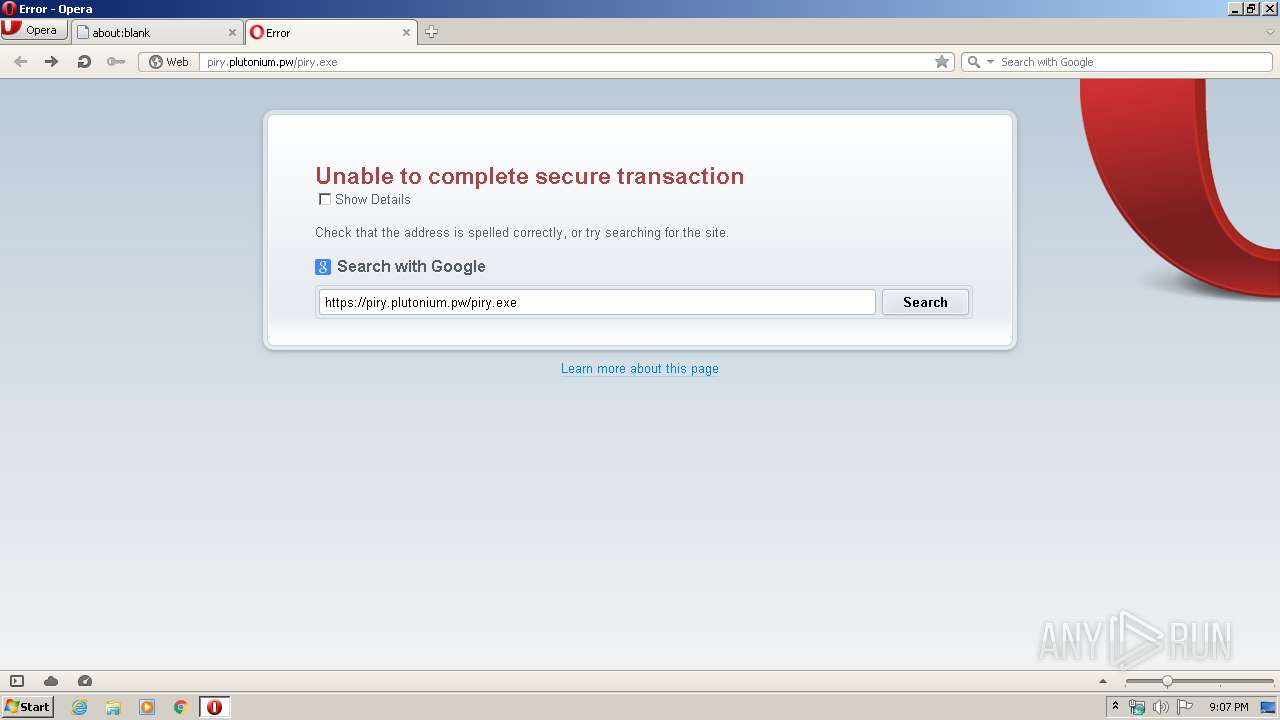
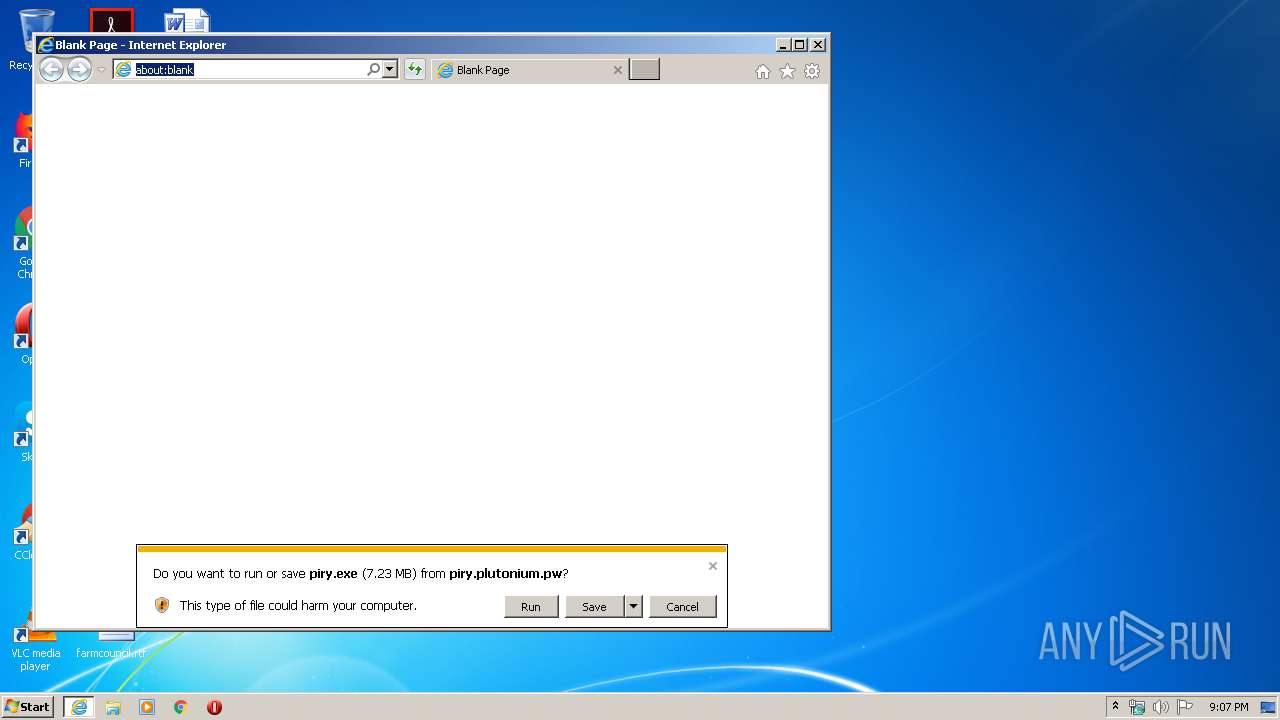
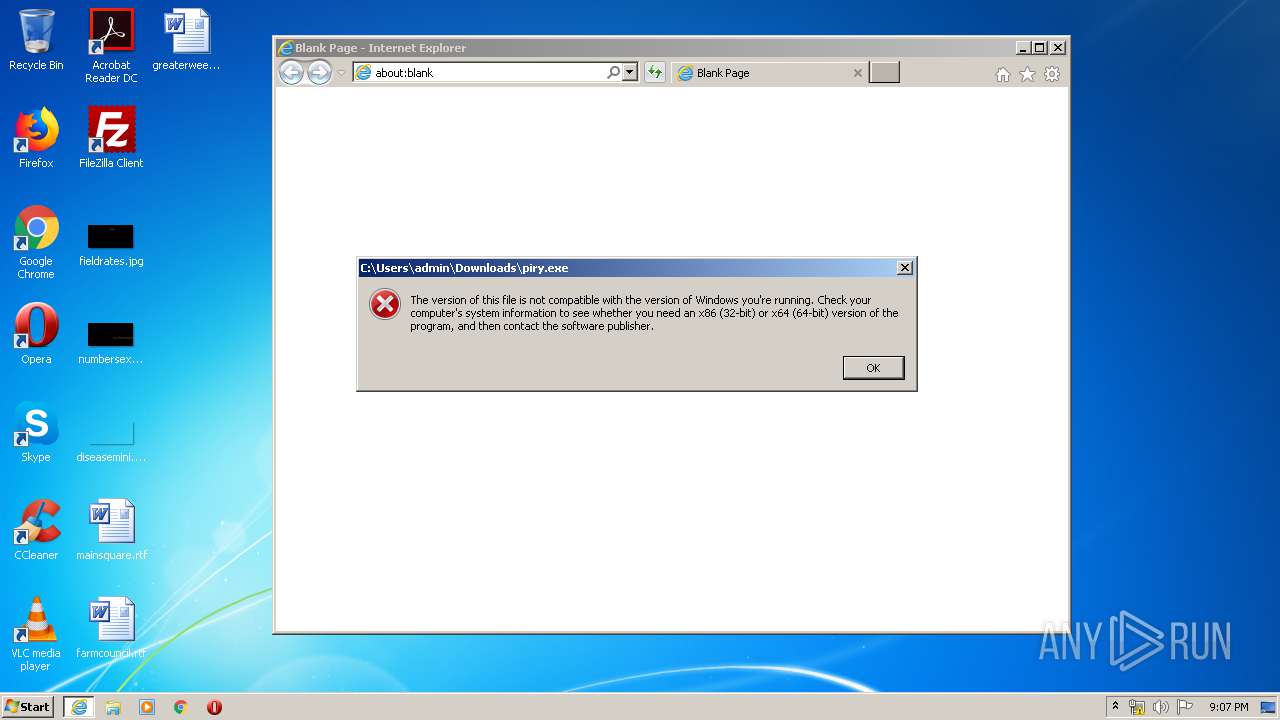
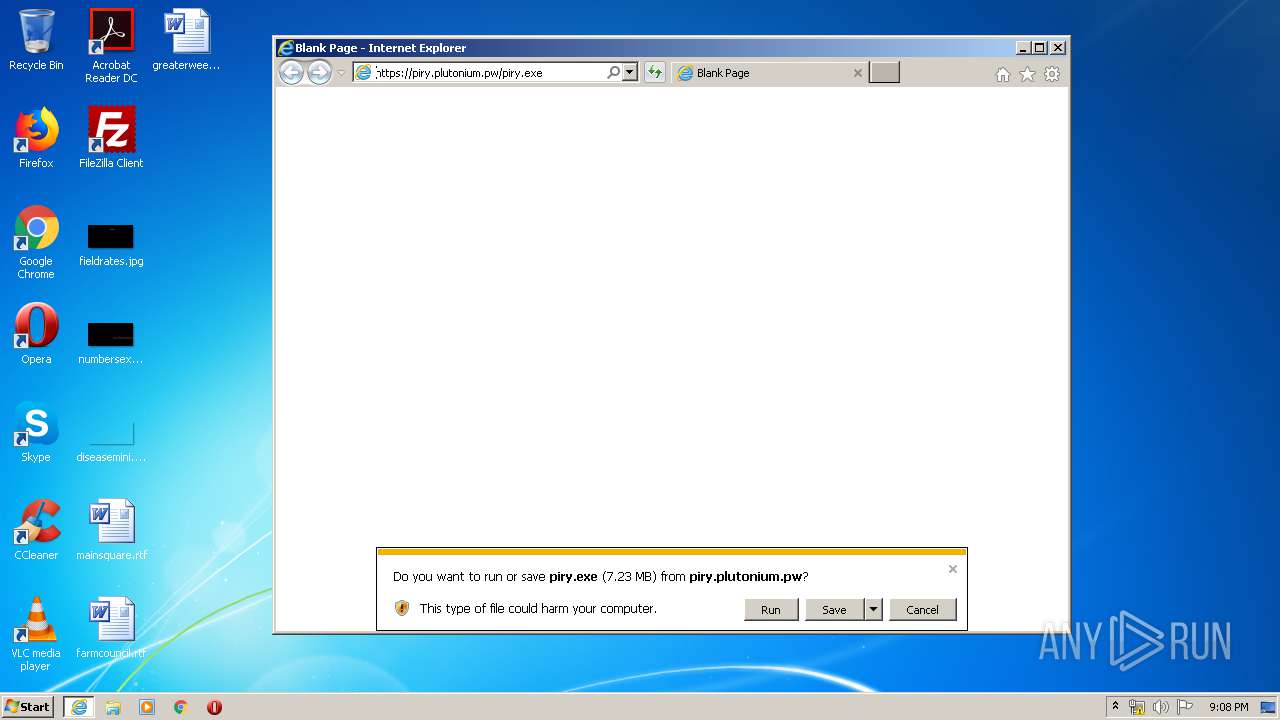
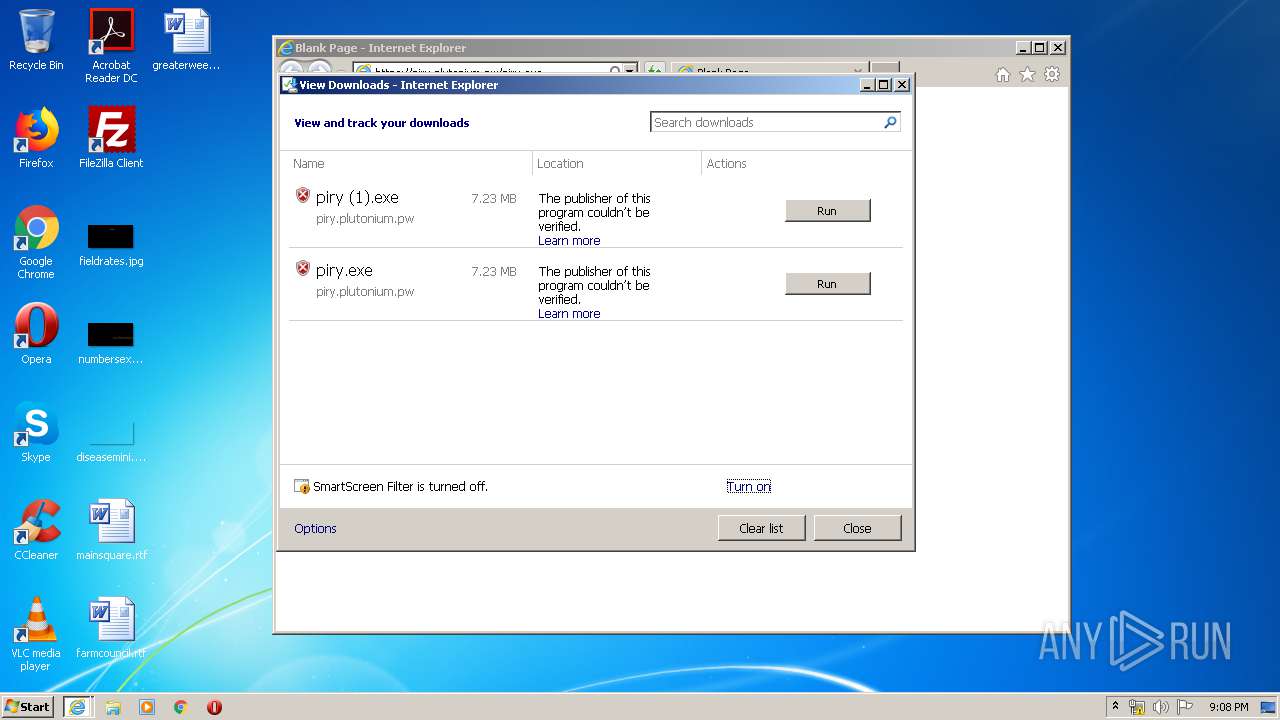
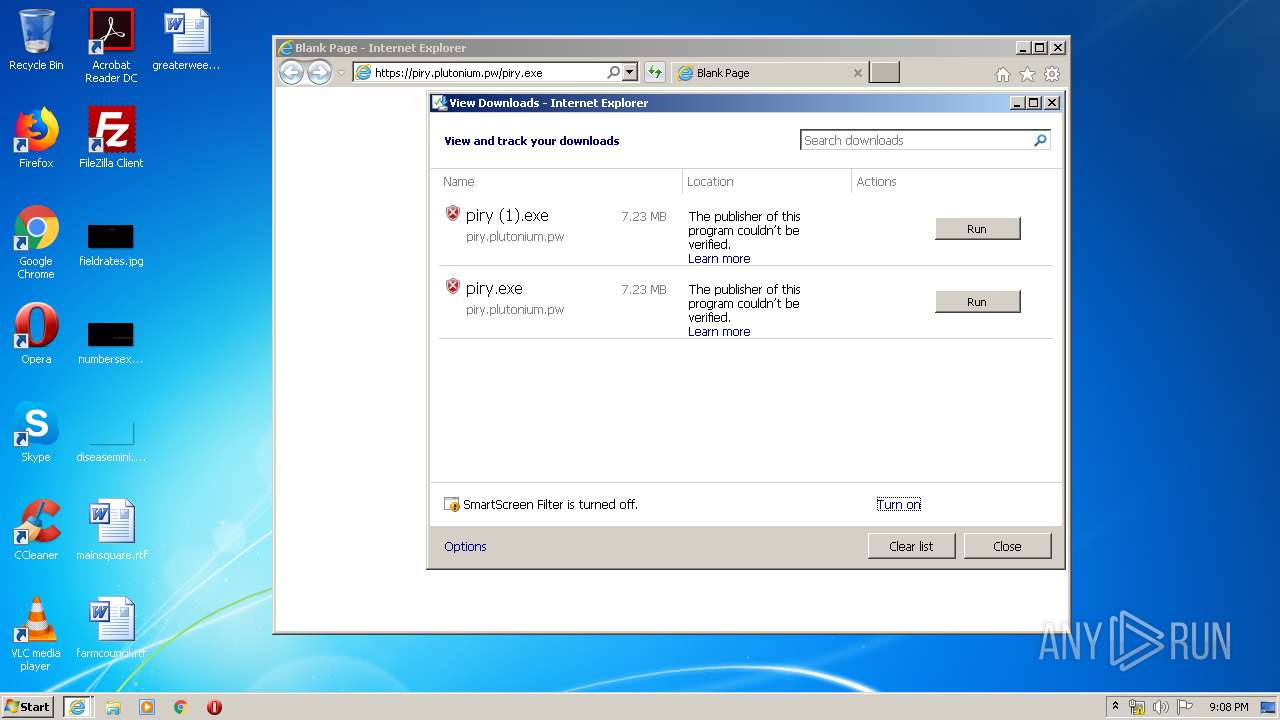
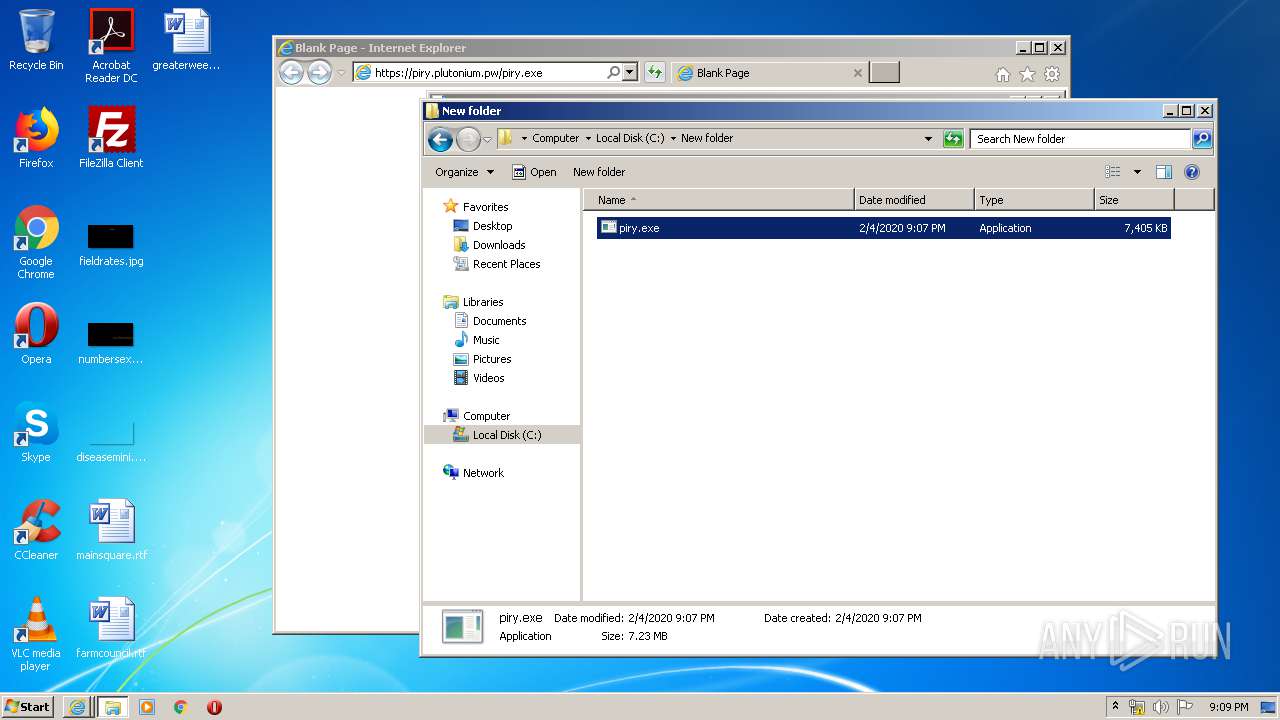
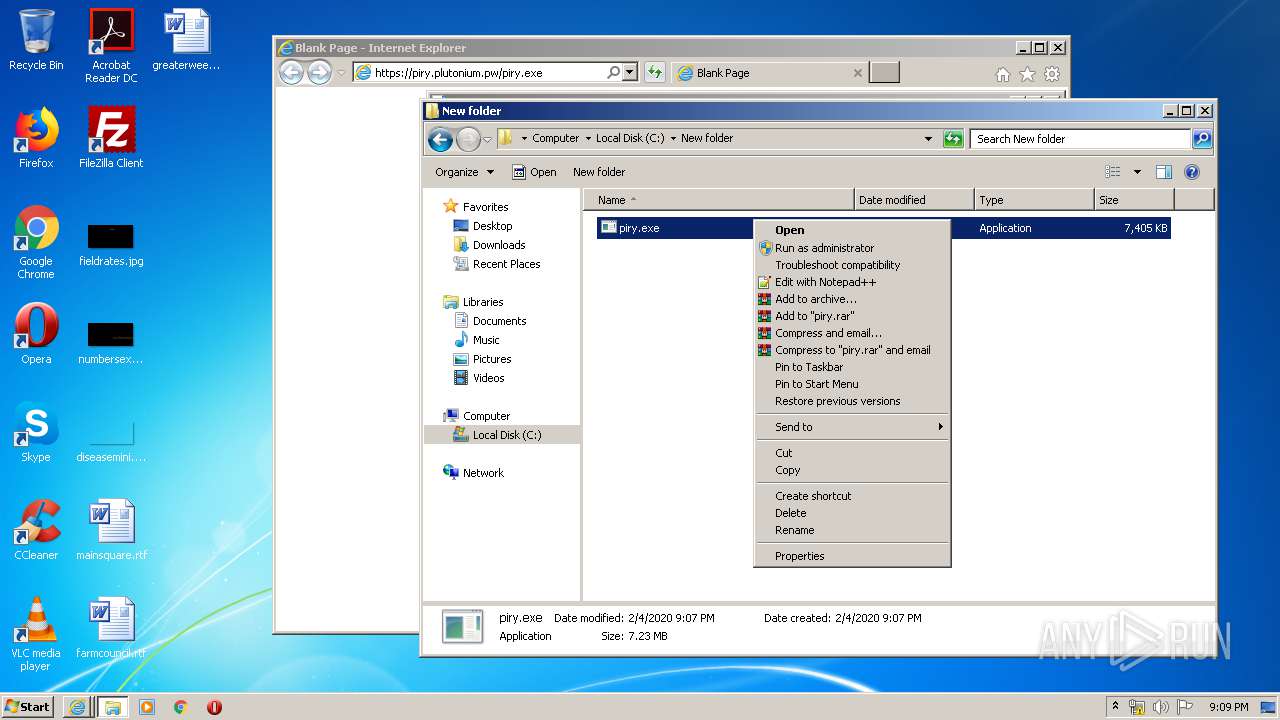
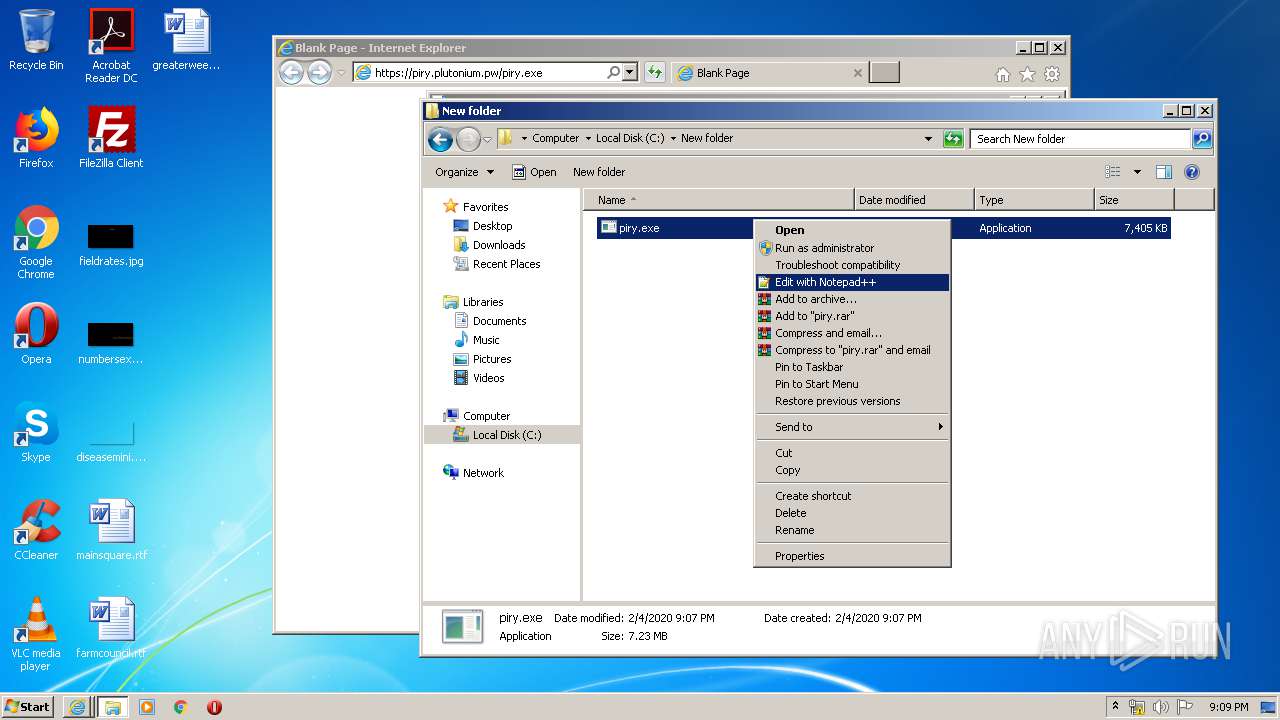
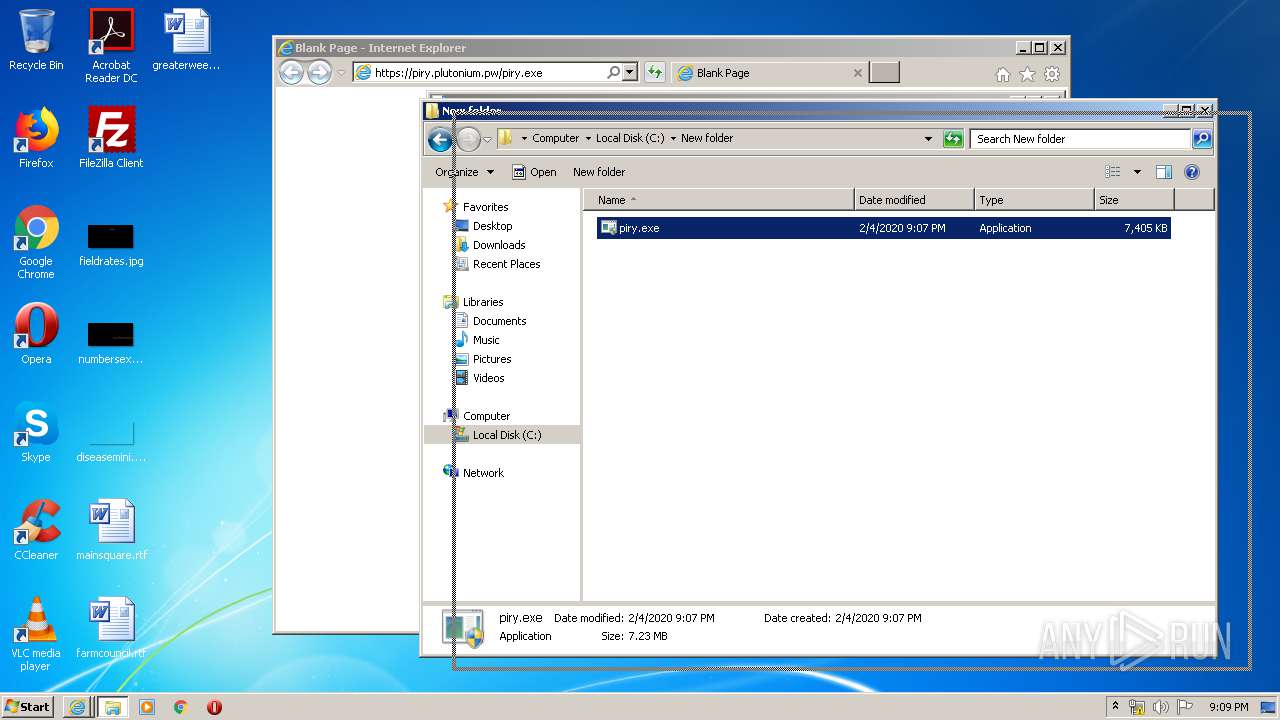
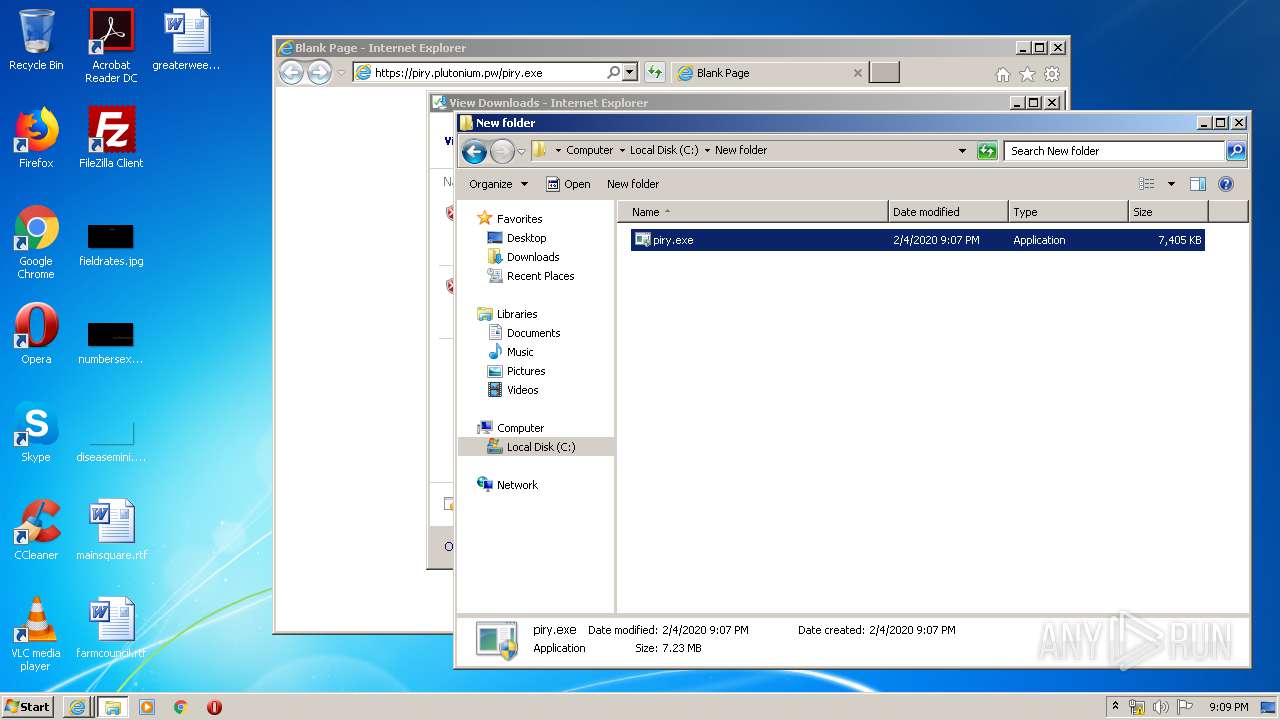
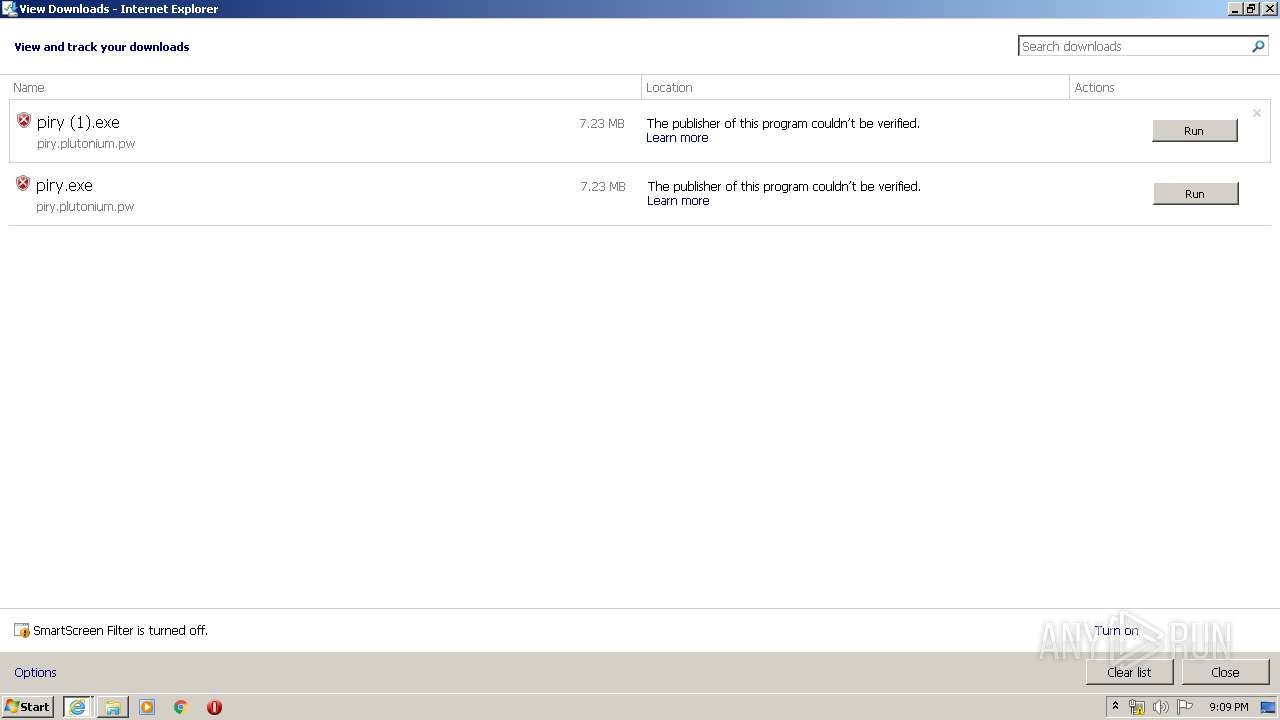
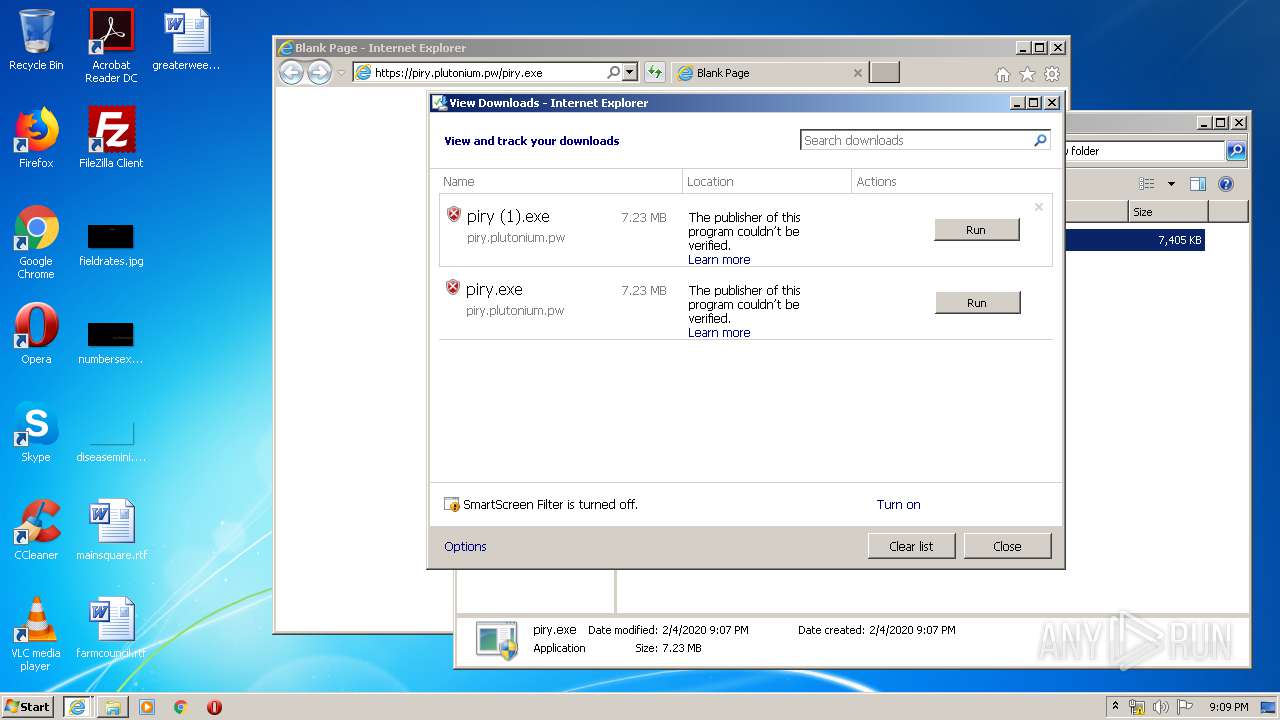
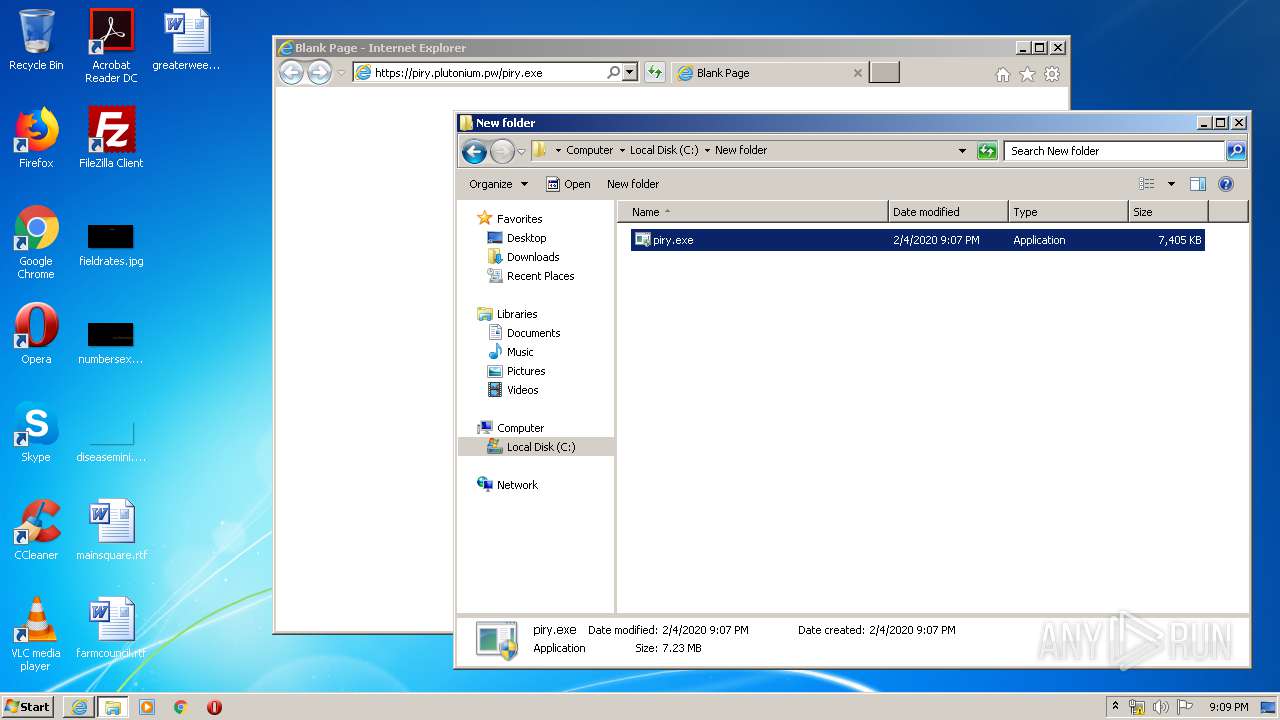
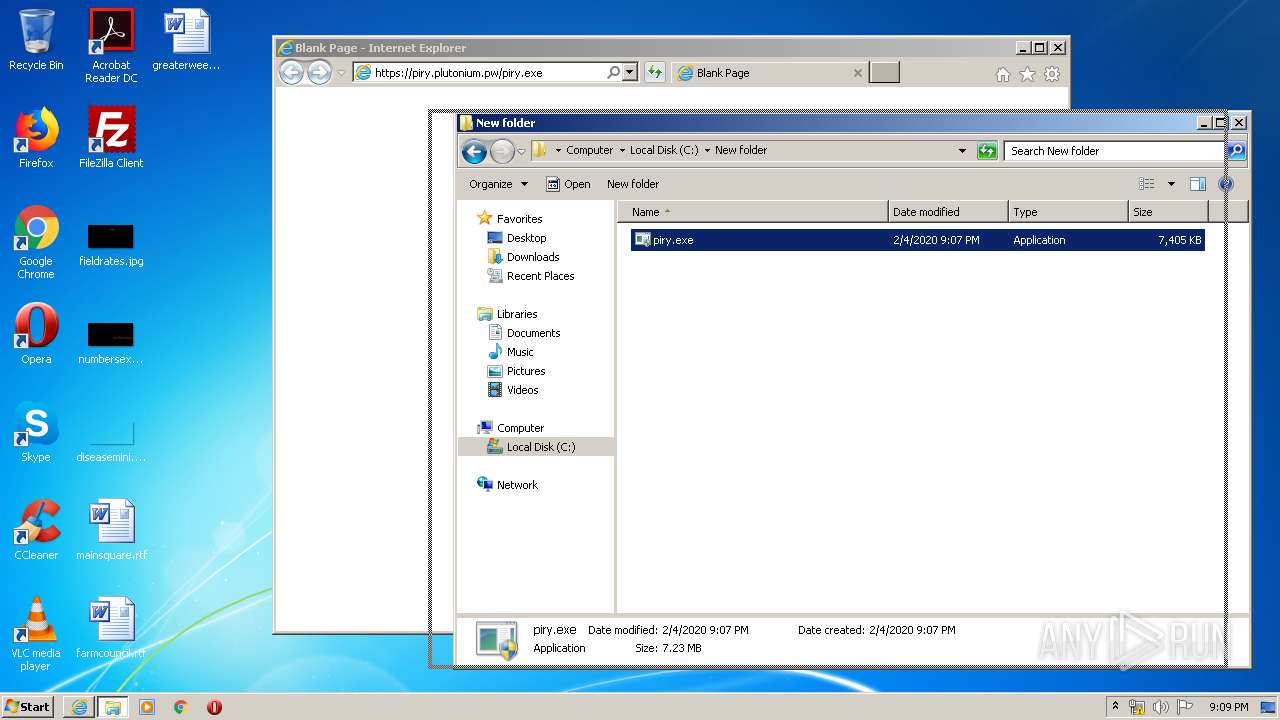
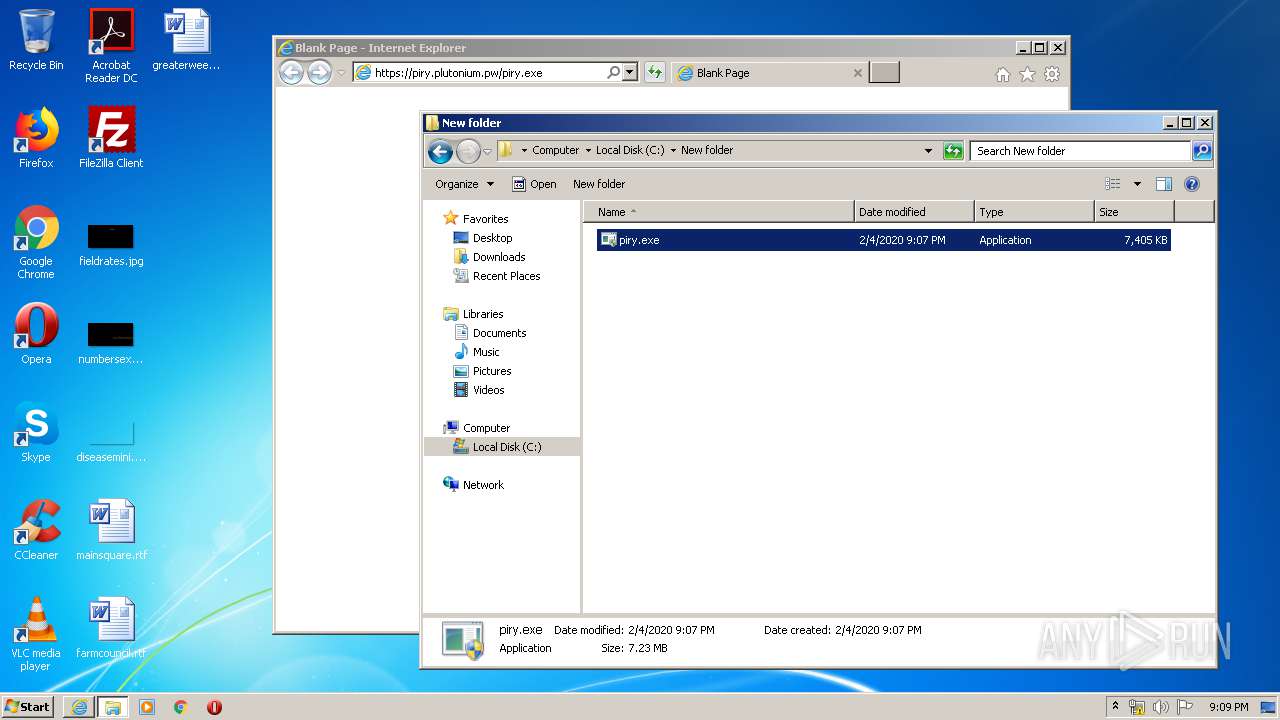
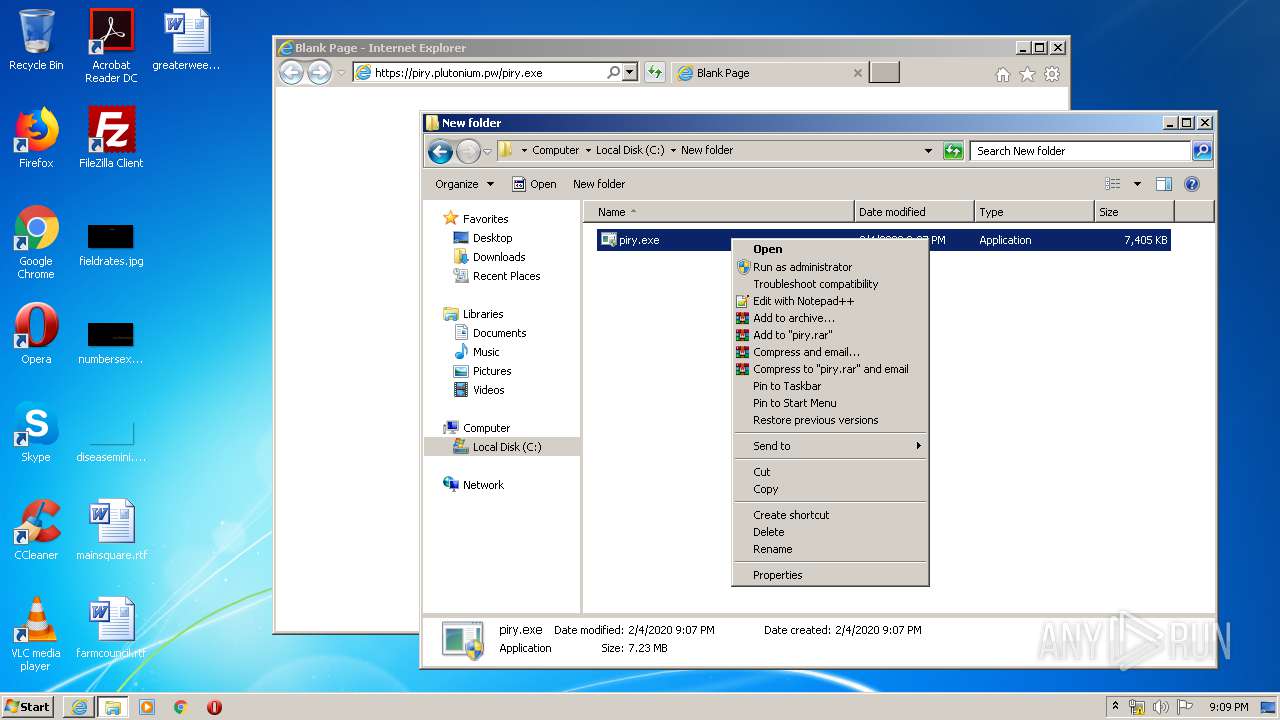
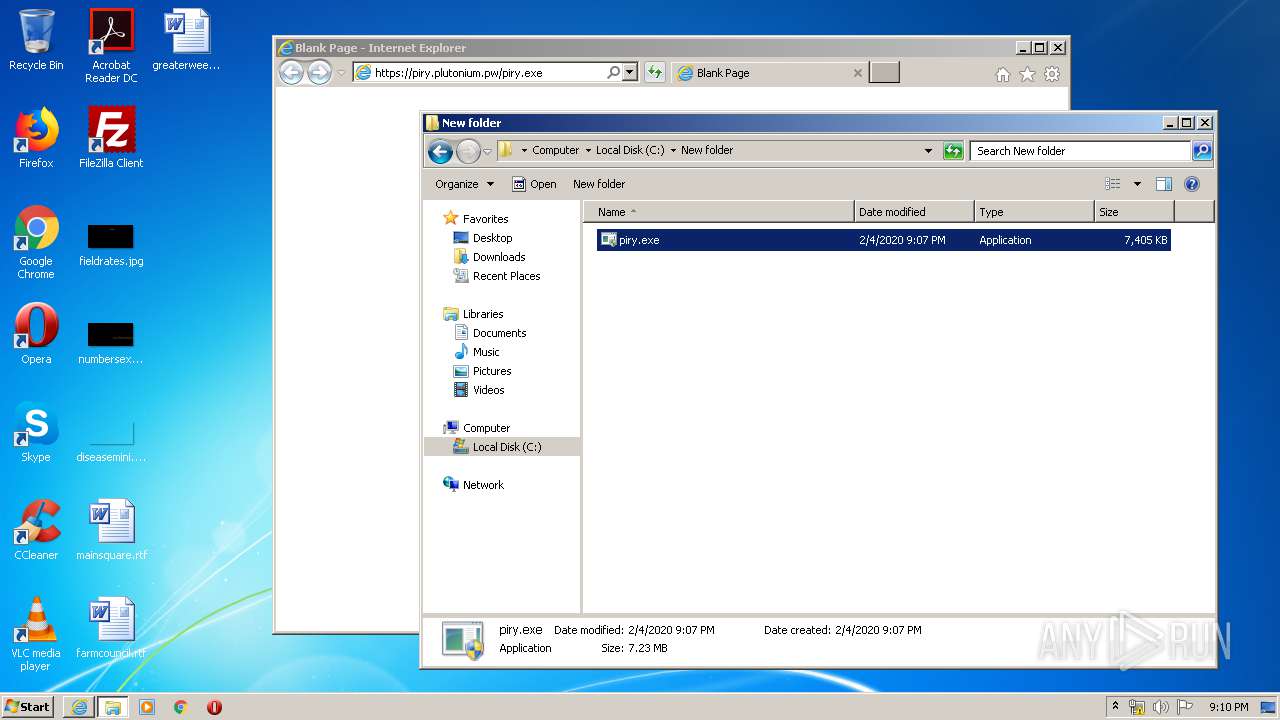
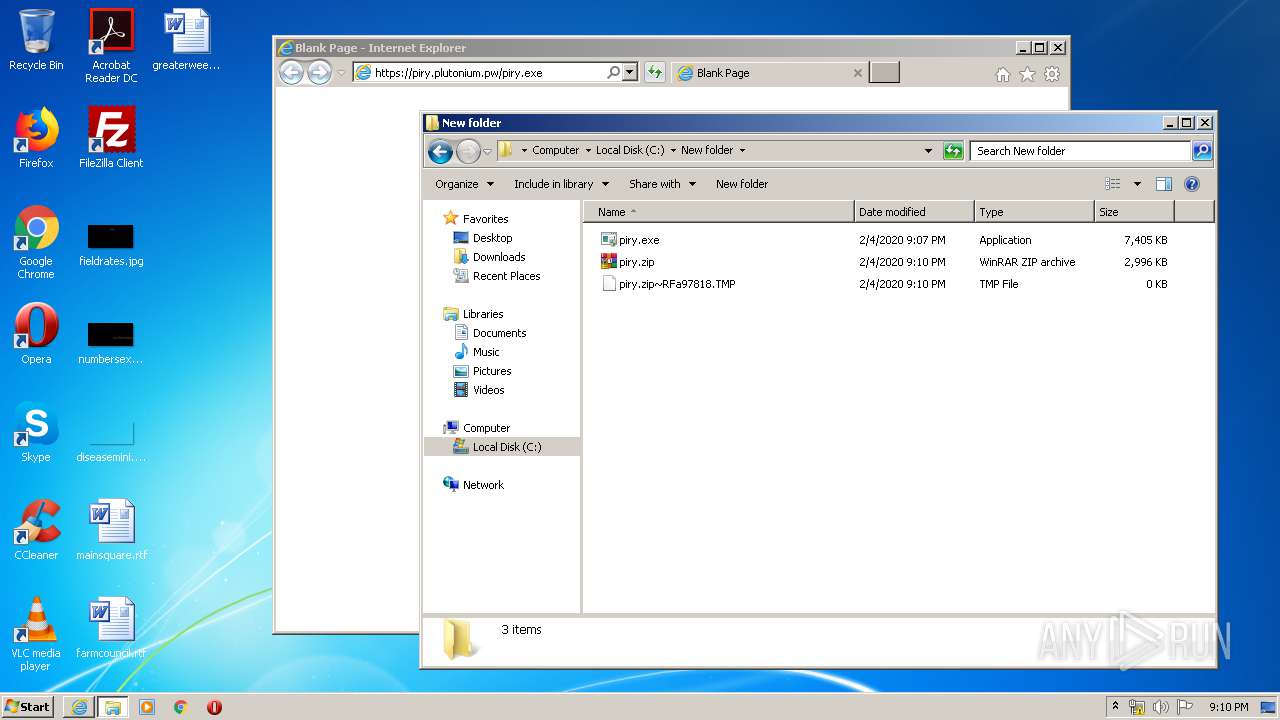
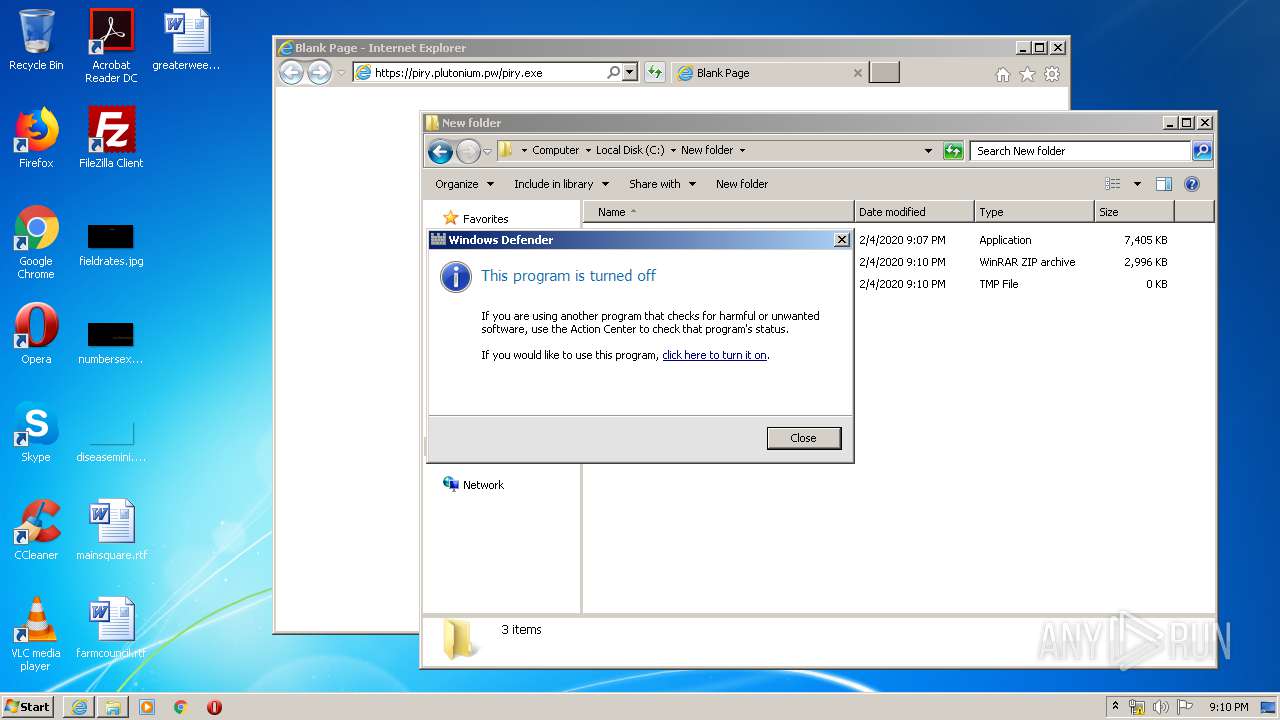
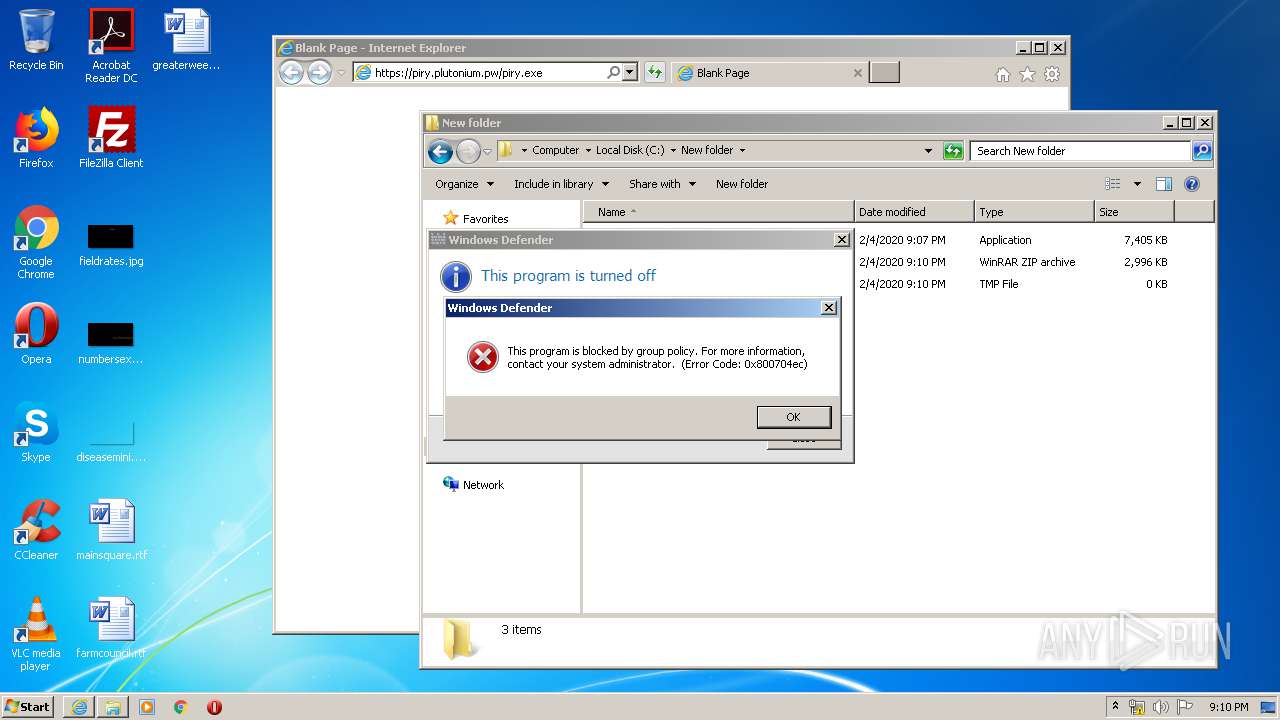
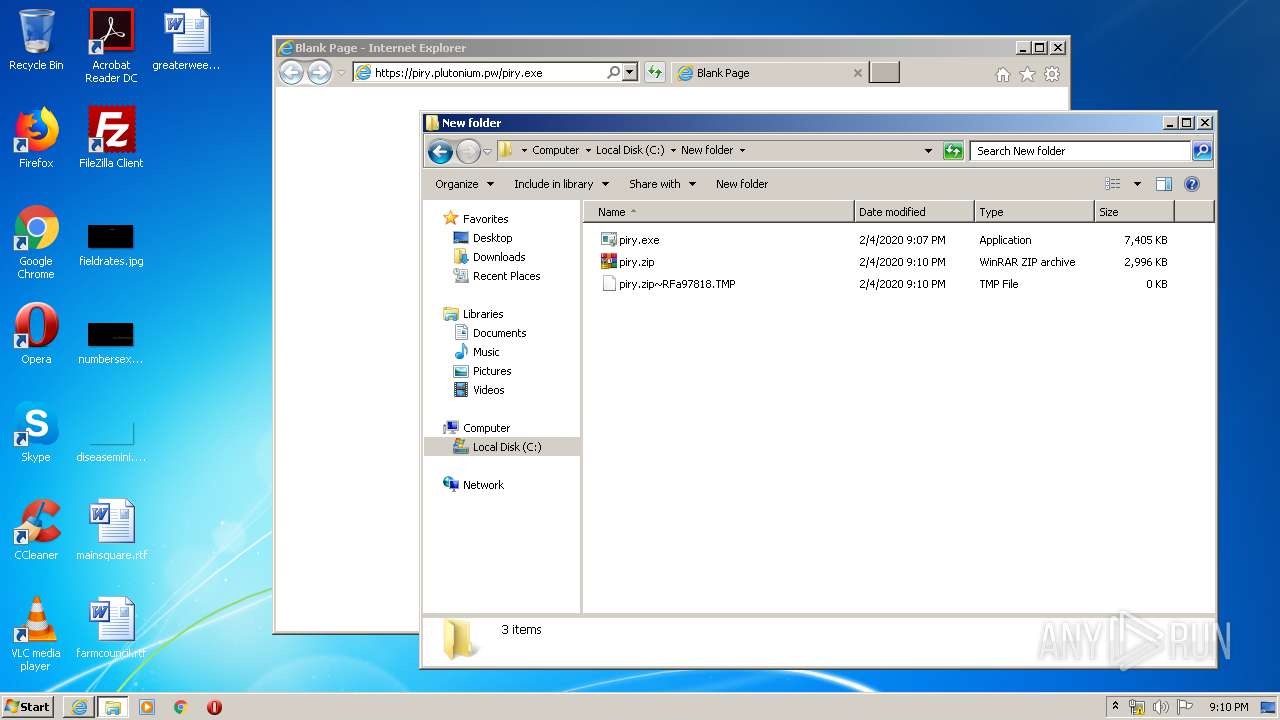
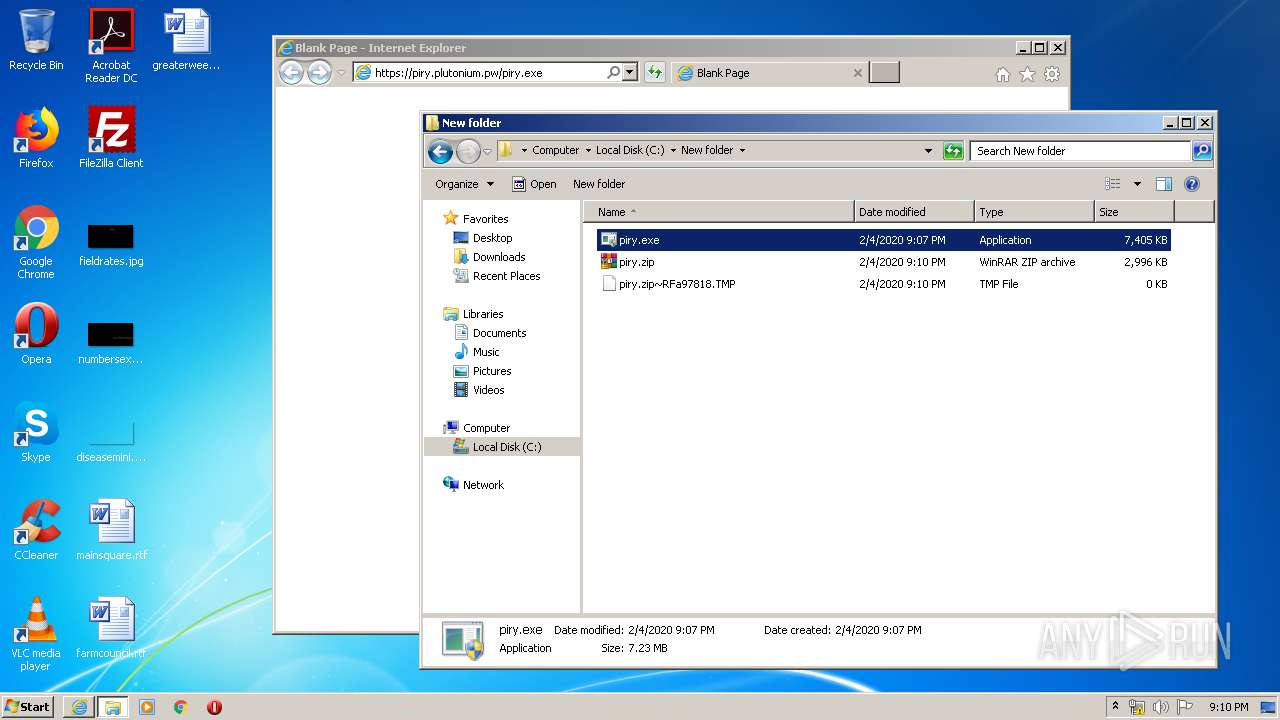
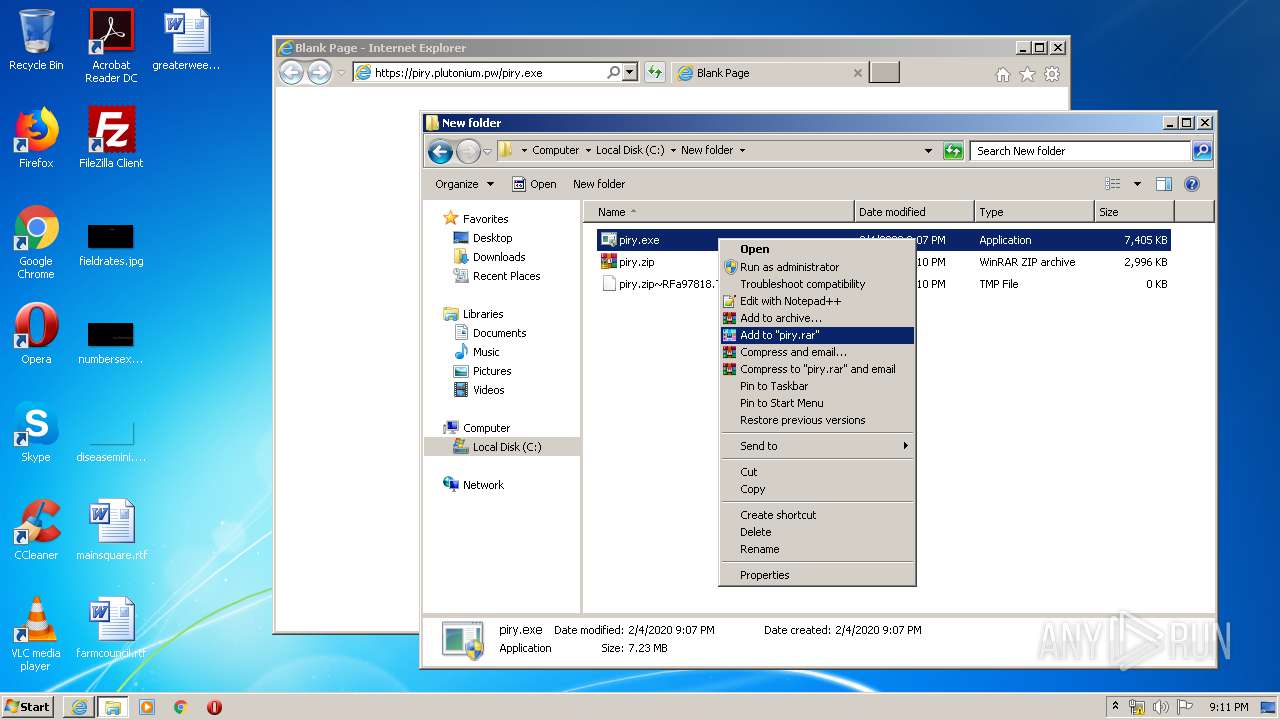
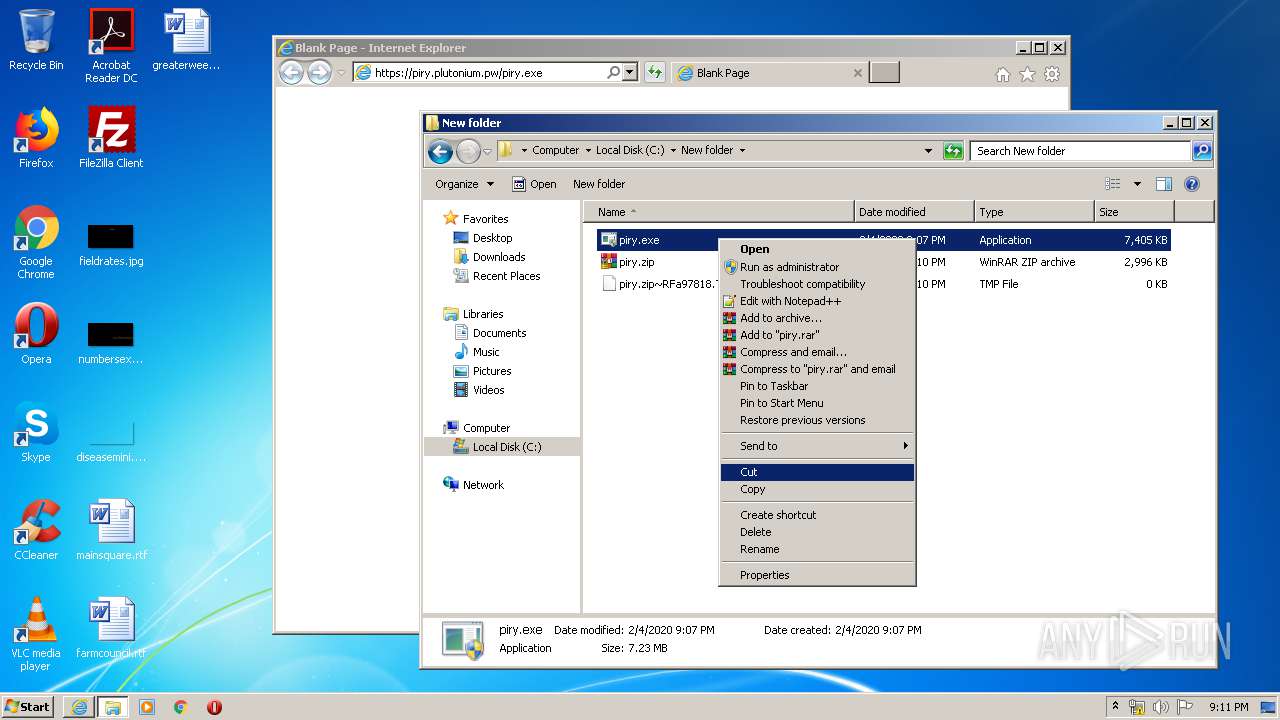
