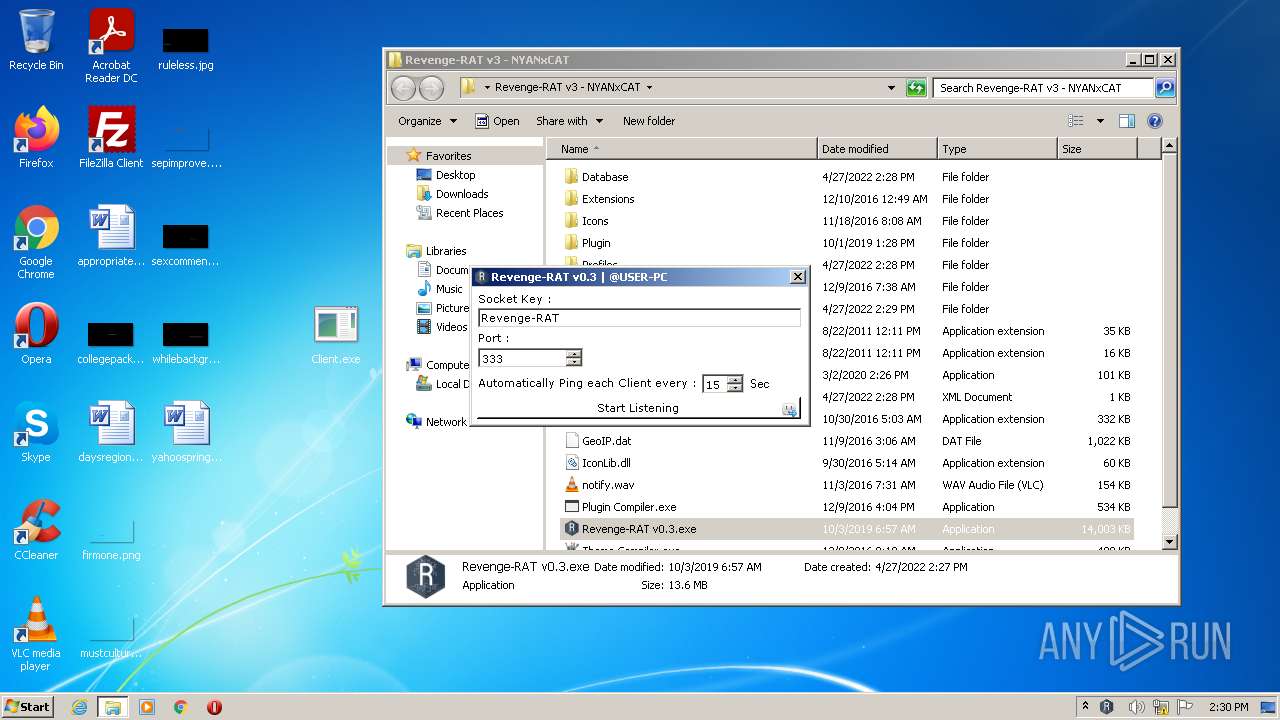
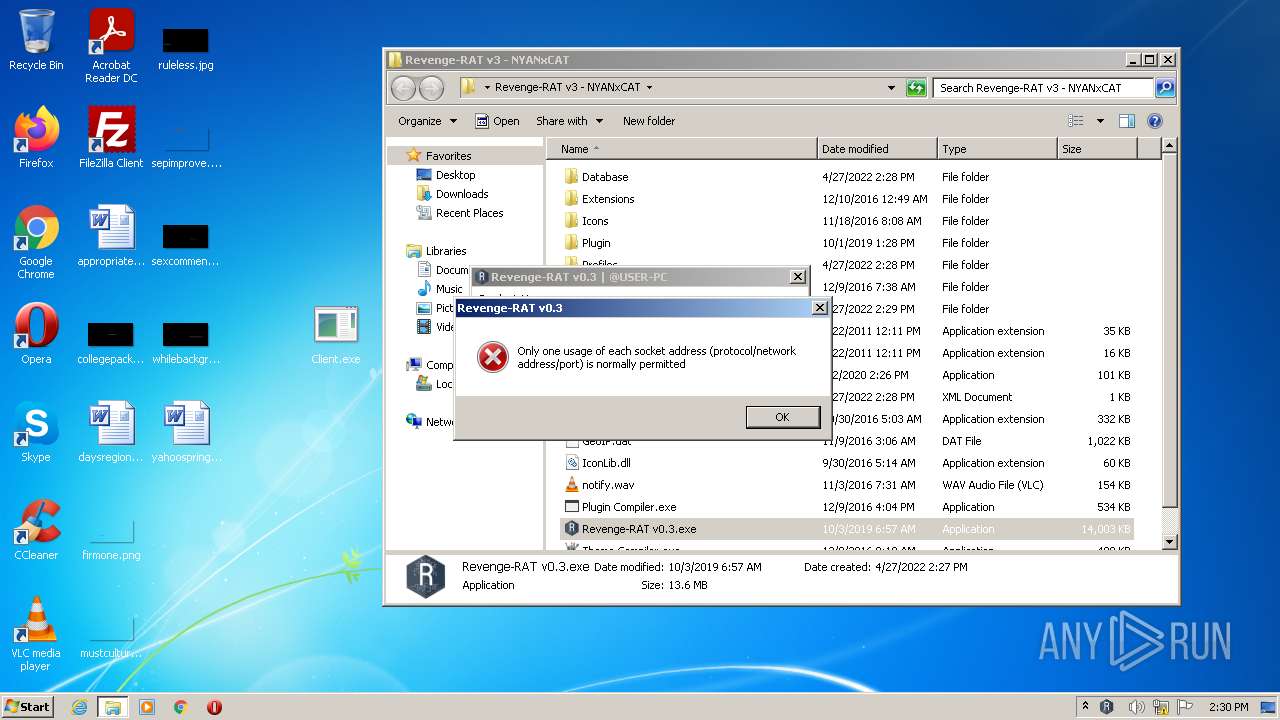
- Revenge-RAT v0.3.exe (PID: 2460)
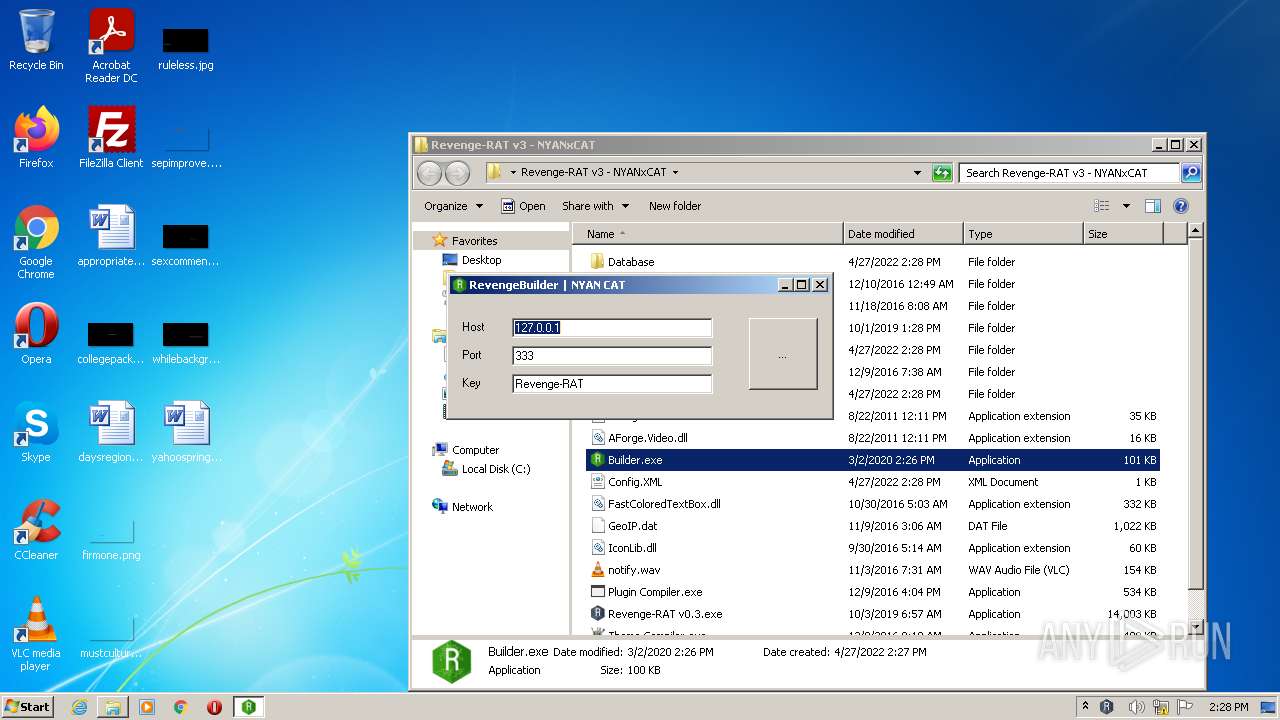
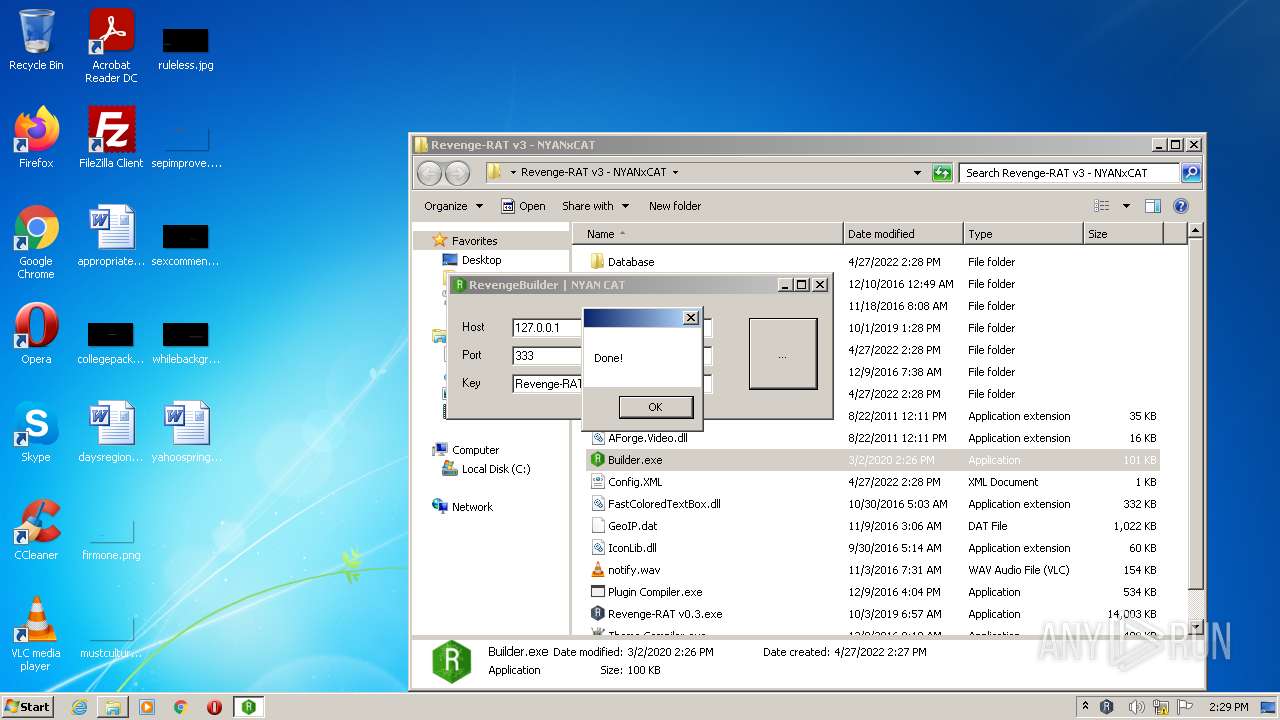
- Builder.exe (PID: 3944)
- Revenge-RAT v0.3.exe (PID: 2064)
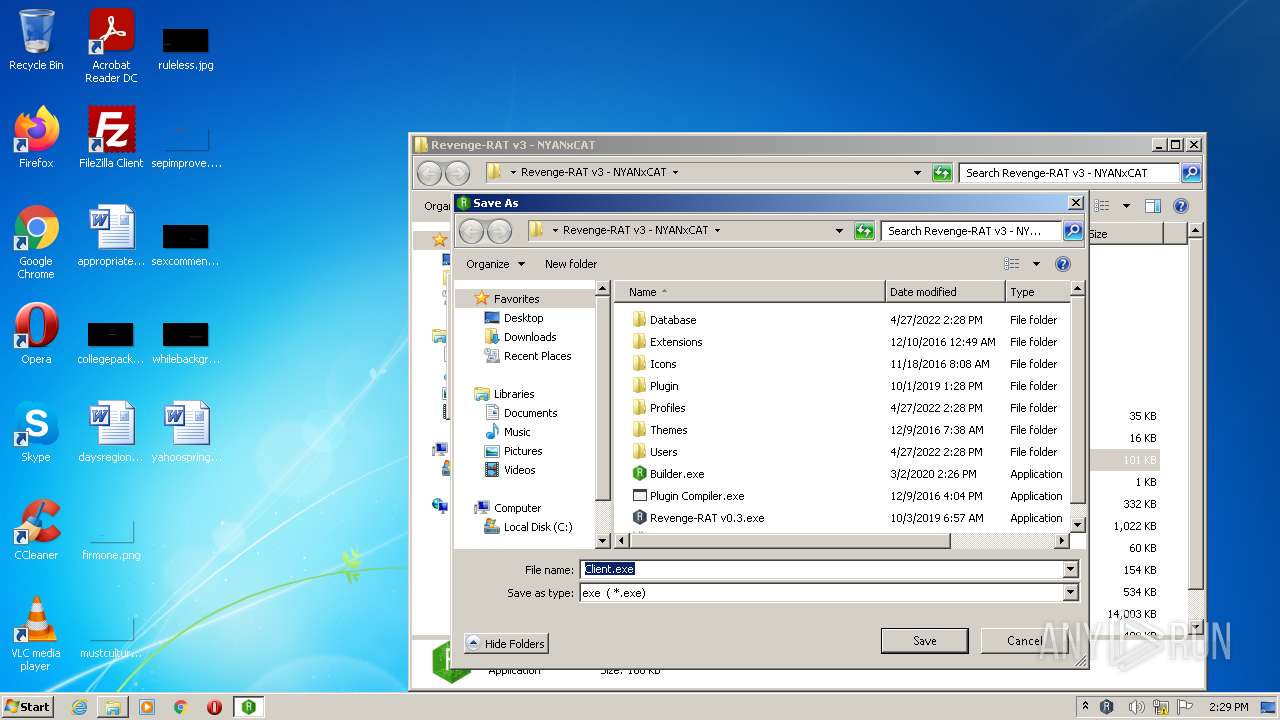
- Client.exe (PID: 3208)
Starts Visual C# compiler
- Builder.exe (PID: 3944)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3500)
- Theme Compiler.exe (PID: 2424)
- Revenge-RAT v0.3.exe (PID: 2460)
- Builder.exe (PID: 3944)
- csc.exe (PID: 4084)
- cvtres.exe (PID: 3628)
- Client.exe (PID: 3208)
- vlc.exe (PID: 3524)
- Revenge-RAT v0.3.exe (PID: 2064)
Reads the computer name
- WinRAR.exe (PID: 3500)
- Theme Compiler.exe (PID: 2424)
- Revenge-RAT v0.3.exe (PID: 2460)
- Builder.exe (PID: 3944)
- Client.exe (PID: 3208)
- vlc.exe (PID: 3524)
- Revenge-RAT v0.3.exe (PID: 2064)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3500)
- csc.exe (PID: 4084)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3500)
- csc.exe (PID: 4084)
Starts Internet Explorer
- MSOXMLED.EXE (PID: 3192)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3848)
- iexplore.exe (PID: 2224)
Reads internet explorer settings
- Revenge-RAT v0.3.exe (PID: 2460)
Reads Environment values
- Client.exe (PID: 3208)
Reads CPU info
- Client.exe (PID: 3208)
Creates files in the user directory
- vlc.exe (PID: 3524)
Modifies files in Chrome extension folder
- chrome.exe (PID: 372)
INFO
Manual execution by user
- MSOXMLED.EXE (PID: 3192)
