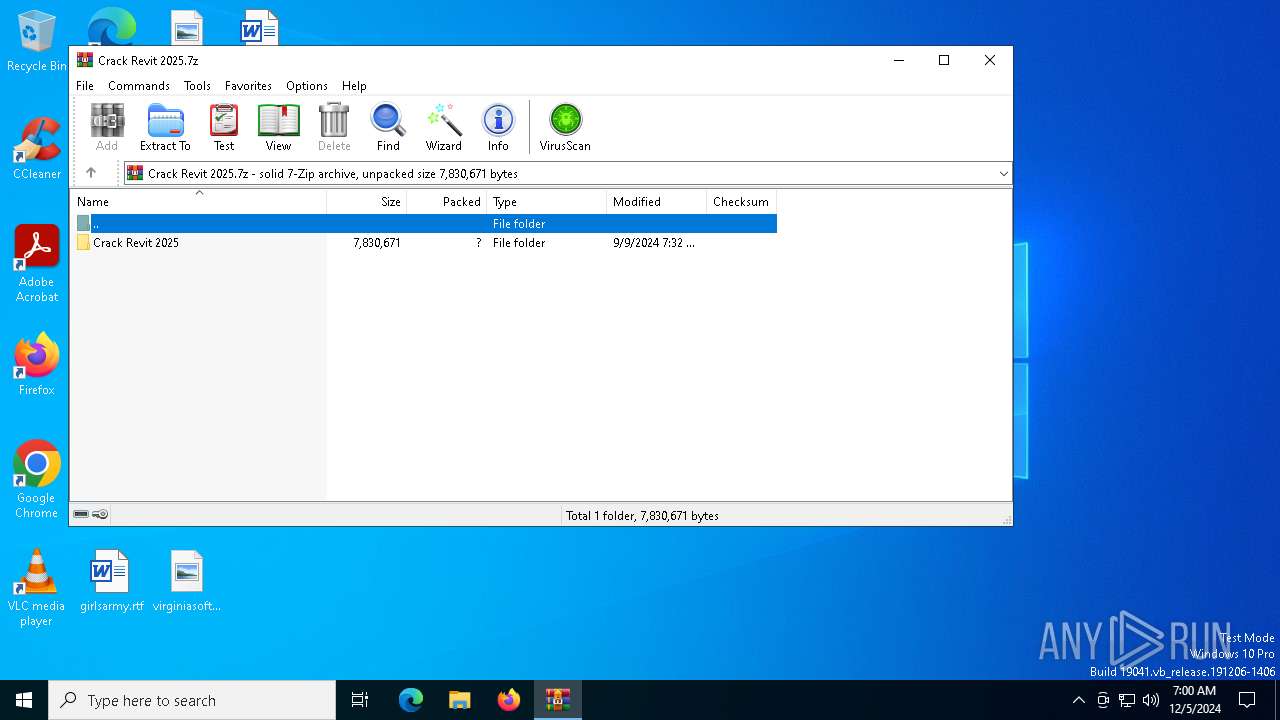
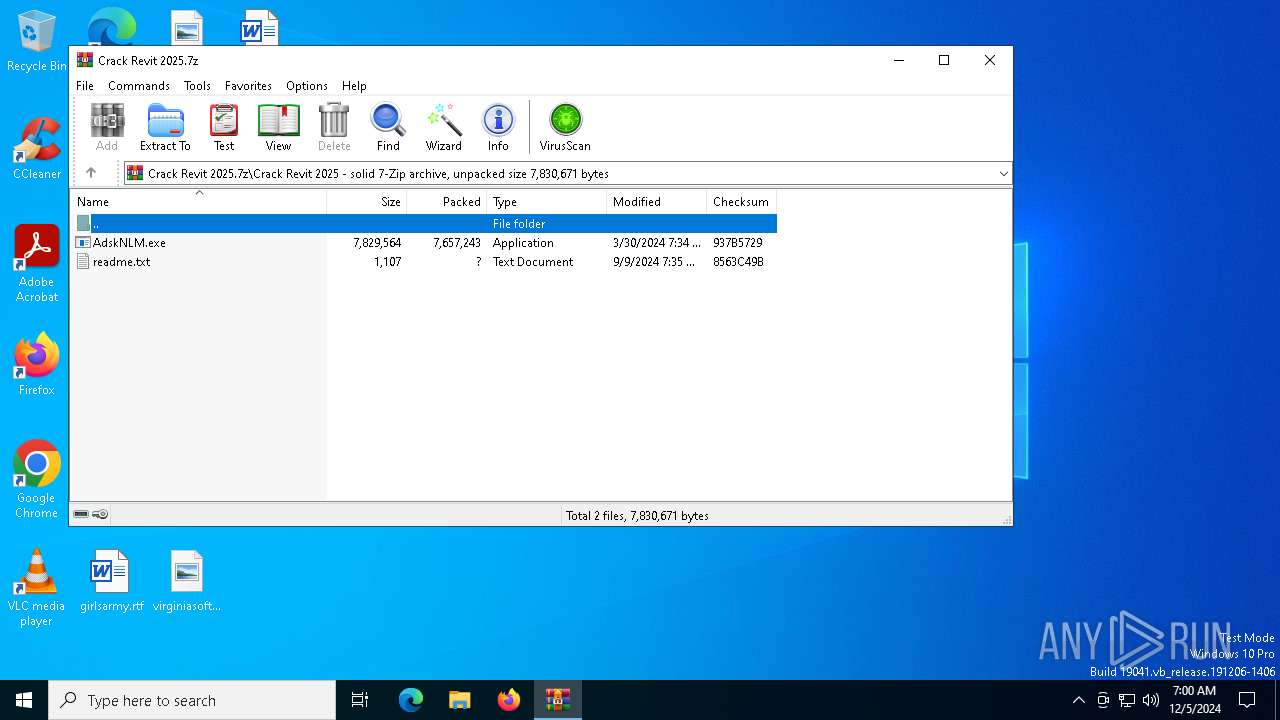
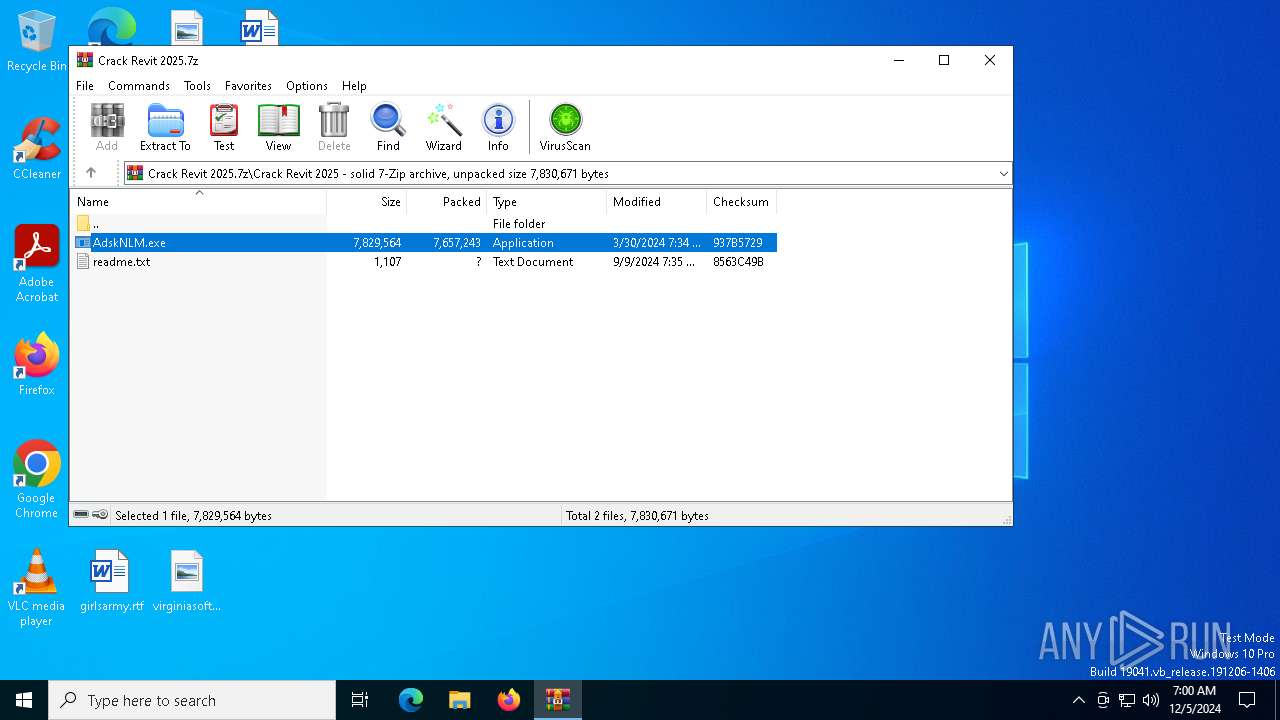
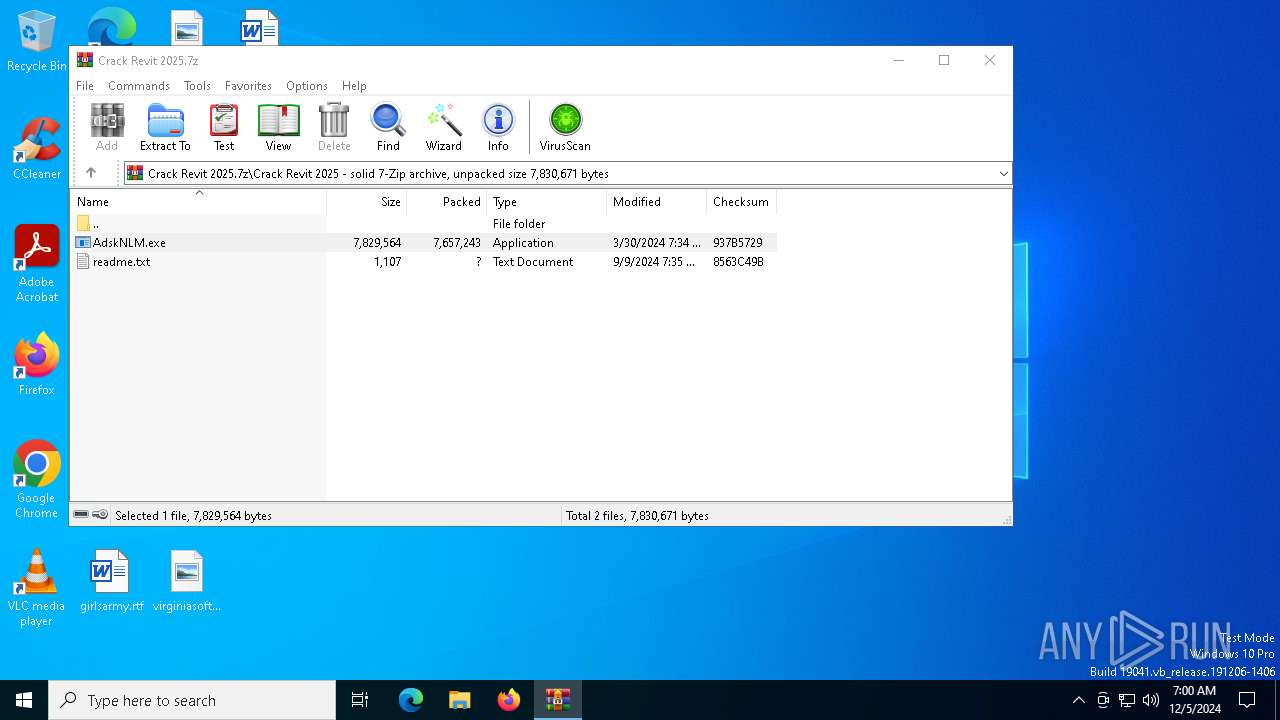
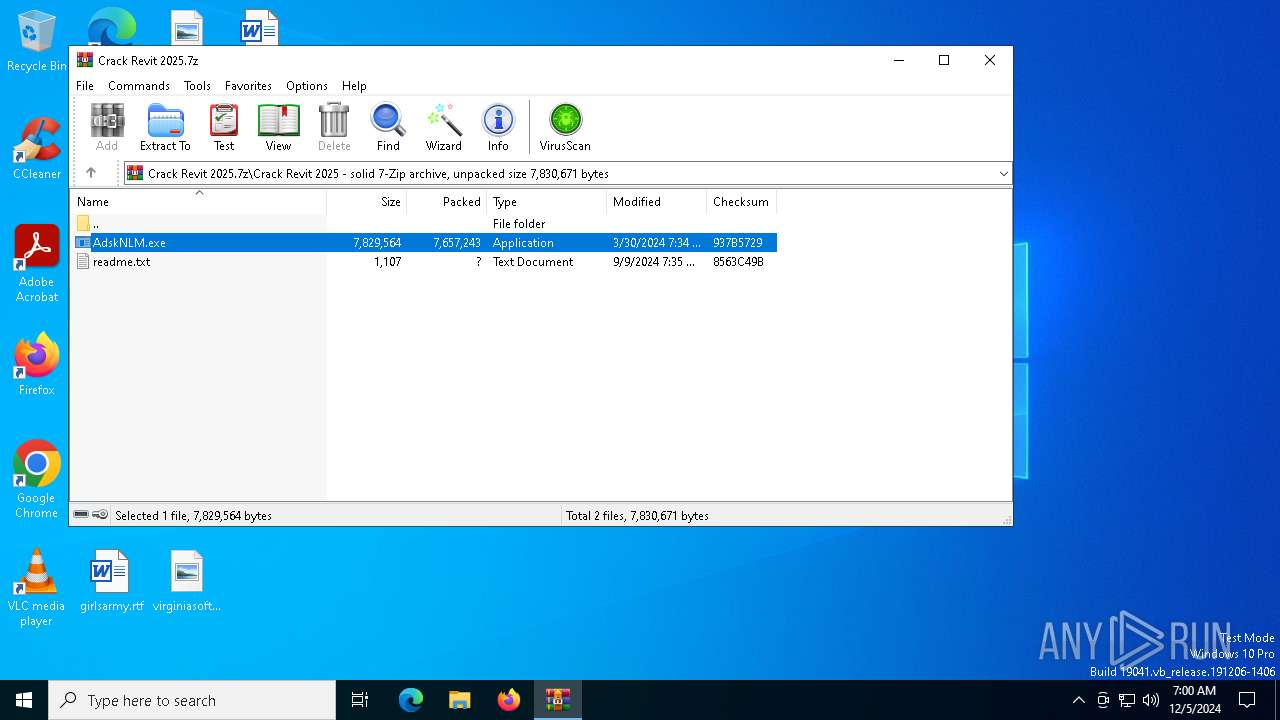
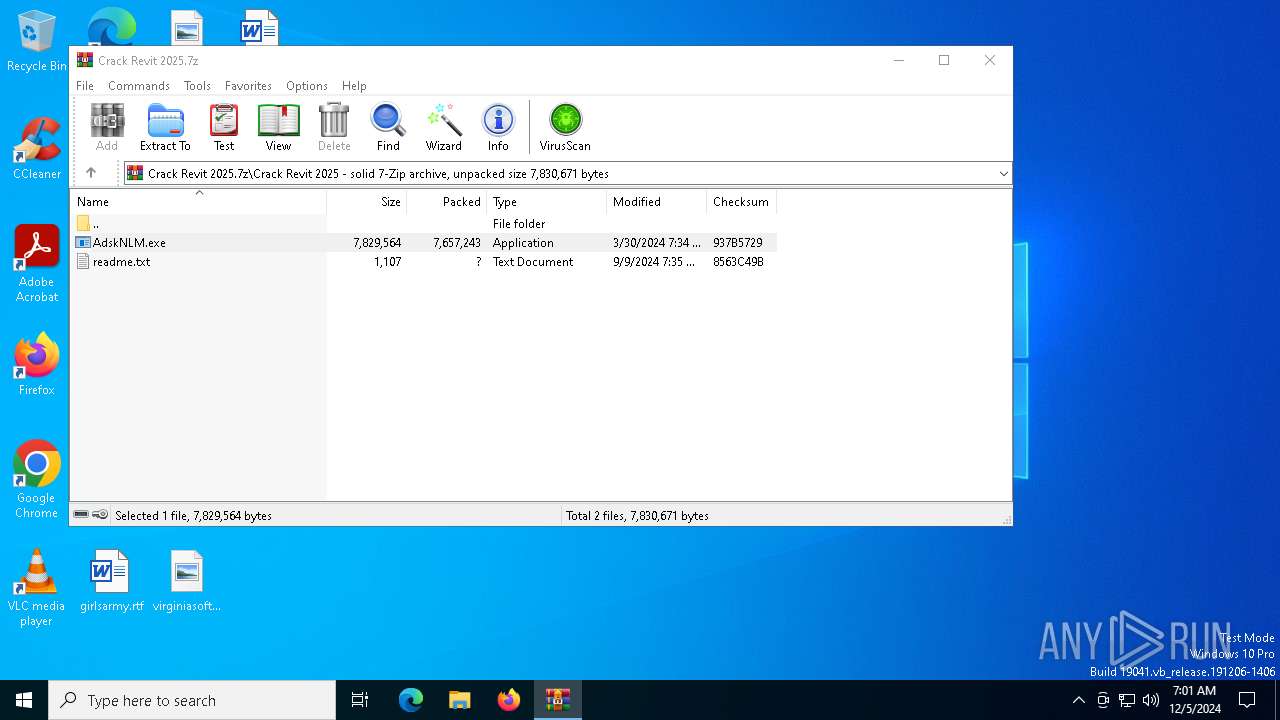
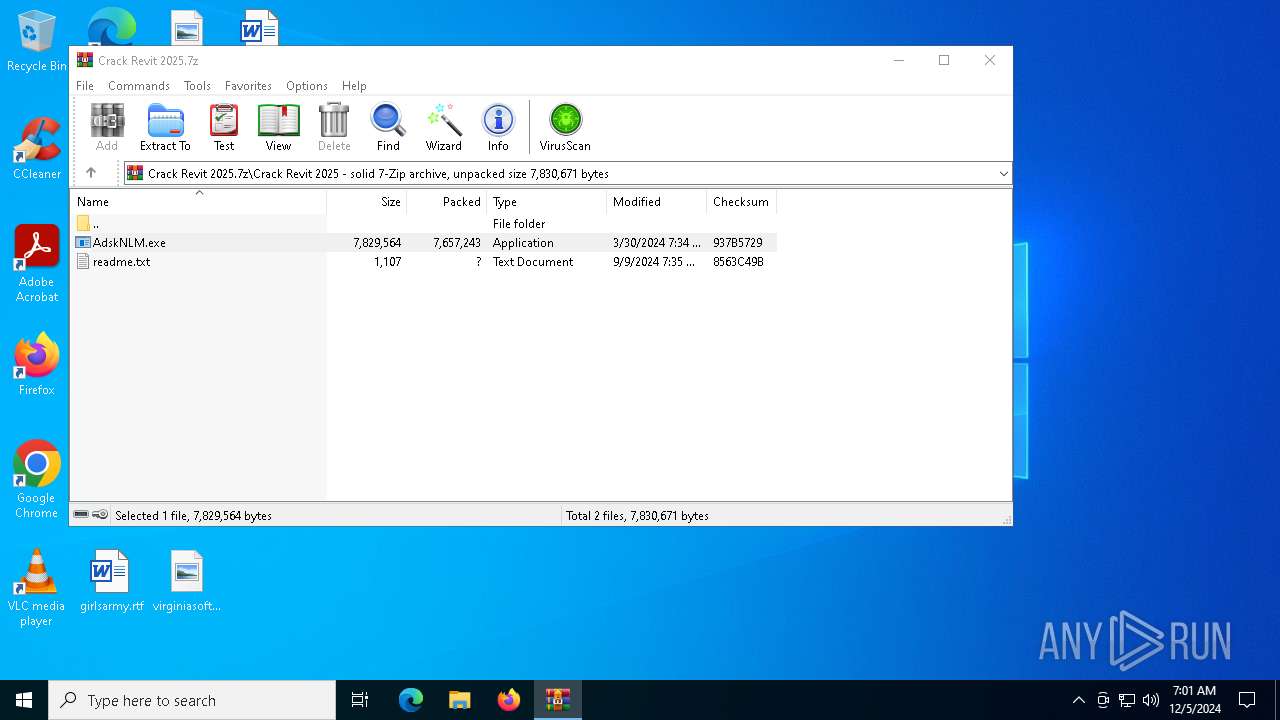
| File name: | Crack Revit 2025.7z |
| Full analysis: | https://app.any.run/tasks/50d315f9-ef9f-4780-97a9-3507e9a97d67 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2024, 07:00:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.3 |
| MD5: | FA60A21BED8629EE9226B9D36E98518C |
| SHA1: | 52DE81E249E459538004ED66108624DD812BFCCB |
| SHA256: | 2CE582ED4DE4DD4E290A7F580DF5AE2D0F26926E174C04714581A87AA22236FE |
| SSDEEP: | 98304:sMPP0yVLUZ0yCXRZRm8bXCEGdABycTBfbW6XuMaUThGLSOCzBqbP82P4ydwrs1it:KI0sBrgdrWV9r+f5EFd |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6384)
Executing a file with an untrusted certificate
- adskflex.exe (PID: 2120)
SUSPICIOUS
Starts CMD.EXE for commands execution
- AdskNLM.exe (PID: 6316)
- AdskNLM.exe (PID: 1864)
- cmd.exe (PID: 4144)
- AdskNLM.exe (PID: 5576)
- AdskNLM.exe (PID: 6840)
- AdskNLM.exe (PID: 3260)
- AdskNLM.exe (PID: 6272)
- AdskNLM.exe (PID: 7004)
- AdskNLM.exe (PID: 7124)
- AdskNLM.exe (PID: 3144)
- AdskNLM.exe (PID: 5568)
- AdskNLM.exe (PID: 4300)
- AdskNLM.exe (PID: 7020)
