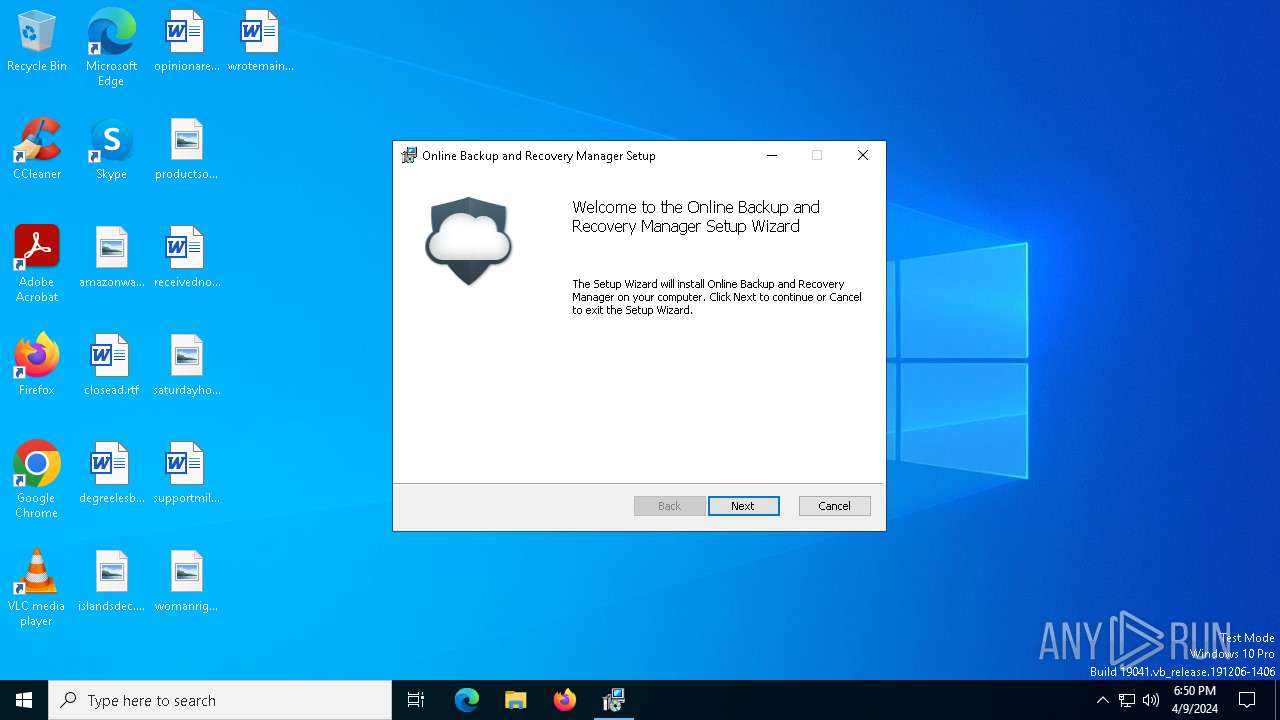
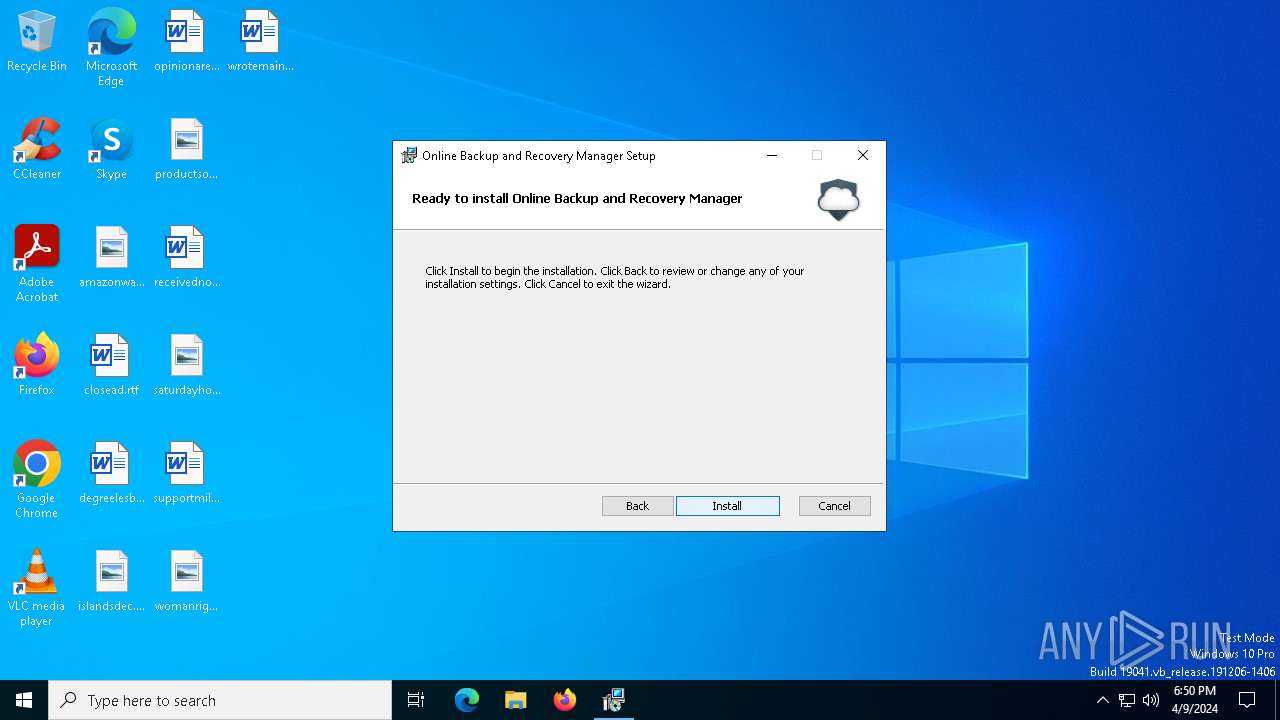
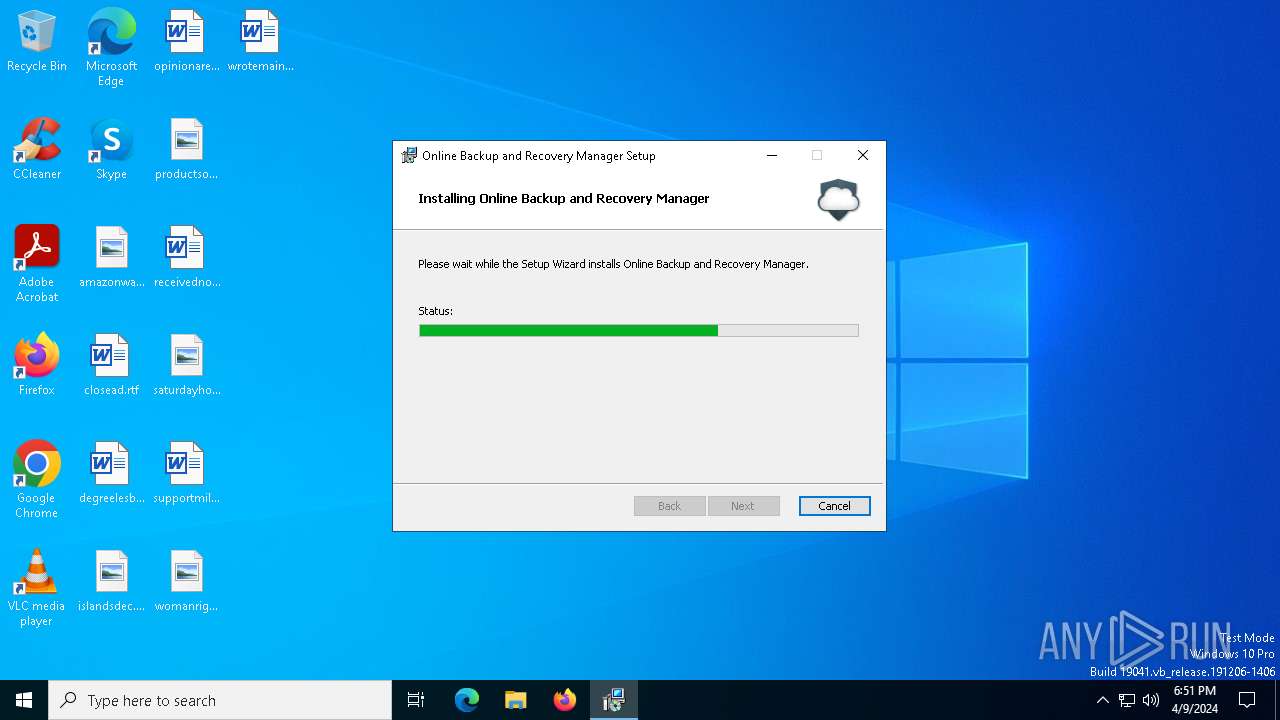
| File name: | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe |
| Full analysis: | https://app.any.run/tasks/b184c084-6137-4a33-aed5-bb7587689199 |
| Verdict: | Malicious activity |
| Analysis date: | April 09, 2024, 18:50:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B4A6D59F0CF7DEFE58A53F64A3F27ABA |
| SHA1: | 75EC37966E19B7360824909D8A5297C87A52EE8B |
| SHA256: | 2CD60D18CF037641460538A2187C01BFFA328E3D6DFD0CEDCB33457C9F606A8F |
| SSDEEP: | 98304:k+1MAK2LBwVD9PdmDi726enHklFFn7GAWj3uP1doeoNesuxx92Lh3HDdcP8RlZAm:pG8rZBSav8GdJoJluNSUSpoosV |
MALICIOUS
Drops the executable file immediately after the start
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 4796)
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- msiexec.exe (PID: 6420)
Changes the autorun value in the registry
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- msiexec.exe (PID: 6420)
SUSPICIOUS
Executable content was dropped or overwritten
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 4796)
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- rundll32.exe (PID: 2064)
- rundll32.exe (PID: 6684)
- rundll32.exe (PID: 2960)
- rundll32.exe (PID: 3852)
- rundll32.exe (PID: 3768)
- rundll32.exe (PID: 3744)
The process creates files with name similar to system file names
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
- rundll32.exe (PID: 2064)
- msiexec.exe (PID: 6420)
Searches for installed software
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- dllhost.exe (PID: 6488)
Reads security settings of Internet Explorer
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- SAgent.Service.exe (PID: 5752)
- SStorage.exe (PID: 6892)
Reads the date of Windows installation
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
Starts itself from another location
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
Executes as Windows Service
- VSSVC.exe (PID: 6772)
- SAgent.Service.exe (PID: 5752)
Creates a software uninstall entry
- Setup-8.2.0.396-Generic.exe (PID: 6496)
Checks Windows Trust Settings
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- msiexec.exe (PID: 6420)
Reads the Windows owner or organization settings
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- msiexec.exe (PID: 6420)
Process drops legitimate windows executable
- msiexec.exe (PID: 6420)
The process drops C-runtime libraries
- msiexec.exe (PID: 6420)
Adds/modifies Windows certificates
- Setup-8.2.0.396-Generic.exe (PID: 6496)
Non-standard symbols in registry
- msiexec.exe (PID: 6420)
INFO
Checks supported languages
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 4796)