- Theme Compiler.exe (PID: 2424)
- Builder.exe (PID: 3944)
- Revenge-RAT v0.3.exe (PID: 2460)
- Client.exe (PID: 3208)
- vlc.exe (PID: 3524)
- chrome.exe (PID: 372)
- Revenge-RAT v0.3.exe (PID: 2064)
Checks supported languages
- iexplore.exe (PID: 2208)
- MSOXMLED.EXE (PID: 3192)
- iexplore.exe (PID: 3848)
- iexplore.exe (PID: 2224)
- chrome.exe (PID: 372)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 584)
- chrome.exe (PID: 2332)
- chrome.exe (PID: 2128)
- chrome.exe (PID: 1544)
- chrome.exe (PID: 2828)
- chrome.exe (PID: 2120)
- chrome.exe (PID: 2900)
- chrome.exe (PID: 1076)
Application launched itself
- iexplore.exe (PID: 2208)
- chrome.exe (PID: 372)
Reads the computer name
- iexplore.exe (PID: 3848)
- MSOXMLED.EXE (PID: 3192)
- iexplore.exe (PID: 2208)
- iexplore.exe (PID: 2224)
- chrome.exe (PID: 372)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 2332)
- chrome.exe (PID: 2900)
Changes internet zones settings
- iexplore.exe (PID: 2208)
Reads internet explorer settings
- iexplore.exe (PID: 2224)
- iexplore.exe (PID: 3848)
Reads the date of Windows installation
- iexplore.exe (PID: 2208)
Reads settings of System Certificates
- iexplore.exe (PID: 2208)
- chrome.exe (PID: 2384)
Checks Windows Trust Settings
- iexplore.exe (PID: 2208)
Reads the hosts file
- chrome.exe (PID: 372)
- chrome.exe (PID: 2384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Revenge-RAT v3 - NYANxCAT/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2020:03:02 17:31:09 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 788 |