- AdskNLM.exe (PID: 5588)
- AdskNLM.exe (PID: 6980)
- AdskNLM.exe (PID: 3208)
- AdskNLM.exe (PID: 4976)
- AdskNLM.exe (PID: 4980)
- AdskNLM.exe (PID: 4328)
- AdskNLM.exe (PID: 5452)
- AdskNLM.exe (PID: 7132)
- cmd.exe (PID: 6060)
- AdskNLM.exe (PID: 5544)
- cmd.exe (PID: 1192)
- AdskNLM.exe (PID: 936)
- cmd.exe (PID: 5536)
- AdskNLM.exe (PID: 5320)
- AdskNLM.exe (PID: 3816)
- AdskNLM.exe (PID: 1944)
- AdskNLM.exe (PID: 4228)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6384)
Executable content was dropped or overwritten
- AdskNLM.exe (PID: 6864)
- xcopy.exe (PID: 5568)
Application launched itself
- AdskNLM.exe (PID: 6784)
- AdskNLM.exe (PID: 6864)
- cmd.exe (PID: 6060)
- cmd.exe (PID: 1192)
- cmd.exe (PID: 5536)
- lmgrd.exe (PID: 5652)
- cmd.exe (PID: 4144)
Starts SC.EXE for service management
- AdskNLM.exe (PID: 6952)
- AdskNLM.exe (PID: 6744)
- AdskNLM.exe (PID: 7020)
- AdskNLM.exe (PID: 6984)
- AdskNLM.exe (PID: 6772)
- AdskNLM.exe (PID: 904)
- AdskNLM.exe (PID: 6304)
Uses TASKKILL.EXE to kill process
- AdskNLM.exe (PID: 7072)
- AdskNLM.exe (PID: 1740)
- AdskNLM.exe (PID: 2676)
- AdskNLM.exe (PID: 488)
- AdskNLM.exe (PID: 5536)
- AdskNLM.exe (PID: 624)
Uses REG/REGEDIT.EXE to modify registry
- AdskNLM.exe (PID: 6864)
- AdskNLM.exe (PID: 7148)
- AdskNLM.exe (PID: 3808)
- AdskNLM.exe (PID: 6324)
- AdskNLM.exe (PID: 4548)