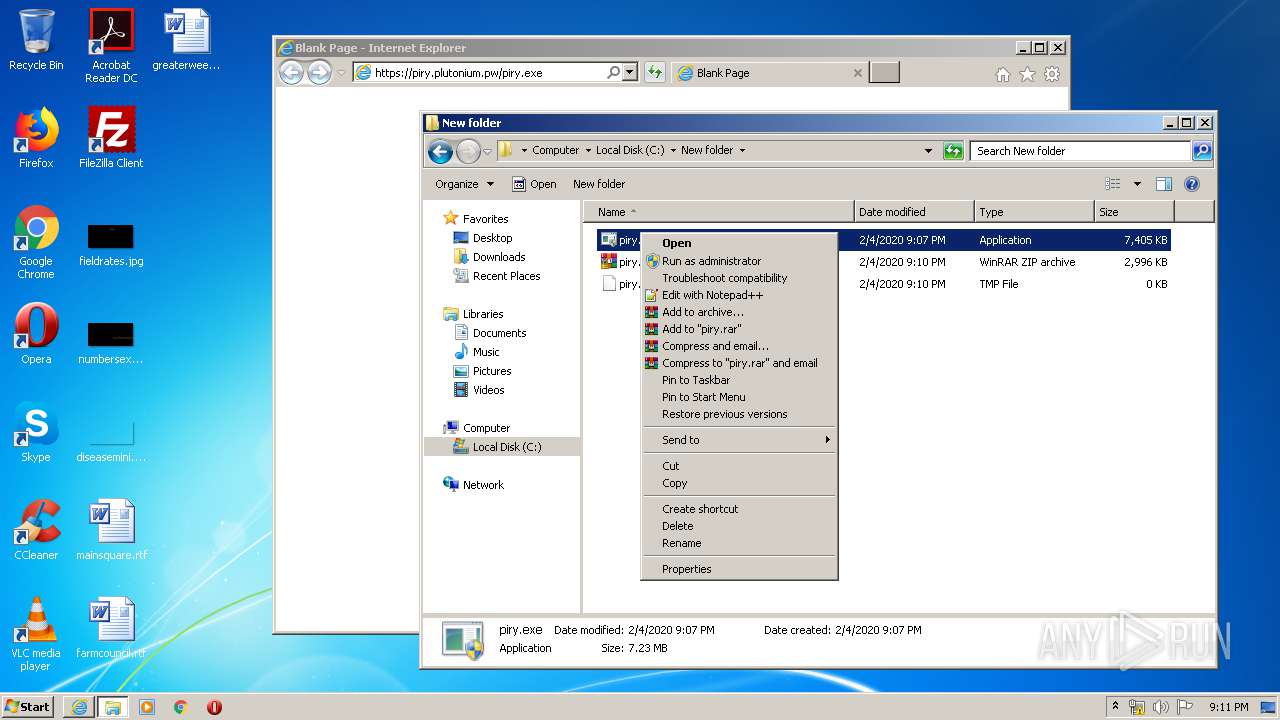
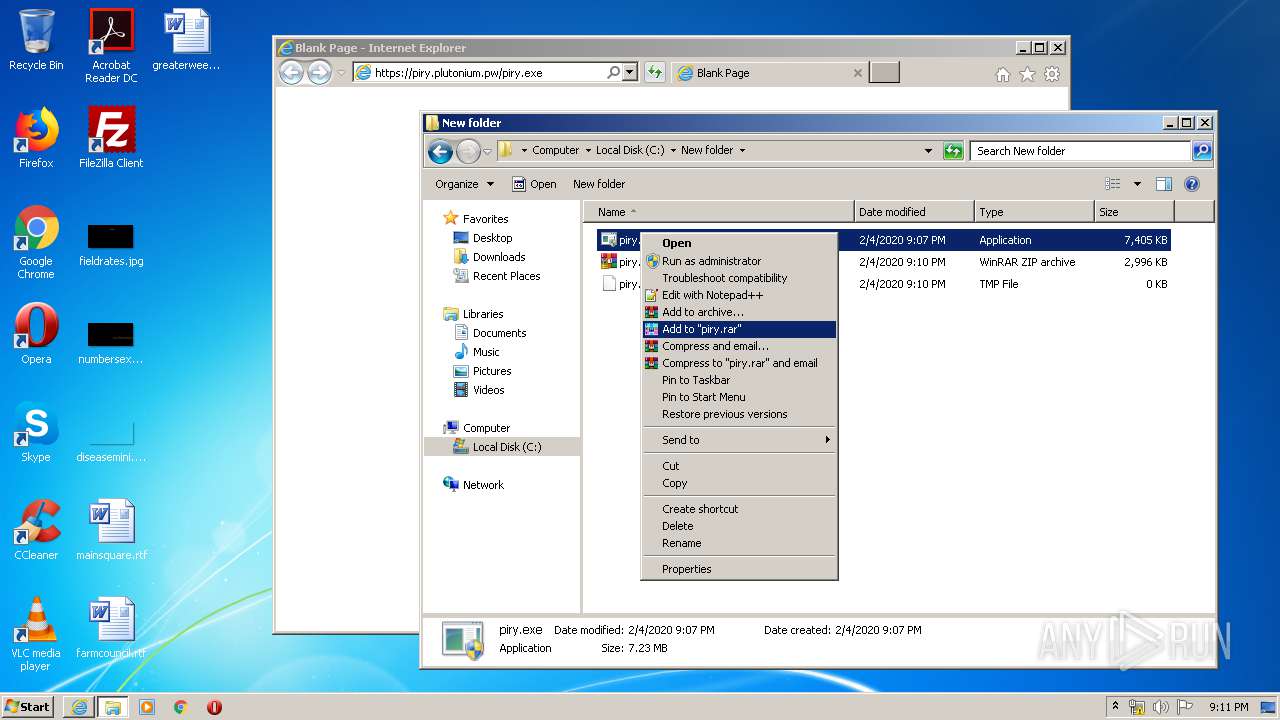
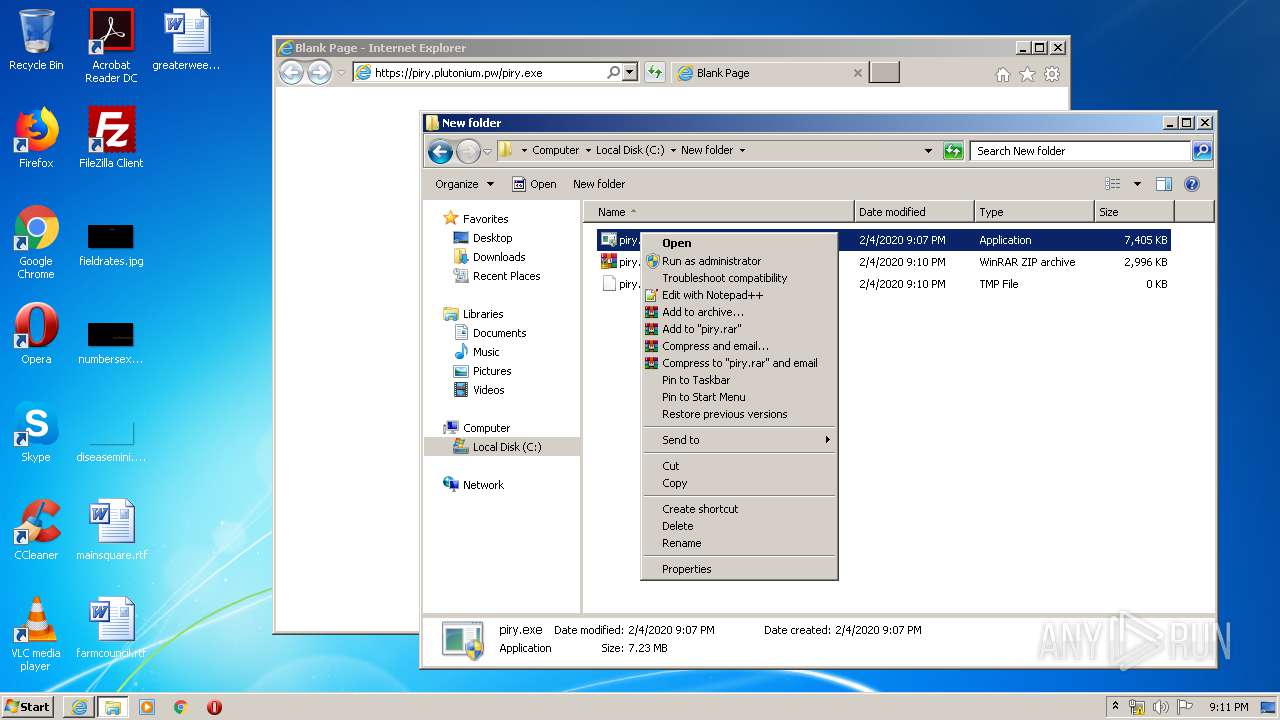
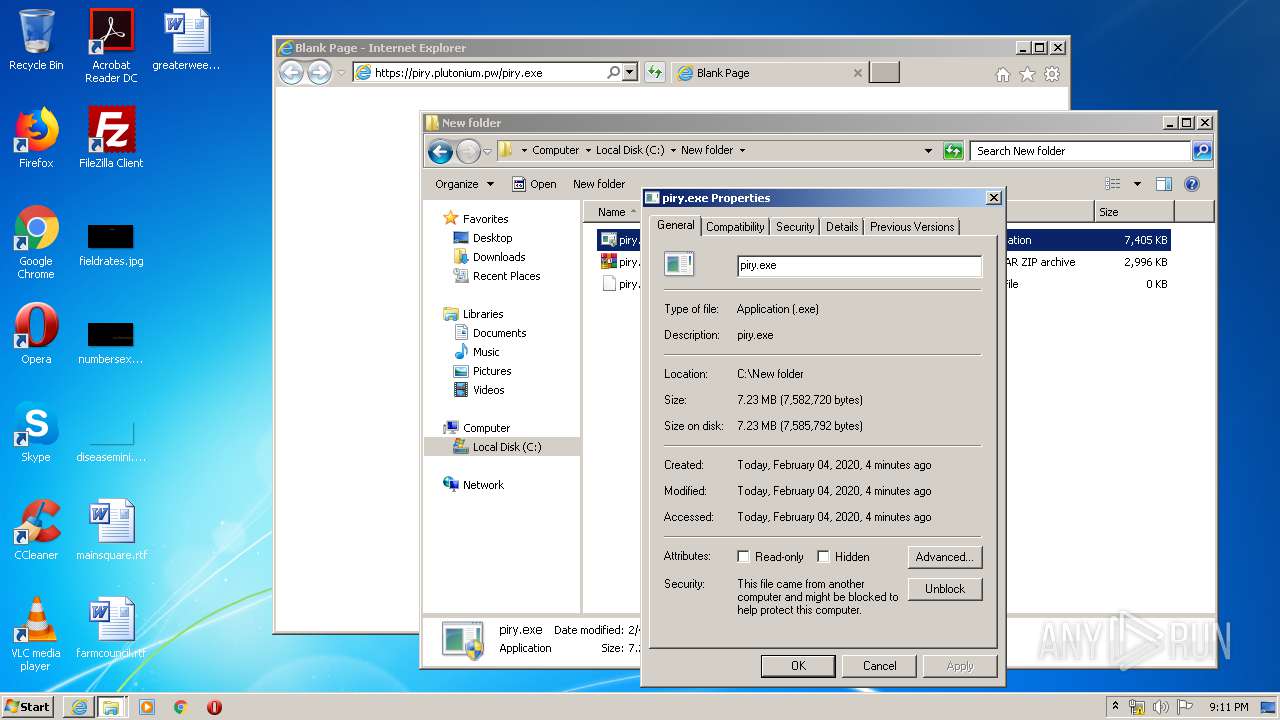
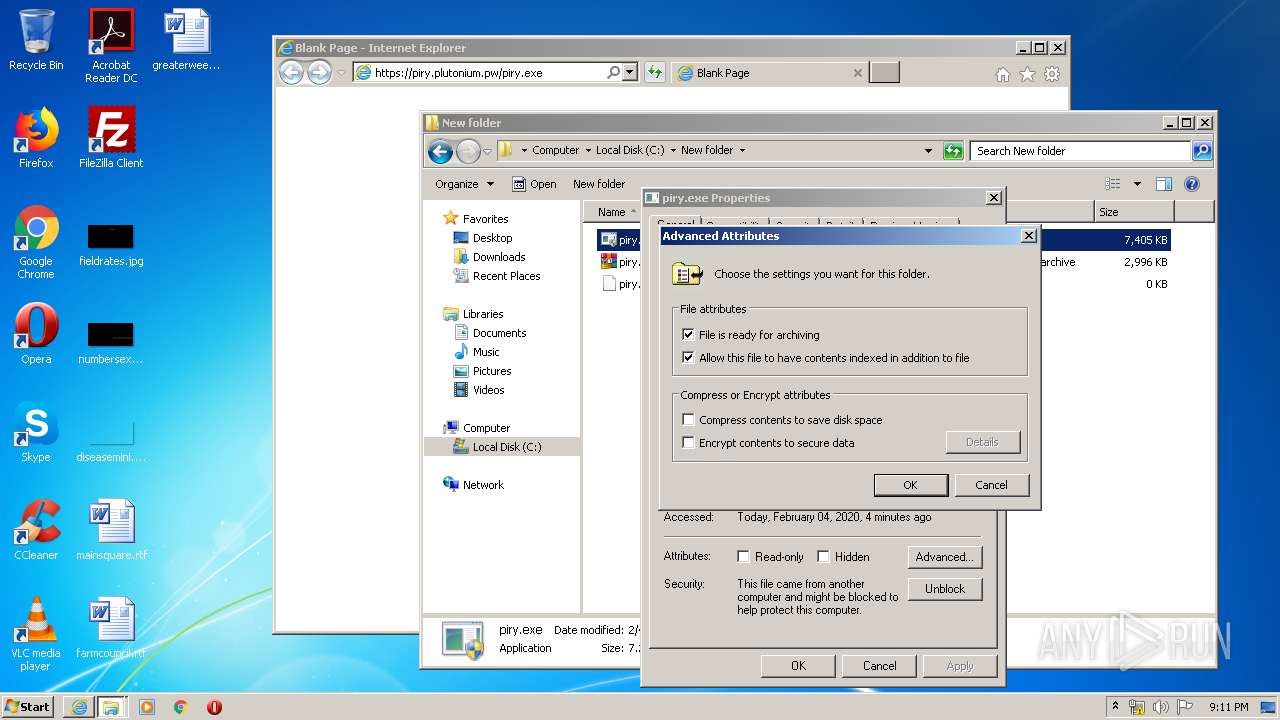
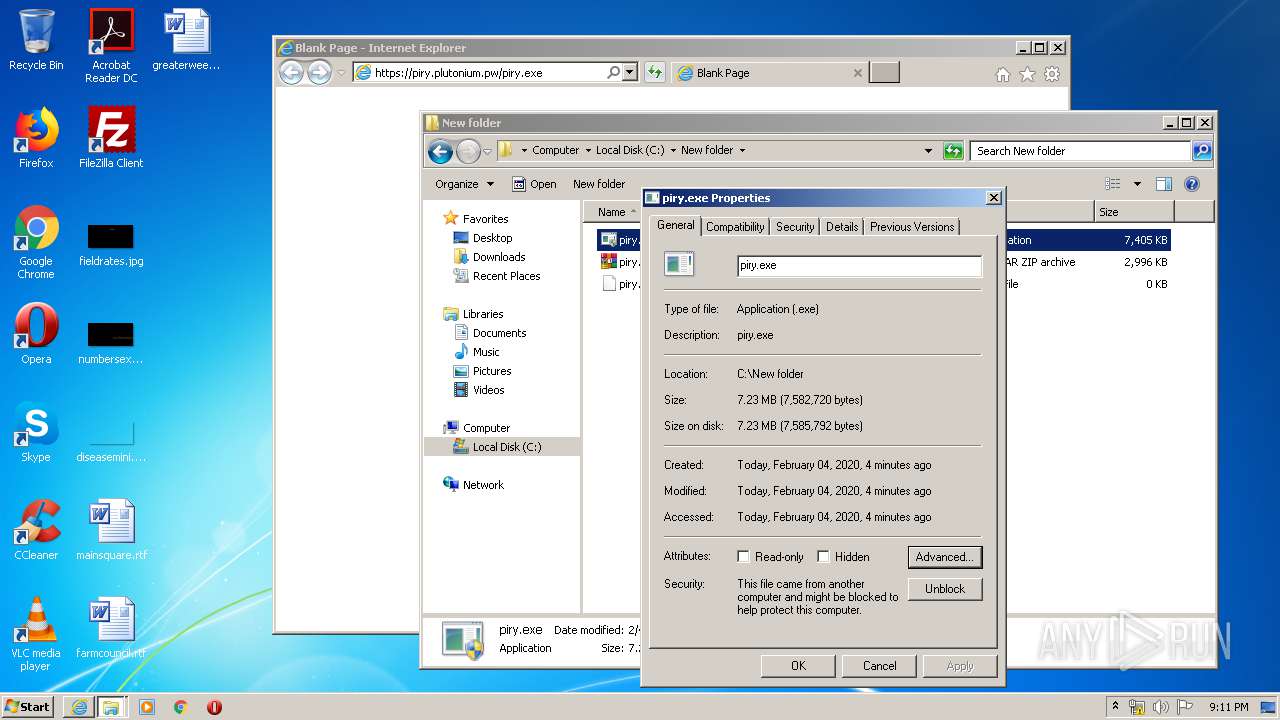
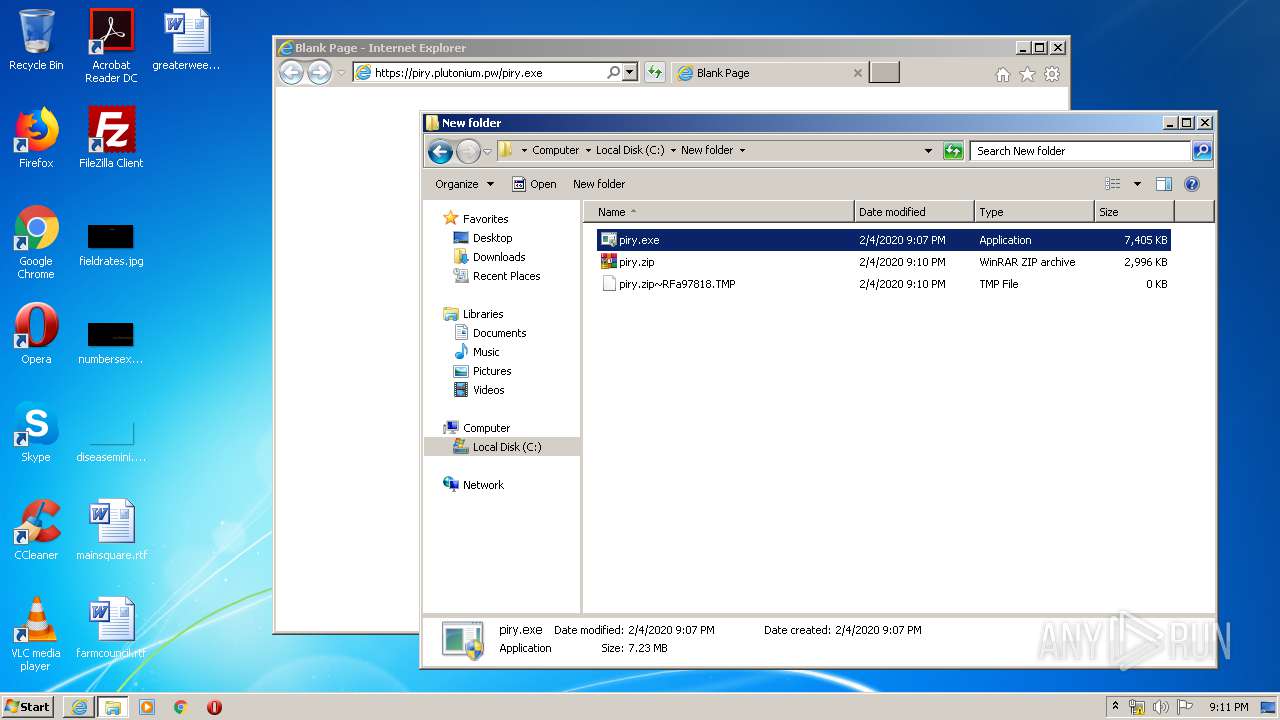
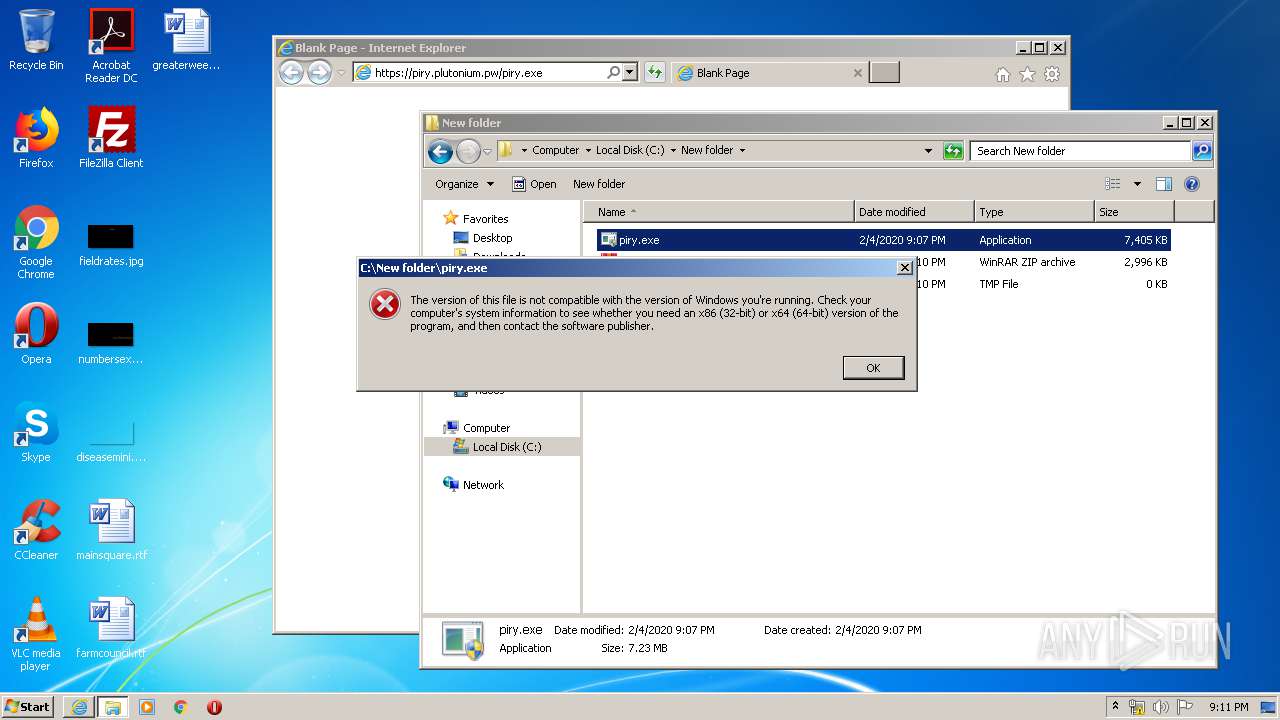
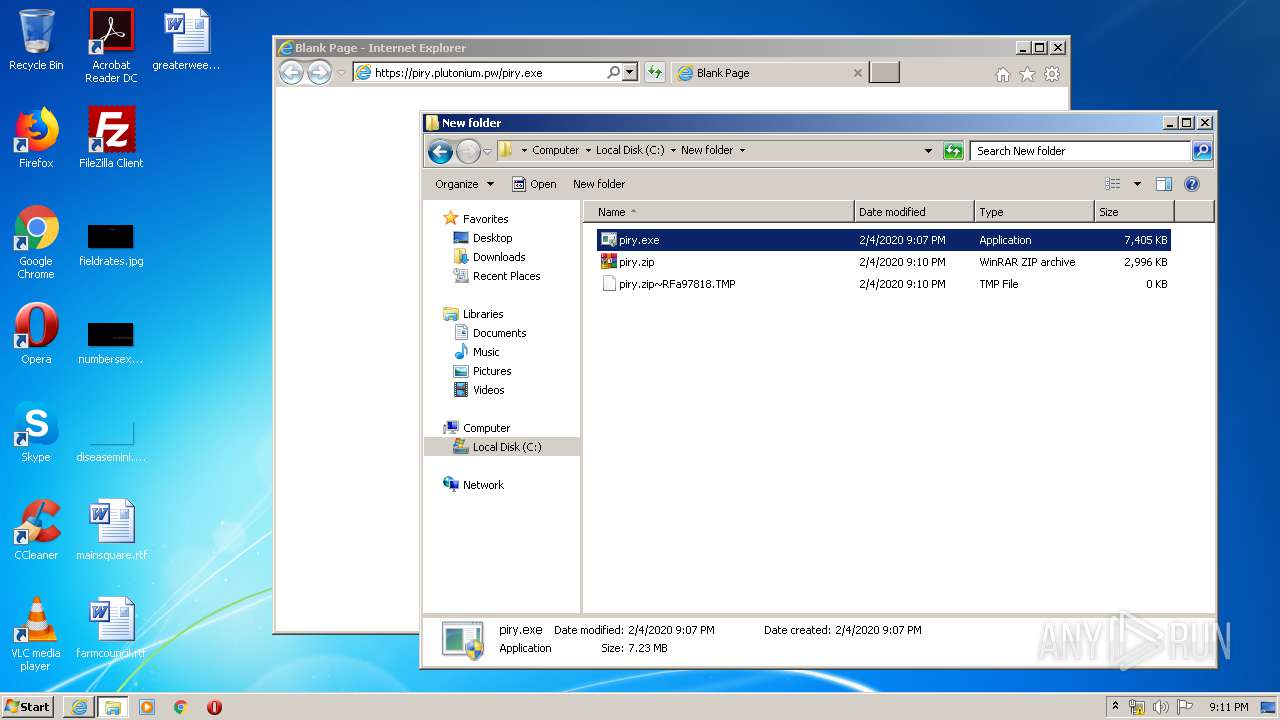
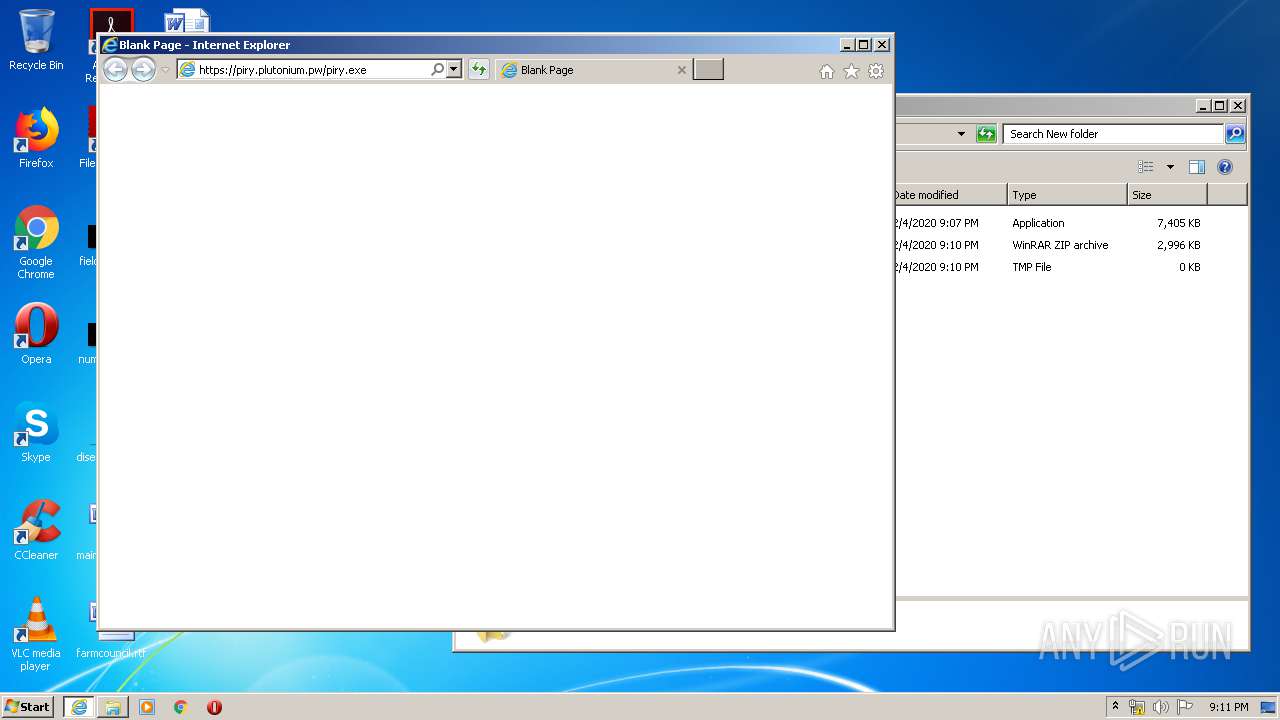
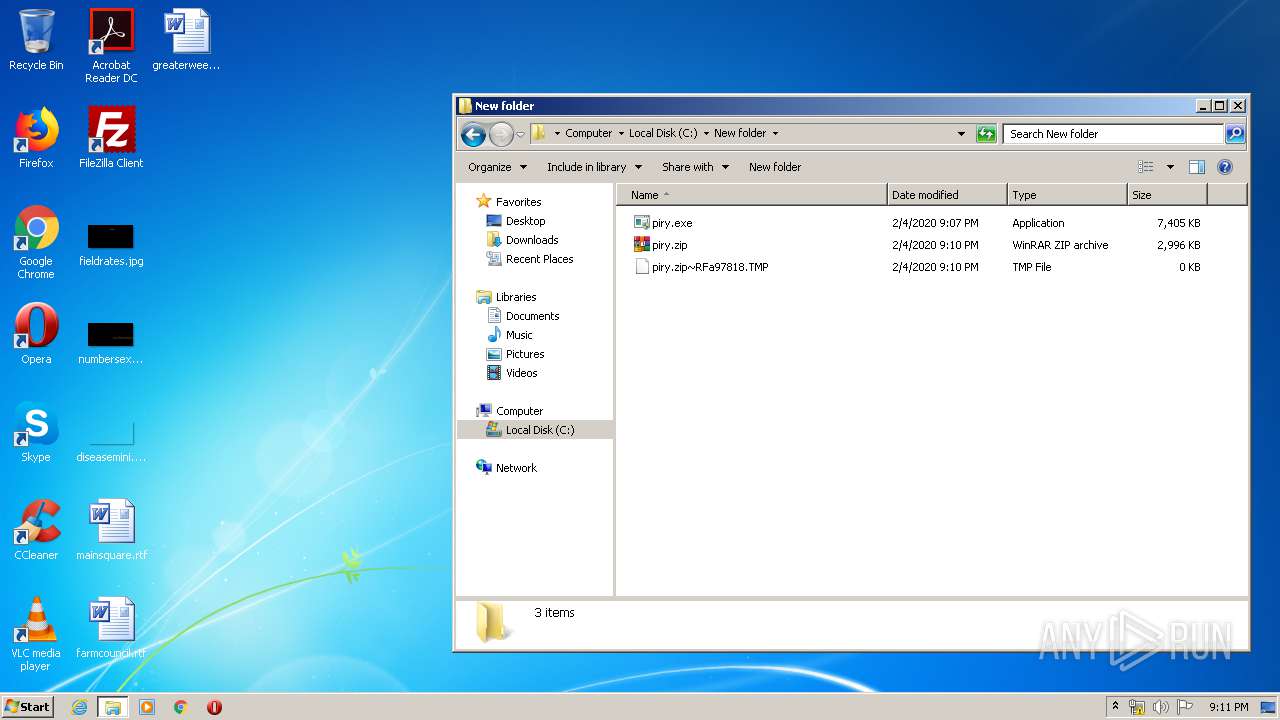
| URL: | https://piry.plutonium.pw/piry.exe |
| Full analysis: | https://app.any.run/tasks/b8d66b57-16d6-4a2e-9780-8d393e3531be |
| Verdict: | Suspicious activity |
| Analysis date: | February 04, 2020, 21:06:45 |
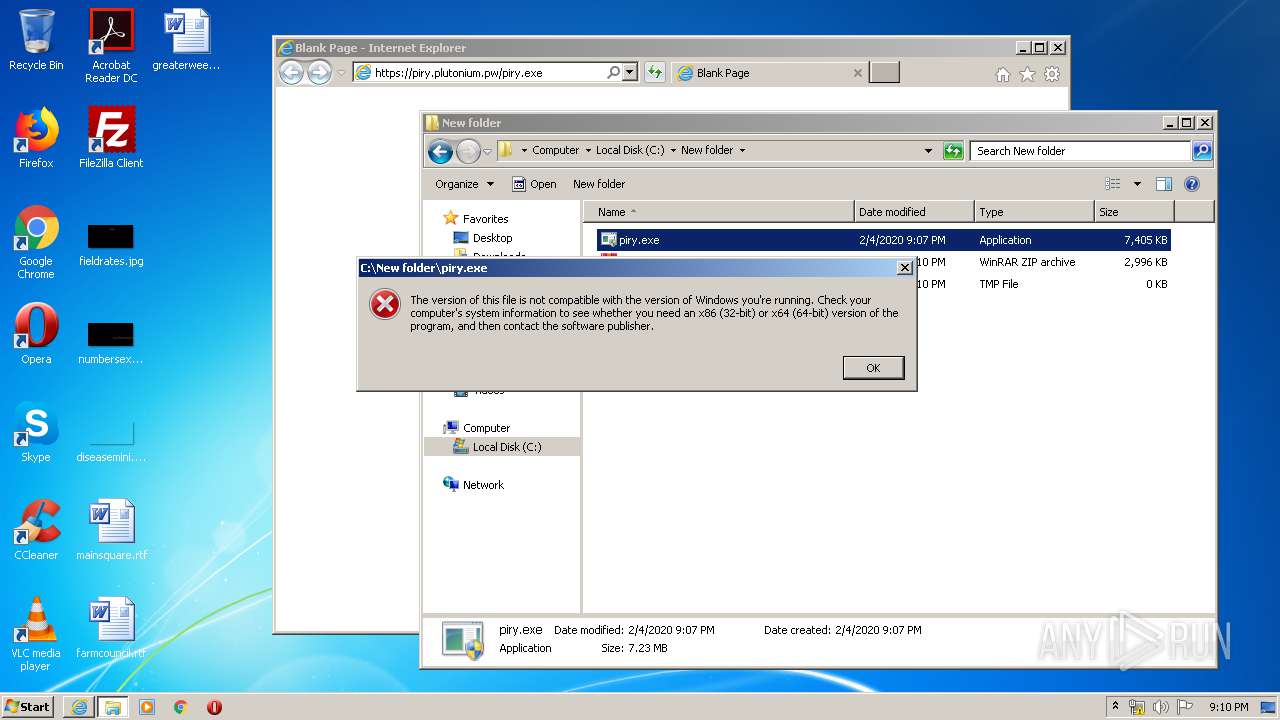
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8E42320E4AFE64AA4D874A5F1A551648 |
| SHA1: | 7650FC2AD84C5719BD6D5399707C6A03AEB75400 |
| SHA256: | 2CDF9E7F15EBC7089F4A56FE7635CCA57827901030CEB3DC08D7223006F48EDD |
| SSDEEP: | 3:N8IMLV+SOvAdAn:2IK4S2AdAn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 2876)