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- msiexec.exe (PID: 6420)
- msiexec.exe (PID: 7012)
- msiexec.exe (PID: 1036)
- SAgent.Service.exe (PID: 5752)
- SOS_ShortcutActions.exe (PID: 3736)
- SStorage.exe (PID: 6892)
Create files in a temporary directory
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 4796)
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- SOS_ShortcutActions.exe (PID: 3736)
Reads the computer name
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- msiexec.exe (PID: 6420)
- msiexec.exe (PID: 7012)
- msiexec.exe (PID: 1036)
- SAgent.Service.exe (PID: 5752)
- SOS_ShortcutActions.exe (PID: 3736)
- SStorage.exe (PID: 6892)
Reads the machine GUID from the registry
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- msiexec.exe (PID: 6420)
- SAgent.Service.exe (PID: 5752)
- SOS_ShortcutActions.exe (PID: 3736)
- SStorage.exe (PID: 6892)
Process checks computer location settings
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
Creates files in the program directory
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- SStorage.exe (PID: 6892)
- SAgent.Service.exe (PID: 5752)
Reads the software policy settings
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- msiexec.exe (PID: 6420)
- slui.exe (PID: 4640)
Checks proxy server information
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- SStorage.exe (PID: 6892)
- slui.exe (PID: 4640)
Creates files or folders in the user directory
- Setup-8.2.0.396-Generic.exe (PID: 6496)
- rundll32.exe (PID: 2064)
- SOS_ShortcutActions.exe (PID: 3736)
- 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe (PID: 6332)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6420)
Drops the executable file immediately after the start
- rundll32.exe (PID: 2064)
- rundll32.exe (PID: 6684)
- rundll32.exe (PID: 3768)
- rundll32.exe (PID: 3852)
- rundll32.exe (PID: 2960)
- rundll32.exe (PID: 3744)
Creates a software uninstall entry
- msiexec.exe (PID: 6420)
Reads Environment values
- SAgent.Service.exe (PID: 5752)
- SStorage.exe (PID: 6892)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 3744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:22 15:58:18+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 302080 |
| InitializedDataSize: | 178176 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2e082 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.2.0.396 |
| ProductVersionNumber: | 8.2.0.396 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Managed Offsite Backup |
| FileDescription: | Online Backup and Recovery Manager |
| FileVersion: | 8.2.0.396 |
| InternalName: | setup |
| LegalCopyright: | Copyright (c) Managed Offsite Backup. All rights reserved. |