- AdskNLM.exe (PID: 3152)
- AdskNLM.exe (PID: 6580)
- AdskNLM.exe (PID: 6780)
- AdskNLM.exe (PID: 3508)
- AdskNLM.exe (PID: 1080)
- AdskNLM.exe (PID: 7088)
- AdskNLM.exe (PID: 6944)
- AdskNLM.exe (PID: 6940)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 5788)
- cmd.exe (PID: 3524)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 3744)
Process copies executable file
- cmd.exe (PID: 6060)
- cmd.exe (PID: 4144)
Executes as Windows Service
- lmgrd.exe (PID: 5652)
There is functionality for VM detection antiVM strings (YARA)
- lmgrd.exe (PID: 5652)
There is functionality for VM detection VirtualBox (YARA)
- lmgrd.exe (PID: 5652)
There is functionality for VM detection VMWare (YARA)
- lmgrd.exe (PID: 5652)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6384)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6384)
- msiexec.exe (PID: 1580)
Reads the computer name
- AdskNLM.exe (PID: 6784)
Checks supported languages
- AdskNLM.exe (PID: 6784)
Changes file name
- cmd.exe (PID: 7100)
- cmd.exe (PID: 6896)
Application launched itself
- msiexec.exe (PID: 1580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (gen) (100) |
|---|
EXIF
ZIP
| FileVersion: | 7z v0.03 |
|---|---|
| ModifyDate: | 2024:03:30 19:34:39+00:00 |
| ArchivedFileName: | Crack Revit 2025/AdskNLM.exe |
Total processes
313
Monitored processes
182
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Windows\System32\cmd.exe" /c if exist "C:\Program Files (x86)\Common Files\Autodesk Shared\AdskLicensing\12.1.0.7121\AdskLicensingAgent\AdskLicensingAgent.exe" ( echo F | xcopy /hkry "C:\Users\admin\AppData\Local\Temp\Adsk-NLM\version_old.dll" "C:\Program Files (x86)\Common Files\Autodesk Shared\AdskLicensing\12.1.0.7121\AdskLicensingAgent\version.dll" ) | C:\Windows\System32\cmd.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.35070\Crack Revit 2025\AdskNLM.exe" -sfxwaitall:0 "taskkill" /f /im AutodeskDesktopApp.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.35070\Crack Revit 2025\AdskNLM.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: MAGNiTUDE & m0nkrus Integrity Level: HIGH Description: Autodesk 2020-2024 Cracked NLM Installer Exit code: 0 Version: 9.0.0.0 Modules
| |||||||||||||||
| 556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 624 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.35070\Crack Revit 2025\AdskNLM.exe" -sfxwaitall:0 "taskkill" /f /im AdskIdentityManager.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.35070\Crack Revit 2025\AdskNLM.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: MAGNiTUDE & m0nkrus Integrity Level: HIGH Description: Autodesk 2020-2024 Cracked NLM Installer Exit code: 0 Version: 9.0.0.0 Modules