Creates files in the user directory
- notepad++.exe (PID: 2684)
INFO
Creates files in the user directory
- opera.exe (PID: 3456)
- iexplore.exe (PID: 3364)
- iexplore.exe (PID: 2876)
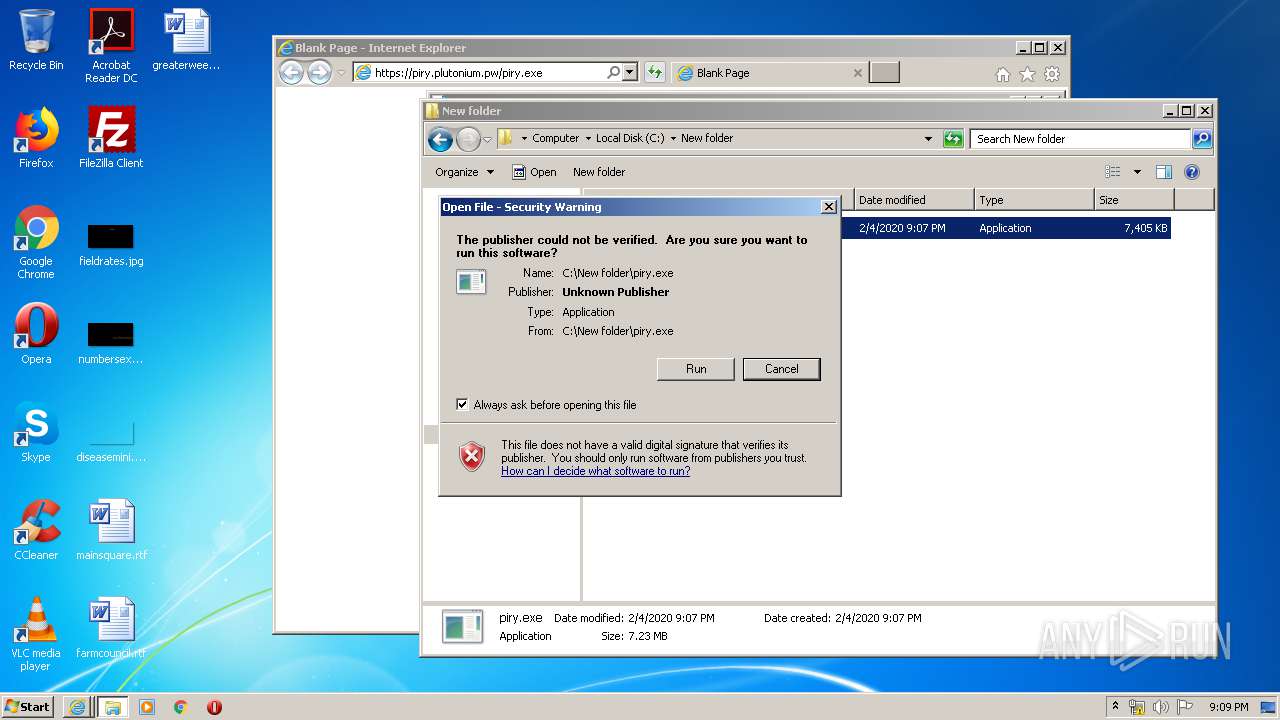
Manual execution by user
- iexplore.exe (PID: 2876)
- explorer.exe (PID: 2948)
- notepad++.exe (PID: 2684)
- wermgr.exe (PID: 2232)
- wermgr.exe (PID: 2916)
- MSASCui.exe (PID: 180)
- wermgr.exe (PID: 2744)
Reads Internet Cache Settings
- iexplore.exe (PID: 3364)
- iexplore.exe (PID: 2876)
Changes internet zones settings
- iexplore.exe (PID: 2876)
Reads internet explorer settings
- iexplore.exe (PID: 3364)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2876)
Reads settings of System Certificates
- iexplore.exe (PID: 3364)
- iexplore.exe (PID: 2876)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2876)
Changes settings of System certificates
- iexplore.exe (PID: 2876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
10
