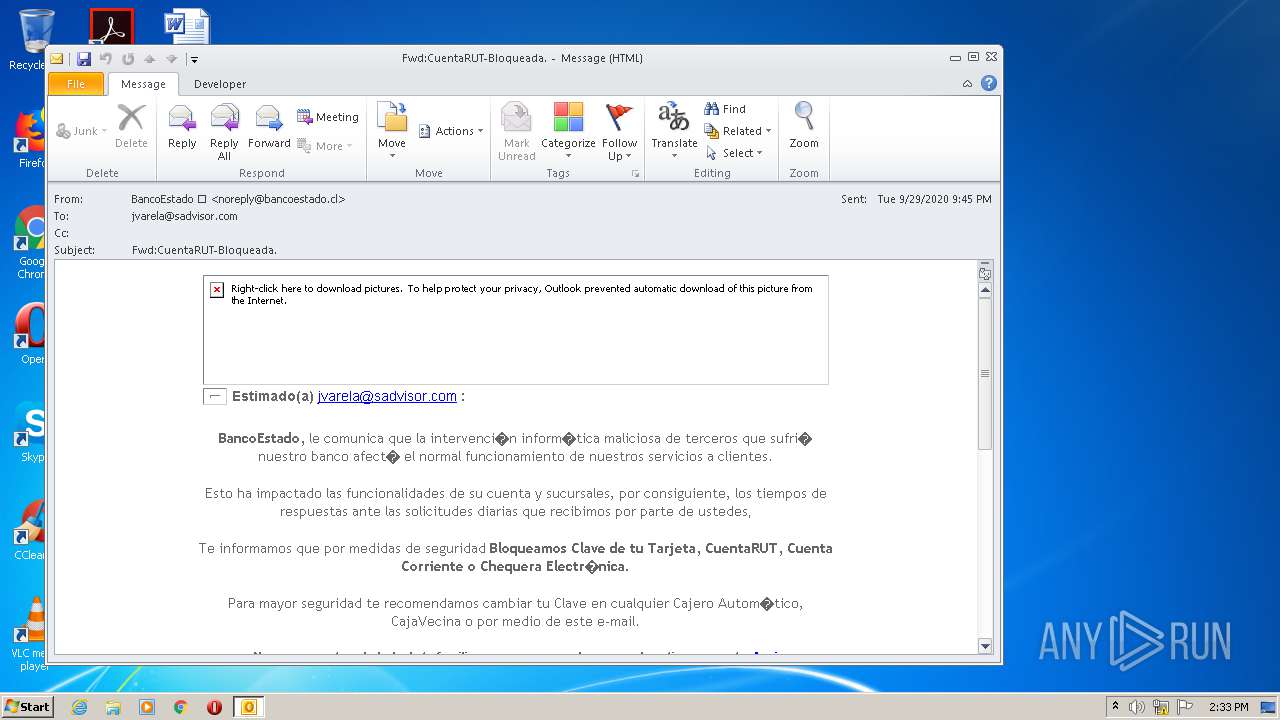
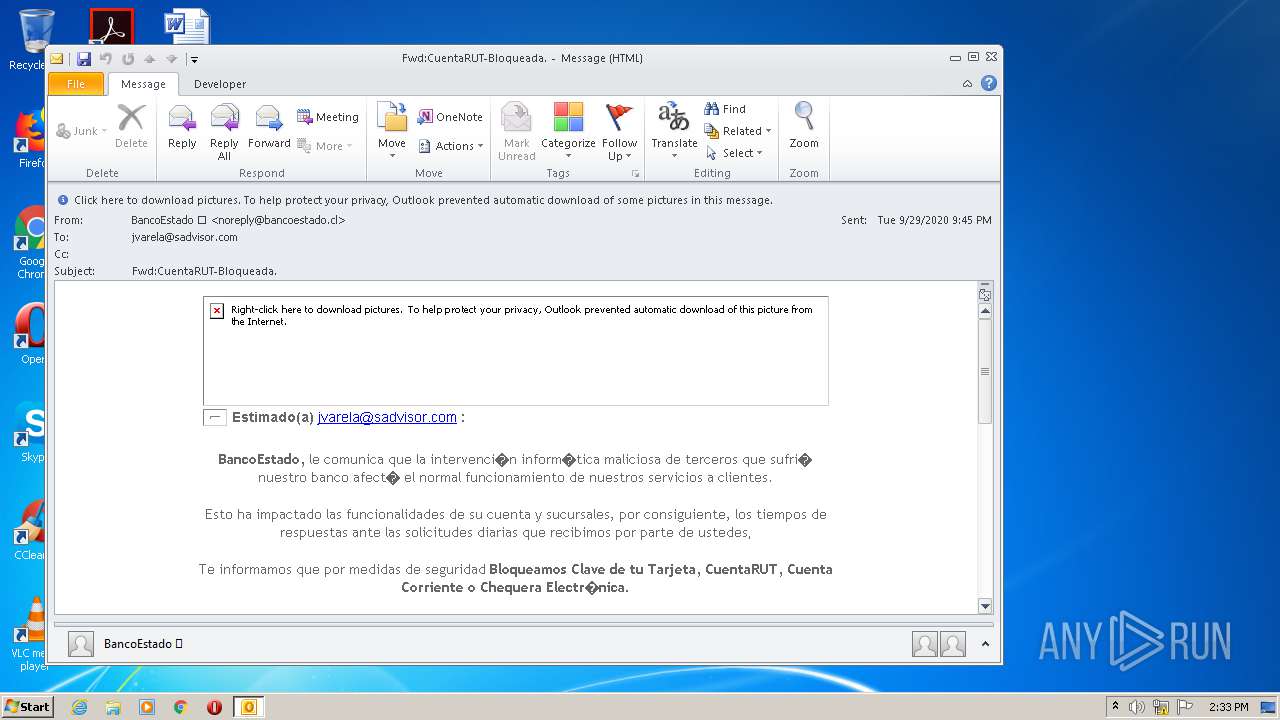
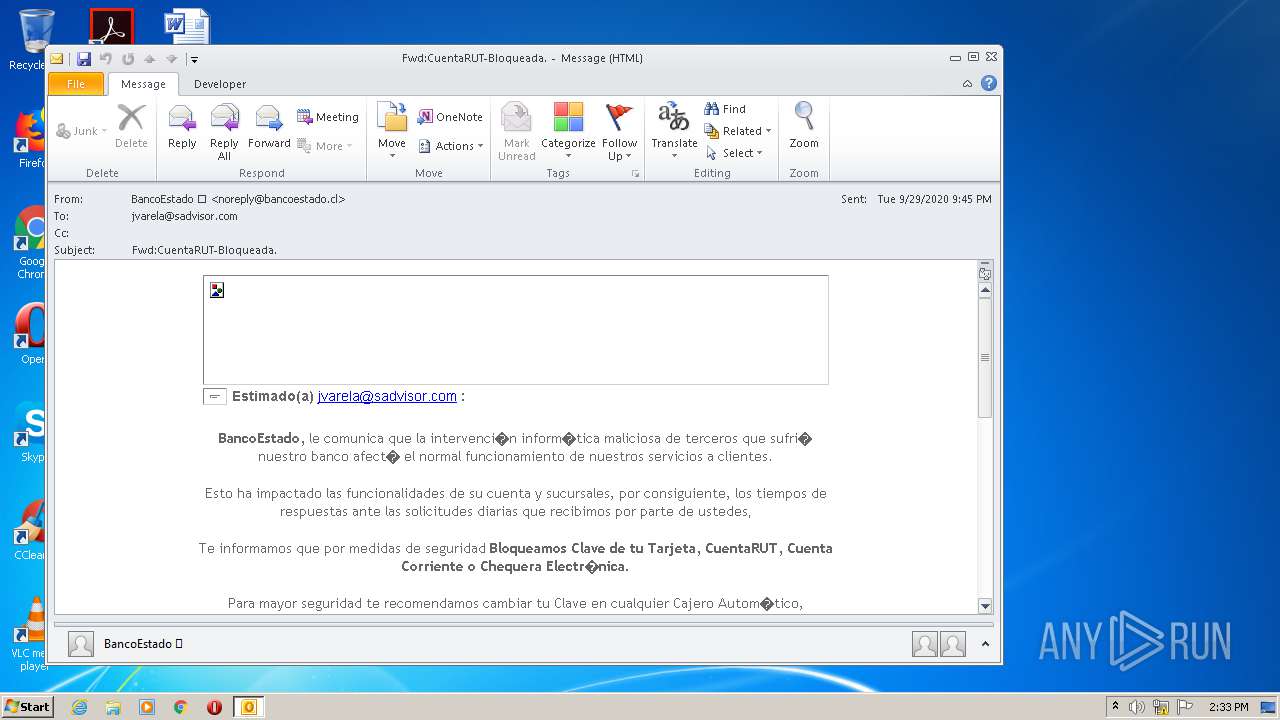
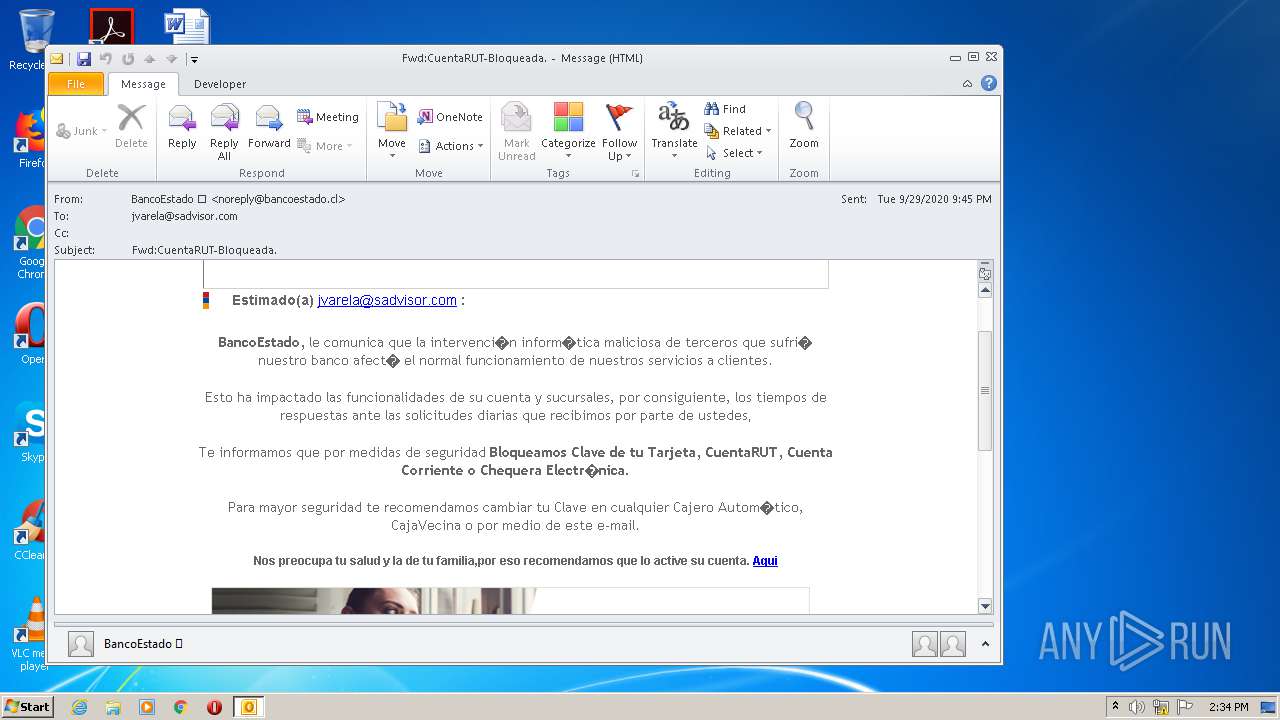
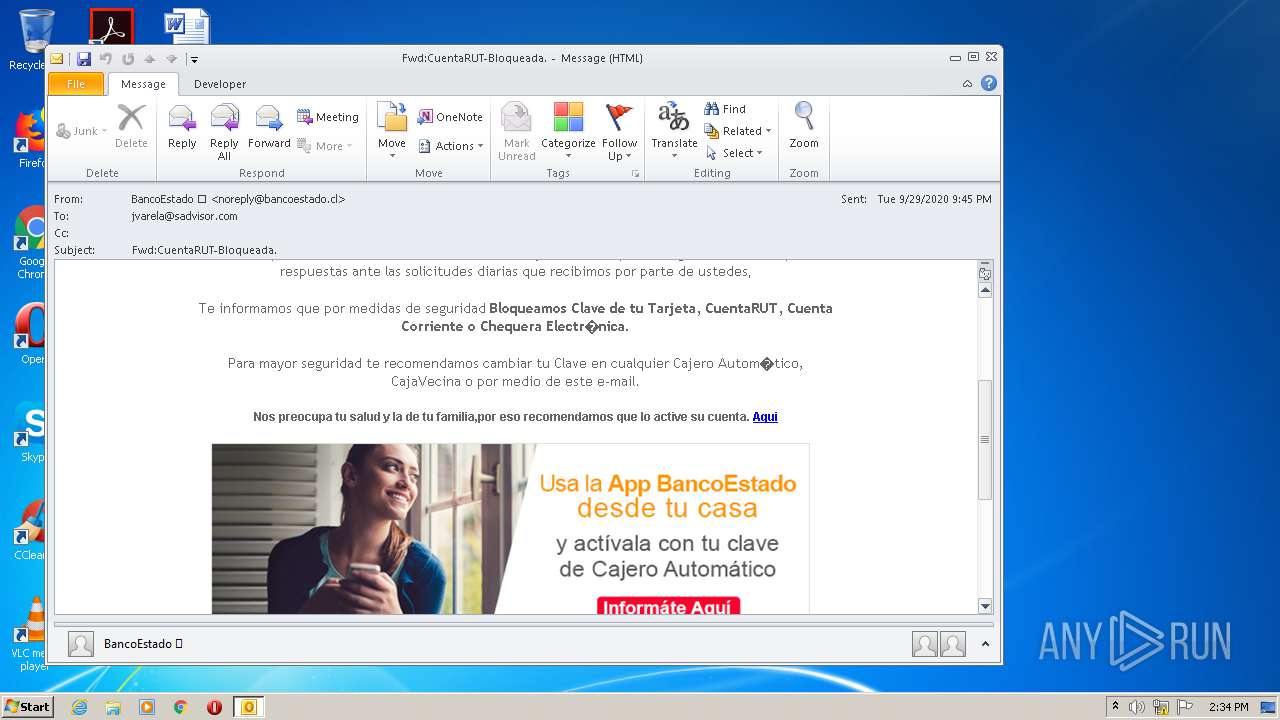
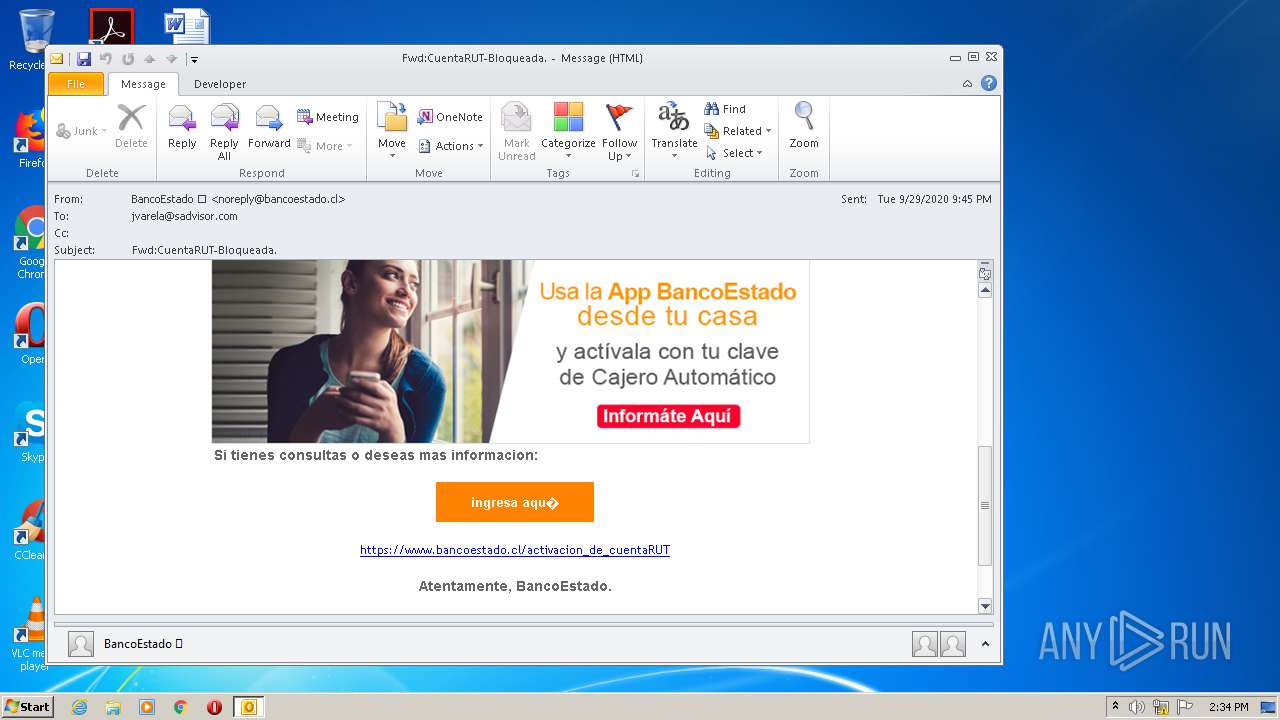
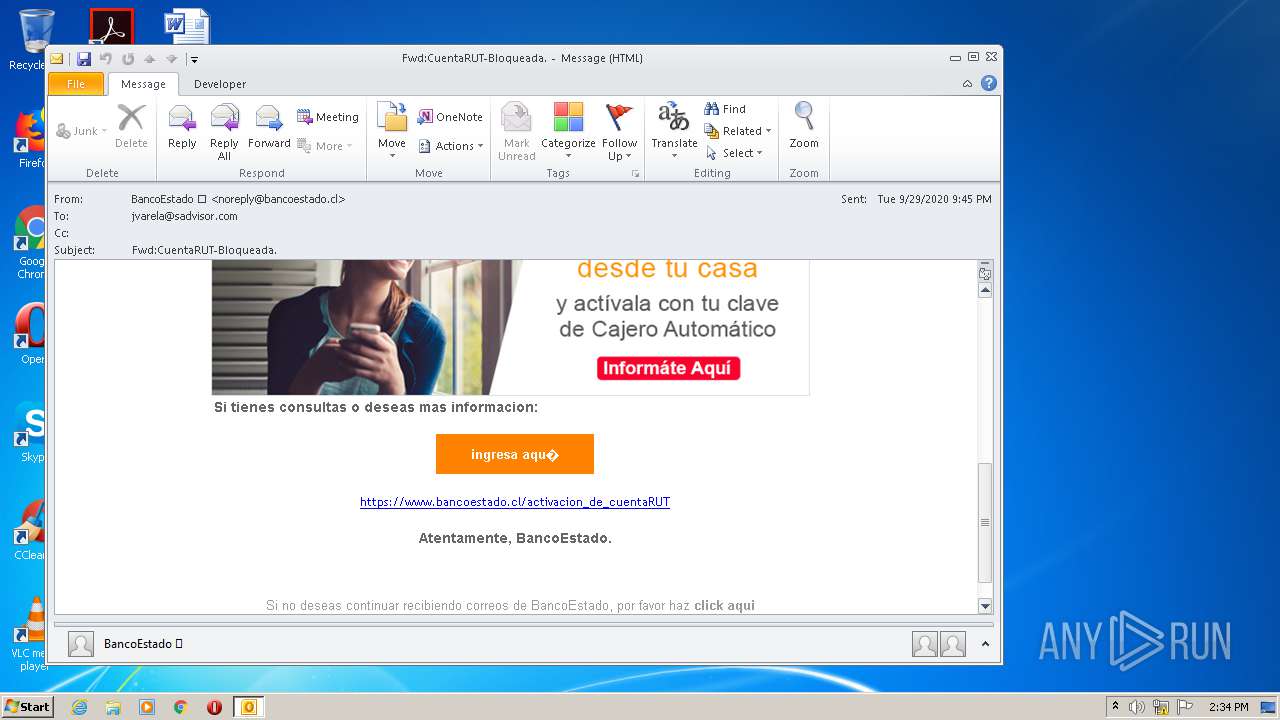
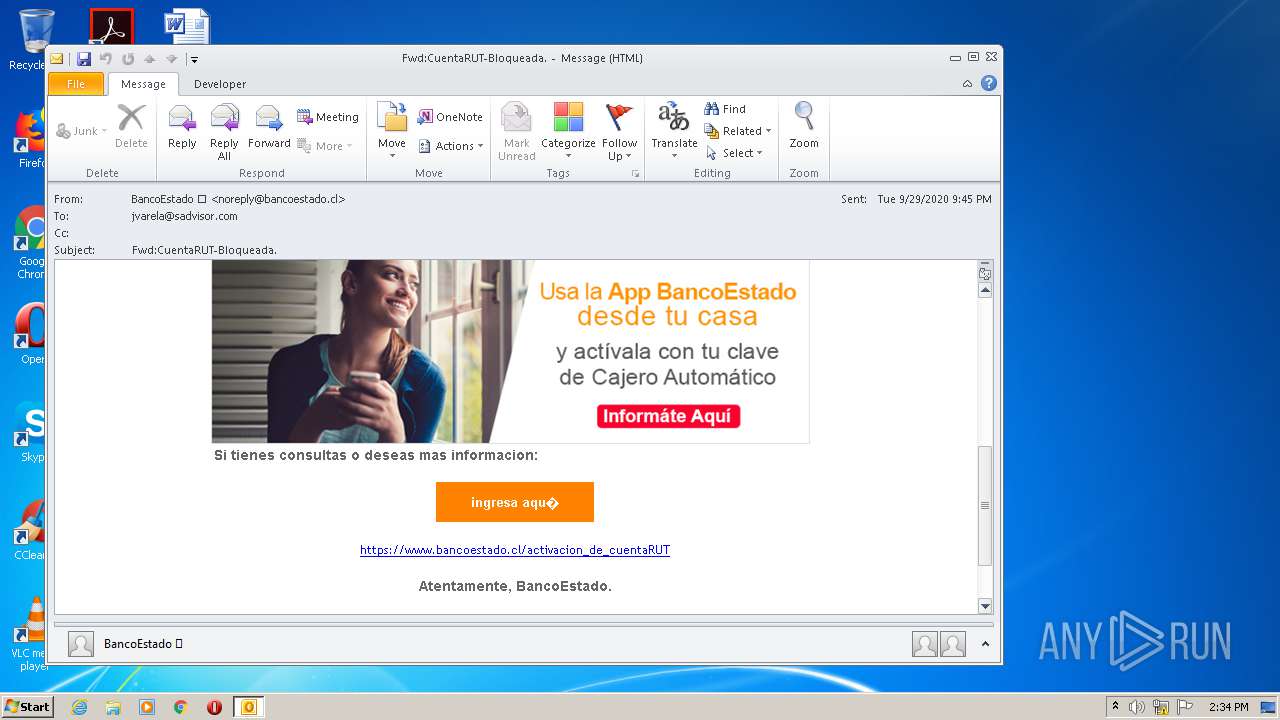
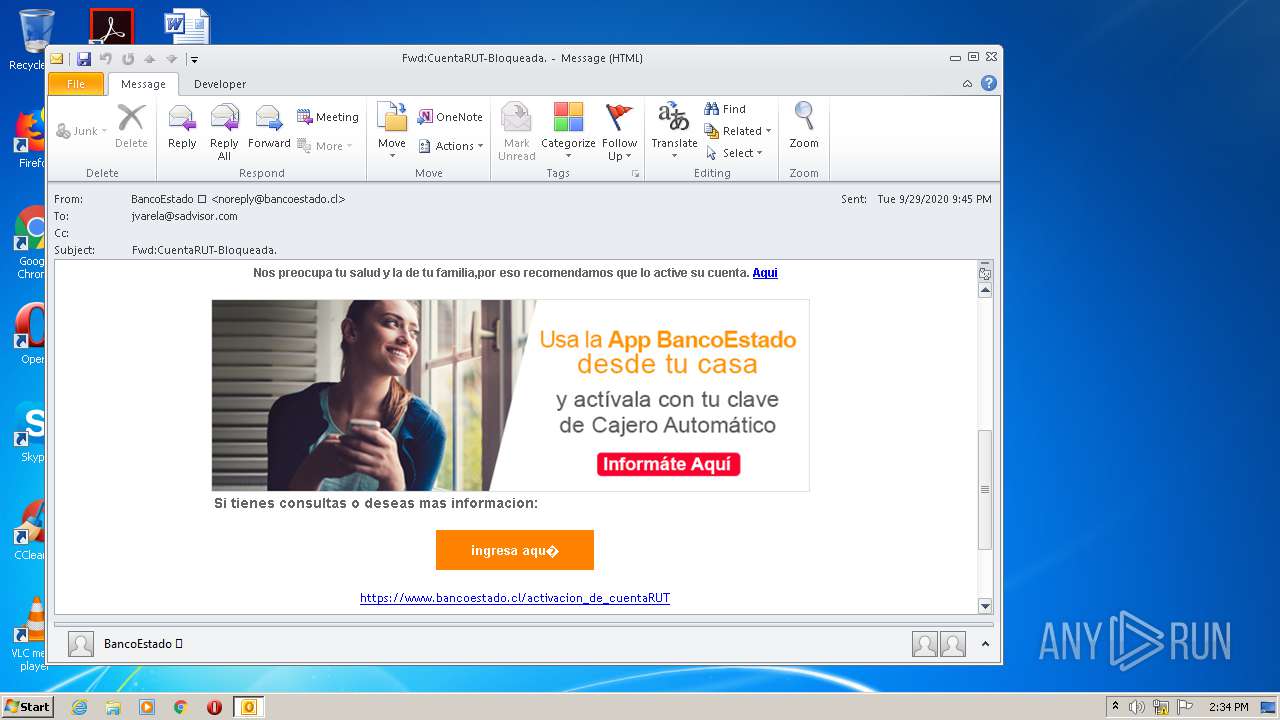
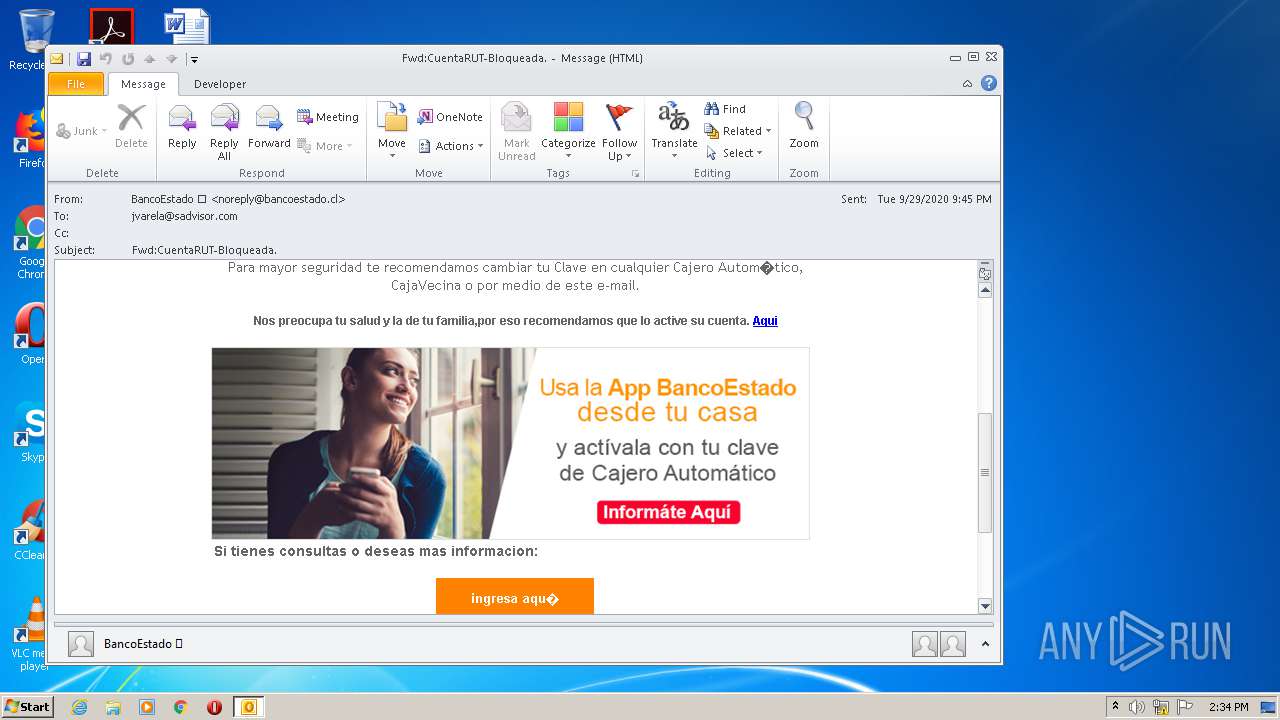
| File name: | Fwd_CuentaRUT-Bloqueada_.msg |
| Full analysis: | https://app.any.run/tasks/3eee25f2-6b8b-4791-bbbc-9cac3ae4e665 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 13:33:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 1A81723BCD30CBAD21B7814D6D57B29E |
| SHA1: | 2D47D60C0099C04FCFCCD5C2B97B594DFDA3095B |
| SHA256: | 2CE3AE38F507E3A0E71211546537D477B763082EA891525226CDA6FD093A75C9 |
| SSDEEP: | 384:69KPKtKj8AVAU2bKFKYJNG8O2GO74z56c9QYcW7t8Zu80K:69KPKtKj8O2bWlJk2GO74VXDzH80K |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2428)
SUSPICIOUS
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2428)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2428)
Reads settings of System Certificates
- OUTLOOK.EXE (PID: 2428)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2428)
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 2696)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2428)
- iexplore.exe (PID: 3864)
Application launched itself
- iexplore.exe (PID: 2696)
Changes internet zones settings
- iexplore.exe (PID: 2696)
Reads internet explorer settings
- iexplore.exe (PID: 3864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
40
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2428 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Fwd_CuentaRUT-Bloqueada_.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
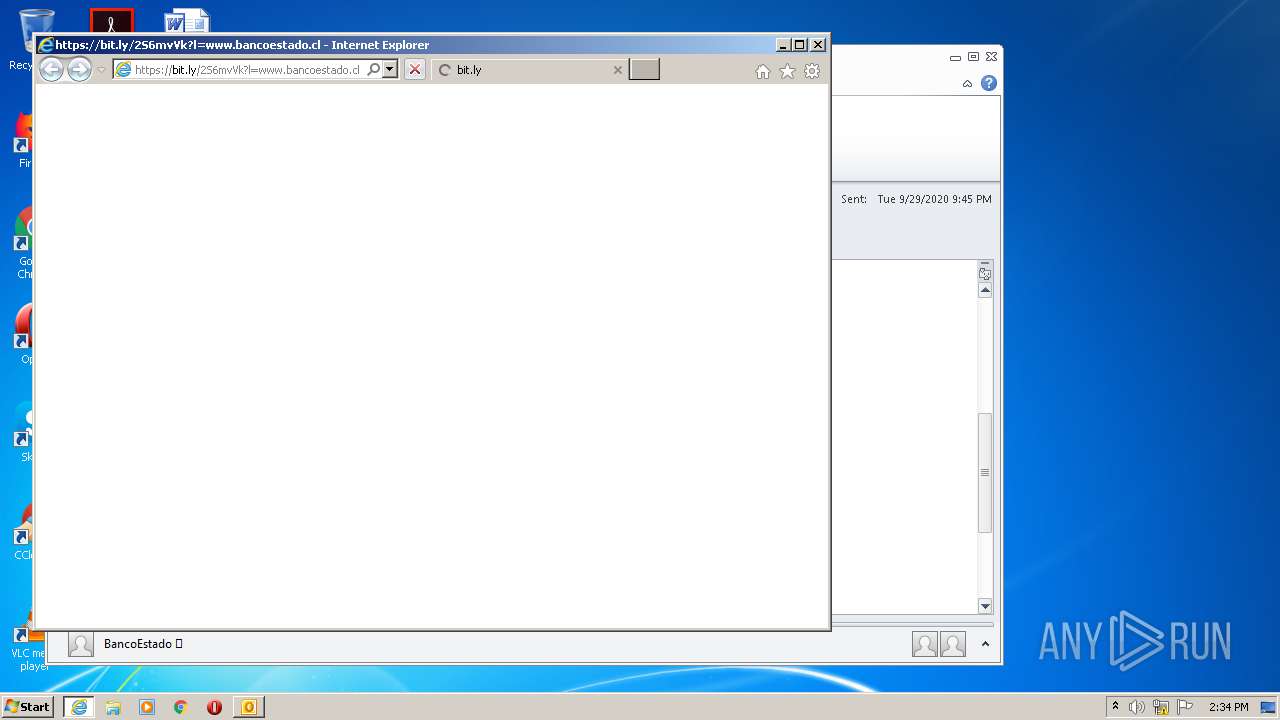
| 2696 | "C:\Program Files\Internet Explorer\iexplore.exe" https://bit.ly/2S6mvVk?l=www.bancoestado.cl | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2696 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
1 827
Read events
1 204
Write events
604
Delete events
19
Modification events
| (PID) Process: | (2428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
10
Text files
32
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR4079.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\Cab7C3A.tmp | — | |
MD5:— | SHA256:— | |||
| 2428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\Tar7C3B.tmp | — | |
MD5:— | SHA256:— | |||
| 2696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2428 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabBD7.tmp | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarBD8.tmp | — | |
MD5:— | SHA256:— | |||
| 2428 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_5FDD03068CBBD8A96F3AB9595BA10093 | binary | |
MD5:— | SHA256:— | |||
| 2428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\sp_banner_app_login_web_generica[1].jpg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
32
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2428 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2428 | OUTLOOK.EXE | GET | 301 | 104.111.237.76:80 | http://www.bancoestado.cl/imagenes/cartola/img_cartola_mut/img_mut_02.jpg | NL | — | — | suspicious |
2428 | OUTLOOK.EXE | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertGlobalRootCA.crl | US | der | 631 b | whitelisted |
3864 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJ9L2KGL92BpjF3kAtaDtxauTmhgQUPdNQpdagre7zSmAKZdMh1Pj41g8CEAqN7HPiQ2%2F4c3rdXE3uHG8%3D | US | der | 471 b | whitelisted |
3864 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEGfe9D7xe9riT%2FWUBgbSwIQ%3D | US | der | 471 b | whitelisted |
— | — | GET | 200 | 216.58.207.35:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEB3oRgfjsJWUCAAAAABbLrQ%3D | US | der | 471 b | whitelisted |
— | — | GET | 200 | 216.58.207.35:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCOUTy4wn8XWggAAAAAWy8I | US | der | 472 b | whitelisted |
— | — | GET | 200 | 216.58.207.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
— | — | GET | 200 | 216.58.207.35:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEBMtUwvbZX3eCAAAAABbLrM%3D | US | der | 471 b | whitelisted |
2696 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3864 | iexplore.exe | 67.199.248.10:443 | bit.ly | Bitly Inc | US | shared |
3864 | iexplore.exe | 203.143.89.30:80 | www.makeupcollege.com.au | OMNIconnect Pty Ltd | AU | unknown |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 67.199.248.10:443 | bit.ly | Bitly Inc | US | shared |
2428 | OUTLOOK.EXE | 104.111.237.76:80 | www.bancoestado.cl | Akamai International B.V. | NL | unknown |
2428 | OUTLOOK.EXE | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3864 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
3864 | iexplore.exe | 203.143.89.30:443 | www.makeupcollege.com.au | OMNIconnect Pty Ltd | AU | unknown |
— | — | 216.58.208.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.bancoestado.cl |
| suspicious |
ocsp.digicert.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
bit.ly |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
www.makeupcollege.com.au |
| unknown |
ocsp.comodoca.com |
| whitelisted |