| |||||||||||||||
| 768 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 904 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.35070\Crack Revit 2025\AdskNLM.exe" -sfxwaitall:0 "sc" create AdskNLM binPath= "\"C:\Program Files (x86)\Common Files\Autodesk Shared\Network License Manager\lmgrd.exe\"" start= auto depend= WinMgmt/+NetworkProvider obj= "NT AUTHORITY\LocalService" displayname= AdskNLM | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.35070\Crack Revit 2025\AdskNLM.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: MAGNiTUDE & m0nkrus Integrity Level: HIGH Description: Autodesk 2020-2024 Cracked NLM Installer Exit code: 0 Version: 9.0.0.0 | |||||||||||||||
| 936 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.35070\Crack Revit 2025\AdskNLM.exe" -sfxwaitall:0 "cmd" /c echo D | xcopy /y "C:\Users\admin\AppData\Local\Temp\Adsk-NLM\UnNamed.json" "C:\Users\admin\AppData\Roaming\Autodesk\ADPSDK\UserConsent" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.35070\Crack Revit 2025\AdskNLM.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: MAGNiTUDE & m0nkrus Integrity Level: HIGH Description: Autodesk 2020-2024 Cracked NLM Installer Exit code: 0 Version: 9.0.0.0 | |||||||||||||||