Total processes
69
Monitored processes
24
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,672910540639994339,4113349212477622571,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1924 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1076 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1060,672910540639994339,4113349212477622571,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2812 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,672910540639994339,4113349212477622571,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2248 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\Desktop\Revenge-RAT v3 - NYANxCAT\Revenge-RAT v0.3.exe" | C:\Users\admin\Desktop\Revenge-RAT v3 - NYANxCAT\Revenge-RAT v0.3.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Revenge-RAT v0.3 Integrity Level: MEDIUM Description: Revenge-RAT v0.3 Exit code: 0 Version: 0.0.0.3 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1060,672910540639994339,4113349212477622571,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2936 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x66abd988,0x66abd998,0x66abd9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2208 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | MSOXMLED.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2224 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2208 CREDAT:78849 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1060,672910540639994339,4113349212477622571,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1052 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
30 406
Read events
30 115
Write events
284
Delete events
7
Modification events
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RevengeRAT_v3_NYANxCAT.zip | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3500) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
20
Suspicious files
45
Text files
126
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
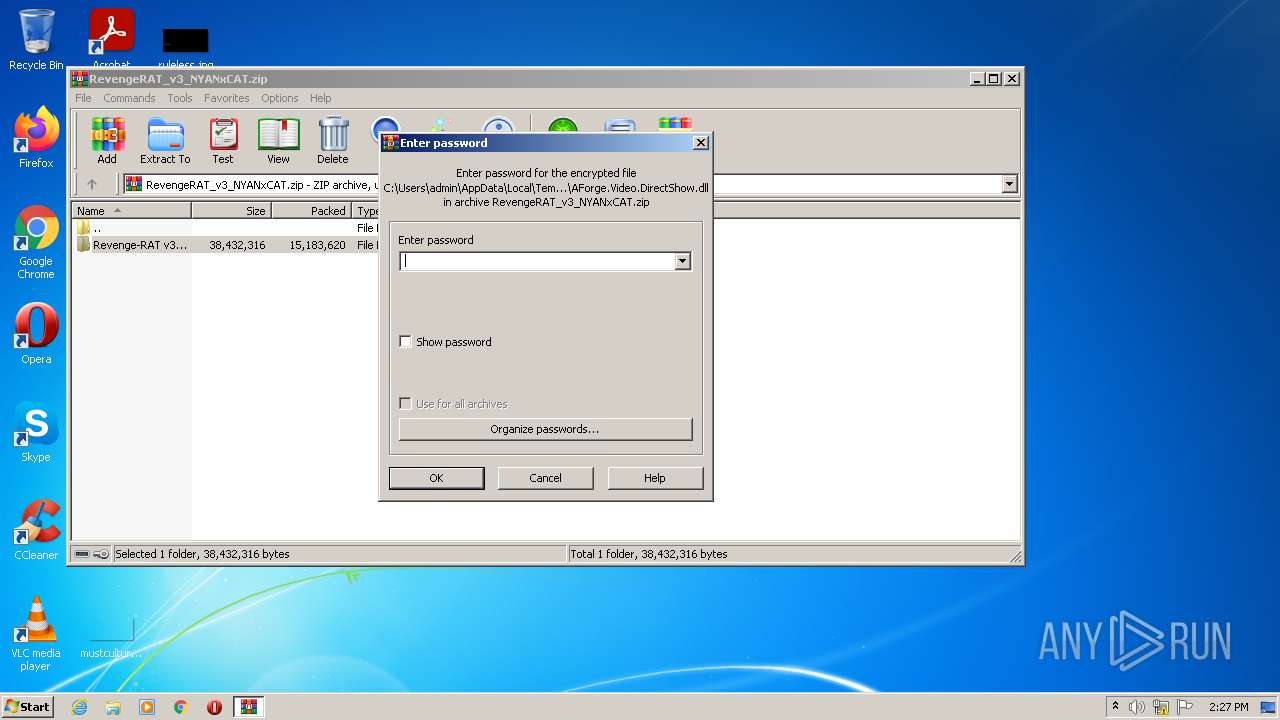
| 3500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3500.21395\Revenge-RAT v3 - NYANxCAT\AForge.Video.DirectShow.dll | executable | |
MD5:2343899EA6B3DFF06A6DB2F0FBD86406 | SHA256:643A7F9754D90D475DB3F84AF7B254A64DD555CED0F039AAA4F08B5B27AB4FDB | |||
| 3500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3500.21395\Revenge-RAT v3 - NYANxCAT\Extensions\AHK\AHK.ahk | text | |
MD5:A908B151CC37C66AEAFF20D43BA0CAE0 | SHA256:B032B99C88289C02388BD1DB21A3CFC34AC9AB36BC48BE5D6570AC6497F70E56 | |||
| 3500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3500.21395\Revenge-RAT v3 - NYANxCAT\Extensions\AHK\AutoHotkeySC.bin | executable | |
MD5:B86564D0EB29A5FAAB9E8DAACF269DF4 | SHA256:2514235C34D17FDB4A8448BD088D89F631F5D70F12F5F7D5EE552144A345ED2D | |||
| 3500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3500.21395\Revenge-RAT v3 - NYANxCAT\Extensions\AHK\Unicode 32-bit.bin | executable | |
MD5:B86564D0EB29A5FAAB9E8DAACF269DF4 | SHA256:2514235C34D17FDB4A8448BD088D89F631F5D70F12F5F7D5EE552144A345ED2D | |||
