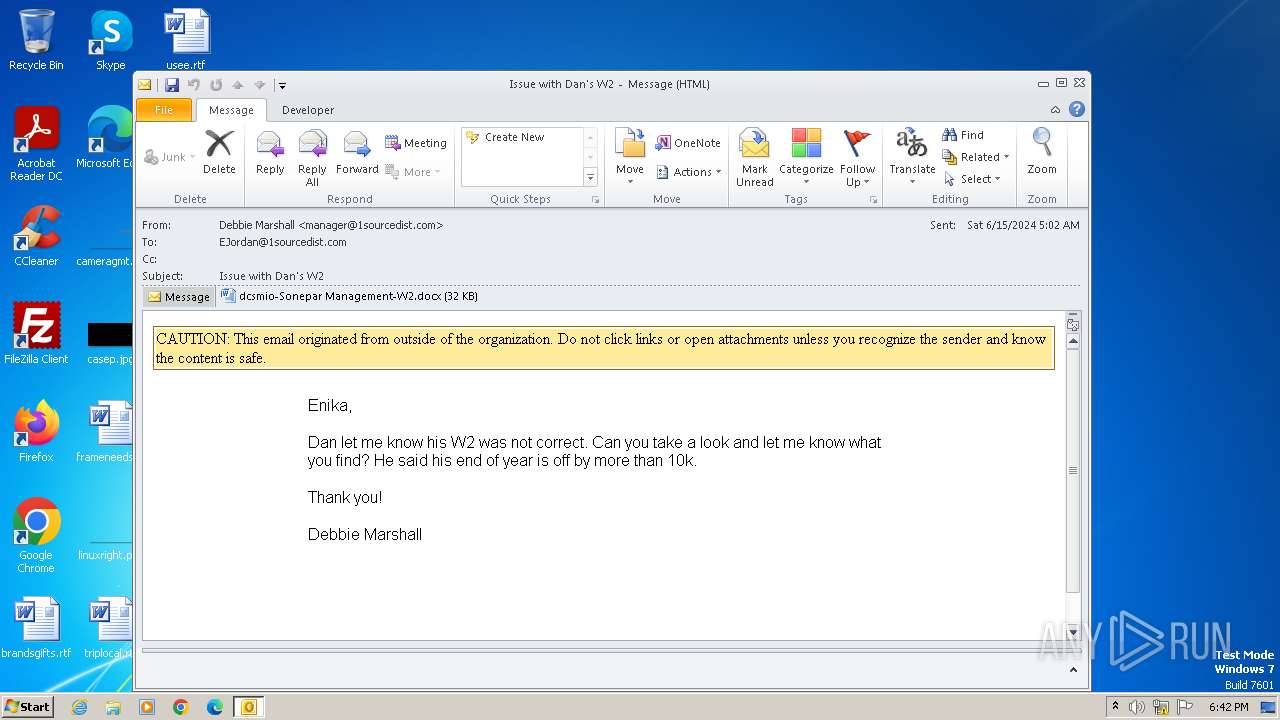
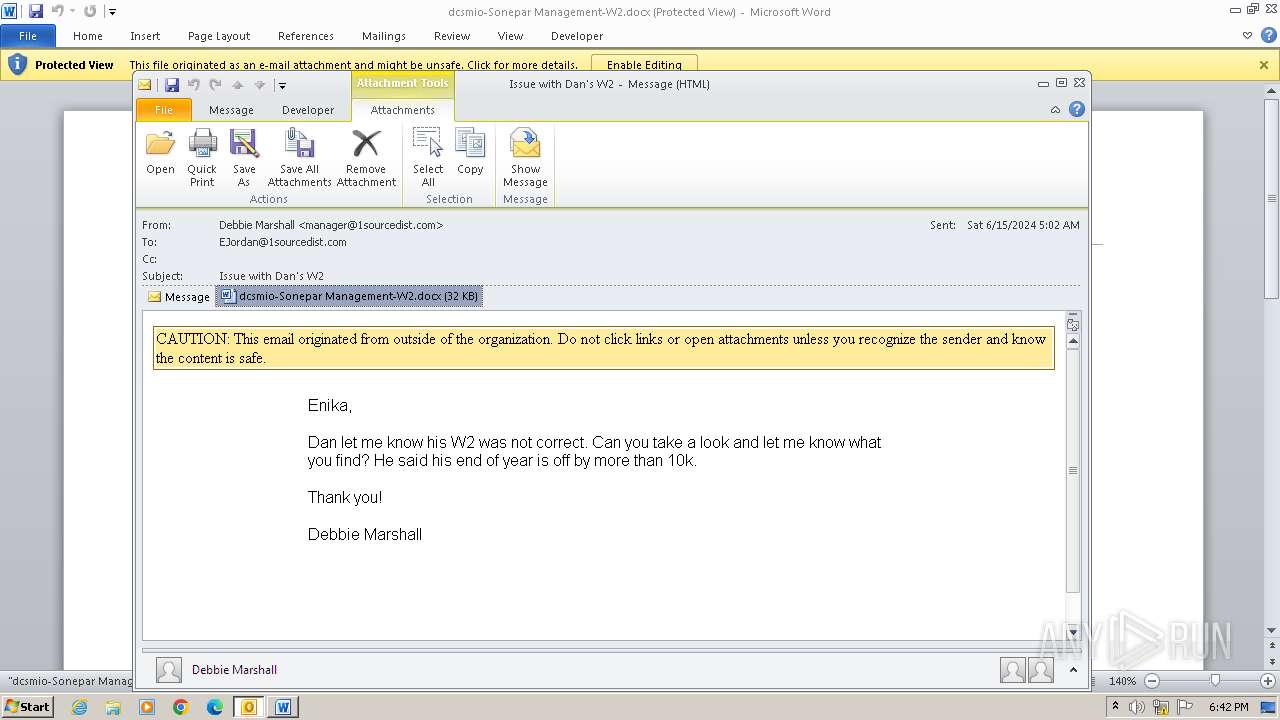
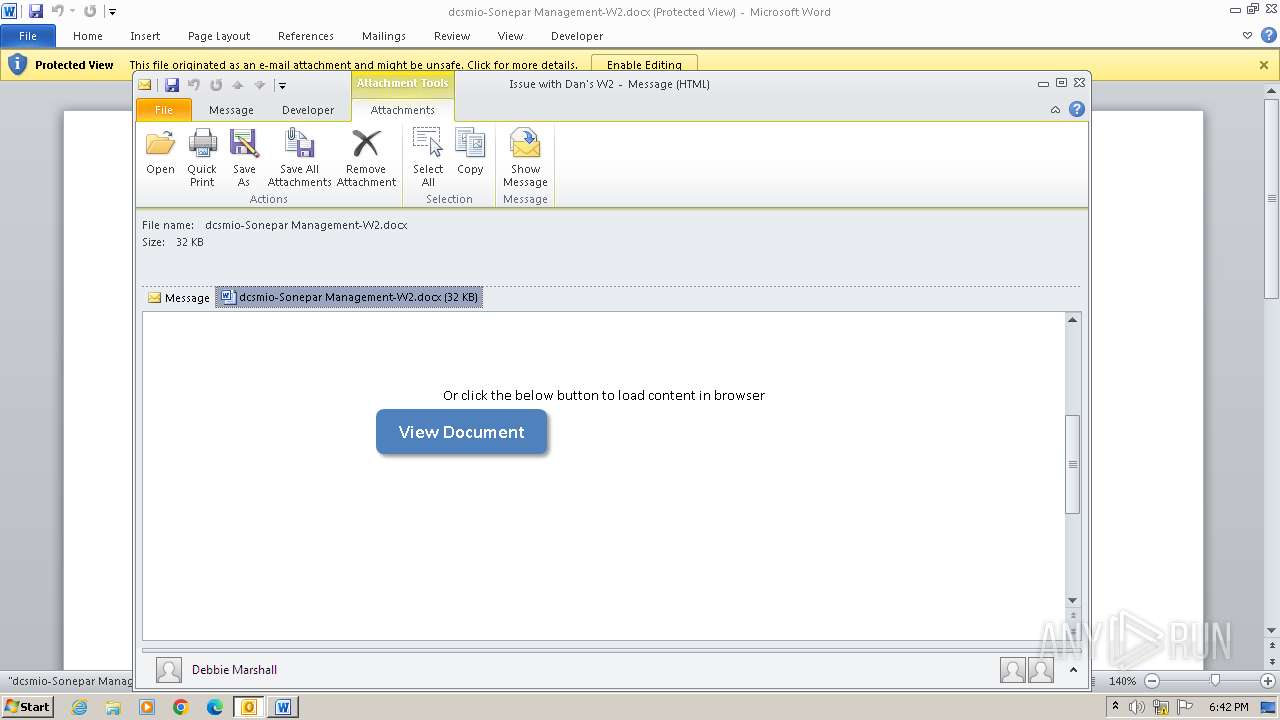
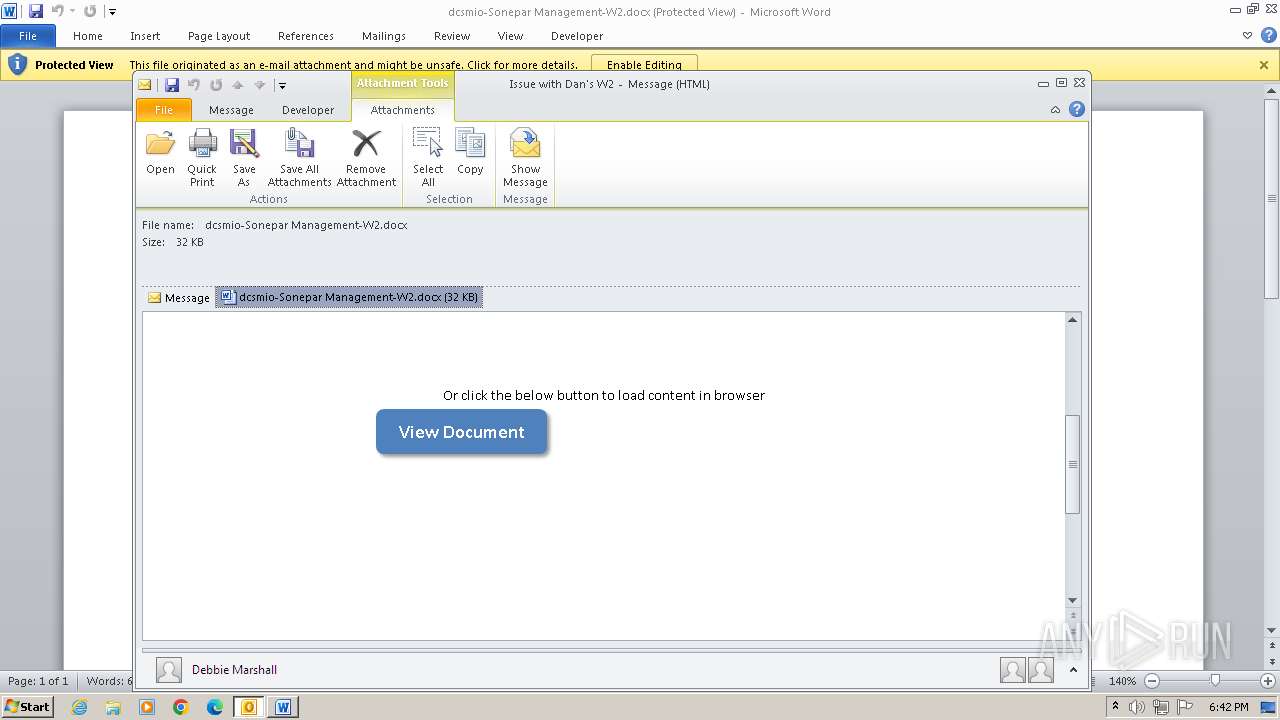
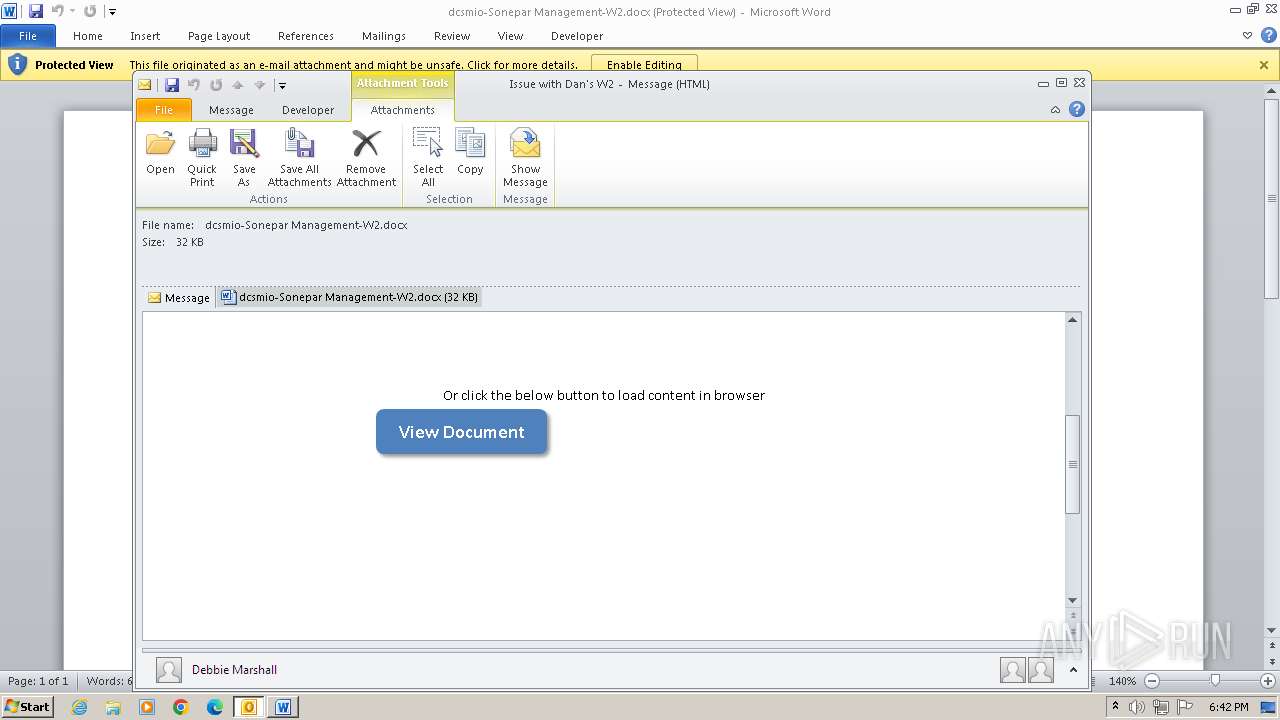
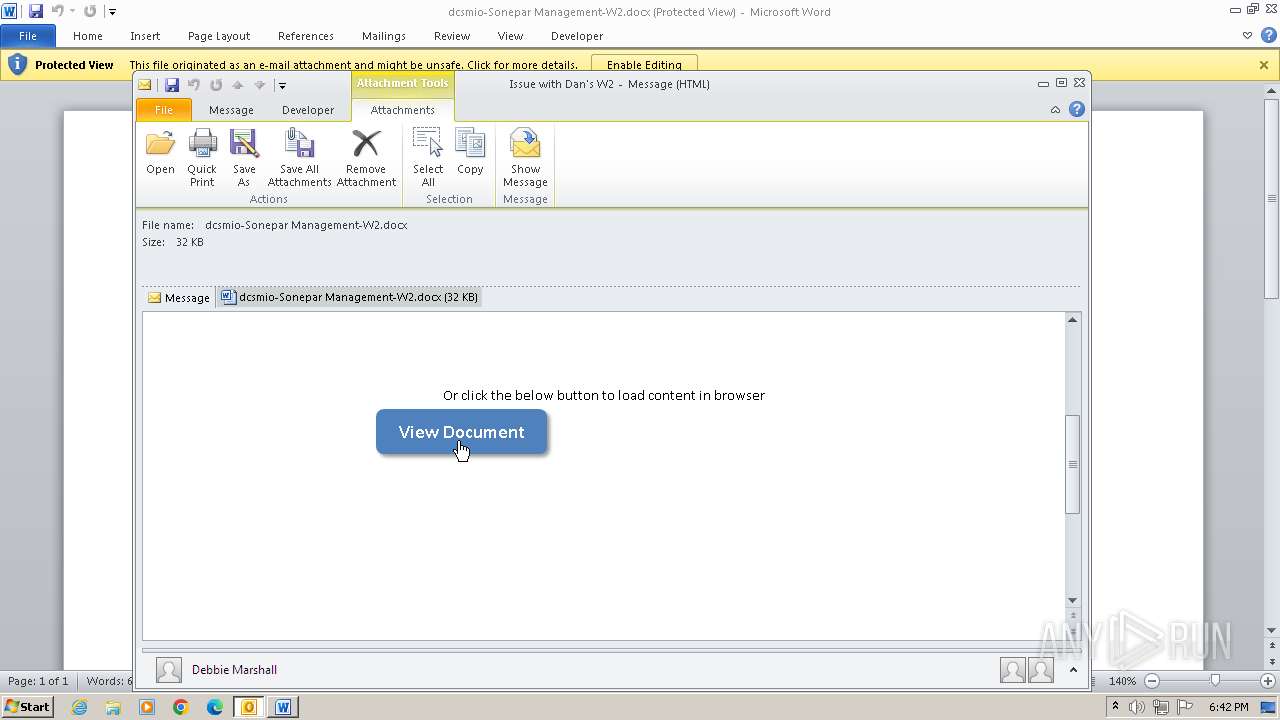
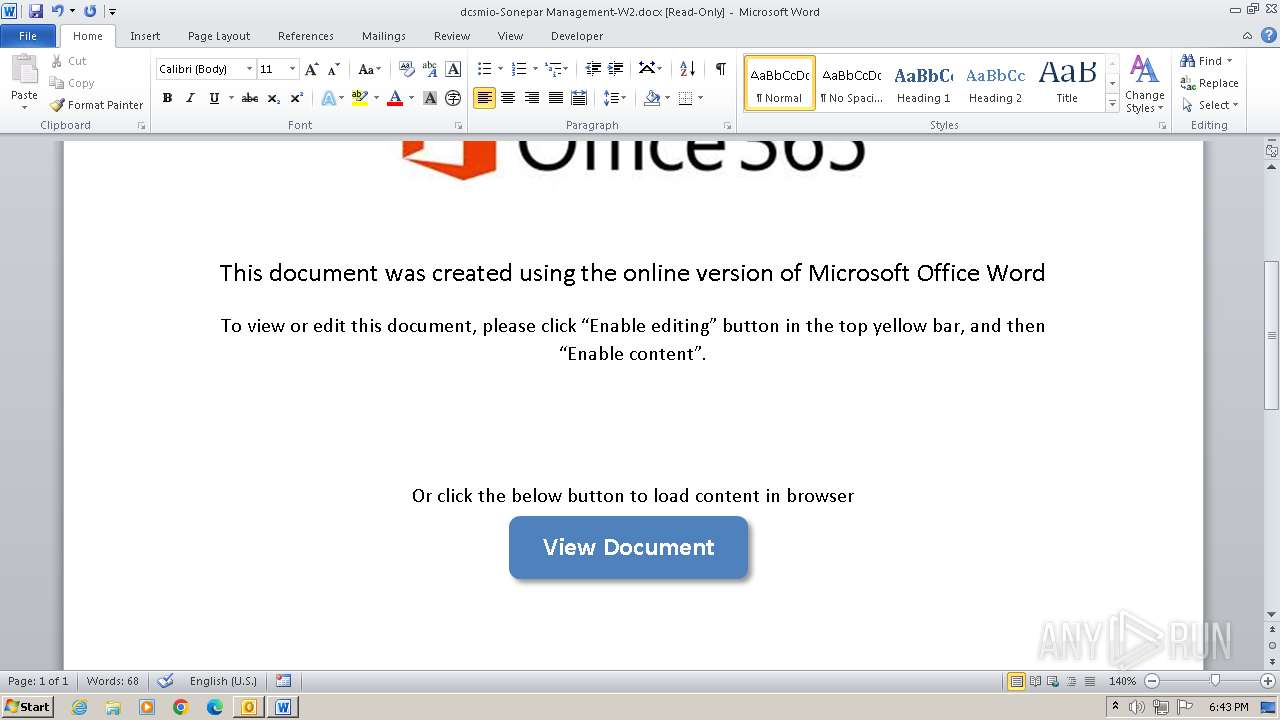
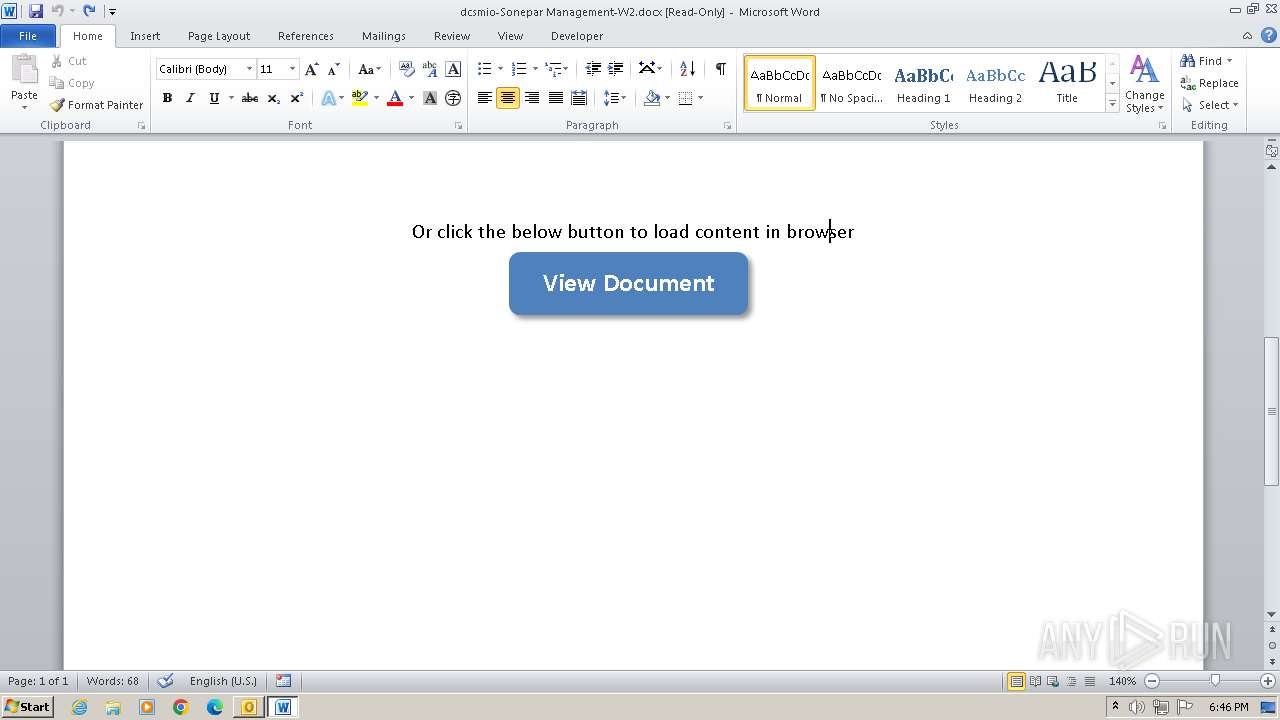
| File name: | Issue with Dan's W2.eml |
| Full analysis: | https://app.any.run/tasks/153fb5a9-d1b8-4585-9846-bc4dfb07d658 |
| Verdict: | Malicious activity |
| Analysis date: | June 17, 2024, 17:42:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, Unicode text, UTF-8 (with BOM) text, with CRLF line terminators |
| MD5: | 4B3D44AB9047BE21322EA0B6F7016682 |
