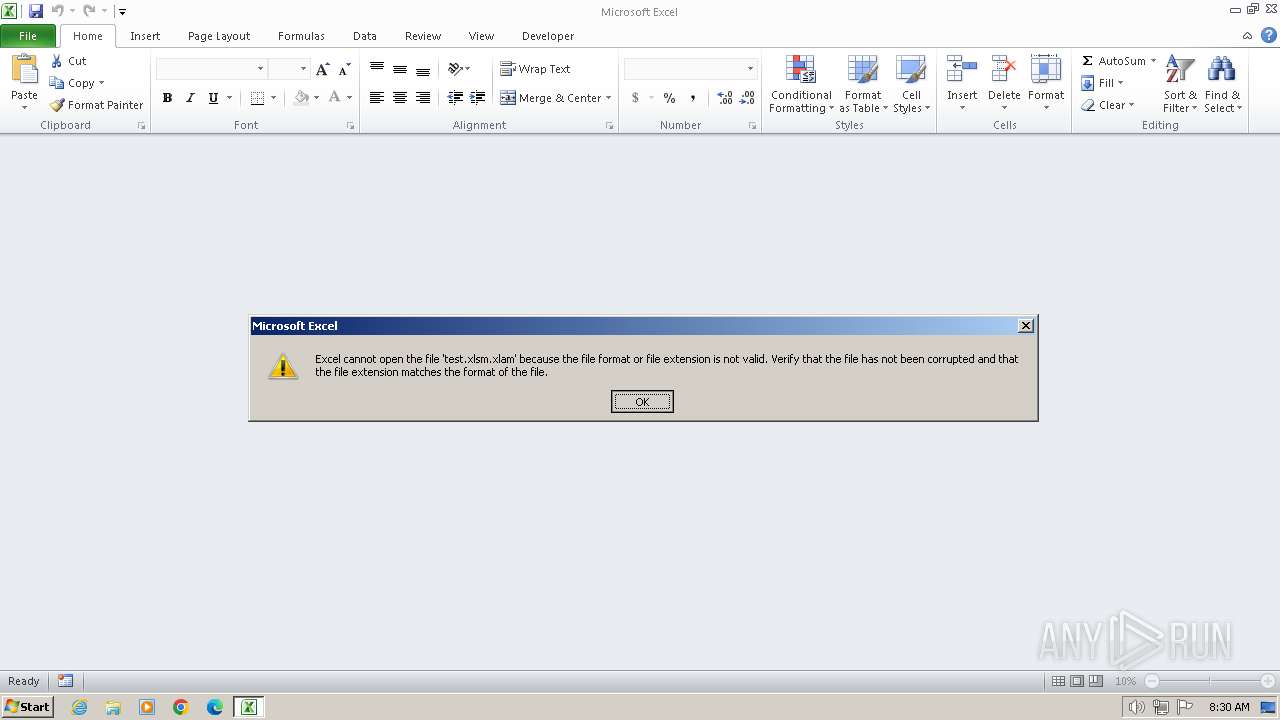
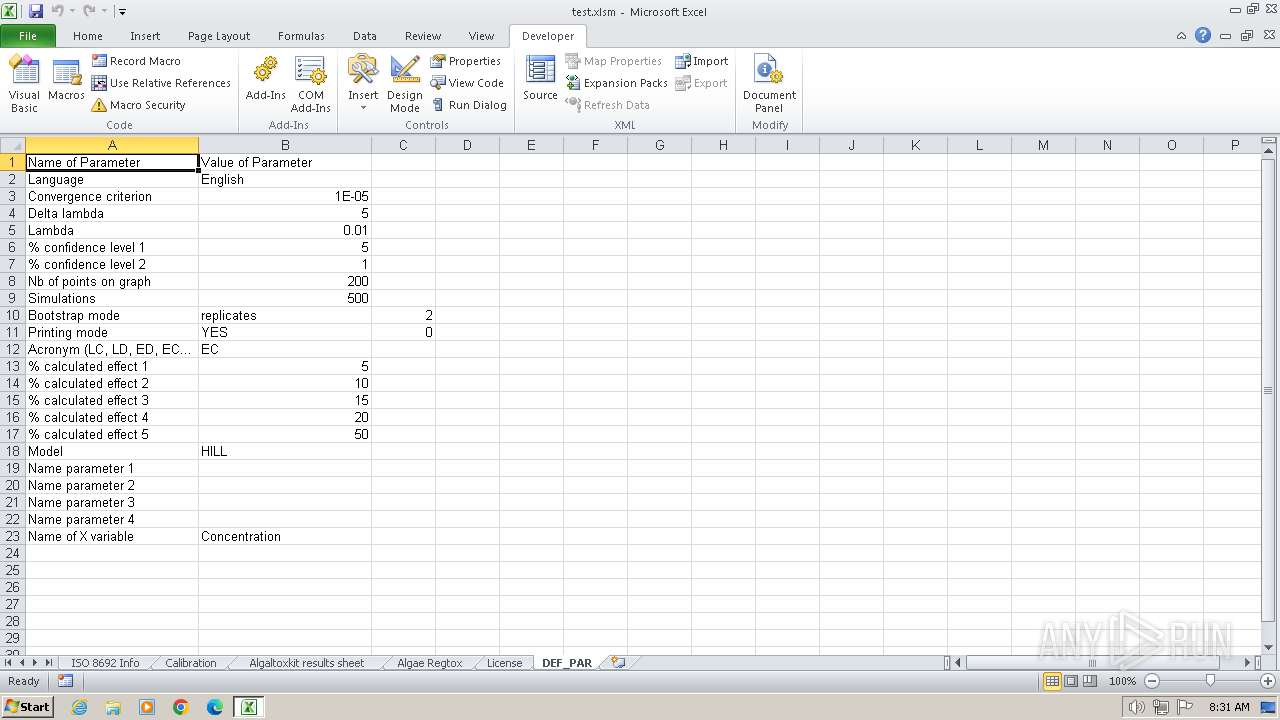
| File name: | test.xlsm |
| Full analysis: | https://app.any.run/tasks/63b1f33b-4986-4510-875c-5d221532c049 |
| Verdict: | Malicious activity |
| Analysis date: | January 09, 2024, 08:30:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 379C50433AF2AFFA68E6756AAD1D3AEA |
| SHA1: | C6BF8B58D6A9E7550AD44860D8C5B0698362F04A |
| SHA256: | 2CE4722ABB1A34A93957A404FE5110CB648AC42D70F55E8824E15CC6C92A58BE |
| SSDEEP: | 6144:BJxnIMPSx8otprlhXpBOLdPD6H9vxX0sEegthZzl102I/IaiIQD6eshvzoNAx:BLIfrfpuPGH9JXzqhdl1wIgI6vhLoNo |
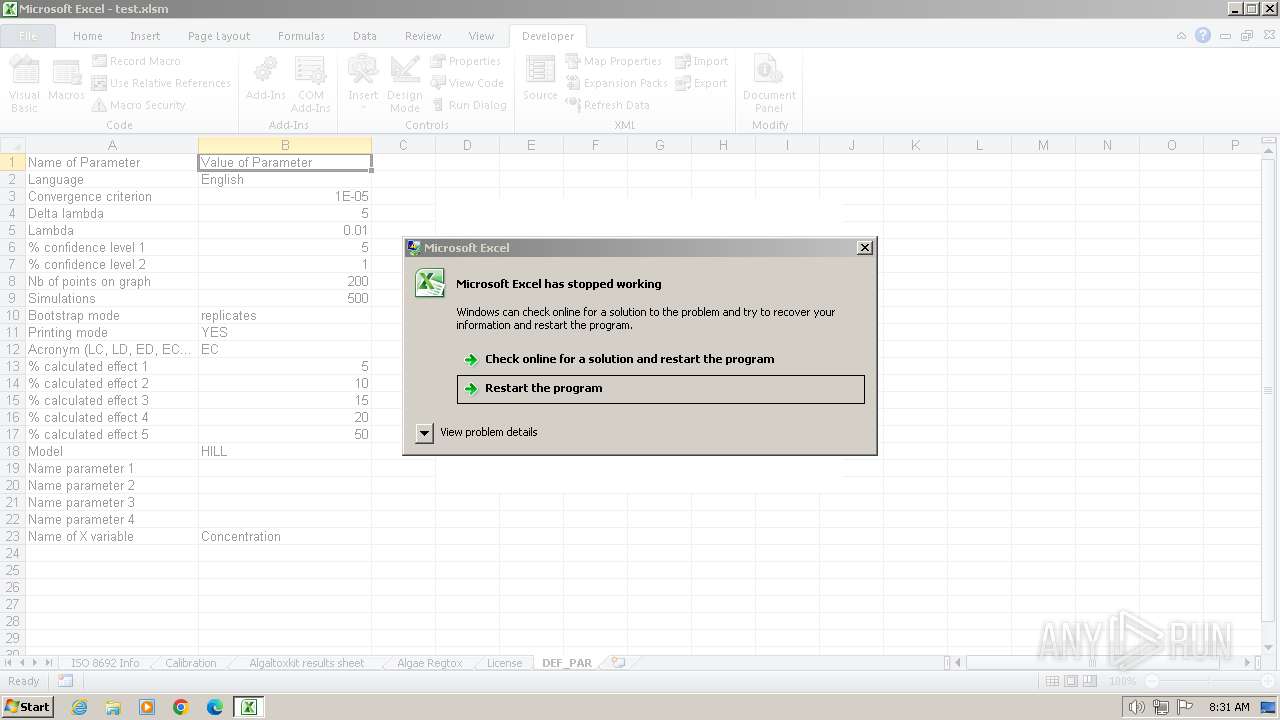
MALICIOUS
Unusual execution from MS Office
- EXCEL.EXE (PID: 2036)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- DW20.EXE (PID: 696)
Reads mouse settings
- EXCEL.EXE (PID: 2036)
Manual execution by a user
- EXCEL.EXE (PID: 2312)
Creates files or folders in the user directory
- DWWIN.EXE (PID: 2128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlam | | | Excel Macro-enabled Open XML add-in (42.4) |
|---|---|---|