| OriginalFileName: | Setup-8.2.0.396-Generic.exe |
| ProductName: | Online Backup and Recovery Manager |
| ProductVersion: | 8.2.0.396 |
Total processes
152
Monitored processes
24
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\WINDOWS\system32\sc.exe" config sagentservice start= delayed-auto | C:\Windows\SysWOW64\sc.exe | — | rundll32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | C:\Windows\syswow64\MsiExec.exe -Embedding F69D94990824D3B4D9127747E6DA2578 E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2064 | rundll32.exe "C:\WINDOWS\Installer\MSIADDF.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_962187 2 SOS.Installer.WixSharp!SOS.Installer.WixSharp.CustomActions.SaveAccountCreatorRunnerSettingsXmlCustomAction.SaveAccountCreatorRunnerSettingsXml | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2960 | rundll32.exe "C:\WINDOWS\Installer\MSIC005.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_966656 52 SOS.Installer.WixSharp!SOS.Installer.WixSharp.CustomActions.SetLocaleCustomAction.SetLocale | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3736 | "C:\Program Files (x86)\Online Backup and Recovery Manager\SOS_ShortcutActions.exe" "C:\Program Files (x86)\Online Backup and Recovery Manager\" | C:\Program Files (x86)\Online Backup and Recovery Manager\SOS_ShortcutActions.exe | — | msiexec.exe | |||||||||||
User: admin Integrity Level: HIGH Description: SOS.ShortcutActions Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3744 | rundll32.exe "C:\WINDOWS\Installer\MSIC49C.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_967937 84 SOS.Installer.WixSharp!SOS.Installer.WixSharp.CustomActions.LaunchSStorageCustomAction.LaunchSStorage | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3768 | rundll32.exe "C:\WINDOWS\Installer\MSIC15F.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_967046 67 SOS.Installer.WixSharp!SOS.Installer.WixSharp.CustomActions.ConfigureSAgentServiceCustomAction.ConfigureSAgentService | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3852 | rundll32.exe "C:\WINDOWS\Installer\MSIBF39.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_966484 36 SOS.Installer.WixSharp!SOS.Installer.WixSharp.CustomActions.MoveFileCustomAction.MoveFile | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.746 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3984 | "C:\WINDOWS\system32\sc.exe" failure sagentservice reset= 0 actions= restart/1000/restart/1000/restart/1000 | C:\Windows\SysWOW64\sc.exe | — | rundll32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4080 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:6 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
31 896
Read events
31 155
Write events
698
Delete events
43
Modification events
| (PID) Process: | (6332) 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6332) 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6332) 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6332) 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6488) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000070C993C4AE8ADA015819000068060000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6496) Setup-8.2.0.396-Generic.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000007E6491C4AE8ADA0160190000EC120000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6488) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000C24FBCC4AE8ADA015819000068060000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6488) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000C24FBCC4AE8ADA015819000068060000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6488) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000C24FBCC4AE8ADA015819000068060000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6488) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000007B16C1C4AE8ADA015819000068060000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
252
Suspicious files
32
Text files
89
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4796 | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | C:\Users\admin\AppData\Local\Temp\{736C4001-A0F6-4E6A-8CF9-EEE79B53FA7A}\.cr\2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | executable | |
MD5:— | SHA256:— | |||
| 6332 | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | C:\Users\admin\AppData\Local\Temp\{B241435E-8821-43AB-83D0-02B2EFA0B29C}\.ba\mbahost.dll | executable | |
MD5:— | SHA256:— | |||
| 6332 | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | C:\Users\admin\AppData\Local\Temp\{B241435E-8821-43AB-83D0-02B2EFA0B29C}\.ba\BootstrapperCore.dll | executable | |
MD5:— | SHA256:— | |||
| 6332 | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | C:\Users\admin\AppData\Local\Temp\{B241435E-8821-43AB-83D0-02B2EFA0B29C}\.ba\SOS.Installer.WixSharp.exe | executable | |
MD5:— | SHA256:— | |||
| 6332 | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | C:\Users\admin\AppData\Local\Temp\{B241435E-8821-43AB-83D0-02B2EFA0B29C}\.ba\BootstrapperCore.config | xml | |
MD5:— | SHA256:— | |||
| 6332 | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | C:\Users\admin\AppData\Local\Temp\{B241435E-8821-43AB-83D0-02B2EFA0B29C}\.ba\Microsoft.Deployment.WindowsInstaller.dll | executable | |
MD5:— | SHA256:— | |||
| 6332 | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | C:\Users\admin\AppData\Local\Temp\{B241435E-8821-43AB-83D0-02B2EFA0B29C}\.ba\mbapreq.dll | executable | |