| SHA1: | 6495F265C10F5D8306CF8D172CE2C46640A64AA7 |
| SHA256: | 2CED9327E8277E9EFA7BBAAE22347412EEFC2B50CA7B86E31CBD1FE65DEA7E51 |
| SSDEEP: | 1536:HquN1VPU5px+hLtomFj97aXpIfEVCtfTlXNaH:KV5atlFj9MpIMwtp+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- WINWORD.EXE (PID: 304)
INFO
The process uses the downloaded file
- WINWORD.EXE (PID: 304)
- OUTLOOK.EXE (PID: 3976)
Reads the computer name
- wmpnscfg.exe (PID: 1792)
Checks supported languages
- wmpnscfg.exe (PID: 1792)
Manual execution by a user
- wmpnscfg.exe (PID: 1792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
Total processes
41
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\3UTWYXA6\dcsmio-Sonepar Management-W2.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1368 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1792 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2012 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3976 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Issue with Dan's W2.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
28 668
Read events
27 198
Write events
1 131
Delete events
339
Modification events
| (PID) Process: | (3976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
16
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR26A4.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3976 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 304 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3C6E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
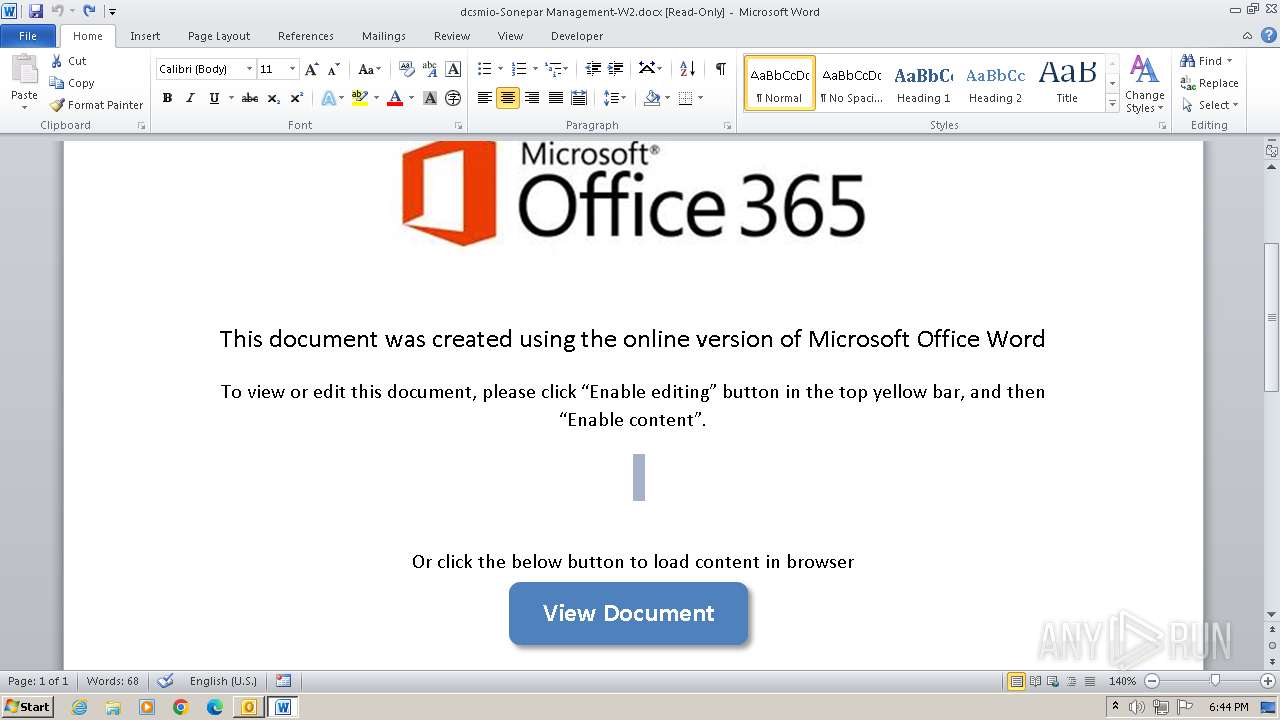
| 3976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\3UTWYXA6\dcsmio-Sonepar Management-W2.docx | document | |
MD5:D0F3855DA5237093CA93FFB5749D7851 | SHA256:C896B11EDFB512F26AA77AEC6FD0CA8A9F099EC7E38A6C5856689E16807DF7BF | |||
| 304 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_4F1581D6-15EC-4096-8803-F8E74B372F9F.0\3BEBA243.docx | document | |
MD5:D0F3855DA5237093CA93FFB5749D7851 | SHA256:C896B11EDFB512F26AA77AEC6FD0CA8A9F099EC7E38A6C5856689E16807DF7BF | |||
| 3976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\3UTWYXA6\dcsmio-Sonepar Management-W2 (2).docx | document | |