| .xlsm | | | Excel Microsoft Office Open XML Format document (with Macro) (29.2) |
| .xlsx | | | Excel Microsoft Office Open XML Format document (17.3) |
| .zip | | | Open Packaging Conventions container (8.9) |
| .zip | | | ZIP compressed archive (2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x819fd8b5 |
| ZipCompressedSize: | 512 |
| ZipUncompressedSize: | 2872 |
| ZipFileName: | [Content_Types].xml |
XML
| Application: | Microsoft Excel |
|---|---|
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: |
|
| Company: | INERIS |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 15.03 |
| LastModifiedBy: | Tecnico |
| CreateDate: | 2000:07:18 20:02:42Z |
| ModifyDate: | 2018:06:20 10:32:51Z |
XMP
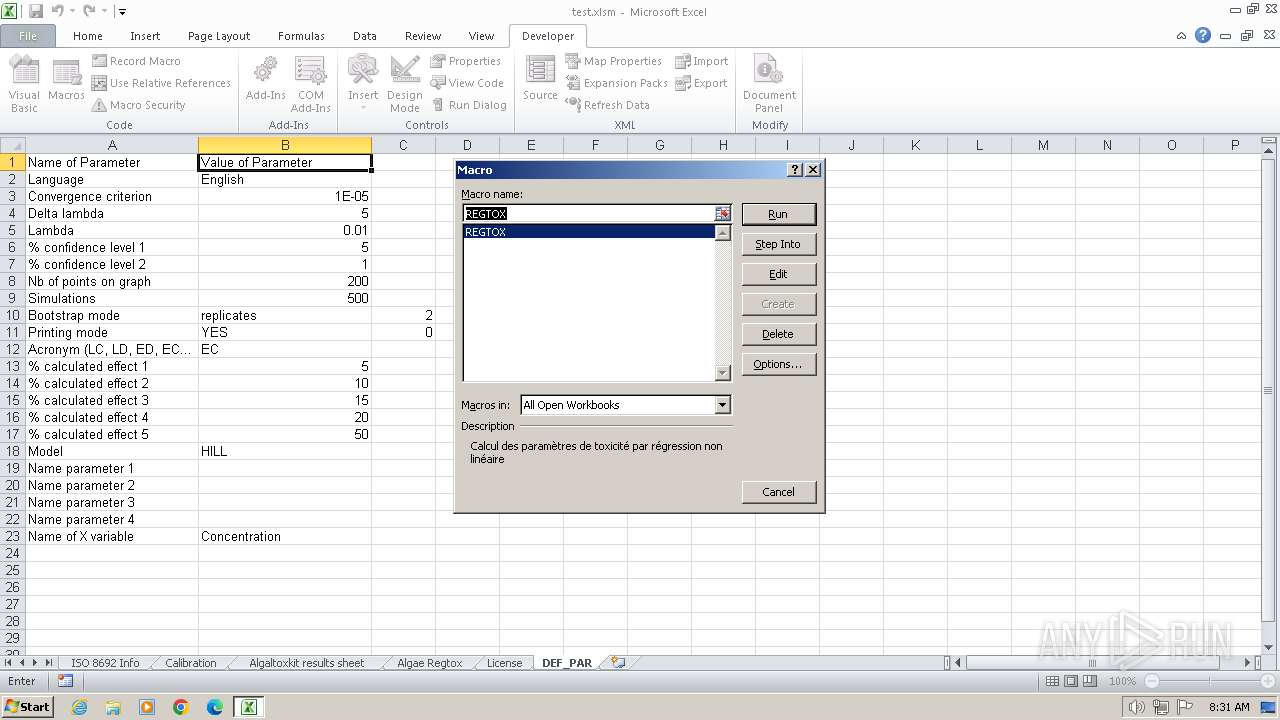
| Title: | REGTOX |
|---|---|
| Subject: | Calculation of toxicity parameters |
| Creator: | Eric Vindimian |
Total processes
41
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | "C:\PROGRA~1\COMMON~1\MICROS~1\DW\DW20.EXE" -x -s 1408 | C:\Program Files\Common Files\microsoft shared\DW\DW20.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Application Error Reporting Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