| 3500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3500.21395\Revenge-RAT v3 - NYANxCAT\Extensions\Aut2Exe\Icons\AutoIt_Main_v10_256x256_RGB-A.ico | image | |
MD5:83918F1A255213FD4448EF834EB3F1E4 | SHA256:B0C2A21CCCB64C4FC11F9BB9DC7F884EED700FE4158C4C36A314258C4F7F6C1A | |||
| 3500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3500.21395\Revenge-RAT v3 - NYANxCAT\Extensions\Aut2Exe\Aut2exe_x64.exe | executable | |
MD5:CECB773C5B0E15B8D1C02840FD118F38 | SHA256:7261BD93161CFE191E354152D489C3721E41D84A87D6C1AF7EAA4DC0C75AB3FF | |||
| 3500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3500.21395\Revenge-RAT v3 - NYANxCAT\Extensions\Aut2Exe\Icons\AutoIt_Main_v9_48x48_RGB-A.ico | image | |
MD5:9019034BC36952EF2539648B95635546 | SHA256:1AF7F2ED9420F5F524AFA5DC2E077F9657D6E13EE153036AA6F71216170C4D6C | |||
| 3500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3500.21395\Revenge-RAT v3 - NYANxCAT\AForge.Video.dll | executable | |
MD5:A614D58E17BA34826B59C4942C32F078 | SHA256:311724FF73B331CD6DE0649B01923F7E43D168AA5B1E7F031B2B175148062757 | |||
| 3500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3500.21395\Revenge-RAT v3 - NYANxCAT\Builder.exe | executable | |
MD5:BE03C752691189795254CEBAB618C21D | SHA256:313A9D09F096B4EB2EFE37E3C0B51268F601C0C9D1CA3508F46769EC89E0594B | |||
| 3500 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3500.21395\Revenge-RAT v3 - NYANxCAT\Extensions\Aut2Exe\Autoit.au3 | text | |
MD5:76592CDB5646CE753B0A032A219CEA41 | SHA256:3B0A9192AE1945357E3E2A05E20C75663BB1788554F50BD5EE7E8B93C5AD1F66 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
13
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2208 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b4125505431d272d | US | compressed | 4.70 Kb | whitelisted |
2208 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2384 | chrome.exe | 142.250.185.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2208 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2208 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2384 | chrome.exe | 142.250.186.33:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
2208 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2384 | chrome.exe | 142.250.181.228:443 | www.google.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 142.250.186.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 142.250.184.206:443 | clients2.google.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 142.250.185.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2384 | chrome.exe | 216.58.212.131:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
iecvlist.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
clients2.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.com |
| malicious |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=i686-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x86/contrib/i686-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc error: stale plugins cache: modified C:\Program Files\VideoLAN\VLC\plugins\access\libaccess_concat_plugin.dll
|