MD5:D0F3855DA5237093CA93FFB5749D7851 | SHA256:C896B11EDFB512F26AA77AEC6FD0CA8A9F099EC7E38A6C5856689E16807DF7BF | |||
| 304 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_4F1581D6-15EC-4096-8803-F8E74B372F9F.0\3BEBA243.docx:Zone.Identifier:$DATA | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{258249A0-A9F2-4998-A59A-5B67633A847E}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 304 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_4F1581D6-15EC-4096-8803-F8E74B372F9F.0\mso3F9B.tmp | compressed | |
MD5:5C6F5F5BE8FA21A6EA03A392B4CF1561 | SHA256:5FAE2AFCB97036C13C2BF5CA282AD036FC6E1C48004AA4CE3961C136EF9C2117 | |||
| 3976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\3UTWYXA6\dcsmio-Sonepar Management-W2 (2).docx:Zone.Identifier:$DATA | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
14
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
304 | WINWORD.EXE | GET | 304 | 95.101.54.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ee54885a54bfc76b | unknown | — | — | unknown |
304 | WINWORD.EXE | GET | 200 | 18.66.22.51:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | unknown |
304 | WINWORD.EXE | GET | 200 | 18.239.15.174:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | unknown |
304 | WINWORD.EXE | GET | 200 | 18.65.41.80:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | — | — | unknown |
304 | WINWORD.EXE | GET | 200 | 18.238.246.206:80 | http://ocsp.r2m02.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRmbQtwnInkvkvr7BNFR%2BS2lTYPjAQUwDFSzVpQw4J8dHHOy%2Bmc%2BXrrguICEARq8gTtce%2BTWBn0R2c%2B82E%3D | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 95.101.54.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?91e4205cfb4a00a1 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3976 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
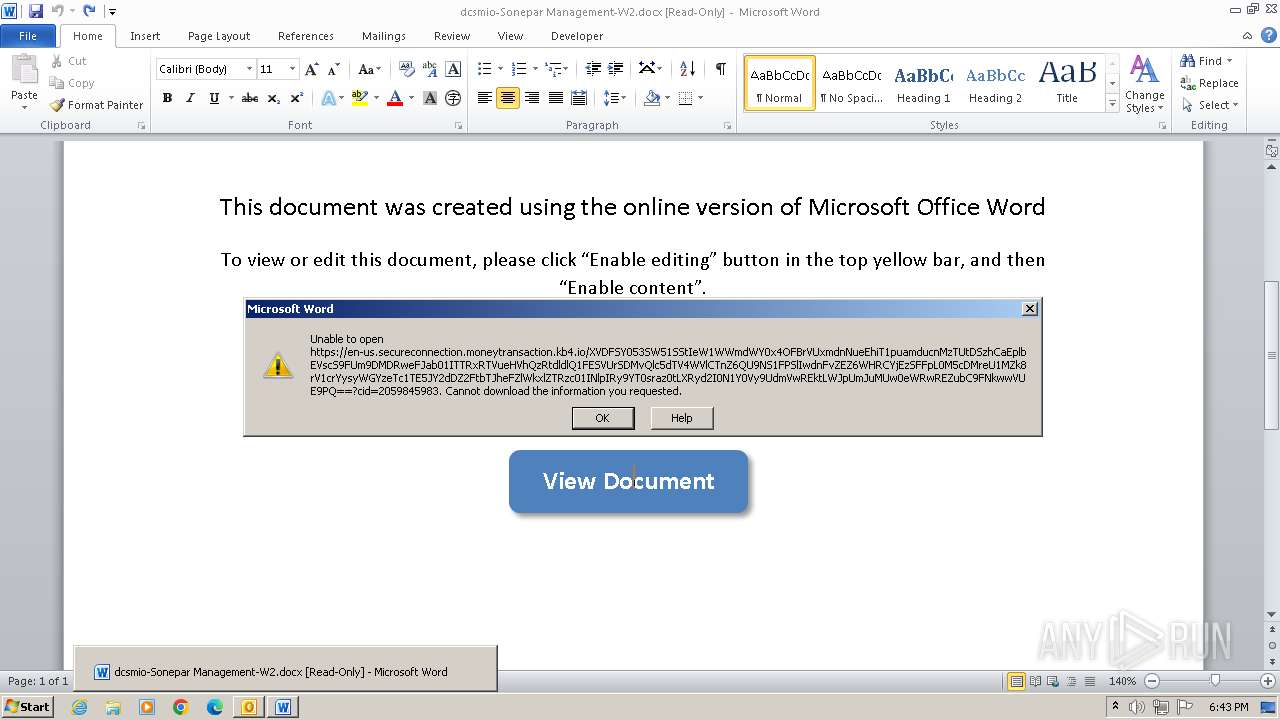
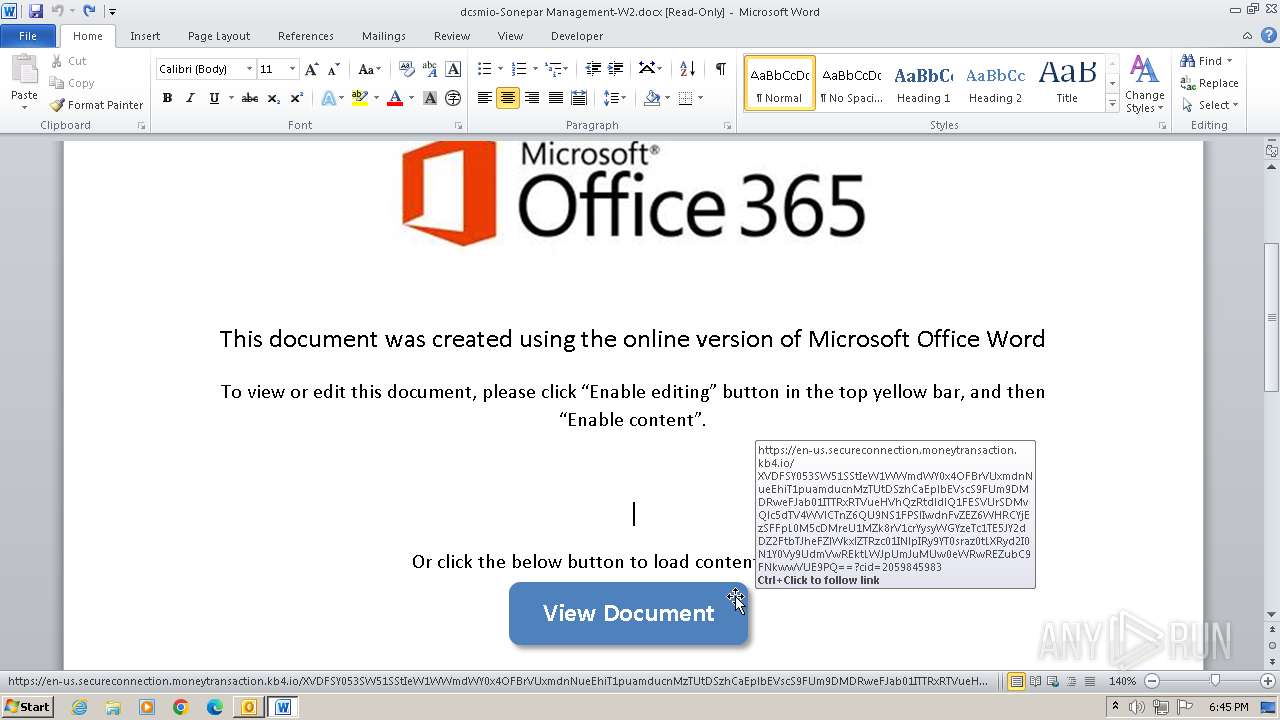
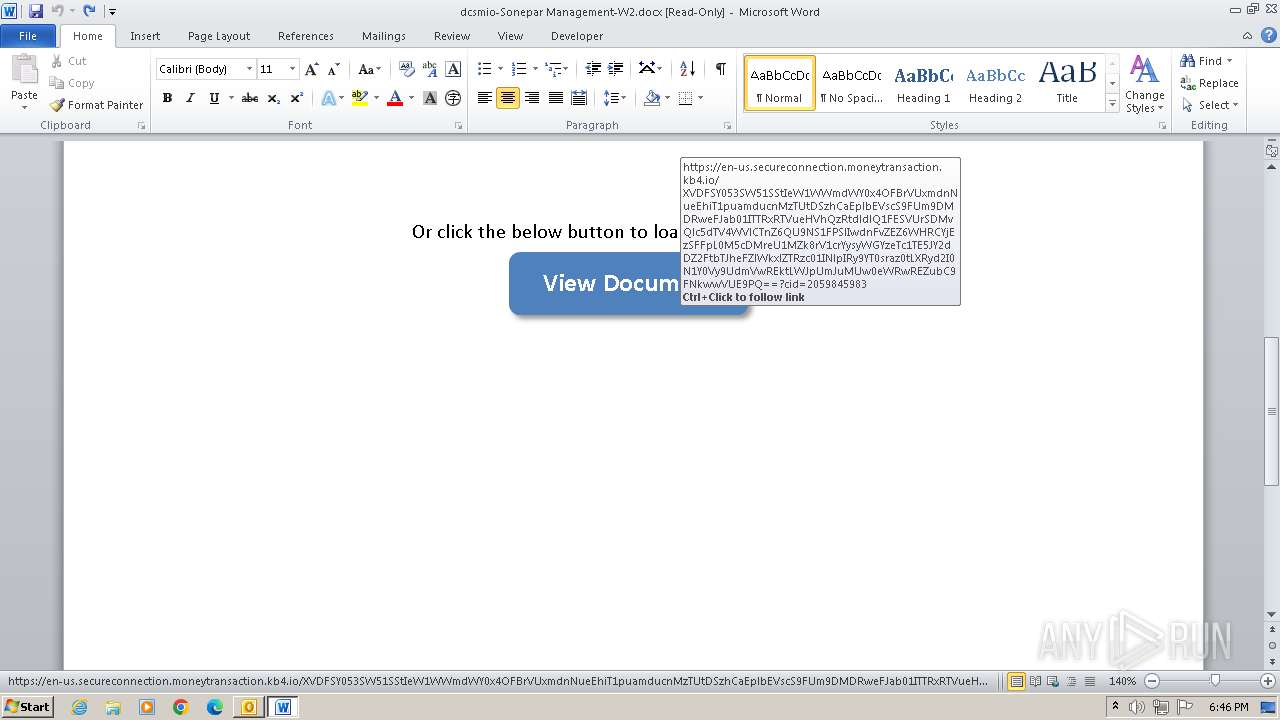
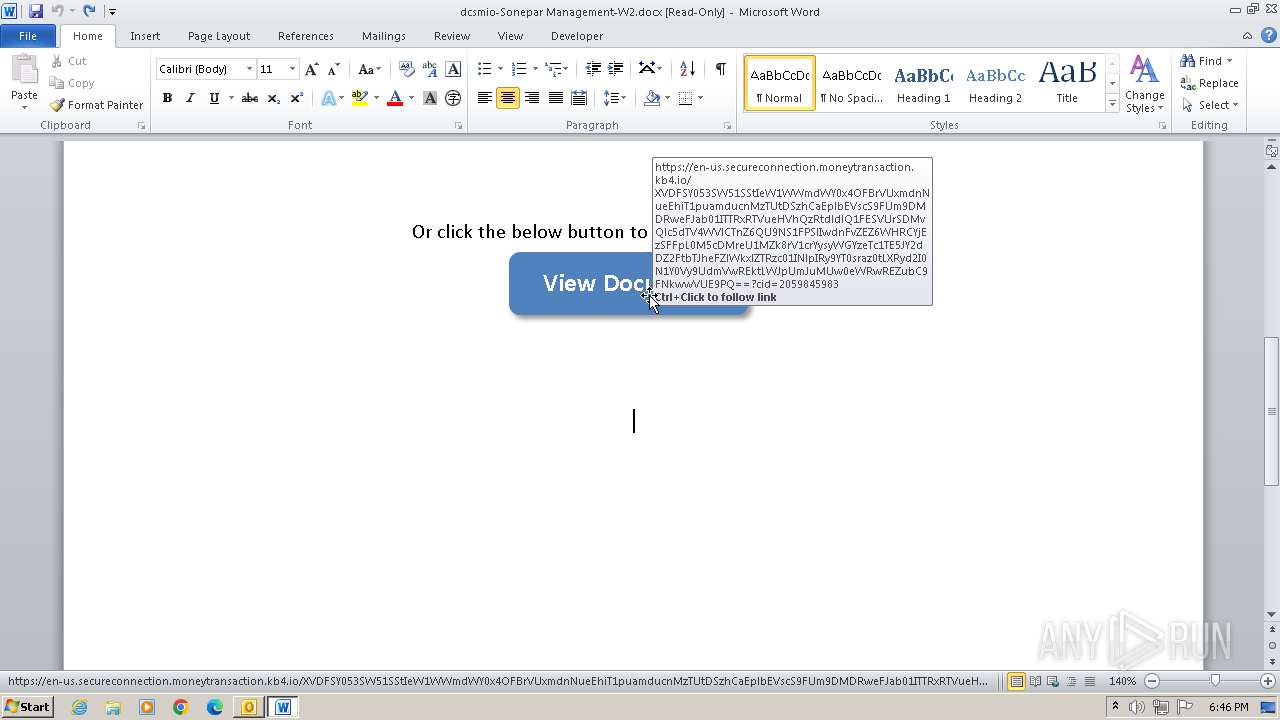
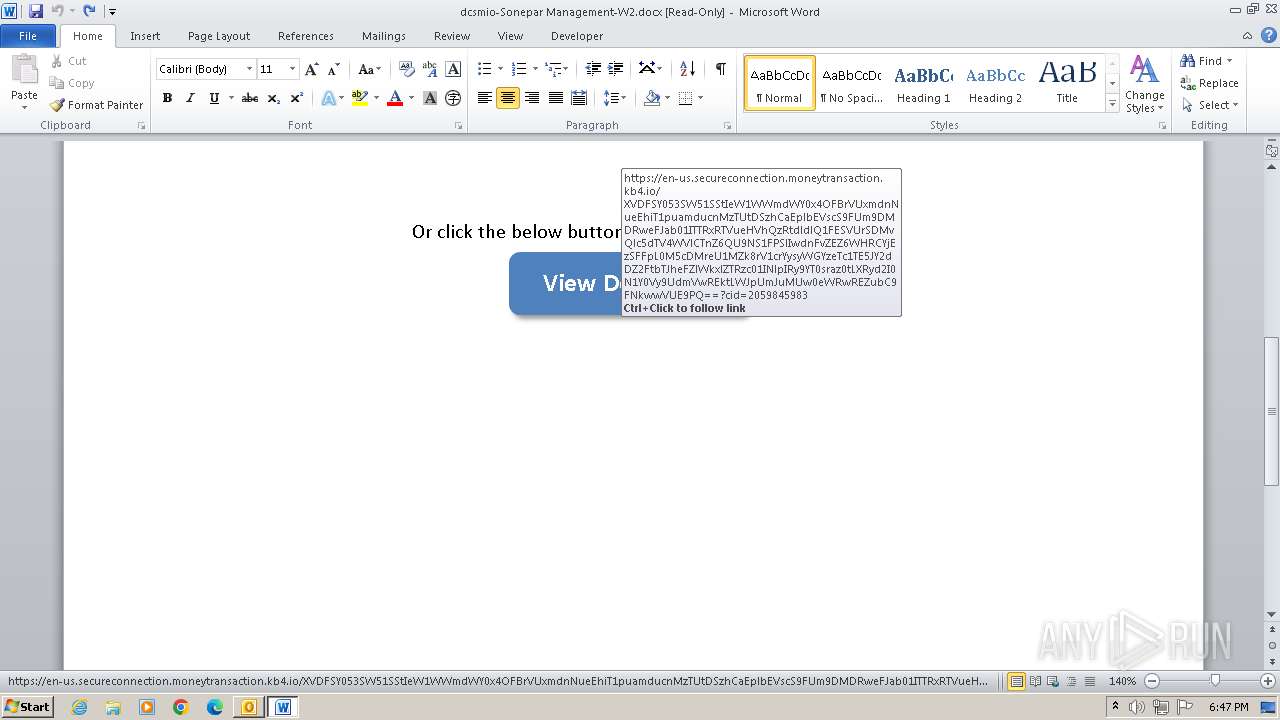
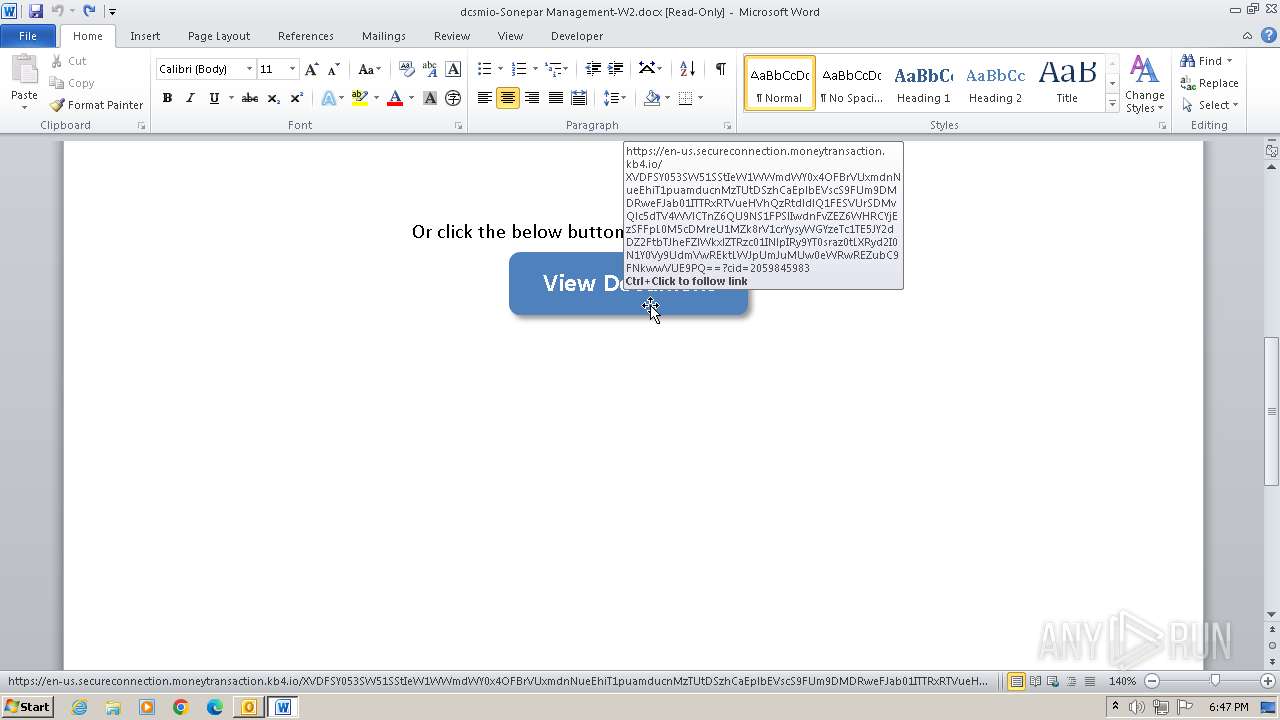
2012 | WINWORD.EXE | 34.231.66.49:443 | en-us.secureconnection.moneytransaction.kb4.io | AMAZON-AES | US | unknown |
304 | WINWORD.EXE | 34.231.66.49:443 | en-us.secureconnection.moneytransaction.kb4.io | AMAZON-AES | US | unknown |
304 | WINWORD.EXE | 95.101.54.121:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
304 | WINWORD.EXE | 18.239.15.174:80 | o.ss2.us | — | US | unknown |
304 | WINWORD.EXE | 18.66.22.51:80 | ocsp.rootg2.amazontrust.com | — | US | unknown |
304 | WINWORD.EXE | 18.65.41.80:80 | ocsp.rootca1.amazontrust.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
en-us.secureconnection.moneytransaction.kb4.io |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m02.amazontrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET POLICY Observed DNS Query to KnowBe4 Simulated Phish Domain (kb4 .io) |