MD5:— | SHA256:— | |||
| 6332 | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | C:\Users\admin\AppData\Local\Temp\{B241435E-8821-43AB-83D0-02B2EFA0B29C}\.ba\mbapreq.thm | xml | |
MD5:— | SHA256:— | |||
| 6332 | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | C:\Users\admin\AppData\Local\Temp\{B241435E-8821-43AB-83D0-02B2EFA0B29C}\.ba\mbapreq.png | image | |
MD5:— | SHA256:— | |||
| 6332 | 2cd60d18cf037641460538a2187c01bffa328e3d6dfd0cedcb33457c9f606a8f.exe | C:\Users\admin\AppData\Local\Temp\{B241435E-8821-43AB-83D0-02B2EFA0B29C}\.ba\mbapreq.wxl | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
37
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3996 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
2060 | svchost.exe | POST | 302 | 2.16.210.157:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
6496 | Setup-8.2.0.396-Generic.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | unknown | — | — | unknown |
6496 | Setup-8.2.0.396-Generic.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | unknown | — | — | unknown |
6304 | SIHClient.exe | GET | 200 | 23.7.139.93:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
6496 | Setup-8.2.0.396-Generic.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEkwRzBFMEMwQTAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCCT6srqaKUzj | unknown | — | — | unknown |
6304 | SIHClient.exe | GET | 200 | 23.7.139.93:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2060 | svchost.exe | POST | 302 | 2.16.210.157:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
2060 | svchost.exe | POST | 502 | 20.231.121.79:80 | http://dmd.metaservices.microsoft.com/metadata.svc | unknown | — | — | unknown |
2060 | svchost.exe | POST | 302 | 2.16.210.157:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1280 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3996 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3996 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
6296 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2060 | svchost.exe | 2.16.210.157:80 | go.microsoft.com | AKAMAI-AS | FR | unknown |
2060 | svchost.exe | 138.91.171.81:80 | dmd.metaservices.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6496 | Setup-8.2.0.396-Generic.exe | 192.124.249.22:80 | ocsp.godaddy.com | SUCURI-SEC | US | unknown |
6304 | SIHClient.exe | 20.114.59.183:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
dmd.metaservices.microsoft.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
SAgent.Service.exe | Verify completed in 0 milliseconds, total of 1 times in 0 milliseconds.
|
SAgent.Service.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\Online Backup and Recovery Manager\x64\SQLite.Interop.dll"...
|