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 180 | "C:\Program Files\Windows Defender\MSASCui.exe" | C:\Program Files\Windows Defender\MSASCui.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Defender User Interface Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2232 | "C:\Windows\system32\wermgr.exe" "-outproc" "372" "4684" | C:\Windows\system32\wermgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
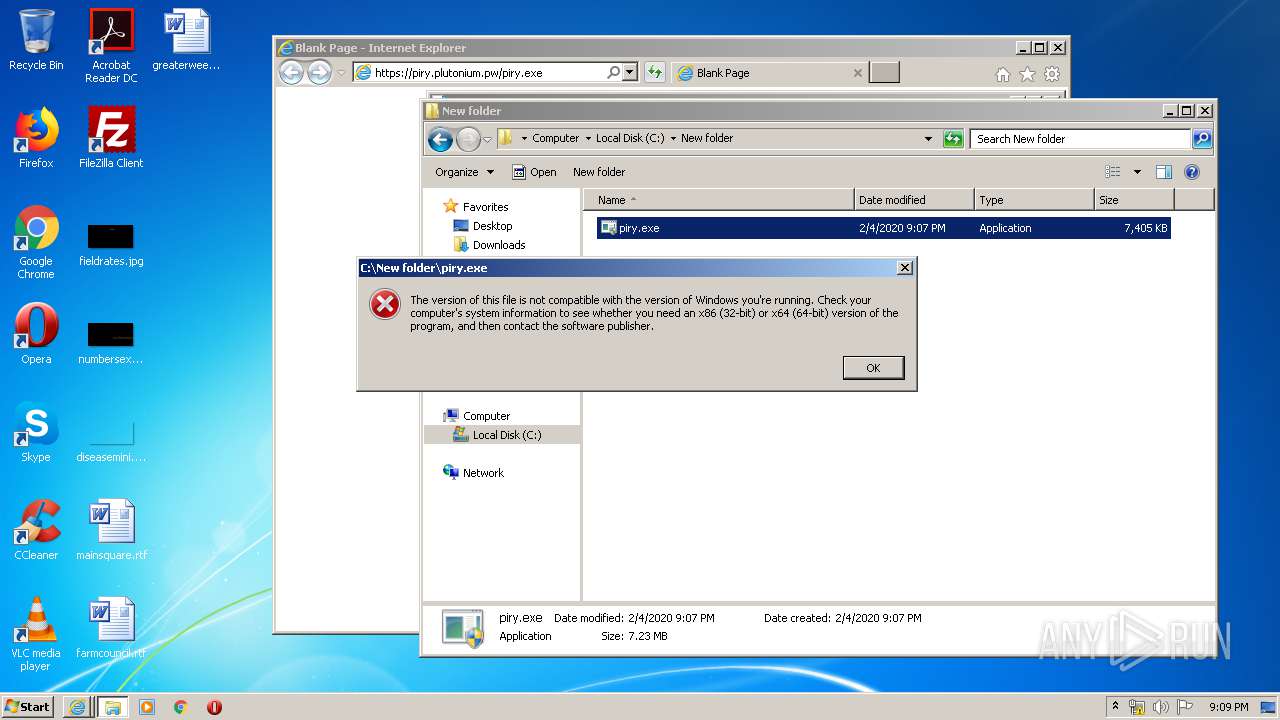
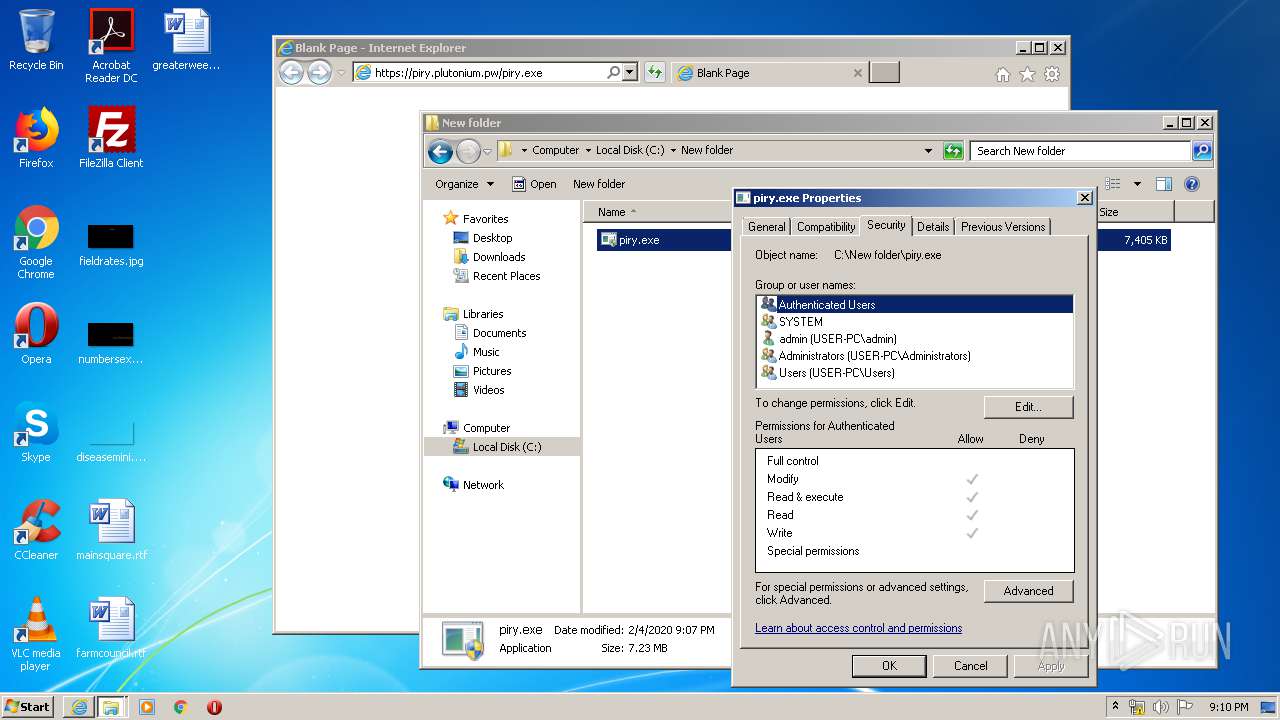
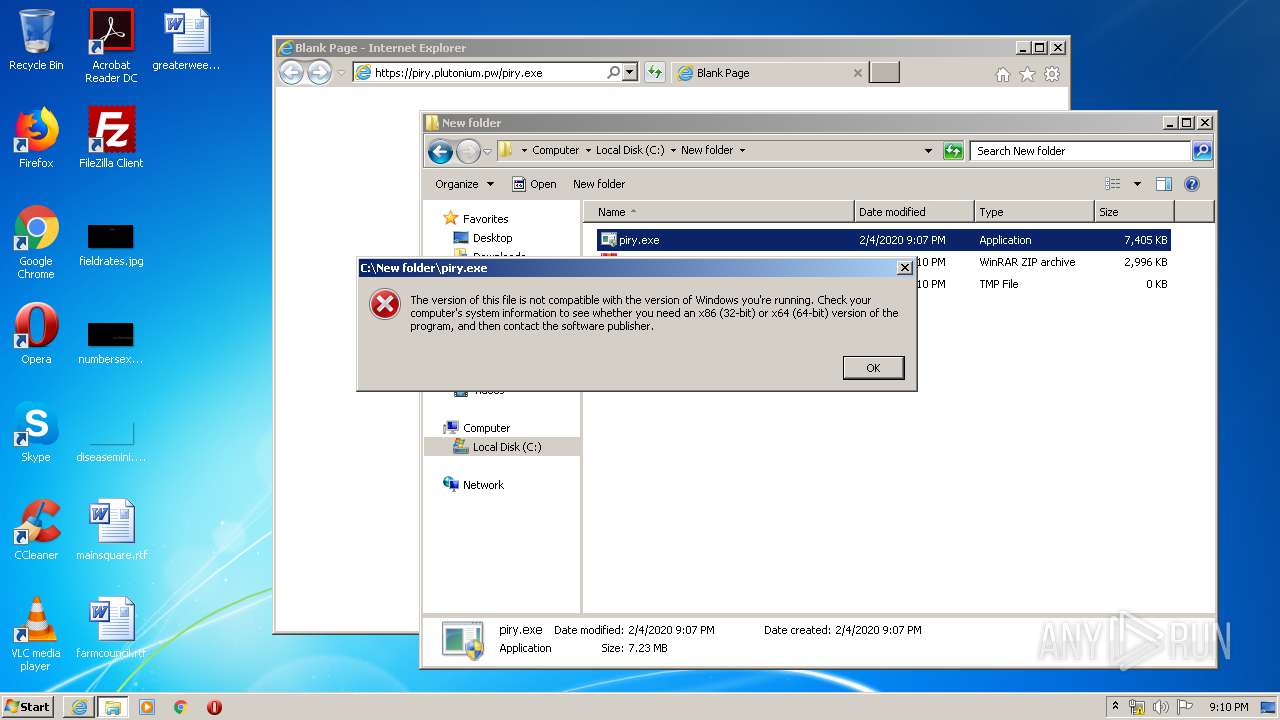
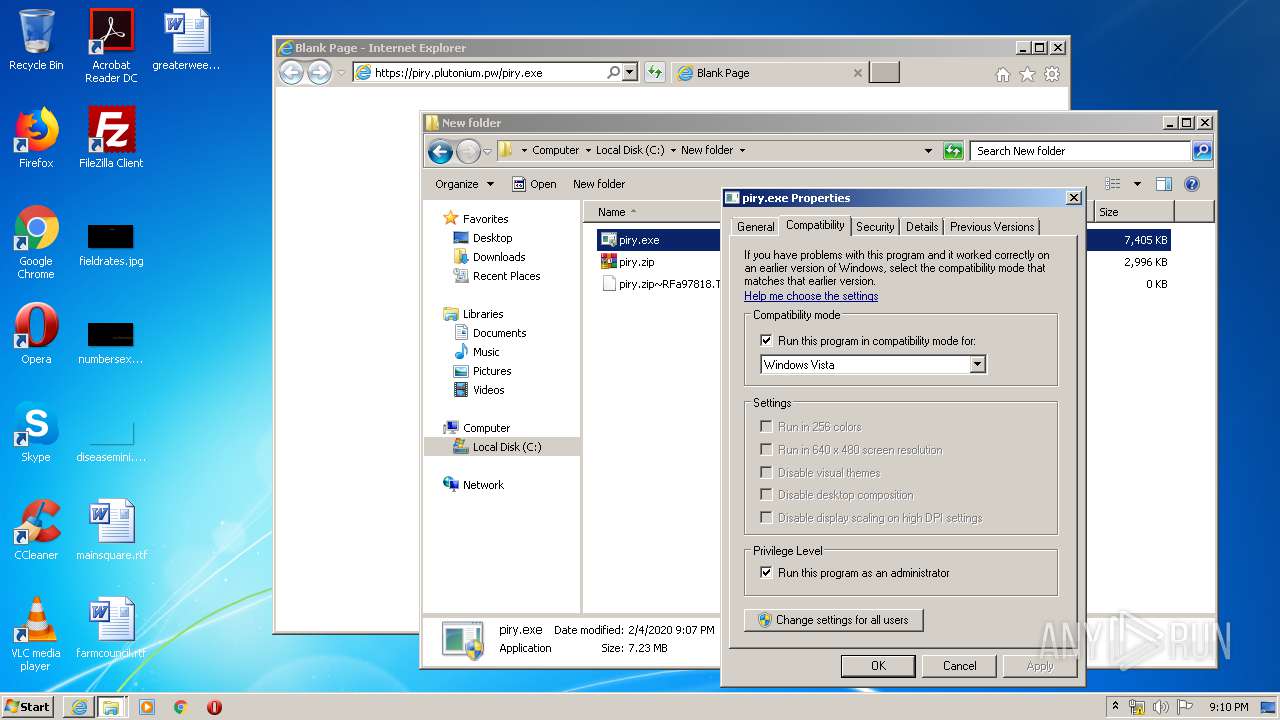
| 2684 | "C:\Program Files\Notepad++\notepad++.exe" "C:\New folder\piry.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 2744 | "C:\Windows\system32\wermgr.exe" "-outproc" "372" "4800" | C:\Windows\system32\wermgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2876 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2916 | "C:\Windows\system32\wermgr.exe" "-outproc" "372" "4812" | C:\Windows\system32\wermgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2948 