| 2036 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2128 | C:\Windows\system32\dwwin.exe -x -s 1408 | C:\Windows\System32\DWWIN.EXE | — | DW20.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Watson Client Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
4 550
Read events
4 441
Write events
71
Delete events
38
Modification events
| (PID) Process: | (2036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
1
Suspicious files
20
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRF9F1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2128 | DWWIN.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_EXCEL.EXE_1221f59ab485ffbc329453c839a59232576bd3ad_085f0546\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2312 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR1813.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2036 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\test.xlsm.LNK | binary | |
MD5:797974F895DF6C471E0B74D73FD9F76E | SHA256:70F226E2B4E1D106DA10F0FC55F383088A000254C3D8155731DABA3A25DEB26E | |||
| 2036 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Forms\RefEdit.exd | binary | |
MD5:93FE9E83AFECC4E1E453B0F8F37B6FA6 | SHA256:AFFD4CD3A92DEBADD50EA1D206508D500FB17C3BD547DA8B7BBE313E1BB4DB9E | |||
| 2036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:B139C09E8D1133678E2D9685C6B83A1C | SHA256:045B473253204E65723AC1CCC5FF2BA6F86BAC470A2B8C1CA7CB2AAC93B4E6EC | |||
| 2036 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:5173705812CDE6C2337AF0F96397F43E | SHA256:F43AD82FEC80A3294D7F807EE2D0F74ED6CF93F085A54210CBDDDB2E10F70C0F | |||
| 2036 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Forms\EXCEL.box | binary | |
MD5:2D33F008646685792B38C09516CB15B7 | SHA256:5CC4A8AF254D5E44F92EECC344F092887D901753B6BBB6C2DFC3F0CBD8AA9933 | |||
| 2036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\43AE65B6.png | image | |
MD5:398AF811EDC72EF057EA0089ACF8D7D0 | SHA256:9364BCE85D6DC9D6F848D661A3B8918B9398BF63E43ABAE024CEEEBEE0401AEA | |||
| 2036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFD174062F63D6A57B.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |