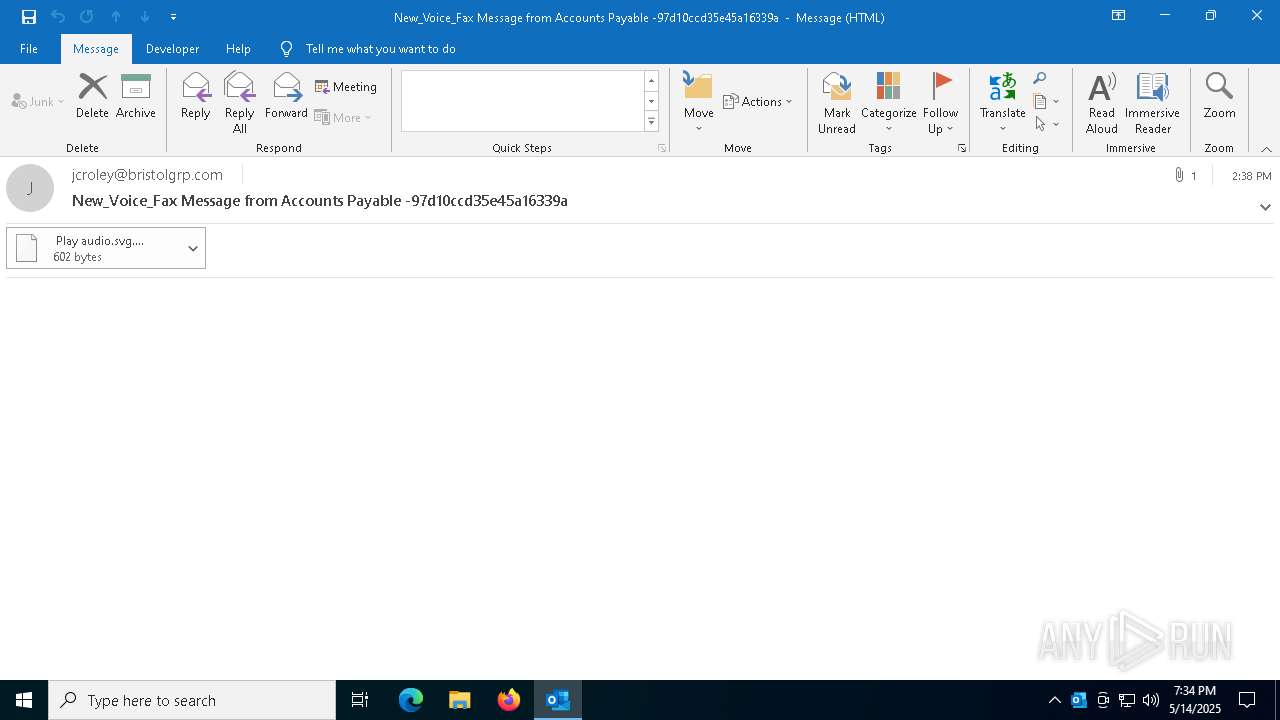
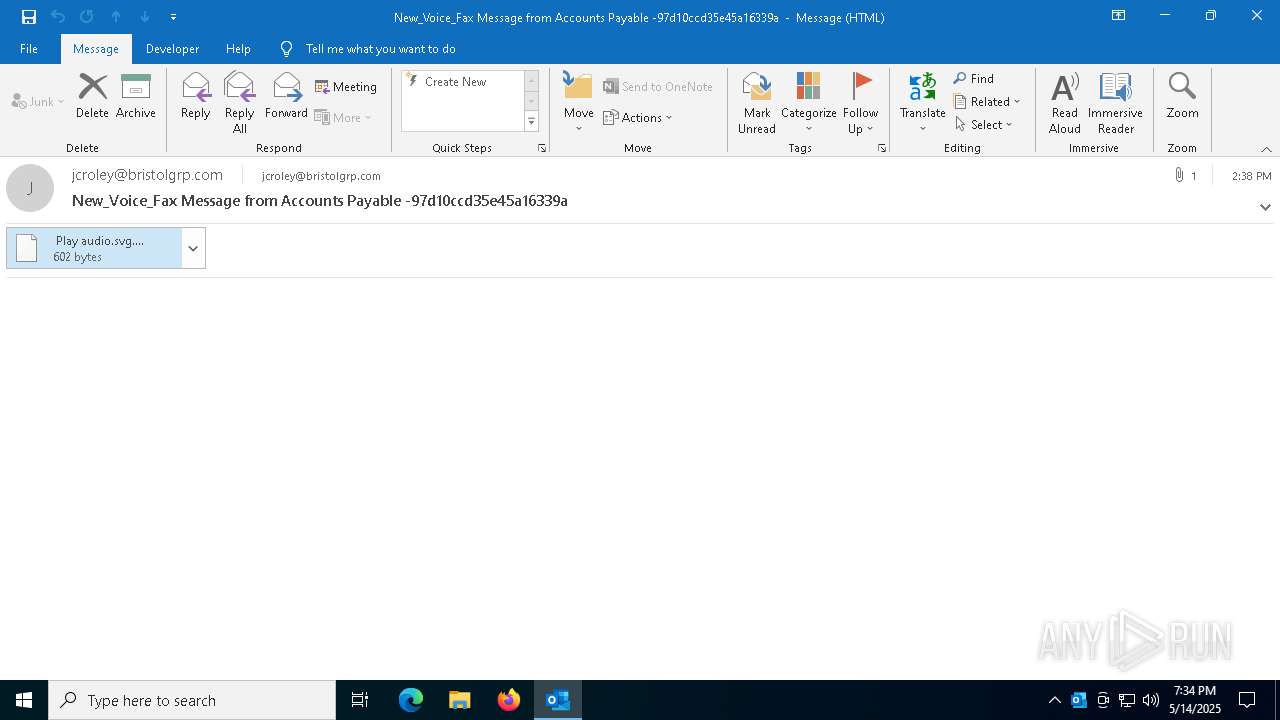
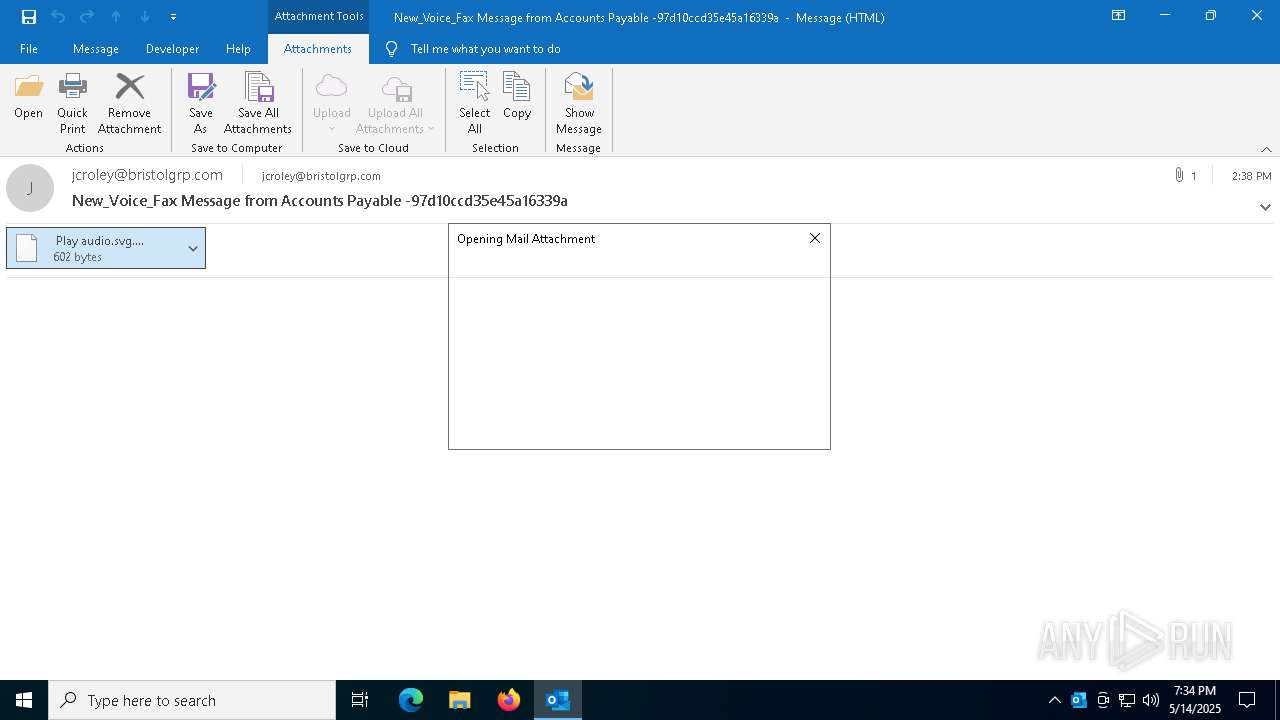
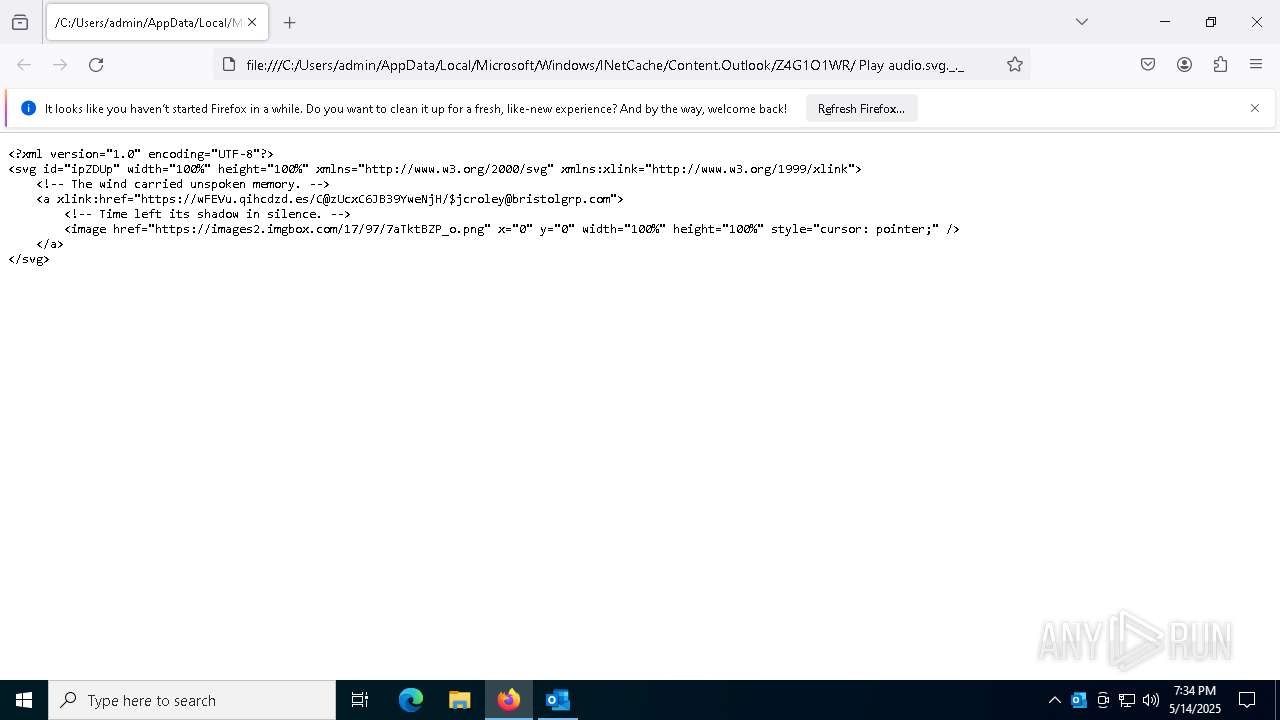
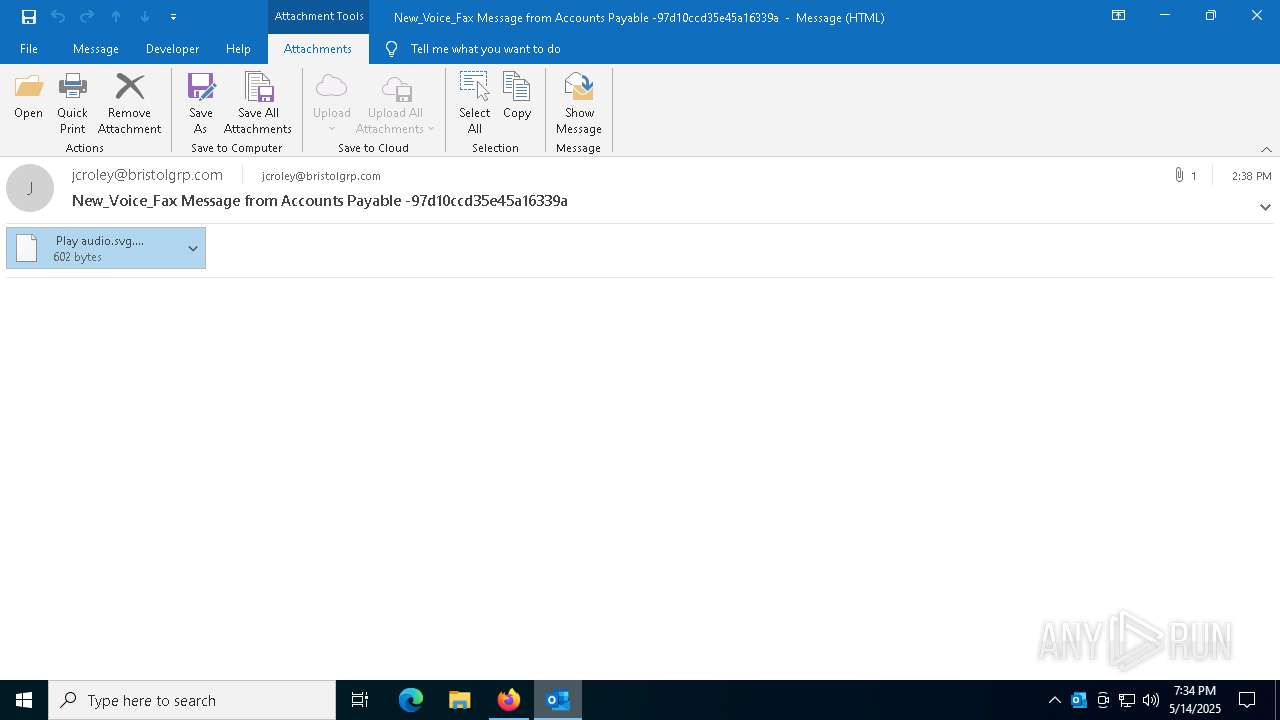
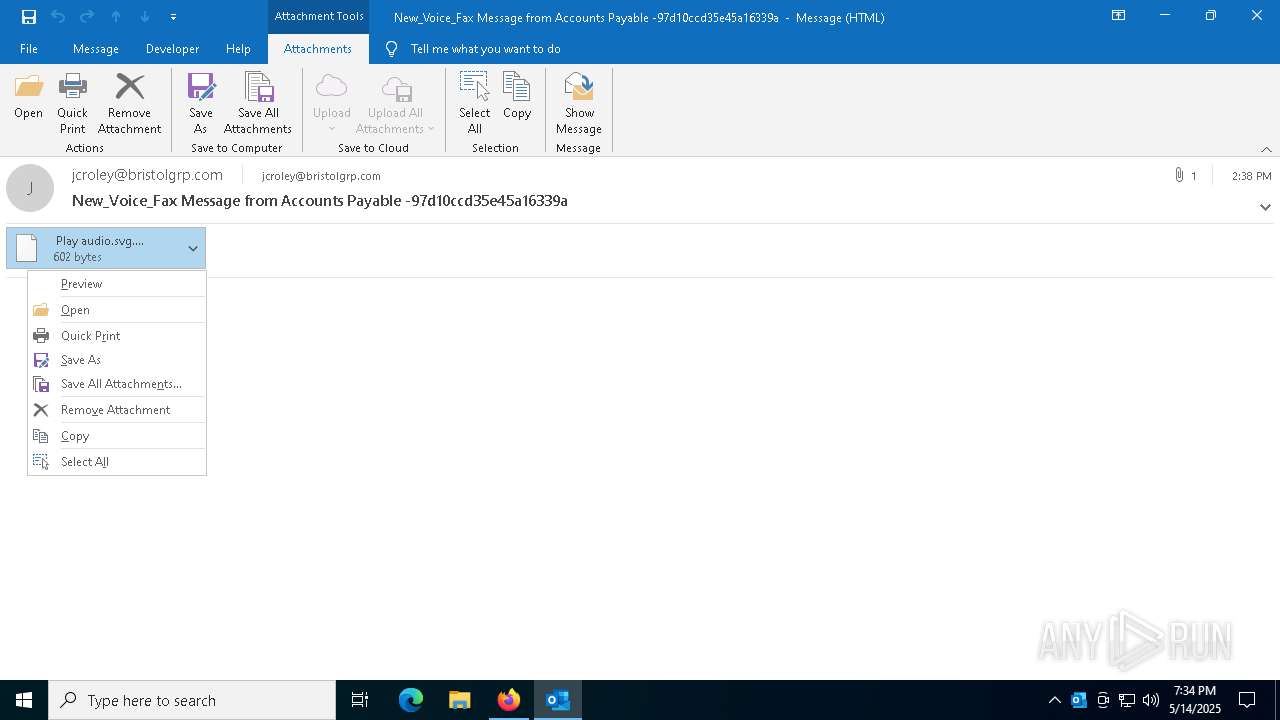
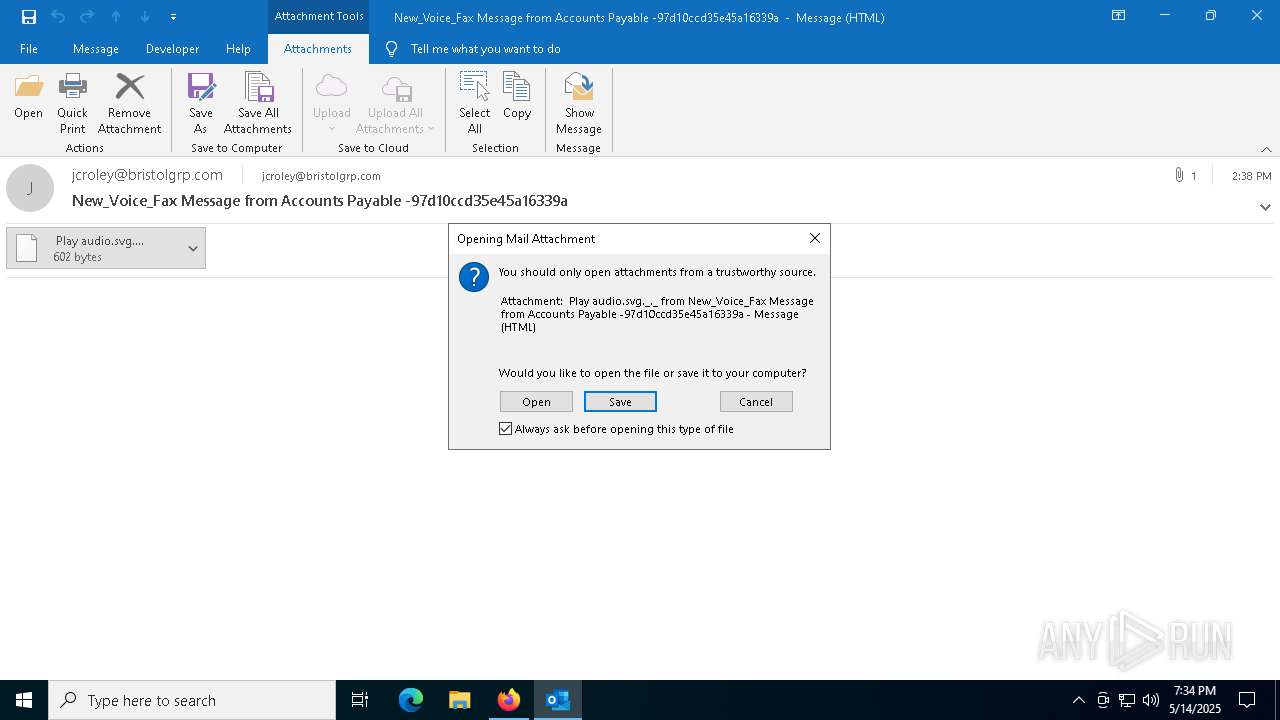
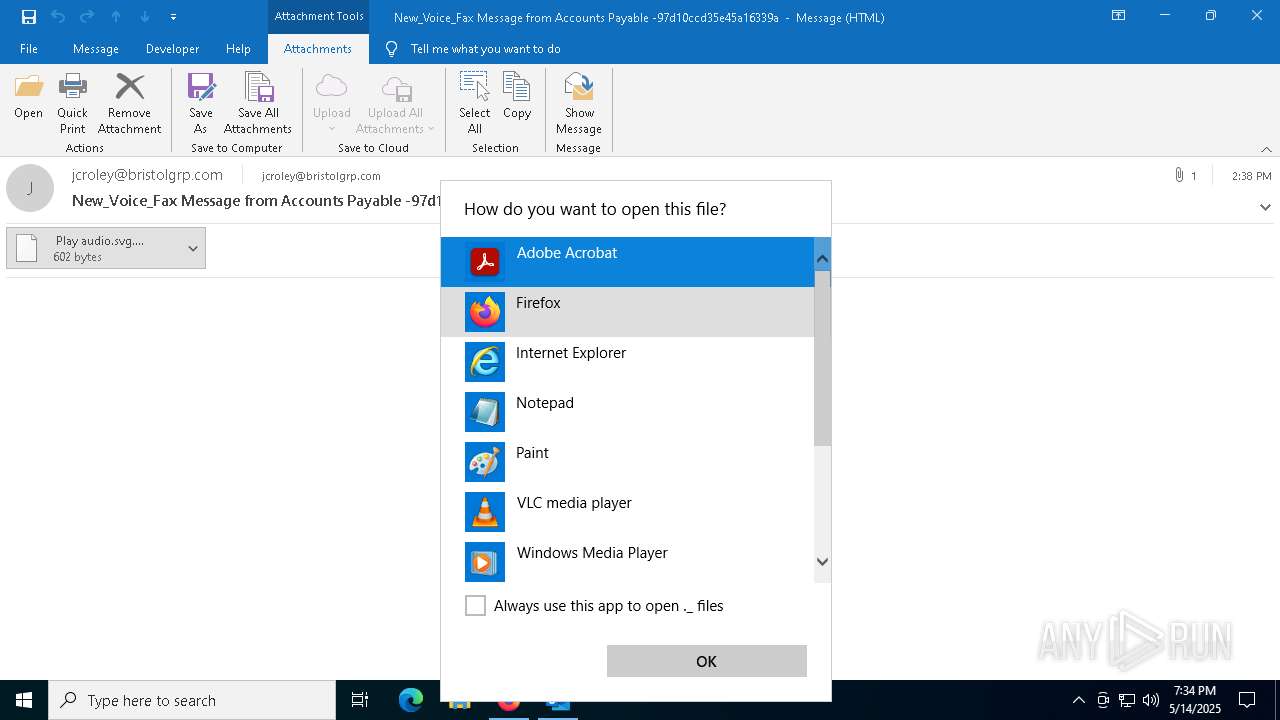
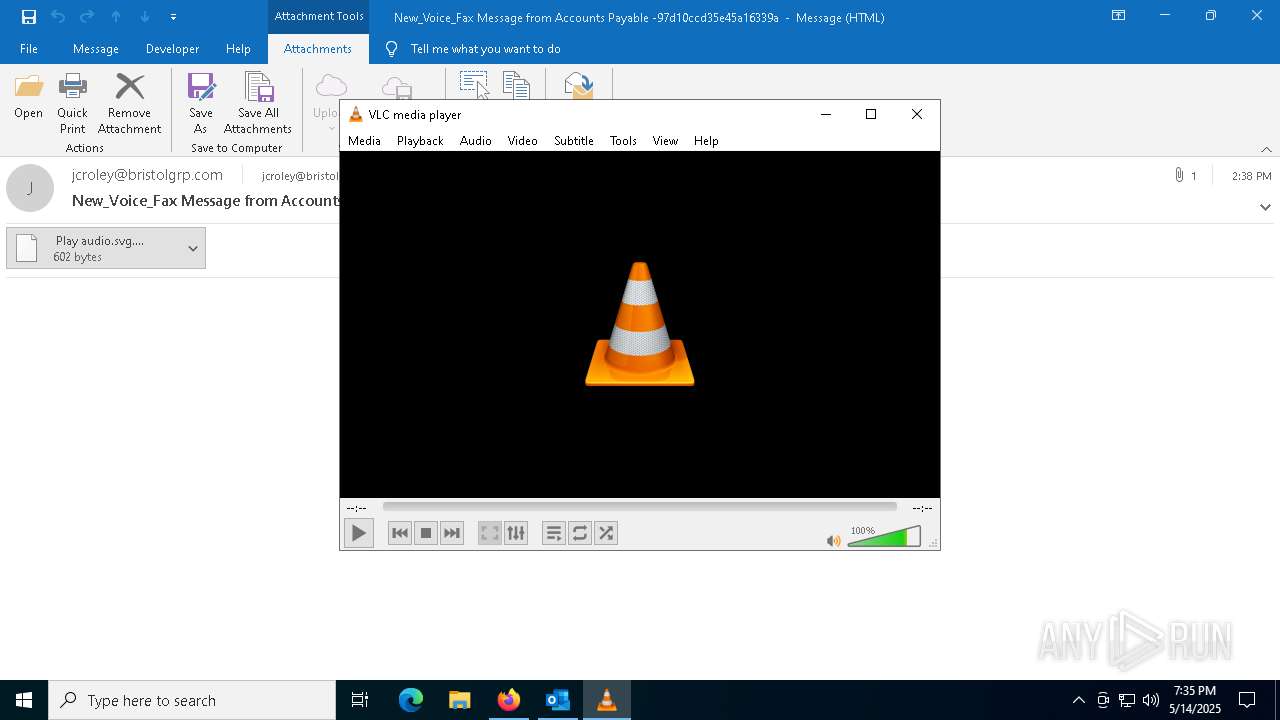
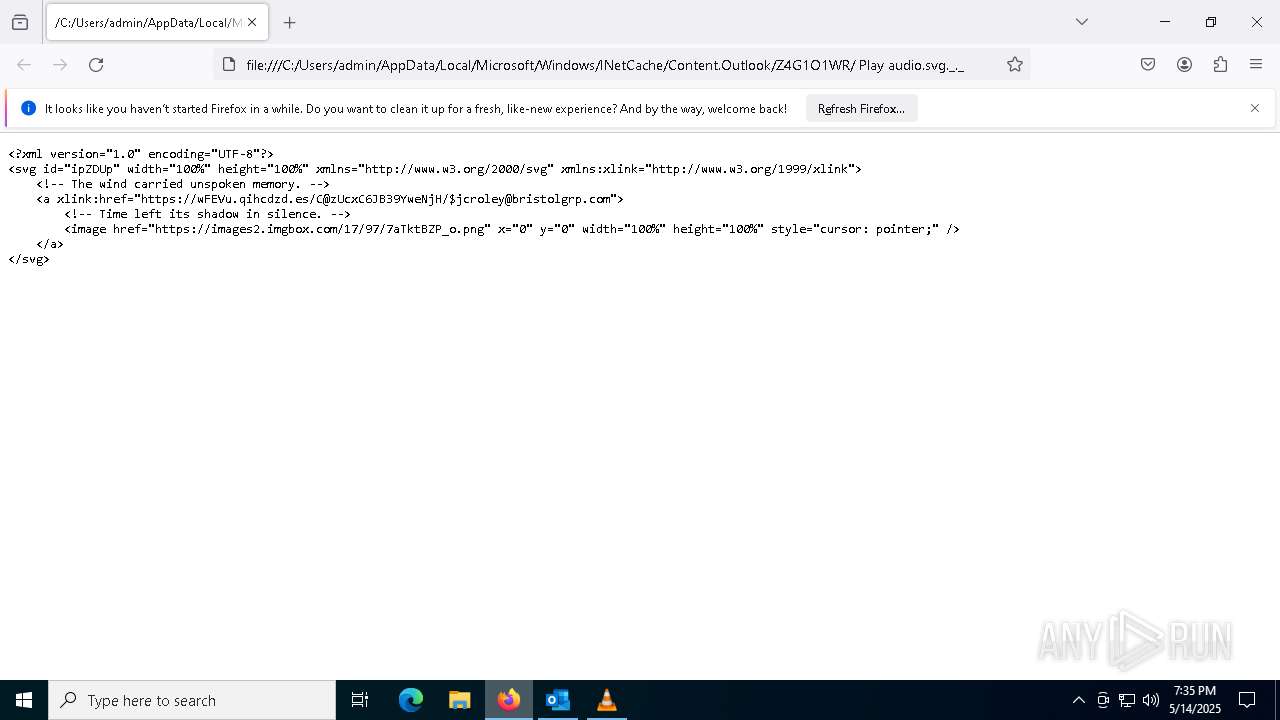
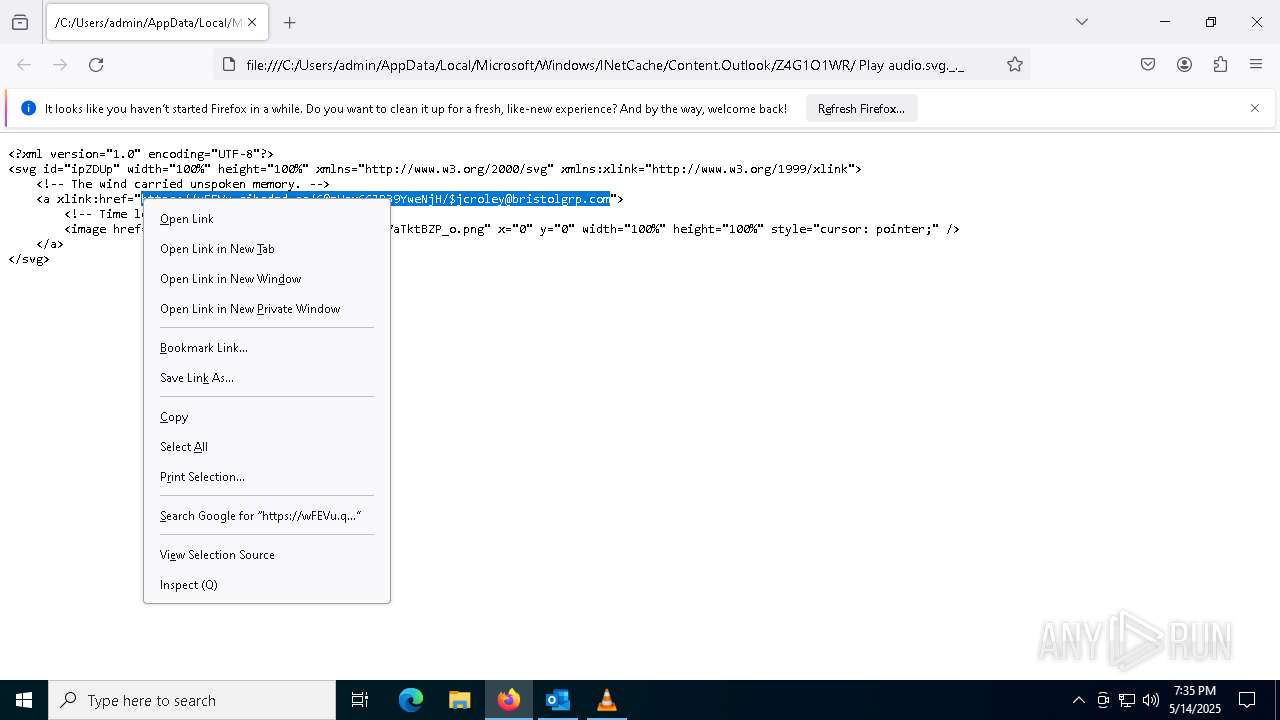
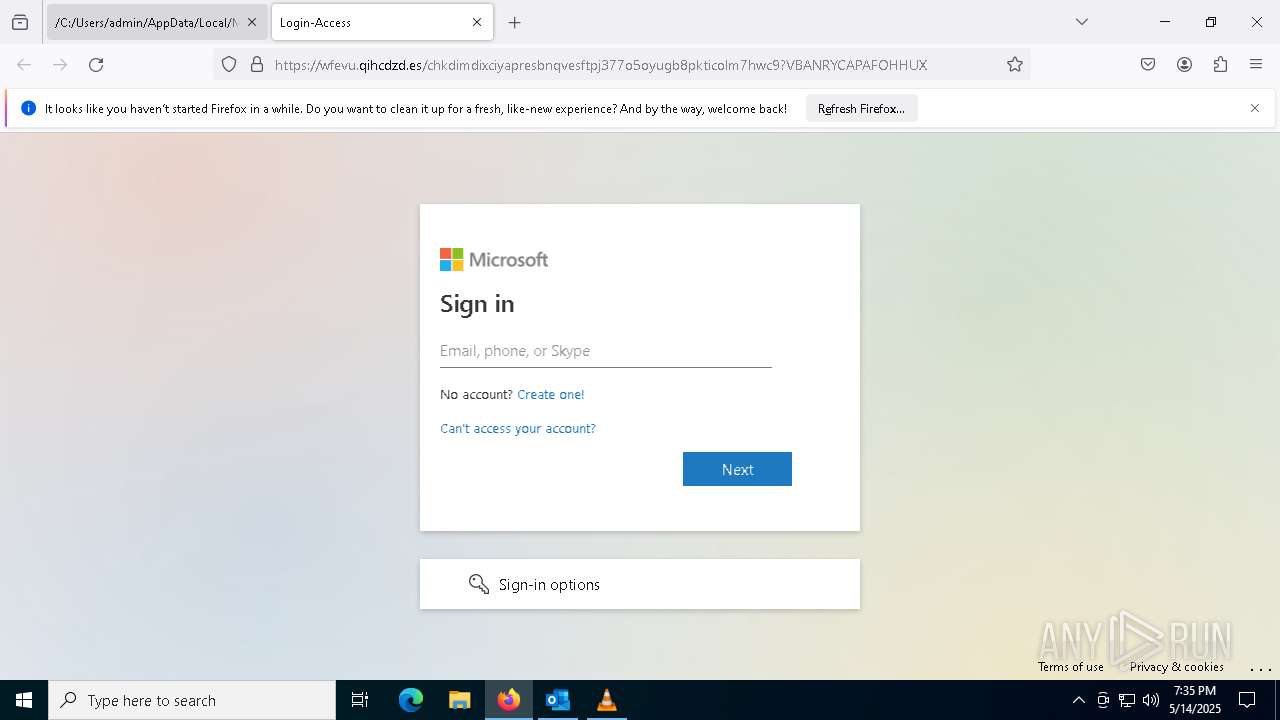
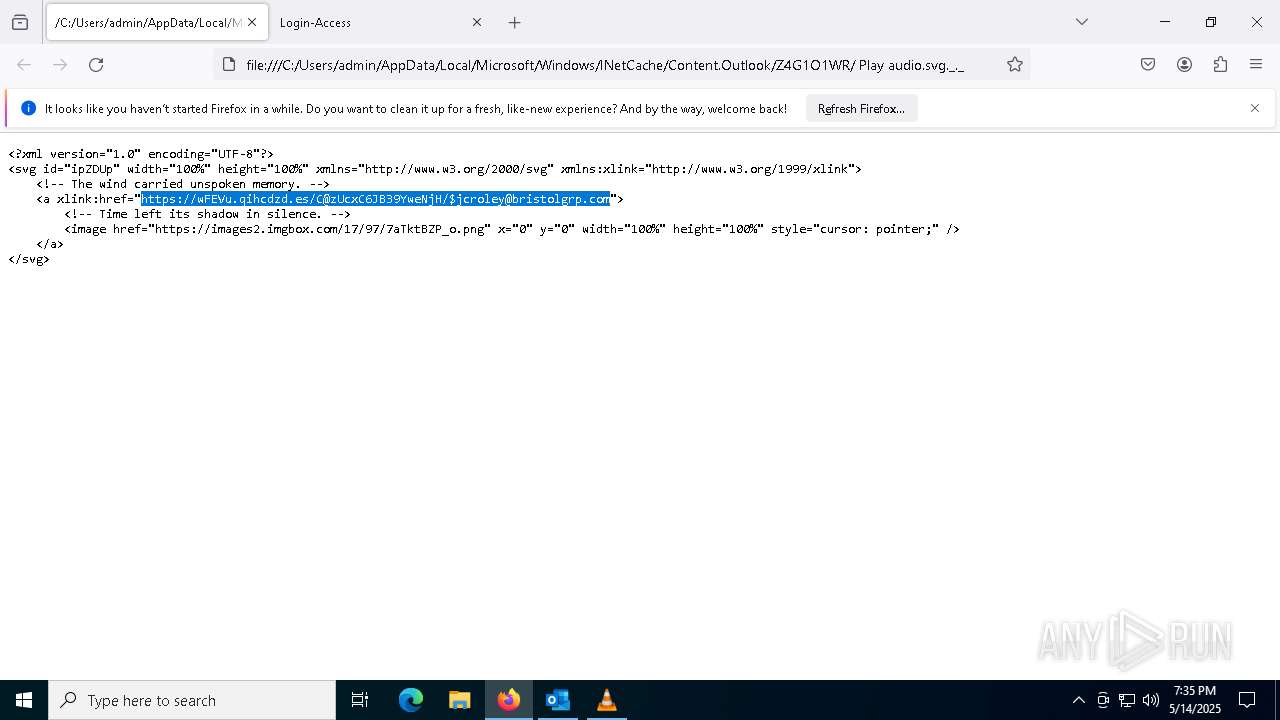
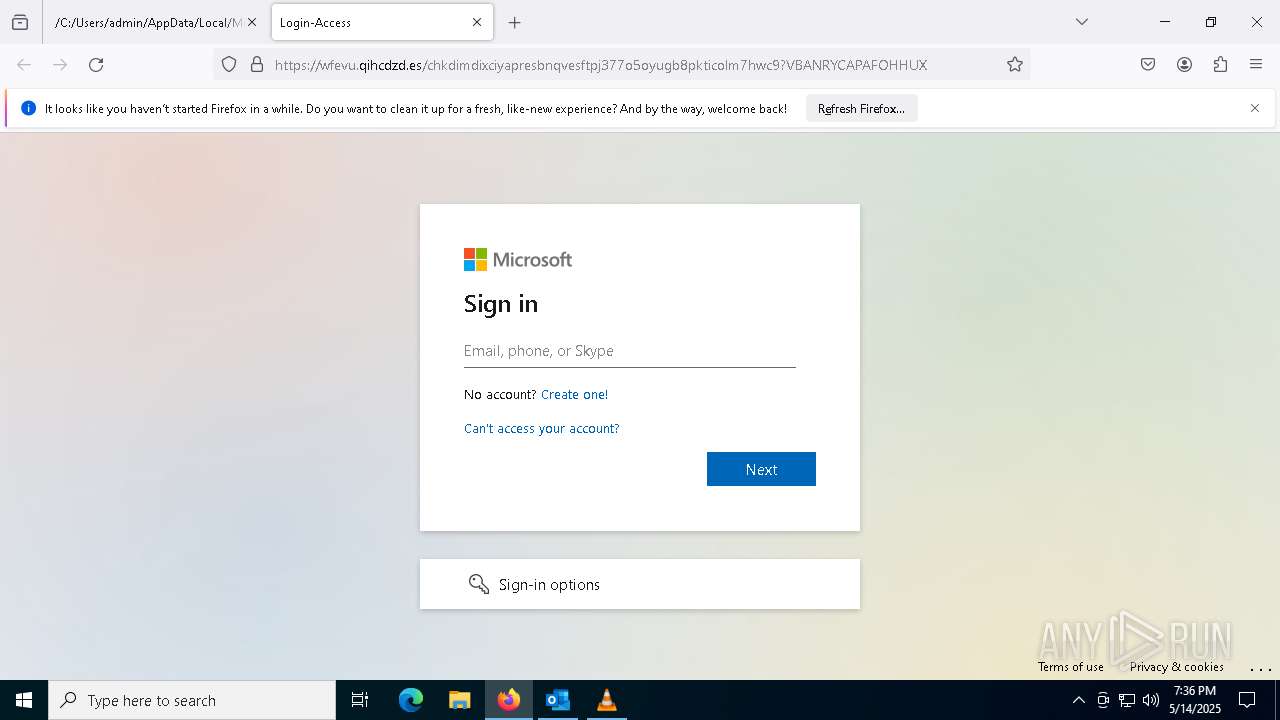
| File name: | New_Voice_Fax Message from Accounts Payable -97d10ccd35e45a16339a.eml |
| Full analysis: | https://app.any.run/tasks/ca8fba97-3914-4ccc-bfd7-7d22c07e680b |
| Verdict: | Malicious activity |
| Analysis date: | May 14, 2025, 19:33:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 74B4AB91070B38D1684B2AFC07929756 |
| SHA1: | D95F9D441BE00B0BED37EE61E46F4ED0F7211F50 |
| SHA256: | 2CE053274080DBC2483A8A34E342CB39F6B53F0EB591C2FCCDDF482EA215DADF |
| SSDEEP: | 96:qqXRZURT+o/I8UxmpNENctmCYIvYIwmGA0FqWWx0l0mX12pi+8ofFIMVZIYrwImM:qq21mmpScIbxA0YJ0ll2chE3IIwIm+Z |
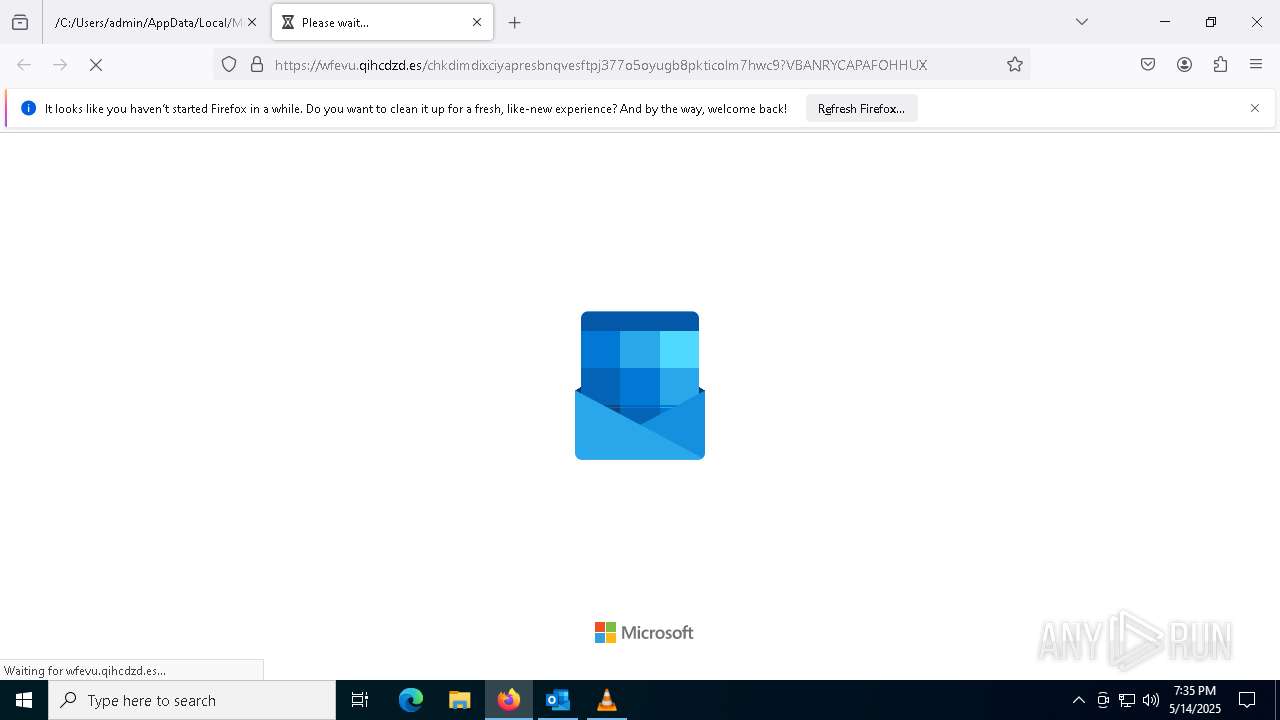
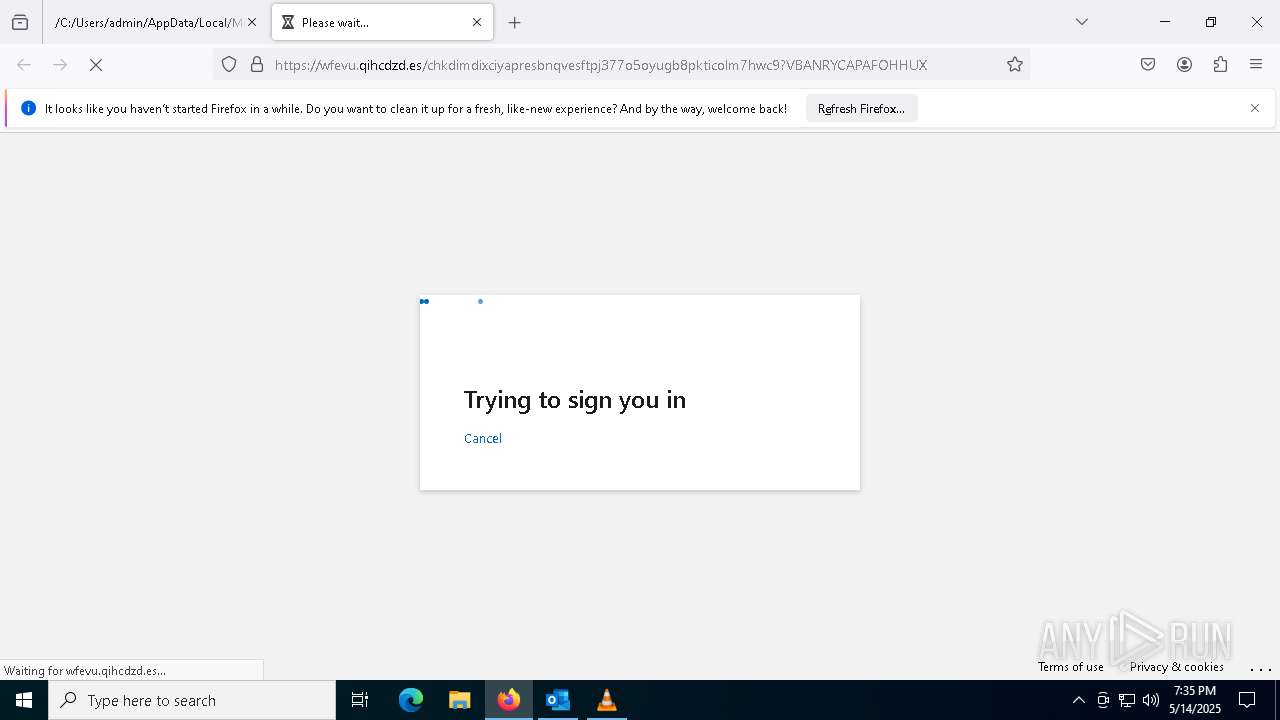
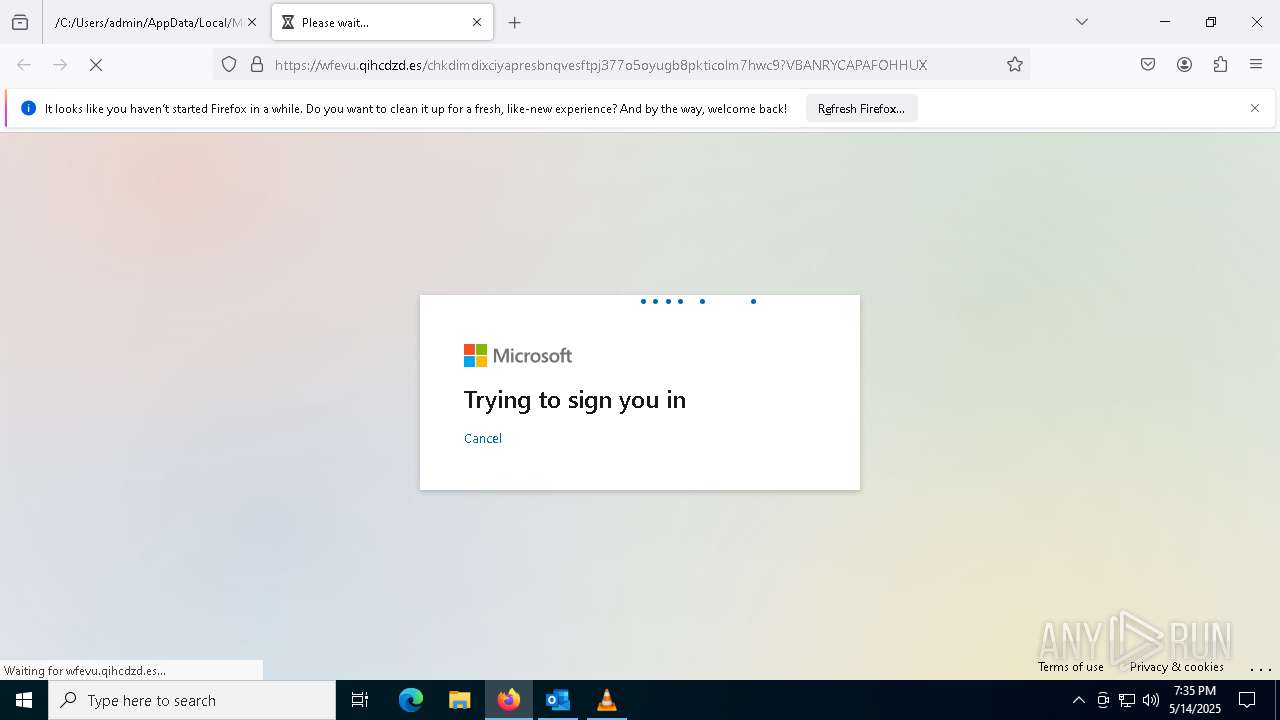
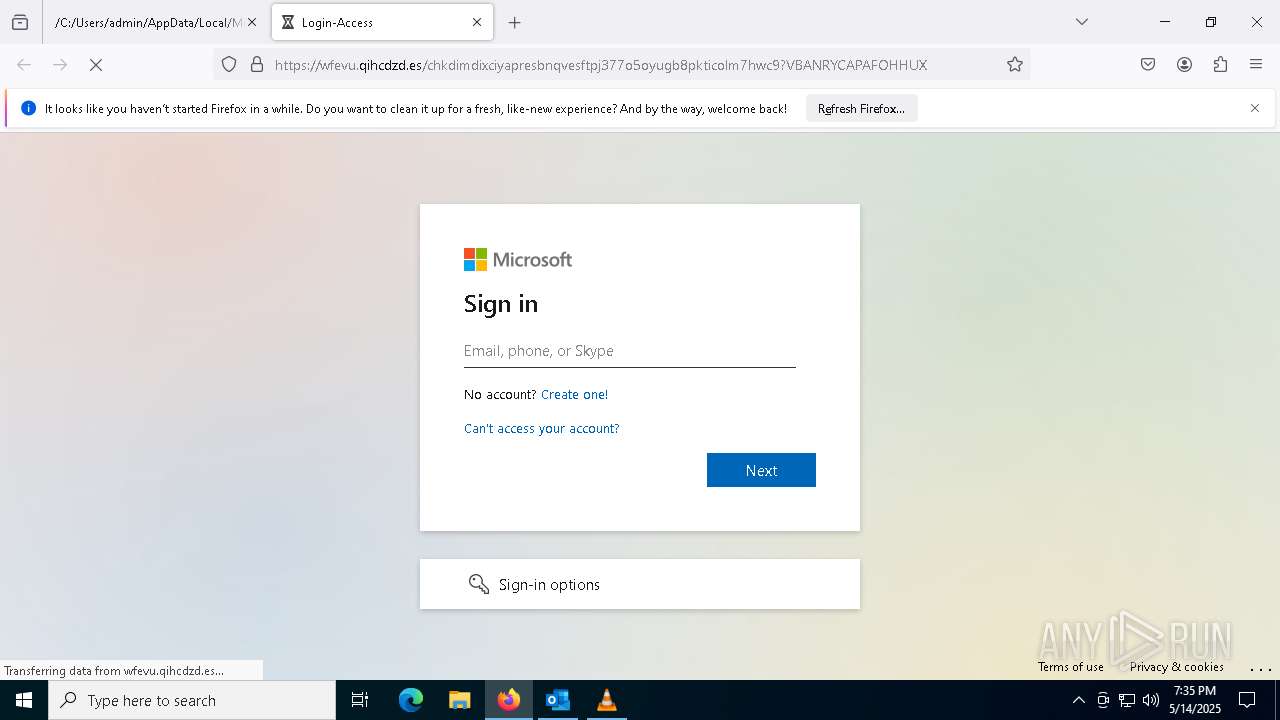
MALICIOUS
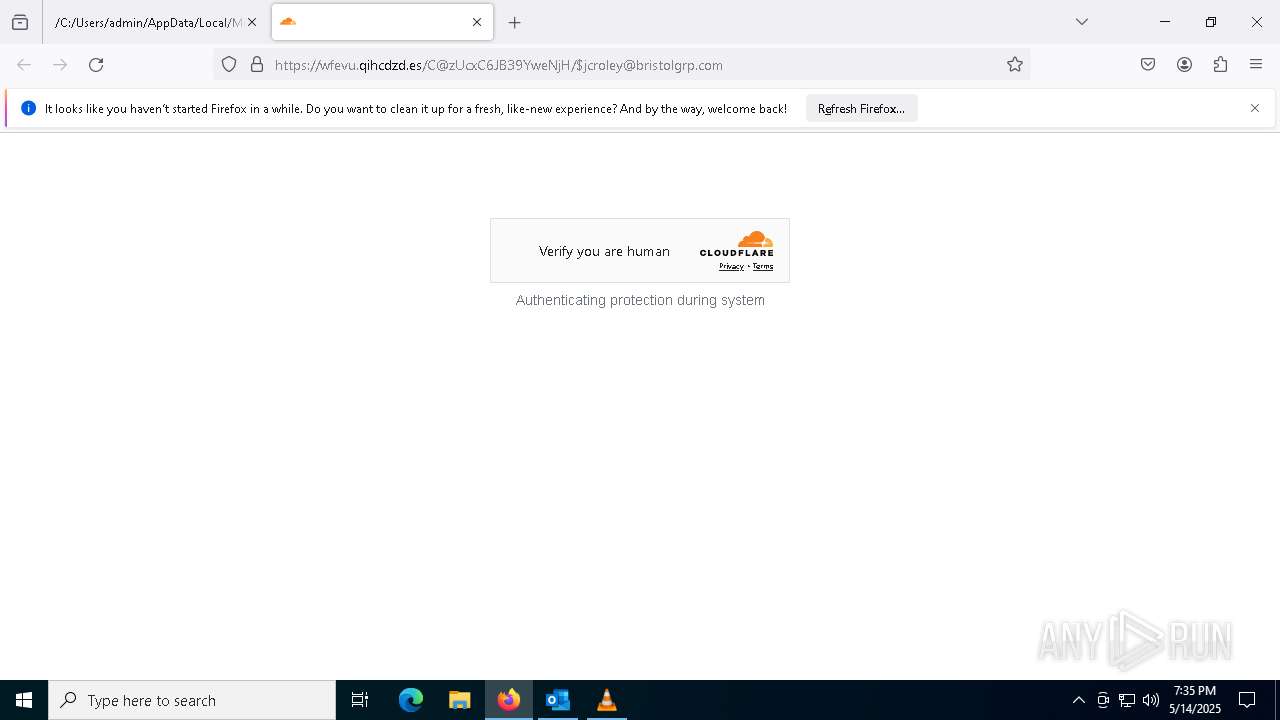
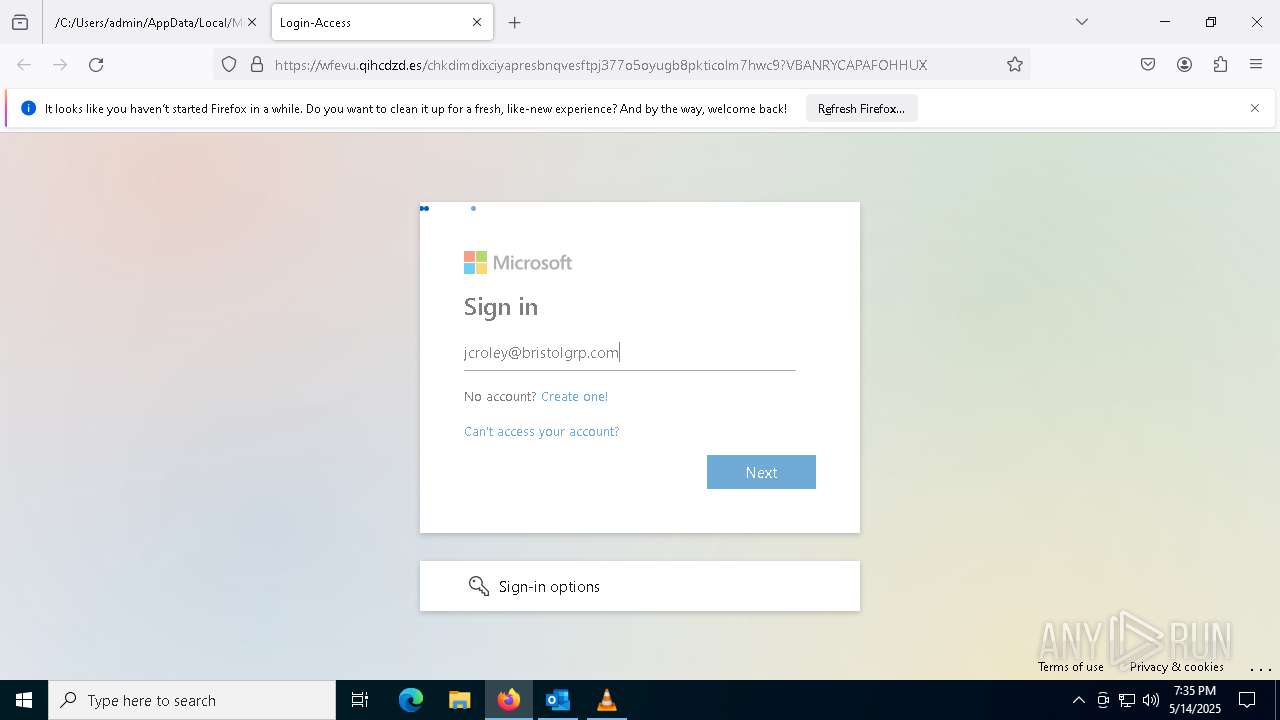
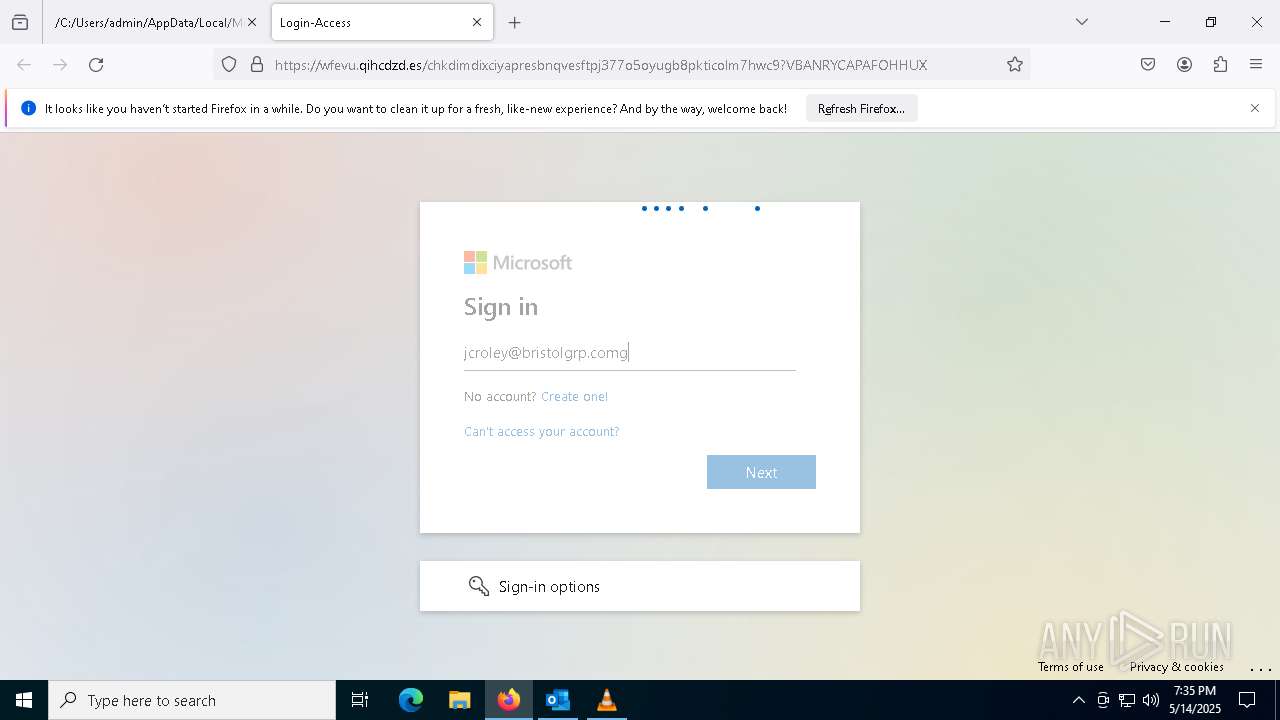
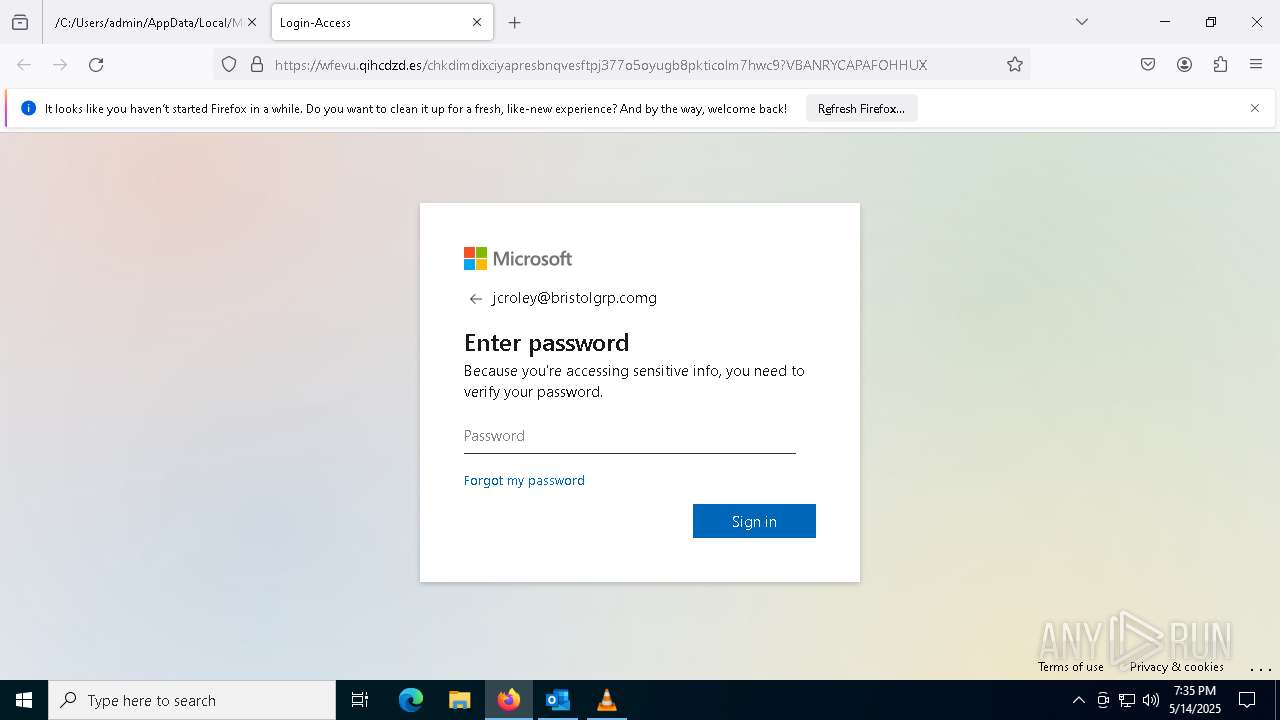
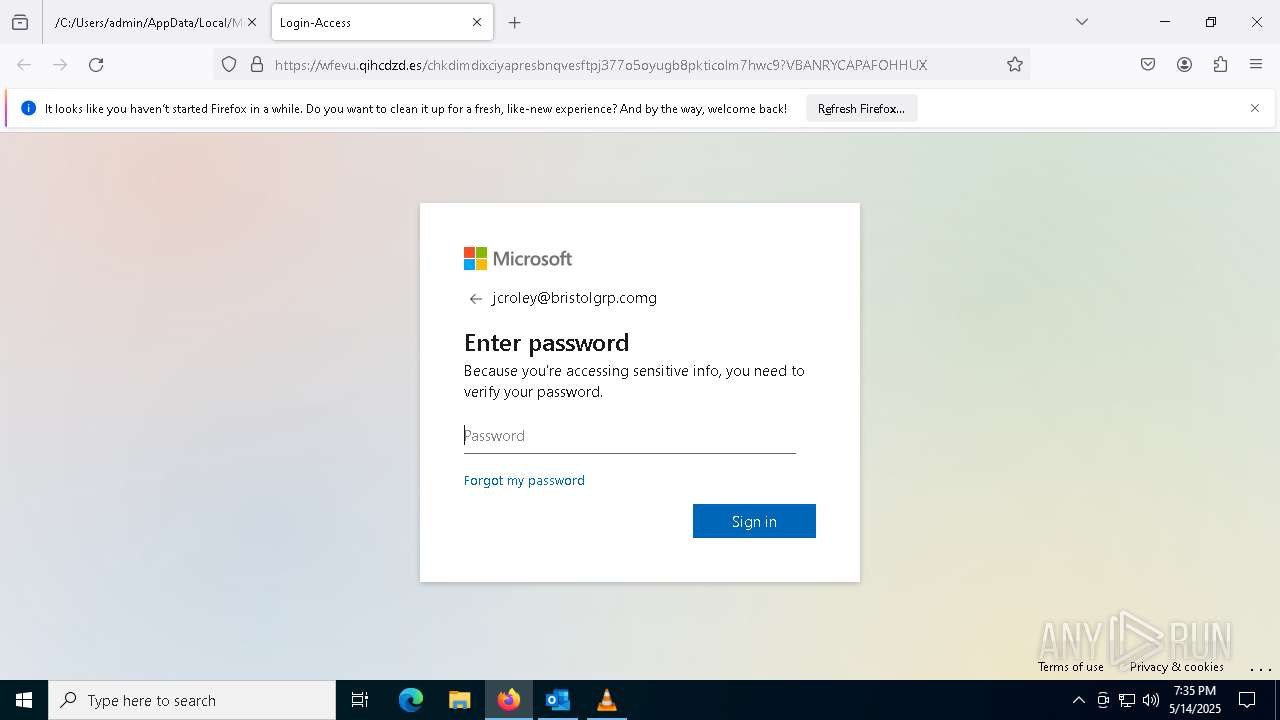
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- vlc.exe (PID: 6456)
Checks for external IP
- svchost.exe (PID: 2196)
INFO
Application launched itself
- firefox.exe (PID: 7408)
- firefox.exe (PID: 4428)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 5868)
- OpenWith.exe (PID: 8092)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5868)
- OpenWith.exe (PID: 8092)
Reads the computer name
- vlc.exe (PID: 6456)
The process uses Lua
- vlc.exe (PID: 6456)
Checks supported languages
- vlc.exe (PID: 6456)
Reads the software policy settings
- slui.exe (PID: 7604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
158
Monitored processes
21
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1904 -parentBuildID 20240213221259 -prefsHandle 1832 -prefMapHandle 1824 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {f29d17a5-b030-4a6c-8365-deeddc56a8bd} 4428 "\\.\pipe\gecko-crash-server-pipe.4428" 209646eae10 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4180 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5004 -childID 4 -isForBrowser -prefsHandle 5048 -prefMapHandle 5016 -prefsLen 31251 -prefMapSize 244583 -jsInitHandle 1492 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {666205e4-357f-4bb8-806d-68637d55cee4} 4428 "\\.\pipe\gecko-crash-server-pipe.4428" 2096e365d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4220 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4924 -childID 3 -isForBrowser -prefsHandle 4988 -prefMapHandle 4984 -prefsLen 31251 -prefMapSize 244583 -jsInitHandle 1492 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {286344b6-47cb-4af0-8c81-97aabfa57481} 4428 "\\.\pipe\gecko-crash-server-pipe.4428" 2096e365f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
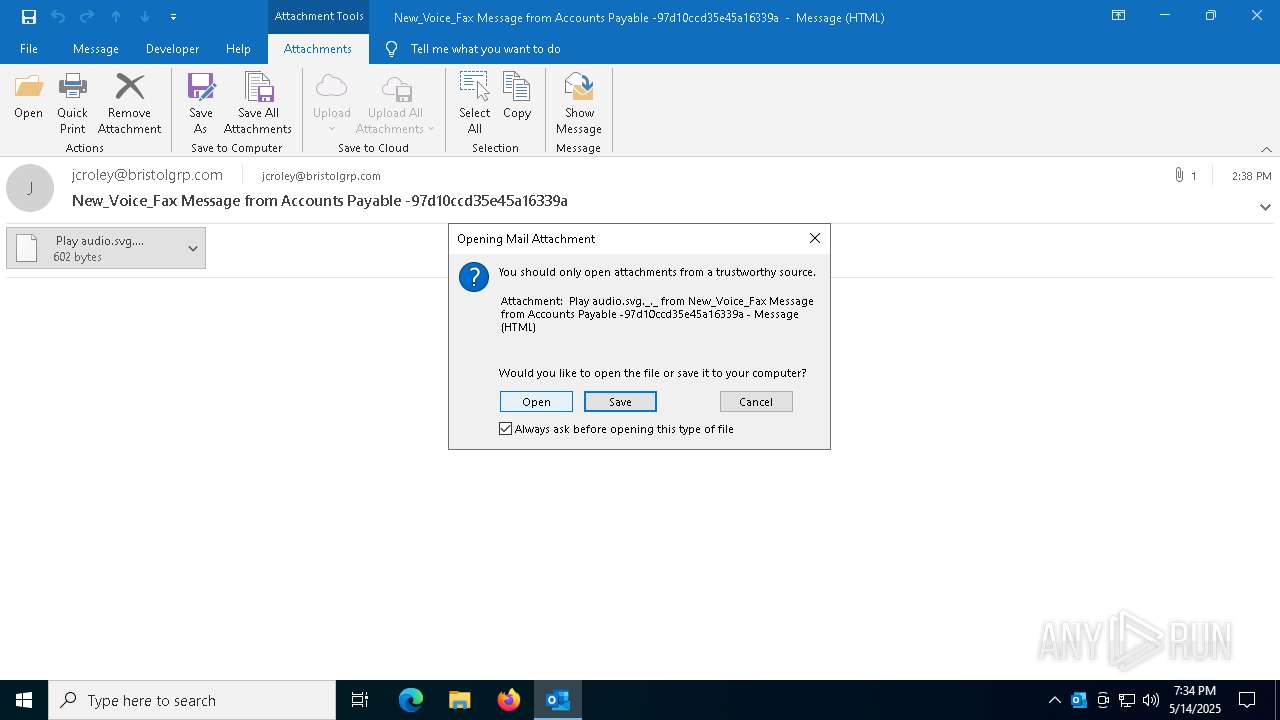
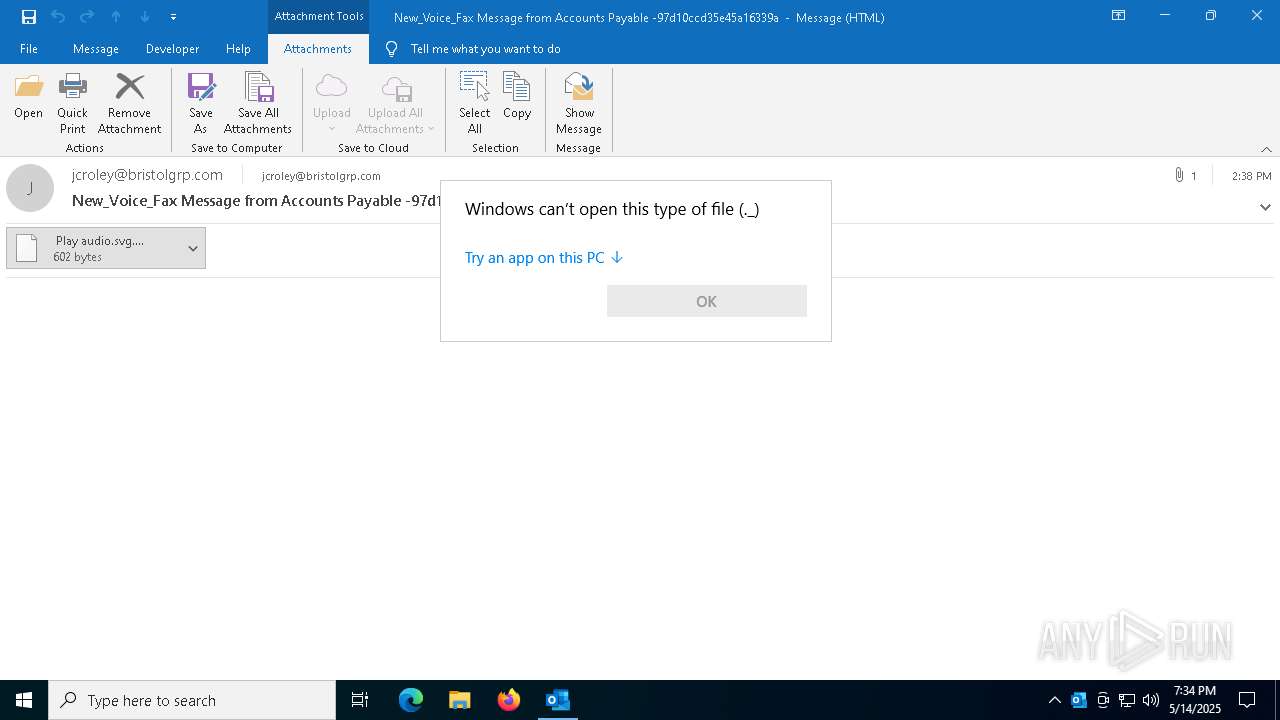
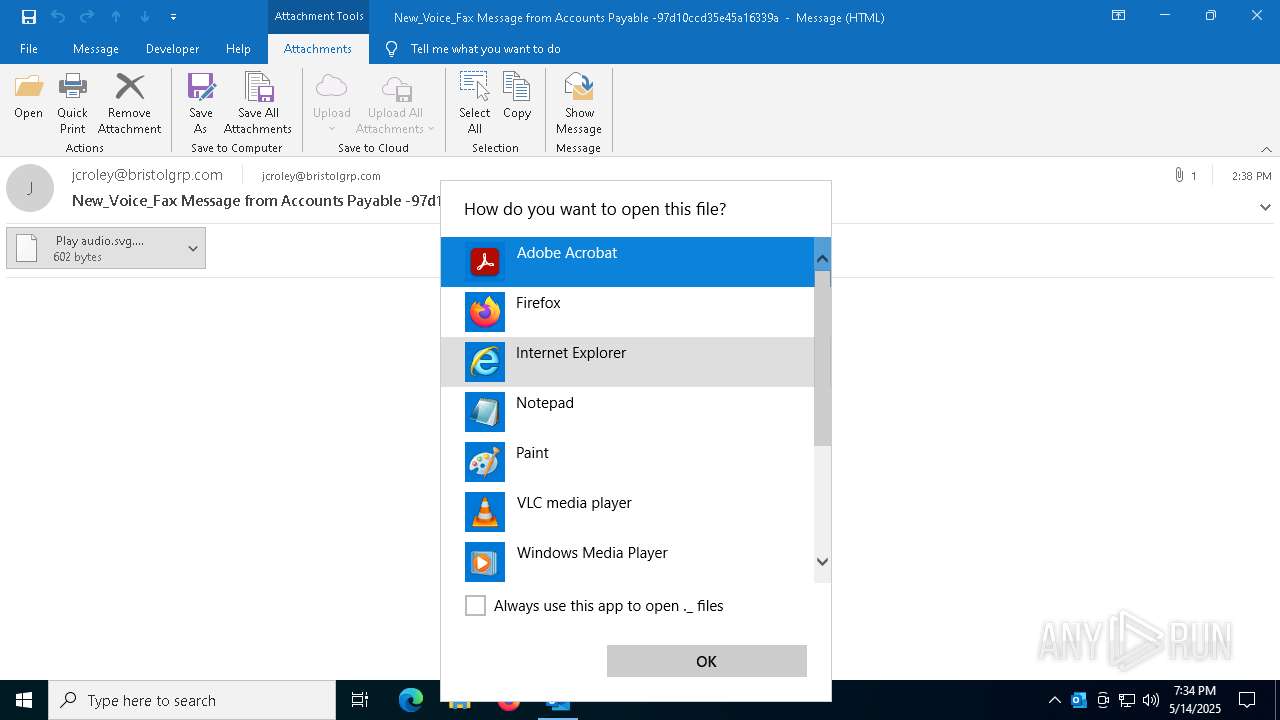
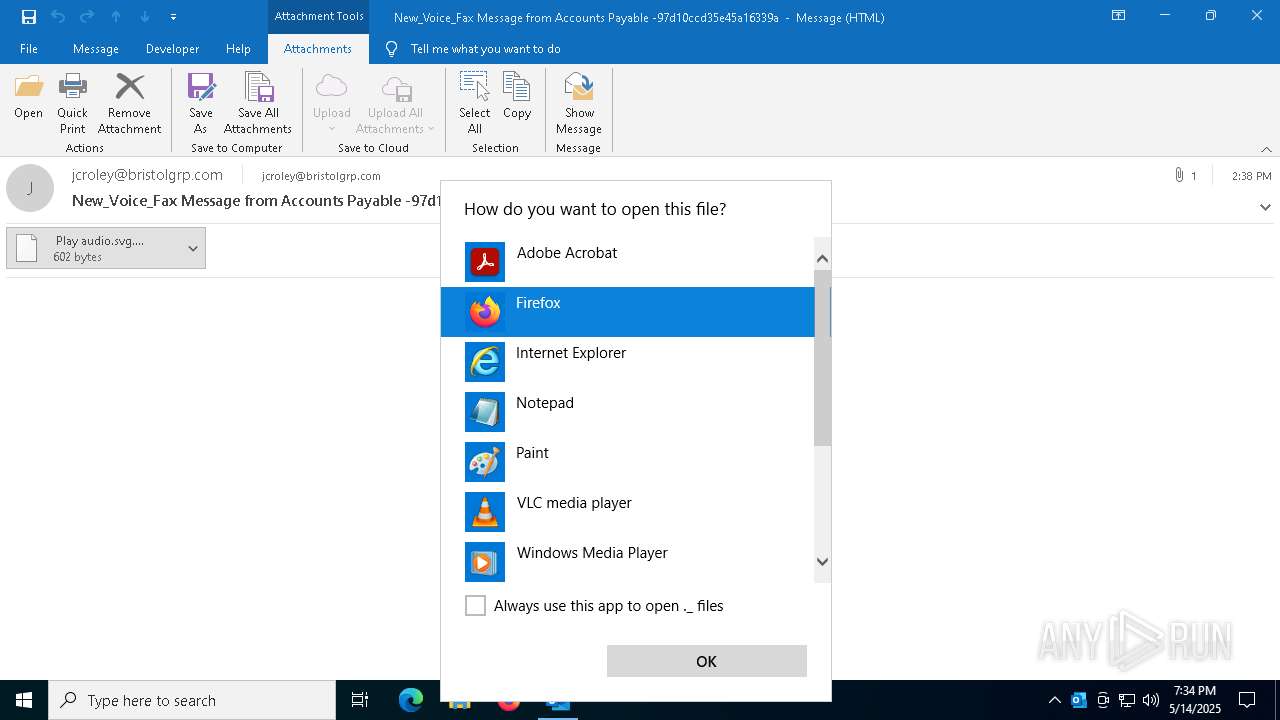
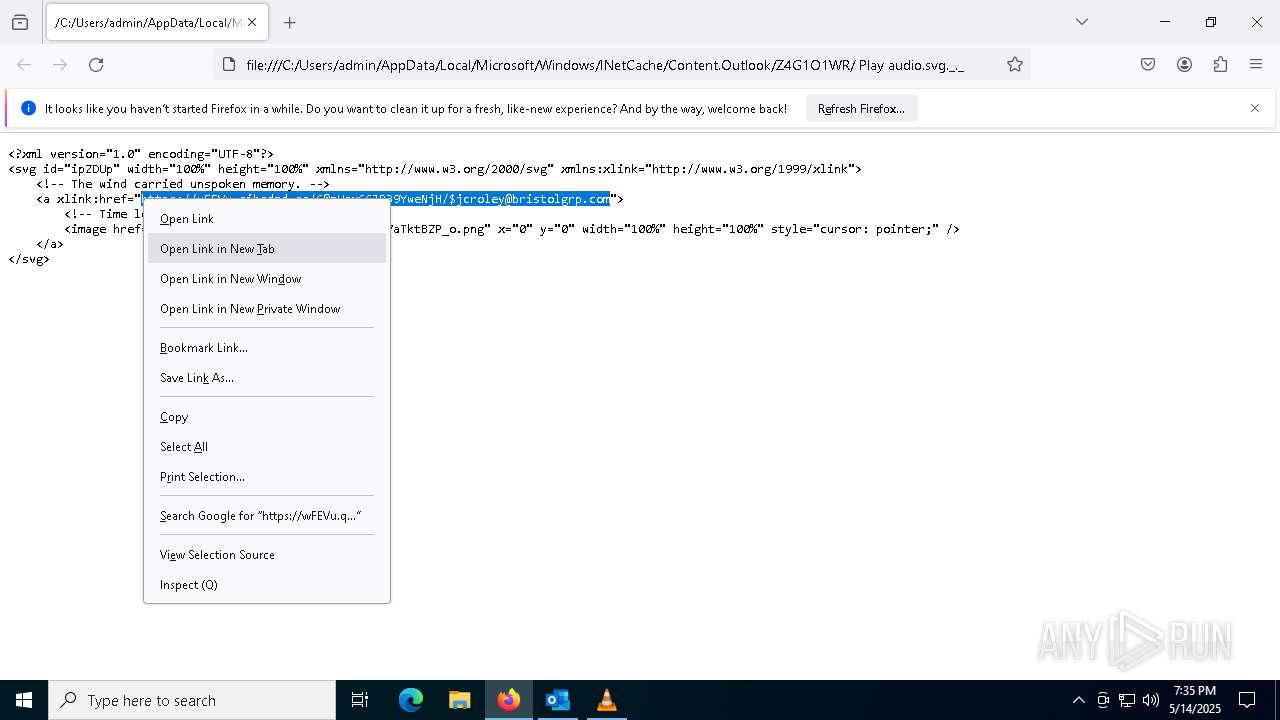
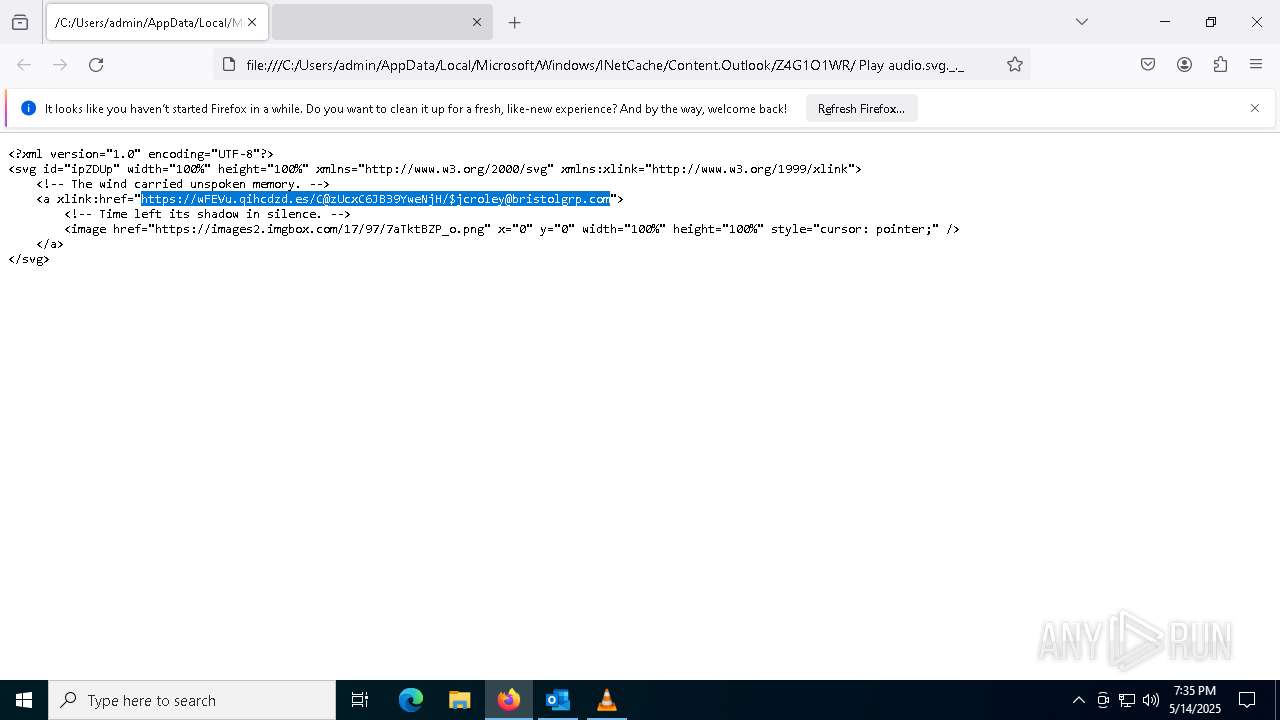
| 4428 | "C:\Program Files\Mozilla Firefox\firefox.exe" -osint -url "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\Z4G1O1WR\ Play audio.svg._._" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5008 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2144 -parentBuildID 20240213221259 -prefsHandle 2136 -prefMapHandle 2124 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {51a81c68-55ea-4258-8042-613fca017e66} 4428 "\\.\pipe\gecko-crash-server-pipe.4428" 20957884110 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5072 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\New_Voice_Fax Message from Accounts Payable -97d10ccd35e45a16339a.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5232 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2260 -childID 7 -isForBrowser -prefsHandle 2300 -prefMapHandle 5808 -prefsLen 31555 -prefMapSize 244583 -jsInitHandle 1492 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {75aa3eb6-a1ad-4e0d-8add-0c53c2bf9b49} 4428 "\\.\pipe\gecko-crash-server-pipe.4428" 2096f0df150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5868 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
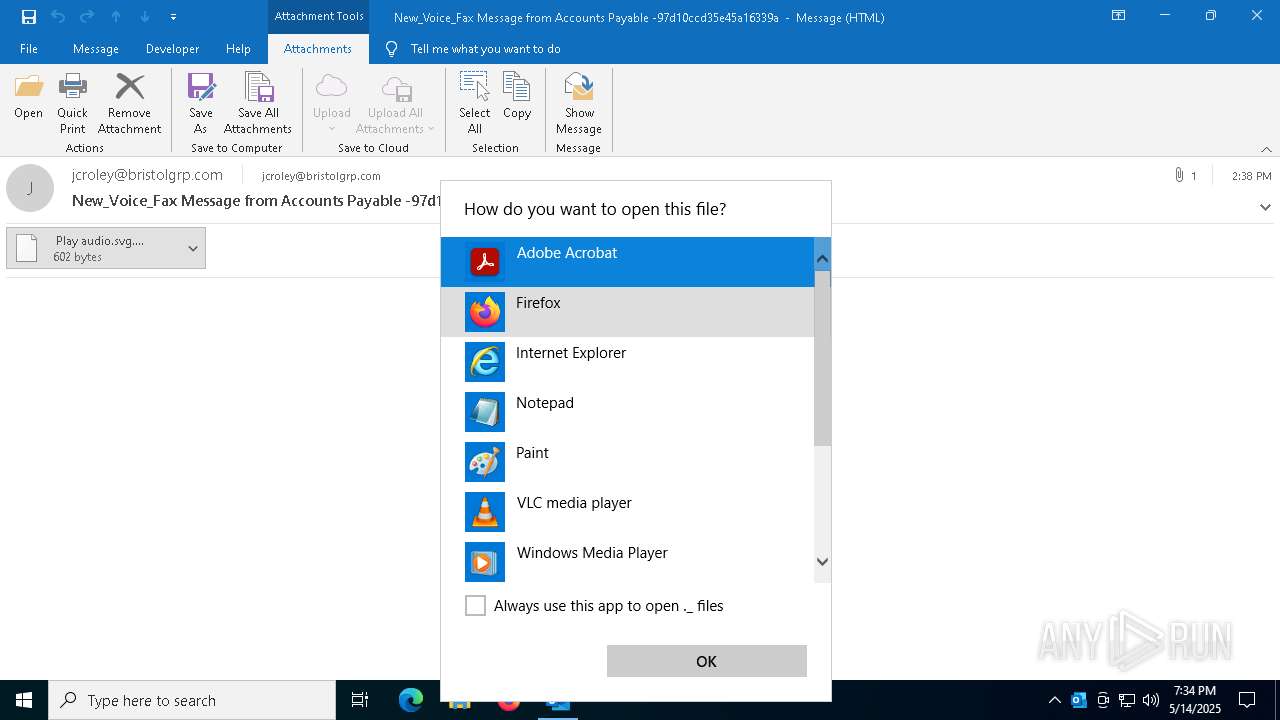
| 6456 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\Z4G1O1WR\ Play audio.svg._._" | C:\Program Files\VideoLAN\VLC\vlc.exe | — | OpenWith.exe | |||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Version: 3.0.11 Modules
| |||||||||||||||
Total events
29 642
Read events
28 398
Write events
1 089
Delete events
155
Modification events
| (PID) Process: | (5072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | -:* |
Value: 2D3A2A00D013000004000000000000009601582807C5DB0196000000010000008E000000430043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C0045006D00610069006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (5072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete value | Name: | -:* |
Value: 㨭*Ꮠ | |||
| (PID) Process: | (5072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete value | Name: | 2'* |
Value: ✲*Ꮠ | |||
| (PID) Process: | (5072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (5072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\5072 |
| Operation: | write | Name: | 0 |
Value: 0B0E10361AAD2E7356294194CCF7AD595BF742230046EF9EE1A8F2A0F1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511D027D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (5072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (5072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
4
Suspicious files
167
Text files
31
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5072 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 4428 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 5072 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:3DEF188D0F008F68A2627803A0737A12 | SHA256:BFBA2DA9FBEB62A930122A77827EB97EB0D48078727BA19F55158564344CBBDB | |||
| 5072 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:8268898AFA791EE6FEC1DC4958A91849 | SHA256:86EEE3372BA1DFA88DCC70ACD26971EFBC8AC7DE87499466E778843C90A43E21 | |||
| 5072 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\Z4G1O1WR\ Play audio.svg._ (002)._ | xml | |
MD5:6DB8A8D9CD8394B77BBD4B5539B72060 | SHA256:9F87E9603DD812F6CB3549B194AC8CFE6D0A5487B320563090D1145A55271340 | |||
| 5072 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\FE6EFE48-72A1-4891-B0AF-9419193A66D8 | xml | |
MD5:83D83F9E3C5024DB4F17904E39B3E2EE | SHA256:71D2483F33FE1D9EDEE73911CD29D71E62361ACBD03579CC1C48C9280EF91181 | |||
| 4428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:A09DCB8A08224209F528AED7224B551B | SHA256:026CDF37925D931CF5627D69F637B380284A69D935CC09A92151C17B78A9D94F | |||
| 5072 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_B9920D9307CD3843B518F2B94D0A7E0E.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
118
DNS requests
153
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5072 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7364 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4428 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
4428 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
4428 | firefox.exe | POST | 200 | 184.24.77.80:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4428 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
4428 | firefox.exe | POST | 200 | 184.24.77.80:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4428 | firefox.exe | POST | 200 | 184.24.77.77:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 2.18.121.147:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
2104 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5072 | OUTLOOK.EXE | 52.109.89.18:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5072 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5072 | OUTLOOK.EXE | 52.109.76.243:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5072 | OUTLOOK.EXE | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (siferhs .es) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (siferhs .es) |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (siferhs .es) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Address Lookup Domain (get .geojs .io) in DNS Lookup |