| 1080 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.35070\Crack Revit 2025\AdskNLM.exe" -sfxwaitall:0 "reg" add "HKCU\SOFTWARE\FLEXlm License Manager" /v "ADSKFLEX_LICENSE_FILE" /d "27080@localhost" /f | C:\Users\admin\AppData\Local\Temp\Rar$EXa6384.35070\Crack Revit 2025\AdskNLM.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: MAGNiTUDE & m0nkrus Integrity Level: HIGH Description: Autodesk 2020-2024 Cracked NLM Installer Exit code: 0 Version: 9.0.0.0 | |||||||||||||||
| 1144 | "C:\Windows\System32\reg.exe" add "HKLM\SOFTWARE\FLEXlm License Manager\AdskNLM" /v "Service" /d "AdskNLM" /f | C:\Windows\System32\reg.exe | — | AdskNLM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
27 043
Read events
26 932
Write events
100
Delete events
11
Modification events
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Crack Revit 2025.7z | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6560) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Autodesk Access |
Value: | |||
| (PID) Process: | (1580) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 2C060000B523266EE346DB01 | |||
Executable files
16
Suspicious files
25
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6864 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\nlm11-19-4-1-ipv4-ipv6-win64.msi | — | |
MD5:— | SHA256:— | |||
| 1580 | msiexec.exe | C:\Windows\Installer\142180.msi | — | |
MD5:— | SHA256:— | |||