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3156 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 3364 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2876 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3456 | "C:\Program Files\Opera\opera.exe" "https://piry.plutonium.pw/piry.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
Total events
11 361
Read events
2 038
Write events
6 272
Delete events
3 051
Modification events
| (PID) Process: | (3456) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe "https://piry.plutonium.pw/piry.exe" | |||
| (PID) Process: | (3456) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 901719172 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30792607 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2876) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
Executable files
2
Suspicious files
71
Text files
37
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3456 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr725A.tmp | — | |
MD5:— | SHA256:— | |||
| 3456 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr726A.tmp | — | |
MD5:— | SHA256:— | |||
| 3456 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr72B9.tmp | — | |
MD5:— | SHA256:— | |||
| 3456 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\PVWSCZ3PB6S0V19LPQ2P.temp | — | |
MD5:— | SHA256:— | |||
| 3456 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr8018.tmp | — | |
MD5:— | SHA256:— | |||
| 3456 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00003.tmp | — | |
MD5:— | SHA256:— | |||
| 3456 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprD713.tmp | — | |
MD5:— | SHA256:— | |||
| 3456 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
| 3456 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3456 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
48
DNS requests
19
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3456 | opera.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAMyqCwkFn9oa4q3%2BwjYTqs%3D | US | der | 471 b | whitelisted |
3364 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
2876 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2876 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2876 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3364 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
2876 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2876 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3456 | opera.exe | GET | 200 | 37.228.108.144:80 | http://redir.opera.com/favicons/google/favicon.ico | US | image | 5.30 Kb | whitelisted |
3456 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 564 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3456 | opera.exe | 104.27.129.63:443 | piry.plutonium.pw | Cloudflare Inc | US | suspicious |
3456 | opera.exe | 185.26.182.94:443 | sitecheck2.opera.com | Opera Software AS | — | whitelisted |
3456 | opera.exe | 104.27.128.63:443 | piry.plutonium.pw | Cloudflare Inc | US | suspicious |
3456 | opera.exe | 185.26.182.112:443 | sitecheck2.opera.com | Opera Software AS | — | malicious |
3456 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3456 | opera.exe | 37.228.108.144:80 | redir.opera.com | Opera Software AS | US | unknown |
3456 | opera.exe | 52.29.59.201:443 | help.opera.com | Amazon.com, Inc. | DE | unknown |
3456 | opera.exe | 35.158.231.255:443 | help.opera.com | Amazon.com, Inc. | DE | unknown |
3456 | opera.exe | 2.19.40.90:443 | www-static-sites.operacdn.com | Akamai International B.V. | — | whitelisted |
2876 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
piry.plutonium.pw |
| suspicious |
sitecheck2.opera.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
redir.opera.com |
| whitelisted |
help.opera.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www-static-sites.operacdn.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
3456 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3456 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3456 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3456 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|