| 6864 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\nlm.mst | binary | |
MD5:29810BAB1EF69A3D26872093EF09372B | SHA256:90E413CD675EE085C441DF6327F6661A3459F4E109E0684B1A361C050D672BDB | |||
| 6864 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\version_old.dll | executable | |
MD5:51F0E19B4CF164ECBA9A006C4CF3B2A5 | SHA256:6F13E52D797A732435C8BB456BE08C64D0B6FADEA29F85486F4B44559D6CC95F | |||
| 6864 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\delnowmic.ps1 | text | |
MD5:67924FF023F149E8B467A8905FF1B4FC | SHA256:4B5EF379990A4663A3341913B0BD4FEDF906B9F6AF8D8FA0CB8BEE4A09FF92F9 | |||
| 1580 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_713A6544EFB2EFA6D8AB75FCC7811104 | binary | |
MD5:815BC6AFF10DABFC68A02AA23A718607 | SHA256:8B0FDDB4733960858B9D8B2FE7367796DBE4BB60C7418EC1965A5F25294E1741 | |||
| 1580 | msiexec.exe | C:\Windows\Installer\MSI22E8.tmp | executable | |
MD5:1DBD78917F6DA40FCDF7078EF82E19B0 | SHA256:B6861D25BDE12B74229DB3A4796CB9A529512042CDE0BC5AD0121B0576D672E4 | |||
| 6864 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\adskflex.exe | executable | |
MD5:E974687B0135A662623056078A8E58E1 | SHA256:82BE4EC8BA546EBF1E3448976D06E163E9C4E258301CFCEB9CE8A2D76ECBD6AE | |||
| 1580 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_713A6544EFB2EFA6D8AB75FCC7811104 | der | |
MD5:39DEC35FE58FDF784B574C8029052B8D | SHA256:96B307C5AD7373D6681BC7C8A76D503E018C49CDBDBB7BDBF50F8D98C69825A0 | |||
| 6864 | AdskNLM.exe | C:\Users\admin\AppData\Local\Temp\Adsk-NLM\netapi32.dll | executable | |
MD5:5C51CC926C76B23830D27A97445BF734 | SHA256:655181D13D9707500BF77FF88B0B6C2595459B475ADE7B919A2B1E00402C1CEB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
43
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5740 | WmiPrvSE.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5740 | WmiPrvSE.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
5740 | WmiPrvSE.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5740 | WmiPrvSE.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl | unknown | — | — | whitelisted |
5740 | WmiPrvSE.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAQJGBtf1btmdVNDtW%2BVUAg%3D | unknown | — | — | whitelisted |
5740 | WmiPrvSE.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
5740 | WmiPrvSE.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnR4FoxLLkI7vkvsUIFlZt%2BlGH3gQUWsS5eyoKo6XqcQPAYPkt9mV1DlgCEAkQWITrlZ07yLmU%2BRintu4%3D | unknown | — | — | whitelisted |
5740 | WmiPrvSE.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5892 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.186:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |